MITS5004 - Data Security Techniques: Algorithm Analysis Report
VerifiedAdded on 2022/10/19
|11
|2207
|437
Report
AI Summary
This report provides a comprehensive analysis of data security techniques, focusing on the application of encryption algorithms for protecting data transmitted within network systems. The report critically assesses three key encryption methods: AES (Advanced Encryption Standard), DES (Data Encryption Standard), and RSA (Rivest-Shamir-Adleman) algorithms. It examines the intention and content of a selected academic article, delving into the functionalities, strengths, and weaknesses of each algorithm. The report discusses the results of the analysis, highlighting key differences in key size, algorithm type (symmetric vs. asymmetric), and implementation aspects. Furthermore, the report compares the algorithms, concluding that encryption methodologies are crucial for data security within network systems and that the selection of an appropriate algorithm is critical for ensuring effective data protection. The report is structured to provide a clear understanding of the algorithms and their practical implications, reinforcing the importance of data security in modern computing environments. The report also provides a comparison of these algorithms, highlighting the best framework for implementation of the algorithm for maintaining the security of the data.

Running head: DATA SECURITY TECHNIQUES
DATA SECURITY TECHNIQUES
Name of the student:
Name of the university:
Author Note:
DATA SECURITY TECHNIQUES
Name of the student:
Name of the university:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1DATA SECURITY TECHNIQUES
Table of Contents
1.0 Introduction..........................................................................................................................2
2.0 Article Analysis....................................................................................................................2
2.1 Intention and Content of the Article.................................................................................3
2.2 Discussion of Results.......................................................................................................7
2.3 Discussion of Conclusion.................................................................................................7
3.0 Conclusion............................................................................................................................8
4.0 References............................................................................................................................9
Table of Contents
1.0 Introduction..........................................................................................................................2
2.0 Article Analysis....................................................................................................................2
2.1 Intention and Content of the Article.................................................................................3
2.2 Discussion of Results.......................................................................................................7
2.3 Discussion of Conclusion.................................................................................................7
3.0 Conclusion............................................................................................................................8
4.0 References............................................................................................................................9

2DATA SECURITY TECHNIQUES
1.0 Introduction
The significant report will be associated with the important techniques associated with
the encryption of the data that are efficiently related with the security of the data. These data
are being identified in respect to the fact that they are being transmitted within the overall
network servers. The potential security of the network has been depicted to be evaluated as
the most significant criteria, which is associated with the security of the data. The sector or
technique of encryption associated with the overall data security as well as the network server
security is depicted to be the important solution in respect to the network server security
mechanisms. The main purpose of this report will be associated with the overall encryption
techniques associated with the protection of the data present within the network systems.
The report will provide a critical assessment as well as a significant analysis in respect
to the three important data encryption techniques, which are depicted as AES, DES as well as
RSA algorithms. These algorithms will provide a critical overview in the fact of the
encryption methodologies that will be helpful for the security of the data associated within
the network servers. This analysis of the significant article will provide a clear overview in
respect to the different encryption methodologies that will be associated with the potential
security of the data. The overall potential analysis of the article will be carried out in respect
to the considered article that will provide a clear overview in the stated encryption
algorithms.
2.0 Article Analysis
The article that that is considered for the critical evaluation of the different algorithms
associated with the encryption methodologies is provided below:
“P. Mahajan and A. Sachdeva, A study of encryption algorithms AES, DES and RSA for
security. Global Journal of Computer Science and Technology, 2013.”
1.0 Introduction
The significant report will be associated with the important techniques associated with
the encryption of the data that are efficiently related with the security of the data. These data
are being identified in respect to the fact that they are being transmitted within the overall
network servers. The potential security of the network has been depicted to be evaluated as
the most significant criteria, which is associated with the security of the data. The sector or
technique of encryption associated with the overall data security as well as the network server
security is depicted to be the important solution in respect to the network server security
mechanisms. The main purpose of this report will be associated with the overall encryption
techniques associated with the protection of the data present within the network systems.
The report will provide a critical assessment as well as a significant analysis in respect
to the three important data encryption techniques, which are depicted as AES, DES as well as
RSA algorithms. These algorithms will provide a critical overview in the fact of the
encryption methodologies that will be helpful for the security of the data associated within
the network servers. This analysis of the significant article will provide a clear overview in
respect to the different encryption methodologies that will be associated with the potential
security of the data. The overall potential analysis of the article will be carried out in respect
to the considered article that will provide a clear overview in the stated encryption
algorithms.
2.0 Article Analysis
The article that that is considered for the critical evaluation of the different algorithms
associated with the encryption methodologies is provided below:
“P. Mahajan and A. Sachdeva, A study of encryption algorithms AES, DES and RSA for
security. Global Journal of Computer Science and Technology, 2013.”
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3DATA SECURITY TECHNIQUES
2.1 Intention and Content of the Article
The significant article depicts that the algorithms such as AES, RSA as well as DES
that are associated with the overall encryption of the data associated within the network
server. According to Mahajan and Sachdeva (2013), it can be analysed that encryption is
identified as a significant solution in respect to the overall security of the information systems
[1] . The noteworthy transmission of the data within the network server from a sender to its
specific receiver must be potentially encrypted in respect to the security of the data.
Moreover, the knowledge of cryptography puts a significant focus in respect to the encryption
as well as decryption techniques that will be used for the enhanced security of the data thus
adhering the overall consequences in respect to the security performance of the overall data
that are being transmitted within the network security [10]. In accordance to the performance
associated with the overall encryption methodologies it can be depicted that the security of
the data. In the further means, it can be identified to provide a great deal of effective data
transmission within the overall server.
The article clearly provides an overview of the encryption algorithms that are
significantly categorized as Symmetric as well as Asymmetric encryption methodologies.
The concept of symmetric algorithms or encryption methodology is depicted to use a single
key that will be used for the security of the data in both the sender as well as receiver end [8].
Moreover, the concept of asymmetric encryption methodology is identified to use two
different keys that is depicted as public as well as private keys. These two keys are used in
both the different aspects of the sender as well as the receiver for maintaining a security of
the data that are being transmitted within the network servers [4]. The usage of the two
different keys in respect to the asymmetric encryption method is depicted to be important,
related to the security of the data. In this procedure, the public key is associated with the
encryption procedure, whereas the private key is associated with the decryption part.
2.1 Intention and Content of the Article
The significant article depicts that the algorithms such as AES, RSA as well as DES
that are associated with the overall encryption of the data associated within the network
server. According to Mahajan and Sachdeva (2013), it can be analysed that encryption is
identified as a significant solution in respect to the overall security of the information systems
[1] . The noteworthy transmission of the data within the network server from a sender to its
specific receiver must be potentially encrypted in respect to the security of the data.
Moreover, the knowledge of cryptography puts a significant focus in respect to the encryption
as well as decryption techniques that will be used for the enhanced security of the data thus
adhering the overall consequences in respect to the security performance of the overall data
that are being transmitted within the network security [10]. In accordance to the performance
associated with the overall encryption methodologies it can be depicted that the security of
the data. In the further means, it can be identified to provide a great deal of effective data
transmission within the overall server.
The article clearly provides an overview of the encryption algorithms that are
significantly categorized as Symmetric as well as Asymmetric encryption methodologies.
The concept of symmetric algorithms or encryption methodology is depicted to use a single
key that will be used for the security of the data in both the sender as well as receiver end [8].
Moreover, the concept of asymmetric encryption methodology is identified to use two
different keys that is depicted as public as well as private keys. These two keys are used in
both the different aspects of the sender as well as the receiver for maintaining a security of
the data that are being transmitted within the network servers [4]. The usage of the two
different keys in respect to the asymmetric encryption method is depicted to be important,
related to the security of the data. In this procedure, the public key is associated with the
encryption procedure, whereas the private key is associated with the decryption part.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
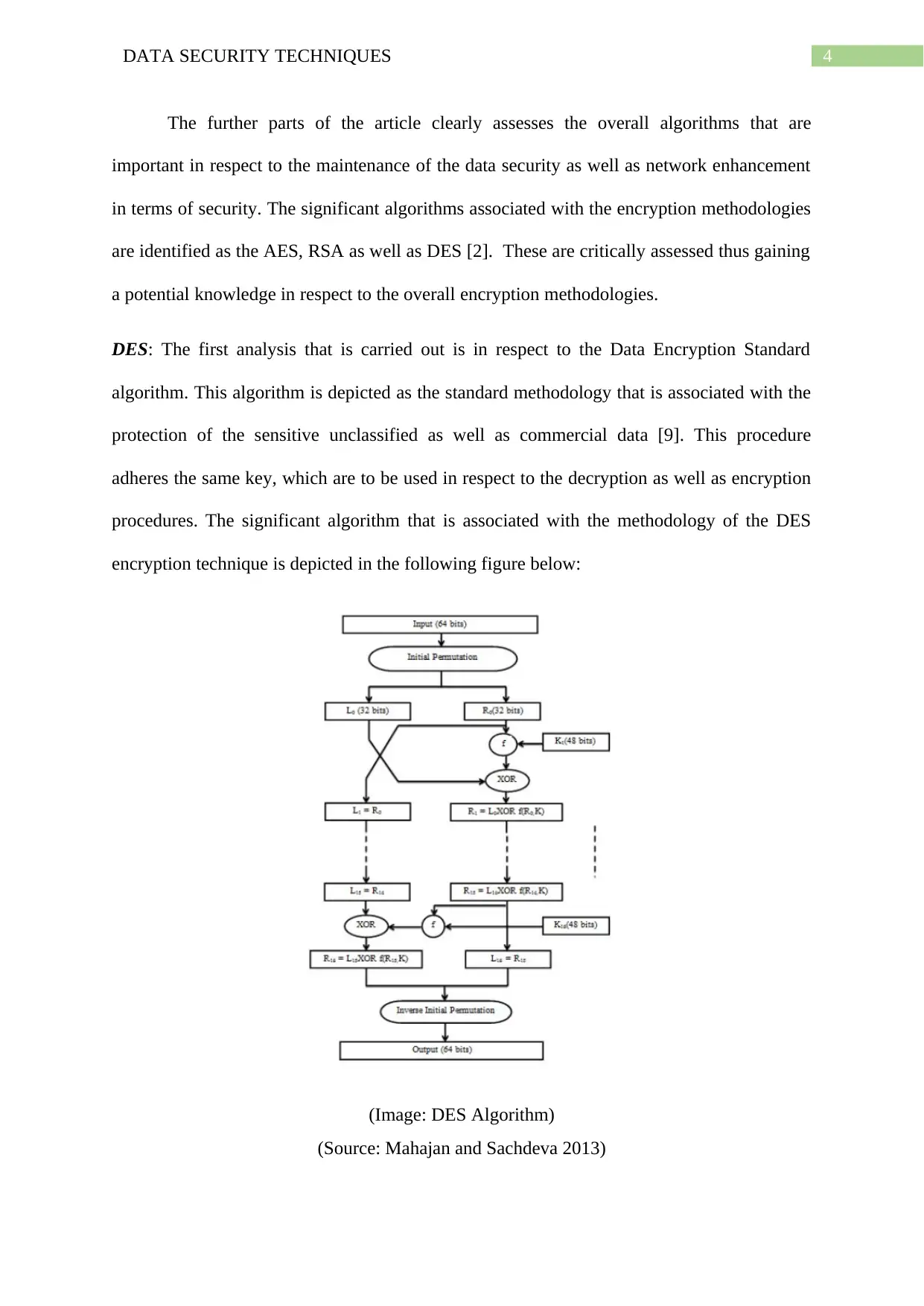
4DATA SECURITY TECHNIQUES
The further parts of the article clearly assesses the overall algorithms that are
important in respect to the maintenance of the data security as well as network enhancement
in terms of security. The significant algorithms associated with the encryption methodologies
are identified as the AES, RSA as well as DES [2]. These are critically assessed thus gaining
a potential knowledge in respect to the overall encryption methodologies.
DES: The first analysis that is carried out is in respect to the Data Encryption Standard
algorithm. This algorithm is depicted as the standard methodology that is associated with the
protection of the sensitive unclassified as well as commercial data [9]. This procedure
adheres the same key, which are to be used in respect to the decryption as well as encryption
procedures. The significant algorithm that is associated with the methodology of the DES
encryption technique is depicted in the following figure below:
(Image: DES Algorithm)
(Source: Mahajan and Sachdeva 2013)
The further parts of the article clearly assesses the overall algorithms that are
important in respect to the maintenance of the data security as well as network enhancement
in terms of security. The significant algorithms associated with the encryption methodologies
are identified as the AES, RSA as well as DES [2]. These are critically assessed thus gaining
a potential knowledge in respect to the overall encryption methodologies.
DES: The first analysis that is carried out is in respect to the Data Encryption Standard
algorithm. This algorithm is depicted as the standard methodology that is associated with the
protection of the sensitive unclassified as well as commercial data [9]. This procedure
adheres the same key, which are to be used in respect to the decryption as well as encryption
procedures. The significant algorithm that is associated with the methodology of the DES
encryption technique is depicted in the following figure below:
(Image: DES Algorithm)
(Source: Mahajan and Sachdeva 2013)
5DATA SECURITY TECHNIQUES
The overall procedure related with the data encryption standard methodology is
depicted to be useful in regards to the security of the data.
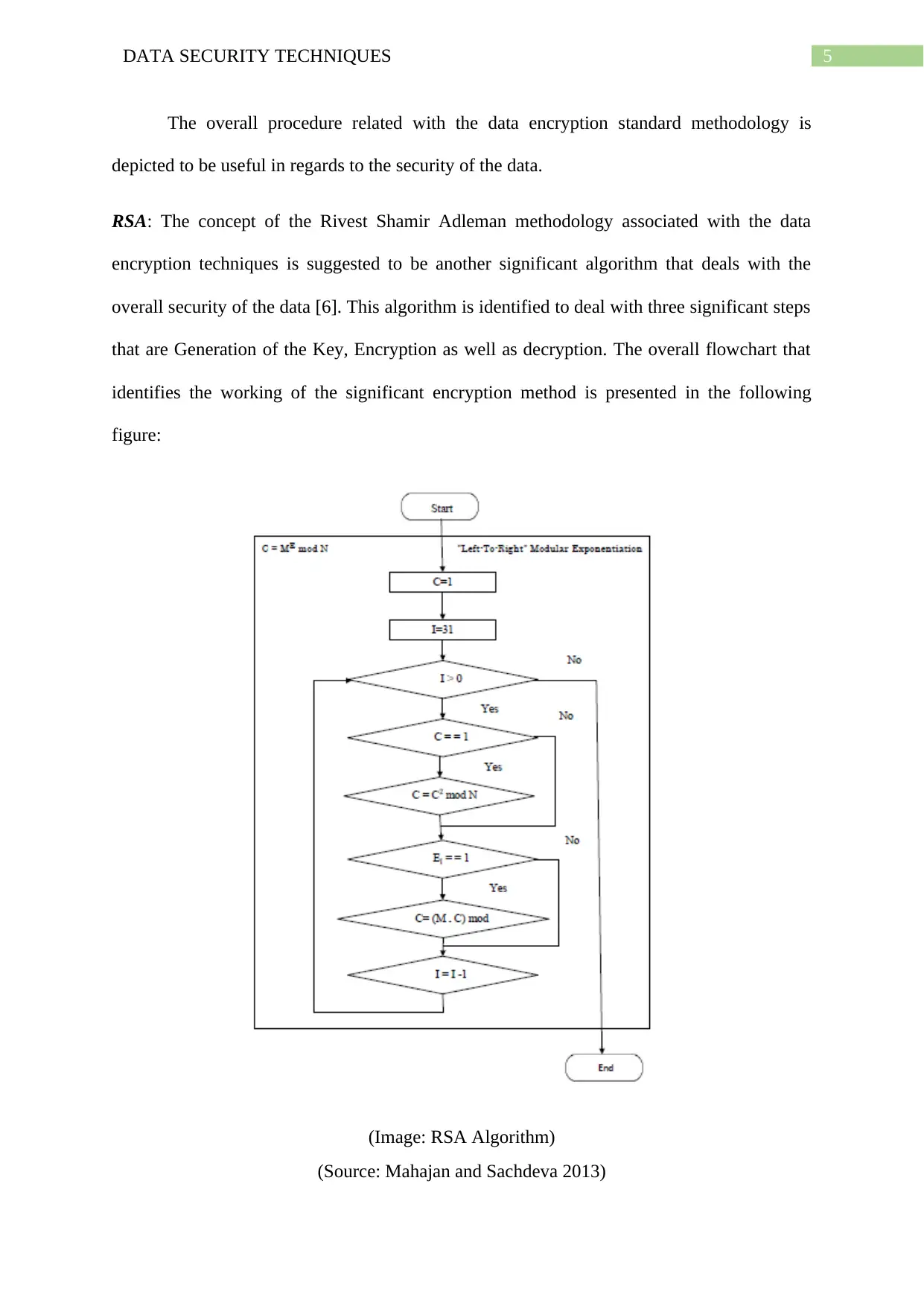
RSA: The concept of the Rivest Shamir Adleman methodology associated with the data
encryption techniques is suggested to be another significant algorithm that deals with the
overall security of the data [6]. This algorithm is identified to deal with three significant steps
that are Generation of the Key, Encryption as well as decryption. The overall flowchart that
identifies the working of the significant encryption method is presented in the following
figure:
(Image: RSA Algorithm)
(Source: Mahajan and Sachdeva 2013)
The overall procedure related with the data encryption standard methodology is
depicted to be useful in regards to the security of the data.
RSA: The concept of the Rivest Shamir Adleman methodology associated with the data
encryption techniques is suggested to be another significant algorithm that deals with the
overall security of the data [6]. This algorithm is identified to deal with three significant steps
that are Generation of the Key, Encryption as well as decryption. The overall flowchart that
identifies the working of the significant encryption method is presented in the following
figure:
(Image: RSA Algorithm)
(Source: Mahajan and Sachdeva 2013)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6DATA SECURITY TECHNIQUES
The potential usage of the asymmetric key algorithm in respect to the overall
procedure of this encryption technique helps the methodology to be significant in respect to
the data security within the overall network server systems [11].
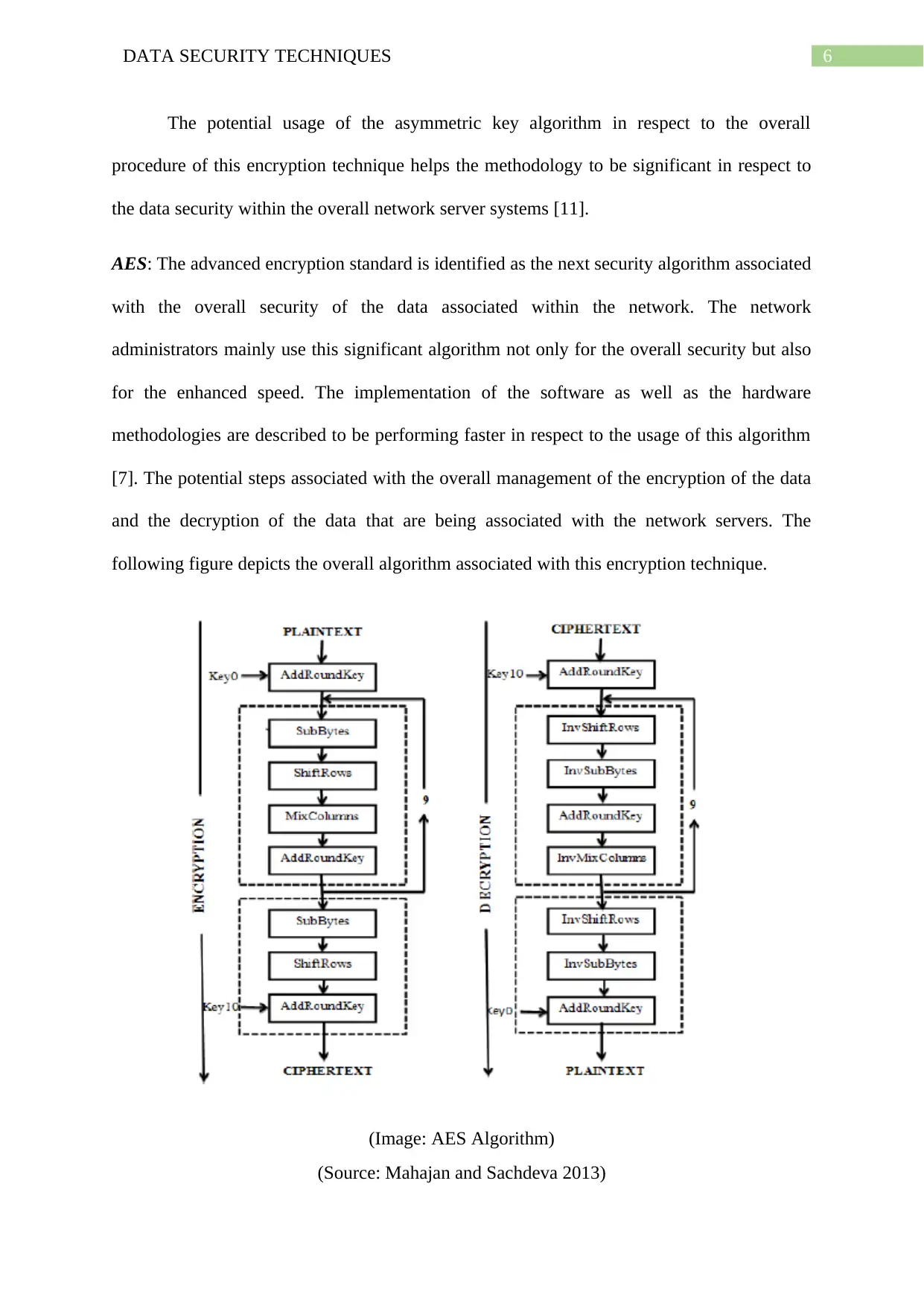
AES: The advanced encryption standard is identified as the next security algorithm associated
with the overall security of the data associated within the network. The network
administrators mainly use this significant algorithm not only for the overall security but also
for the enhanced speed. The implementation of the software as well as the hardware
methodologies are described to be performing faster in respect to the usage of this algorithm
[7]. The potential steps associated with the overall management of the encryption of the data
and the decryption of the data that are being associated with the network servers. The
following figure depicts the overall algorithm associated with this encryption technique.
(Image: AES Algorithm)
(Source: Mahajan and Sachdeva 2013)
The potential usage of the asymmetric key algorithm in respect to the overall
procedure of this encryption technique helps the methodology to be significant in respect to
the data security within the overall network server systems [11].
AES: The advanced encryption standard is identified as the next security algorithm associated
with the overall security of the data associated within the network. The network
administrators mainly use this significant algorithm not only for the overall security but also
for the enhanced speed. The implementation of the software as well as the hardware
methodologies are described to be performing faster in respect to the usage of this algorithm
[7]. The potential steps associated with the overall management of the encryption of the data
and the decryption of the data that are being associated with the network servers. The
following figure depicts the overall algorithm associated with this encryption technique.
(Image: AES Algorithm)
(Source: Mahajan and Sachdeva 2013)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7DATA SECURITY TECHNIQUES
2.2 Discussion of Results
The significant result that is depicted in the considered article revolves round the fact
of the three significant data encryption as well as decryption of the data that flows within the
overall network systems [12]. The detailed explanation of the overall working procedures
associated with these data security techniques are clearly stated within the article that are
potentially analysed as well as evaluated and presented within the report. Moreover, the
comparison of these three types of data security algorithms are also provided within the
article. The comparison duly states the overall points that are stated below:
Key Size: The overall key size that is used by the AES algorithm is identified as 126,256 as
well as192 bits. In case of DES, the key size is identified as 56 bits whereas for the RSA
algorithm the key size is identified to be greater than 1024 bits.
Algorithm: In both cases of AES and DES, symmetric algorithm is used whereas only in the
case of RSA asymmetric algorithm is used [3]. Thus, the ciphering and the deciphering
algorithm is same for the RSA algorithm but the algorithm is different in both the cases of
AES and DES.
Implementation: The significant implementation of the hardware as well as software
becomes faster with the AES methodology whereas the hardware implementation is better in
the DES algorithm rather than in software implementation [5]. The implementation is not at
all efficient in respect to the RSA methodology.
2.3 Discussion of Conclusion
The significant article deals with the fact of the data security in respect to the
implementation of the encryption algorithm. The three types of encryption techniques are
critically assessed in respect to the usage of the particular algorithms. Moreover, the
2.2 Discussion of Results
The significant result that is depicted in the considered article revolves round the fact
of the three significant data encryption as well as decryption of the data that flows within the
overall network systems [12]. The detailed explanation of the overall working procedures
associated with these data security techniques are clearly stated within the article that are
potentially analysed as well as evaluated and presented within the report. Moreover, the
comparison of these three types of data security algorithms are also provided within the
article. The comparison duly states the overall points that are stated below:
Key Size: The overall key size that is used by the AES algorithm is identified as 126,256 as
well as192 bits. In case of DES, the key size is identified as 56 bits whereas for the RSA
algorithm the key size is identified to be greater than 1024 bits.
Algorithm: In both cases of AES and DES, symmetric algorithm is used whereas only in the
case of RSA asymmetric algorithm is used [3]. Thus, the ciphering and the deciphering
algorithm is same for the RSA algorithm but the algorithm is different in both the cases of
AES and DES.
Implementation: The significant implementation of the hardware as well as software
becomes faster with the AES methodology whereas the hardware implementation is better in
the DES algorithm rather than in software implementation [5]. The implementation is not at
all efficient in respect to the RSA methodology.
2.3 Discussion of Conclusion
The significant article deals with the fact of the data security in respect to the
implementation of the encryption algorithm. The three types of encryption techniques are
critically assessed in respect to the usage of the particular algorithms. Moreover, the

8DATA SECURITY TECHNIQUES
comparison of the different algorithms thus suggesting the best framework for the
implementation of the algorithm for maintaining the security of the data.
3.0 Conclusion
Thus, the overall report deals with the significant usage of the different enhanced
algorithms that are related with the aspects of the security of the data. Moreover, the
algorithms are critically assessed in respect to the considered article thus adhering the three
significant concepts that that are likely to be AES, RSA as well as DES encryption
techniques. Thus, it can be depicted that the overall usage of the encryption techniques will
intend to amplify the security of the data that are being transmitted within the overall network
systems. Lastly, it can be concluded that the encryption methodology is a significant
technique that is used in respect the security of the overall data that are transmitted within the
overall network server systems.
comparison of the different algorithms thus suggesting the best framework for the
implementation of the algorithm for maintaining the security of the data.
3.0 Conclusion
Thus, the overall report deals with the significant usage of the different enhanced
algorithms that are related with the aspects of the security of the data. Moreover, the
algorithms are critically assessed in respect to the considered article thus adhering the three
significant concepts that that are likely to be AES, RSA as well as DES encryption
techniques. Thus, it can be depicted that the overall usage of the encryption techniques will
intend to amplify the security of the data that are being transmitted within the overall network
systems. Lastly, it can be concluded that the encryption methodology is a significant
technique that is used in respect the security of the overall data that are transmitted within the
overall network server systems.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9DATA SECURITY TECHNIQUES
4.0 References
[1] P. Mahajan and A. Sachdeva, A study of encryption algorithms AES, DES and RSA for
security. Global Journal of Computer Science and Technology, 2013.
[2] P. Patil, P. Narayankar, D.G. Narayan and S.M. Meena, A comprehensive evaluation of
cryptographic algorithms: DES, 3DES, AES, RSA and Blowfish. Procedia Computer
Science, 78, pp.617-624, 2016.
[3] V.R. Pancholi and B.P. Patel, Enhancement of cloud computing security with secure data
storage using AES. International Journal for Innovative Research in Science and
Technology, 2(9), pp.18-21, 2016.
[4] S.D. Rihan, A. Khalid and S.E.F. Osman, A performance comparison of encryption
algorithms AES and DES. International Journal of Engineering Research & Technology
(IJERT), 4(12), pp.151-154, 2015.
[5] M.N.A. Wahid, A. Ali, B. Esparham and M. Marwan, A Comparison of Cryptographic
Algorithms: DES, 3DES, AES, RSA and Blowfish for Guessing Attacks Prevention. Journal
Computer Science Applications and Information Technology, 3, pp.1-7, 2018.
[6] M.P. Babitha, and K.R. Babu, Secure cloud storage using AES encryption. In 2016
International Conference on Automatic Control and Dynamic Optimization Techniques
(ICACDOT) (pp. 859-864). IEEE, 2016, September.
[7] A. Devi, A. Sharma and A. Rangra, A review on DES, AES and blowfish for image
encryption & decryption. International Journal of Computer Science and Information
Technologies, 6(3), pp.3034-3036, 2015.
[8] A. Gupta and S. Kaushik, A Review: RSA and AES Algorithm. IITM Journal of
Management and IT, 8(1), pp.82-85, 2017.
4.0 References
[1] P. Mahajan and A. Sachdeva, A study of encryption algorithms AES, DES and RSA for
security. Global Journal of Computer Science and Technology, 2013.
[2] P. Patil, P. Narayankar, D.G. Narayan and S.M. Meena, A comprehensive evaluation of
cryptographic algorithms: DES, 3DES, AES, RSA and Blowfish. Procedia Computer
Science, 78, pp.617-624, 2016.
[3] V.R. Pancholi and B.P. Patel, Enhancement of cloud computing security with secure data
storage using AES. International Journal for Innovative Research in Science and
Technology, 2(9), pp.18-21, 2016.
[4] S.D. Rihan, A. Khalid and S.E.F. Osman, A performance comparison of encryption
algorithms AES and DES. International Journal of Engineering Research & Technology
(IJERT), 4(12), pp.151-154, 2015.
[5] M.N.A. Wahid, A. Ali, B. Esparham and M. Marwan, A Comparison of Cryptographic
Algorithms: DES, 3DES, AES, RSA and Blowfish for Guessing Attacks Prevention. Journal
Computer Science Applications and Information Technology, 3, pp.1-7, 2018.
[6] M.P. Babitha, and K.R. Babu, Secure cloud storage using AES encryption. In 2016
International Conference on Automatic Control and Dynamic Optimization Techniques
(ICACDOT) (pp. 859-864). IEEE, 2016, September.
[7] A. Devi, A. Sharma and A. Rangra, A review on DES, AES and blowfish for image
encryption & decryption. International Journal of Computer Science and Information
Technologies, 6(3), pp.3034-3036, 2015.
[8] A. Gupta and S. Kaushik, A Review: RSA and AES Algorithm. IITM Journal of
Management and IT, 8(1), pp.82-85, 2017.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10DATA SECURITY TECHNIQUES
[9] M. Kannan, C. Priya and S. VaishnaviSree, A COMPARATIVE ANALYSIS OF DES,
AES AND RSA CRYPT ALGORITHMS FOR NETWORK SECURITY IN CLOUD
COMPUTING, 2019.
[10] I. Bhargavi, D. Veeraiah and T.M. Padmaja, Securing BIG DATA: A Comparative
Study Across RSA, AES, DES, EC and ECDH. In Computer Communication, Networking
and Internet Security (pp. 355-362). Springer, Singapore, 2017.
[11] S.N. Ghosh, Performance Analysis of AES, DES, RSA And AES-DES-RSA Hybrid
Algorithm for Data Security. International Journal of Innovative and Emerging Research in
Engineering, 2(5), pp.83-88, 2015.
[12] E.S.I. Harba, Secure Data Encryption Through a Combination of AES, RSA and
HMAC. Engineering, Technology & Applied Science Research, 7(4), pp.1781-1785, 2017.
[9] M. Kannan, C. Priya and S. VaishnaviSree, A COMPARATIVE ANALYSIS OF DES,
AES AND RSA CRYPT ALGORITHMS FOR NETWORK SECURITY IN CLOUD
COMPUTING, 2019.
[10] I. Bhargavi, D. Veeraiah and T.M. Padmaja, Securing BIG DATA: A Comparative
Study Across RSA, AES, DES, EC and ECDH. In Computer Communication, Networking
and Internet Security (pp. 355-362). Springer, Singapore, 2017.
[11] S.N. Ghosh, Performance Analysis of AES, DES, RSA And AES-DES-RSA Hybrid
Algorithm for Data Security. International Journal of Innovative and Emerging Research in
Engineering, 2(5), pp.83-88, 2015.
[12] E.S.I. Harba, Secure Data Encryption Through a Combination of AES, RSA and
HMAC. Engineering, Technology & Applied Science Research, 7(4), pp.1781-1785, 2017.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





