Encryption and Security Measures in Computing
VerifiedAdded on 2020/03/01
|6
|2152
|151
Report
AI Summary
This report covers essential concepts of encryption, including symmetric and public key encryption, hashing, and security measures necessary for protecting organizational assets. It discusses the importance of access control, password protection, and the role of deep packet inspection in network security. The report emphasizes the need for robust security policies and training to safeguard sensitive information and prevent unauthorized access.
TOPIC 3
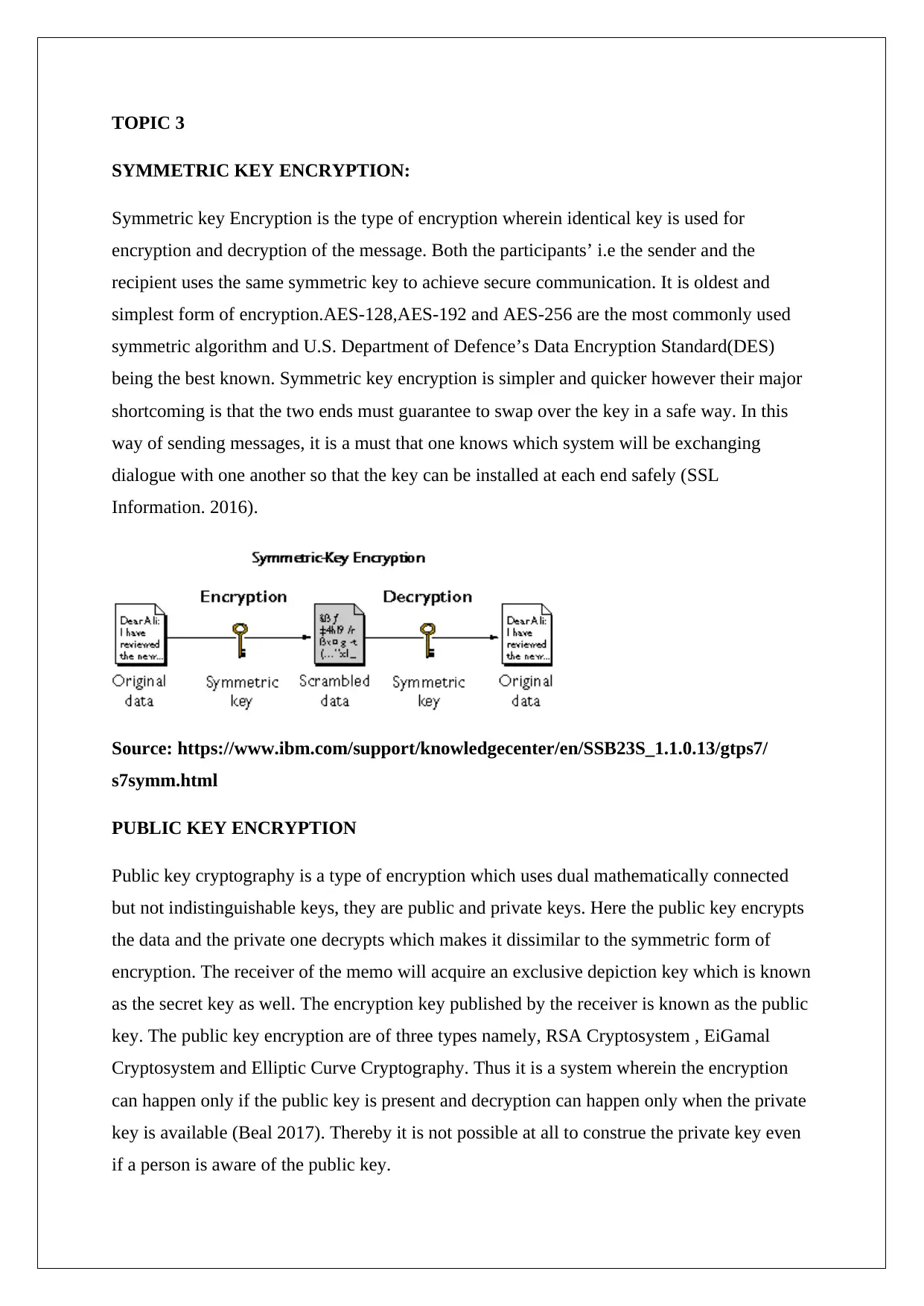
SYMMETRIC KEY ENCRYPTION:
Symmetric key Encryption is the type of encryption wherein identical key is used for
encryption and decryption of the message. Both the participants’ i.e the sender and the
recipient uses the same symmetric key to achieve secure communication. It is oldest and
simplest form of encryption.AES-128,AES-192 and AES-256 are the most commonly used
symmetric algorithm and U.S. Department of Defence’s Data Encryption Standard(DES)
being the best known. Symmetric key encryption is simpler and quicker however their major
shortcoming is that the two ends must guarantee to swap over the key in a safe way. In this
way of sending messages, it is a must that one knows which system will be exchanging
dialogue with one another so that the key can be installed at each end safely (SSL
Information. 2016).
Source: https://www.ibm.com/support/knowledgecenter/en/SSB23S_1.1.0.13/gtps7/
s7symm.html
PUBLIC KEY ENCRYPTION
Public key cryptography is a type of encryption which uses dual mathematically connected
but not indistinguishable keys, they are public and private keys. Here the public key encrypts
the data and the private one decrypts which makes it dissimilar to the symmetric form of
encryption. The receiver of the memo will acquire an exclusive depiction key which is known
as the secret key as well. The encryption key published by the receiver is known as the public
key. The public key encryption are of three types namely, RSA Cryptosystem , EiGamal
Cryptosystem and Elliptic Curve Cryptography. Thus it is a system wherein the encryption
can happen only if the public key is present and decryption can happen only when the private
key is available (Beal 2017). Thereby it is not possible at all to construe the private key even
if a person is aware of the public key.
SYMMETRIC KEY ENCRYPTION:
Symmetric key Encryption is the type of encryption wherein identical key is used for
encryption and decryption of the message. Both the participants’ i.e the sender and the
recipient uses the same symmetric key to achieve secure communication. It is oldest and
simplest form of encryption.AES-128,AES-192 and AES-256 are the most commonly used
symmetric algorithm and U.S. Department of Defence’s Data Encryption Standard(DES)
being the best known. Symmetric key encryption is simpler and quicker however their major
shortcoming is that the two ends must guarantee to swap over the key in a safe way. In this
way of sending messages, it is a must that one knows which system will be exchanging
dialogue with one another so that the key can be installed at each end safely (SSL
Information. 2016).
Source: https://www.ibm.com/support/knowledgecenter/en/SSB23S_1.1.0.13/gtps7/
s7symm.html
PUBLIC KEY ENCRYPTION
Public key cryptography is a type of encryption which uses dual mathematically connected
but not indistinguishable keys, they are public and private keys. Here the public key encrypts
the data and the private one decrypts which makes it dissimilar to the symmetric form of
encryption. The receiver of the memo will acquire an exclusive depiction key which is known
as the secret key as well. The encryption key published by the receiver is known as the public
key. The public key encryption are of three types namely, RSA Cryptosystem , EiGamal
Cryptosystem and Elliptic Curve Cryptography. Thus it is a system wherein the encryption
can happen only if the public key is present and decryption can happen only when the private
key is available (Beal 2017). Thereby it is not possible at all to construe the private key even
if a person is aware of the public key.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

HASHING
Hashing is a conversion of a twine of characters into a generally fixed-length value of a short
nature or key that signify the unique sequence. Hashing is used to key and recover objects
from a record since it is quicker to search the objects with the help of a shorter hashed key
than to search for the same with the help of the unique value. Hashing is also used in various
encryption algorithms. It is popularly known as the hash function. Apart from helping in
quicker retrieval of data, the said function also helps to encrypt and decrypt digital signatures
(Technopaedia.com. 2017). The hash function is used to index the unique key and then is
used later each time the information correlated with the value or key is to be regained.
Therefore it can be concluded that hashing is a one way operation. Hence it can be rightly
said that hashing is one of the best ways to ensure safety during the procedure of transfer of
messages when the particular message is meant for a specific receiver only. There is a
formula which is used for generation of the hash, which in turn lends a solution towards
protecting the safety of the communication from unofficial admittance (Rouse 2015).
After understanding the above three terms, it is very clear that symmetric key encryption is
used for maintaining authentication and confidentiality of databases. As the said method
helps to maintain confidentiality by ensuring that the data is not leaked in between
transmission stage. Further even if the same is leaked, the leaker or the hacker will not be
able to interpret the meaning due to encryption technology. With regards authentication also
symmetric key encryption is best as it simply means that access and authorisation is given
only to that person who has the password and the key for decrypting the database.
REFERENCES:
Beal,V. (2017). Public-key encryption. Retrieved from
http://www.webopedia.com/TERM/P/public_key_cryptography.html
Rouse,M. (2015).Hashing. Retrieved from
http://searchsqlserver.techtarget.com/definition/hashing
SSL Information. (2016). Symmetric vs. Asymmetric Encryption – What are differences?
Retrieved from https://www.ssl2buy.com/wiki/symmetric-vs-asymmetric-encryption-
what-are-differences
Hashing is a conversion of a twine of characters into a generally fixed-length value of a short
nature or key that signify the unique sequence. Hashing is used to key and recover objects
from a record since it is quicker to search the objects with the help of a shorter hashed key
than to search for the same with the help of the unique value. Hashing is also used in various
encryption algorithms. It is popularly known as the hash function. Apart from helping in
quicker retrieval of data, the said function also helps to encrypt and decrypt digital signatures
(Technopaedia.com. 2017). The hash function is used to index the unique key and then is
used later each time the information correlated with the value or key is to be regained.
Therefore it can be concluded that hashing is a one way operation. Hence it can be rightly
said that hashing is one of the best ways to ensure safety during the procedure of transfer of
messages when the particular message is meant for a specific receiver only. There is a
formula which is used for generation of the hash, which in turn lends a solution towards
protecting the safety of the communication from unofficial admittance (Rouse 2015).
After understanding the above three terms, it is very clear that symmetric key encryption is
used for maintaining authentication and confidentiality of databases. As the said method
helps to maintain confidentiality by ensuring that the data is not leaked in between
transmission stage. Further even if the same is leaked, the leaker or the hacker will not be
able to interpret the meaning due to encryption technology. With regards authentication also
symmetric key encryption is best as it simply means that access and authorisation is given
only to that person who has the password and the key for decrypting the database.
REFERENCES:
Beal,V. (2017). Public-key encryption. Retrieved from
http://www.webopedia.com/TERM/P/public_key_cryptography.html
Rouse,M. (2015).Hashing. Retrieved from
http://searchsqlserver.techtarget.com/definition/hashing
SSL Information. (2016). Symmetric vs. Asymmetric Encryption – What are differences?
Retrieved from https://www.ssl2buy.com/wiki/symmetric-vs-asymmetric-encryption-
what-are-differences

Technopaedia.com. (2017). Hashing. Retrieved from
https://www.techopedia.com/definition/14316/hashing
TOPIC 5
Computers and laptops have become a very crucial part of everybody’s life, be it any
organization or for personal use. However with regards the organisations, the entire system of
working with computers and laptops is not as simple as it seems. It is of a complex nature
simple because the system of any organization does not work independently, rather it works
in conjunction with the entire organization. Being a part of the security administrator, it is
very crucial as well as essential to draft a proper way out for securing the assets of the
organization. One of the most important part of the job is to have access control. There are
various rules which one has to comply with while working in secure areas. They are enlisted
below:
1. Access control being one of the primary rules wherein the accessibility is not made
available to all and the authorisation for the usage of the system or entering the secure
area is given to only a few who are trusted and have the adequate authority.
2. Second most important rule pens down to the fact that the important and critical
documents and data should be secured with the help of strong passwords which would
make unauthorised access difficult or impossible in certain cases.
3. Being a security administrator, simply writing down the security rules would not
suffice or conform to the security of the data of an entity. Adequate training has to be
provided on a frequent basis (National Centre for Education Statistics. 2017).
4. Backups should be taken for all the crucial information as a loss of any would not lead
to incurrence of much cost to the company.
5. The security administrator should ensure that the firewalls are adequately installed
and they are updated on a timely basis.
https://www.techopedia.com/definition/14316/hashing
TOPIC 5
Computers and laptops have become a very crucial part of everybody’s life, be it any
organization or for personal use. However with regards the organisations, the entire system of
working with computers and laptops is not as simple as it seems. It is of a complex nature
simple because the system of any organization does not work independently, rather it works
in conjunction with the entire organization. Being a part of the security administrator, it is
very crucial as well as essential to draft a proper way out for securing the assets of the
organization. One of the most important part of the job is to have access control. There are
various rules which one has to comply with while working in secure areas. They are enlisted
below:
1. Access control being one of the primary rules wherein the accessibility is not made
available to all and the authorisation for the usage of the system or entering the secure
area is given to only a few who are trusted and have the adequate authority.
2. Second most important rule pens down to the fact that the important and critical
documents and data should be secured with the help of strong passwords which would
make unauthorised access difficult or impossible in certain cases.
3. Being a security administrator, simply writing down the security rules would not
suffice or conform to the security of the data of an entity. Adequate training has to be
provided on a frequent basis (National Centre for Education Statistics. 2017).
4. Backups should be taken for all the crucial information as a loss of any would not lead
to incurrence of much cost to the company.
5. The security administrator should ensure that the firewalls are adequately installed
and they are updated on a timely basis.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6. Failure to compliance of any security policy should lead to strict punishment and the
same should be communicated to the staff around so that an individual would think
twice before acting in an unwanted manner.
7. Printers is another area from where data can easily be stolen, today’s generation
printers have the ability to store the documents being printed, thereby it should be
placed at a secure place and under lock and key.
8. Another very important rule is accessibility or accessing someone else’s system
without his or her knowledge, then a system should be installed which would give a
message to the actual owner of the system about usage of the same.
9. All the unused systems if connected to the LAN of the organization should be
immediately disconnected as it is easy for the hackers to get hold of such systems
which have not been used for a long time.
10. Last but not the least, if working in a secure area then the person should not open
spam mails and check the system and sender details before accessing any such
unknown data as they may contain viruses (Shinder, 2007).
There are times when certain information which are no more needed are deleted but they still
can be retrieved as after deletion they go and stay in the recycle bin from where the same can
easily be restored. Thereby protection of the same is a necessity. One of the most sought after
way is password protection which would help safeguarding of the theft of data being deleted
but still a part of the recycle bin.
To reduce the theft of desktop PC and unauthorised use, one has to first and foremost ensure
to maintain a log of the inventory of the system due to the size of the companies. Further to
this the unattended systems should be kept under lock and key and each room of the
organization should be installed with a security alarm which would work in case of an
unidentified intruder (The Barking Seal. 2008). Further unauthorised use of the system can be
halted by protecting each PC and desktop with a unique log in and password thereby allowing
only those who have the authorised access. However security is possible against the
unauthorised access only if the data is protected and the passcode are strong enough to be
easily guessed.
same should be communicated to the staff around so that an individual would think
twice before acting in an unwanted manner.
7. Printers is another area from where data can easily be stolen, today’s generation
printers have the ability to store the documents being printed, thereby it should be
placed at a secure place and under lock and key.
8. Another very important rule is accessibility or accessing someone else’s system
without his or her knowledge, then a system should be installed which would give a
message to the actual owner of the system about usage of the same.
9. All the unused systems if connected to the LAN of the organization should be
immediately disconnected as it is easy for the hackers to get hold of such systems
which have not been used for a long time.
10. Last but not the least, if working in a secure area then the person should not open
spam mails and check the system and sender details before accessing any such
unknown data as they may contain viruses (Shinder, 2007).
There are times when certain information which are no more needed are deleted but they still
can be retrieved as after deletion they go and stay in the recycle bin from where the same can
easily be restored. Thereby protection of the same is a necessity. One of the most sought after
way is password protection which would help safeguarding of the theft of data being deleted
but still a part of the recycle bin.
To reduce the theft of desktop PC and unauthorised use, one has to first and foremost ensure
to maintain a log of the inventory of the system due to the size of the companies. Further to
this the unattended systems should be kept under lock and key and each room of the
organization should be installed with a security alarm which would work in case of an
unidentified intruder (The Barking Seal. 2008). Further unauthorised use of the system can be
halted by protecting each PC and desktop with a unique log in and password thereby allowing
only those who have the authorised access. However security is possible against the
unauthorised access only if the data is protected and the passcode are strong enough to be
easily guessed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES:
National Centre for Education Statistics. (2017). Security Policy: Development and
Implementation. Retrieved from https://nces.ed.gov/pubs98/safetech/chapter3.asp
Shinder,D. (2007). 10 physical security measures every organization should take. Retrieved
from http://www.techrepublic.com/blog/10-things/10-physical-security-measures-
every-organization-should-take/
The Barking Seal. (2008). Every Company needs to have a security program. Retrieved from
https://www.appliedtrust.com/resources/security/every-company-needs-to-have-a-
security-program
TOPIC 6
DEEP PACKET INSPECTION
Deep packet inspection (DPI), also known as a complete packet inspection, is a type of
computer network packet used for sorting which is used to examine and scrutinize
information packs transferred from one system to the other over a network. The method
adopted by DPI is pretty complicated which functions at the seventh layer of the Open
System Interconnection reference model. It importance of the DPI providing vendors have
increased over the past few years. The same has increased because of the increasing threats
being posed by internet which has led to augment in the desire to stop the misutilization of
the system by the end user (Ohlhorst 2014). DPI not only caters to the header or footer of a
packet but also evaluates the main content of the packet and thereby looks for any such
information which is illegitimate and predefined principle. Through this method, it ensures
that a firewall is permitted to make a more particular decision on whether to allow or disallow
the packet basis the substance contained. DPI engines can also occupy autograph
identification, surreptitiousness consignment recognition and plentiful other safety measures
(endace. 2017).
The deep packet inspection is processing intensive since it takes care all the fields within a
packet such as the main content, header and footer. Due to the same, the said DPI calls for
extra time and processing power as well due to which they dare to do at 10Gbps.
National Centre for Education Statistics. (2017). Security Policy: Development and
Implementation. Retrieved from https://nces.ed.gov/pubs98/safetech/chapter3.asp
Shinder,D. (2007). 10 physical security measures every organization should take. Retrieved
from http://www.techrepublic.com/blog/10-things/10-physical-security-measures-
every-organization-should-take/
The Barking Seal. (2008). Every Company needs to have a security program. Retrieved from
https://www.appliedtrust.com/resources/security/every-company-needs-to-have-a-
security-program
TOPIC 6
DEEP PACKET INSPECTION
Deep packet inspection (DPI), also known as a complete packet inspection, is a type of
computer network packet used for sorting which is used to examine and scrutinize
information packs transferred from one system to the other over a network. The method
adopted by DPI is pretty complicated which functions at the seventh layer of the Open
System Interconnection reference model. It importance of the DPI providing vendors have
increased over the past few years. The same has increased because of the increasing threats
being posed by internet which has led to augment in the desire to stop the misutilization of
the system by the end user (Ohlhorst 2014). DPI not only caters to the header or footer of a
packet but also evaluates the main content of the packet and thereby looks for any such
information which is illegitimate and predefined principle. Through this method, it ensures
that a firewall is permitted to make a more particular decision on whether to allow or disallow
the packet basis the substance contained. DPI engines can also occupy autograph
identification, surreptitiousness consignment recognition and plentiful other safety measures
(endace. 2017).
The deep packet inspection is processing intensive since it takes care all the fields within a
packet such as the main content, header and footer. Due to the same, the said DPI calls for
extra time and processing power as well due to which they dare to do at 10Gbps.

PACKET STREAM ANALYSIS
While functioning on system arrest, there can be manifold cases of network actions going on.
Its importance can be understood with the help of the particular example wherein manifold
websites are being browsed through one browser and it becomes mind-numbing to keep a
trail of the data packets which belong to a specific stream. It is at this point of time when the
packet streams play a vital role. Thereby while viewing various websites, each site preserves
its own flow of data packets and by the application of sufficient filter specific packets can be
located as and when needed (Singh, 2013). Thus it can be said that even though flow based
analysis solutions is most apt, yet there are certain patches where packet capture and analysis
is a must even then. Thus when analysing any application, it is crucial to utilise the packet
arrest resolutions since they allow one to use the actual packets occupied in user dialogues
and recognize the source reason of a problem (netfort.com. 2014).
Further to this one can also conclude that a packet stream analyser is crucial since a single
packet does not have enough potential to determine some type of attacks such as it takes
numerous packets to find out if a network is being methodically looked and checked into or if
a TCP half-open DOS attack is happening.
Packet stream analysis needs the Intrusion Detection System to rebuild or uphold and contrast
the packets so as to conclude if an assault is taking place. The augmented packet whole and
reconstruction positions a huge dispensation pressure on IDS.
REFERENCES:
Endace. (2017). Deep Packet Inspection. Retrieved from https://www.endace.com/deep-
packet-inspection.html
Netfort.com. (2014). Flow Analysis Versus Packet Analysis . What Should You Choose?
Retrieved from
https://www.netfort.com/wp-content/uploads/PDF/WhitePapers/NetFlow-Vs-Packet-
Analysis-What-Should-You-Choose.pdf
Ohlhorst,F. (2014). Why Deep Packet Inspection still matters .Retrieved from
http://www.techrepublic.com/article/why-deep-packet-inspection-still-matters/
Singh,A. (2013). Wireshark: Working with Packet streams. Retrieved from
https://www.packtpub.com/books/content/wireshark-working-packet-streams
While functioning on system arrest, there can be manifold cases of network actions going on.
Its importance can be understood with the help of the particular example wherein manifold
websites are being browsed through one browser and it becomes mind-numbing to keep a
trail of the data packets which belong to a specific stream. It is at this point of time when the
packet streams play a vital role. Thereby while viewing various websites, each site preserves
its own flow of data packets and by the application of sufficient filter specific packets can be
located as and when needed (Singh, 2013). Thus it can be said that even though flow based
analysis solutions is most apt, yet there are certain patches where packet capture and analysis
is a must even then. Thus when analysing any application, it is crucial to utilise the packet
arrest resolutions since they allow one to use the actual packets occupied in user dialogues
and recognize the source reason of a problem (netfort.com. 2014).
Further to this one can also conclude that a packet stream analyser is crucial since a single
packet does not have enough potential to determine some type of attacks such as it takes
numerous packets to find out if a network is being methodically looked and checked into or if
a TCP half-open DOS attack is happening.
Packet stream analysis needs the Intrusion Detection System to rebuild or uphold and contrast
the packets so as to conclude if an assault is taking place. The augmented packet whole and
reconstruction positions a huge dispensation pressure on IDS.
REFERENCES:
Endace. (2017). Deep Packet Inspection. Retrieved from https://www.endace.com/deep-
packet-inspection.html
Netfort.com. (2014). Flow Analysis Versus Packet Analysis . What Should You Choose?
Retrieved from
https://www.netfort.com/wp-content/uploads/PDF/WhitePapers/NetFlow-Vs-Packet-
Analysis-What-Should-You-Choose.pdf
Ohlhorst,F. (2014). Why Deep Packet Inspection still matters .Retrieved from
http://www.techrepublic.com/article/why-deep-packet-inspection-still-matters/
Singh,A. (2013). Wireshark: Working with Packet streams. Retrieved from
https://www.packtpub.com/books/content/wireshark-working-packet-streams
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




