Analyzing Efficient Encryption Techniques for Network Security
VerifiedAdded on 2019/09/21
|8
|3512
|331
Report
AI Summary
This report provides a comprehensive overview of efficient encryption techniques essential for network security. It begins by defining network security and its importance in protecting data transmitted over wireless channels, emphasizing the need for authentication, authorization, and the role of administrators. The report then delves into the core concepts of cryptography, explaining the processes of encryption and decryption and the different types of attacks, including active and passive attacks. It highlights key security services such as data integrity, confidentiality, authentication, non-repudiation, and access control. The report further explores cryptography principles like replication, cleanness, and timely arrival, and differentiates between symmetric and asymmetric cryptosystems. It discusses various cryptographic algorithms, including DES, AES, RSA, MD5, and SHA, while also examining the advantages and disadvantages of cryptography. Additionally, the report touches upon network security types, such as wireless sensor networks (WSN), secured sessions, and IP security, and briefly introduces steganography as a method for hiding messages. Overall, the report serves as a valuable resource for understanding and implementing efficient encryption techniques to secure network communications.

EFFICIENT ENCRYPTION TECHNIQUES FOR NETWORK SECURITY
Abstract
Providing security is an essential part of
every application and providing security on
the network is to protect data transmission
on the wireless channel. Data transmission
on the untrustworthy network needs a secure
process that ensures secure transmission on
a network channel. This contains the process
of authentication and authorization that
provides a secure data access and all this
works where carried by an administrator.
Authentication has an ID and password that
allows them to access information according
to their authenticity. Authorization helps to
validate the user authenticity and provide
access to their authority. Every job have to
be protected and providing security on
network channels covers most of the works
on computer networks. Very transaction and
communication on network channel have to
be secure in a private and public sense.
Applications like industry, corporate
organizations, government’s agencies, and
personal data transmissions need security to
protect their sensitive data’s. Networks can
be private and public according to the
applications, some industry;the organization
has a private network channel that provides
authority to access by their peoples. Public
networks like social websites, social
networks have an access to personal
individuals can access, so by providing
security to individual data is more required.
Cryptographic techniques are used to protect
the data’s that are both private and public.
Keywords: Cryptography, encryption,
security, network security, computer
networks, wireless network channels.
1. Introduction
Network security is essential in information
security as it has the responsibilities to
secure all data’s that are in network
channel.A security involves a layer of
protection like monitoring network
channels, Anti-virus software, Security
software, and firewalls. Monitoring and
security software’s works together to
providing security on network channels [1].
Network security consists of the
requirements and procedures that a network
administrator should adopt to protect the
user data from unauthorized access from
misusing, alteration, eliminating the
unauthorized access to network resources.
Everyday job that in today’s world on
network conducting data transaction and
transmission on business organization,
government and individual people data [1].
The process of converting plain text into a
ciphertext is called cryptography. Some
protocols using cryptography is used to
block rivals.Cryptography contains a
complex mathematics with computer science
that helps to provide data security. Data
security relays data integrity, confidentiality,
authentication and authorization.
Cryptography and cryptanalysis is a
combination of cryptology. Converting plain
text into cypher text is called cryptography
where else decrypting the cypher back to
plain text is called cryptanalysis. Encryption
is a process that converts a normal text into
a non-understandable text called cipher test.
Decryption is the process that converts the
ciphertext back to the original plaintext [1].
This report has a survey and reviews on
security service on network channels with
cryptographic methods.
Abstract
Providing security is an essential part of
every application and providing security on
the network is to protect data transmission
on the wireless channel. Data transmission
on the untrustworthy network needs a secure
process that ensures secure transmission on
a network channel. This contains the process
of authentication and authorization that
provides a secure data access and all this
works where carried by an administrator.
Authentication has an ID and password that
allows them to access information according
to their authenticity. Authorization helps to
validate the user authenticity and provide
access to their authority. Every job have to
be protected and providing security on
network channels covers most of the works
on computer networks. Very transaction and
communication on network channel have to
be secure in a private and public sense.
Applications like industry, corporate
organizations, government’s agencies, and
personal data transmissions need security to
protect their sensitive data’s. Networks can
be private and public according to the
applications, some industry;the organization
has a private network channel that provides
authority to access by their peoples. Public
networks like social websites, social
networks have an access to personal
individuals can access, so by providing
security to individual data is more required.
Cryptographic techniques are used to protect
the data’s that are both private and public.
Keywords: Cryptography, encryption,
security, network security, computer
networks, wireless network channels.
1. Introduction
Network security is essential in information
security as it has the responsibilities to
secure all data’s that are in network
channel.A security involves a layer of
protection like monitoring network
channels, Anti-virus software, Security
software, and firewalls. Monitoring and
security software’s works together to
providing security on network channels [1].
Network security consists of the
requirements and procedures that a network
administrator should adopt to protect the
user data from unauthorized access from
misusing, alteration, eliminating the
unauthorized access to network resources.
Everyday job that in today’s world on
network conducting data transaction and
transmission on business organization,
government and individual people data [1].
The process of converting plain text into a
ciphertext is called cryptography. Some
protocols using cryptography is used to
block rivals.Cryptography contains a
complex mathematics with computer science
that helps to provide data security. Data
security relays data integrity, confidentiality,
authentication and authorization.
Cryptography and cryptanalysis is a
combination of cryptology. Converting plain
text into cypher text is called cryptography
where else decrypting the cypher back to
plain text is called cryptanalysis. Encryption
is a process that converts a normal text into
a non-understandable text called cipher test.
Decryption is the process that converts the
ciphertext back to the original plaintext [1].
This report has a survey and reviews on
security service on network channels with
cryptographic methods.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2. Possible types of Attacks
Passive and active attacks are the types of
attacks present in the network channels [2]
[7].
2.1 Active Attacks
These types of attacks are harmful, as it will
change the information in the data flow that
could affect the resource.
Alteration of massage: A delay while
receiving message show that the messages
are altered. Fully or some portion of
message are changed.
Denial of service: Destroy message that is at
receiving end.
Replay content: It is that the attacker reads a
data and retransfer the data to a receiver or it
can retransmit to an unauthorized user.
Masquerade: They pretends to be not
involved or involved to some other entity.
2.2 Passive Attacks
These type of attacks does not have any
harmful to the system resource, as it will just
to learn the message. This will not affect the
system resource. The main aim of the
attacker is to obtain the data that are being
transmitted.
Traffic analysis: A traffic message is sent so
that both sender and receiver do not have a
knowledge that their message is read by
someone.
Reveal the message: the attacker reads
sender message or third party member
before it reaches to the target person.
3. Security service
Open system communication has a layer of
protocol that ensures a system security
during data transfer. Improves security
during data processing and data transmission
[9].
3.1 Data Integrity
This refers to the data accuracy and ensure
that that data in network channel does not
modify attackers. If both the sender and
receiver receives the same message then it
ensures the data integrity.
3.2 Data Confidentiality
Allowing only an authorized person to
access the data, this means protecting
privacy to the user personal data. A lack of
data confidentiality will reveal user
information.
3.3 Authentication
Providing authenticity to all channels nodes
on the network to ensure the security by
allowing authorized persons to access.
3.4 Non-repudiation
Both sender and receiver should
acknowledge, the sender should receive an
acknowledgment that the message is sent to
the receiver and when a receiver receives a
message then sender should know that the
receiver received a message.
3.5 Access control
This is to control the access to the system
and application with links. To achieve
access control each entry has to gain access
so that they can access the information so
that unauthorized access can be avoided.
4. Cryptography principles for
security
4.1 Replication
Ciphertext contains a redundancy of data so
that attackers do not understand what the
message is. It is necessary to have a
redundancy in the message so that it will
become difficult to find out the encrypted
message [4].
Passive and active attacks are the types of
attacks present in the network channels [2]
[7].
2.1 Active Attacks
These types of attacks are harmful, as it will
change the information in the data flow that
could affect the resource.
Alteration of massage: A delay while
receiving message show that the messages
are altered. Fully or some portion of
message are changed.
Denial of service: Destroy message that is at
receiving end.
Replay content: It is that the attacker reads a
data and retransfer the data to a receiver or it
can retransmit to an unauthorized user.
Masquerade: They pretends to be not
involved or involved to some other entity.
2.2 Passive Attacks
These type of attacks does not have any
harmful to the system resource, as it will just
to learn the message. This will not affect the
system resource. The main aim of the
attacker is to obtain the data that are being
transmitted.
Traffic analysis: A traffic message is sent so
that both sender and receiver do not have a
knowledge that their message is read by
someone.
Reveal the message: the attacker reads
sender message or third party member
before it reaches to the target person.
3. Security service
Open system communication has a layer of
protocol that ensures a system security
during data transfer. Improves security
during data processing and data transmission
[9].
3.1 Data Integrity
This refers to the data accuracy and ensure
that that data in network channel does not
modify attackers. If both the sender and
receiver receives the same message then it
ensures the data integrity.
3.2 Data Confidentiality
Allowing only an authorized person to
access the data, this means protecting
privacy to the user personal data. A lack of
data confidentiality will reveal user
information.
3.3 Authentication
Providing authenticity to all channels nodes
on the network to ensure the security by
allowing authorized persons to access.
3.4 Non-repudiation
Both sender and receiver should
acknowledge, the sender should receive an
acknowledgment that the message is sent to
the receiver and when a receiver receives a
message then sender should know that the
receiver received a message.
3.5 Access control
This is to control the access to the system
and application with links. To achieve
access control each entry has to gain access
so that they can access the information so
that unauthorized access can be avoided.
4. Cryptography principles for
security
4.1 Replication
Ciphertext contains a redundancy of data so
that attackers do not understand what the
message is. It is necessary to have a
redundancy in the message so that it will
become difficult to find out the encrypted
message [4].
4.2 Cleanness and timely-arrival
Every message should have a timestamp so
that whenever receiver receives the last
message then by timestamp says that the
received message can be stolen or changed
by someone [9].
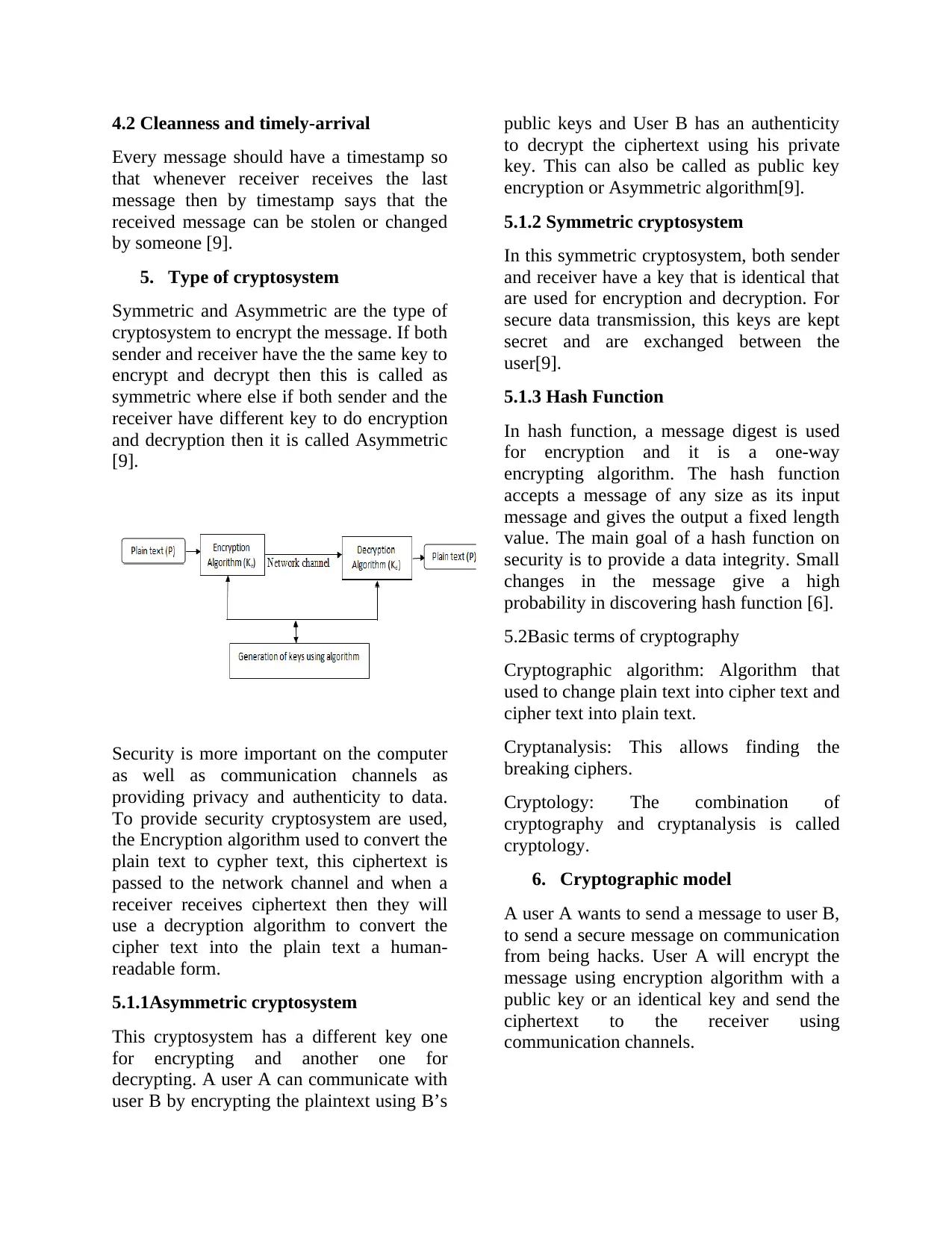
5. Type of cryptosystem
Symmetric and Asymmetric are the type of
cryptosystem to encrypt the message. If both
sender and receiver have the the same key to
encrypt and decrypt then this is called as
symmetric where else if both sender and the
receiver have different key to do encryption
and decryption then it is called Asymmetric
[9].
Security is more important on the computer
as well as communication channels as
providing privacy and authenticity to data.
To provide security cryptosystem are used,
the Encryption algorithm used to convert the
plain text to cypher text, this ciphertext is
passed to the network channel and when a
receiver receives ciphertext then they will
use a decryption algorithm to convert the
cipher text into the plain text a human-
readable form.
5.1.1Asymmetric cryptosystem
This cryptosystem has a different key one
for encrypting and another one for
decrypting. A user A can communicate with
user B by encrypting the plaintext using B’s
public keys and User B has an authenticity
to decrypt the ciphertext using his private
key. This can also be called as public key
encryption or Asymmetric algorithm[9].
5.1.2 Symmetric cryptosystem
In this symmetric cryptosystem, both sender
and receiver have a key that is identical that
are used for encryption and decryption. For
secure data transmission, this keys are kept
secret and are exchanged between the
user[9].
5.1.3 Hash Function
In hash function, a message digest is used
for encryption and it is a one-way
encrypting algorithm. The hash function
accepts a message of any size as its input
message and gives the output a fixed length
value. The main goal of a hash function on
security is to provide a data integrity. Small
changes in the message give a high
probability in discovering hash function [6].
5.2Basic terms of cryptography
Cryptographic algorithm: Algorithm that
used to change plain text into cipher text and
cipher text into plain text.
Cryptanalysis: This allows finding the
breaking ciphers.
Cryptology: The combination of
cryptography and cryptanalysis is called
cryptology.
6. Cryptographic model
A user A wants to send a message to user B,
to send a secure message on communication
from being hacks. User A will encrypt the
message using encryption algorithm with a
public key or an identical key and send the
ciphertext to the receiver using
communication channels.
Every message should have a timestamp so
that whenever receiver receives the last
message then by timestamp says that the
received message can be stolen or changed
by someone [9].
5. Type of cryptosystem
Symmetric and Asymmetric are the type of
cryptosystem to encrypt the message. If both
sender and receiver have the the same key to
encrypt and decrypt then this is called as
symmetric where else if both sender and the
receiver have different key to do encryption
and decryption then it is called Asymmetric
[9].
Security is more important on the computer
as well as communication channels as
providing privacy and authenticity to data.
To provide security cryptosystem are used,
the Encryption algorithm used to convert the
plain text to cypher text, this ciphertext is
passed to the network channel and when a
receiver receives ciphertext then they will
use a decryption algorithm to convert the
cipher text into the plain text a human-
readable form.
5.1.1Asymmetric cryptosystem
This cryptosystem has a different key one
for encrypting and another one for
decrypting. A user A can communicate with
user B by encrypting the plaintext using B’s
public keys and User B has an authenticity
to decrypt the ciphertext using his private
key. This can also be called as public key
encryption or Asymmetric algorithm[9].
5.1.2 Symmetric cryptosystem
In this symmetric cryptosystem, both sender
and receiver have a key that is identical that
are used for encryption and decryption. For
secure data transmission, this keys are kept
secret and are exchanged between the
user[9].
5.1.3 Hash Function
In hash function, a message digest is used
for encryption and it is a one-way
encrypting algorithm. The hash function
accepts a message of any size as its input
message and gives the output a fixed length
value. The main goal of a hash function on
security is to provide a data integrity. Small
changes in the message give a high
probability in discovering hash function [6].
5.2Basic terms of cryptography
Cryptographic algorithm: Algorithm that
used to change plain text into cipher text and
cipher text into plain text.
Cryptanalysis: This allows finding the
breaking ciphers.
Cryptology: The combination of
cryptography and cryptanalysis is called
cryptology.
6. Cryptographic model
A user A wants to send a message to user B,
to send a secure message on communication
from being hacks. User A will encrypt the
message using encryption algorithm with a
public key or an identical key and send the
ciphertext to the receiver using
communication channels.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
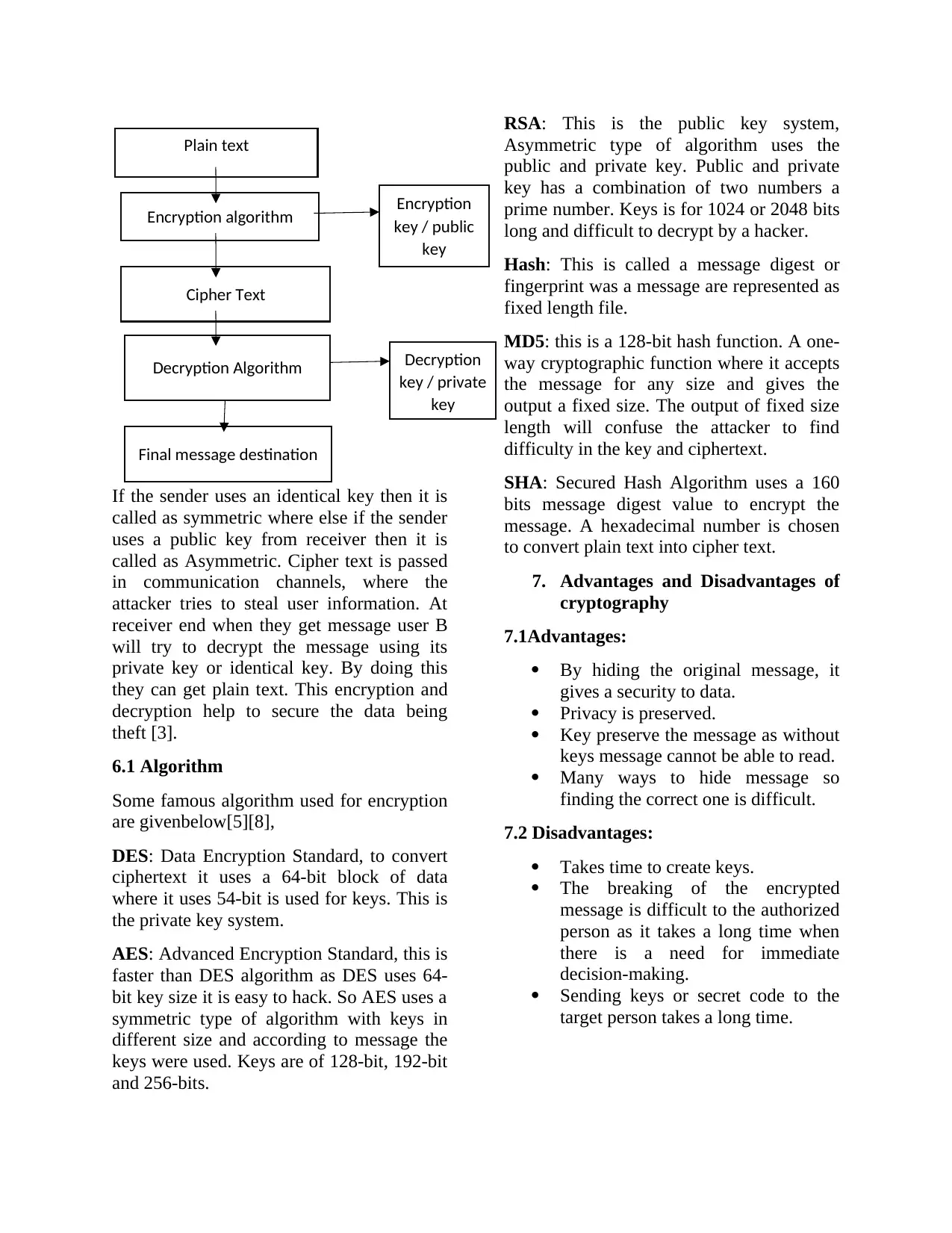
If the sender uses an identical key then it is
called as symmetric where else if the sender
uses a public key from receiver then it is
called as Asymmetric. Cipher text is passed
in communication channels, where the
attacker tries to steal user information. At
receiver end when they get message user B
will try to decrypt the message using its
private key or identical key. By doing this
they can get plain text. This encryption and
decryption help to secure the data being
theft [3].
6.1 Algorithm
Some famous algorithm used for encryption
are givenbelow[5][8],
DES: Data Encryption Standard, to convert
ciphertext it uses a 64-bit block of data
where it uses 54-bit is used for keys. This is
the private key system.
AES: Advanced Encryption Standard, this is
faster than DES algorithm as DES uses 64-
bit key size it is easy to hack. So AES uses a
symmetric type of algorithm with keys in
different size and according to message the
keys were used. Keys are of 128-bit, 192-bit
and 256-bits.
RSA: This is the public key system,
Asymmetric type of algorithm uses the
public and private key. Public and private
key has a combination of two numbers a
prime number. Keys is for 1024 or 2048 bits
long and difficult to decrypt by a hacker.
Hash: This is called a message digest or
fingerprint was a message are represented as
fixed length file.
MD5: this is a 128-bit hash function. A one-
way cryptographic function where it accepts
the message for any size and gives the
output a fixed size. The output of fixed size
length will confuse the attacker to find
difficulty in the key and ciphertext.
SHA: Secured Hash Algorithm uses a 160
bits message digest value to encrypt the
message. A hexadecimal number is chosen
to convert plain text into cipher text.
7. Advantages and Disadvantages of
cryptography
7.1Advantages:
By hiding the original message, it
gives a security to data.
Privacy is preserved.
Key preserve the message as without
keys message cannot be able to read.
Many ways to hide message so
finding the correct one is difficult.
7.2 Disadvantages:
Takes time to create keys.
The breaking of the encrypted
message is difficult to the authorized
person as it takes a long time when
there is a need for immediate
decision-making.
Sending keys or secret code to the
target person takes a long time.
Plain text
Encryption algorithm Encryption
key / public
key
Cipher Text
Decryption Algorithm Decryption
key / private
key
Final message destination
called as symmetric where else if the sender
uses a public key from receiver then it is
called as Asymmetric. Cipher text is passed
in communication channels, where the
attacker tries to steal user information. At
receiver end when they get message user B
will try to decrypt the message using its
private key or identical key. By doing this
they can get plain text. This encryption and
decryption help to secure the data being
theft [3].
6.1 Algorithm
Some famous algorithm used for encryption
are givenbelow[5][8],
DES: Data Encryption Standard, to convert
ciphertext it uses a 64-bit block of data
where it uses 54-bit is used for keys. This is
the private key system.
AES: Advanced Encryption Standard, this is
faster than DES algorithm as DES uses 64-
bit key size it is easy to hack. So AES uses a
symmetric type of algorithm with keys in
different size and according to message the
keys were used. Keys are of 128-bit, 192-bit
and 256-bits.
RSA: This is the public key system,
Asymmetric type of algorithm uses the
public and private key. Public and private
key has a combination of two numbers a
prime number. Keys is for 1024 or 2048 bits
long and difficult to decrypt by a hacker.
Hash: This is called a message digest or
fingerprint was a message are represented as
fixed length file.
MD5: this is a 128-bit hash function. A one-
way cryptographic function where it accepts
the message for any size and gives the
output a fixed size. The output of fixed size
length will confuse the attacker to find
difficulty in the key and ciphertext.
SHA: Secured Hash Algorithm uses a 160
bits message digest value to encrypt the
message. A hexadecimal number is chosen
to convert plain text into cipher text.
7. Advantages and Disadvantages of
cryptography
7.1Advantages:
By hiding the original message, it
gives a security to data.
Privacy is preserved.
Key preserve the message as without
keys message cannot be able to read.
Many ways to hide message so
finding the correct one is difficult.
7.2 Disadvantages:
Takes time to create keys.
The breaking of the encrypted
message is difficult to the authorized
person as it takes a long time when
there is a need for immediate
decision-making.
Sending keys or secret code to the
target person takes a long time.
Plain text
Encryption algorithm Encryption
key / public
key
Cipher Text
Decryption Algorithm Decryption
key / private
key
Final message destination
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8. Network security types
8.1WSN: Wireless sensor network, this is to
provide security for unauthorized access to
the wireless channel. Both wired and
wireless should be secured and wired
equivalent privacy and wireless ( Wi-Fi)
protected access are the types in network
channels. Wired privacy can be cracked by
easily getting the user password, password is
weaker to reveal by some combinations of
users favourite information like name,
relatives name, children name, DOB,
Favorite foods etc. Wireless channels need
security layer on the application layer to
avoid attackers [2].
8.2 Secured session and connection: A
secure connection is a one that is ensuring
that the data are secure in the open
communication channel. Providing security
on ISO layer for every session is maintained.
8.3 IP security: Internet protocol security is
used to secure IP during communication on
network channels by allowing to access after
verifying authenticity and encrypting IP for
every session.
9. Steganography
This helps to hide the message that is
difficult to detect. Only a sender and a
receiver know how to decrypt the message.
This is to hide the secret message so that
hacker could not detect what the secret key
or information is. All types of data’s like
text, image, audio and video message can be
steganography.
It has three modules,
Cover object: It is also called as carrier
image that helps to hide the message.
Message: Data, images, audio and video are
the messages used to keep secret.
Steganography
Key: This to decode the hidden message.
9.1 Types of steganography
Types of steganography are defined on what
the message type is taken to encode [13]
[14].
Text steganography
Image steganography
Audio steganography
Video steganography
Text Steganography
The text is used to hide text message i.e.
hide text with another text folder. Some
techniques used to hide text message is
format based, linguistically based and
statistical based method.
Image Steganography
This uses the image to cover another image
object. It is of a two-step process where first
it creates stego image to cover images and
extract the image.
Audio steganography
To hide the message here a sound is
embedded to cover the image. Secret
message is of format .wav, au, .mp3 files.
Low-bit encoding and phase encoding is
types to use in audio steganography.
Video Steganography:
It uses a mixing of sound and images,
combination of sound and images are sent to
make the video message secret in the
communication medium. Spectrum, discrete
cosine transform, video compressed,
filtering are some types of video
steganography methods to hide video
message.
10. Intrusion detection system
IDS (Intrusion Detection1s System) is a
software that helps to detect the intrusion on
network channels likes malicious attacks,
8.1WSN: Wireless sensor network, this is to
provide security for unauthorized access to
the wireless channel. Both wired and
wireless should be secured and wired
equivalent privacy and wireless ( Wi-Fi)
protected access are the types in network
channels. Wired privacy can be cracked by
easily getting the user password, password is
weaker to reveal by some combinations of
users favourite information like name,
relatives name, children name, DOB,
Favorite foods etc. Wireless channels need
security layer on the application layer to
avoid attackers [2].
8.2 Secured session and connection: A
secure connection is a one that is ensuring
that the data are secure in the open
communication channel. Providing security
on ISO layer for every session is maintained.
8.3 IP security: Internet protocol security is
used to secure IP during communication on
network channels by allowing to access after
verifying authenticity and encrypting IP for
every session.
9. Steganography
This helps to hide the message that is
difficult to detect. Only a sender and a
receiver know how to decrypt the message.
This is to hide the secret message so that
hacker could not detect what the secret key
or information is. All types of data’s like
text, image, audio and video message can be
steganography.
It has three modules,
Cover object: It is also called as carrier
image that helps to hide the message.
Message: Data, images, audio and video are
the messages used to keep secret.
Steganography
Key: This to decode the hidden message.
9.1 Types of steganography
Types of steganography are defined on what
the message type is taken to encode [13]
[14].
Text steganography
Image steganography
Audio steganography
Video steganography
Text Steganography
The text is used to hide text message i.e.
hide text with another text folder. Some
techniques used to hide text message is
format based, linguistically based and
statistical based method.
Image Steganography
This uses the image to cover another image
object. It is of a two-step process where first
it creates stego image to cover images and
extract the image.
Audio steganography
To hide the message here a sound is
embedded to cover the image. Secret
message is of format .wav, au, .mp3 files.
Low-bit encoding and phase encoding is
types to use in audio steganography.
Video Steganography:
It uses a mixing of sound and images,
combination of sound and images are sent to
make the video message secret in the
communication medium. Spectrum, discrete
cosine transform, video compressed,
filtering are some types of video
steganography methods to hide video
message.
10. Intrusion detection system
IDS (Intrusion Detection1s System) is a
software that helps to detect the intrusion on
network channels likes malicious attacks,

security policy violations, and unauthorized
access. If intrusions are detected then the
system will report to the network
administrator and security teams [2].
There are two type of IDS (Intrusion
Detection System), they are
Host-based intrusion detection
system (IDS)
Network-based intrusion detection
system (IDS)
Host-based IDS:
Intrusion detection system is implemented
on a server or host-targeted machines to
detect intrusion. This can be checked by
comparing the malicious match in the
database.
When an Intrusion detection system is
installed then it will create a file storage and
frequently checks the incoming files and
stores as a signature. When a file system
received is changed or being a mismatch
with the safe signature then it will alert the
administrator that file is theft.
Network-based IDS:
This is easy to implement on network
channels and a sniffer kept within the
database to check the attack signature. Each
packet of the message is checked with
matches in the database.
When an intrusion occurs, it will alert the
administrator.
11. Firewalls
Firewalls on network channels help to
monitor the access to network traffic by
using predefined policy rules. This controls
the communication traffics from allowing
access to the incoming and outgoing
messages. This provides the trust between
the users. By using tunnel mode an
administrator can use a firewall with VPNs.
This can hide from public user to avoid
traffic from unauthorized access [10].
Packet filtering firewall
Application level gateways
Inspection firewall
o Single layer inspection
firewall
o Multiple layer inspection
firewall
Gateways
Packet filtering firewall: This is over on
network layer in ISO layer, firewall on this
will be checked on source or destination and
port address. Packet filtering is performed
on network devices also. Using firewalls on
devices like router will sort the incoming
access.
Application level gateways: A combination
of packet filtering with gateways, this will
stop the direct connection between the
system on firewalls and becomes a hard one
to crack the message from hackers.
Inspection firewalls: Stateful inspection will
keep track the activities on network channels
to regain the lost message from where it lost.
Multiple layer inspection firewalls: has both
packet filtering and circuit monitoring that
are transparent on the network. A regular
algorithm used to monitor the intrusion and
alert them whenever an intrusion occurs.
Gateways: It provides the handshake
between local and remote system to
determine and check the connection is
secure and trusted [11].
12. Conclusion
In the field of information security where
security is more important as all the
information’s and data’s are communicated
through network channels. Network security
comprises of providing secure network
channel from infrastructure, in order to
protect and ensure security a network
access. If intrusions are detected then the
system will report to the network
administrator and security teams [2].
There are two type of IDS (Intrusion
Detection System), they are
Host-based intrusion detection
system (IDS)
Network-based intrusion detection
system (IDS)
Host-based IDS:
Intrusion detection system is implemented
on a server or host-targeted machines to
detect intrusion. This can be checked by
comparing the malicious match in the
database.
When an Intrusion detection system is
installed then it will create a file storage and
frequently checks the incoming files and
stores as a signature. When a file system
received is changed or being a mismatch
with the safe signature then it will alert the
administrator that file is theft.
Network-based IDS:
This is easy to implement on network
channels and a sniffer kept within the
database to check the attack signature. Each
packet of the message is checked with
matches in the database.
When an intrusion occurs, it will alert the
administrator.
11. Firewalls
Firewalls on network channels help to
monitor the access to network traffic by
using predefined policy rules. This controls
the communication traffics from allowing
access to the incoming and outgoing
messages. This provides the trust between
the users. By using tunnel mode an
administrator can use a firewall with VPNs.
This can hide from public user to avoid
traffic from unauthorized access [10].
Packet filtering firewall
Application level gateways
Inspection firewall
o Single layer inspection
firewall
o Multiple layer inspection
firewall
Gateways
Packet filtering firewall: This is over on
network layer in ISO layer, firewall on this
will be checked on source or destination and
port address. Packet filtering is performed
on network devices also. Using firewalls on
devices like router will sort the incoming
access.
Application level gateways: A combination
of packet filtering with gateways, this will
stop the direct connection between the
system on firewalls and becomes a hard one
to crack the message from hackers.
Inspection firewalls: Stateful inspection will
keep track the activities on network channels
to regain the lost message from where it lost.
Multiple layer inspection firewalls: has both
packet filtering and circuit monitoring that
are transparent on the network. A regular
algorithm used to monitor the intrusion and
alert them whenever an intrusion occurs.
Gateways: It provides the handshake
between local and remote system to
determine and check the connection is
secure and trusted [11].
12. Conclusion
In the field of information security where
security is more important as all the
information’s and data’s are communicated
through network channels. Network security
comprises of providing secure network
channel from infrastructure, in order to
protect and ensure security a network
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

administrator has to adopt security policies
and authenticated access to stop
unauthorized user. Every communication on
network channels need a security and by
doing cryptographic algorithms and
functions an information from organizations,
governments or individuals can be secured.
From being theft from digital
communication cryptographic algorithms
are used with security protocols can improve
where the communication between users
from being attacked.
References
[1]SumedhaKaushik,AnkurSinghal,
”Network Security using cryptographic
Techniques”, International Journal of
advanced Research in computer science and
software engineering. Vol 2, Issue 12,
December 2012.
[2] Simmonds, A; Sandilands, P; van Ekert,
L,”Ontology for Network Security Attacks".
Lecture Notes in Computer Science. Lecture
Notes in Computer Science 3285, pp.317–
323, 2004.
[3] Sanchez-Avila, C. Sanchez-Reillol,
R,“TheRijndael block cipher (AES
proposal): A comparison with DES”, 35th
International Conference on Security
Technology 2001, IEEE.
[4] Murat Fiskiran, Ruby B. Lee, ”Workload
Characterization of Elliptic Curve
Cryptography and other Network Security
Algorithms for Constrained Environments”,
IEEE International Workshop on Workload
Characterization, 2002. WWC-5. 2002.
[5] Aameer Nadeem, Dr.
M.YounusJaved,”A performance
comparison of data Encryption Algorithm”,
Global Telecommunication Workshops,
2004 GlobeCom Workshops 2004, IEEE.
[6] Elkamchouchi, H.M;Emarah, A.-A.M;
Hagras, E.A.A, ”A New Secure Hash
Dynamic Structure Algorithm (SHDSA) for
Public Key Digital Signature Schemes”, the
23rd National Radio Science
Conference,2006.
[7] Like Zhang, Gregory B. White,
”Anomaly Detection for Application Level
Network Attacks Using Payload Keywords”,
Proceedings of the 2007 IEEE Symposium
on Computational Intelligence in Security
and Defense Applications,2007.
[8] SuhailaOrner Sharif, S.P.
Mansoor,”Performance analysis of Stream
and Block cipher algorithms”, 3rd
International Conference on Advanced
Computer Theory and Engineering
(ICACTE), 2010.
[9] PunitaMellu&SitenderMali,”AES:
Asymmetric key cryptographic System”,
International Journal of Information
Technology and Knowledge Management,
2011, Vol, No. 4 pp. 113-117.
[10] YudhvirSingh, YogeshChaba,
”Information Theory test based Performance
Evaluation of Cryptographic Techniques” ,
International Journal of Information
Technology and Knowledge Management,
Vol 1,No.2,2008 , pp. 475-483.
[11] YanWang, Ming Hu,”Timing
Evaluation of known cryptographic
Algorithm”, International Conference on
Computational Intelligence and security,
2009.
[12] Gandharba Swain, Saroj Kumar Lanka,
“A Quick review of Network Security and
Steganography” International Journal of
Electronics and Computer Science
and authenticated access to stop
unauthorized user. Every communication on
network channels need a security and by
doing cryptographic algorithms and
functions an information from organizations,
governments or individuals can be secured.
From being theft from digital
communication cryptographic algorithms
are used with security protocols can improve
where the communication between users
from being attacked.
References
[1]SumedhaKaushik,AnkurSinghal,
”Network Security using cryptographic
Techniques”, International Journal of
advanced Research in computer science and
software engineering. Vol 2, Issue 12,
December 2012.
[2] Simmonds, A; Sandilands, P; van Ekert,
L,”Ontology for Network Security Attacks".
Lecture Notes in Computer Science. Lecture
Notes in Computer Science 3285, pp.317–
323, 2004.
[3] Sanchez-Avila, C. Sanchez-Reillol,
R,“TheRijndael block cipher (AES
proposal): A comparison with DES”, 35th
International Conference on Security
Technology 2001, IEEE.
[4] Murat Fiskiran, Ruby B. Lee, ”Workload
Characterization of Elliptic Curve
Cryptography and other Network Security
Algorithms for Constrained Environments”,
IEEE International Workshop on Workload
Characterization, 2002. WWC-5. 2002.
[5] Aameer Nadeem, Dr.
M.YounusJaved,”A performance
comparison of data Encryption Algorithm”,
Global Telecommunication Workshops,
2004 GlobeCom Workshops 2004, IEEE.
[6] Elkamchouchi, H.M;Emarah, A.-A.M;
Hagras, E.A.A, ”A New Secure Hash
Dynamic Structure Algorithm (SHDSA) for
Public Key Digital Signature Schemes”, the
23rd National Radio Science
Conference,2006.
[7] Like Zhang, Gregory B. White,
”Anomaly Detection for Application Level
Network Attacks Using Payload Keywords”,
Proceedings of the 2007 IEEE Symposium
on Computational Intelligence in Security
and Defense Applications,2007.
[8] SuhailaOrner Sharif, S.P.
Mansoor,”Performance analysis of Stream
and Block cipher algorithms”, 3rd
International Conference on Advanced
Computer Theory and Engineering
(ICACTE), 2010.
[9] PunitaMellu&SitenderMali,”AES:
Asymmetric key cryptographic System”,
International Journal of Information
Technology and Knowledge Management,
2011, Vol, No. 4 pp. 113-117.
[10] YudhvirSingh, YogeshChaba,
”Information Theory test based Performance
Evaluation of Cryptographic Techniques” ,
International Journal of Information
Technology and Knowledge Management,
Vol 1,No.2,2008 , pp. 475-483.
[11] YanWang, Ming Hu,”Timing
Evaluation of known cryptographic
Algorithm”, International Conference on
Computational Intelligence and security,
2009.
[12] Gandharba Swain, Saroj Kumar Lanka,
“A Quick review of Network Security and
Steganography” International Journal of
Electronics and Computer Science
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Engineering, ISSN:2277-1956 Available
online at www.ijecse.org.
[13] Khan Muhammad, “Steganography: A
Secure way for Transmission in Wireless
Sensor Networks”,2015 Department of
computer science, Islamia College
Peshawar, Pakistan,.
[14] R. J. Mstafa and K. M. Elleithy, "A
highly secure video steganography using
Hamming code (7, 4)," in Systems,
Applications and Technology Conference
(LISAT), 2014 IEEE Long Island, 2014, pp.
1-6.
online at www.ijecse.org.
[13] Khan Muhammad, “Steganography: A
Secure way for Transmission in Wireless
Sensor Networks”,2015 Department of
computer science, Islamia College
Peshawar, Pakistan,.
[14] R. J. Mstafa and K. M. Elleithy, "A
highly secure video steganography using
Hamming code (7, 4)," in Systems,
Applications and Technology Conference
(LISAT), 2014 IEEE Long Island, 2014, pp.
1-6.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




