Enhanced Online Voting System Security using VPN - AES Report
VerifiedAdded on 2023/06/11
|12
|3976
|439
Report
AI Summary
This report proposes a new model for online voting systems that incorporates VPN and AES encryption to enhance security and address vulnerabilities in previous models. The proposed system uses a three-step identification process involving MEC smart cards, OTP generation, and VPN implementation to verify voters. The VPN encryption masks the voter's location and identity, while AES encryption secures the electronic data. The model details the process from login to vote casting, including fingerprint verification, candidate selection, encryption with unique keys, admin signing, and secure storage in a database. Strengths of the model include enhanced security, remote control, file sharing, online anonymity, bypassing filters, IP address changes, and cost reduction compared to previous systems. The report also discusses the implementation context, demonstrating how the model can be applied to make online voting processes more secure and reliable.
Title of Report Online election using VPN
Table of Contents
Abstract
1.Introduction
2.Literature Review
3. A proposed model Justifications for the newly/updated model, identifying which areas have been enhanced
The VPN and AES encryptions used for the online voting systems were not previously used or were not in vogue. This has always
caused disruption in the authenticity of the online voting system. Since, there are major chances that the voting system published online
can be easily rigged; online voting system with VPN should be used in the latest voting systems that are published online. The VPN or
Virtual Private Network is becoming much more widely used with every passing day since there has been a provision for the users in
the VPN networks to go anonymous while browsing. There are several reasons why a VPN encryption implementation should be ideal
for an online voting system.
One of the major reasons for VPN encryption is that it prevents online spying over a user while he or she is surfing the internet. This
provides ultimate support a person is on the move with their internet connectivity options open via mobile data or WiFi hotspots on
through their laptop, mobile or other connecting devices. Similarly it keeps a user safe from being spied over while surfing the internet
from a static network like at work or at home.
VPN also has a major masking capability that enables a user to alter the real location from where he or she is actually surfing the
internet. For instance, it is possible that Netflix US can be accessed while the user is in the United Kingdom. Therefore, using VPN
encryptions for online voting systems are safe enough to mask the location and the identity of a voter in order to save the person from
being spied over. It had been previously seen that the voters were easily spied on to find out where the votes have been casted and
were easily tracked down so that the voting system could be rigged. Implementation of VPN encryption would alter the matter for the
betterment of the procedure.
On the other hand, the use of AES or Advanced Encryption Standards could be very beneficial for the online voting systems since it is
one of the most secured encryption algorithms being used in the contemporary times. Although publicly accessible, the documents are
all encrypted in ciphers with the denotation of ‘top secret’. AES encryption is also known as block cipher, since the entire algorithm is
1
Table of Contents
Abstract
1.Introduction
2.Literature Review
3. A proposed model Justifications for the newly/updated model, identifying which areas have been enhanced
The VPN and AES encryptions used for the online voting systems were not previously used or were not in vogue. This has always
caused disruption in the authenticity of the online voting system. Since, there are major chances that the voting system published online
can be easily rigged; online voting system with VPN should be used in the latest voting systems that are published online. The VPN or
Virtual Private Network is becoming much more widely used with every passing day since there has been a provision for the users in
the VPN networks to go anonymous while browsing. There are several reasons why a VPN encryption implementation should be ideal
for an online voting system.
One of the major reasons for VPN encryption is that it prevents online spying over a user while he or she is surfing the internet. This
provides ultimate support a person is on the move with their internet connectivity options open via mobile data or WiFi hotspots on
through their laptop, mobile or other connecting devices. Similarly it keeps a user safe from being spied over while surfing the internet
from a static network like at work or at home.
VPN also has a major masking capability that enables a user to alter the real location from where he or she is actually surfing the
internet. For instance, it is possible that Netflix US can be accessed while the user is in the United Kingdom. Therefore, using VPN
encryptions for online voting systems are safe enough to mask the location and the identity of a voter in order to save the person from
being spied over. It had been previously seen that the voters were easily spied on to find out where the votes have been casted and
were easily tracked down so that the voting system could be rigged. Implementation of VPN encryption would alter the matter for the
betterment of the procedure.
On the other hand, the use of AES or Advanced Encryption Standards could be very beneficial for the online voting systems since it is
one of the most secured encryption algorithms being used in the contemporary times. Although publicly accessible, the documents are
all encrypted in ciphers with the denotation of ‘top secret’. AES encryption is also known as block cipher, since the entire algorithm is
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

based on several permutations, substitutions, and linear transformations that are executed on 16 byte data blocks for each of them. This
encryption process has the ability to encrypt electronic data in a symmetric block cipher. Without the use of this encryption method, the
traditional method of DES algorithm or Data Encryption Standard algorithm was gradually falling into becoming vulnerable to brute-
force attacks. This problem could be easily resolved with the use of Advanced Encryption Standards since the encryption method had
the capability of securing online electronic data through to the next century. AES is also very easy to implement in both hardware,
software and into restricted environments, such as smart cards, as well.
Therefore, it is justified to implement VPN and AES encryption algorithm standards for the online voting system to make the entire
process far more secured than it had been in the traditional way.
Explanations of the model, selecting key models used.
VPN AES Model for online voting system: The models used for the online voting system encryption to provide maximum security to
the voters as well as the casted votes, the VPN and AES models are to be used. This would be done by a very simple procedure as
described below.
At first, in the online voting system portal is accessed and then the voters would be available to enter their information in the login
form. If the login details are valid, then only it can be moved on to the next phase or else, the login page would not redirect to the next
pages. This would be justified with the unique login ID for each voter.
Each voters must be identified with a unique identifier, and for that, the proposed solution puts forward the idea of implementing a
three-step identification process. This process would be generated in the following way with the use of MEC smart cards, generating of
OTP or One Time Passwords and then the implementation of the VPN systems. The Multipurpose Electronic Card or the MEC card
would consist of all the electronic data to hold the information of the individual voters. The MEC card would be needed to be swiped
down to feed in the identification details into the computer.
The next phase of the online voting system would then ask the voter for their fingerprint, since fingerprints are unique to every human
being and cannot be altered in any manner. Only when the designated or registered fingerprint is verified for each voter, only then the
candidate list would be displayed, otherwise it would not open (Backert, Backert & Dahl, 2016). As per the proposed system, the
fingerprint verification would be justified by the generation of a unique OTP that would be send in the individual voter’s phone or
email account registered before. Only then the biometric verification would be justified.
When a specific candidate is chosen, the model thus selected would display whether or not the candidate has already casted their vote.
If it is found that the voter had already casted their vote for the specific candidate, he or she would not be allowed to cast their vote
anew and the process would end. However, if it comes to light that the voter chosen has not yet casted their vote before for any of the
candidates, then only it would assign the voter to encrypt themselves with the unique and specific encryption key. An admin would
randomly be selected to sign and bind the casted vote by the designated voter. The next phase would follow the generation of the
signature to append to the casted vote along with the unique ID of the designated admin. In the next phase of the online voting system,
the casted vote by the voters would be sealed with the process of a unique hash value along with unique hash values generated for the
2
encryption process has the ability to encrypt electronic data in a symmetric block cipher. Without the use of this encryption method, the
traditional method of DES algorithm or Data Encryption Standard algorithm was gradually falling into becoming vulnerable to brute-
force attacks. This problem could be easily resolved with the use of Advanced Encryption Standards since the encryption method had
the capability of securing online electronic data through to the next century. AES is also very easy to implement in both hardware,
software and into restricted environments, such as smart cards, as well.
Therefore, it is justified to implement VPN and AES encryption algorithm standards for the online voting system to make the entire
process far more secured than it had been in the traditional way.
Explanations of the model, selecting key models used.
VPN AES Model for online voting system: The models used for the online voting system encryption to provide maximum security to
the voters as well as the casted votes, the VPN and AES models are to be used. This would be done by a very simple procedure as
described below.
At first, in the online voting system portal is accessed and then the voters would be available to enter their information in the login
form. If the login details are valid, then only it can be moved on to the next phase or else, the login page would not redirect to the next
pages. This would be justified with the unique login ID for each voter.
Each voters must be identified with a unique identifier, and for that, the proposed solution puts forward the idea of implementing a
three-step identification process. This process would be generated in the following way with the use of MEC smart cards, generating of
OTP or One Time Passwords and then the implementation of the VPN systems. The Multipurpose Electronic Card or the MEC card
would consist of all the electronic data to hold the information of the individual voters. The MEC card would be needed to be swiped
down to feed in the identification details into the computer.
The next phase of the online voting system would then ask the voter for their fingerprint, since fingerprints are unique to every human
being and cannot be altered in any manner. Only when the designated or registered fingerprint is verified for each voter, only then the
candidate list would be displayed, otherwise it would not open (Backert, Backert & Dahl, 2016). As per the proposed system, the
fingerprint verification would be justified by the generation of a unique OTP that would be send in the individual voter’s phone or
email account registered before. Only then the biometric verification would be justified.
When a specific candidate is chosen, the model thus selected would display whether or not the candidate has already casted their vote.
If it is found that the voter had already casted their vote for the specific candidate, he or she would not be allowed to cast their vote
anew and the process would end. However, if it comes to light that the voter chosen has not yet casted their vote before for any of the
candidates, then only it would assign the voter to encrypt themselves with the unique and specific encryption key. An admin would
randomly be selected to sign and bind the casted vote by the designated voter. The next phase would follow the generation of the
signature to append to the casted vote along with the unique ID of the designated admin. In the next phase of the online voting system,
the casted vote by the voters would be sealed with the process of a unique hash value along with unique hash values generated for the
2

signature and the time stamp for the casting of the vote as well. The system would then store this entirely encrypted file in the database.
This entire system would form the suitable model that would be far more essential than the traditional ways of recording online votes in
an online voting system.
Highlighting some strengths of the model compared to previous models
There are several reasons behind the implementation of VPN algorithm and AES encryption process in the proposed system. Most
definitely because it possesses numerous advantages over the previous tradition method of online voting systems. The strengths of the
proposed model in comparison with the previous models in vogue are as listed as below:
i. Enhanced Security: The proposed model is far more secured in comparison with the previous models given the VPN
algorithm system and AES encryption methods. This is because with the use of the VPN method, data is kept from being
stolen, altered or hacked by keeping it encrypted. The AES algorithm is used for the encryption. This acts as an advantage on
the previous online voting systems as they were easily prone to get hacked given the less secured system.
ii. Remote Control: With the use of VPN, the online voting system can be managed from any area and information can be
accessed from any device. In addition, the VPN algorithm also allows masking the accessing location from the hackers. This is
another reason why the productivity can be increased much more in comparison with the traditional system of online voting.
iii. Sharing of Files: VPN algorithm, along with AES encryption system also allows several devices to share files amongst each
other for a long period of time.
iv. Online Anonymity: VPN possesses another quality of successfully hiding the web browsing for any user maintaining
complete anonymity. Although, there are other ways by which user anonymity can be achieved, like the web proxies and Hide
IP software, but the proposed system allows a user to access both websites as well as web applications maintaining complete
anonymity of a user.
v. Bypass filters and unblocking of websites: There are various reasons for which the proposed system uses VPN and AES to
access blocked websites and bypass internet filters. While remote accessing the online voting portal, it may happen that the
user is situated in a place that does not allow the specific IP or URL to be accessed from that region (Backert, Backert & Dahl,
2016). Therefore, this new implemented technology would enable accessing the portal from any place in the planet penetrating
the website blockers and bypass internet filters. Compared to the older technologies, this is a breakthrough system proposed for
the online voting systems since in previous times remote accessing and penetrating website blockers was not at all possible.
vi. Change of IP address: The proposed system is also available to make changes in the IP address when needed while moving
from one country to another and accessing the portal from different IP addresses. This system was unavailable in the old
systems.
vii. Cost Reduction: Since maintenance of the entire system is severely low, it has a much reduced cost than the older systems for
3
This entire system would form the suitable model that would be far more essential than the traditional ways of recording online votes in
an online voting system.
Highlighting some strengths of the model compared to previous models
There are several reasons behind the implementation of VPN algorithm and AES encryption process in the proposed system. Most
definitely because it possesses numerous advantages over the previous tradition method of online voting systems. The strengths of the
proposed model in comparison with the previous models in vogue are as listed as below:
i. Enhanced Security: The proposed model is far more secured in comparison with the previous models given the VPN
algorithm system and AES encryption methods. This is because with the use of the VPN method, data is kept from being
stolen, altered or hacked by keeping it encrypted. The AES algorithm is used for the encryption. This acts as an advantage on
the previous online voting systems as they were easily prone to get hacked given the less secured system.
ii. Remote Control: With the use of VPN, the online voting system can be managed from any area and information can be
accessed from any device. In addition, the VPN algorithm also allows masking the accessing location from the hackers. This is
another reason why the productivity can be increased much more in comparison with the traditional system of online voting.
iii. Sharing of Files: VPN algorithm, along with AES encryption system also allows several devices to share files amongst each
other for a long period of time.
iv. Online Anonymity: VPN possesses another quality of successfully hiding the web browsing for any user maintaining
complete anonymity. Although, there are other ways by which user anonymity can be achieved, like the web proxies and Hide
IP software, but the proposed system allows a user to access both websites as well as web applications maintaining complete
anonymity of a user.
v. Bypass filters and unblocking of websites: There are various reasons for which the proposed system uses VPN and AES to
access blocked websites and bypass internet filters. While remote accessing the online voting portal, it may happen that the
user is situated in a place that does not allow the specific IP or URL to be accessed from that region (Backert, Backert & Dahl,
2016). Therefore, this new implemented technology would enable accessing the portal from any place in the planet penetrating
the website blockers and bypass internet filters. Compared to the older technologies, this is a breakthrough system proposed for
the online voting systems since in previous times remote accessing and penetrating website blockers was not at all possible.
vi. Change of IP address: The proposed system is also available to make changes in the IP address when needed while moving
from one country to another and accessing the portal from different IP addresses. This system was unavailable in the old
systems.
vii. Cost Reduction: Since maintenance of the entire system is severely low, it has a much reduced cost than the older systems for
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

online voting.
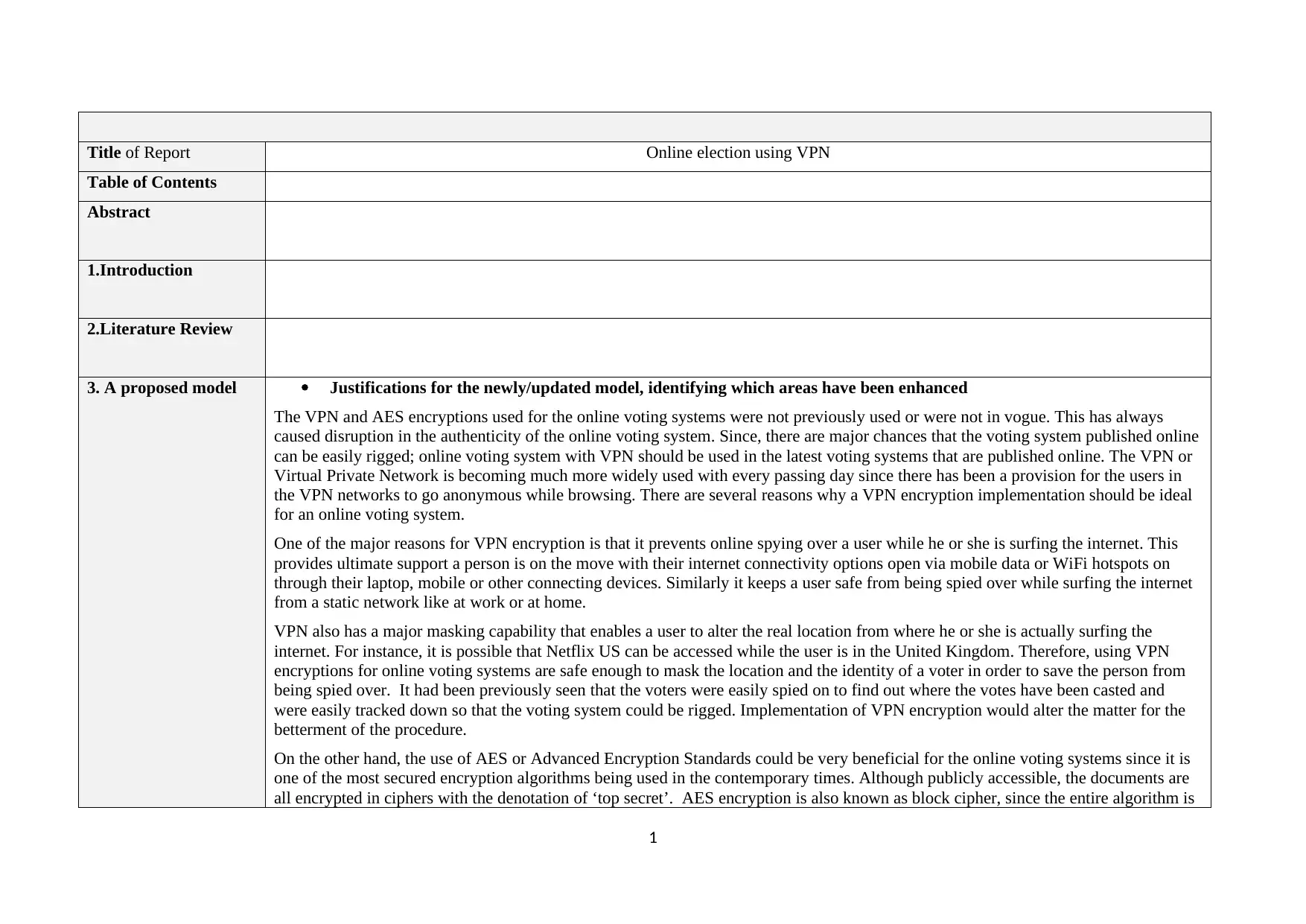
4. Implementation of
the model
Context of the model implementation:
Voting processes are considered to be one of the chief elements that support democracy which helps the entire population of a country
to decide unanimously. These processes are influenced by the information technology processes and hence are evolved into e-voting or
online voting systems. The topic forms an important aspect for research where cryptographic primitives were utilized in order to make
the voting system much more secure. This was done since every data in the cyberworld are prone to extensive hacking. The encryption
process have so far been tried to be made more and more secure since the previous models are still prone to hacking. The proposed
models hold the use of VPN and AES encryption models to make it impenetrable by the hackers. Through the use of the model
proposed, it could be seen that there are many advantages due to the implementation of the newest proposed model. The use of VPN
and AES algorithms help in maintaining utmost security. Maintaining security is the primary important factor for online voting system
since there is a high chance of the voting results being rigged as this hold utmost importance for the entire country. Therefore, the
primary factor that should be focused on is the security reasons of the online voting results. This holds great importance in the
maintenance of democracy in a country and forms a deciding factor for the entire nation.
Demonstration of implementation:
The models used for the online voting system encryption to provide maximum security to the voters as well as the casted votes, the
VPN and AES models are to be used. This would be done by a straightforward procedure as described below.
At first, in the online voting system portal is accessed and then the voters would be available to enter their information in the login
form. If the login details are valid, then only it can be moved on to the next phase or else, the login page would not redirect to the
following pages. This would be justified with the unique login ID for each voter.
Each voter must be identified with a unique identifier, and for that, the proposed solution puts forward the idea of implementing a
three-step identification process. This process would be generated in the following way with the use of MEC smart cards, making of
OTP or One Time Passwords and then the implementation of the VPN systems (AboSamra et al., 2017). The Multipurpose Electronic
Card or the MEC card would consist of all the electronic data to hold the information of the individual voters. The MEC card would be
needed to be swiped down to feed in the identification details into the computer.
The next phase of the online voting system would then ask the voter for their fingerprint since fingerprints are unique to every human
being and cannot be altered in any manner. Only when the designated or registered fingerprint is verified for each voter, only then the
candidate list would be displayed; otherwise, it would not open. As per the proposed system, the fingerprint verification would be
justified by the generation of a unique OTP that would be sent in the individual voter’s phone or email account registered before. Only
then the biometric verification would be justified.
When a specific candidate is chosen, the model thus selected would display whether or not the candidate has already cast their vote. If
it is found that the voter had already cast their vote for the specific candidate, he or she would not be allowed to cast their vote anew,
4
4. Implementation of
the model
Context of the model implementation:
Voting processes are considered to be one of the chief elements that support democracy which helps the entire population of a country
to decide unanimously. These processes are influenced by the information technology processes and hence are evolved into e-voting or
online voting systems. The topic forms an important aspect for research where cryptographic primitives were utilized in order to make
the voting system much more secure. This was done since every data in the cyberworld are prone to extensive hacking. The encryption
process have so far been tried to be made more and more secure since the previous models are still prone to hacking. The proposed
models hold the use of VPN and AES encryption models to make it impenetrable by the hackers. Through the use of the model
proposed, it could be seen that there are many advantages due to the implementation of the newest proposed model. The use of VPN
and AES algorithms help in maintaining utmost security. Maintaining security is the primary important factor for online voting system
since there is a high chance of the voting results being rigged as this hold utmost importance for the entire country. Therefore, the
primary factor that should be focused on is the security reasons of the online voting results. This holds great importance in the
maintenance of democracy in a country and forms a deciding factor for the entire nation.
Demonstration of implementation:
The models used for the online voting system encryption to provide maximum security to the voters as well as the casted votes, the
VPN and AES models are to be used. This would be done by a straightforward procedure as described below.
At first, in the online voting system portal is accessed and then the voters would be available to enter their information in the login
form. If the login details are valid, then only it can be moved on to the next phase or else, the login page would not redirect to the
following pages. This would be justified with the unique login ID for each voter.
Each voter must be identified with a unique identifier, and for that, the proposed solution puts forward the idea of implementing a
three-step identification process. This process would be generated in the following way with the use of MEC smart cards, making of
OTP or One Time Passwords and then the implementation of the VPN systems (AboSamra et al., 2017). The Multipurpose Electronic
Card or the MEC card would consist of all the electronic data to hold the information of the individual voters. The MEC card would be
needed to be swiped down to feed in the identification details into the computer.
The next phase of the online voting system would then ask the voter for their fingerprint since fingerprints are unique to every human
being and cannot be altered in any manner. Only when the designated or registered fingerprint is verified for each voter, only then the
candidate list would be displayed; otherwise, it would not open. As per the proposed system, the fingerprint verification would be
justified by the generation of a unique OTP that would be sent in the individual voter’s phone or email account registered before. Only
then the biometric verification would be justified.
When a specific candidate is chosen, the model thus selected would display whether or not the candidate has already cast their vote. If
it is found that the voter had already cast their vote for the specific candidate, he or she would not be allowed to cast their vote anew,
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

and the process would end. However, if it comes to light that the voter chosen has not yet cast their ballot before for any of the
candidates, then only it would assign the voter to encrypt themselves with the unique and specific encryption key. An admin would
randomly be selected to sign and bind the casted vote by the designated voter. The next phase would follow the generation of the
signature to append to the casted vote along with the unique ID of the designated admin. In the next period of the online voting system,
the casted vote by the voters would be sealed with the process of a unique hash value along with unique hash values generated for the
signature and the time stamp for the casting of the vote as well. The system would then store this entirely encrypted file in the database.
This entire system would form the suitable model that would be far more essential than the traditional ways of recording online votes in
an online voting system.
5
candidates, then only it would assign the voter to encrypt themselves with the unique and specific encryption key. An admin would
randomly be selected to sign and bind the casted vote by the designated voter. The next phase would follow the generation of the
signature to append to the casted vote along with the unique ID of the designated admin. In the next period of the online voting system,
the casted vote by the voters would be sealed with the process of a unique hash value along with unique hash values generated for the
signature and the time stamp for the casting of the vote as well. The system would then store this entirely encrypted file in the database.
This entire system would form the suitable model that would be far more essential than the traditional ways of recording online votes in
an online voting system.
5
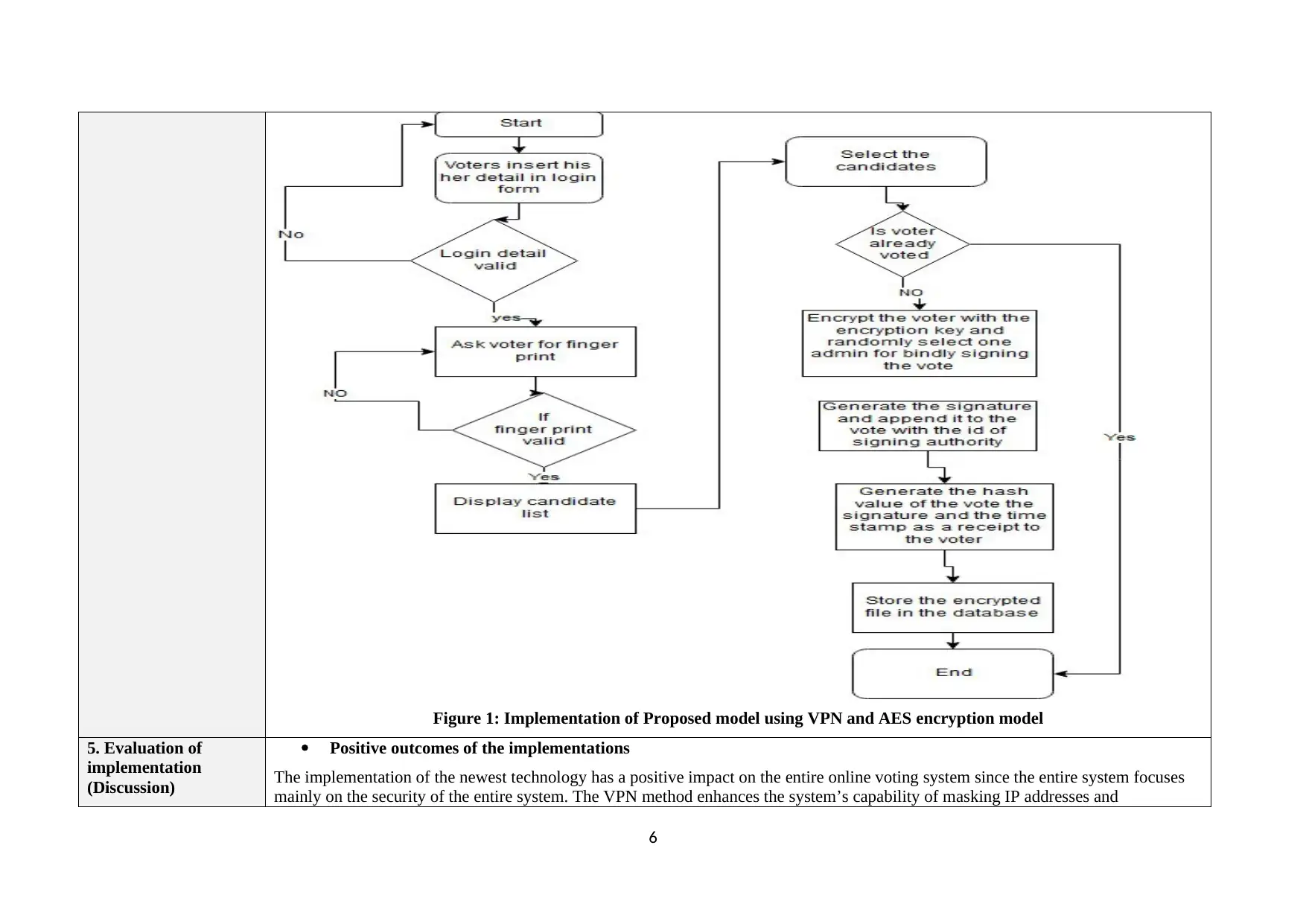
Figure 1: Implementation of Proposed model using VPN and AES encryption model
5. Evaluation of
implementation
(Discussion)
Positive outcomes of the implementations
The implementation of the newest technology has a positive impact on the entire online voting system since the entire system focuses
mainly on the security of the entire system. The VPN method enhances the system’s capability of masking IP addresses and
6
5. Evaluation of
implementation
(Discussion)
Positive outcomes of the implementations
The implementation of the newest technology has a positive impact on the entire online voting system since the entire system focuses
mainly on the security of the entire system. The VPN method enhances the system’s capability of masking IP addresses and
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
maintaining total security in both the cases of the voters and the candidates the voters are voting for. The online voting system forms a
major issue in maintaining complete security since it is essential in determining the future of a nation.
Justification:
Figure: Before using VPN in the system
It can be clearly noticed that without the use VPN in the system, the information that have been transferred through the
system from one device to another can be easily seen through the information bar. Therefore, any hacker can access the
system information once disclosed through the previous processes.
7
major issue in maintaining complete security since it is essential in determining the future of a nation.
Justification:
Figure: Before using VPN in the system
It can be clearly noticed that without the use VPN in the system, the information that have been transferred through the
system from one device to another can be easily seen through the information bar. Therefore, any hacker can access the
system information once disclosed through the previous processes.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
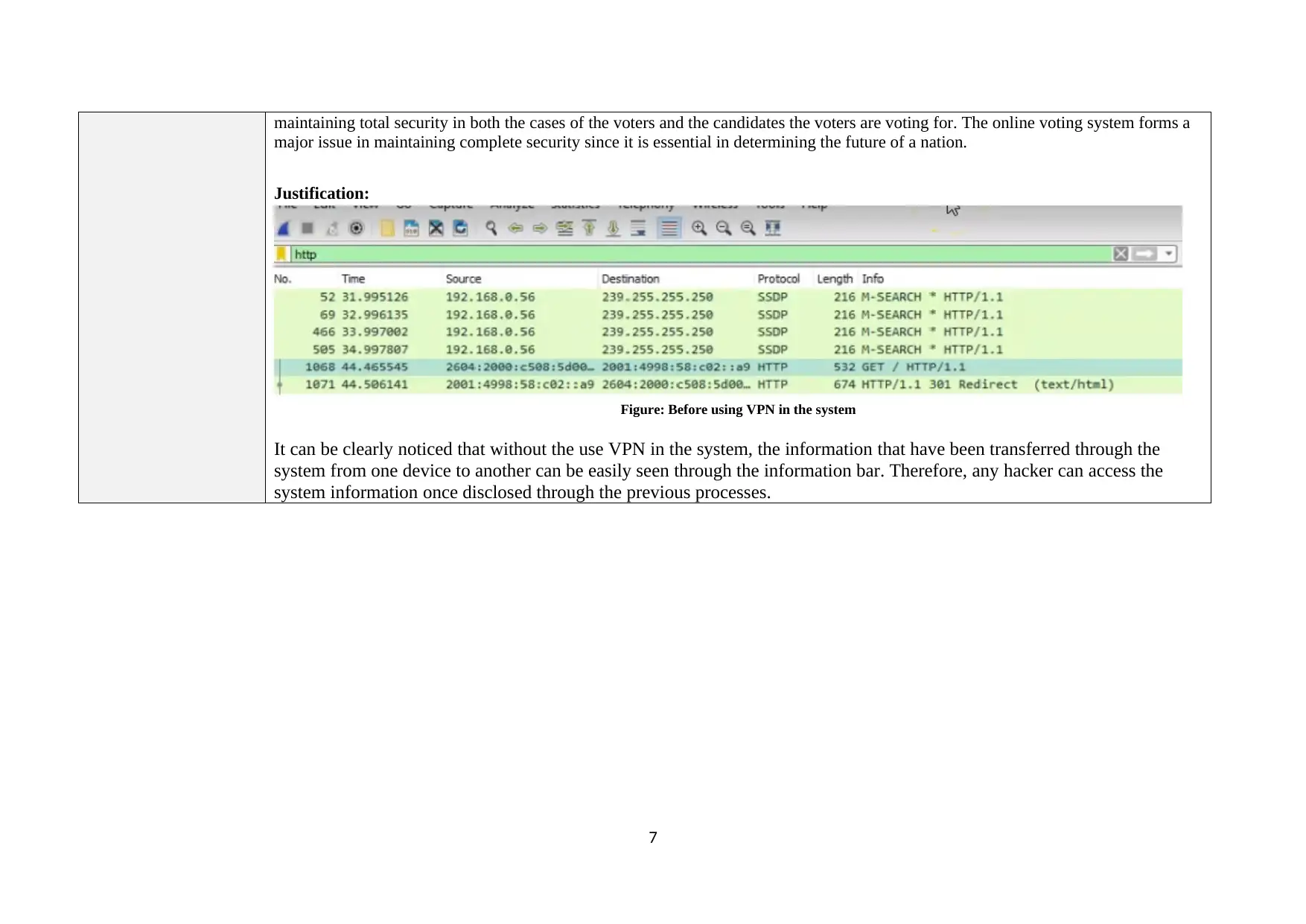
Figure: After using VPN in the system
Right after the implementation of the VPN algorithm, it can be clearly seen that the information transferred in the system from one
device to the other cannot be seen in any way since they have been encrypted. Therefore, it is safe from being hacked by malicious
hackers.
8
Right after the implementation of the VPN algorithm, it can be clearly seen that the information transferred in the system from one
device to the other cannot be seen in any way since they have been encrypted. Therefore, it is safe from being hacked by malicious
hackers.
8
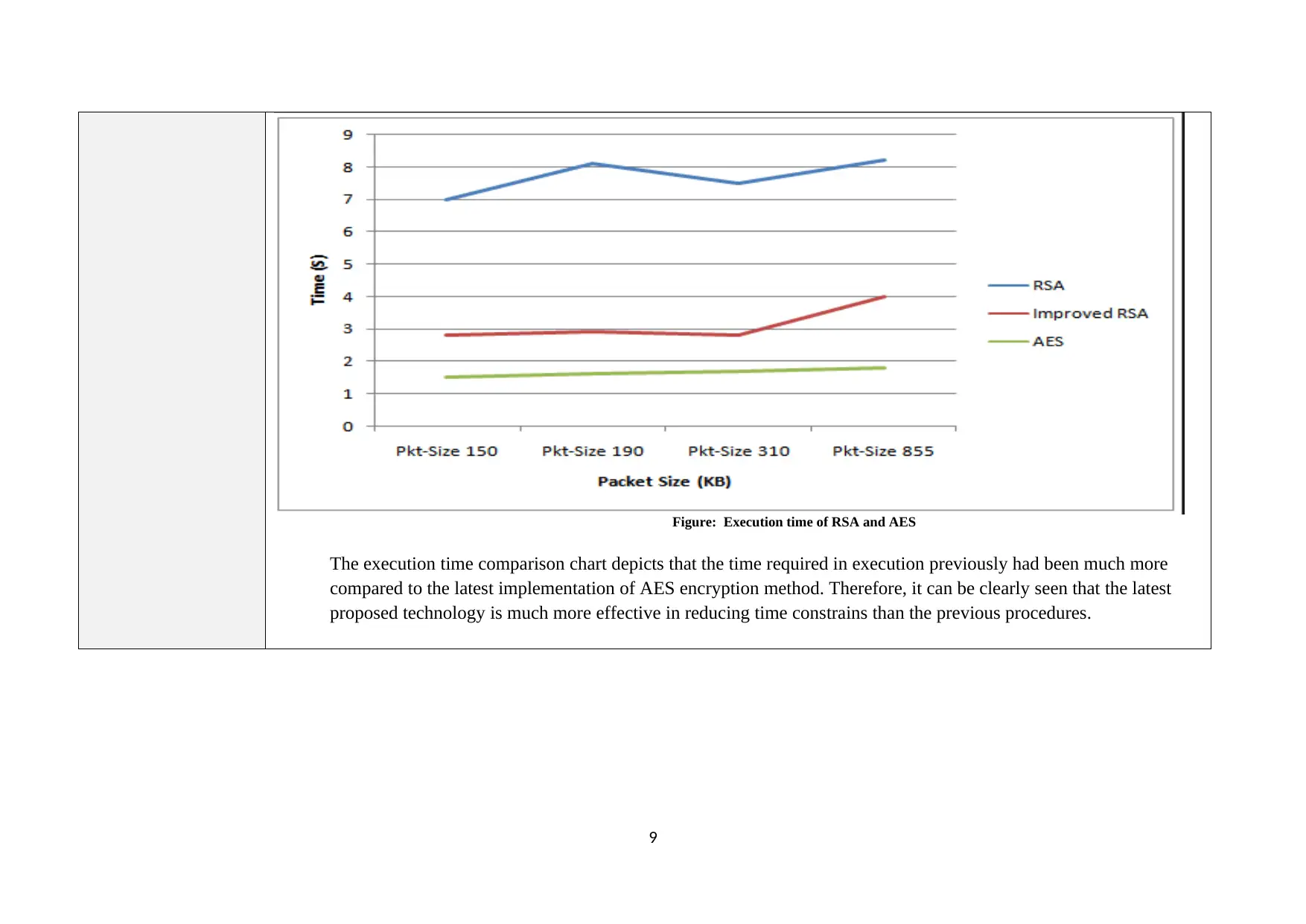
Figure: Execution time of RSA and AES
The execution time comparison chart depicts that the time required in execution previously had been much more
compared to the latest implementation of AES encryption method. Therefore, it can be clearly seen that the latest
proposed technology is much more effective in reducing time constrains than the previous procedures.
9
The execution time comparison chart depicts that the time required in execution previously had been much more
compared to the latest implementation of AES encryption method. Therefore, it can be clearly seen that the latest
proposed technology is much more effective in reducing time constrains than the previous procedures.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
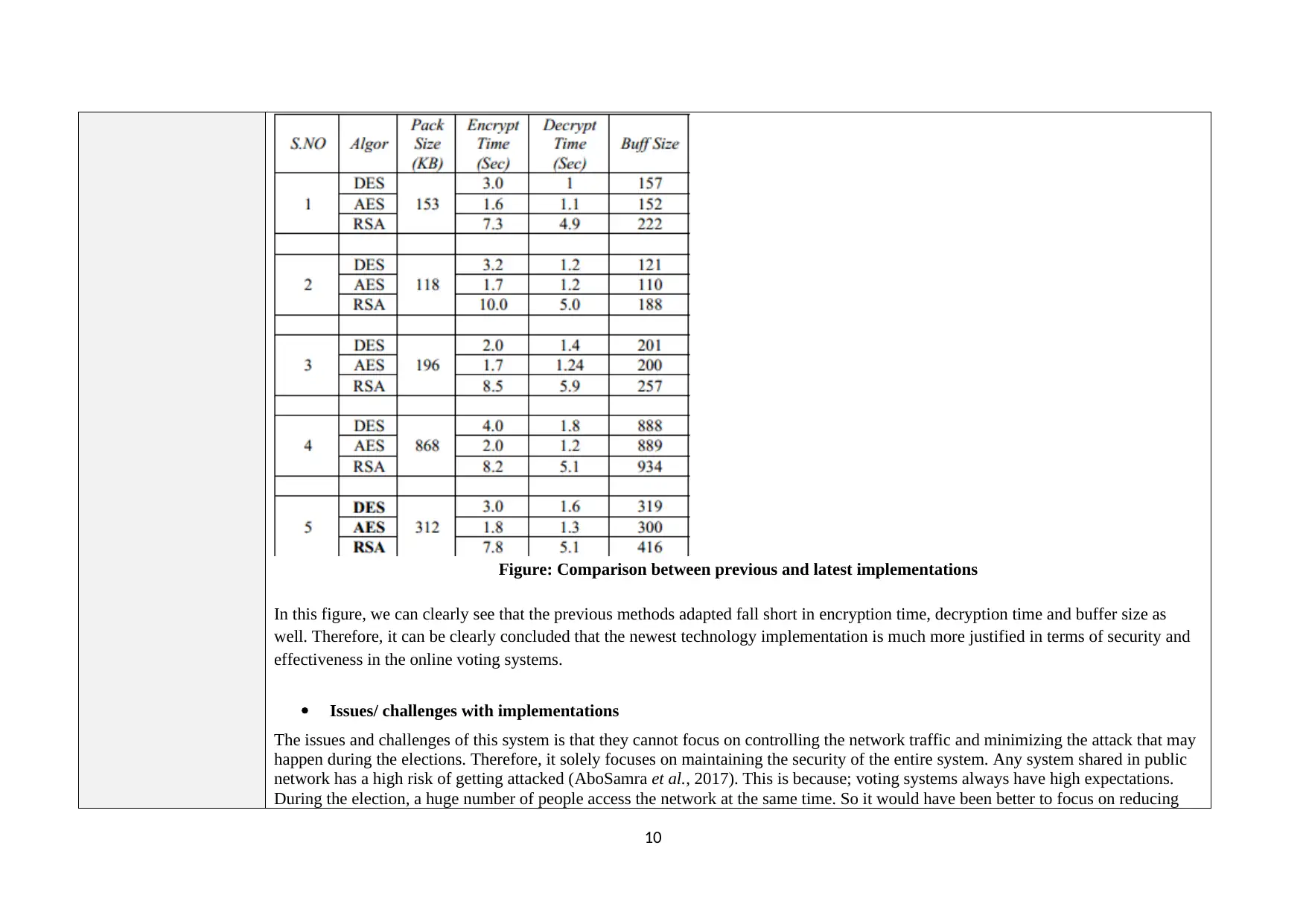
Figure: Comparison between previous and latest implementations
In this figure, we can clearly see that the previous methods adapted fall short in encryption time, decryption time and buffer size as
well. Therefore, it can be clearly concluded that the newest technology implementation is much more justified in terms of security and
effectiveness in the online voting systems.
Issues/ challenges with implementations
The issues and challenges of this system is that they cannot focus on controlling the network traffic and minimizing the attack that may
happen during the elections. Therefore, it solely focuses on maintaining the security of the entire system. Any system shared in public
network has a high risk of getting attacked (AboSamra et al., 2017). This is because; voting systems always have high expectations.
During the election, a huge number of people access the network at the same time. So it would have been better to focus on reducing
10
In this figure, we can clearly see that the previous methods adapted fall short in encryption time, decryption time and buffer size as
well. Therefore, it can be clearly concluded that the newest technology implementation is much more justified in terms of security and
effectiveness in the online voting systems.
Issues/ challenges with implementations
The issues and challenges of this system is that they cannot focus on controlling the network traffic and minimizing the attack that may
happen during the elections. Therefore, it solely focuses on maintaining the security of the entire system. Any system shared in public
network has a high risk of getting attacked (AboSamra et al., 2017). This is because; voting systems always have high expectations.
During the election, a huge number of people access the network at the same time. So it would have been better to focus on reducing
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

the traffic or having activity control of the system in network.
The confidentiality of the voter votes may be in question because of the same interface and database that they have in the
authentication and voting process. This is an authentication phase of the system. Same database have been used in the interface
which joins the authentication and voting phase. Problem like “Man in middle” can occur and change the vote. For instance,
when a user logs in using their id and password than they are subjected to receive the UI which allow them to vote. Both login and
voting interface has same database. As a result of the same database, now if admin or polling officer of the system wants than he can
easily see what a particular identity has vote for and at the same time he or she can tamper with the data as well. In fact, it would be
problematic to trust on any authority because in fear of getting corrupted. There is not such mechanism in the network which
provides the honesty and evidence that they are safe and secured. Mechanism to control the network traffic and network
attack should be implementing in future proposal.
6. Conclusion with
Recommendations
References AboSamra, K. M., AbdelHafez, A. A., Assassa, G. M., & Mursi, M. F. (2017). A practical, secure, and auditable e-voting
system. Journal of Information Security and Applications, 36, 69-89.
Aziz, A. A. A., Qunoo, H. N., & Samra, A. A. A. (2018). Using homomorphic cryptographic solutions on E-voting Systems.
Backert, A., Backert, C. C., & Dahl, C. C. (2016). U.S. Patent No. 9,401,059. Washington, DC: U.S. Patent and Trademark Office.
Darwish, A., El-Gendy, M. M., & Hassanien, A. E. (2017). A New Hybrid Cryptosystem for Internet of Things Applications.
In Multimedia Forensics and Security (pp. 365-380). Springer, Cham.
Divya, P., agrahwal, P., & ojha, S. (2014). International Journal of Scientific Research Engineering & Technology (IJSRET).
ADVANCED ONLINE VOTING SYSTEM , 687-691.
Garfinkle, N., & Garfinkle, R. (2017). U.S. Patent No. 9,536,366. Washington, DC: U.S. Patent and Trademark Office.
Guasch Castelló, S., Escala Ribas, A., & Puiggalí, A. J. (2017). U.S. Patent Application No. 15/538,033.
Haibin, W., Xia, L., & Sheng, Z. (2015). Wireless Sensor Network Application in engineering. Multi authority E-voting system based
on Group blind signature , 89-93.
Hon, C. T., Tam, C. H., & Ma, T. H. (2017). U.S. Patent Application No. 15/654,739.
Khatun, R., Bandopadhyay, T., & Roy, D. A. (2017). I.J. Information Engineering and Electronic Business. Data Modeling for Evoting
system Using smart card based E-governance system , 45-52.
Marinescu, L. (2015). Journal of Mobile, Embedded and Distributed Systems. Security System for mobile voting Biometric , 100-108.
Mohammadpourfard, M., Doostari, M. A., Ghoushchi, M. B., & Shakiba, N. (2014). RESEARCH ARTICLE. A new secure Internet
11
The confidentiality of the voter votes may be in question because of the same interface and database that they have in the
authentication and voting process. This is an authentication phase of the system. Same database have been used in the interface
which joins the authentication and voting phase. Problem like “Man in middle” can occur and change the vote. For instance,
when a user logs in using their id and password than they are subjected to receive the UI which allow them to vote. Both login and
voting interface has same database. As a result of the same database, now if admin or polling officer of the system wants than he can
easily see what a particular identity has vote for and at the same time he or she can tamper with the data as well. In fact, it would be
problematic to trust on any authority because in fear of getting corrupted. There is not such mechanism in the network which
provides the honesty and evidence that they are safe and secured. Mechanism to control the network traffic and network
attack should be implementing in future proposal.
6. Conclusion with
Recommendations
References AboSamra, K. M., AbdelHafez, A. A., Assassa, G. M., & Mursi, M. F. (2017). A practical, secure, and auditable e-voting
system. Journal of Information Security and Applications, 36, 69-89.
Aziz, A. A. A., Qunoo, H. N., & Samra, A. A. A. (2018). Using homomorphic cryptographic solutions on E-voting Systems.
Backert, A., Backert, C. C., & Dahl, C. C. (2016). U.S. Patent No. 9,401,059. Washington, DC: U.S. Patent and Trademark Office.
Darwish, A., El-Gendy, M. M., & Hassanien, A. E. (2017). A New Hybrid Cryptosystem for Internet of Things Applications.
In Multimedia Forensics and Security (pp. 365-380). Springer, Cham.
Divya, P., agrahwal, P., & ojha, S. (2014). International Journal of Scientific Research Engineering & Technology (IJSRET).
ADVANCED ONLINE VOTING SYSTEM , 687-691.
Garfinkle, N., & Garfinkle, R. (2017). U.S. Patent No. 9,536,366. Washington, DC: U.S. Patent and Trademark Office.
Guasch Castelló, S., Escala Ribas, A., & Puiggalí, A. J. (2017). U.S. Patent Application No. 15/538,033.
Haibin, W., Xia, L., & Sheng, Z. (2015). Wireless Sensor Network Application in engineering. Multi authority E-voting system based
on Group blind signature , 89-93.
Hon, C. T., Tam, C. H., & Ma, T. H. (2017). U.S. Patent Application No. 15/654,739.
Khatun, R., Bandopadhyay, T., & Roy, D. A. (2017). I.J. Information Engineering and Electronic Business. Data Modeling for Evoting
system Using smart card based E-governance system , 45-52.
Marinescu, L. (2015). Journal of Mobile, Embedded and Distributed Systems. Security System for mobile voting Biometric , 100-108.
Mohammadpourfard, M., Doostari, M. A., Ghoushchi, M. B., & Shakiba, N. (2014). RESEARCH ARTICLE. A new secure Internet
11

voting protocol using Java Card 3 , 261-284.
Neha Saini, H. V. (2017). Recent Research aspect. An Analytical study of E-voting System , 75-85.
Nielsen, J. (2015). Design principle FTW. Retrieved 4 22, 2017, from 10 Usability Heuristics for User Interface Design:
https://www.designprinciplesftw.com/collections/10-usability-heuristics-for-user-interface-design
Olaniyi, O. M., Folorunso, T. A., Ahmed, A., & Joshep, O. (2016). Information Engineering and Electronic Business. Design of secure
Electronic Voting System Using fingerprint biometric and Cryptography watermarking approach , 9-17.
Osho, L. O. (2016). I.J. Information Engineering and Electronic Business. Framework for an E-voting system Applicable in developing
economy , 9-21.
R., I., & S., S. (2018). Web Based Application For Secure Online Voting System. International Journal Of Computer Science
Engineering & Technology, 8(2), 23-27
Rura, L., Issac, B., & Haldar, M. K. (2017). Journal of Computing and Information Technology, Vo. Online Voting System Based on
Image , 47-61.
Selvadurai, N. (2015). Not just a face in the crowd: addressing the intrusive potential of the online application of face recognition
technologies. International Journal Of Law & Information Technology, 23(3), 187-218. doi:10.1093/ijlit/eav006
Tanveer, A., Ali, A., Paracha, M. A., & Raja, F. R. (2015, January). Performance analysis of AES-finalists along with SHS in IPSEC
VPN over 1Gbps link. In Applied Sciences and Technology (IBCAST), 2015 12th International Bhurban Conference on (pp. 323-332).
IEEE.
Appendices
12
Neha Saini, H. V. (2017). Recent Research aspect. An Analytical study of E-voting System , 75-85.
Nielsen, J. (2015). Design principle FTW. Retrieved 4 22, 2017, from 10 Usability Heuristics for User Interface Design:
https://www.designprinciplesftw.com/collections/10-usability-heuristics-for-user-interface-design
Olaniyi, O. M., Folorunso, T. A., Ahmed, A., & Joshep, O. (2016). Information Engineering and Electronic Business. Design of secure
Electronic Voting System Using fingerprint biometric and Cryptography watermarking approach , 9-17.
Osho, L. O. (2016). I.J. Information Engineering and Electronic Business. Framework for an E-voting system Applicable in developing
economy , 9-21.
R., I., & S., S. (2018). Web Based Application For Secure Online Voting System. International Journal Of Computer Science
Engineering & Technology, 8(2), 23-27
Rura, L., Issac, B., & Haldar, M. K. (2017). Journal of Computing and Information Technology, Vo. Online Voting System Based on
Image , 47-61.
Selvadurai, N. (2015). Not just a face in the crowd: addressing the intrusive potential of the online application of face recognition
technologies. International Journal Of Law & Information Technology, 23(3), 187-218. doi:10.1093/ijlit/eav006
Tanveer, A., Ali, A., Paracha, M. A., & Raja, F. R. (2015, January). Performance analysis of AES-finalists along with SHS in IPSEC
VPN over 1Gbps link. In Applied Sciences and Technology (IBCAST), 2015 12th International Bhurban Conference on (pp. 323-332).
IEEE.
Appendices
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





