Comprehensive Analysis of ENISA Big Data Infrastructure and Threats
VerifiedAdded on 2019/11/19
|14
|3649
|302
Report
AI Summary
This report provides a comprehensive analysis of the ENISA Big Data Infrastructure, focusing on the cyber threat landscape as reported in 2016. It details fifteen types of threats faced by the European cyber sector, categorized into unintentional damage, hijacking, nefarious abuse, legal threats, and organizational threats. The report examines the threats, including their kill chain methods, and discusses the threat agents, such as corporations, cybercriminals, cyber terrorists, script kiddies, online social hackers, and employees. It also outlines mitigation strategies to address these threats, emphasizing the importance of threat defenders. The report highlights the most significant threats, such as nefarious abuse and their activities, which involve financial account and personal data access, and emphasizes the need for policy makers and companies to handle cyber threats effectively.

Running head: ENISA BIG DATA INFRASTRUCTURE
ENISA Big Data Infrastructure
Name of Student-
Name of University-
Student ID-
Author Note-
ENISA Big Data Infrastructure
Name of Student-
Name of University-
Student ID-
Author Note-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ENISA BIG DATA INFRASTRUCTURE
Introduction
The agency that gives the security that is related to the cyber space in Europe’s
organizations is known as European Union Agency for Network and Information Security.
European Union Agency for Network and Information Security is better known as ENISA. The
security related to cyber space is known as Network and Information Security (NIS). The NIS
security is provided by the European Union Agency for Network and Information Security
(ENISA). The security of Network and Information Security is carried out that is related to
develop and promote the culture of security (Silva, Rocha & Guimaraes, 2016). To make
Network and Information Security a level up, the European Union Agency for Network and
Information Security was set up in the year 2004 in European Union. A developed process of
Network and Information Security for the market to function properly European Union Agency
for Network and Information Security was implied.
The agency of ENISA (European Union Agency for Network and Information Security)
was introduced to give advice and the related solutions to the problem. It works with the private
sector as well as the members of that state in which ENISA is located (Bastl, Mareš & Tvrdá,
2015). The planning that are made to develop the National Cyber Security is exercised by
European Union Agency for Network and Information Security and also are concerned with the
pan European’s cyber security (Bartsch & Frey, 2017). Cooperation and capacity that are related
to CSIRT are also exercised by ENISA and also schedules in increasing the technologies which
are owned by private organizations, private technologies that are coming in organizations,
adoption of cloud and also to the email ids that are related to cyber threat landscape (CTL). The
laws that are tied up with NIS (Network and Information Security) are promoted by European
Introduction
The agency that gives the security that is related to the cyber space in Europe’s
organizations is known as European Union Agency for Network and Information Security.
European Union Agency for Network and Information Security is better known as ENISA. The
security related to cyber space is known as Network and Information Security (NIS). The NIS
security is provided by the European Union Agency for Network and Information Security
(ENISA). The security of Network and Information Security is carried out that is related to
develop and promote the culture of security (Silva, Rocha & Guimaraes, 2016). To make
Network and Information Security a level up, the European Union Agency for Network and
Information Security was set up in the year 2004 in European Union. A developed process of
Network and Information Security for the market to function properly European Union Agency
for Network and Information Security was implied.
The agency of ENISA (European Union Agency for Network and Information Security)
was introduced to give advice and the related solutions to the problem. It works with the private
sector as well as the members of that state in which ENISA is located (Bastl, Mareš & Tvrdá,
2015). The planning that are made to develop the National Cyber Security is exercised by
European Union Agency for Network and Information Security and also are concerned with the
pan European’s cyber security (Bartsch & Frey, 2017). Cooperation and capacity that are related
to CSIRT are also exercised by ENISA and also schedules in increasing the technologies which
are owned by private organizations, private technologies that are coming in organizations,
adoption of cloud and also to the email ids that are related to cyber threat landscape (CTL). The
laws that are tied up with NIS (Network and Information Security) are promoted by European

2ENISA BIG DATA INFRASTRUCTURE
Union Agency for Network and Information Security and it also looks to develop and implement
the policy of the European Union.
Answer to Question 1:
The case study deals with the security of the threat landscape of European Union Agency
for Network and Information Security which was recorded in the year 2016. There are almost
fifteen types of threats are faced by the cyber sector of the Europe and all the top threats are
discussed in details in the ENISA case study. All these data related to cyber attacks that were
accessed was recorded in 2016 (Kleineidam et al., 2017). Concentration was given more on
attacker and the vectors that attack the cyber space and their related solutions to decrease the
attacks on cyber space have been discussed in the European Threat Landscape. The case study
deals with all those cyber threats are the ways to solve them are elaborately given in the
European Union Agency for Network and Information Security case study. The kill chain
methods of all the threats are stated with diagram. There are almost five group of threat including
the unintentional damage, hijacking, eavesdropping and interception, nefarious activity, legal
threats and the organizational threats (Hänisch & Rogge, 2017). Threats agents are discussed and
their relative good practices to mitigate threats are also showcased in the given case study. The
following diagram shows the European Union Agency for Network and Information Security
landscape infrastructure is given below.
Union Agency for Network and Information Security and it also looks to develop and implement
the policy of the European Union.
Answer to Question 1:
The case study deals with the security of the threat landscape of European Union Agency
for Network and Information Security which was recorded in the year 2016. There are almost
fifteen types of threats are faced by the cyber sector of the Europe and all the top threats are
discussed in details in the ENISA case study. All these data related to cyber attacks that were
accessed was recorded in 2016 (Kleineidam et al., 2017). Concentration was given more on
attacker and the vectors that attack the cyber space and their related solutions to decrease the
attacks on cyber space have been discussed in the European Threat Landscape. The case study
deals with all those cyber threats are the ways to solve them are elaborately given in the
European Union Agency for Network and Information Security case study. The kill chain
methods of all the threats are stated with diagram. There are almost five group of threat including
the unintentional damage, hijacking, eavesdropping and interception, nefarious activity, legal
threats and the organizational threats (Hänisch & Rogge, 2017). Threats agents are discussed and
their relative good practices to mitigate threats are also showcased in the given case study. The
following diagram shows the European Union Agency for Network and Information Security
landscape infrastructure is given below.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
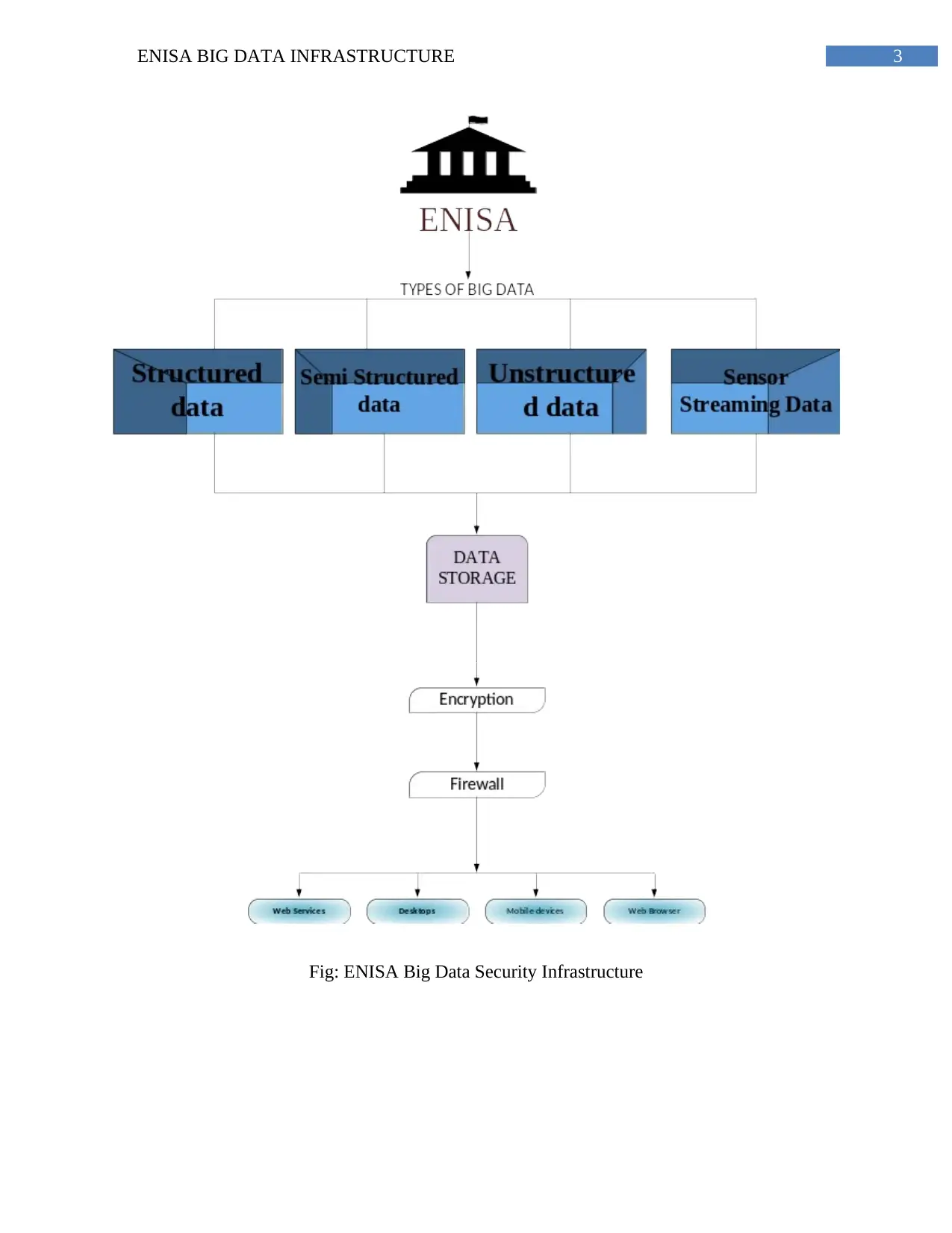
3ENISA BIG DATA INFRASTRUCTURE
Fig: ENISA Big Data Security Infrastructure
Fig: ENISA Big Data Security Infrastructure
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4ENISA BIG DATA INFRASTRUCTURE
Answer to Question 2:
The categorizations that are done for cyber threats for Europe are grouped mainly in five
sectors. Threat group 1 includes: unintentional damage or the loss of IT assets and information or
data. Threat group 2 includes: hijacking, eavesdropping and interception. Threat group 3
includes: nefarious abuse and their activities. Threat group 3 contains the legal threats and lastly
threat group 4 contains threats that comes from the organization itself or may be known as the
intentional threats.
Unintentional damage or the loss of IT assets and Information or data: This group of threat
includes erroneous or unintentional intervention, devices that are lost and sharing and leakage of
data caused due to human error. The threats that are not done intentionally by the organizations
or humans are known as the accidental threats. This accidental threat occurs due to clerical
errors, slips that are skill based and the misconfiguration, management of poor patch, using user
names that are default and the passwords that are easy to guess. The mistakes that are also based
on knowledge which includes crashes and update of software, procedural flaws and integration
problems are also included accidental threats (Lanfer, 2017). The Computer Associate and the
other sources that provides security also announced that threats come from APIs that are
insecure, social networks, photo sharing in mobile, video sharing, snapchat and may be due to
data breach and also facebook. For instance, if the Big data duplicates the data records to ten
times and then divides the copies to again ten nodes of storage for some of the reasons or other,
the nodes may come to an end where it changes the robustness of security at different levels. And
Answer to Question 2:
The categorizations that are done for cyber threats for Europe are grouped mainly in five
sectors. Threat group 1 includes: unintentional damage or the loss of IT assets and information or
data. Threat group 2 includes: hijacking, eavesdropping and interception. Threat group 3
includes: nefarious abuse and their activities. Threat group 3 contains the legal threats and lastly
threat group 4 contains threats that comes from the organization itself or may be known as the
intentional threats.
Unintentional damage or the loss of IT assets and Information or data: This group of threat
includes erroneous or unintentional intervention, devices that are lost and sharing and leakage of
data caused due to human error. The threats that are not done intentionally by the organizations
or humans are known as the accidental threats. This accidental threat occurs due to clerical
errors, slips that are skill based and the misconfiguration, management of poor patch, using user
names that are default and the passwords that are easy to guess. The mistakes that are also based
on knowledge which includes crashes and update of software, procedural flaws and integration
problems are also included accidental threats (Lanfer, 2017). The Computer Associate and the
other sources that provides security also announced that threats come from APIs that are
insecure, social networks, photo sharing in mobile, video sharing, snapchat and may be due to
data breach and also facebook. For instance, if the Big data duplicates the data records to ten
times and then divides the copies to again ten nodes of storage for some of the reasons or other,
the nodes may come to an end where it changes the robustness of security at different levels. And

5ENISA BIG DATA INFRASTRUCTURE
also the probability of data leak and data disclosure is also increased. This is considered as a
major drawback of design of Big Data.
Hijacking, Eavesdropping and Interception: The software distribution of big data is done by
Hadoop, MongoDB63, Cassandra or Couchbase (Stupka, Horák & Husák, 2017). All the
software maintains a protocol that gives integrity and data confidentiality that are done between
application communications enabled by changing the default passwords.
Nefarious abuse and their activities: The information that is managed and stored in big data that
are needed to access financial account and personal data such as payment, billing details and
credit card details. This sector is mainly targeted by the cyber criminals. The profiling of data
that are stored by big data also describes preferences, travel, habits and behavior and creates
much bigger opportunity to identify the thieves (Kubicek & Diederich, 2015). The generic
threats that are mostly affects the components of ICT of infrastructure are exploit kits that allows
malware infections and viruses, worms that allows distribution of the copies of infectious
malware over the network, Trojan are small infectious malware that increases the unauthorized
access of computer system, trapdoors and backdoors are the entry points that are undocumented
in computer system and also service spoofing that attacks the computer system in falsifying the
data and gets such advantages.
Legal Threats: The data storage that comes under directive of data protection in Europe are
needed to compile with the compliancy law of data security throughout the lifecycle of the data,
the personal data that are kept personal for employees and the customers and the guarantee that is
given for the security of the cyber threat by implementing cloud provider.
also the probability of data leak and data disclosure is also increased. This is considered as a
major drawback of design of Big Data.
Hijacking, Eavesdropping and Interception: The software distribution of big data is done by
Hadoop, MongoDB63, Cassandra or Couchbase (Stupka, Horák & Husák, 2017). All the
software maintains a protocol that gives integrity and data confidentiality that are done between
application communications enabled by changing the default passwords.
Nefarious abuse and their activities: The information that is managed and stored in big data that
are needed to access financial account and personal data such as payment, billing details and
credit card details. This sector is mainly targeted by the cyber criminals. The profiling of data
that are stored by big data also describes preferences, travel, habits and behavior and creates
much bigger opportunity to identify the thieves (Kubicek & Diederich, 2015). The generic
threats that are mostly affects the components of ICT of infrastructure are exploit kits that allows
malware infections and viruses, worms that allows distribution of the copies of infectious
malware over the network, Trojan are small infectious malware that increases the unauthorized
access of computer system, trapdoors and backdoors are the entry points that are undocumented
in computer system and also service spoofing that attacks the computer system in falsifying the
data and gets such advantages.
Legal Threats: The data storage that comes under directive of data protection in Europe are
needed to compile with the compliancy law of data security throughout the lifecycle of the data,
the personal data that are kept personal for employees and the customers and the guarantee that is
given for the security of the cyber threat by implementing cloud provider.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ENISA BIG DATA INFRASTRUCTURE
Organizational Threats: The analysis of datasets that are large can undergo new signs of
innovation and productivity and also unlocks the values that ate significant (Christou, 2017). The
policy makers and the companies must handle the threats that are related to cyber space.
Most significant Threat- The most significant group that is identified as most dangerous group
of threat is the nefarious abuse and their activities (Eininger, Skopik & Fiedler, 2015). The
information that is managed and stored in big data that are needed to access financial account
and personal data such as payment, billing details and credit card details. This sector is mainly
targeted by the cyber criminals. The profiling of data that are stored by big data also describes
preferences, travel, habits and behavior and creates much bigger opportunity to identify the
thieves. The generic threats that are mostly affects the components of ICT of infrastructure are
exploit kits that allows malware infections and viruses, worms that allows distribution of the
copies of infectious malware over the network, Trojan are small infectious malware that
increases the unauthorized access of computer system, trapdoors and backdoors are the entry
points that are undocumented in computer system and also service spoofing that attacks the
computer system in falsifying the data and gets such advantages (Schneider, 2017). The threats
coming under nefarious threats are infected code, denial of services, activities or software,
unused audit tools, using duplicate certificates, unauthorized activities, authorization abuse,
failure processes in business and identity fraud.
Answer to Question 3:
Threat agents are those people who come in group or something in group that has some
good capabilities and intension to cope up with the threat and also records the activities that has
already occurred (Jentzsch, 2016). The threats coming from which particular groups of agent are
Organizational Threats: The analysis of datasets that are large can undergo new signs of
innovation and productivity and also unlocks the values that ate significant (Christou, 2017). The
policy makers and the companies must handle the threats that are related to cyber space.
Most significant Threat- The most significant group that is identified as most dangerous group
of threat is the nefarious abuse and their activities (Eininger, Skopik & Fiedler, 2015). The
information that is managed and stored in big data that are needed to access financial account
and personal data such as payment, billing details and credit card details. This sector is mainly
targeted by the cyber criminals. The profiling of data that are stored by big data also describes
preferences, travel, habits and behavior and creates much bigger opportunity to identify the
thieves. The generic threats that are mostly affects the components of ICT of infrastructure are
exploit kits that allows malware infections and viruses, worms that allows distribution of the
copies of infectious malware over the network, Trojan are small infectious malware that
increases the unauthorized access of computer system, trapdoors and backdoors are the entry
points that are undocumented in computer system and also service spoofing that attacks the
computer system in falsifying the data and gets such advantages (Schneider, 2017). The threats
coming under nefarious threats are infected code, denial of services, activities or software,
unused audit tools, using duplicate certificates, unauthorized activities, authorization abuse,
failure processes in business and identity fraud.
Answer to Question 3:
Threat agents are those people who come in group or something in group that has some
good capabilities and intension to cope up with the threat and also records the activities that has
already occurred (Jentzsch, 2016). The threats coming from which particular groups of agent are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7ENISA BIG DATA INFRASTRUCTURE
very difficult to detect for the owners of asset of big data. The categories of threat agents of
ENISA Threat Landscape (ETL) are:
Corporations: Some of the enterprises and organizations use very offensive and bad
tricks in their procedures. Such type of enterprises and organizations are considered as the hostile
agent of threat (Bendiek, 2015). The main motives of these types of hostile agents are building
advantage in competitive markets over competitors. Related with their sector and size, significant
capabilities are usually possessed that ranges from intelligence of human engineering to
technology especially in the sectors in which they are expert.
Cyber criminals: The main objective of cyber criminals are they gain financially and their
skill levels are also too high to cope up with. The nature of cyber criminals is they are hostile.
The attack of cyber criminals can be of any type including national and international level.
Cyber terrorists: Cyber terrorists expanded their own activities and are also engaged
themselves in cyber space attacks. The main objective of cyber criminals are they gain
financially and their skill levels are also too high to cope up with. The nature of cyber criminals
is they are hostile (Schaumüller-Bichl & Kolberger, 2016). The attack of cyber criminals can be
of any type including national and international level. The attacks that are done by cyber
terrorists are mainly in the sector of public health, telecommunications and production. The
failures of such systems cause much loss to the government and the society which helps in
completion of their motive.
Script kiddies: Script kiddies are the copy cats and copy the process of hacking. They
mainly attack for the cause of fun (Weber, A., & Weber, 2015). No such serious motive is
present behind their motive of attack. Script kiddies have low motivation and their capability is
very difficult to detect for the owners of asset of big data. The categories of threat agents of
ENISA Threat Landscape (ETL) are:
Corporations: Some of the enterprises and organizations use very offensive and bad
tricks in their procedures. Such type of enterprises and organizations are considered as the hostile
agent of threat (Bendiek, 2015). The main motives of these types of hostile agents are building
advantage in competitive markets over competitors. Related with their sector and size, significant
capabilities are usually possessed that ranges from intelligence of human engineering to
technology especially in the sectors in which they are expert.
Cyber criminals: The main objective of cyber criminals are they gain financially and their
skill levels are also too high to cope up with. The nature of cyber criminals is they are hostile.
The attack of cyber criminals can be of any type including national and international level.
Cyber terrorists: Cyber terrorists expanded their own activities and are also engaged
themselves in cyber space attacks. The main objective of cyber criminals are they gain
financially and their skill levels are also too high to cope up with. The nature of cyber criminals
is they are hostile (Schaumüller-Bichl & Kolberger, 2016). The attack of cyber criminals can be
of any type including national and international level. The attacks that are done by cyber
terrorists are mainly in the sector of public health, telecommunications and production. The
failures of such systems cause much loss to the government and the society which helps in
completion of their motive.
Script kiddies: Script kiddies are the copy cats and copy the process of hacking. They
mainly attack for the cause of fun (Weber, A., & Weber, 2015). No such serious motive is
present behind their motive of attack. Script kiddies have low motivation and their capability is

8ENISA BIG DATA INFRASTRUCTURE
very low. They are unskilled and take help of script and programs to attack the server or some
system. For the purpose of hacking they mainly take help of some tools to make their attacks
more serious.
Online social hackers (hacktivists): The begun of hactivists mainly came in the year
2016. Their main motive is to protest some cause and also to make promotion of their cause. The
hacktivists mainly attacks on problems of public health, corporations, environmental policy,
military institutions and intelligence agencies.
Employees: The employees group of threat agents lies in the organizations itself. The analysis of
datasets that are large can undergo new signs of innovation and productivity and also unlocks the
values that ate significant (Reuter, 2015). The policy makers and the companies must handle the
threats that are related to cyber space. The employee threat agent consists of contractors, staffs,
security guards and operational staffs of an organization they work in.
Mitigate the effect of threat agents:
To mitigate the effect of threat agents, threat defenders are appointed. This accidental
threat that happens due to clerical errors, slips that are skill based and the misconfiguration,
management of poor patch, using user names that are default and the passwords that are easy to
guess can be mitigated by the defenders of threat agents (Exchange, 2016). The mistakes that are
also based on knowledge which includes crashes and update of software, procedural flaws and
integration problems included accidental threats can also be mitigated by the threat defenders.
The Computer Associate and the other sources that provides security also finds out way to make
the APIs secure and also secure the social networks, photo sharing in mobile, video sharing, and
snapchat processes.
very low. They are unskilled and take help of script and programs to attack the server or some
system. For the purpose of hacking they mainly take help of some tools to make their attacks
more serious.
Online social hackers (hacktivists): The begun of hactivists mainly came in the year
2016. Their main motive is to protest some cause and also to make promotion of their cause. The
hacktivists mainly attacks on problems of public health, corporations, environmental policy,
military institutions and intelligence agencies.
Employees: The employees group of threat agents lies in the organizations itself. The analysis of
datasets that are large can undergo new signs of innovation and productivity and also unlocks the
values that ate significant (Reuter, 2015). The policy makers and the companies must handle the
threats that are related to cyber space. The employee threat agent consists of contractors, staffs,
security guards and operational staffs of an organization they work in.
Mitigate the effect of threat agents:
To mitigate the effect of threat agents, threat defenders are appointed. This accidental
threat that happens due to clerical errors, slips that are skill based and the misconfiguration,
management of poor patch, using user names that are default and the passwords that are easy to
guess can be mitigated by the defenders of threat agents (Exchange, 2016). The mistakes that are
also based on knowledge which includes crashes and update of software, procedural flaws and
integration problems included accidental threats can also be mitigated by the threat defenders.
The Computer Associate and the other sources that provides security also finds out way to make
the APIs secure and also secure the social networks, photo sharing in mobile, video sharing, and
snapchat processes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9ENISA BIG DATA INFRASTRUCTURE
Answer to Question 4:
To processes by which the European Threat Landscape can be improved are as follows:
The resource certification (RPKI) should be utilized to give the origin of AS a
validation (Catteddu & Hogben, 2015). The readers should be made aware of
what they are clicking to and what not to click. This decrease the possibility of
hacking.
Proper policy should be implemented to promote the rules of making the peering
secure. Such policies are known as Appropriate Use Policy (AUP).
Egress filtering should be done at the base of the router where all the signals
comes into so that the traffic can be controlled at the base itself. It the control is
done at the base, it can be stopped from expanding those to the systems of the
users or the clients.
The ETL should inform the organizations to take authorized users who know
about all the mitigation processes of the threats. There is also some work of the
registrants. They must keep their account details personal and they must not share
with anyone.
The DNS clients can be secured by deployment of DNSSEC which origins the
authentication of DNS of data, data integrity and existence denial that are
authenticated.
Good practices for the process of routing should cover all the aspects that are
related with technical staring from monitoring to filtering.
The process of ETL should promote to stop the use of domain names that are
taken randomly that are mainly not owned by the internal infrastructure. The top
Answer to Question 4:
To processes by which the European Threat Landscape can be improved are as follows:
The resource certification (RPKI) should be utilized to give the origin of AS a
validation (Catteddu & Hogben, 2015). The readers should be made aware of
what they are clicking to and what not to click. This decrease the possibility of
hacking.
Proper policy should be implemented to promote the rules of making the peering
secure. Such policies are known as Appropriate Use Policy (AUP).
Egress filtering should be done at the base of the router where all the signals
comes into so that the traffic can be controlled at the base itself. It the control is
done at the base, it can be stopped from expanding those to the systems of the
users or the clients.
The ETL should inform the organizations to take authorized users who know
about all the mitigation processes of the threats. There is also some work of the
registrants. They must keep their account details personal and they must not share
with anyone.
The DNS clients can be secured by deployment of DNSSEC which origins the
authentication of DNS of data, data integrity and existence denial that are
authenticated.
Good practices for the process of routing should cover all the aspects that are
related with technical staring from monitoring to filtering.
The process of ETL should promote to stop the use of domain names that are
taken randomly that are mainly not owned by the internal infrastructure. The top
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10ENISA BIG DATA INFRASTRUCTURE
level of domains should not be considered for domain name spaces that are
private.
Answer to Question 5:
The ENISA (European Union Agency for Network and Information Security) should
continue to improve the security processes that are related to the threat landscape of Europe.
Operators of DNS infrastructures are responsible to develop security rules that
administrators can apply to Internet infrastructure assets. However, humans are not immune to
mistakes. Moreover, the effect of certain technical security rule may differ depending on the
specificities of a given Internet infrastructure (Witt & Freudenberg, 2016). There is a drawback
in the system configuration the help in security policy. The ENISA also lacks behind the
administration that are identical in only one type of group of threat that is DNS and routing. This
leads to different outcomes. The gap also comes in operators of an organization. There is also a
drawback in the DNS spoofing of the threat landscape. The APIs should be made more secure
than that is present in the present protocol.
Conclusion
The security related to cyber space is known as Network and Information Security (NIS).
The NIS security is provided by the European Union Agency for Network and Information
Security (ENISA). The security of Network and Information Security is carried out that is related
to develop and promote the culture of security. To make Network and Information Security a
level up, the European Union Agency for Network and Information Security was set up in the
year 2004 in European Union. A developed process of Network and Information Security for the
level of domains should not be considered for domain name spaces that are
private.
Answer to Question 5:
The ENISA (European Union Agency for Network and Information Security) should
continue to improve the security processes that are related to the threat landscape of Europe.
Operators of DNS infrastructures are responsible to develop security rules that
administrators can apply to Internet infrastructure assets. However, humans are not immune to
mistakes. Moreover, the effect of certain technical security rule may differ depending on the
specificities of a given Internet infrastructure (Witt & Freudenberg, 2016). There is a drawback
in the system configuration the help in security policy. The ENISA also lacks behind the
administration that are identical in only one type of group of threat that is DNS and routing. This
leads to different outcomes. The gap also comes in operators of an organization. There is also a
drawback in the DNS spoofing of the threat landscape. The APIs should be made more secure
than that is present in the present protocol.
Conclusion
The security related to cyber space is known as Network and Information Security (NIS).
The NIS security is provided by the European Union Agency for Network and Information
Security (ENISA). The security of Network and Information Security is carried out that is related
to develop and promote the culture of security. To make Network and Information Security a
level up, the European Union Agency for Network and Information Security was set up in the
year 2004 in European Union. A developed process of Network and Information Security for the

11ENISA BIG DATA INFRASTRUCTURE
market to function properly European Union Agency for Network and Information Security was
implied.
A diagram is shown in this write up that shows the infrastructure of the ENISA
Landscape Threat. The case given describes all those cyber threats and the ways to solve them
are elaborately given in the European Union Agency for Network and Information Security case
study. The kill chain methods of all the threats are stated with diagram. There are almost five
group of threat including the unintentional damage, hijacking, eavesdropping and interception,
nefarious activity, legal threats and the organizational threats. Threats agents are discussed and
their relative good practices to mitigate threats are also detailed in the paper.
References
Bartsch, M., & Frey, S. (2017). State-of-the-art approaches. In cyber strategies for enterprises
and authorities (pp. 55-71). Springer Specialties Wiesbaden.
Bastl, M., Mareš, M., & Tvrdá, K. (2015). Cybersecurity policy at national, European and
international level: a framework analysis. In cyber security (pp. 45-67). Springer
Specialties Wiesbaden.
Bendiek, A. (2015, December). Digital Agenda and Cybersecurity. In the Yearbook of European
Integration 2015 (pp. 176-181). Nomos publishing company mbH & Co. KG.
Catteddu, D., & Hogben, G. (2015). Cloud computing. Benefits, Risks and Recommendations for
Information Security/European Network and Information Security Agency, ENISA
(November 2015).
Christou, G. (2017). The EU's Approach to Cybersecurity.
market to function properly European Union Agency for Network and Information Security was
implied.
A diagram is shown in this write up that shows the infrastructure of the ENISA
Landscape Threat. The case given describes all those cyber threats and the ways to solve them
are elaborately given in the European Union Agency for Network and Information Security case
study. The kill chain methods of all the threats are stated with diagram. There are almost five
group of threat including the unintentional damage, hijacking, eavesdropping and interception,
nefarious activity, legal threats and the organizational threats. Threats agents are discussed and
their relative good practices to mitigate threats are also detailed in the paper.
References
Bartsch, M., & Frey, S. (2017). State-of-the-art approaches. In cyber strategies for enterprises
and authorities (pp. 55-71). Springer Specialties Wiesbaden.
Bastl, M., Mareš, M., & Tvrdá, K. (2015). Cybersecurity policy at national, European and
international level: a framework analysis. In cyber security (pp. 45-67). Springer
Specialties Wiesbaden.
Bendiek, A. (2015, December). Digital Agenda and Cybersecurity. In the Yearbook of European
Integration 2015 (pp. 176-181). Nomos publishing company mbH & Co. KG.
Catteddu, D., & Hogben, G. (2015). Cloud computing. Benefits, Risks and Recommendations for
Information Security/European Network and Information Security Agency, ENISA
(November 2015).
Christou, G. (2017). The EU's Approach to Cybersecurity.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





