Analyzing ENISA's Big Data Threat Landscape and Mitigation Strategies
VerifiedAdded on 2020/02/24
|16
|3168
|61
Report
AI Summary
This report provides a comprehensive overview of the ENISA Big Data threat landscape, focusing on the key security challenges faced by organizations implementing analytics applications. It identifies top threats such as drive-by exploits, worms/Trojans, and code injection attacks, along with the threat agents including corporations, cybercriminals, employees, hacktivists, nation-states, and terrorists. The report also outlines best practices for mitigating these threats, including end-user perspectives, common terminology, and the use of case studies. Furthermore, it details methods to improve the ETL process, such as tackling bottlenecks, incremental data loading, partitioning large tables, and eliminating extraneous data. The report emphasizes the importance of data security in various sectors, including telecom, energy, and finance, highlighting the strategic plans of ENISA to combat data theft and misuse. The report also underscores the significance of protecting big data for economic growth, national security, and military applications.

ENISIA Big Data threat Land Scape
1
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Overview of the study................................................................................................................2
Top threats which have a high damaging effect in ENISA’s Big Data infrastructure...............4
Key threat agents identified by ENISA in Cyber space.............................................................6
Best practices to get rid of threat................................................................................................9
Should ENISA be satisfied with current state of IT security?.................................................11
Conclusion................................................................................................................................13
References................................................................................................................................14
2
Overview of the study................................................................................................................2
Top threats which have a high damaging effect in ENISA’s Big Data infrastructure...............4
Key threat agents identified by ENISA in Cyber space.............................................................6
Best practices to get rid of threat................................................................................................9
Should ENISA be satisfied with current state of IT security?.................................................11
Conclusion................................................................................................................................13
References................................................................................................................................14
2

Overview of the study
The main purpose of this study is to identify the key security challenges, which the
companies are facing while implementing Analytics application to infrastructures. How these
two are mitigated with each other. This data focuses mostly on the data security of the private
organizations it may be in the sectors of (Telecom, Energy, and Finance). However, more
organizations like public organizations, government agencies, and research centres are
considered as well. The main objective of ENISA is data security. They have formulated
certain strategic plan to stop the Data theft and misuse. There has been a significant threat in
Big Data. Here Big Data means a bunch of information which has a significant effect on
various aspects of society it ranges from food security, climate, and health, resource
efficiency to energy, smart cities and intelligent transport system. As per the consideration of
European Commission, they have acknowledged the fact of the impact of the data driven
economy in the years to come. This is only possible by figuring out the strategic plan of big
data.
As per the estimation, only the EU citizen can contribute to the data driven
technology worth €1 trillion annually by 2020”. Thus it can be easily proven that data plays a
very significant role in determining the economic strength of a country. Another most
important and vital reasons for protecting Big data is that it can be used for fighting terrorism,
and many other important military applications. In understanding the battle field situation and
other military aspects this data is of great use. So proper planning for protecting this data is of
high importance (Shao and Zhao, 2010). As per the current statistical data, Facebook is
considered to hold 300 Petabytes of both unstructured and structured data. Twitter has
currently decided to tap its own raw data using big data analytics. In the year of 2007 worlds
telecommunication system has to make usage of 65 Exabyte without any scope of declining.
Thus, with the increasing trend in technology and data advancement, there is an
urgent requirement to store this Big Data in a secured and safe manner. These are the key
points which have been highlighted in this report of ENISA.
Scope
This report considers the threat land scape for big data. This report gives an idea about the
Emerging and probable threat possibilities for Big data technologies through various
3
The main purpose of this study is to identify the key security challenges, which the
companies are facing while implementing Analytics application to infrastructures. How these
two are mitigated with each other. This data focuses mostly on the data security of the private
organizations it may be in the sectors of (Telecom, Energy, and Finance). However, more
organizations like public organizations, government agencies, and research centres are
considered as well. The main objective of ENISA is data security. They have formulated
certain strategic plan to stop the Data theft and misuse. There has been a significant threat in
Big Data. Here Big Data means a bunch of information which has a significant effect on
various aspects of society it ranges from food security, climate, and health, resource
efficiency to energy, smart cities and intelligent transport system. As per the consideration of
European Commission, they have acknowledged the fact of the impact of the data driven
economy in the years to come. This is only possible by figuring out the strategic plan of big
data.
As per the estimation, only the EU citizen can contribute to the data driven
technology worth €1 trillion annually by 2020”. Thus it can be easily proven that data plays a
very significant role in determining the economic strength of a country. Another most
important and vital reasons for protecting Big data is that it can be used for fighting terrorism,
and many other important military applications. In understanding the battle field situation and
other military aspects this data is of great use. So proper planning for protecting this data is of
high importance (Shao and Zhao, 2010). As per the current statistical data, Facebook is
considered to hold 300 Petabytes of both unstructured and structured data. Twitter has
currently decided to tap its own raw data using big data analytics. In the year of 2007 worlds
telecommunication system has to make usage of 65 Exabyte without any scope of declining.
Thus, with the increasing trend in technology and data advancement, there is an
urgent requirement to store this Big Data in a secured and safe manner. These are the key
points which have been highlighted in this report of ENISA.
Scope
This report considers the threat land scape for big data. This report gives an idea about the
Emerging and probable threat possibilities for Big data technologies through various
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

illustrations and definitions (Lee and Kang, 2015). The main focus is to protect the assets,
from various threats and to implement prominent controlling measures to safe guard the Big
Data systems in the world.
Target audience:-
This report is basically helpful for big data operators and data providers as they can use this
information for their Risk assessment and Risk management analysis as per their specific
needs while drafting SLAs for their Big Data consumers. To prevent the Cyber threat analysis
using RA/ RM technique, this report can prove to be very useful and authenticated source for
their detailed analysis to cope up with big data security issue.
Figure 1: ENISA Big Data Infrastructure diagram
Source: (Everett, 2015)
4
from various threats and to implement prominent controlling measures to safe guard the Big
Data systems in the world.
Target audience:-
This report is basically helpful for big data operators and data providers as they can use this
information for their Risk assessment and Risk management analysis as per their specific
needs while drafting SLAs for their Big Data consumers. To prevent the Cyber threat analysis
using RA/ RM technique, this report can prove to be very useful and authenticated source for
their detailed analysis to cope up with big data security issue.
Figure 1: ENISA Big Data Infrastructure diagram
Source: (Everett, 2015)
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Top threats which have a high damaging effect in ENISA’s Big Data infrastructure
There are several data threats which are highlighted in this report like Threat due to
information leakage or sharing due to human error, Leaks of Data via web application
(unsecured API's), Inadequate design and planning or incorrect adaptation, Interception of
Information, Threat due to identity fraud, Denial of service, Malicious code or software or
activity, Generation or use of rogue certificate, and misuse of audit tools. In the report these
are some of the threat issues are discussed but the most damaging and harmful threats are as
follows:-
Drive by exploits
The most dangerous threat which is showing its growing trend is drive by exploits and the
injection of the malicious code in the HTML code as it exploits the vulnerabilities of the web
users due to the exploitation of legitimate compromised website creation. This types of
attacks are been detected on several occasions when the victims are infected visiting a drive
by download website, While downloading adobe reader or Adobe flash, and attackers mainly
exploit during the browser plug-in in Java (Lee and Kang, 2015). Some interesting mobile
platforms also some times are responsible for attacking the defence wall of big data security.
In the year May 2012 this type of attacks are first observed in first drive download for
Android OS. This type of technique is basically adopted by the cyber criminals. In some
recent events, it has been demonstrated in a seminar that the use of targeted attacks for cyber
espionage.
Worms / Trojans:-
The effect of this malware is very versatile and dreaded in nature. In most of the time, it was
found that they are used by the cyber criminals and government for various purposes such as
offensive attacks. Cyber Espionage is used for sophisticated cyber scams. For performing
bank frauds cybercrime is extensively responsible for these attacks. Sometimes mobile
platforms and social networking sites are used and exploited to spread large scale, malicious
agents. In a report, this has been proved that Data theft Trojans are widely used by cyber
criminals for making money (Richins, Stratopoulos and Wong, 2016). Trojan Auto run and
Cockficker worm are still considered as one of the most dangerous malware worldwide. They
are basically four years old still their effect is vicious in modern Data exchange system.
5
There are several data threats which are highlighted in this report like Threat due to
information leakage or sharing due to human error, Leaks of Data via web application
(unsecured API's), Inadequate design and planning or incorrect adaptation, Interception of
Information, Threat due to identity fraud, Denial of service, Malicious code or software or
activity, Generation or use of rogue certificate, and misuse of audit tools. In the report these
are some of the threat issues are discussed but the most damaging and harmful threats are as
follows:-
Drive by exploits
The most dangerous threat which is showing its growing trend is drive by exploits and the
injection of the malicious code in the HTML code as it exploits the vulnerabilities of the web
users due to the exploitation of legitimate compromised website creation. This types of
attacks are been detected on several occasions when the victims are infected visiting a drive
by download website, While downloading adobe reader or Adobe flash, and attackers mainly
exploit during the browser plug-in in Java (Lee and Kang, 2015). Some interesting mobile
platforms also some times are responsible for attacking the defence wall of big data security.
In the year May 2012 this type of attacks are first observed in first drive download for
Android OS. This type of technique is basically adopted by the cyber criminals. In some
recent events, it has been demonstrated in a seminar that the use of targeted attacks for cyber
espionage.
Worms / Trojans:-
The effect of this malware is very versatile and dreaded in nature. In most of the time, it was
found that they are used by the cyber criminals and government for various purposes such as
offensive attacks. Cyber Espionage is used for sophisticated cyber scams. For performing
bank frauds cybercrime is extensively responsible for these attacks. Sometimes mobile
platforms and social networking sites are used and exploited to spread large scale, malicious
agents. In a report, this has been proved that Data theft Trojans are widely used by cyber
criminals for making money (Richins, Stratopoulos and Wong, 2016). Trojan Auto run and
Cockficker worm are still considered as one of the most dangerous malware worldwide. They
are basically four years old still their effect is vicious in modern Data exchange system.
5
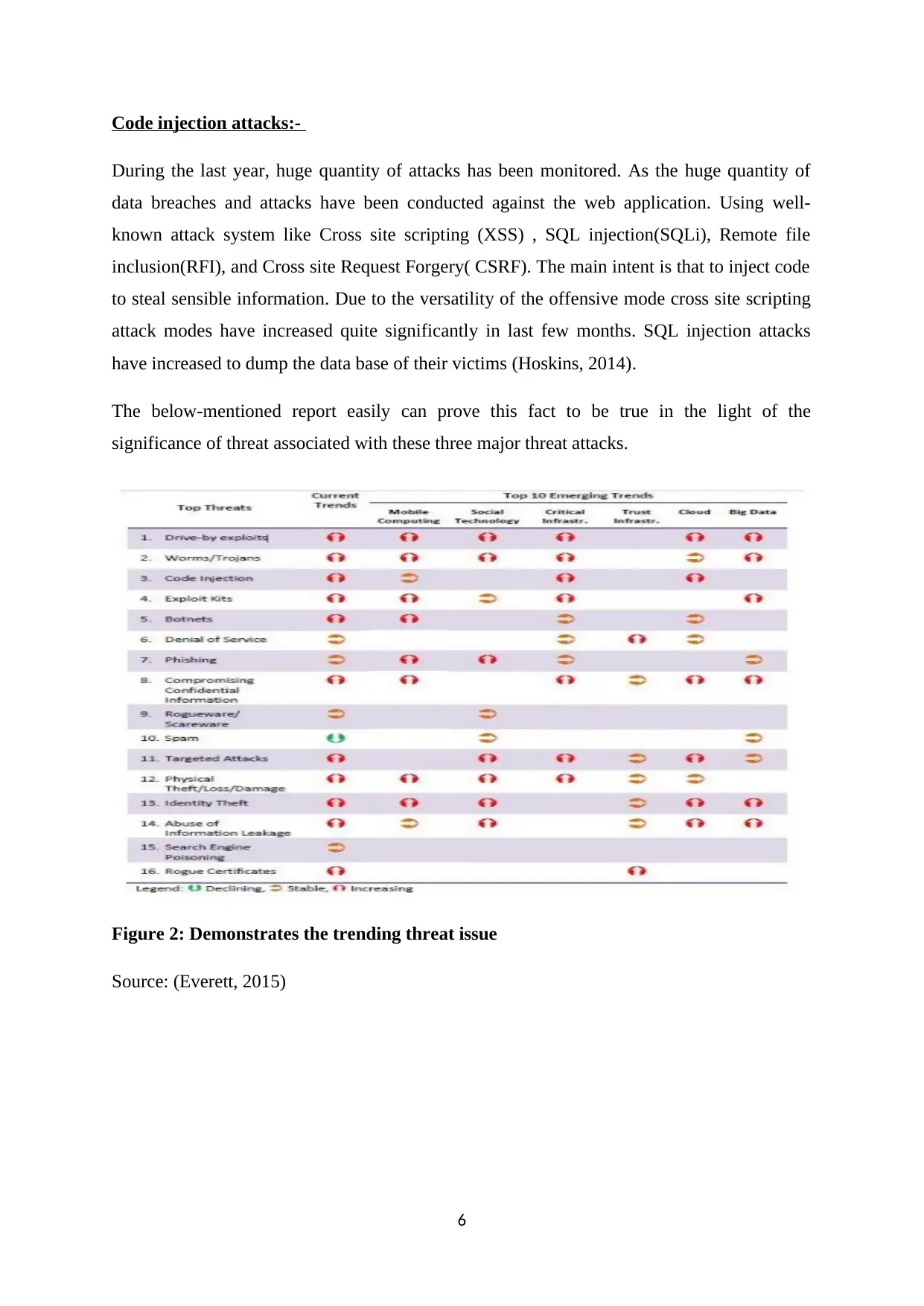
Code injection attacks:-
During the last year, huge quantity of attacks has been monitored. As the huge quantity of
data breaches and attacks have been conducted against the web application. Using well-
known attack system like Cross site scripting (XSS) , SQL injection(SQLi), Remote file
inclusion(RFI), and Cross site Request Forgery( CSRF). The main intent is that to inject code
to steal sensible information. Due to the versatility of the offensive mode cross site scripting
attack modes have increased quite significantly in last few months. SQL injection attacks
have increased to dump the data base of their victims (Hoskins, 2014).
The below-mentioned report easily can prove this fact to be true in the light of the
significance of threat associated with these three major threat attacks.
Figure 2: Demonstrates the trending threat issue
Source: (Everett, 2015)
6
During the last year, huge quantity of attacks has been monitored. As the huge quantity of
data breaches and attacks have been conducted against the web application. Using well-
known attack system like Cross site scripting (XSS) , SQL injection(SQLi), Remote file
inclusion(RFI), and Cross site Request Forgery( CSRF). The main intent is that to inject code
to steal sensible information. Due to the versatility of the offensive mode cross site scripting
attack modes have increased quite significantly in last few months. SQL injection attacks
have increased to dump the data base of their victims (Hoskins, 2014).
The below-mentioned report easily can prove this fact to be true in the light of the
significance of threat associated with these three major threat attacks.
Figure 2: Demonstrates the trending threat issue
Source: (Everett, 2015)
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Key threat agents identified by ENISA in Cyber space
Corporation:-
Corporations are considered as one of the most hostile threat agents. They can be in the form
of organizations enterprises that adopts various offensive tactics. This is done by the
corporations to outsmart its competitors. They target their competitors to gain a competitive
advantage over its competitors (Catlett and Ghani, 2015). On the basis of size, sectors and
corporations they usually possess capabilities which may range from human engineering
intelligence to technology especially depending on the field of their expertise.
Cyber criminals:-
They are considered to be the most hostile agents against data security. As their main motive
is high financial gain, the skill levels on their counter parts are also very high nowadays.
These cyber criminals are spread over the entire world. They may be organized in local,
national, and at international levels. A certain level of organized networking among these
cyber criminals is maintained all around the globe from where they operate their function.
Employees:-
This category actually refers to the company staffs they may be operational staff, contractors,
and security guard of the company (Zhang et al., 2017). As they possess the insider access of
the company's data information so they can be considered as both hostile as well as non-
hostile agents of cybercrime. This kind of agents has sound knowledge which helps them to
place an effective attack on the assets of the organizations.
Hacktivists:-
They are the new trends in the threat agents that are socially and politically motivated
individuals who try to promote their cause using the computer system to raise their protest.
They usually target high profile intelligence agencies, websites, corporations and military
institutions.
Nation States:-
They have offensive cyber capabilities which they can use as an adversary. By means of their
disposal and nature, they may pose a huge threat in the cyber war fare.
7
Corporation:-
Corporations are considered as one of the most hostile threat agents. They can be in the form
of organizations enterprises that adopts various offensive tactics. This is done by the
corporations to outsmart its competitors. They target their competitors to gain a competitive
advantage over its competitors (Catlett and Ghani, 2015). On the basis of size, sectors and
corporations they usually possess capabilities which may range from human engineering
intelligence to technology especially depending on the field of their expertise.
Cyber criminals:-
They are considered to be the most hostile agents against data security. As their main motive
is high financial gain, the skill levels on their counter parts are also very high nowadays.
These cyber criminals are spread over the entire world. They may be organized in local,
national, and at international levels. A certain level of organized networking among these
cyber criminals is maintained all around the globe from where they operate their function.
Employees:-
This category actually refers to the company staffs they may be operational staff, contractors,
and security guard of the company (Zhang et al., 2017). As they possess the insider access of
the company's data information so they can be considered as both hostile as well as non-
hostile agents of cybercrime. This kind of agents has sound knowledge which helps them to
place an effective attack on the assets of the organizations.
Hacktivists:-
They are the new trends in the threat agents that are socially and politically motivated
individuals who try to promote their cause using the computer system to raise their protest.
They usually target high profile intelligence agencies, websites, corporations and military
institutions.
Nation States:-
They have offensive cyber capabilities which they can use as an adversary. By means of their
disposal and nature, they may pose a huge threat in the cyber war fare.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
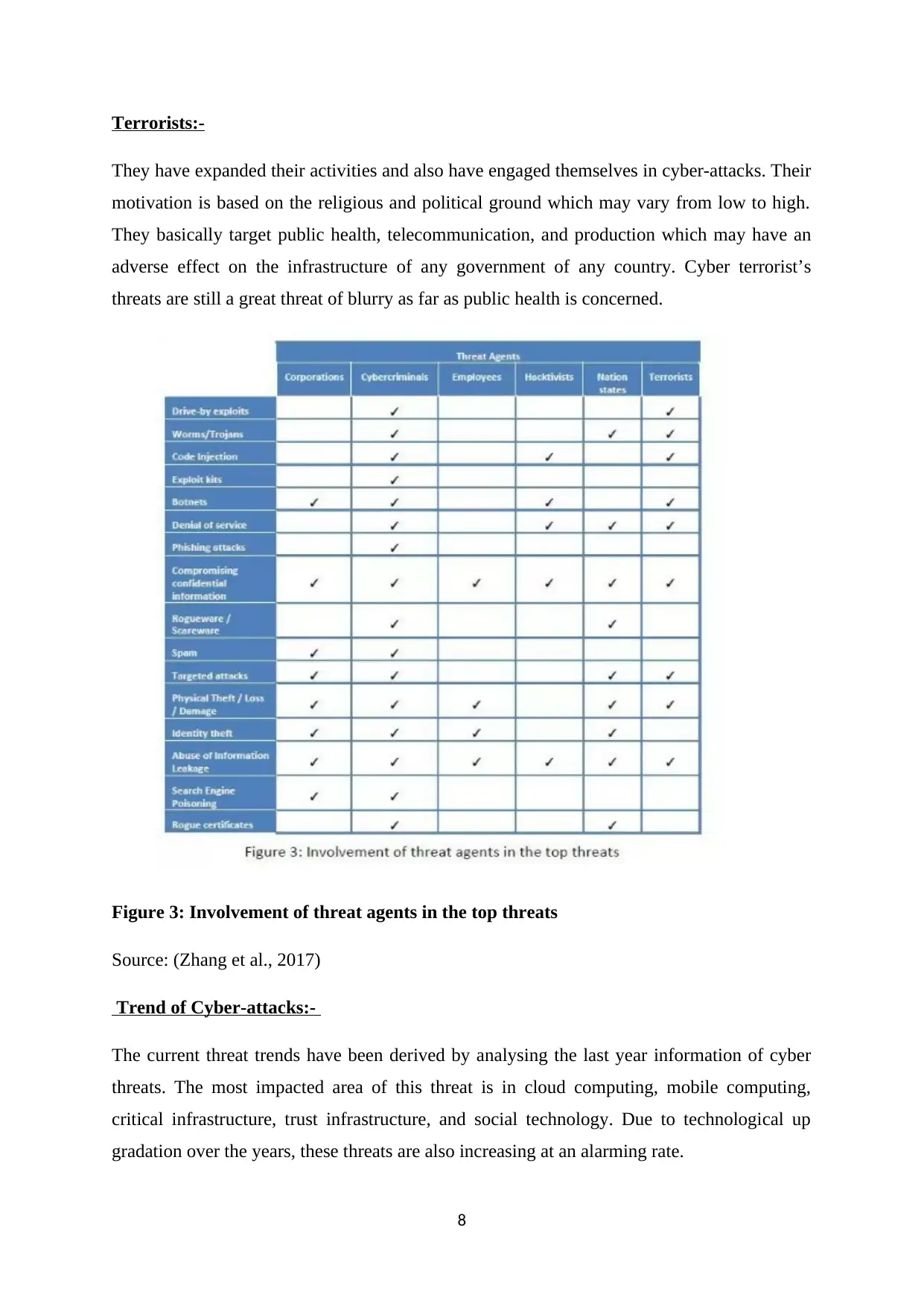
Terrorists:-
They have expanded their activities and also have engaged themselves in cyber-attacks. Their
motivation is based on the religious and political ground which may vary from low to high.
They basically target public health, telecommunication, and production which may have an
adverse effect on the infrastructure of any government of any country. Cyber terrorist’s
threats are still a great threat of blurry as far as public health is concerned.
Figure 3: Involvement of threat agents in the top threats
Source: (Zhang et al., 2017)
Trend of Cyber-attacks:-
The current threat trends have been derived by analysing the last year information of cyber
threats. The most impacted area of this threat is in cloud computing, mobile computing,
critical infrastructure, trust infrastructure, and social technology. Due to technological up
gradation over the years, these threats are also increasing at an alarming rate.
8
They have expanded their activities and also have engaged themselves in cyber-attacks. Their
motivation is based on the religious and political ground which may vary from low to high.
They basically target public health, telecommunication, and production which may have an
adverse effect on the infrastructure of any government of any country. Cyber terrorist’s
threats are still a great threat of blurry as far as public health is concerned.
Figure 3: Involvement of threat agents in the top threats
Source: (Zhang et al., 2017)
Trend of Cyber-attacks:-
The current threat trends have been derived by analysing the last year information of cyber
threats. The most impacted area of this threat is in cloud computing, mobile computing,
critical infrastructure, trust infrastructure, and social technology. Due to technological up
gradation over the years, these threats are also increasing at an alarming rate.
8
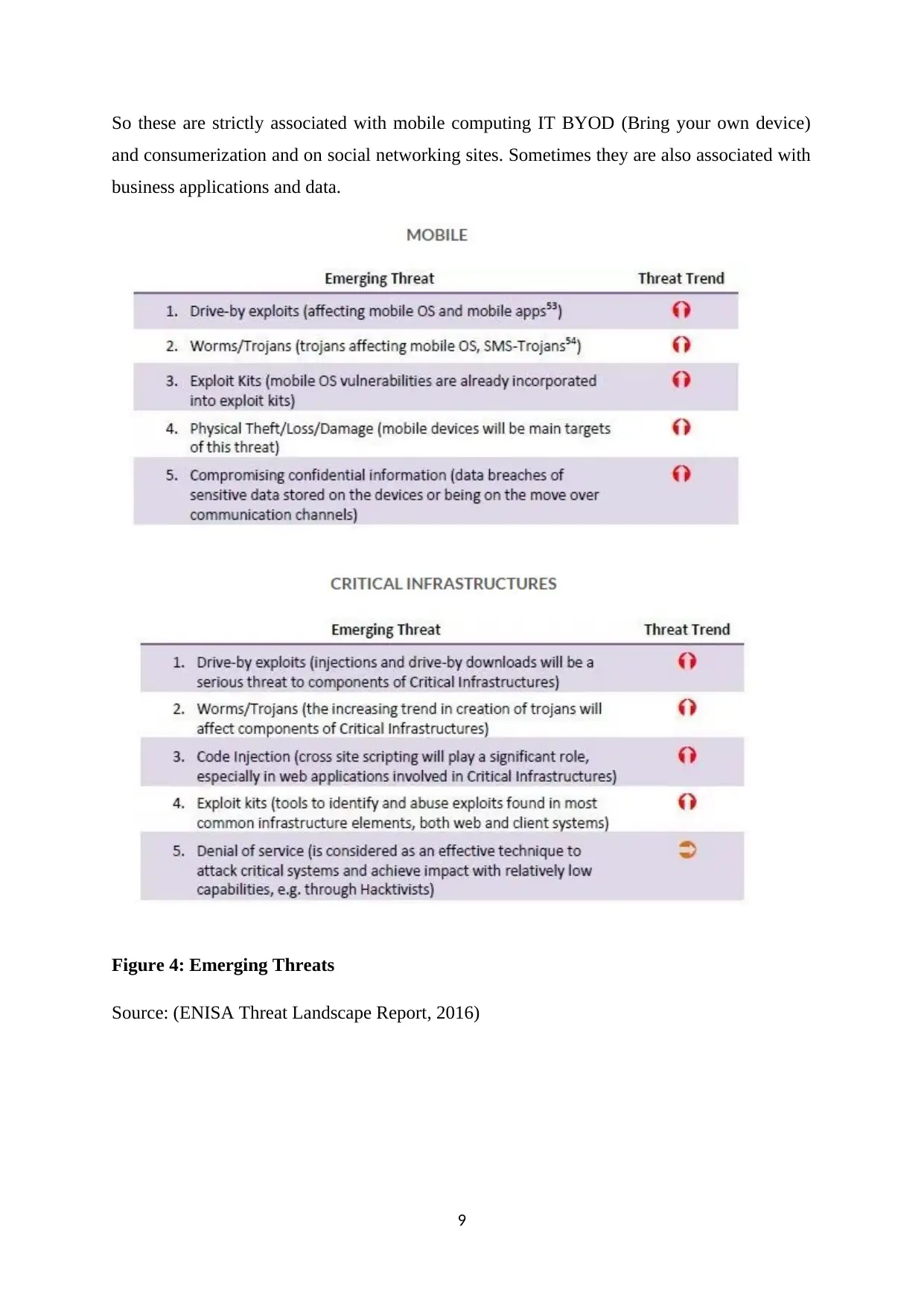
So these are strictly associated with mobile computing IT BYOD (Bring your own device)
and consumerization and on social networking sites. Sometimes they are also associated with
business applications and data.
Figure 4: Emerging Threats
Source: (ENISA Threat Landscape Report, 2016)
9
and consumerization and on social networking sites. Sometimes they are also associated with
business applications and data.
Figure 4: Emerging Threats
Source: (ENISA Threat Landscape Report, 2016)
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Best practices to get rid of threat
ENISA has proposed to follow certain best practices to avoid cyber threats:-
The Inclusion of end user perspective.
Within threat reports use of common terminology.
For threat, land scape develops use cases.
Maintain and collect more qualitative information about threat agents.
Collect and develop better evidence on the impact reached by the attackers.
Accommodate shift in security controls on emerging data threats.
Methods to improve ETL process:-
There are several methods which can be implemented to improve the ETL
Tackle bottle necks:-
Check how many resources each part of the process takes and address the heaviest one.
Make sure your log metrics such as time, number of records processed, and hardware usage.
It will be a second part, building facts and dimensions in the staging environment. Wherever
your bottleneck may be, take a deep breath and dive into the code.
Load Data Incrementally:-
Making the changes between the previous and the new data saves a lot of time as compared
to a full load. It’s more difficult to implement and maintain loaded data. As it is difficult it
doesn’t mean impossible (Big Data Threat Landscape and Good Practice Guide, 2016). So,
loading incrementally can definitely improve the ETL performance.
Partition of Large tables:-
If relational databases are used and there is need to improve the data processing window, the
partition of large tables can sort out the problem. It means, cutting big tables down to
physically smaller ones, probably by date (Big Data Threat Landscape and Good Practice
Guide, 2016). Each and Every partition has its own indices and the indices tree is shallower
which allows for quicker access to the data. It also allows ensures switching of data in and
out of a table for a quick Meta data operation instead of being actual insertion or deletion of
data records.
10
ENISA has proposed to follow certain best practices to avoid cyber threats:-
The Inclusion of end user perspective.
Within threat reports use of common terminology.
For threat, land scape develops use cases.
Maintain and collect more qualitative information about threat agents.
Collect and develop better evidence on the impact reached by the attackers.
Accommodate shift in security controls on emerging data threats.
Methods to improve ETL process:-
There are several methods which can be implemented to improve the ETL
Tackle bottle necks:-
Check how many resources each part of the process takes and address the heaviest one.
Make sure your log metrics such as time, number of records processed, and hardware usage.
It will be a second part, building facts and dimensions in the staging environment. Wherever
your bottleneck may be, take a deep breath and dive into the code.
Load Data Incrementally:-
Making the changes between the previous and the new data saves a lot of time as compared
to a full load. It’s more difficult to implement and maintain loaded data. As it is difficult it
doesn’t mean impossible (Big Data Threat Landscape and Good Practice Guide, 2016). So,
loading incrementally can definitely improve the ETL performance.
Partition of Large tables:-
If relational databases are used and there is need to improve the data processing window, the
partition of large tables can sort out the problem. It means, cutting big tables down to
physically smaller ones, probably by date (Big Data Threat Landscape and Good Practice
Guide, 2016). Each and Every partition has its own indices and the indices tree is shallower
which allows for quicker access to the data. It also allows ensures switching of data in and
out of a table for a quick Meta data operation instead of being actual insertion or deletion of
data records.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cut out of extraneous data:-
It’s very important to collect as much data as possible, but not all of it is not worthy enough
to gain entry into the data warehouse. As for example, images of furniture models are useless
to BI analysts. If there is need to improve the ETL performance, then define exactly which
data should be processed and leave irrelevant rows/columns out. It is better to start small and
grow as you go as opposed to creating a giant data monster (Big Data Threat Landscape and
Good Practice Guide, 2016).
Cache the data:-
As memory access performs faster than hard drives so catching the data can surely speed up
the things. This can help to perform the task faster than to hard drives. As catching is present
in a very limited by the maximum amount of memory the hard ware can support. Huge big
data s may not be fitted in it properly.
Use of Hadoop:-
For distribution and processing of large data over a cluster of machines, Apahe Hadoop is
designed. Actually, it uses HDFS which is considered as a dedicated file system which has a
speciality to cut data into small chunks and to spread them over the cluster (Big Data Threat
Landscape and Good Practice Guide, 2016). Duplicate copies are kept into the system to
maintain the integrity of the machine automatically.
So these are the above methods which can reduce the chances of data theft and improves ETL
process.
11
It’s very important to collect as much data as possible, but not all of it is not worthy enough
to gain entry into the data warehouse. As for example, images of furniture models are useless
to BI analysts. If there is need to improve the ETL performance, then define exactly which
data should be processed and leave irrelevant rows/columns out. It is better to start small and
grow as you go as opposed to creating a giant data monster (Big Data Threat Landscape and
Good Practice Guide, 2016).
Cache the data:-
As memory access performs faster than hard drives so catching the data can surely speed up
the things. This can help to perform the task faster than to hard drives. As catching is present
in a very limited by the maximum amount of memory the hard ware can support. Huge big
data s may not be fitted in it properly.
Use of Hadoop:-
For distribution and processing of large data over a cluster of machines, Apahe Hadoop is
designed. Actually, it uses HDFS which is considered as a dedicated file system which has a
speciality to cut data into small chunks and to spread them over the cluster (Big Data Threat
Landscape and Good Practice Guide, 2016). Duplicate copies are kept into the system to
maintain the integrity of the machine automatically.
So these are the above methods which can reduce the chances of data theft and improves ETL
process.
11

Should ENISA be satisfied with current state of IT security?
Unfortunately, the answer is no, as cybercrime is increasing at an alarming rate so it becomes
the responsibility to stop this threat issues by formulating certain strategies to avoid such a
huge amount of data theft. That is the reason why ENISA has formulated certain strategies to
control this threat factors in Cyber security issue. The strategic objectives of ENISA are
governed by the rules and regulation of ENISA valuable inputs from the member states and
relevant communities including the private sectors:-
#Expertise:-
ENISA possess a team of experts who can handle this grave IT security issue very easily. So
it becomes the duty of ENISA to anticipate and support European nation and the world at a
large to cope up with this challenge of information Security by collating analysing available
information and Key NIS issues which are cropping up day after day due to the evolution of
digital environment.
#Policy:-
Maintaining the guidelines of EU it should promote the network and information security by
assisting European Union institution and member states for developing and implementing EU
policies and law related to NIS.
#Capacity:-
Another most important relevant duty of ENISA is that to increase the capacity of the
European Union and its member states to fight against data threat issues (Big Data Threat
Landscape and Good Practice Guide, 2016). It is possible when ENISA reinforces NIS
capacities in maintaining art network and information security capacities by member states.
# Community:-
In the EU community among the member states, ENISA spreads awareness about the Data
threat issues along with its remedies to combat the unforeseen situation of the member
countries and to stop the alarming increase of Big Data problem.
# Enabling:-
12
Unfortunately, the answer is no, as cybercrime is increasing at an alarming rate so it becomes
the responsibility to stop this threat issues by formulating certain strategies to avoid such a
huge amount of data theft. That is the reason why ENISA has formulated certain strategies to
control this threat factors in Cyber security issue. The strategic objectives of ENISA are
governed by the rules and regulation of ENISA valuable inputs from the member states and
relevant communities including the private sectors:-
#Expertise:-
ENISA possess a team of experts who can handle this grave IT security issue very easily. So
it becomes the duty of ENISA to anticipate and support European nation and the world at a
large to cope up with this challenge of information Security by collating analysing available
information and Key NIS issues which are cropping up day after day due to the evolution of
digital environment.
#Policy:-
Maintaining the guidelines of EU it should promote the network and information security by
assisting European Union institution and member states for developing and implementing EU
policies and law related to NIS.
#Capacity:-
Another most important relevant duty of ENISA is that to increase the capacity of the
European Union and its member states to fight against data threat issues (Big Data Threat
Landscape and Good Practice Guide, 2016). It is possible when ENISA reinforces NIS
capacities in maintaining art network and information security capacities by member states.
# Community:-
In the EU community among the member states, ENISA spreads awareness about the Data
threat issues along with its remedies to combat the unforeseen situation of the member
countries and to stop the alarming increase of Big Data problem.
# Enabling:-
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





