Comprehensive Analysis of ENISA Big Data Security Report
VerifiedAdded on 2019/11/20
|12
|3085
|203
Report
AI Summary
This report provides a detailed analysis of the European Union Agency for Network and Information Security (ENISA) Big Data security. It examines the ENISA Technology Landscape (ETL) and the associated threats, including eavesdropping, nefarious activity, unintentional data loss, organizational skill shortages, and legal issues. The report outlines the ENISA Big Data security infrastructure, including data sources, integration processes, storage, analytics, and presentation. It identifies key threat agents like cybercriminals, online social hackers, nation-states, employees, cyber terrorists, and script kiddies, and suggests measures to minimize their impact. The report also assesses trends in threat probability, focusing on high-probability threats such as denial-of-service, ransomware, phishing, and spam, as well as medium and low probability threats. Furthermore, the report recommends improvements in ETL processes, emphasizing the importance of encryption, advanced algorithms, and comprehensive security controls to enhance the overall security architecture. The analysis highlights the importance of training, administrative controls, and legal frameworks to mitigate risks and protect sensitive information within the ENISA framework.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ENISA Big Data Security
Overview of Case Study..............................................................................................................................3
ENISA Big Data Security Infrastructure Diagram.......................................................................................3
Top Threats & Most Significant Threat.......................................................................................................4
Threat Agents & Steps to Minimize their Impact........................................................................................5
Trends in Threat Probability........................................................................................................................9
Improvements in ETL Processes...............................................................................................................10
Challenging Threats for ENISA............................................................................................................10
Current IT Security State of ENISA – Recommendations & Conclusion..................................................11
References.................................................................................................................................................12
2
Overview of Case Study..............................................................................................................................3
ENISA Big Data Security Infrastructure Diagram.......................................................................................3
Top Threats & Most Significant Threat.......................................................................................................4
Threat Agents & Steps to Minimize their Impact........................................................................................5
Trends in Threat Probability........................................................................................................................9
Improvements in ETL Processes...............................................................................................................10
Challenging Threats for ENISA............................................................................................................10
Current IT Security State of ENISA – Recommendations & Conclusion..................................................11
References.................................................................................................................................................12
2

ENISA Big Data Security
Overview of Case Study
ENISA is an abbreviation for European Union Agency for Network and Information Security. It
is a centre that has been set up for the maintenance and improvement of the information and
network security across Europe. A case study has been covered on the Big Data threats that are
associated with ENISA and an ENISA Technology Landscape (ETL) was published discussing
the same in the year 2016. Big Data is a term that refers to the huge volumes of structured, semi-
structured and unstructured data that may comprise of data of different data types. There are
many threats that have been discussed in the case study that are associated with Big Data. The
threats that have been described in the case study mainly include the
eavesdropping/interception/hijacking threats, nefarious activity/abuse, unintentional loss and
damage of IT assets and information, organizational threats due to skill shortage and legal threats
(Enisa, 2016).
The case study is spread across seven sections and there are sub-sections and appendices that are
also included. Section one provides an introduction to the case study covering the policy context,
scope, target audience, methodology and structure of the document. It is followed by the
discussion of Big Data environments and assets in sections two and three respectively. Big Data
threats and threat agents have been illustrated in section four and five followed by good practices
and gap analysis in sections six and seven.
ENISA Big Data Security Infrastructure Diagram
There are a lot of elements that are involved in the Big Data architecture. These elements include
the data sources, integration process, data storage, analytics and computing models along with
the presentation. All of these elements further include various components and entities. Due to
the involvement of so many entities and the requirement to manage huge clusters of data sets,
there are various risks that are associated with ENISA Big Data.
There may be security risks and attacks in the form of eavesdropping attacks, malware attacks,
information breaches, loss and leakage. These may result in legal obligations as well. There may
also be organizational issues that may result in compromise of security.
3
Overview of Case Study
ENISA is an abbreviation for European Union Agency for Network and Information Security. It
is a centre that has been set up for the maintenance and improvement of the information and
network security across Europe. A case study has been covered on the Big Data threats that are
associated with ENISA and an ENISA Technology Landscape (ETL) was published discussing
the same in the year 2016. Big Data is a term that refers to the huge volumes of structured, semi-
structured and unstructured data that may comprise of data of different data types. There are
many threats that have been discussed in the case study that are associated with Big Data. The
threats that have been described in the case study mainly include the
eavesdropping/interception/hijacking threats, nefarious activity/abuse, unintentional loss and
damage of IT assets and information, organizational threats due to skill shortage and legal threats
(Enisa, 2016).
The case study is spread across seven sections and there are sub-sections and appendices that are
also included. Section one provides an introduction to the case study covering the policy context,
scope, target audience, methodology and structure of the document. It is followed by the
discussion of Big Data environments and assets in sections two and three respectively. Big Data
threats and threat agents have been illustrated in section four and five followed by good practices
and gap analysis in sections six and seven.
ENISA Big Data Security Infrastructure Diagram
There are a lot of elements that are involved in the Big Data architecture. These elements include
the data sources, integration process, data storage, analytics and computing models along with
the presentation. All of these elements further include various components and entities. Due to
the involvement of so many entities and the requirement to manage huge clusters of data sets,
there are various risks that are associated with ENISA Big Data.
There may be security risks and attacks in the form of eavesdropping attacks, malware attacks,
information breaches, loss and leakage. These may result in legal obligations as well. There may
also be organizational issues that may result in compromise of security.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
ENISA Big Data Security
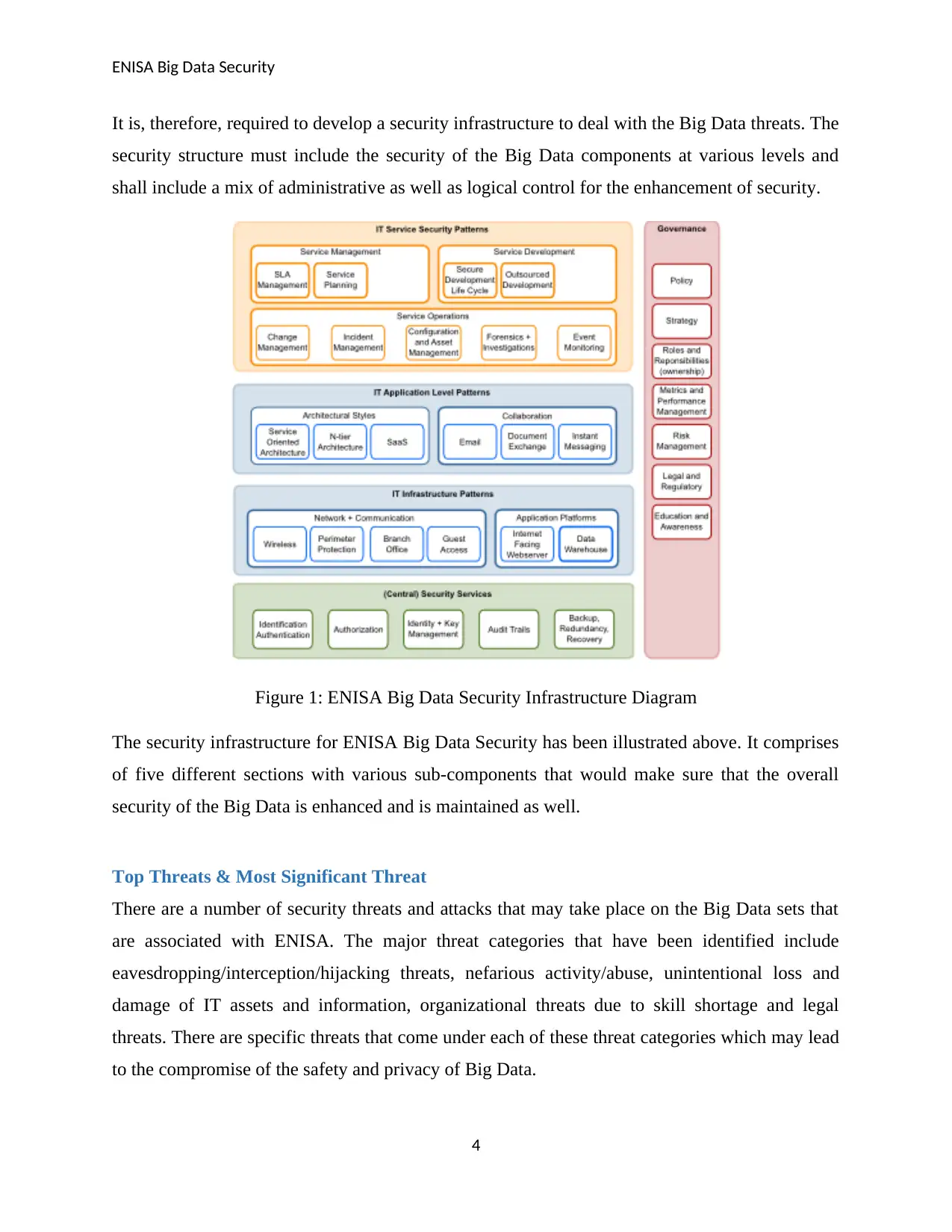
It is, therefore, required to develop a security infrastructure to deal with the Big Data threats. The
security structure must include the security of the Big Data components at various levels and
shall include a mix of administrative as well as logical control for the enhancement of security.
Figure 1: ENISA Big Data Security Infrastructure Diagram
The security infrastructure for ENISA Big Data Security has been illustrated above. It comprises
of five different sections with various sub-components that would make sure that the overall
security of the Big Data is enhanced and is maintained as well.
Top Threats & Most Significant Threat
There are a number of security threats and attacks that may take place on the Big Data sets that
are associated with ENISA. The major threat categories that have been identified include
eavesdropping/interception/hijacking threats, nefarious activity/abuse, unintentional loss and
damage of IT assets and information, organizational threats due to skill shortage and legal
threats. There are specific threats that come under each of these threat categories which may lead
to the compromise of the safety and privacy of Big Data.
4
It is, therefore, required to develop a security infrastructure to deal with the Big Data threats. The
security structure must include the security of the Big Data components at various levels and
shall include a mix of administrative as well as logical control for the enhancement of security.
Figure 1: ENISA Big Data Security Infrastructure Diagram
The security infrastructure for ENISA Big Data Security has been illustrated above. It comprises
of five different sections with various sub-components that would make sure that the overall
security of the Big Data is enhanced and is maintained as well.
Top Threats & Most Significant Threat
There are a number of security threats and attacks that may take place on the Big Data sets that
are associated with ENISA. The major threat categories that have been identified include
eavesdropping/interception/hijacking threats, nefarious activity/abuse, unintentional loss and
damage of IT assets and information, organizational threats due to skill shortage and legal
threats. There are specific threats that come under each of these threat categories which may lead
to the compromise of the safety and privacy of Big Data.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ENISA Big Data Security
Out of the various threats that have been identified in association with Big Data, the most
significant threat category is the unintentional damage/loss of IT information or IT assets. This is
due to the reason that there are a lot many causes and reasons that are associated with this
particular form of security attack. The loss of information in the cloud is one of the most
significant threats with high probability. There are a lot many different agencies, units and
organizations that come under ENISA. Each of these entities makes use of cloud for information
storage and management. There are also a lot many business activities, services and operations
that are carried out using the cloud computing services. Due to the varied nature of operations
and the enhanced number of operators, the information and data may get loss or may get leaked
in the cloud environment. This may be unintentional in most of the cases due to a technical or an
operational fault. However, it may possess a lot of danger to the privacy of the information on
the cloud (Ko & Dorantes, 2016).
There can be varied data sets of huge volumes that may be available on the cloud. These data
sets may comprise of the information that may be public, private, sensitive, confidential or
critical in nature. The properties of information such as its privacy, availability, integrity and
confidentiality may get violated due to the loss of information in the cloud. The data leaks may
have an impact on the associated IT assets as well. There have been a number of such cases that
have been reported in the past and there are measures that have been taken to put a check on the
same. However, the occurrence of these risks and threats are still continuing which may cause a
lot of trouble for the entities that come under ENISA (Amato, 2016).
Threat Agents & Steps to Minimize their Impact
The threats that have been identified in association with Big Data involve a lot many threat
agents. These agents are the carriers of threats that assist in shaping and execution of the threat.
Cyber Criminals: These are the categories of threat agents that give shape to the nefarious
activities in the cyber space and they have a selfish motive associated with the attacks.
The attacks that are performed by these agents are deliberate and intentional in nature so
that they may gain benefits as a result. There may be legal actions that may be taken if
the attacks are reported and these criminals are identified.
5
Out of the various threats that have been identified in association with Big Data, the most
significant threat category is the unintentional damage/loss of IT information or IT assets. This is
due to the reason that there are a lot many causes and reasons that are associated with this
particular form of security attack. The loss of information in the cloud is one of the most
significant threats with high probability. There are a lot many different agencies, units and
organizations that come under ENISA. Each of these entities makes use of cloud for information
storage and management. There are also a lot many business activities, services and operations
that are carried out using the cloud computing services. Due to the varied nature of operations
and the enhanced number of operators, the information and data may get loss or may get leaked
in the cloud environment. This may be unintentional in most of the cases due to a technical or an
operational fault. However, it may possess a lot of danger to the privacy of the information on
the cloud (Ko & Dorantes, 2016).
There can be varied data sets of huge volumes that may be available on the cloud. These data
sets may comprise of the information that may be public, private, sensitive, confidential or
critical in nature. The properties of information such as its privacy, availability, integrity and
confidentiality may get violated due to the loss of information in the cloud. The data leaks may
have an impact on the associated IT assets as well. There have been a number of such cases that
have been reported in the past and there are measures that have been taken to put a check on the
same. However, the occurrence of these risks and threats are still continuing which may cause a
lot of trouble for the entities that come under ENISA (Amato, 2016).
Threat Agents & Steps to Minimize their Impact
The threats that have been identified in association with Big Data involve a lot many threat
agents. These agents are the carriers of threats that assist in shaping and execution of the threat.
Cyber Criminals: These are the categories of threat agents that give shape to the nefarious
activities in the cyber space and they have a selfish motive associated with the attacks.
The attacks that are performed by these agents are deliberate and intentional in nature so
that they may gain benefits as a result. There may be legal actions that may be taken if
the attacks are reported and these criminals are identified.
5

ENISA Big Data Security
Online social hackers: These agents are also known as Hacktivists and these give shape to
the social engineering attacks. The primary targets of these agents are the high profile
web sites along with military institutions so that they may achieve a one-time high profit
as a result of the execution of the attacks (Wood, 2016).
Nation States: Many of the top threats are given shape by these threat agents that make
use of the huge number of resources and cyber intelligence for threat execution. These
threats agents give shape to the security attacks so that the damage that is caused is huge
and severe.
Employees: There are members of the staff that are associated with every organization.
The unintentional data loss and leakages are primarily caused by these threat agents due
to certain technical or operational fault. They may also be involved in other deliberate
and intentional attacks so that they make gain benefits as a result.
Cyber Terrorists: These agents may be motivated due to a political or a religious reason
behind the execution of an attack. The forms of attacks that are given shape by these
agents may have some extremely severe impacts (Casey, Koeberl, & Vishik, 2010).
Script Kiddies: These are the unskilled individuals that may cause the attacks and threats
to take place due to their malicious code or program.
6
Online social hackers: These agents are also known as Hacktivists and these give shape to
the social engineering attacks. The primary targets of these agents are the high profile
web sites along with military institutions so that they may achieve a one-time high profit
as a result of the execution of the attacks (Wood, 2016).
Nation States: Many of the top threats are given shape by these threat agents that make
use of the huge number of resources and cyber intelligence for threat execution. These
threats agents give shape to the security attacks so that the damage that is caused is huge
and severe.
Employees: There are members of the staff that are associated with every organization.
The unintentional data loss and leakages are primarily caused by these threat agents due
to certain technical or operational fault. They may also be involved in other deliberate
and intentional attacks so that they make gain benefits as a result.
Cyber Terrorists: These agents may be motivated due to a political or a religious reason
behind the execution of an attack. The forms of attacks that are given shape by these
agents may have some extremely severe impacts (Casey, Koeberl, & Vishik, 2010).
Script Kiddies: These are the unskilled individuals that may cause the attacks and threats
to take place due to their malicious code or program.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
ENISA Big Data Security
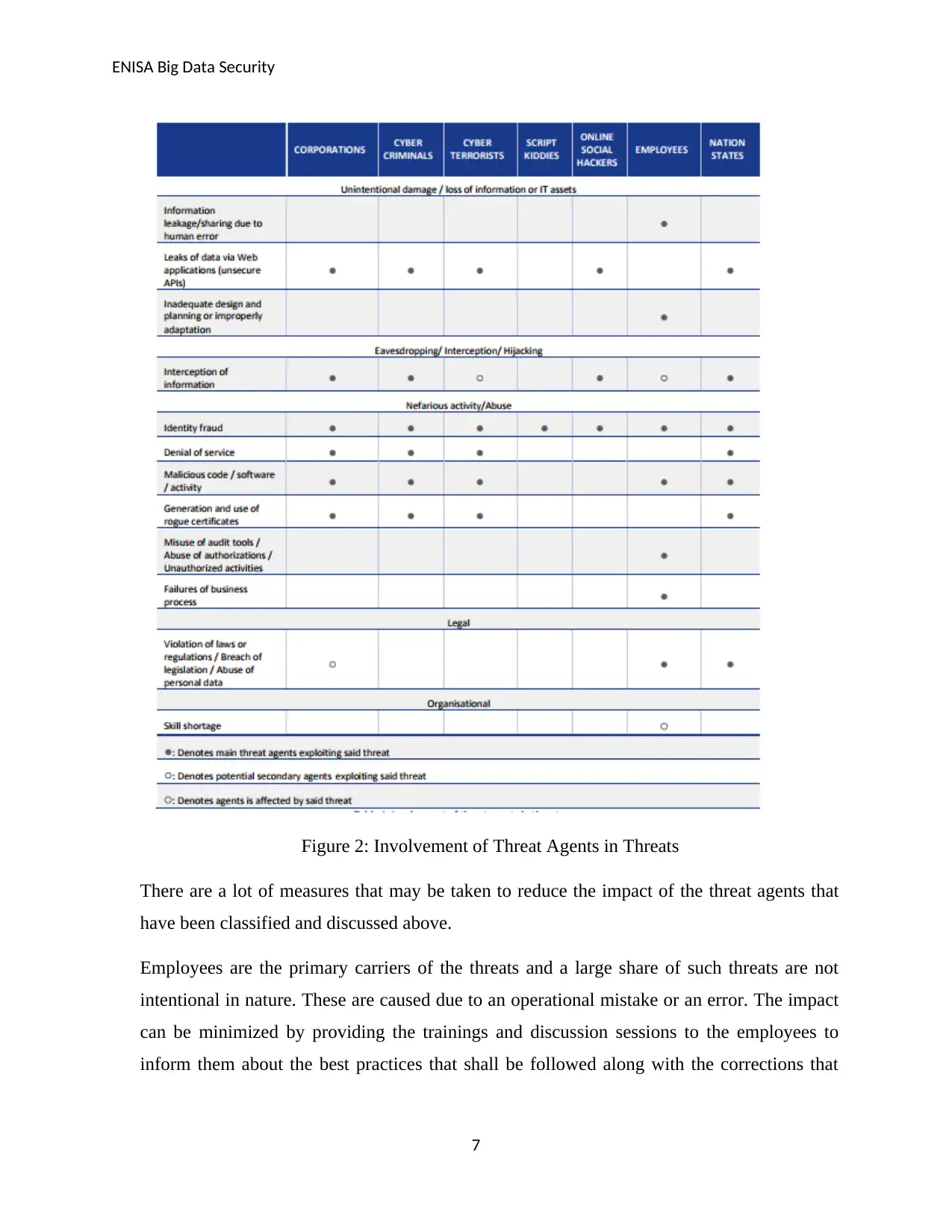
Figure 2: Involvement of Threat Agents in Threats
There are a lot of measures that may be taken to reduce the impact of the threat agents that
have been classified and discussed above.
Employees are the primary carriers of the threats and a large share of such threats are not
intentional in nature. These are caused due to an operational mistake or an error. The impact
can be minimized by providing the trainings and discussion sessions to the employees to
inform them about the best practices that shall be followed along with the corrections that
7
Figure 2: Involvement of Threat Agents in Threats
There are a lot of measures that may be taken to reduce the impact of the threat agents that
have been classified and discussed above.
Employees are the primary carriers of the threats and a large share of such threats are not
intentional in nature. These are caused due to an operational mistake or an error. The impact
can be minimized by providing the trainings and discussion sessions to the employees to
inform them about the best practices that shall be followed along with the corrections that
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ENISA Big Data Security
they make apply in case of an error. It is also necessary to apply enhanced administrative
control so that the frequency of such attacks is reduced.
There are many of the threat agents that give shape to the deliberate threats, such as,
eavesdropping attacks and many of the nefarious activities. These threat agents include cyber
criminals and cyber terrorists along with nation states and online social hackers. The best
possible method to control the impact of these threat agents is the enhancement of the legal
and regulatory policies for information protection and safety. There shall also be technical
and logical controls that must be implemented so that any of the nefarious activities
attempted by these agents is avoided.
Script kiddies must be explained and made aware about the legal obligations that they may
have to face in case they are found guilty of executing a security threat. There shall be
sessions and awareness campaigns that must be launched so that the required information is
adequately communicated.
In addition to the above measures, strong administrative control and monitoring shall also be
used and applied so that the impact of these threat agents is reduced. These administrative
checks must include the regular security audits, security reviews and inspections to be carried
out to obtain a picture of the security state. This will lead to the detection of the areas of
improvements and will also lead to the maintenance of the security logs.
8
they make apply in case of an error. It is also necessary to apply enhanced administrative
control so that the frequency of such attacks is reduced.
There are many of the threat agents that give shape to the deliberate threats, such as,
eavesdropping attacks and many of the nefarious activities. These threat agents include cyber
criminals and cyber terrorists along with nation states and online social hackers. The best
possible method to control the impact of these threat agents is the enhancement of the legal
and regulatory policies for information protection and safety. There shall also be technical
and logical controls that must be implemented so that any of the nefarious activities
attempted by these agents is avoided.
Script kiddies must be explained and made aware about the legal obligations that they may
have to face in case they are found guilty of executing a security threat. There shall be
sessions and awareness campaigns that must be launched so that the required information is
adequately communicated.
In addition to the above measures, strong administrative control and monitoring shall also be
used and applied so that the impact of these threat agents is reduced. These administrative
checks must include the regular security audits, security reviews and inspections to be carried
out to obtain a picture of the security state. This will lead to the detection of the areas of
improvements and will also lead to the maintenance of the security logs.
8
ENISA Big Data Security
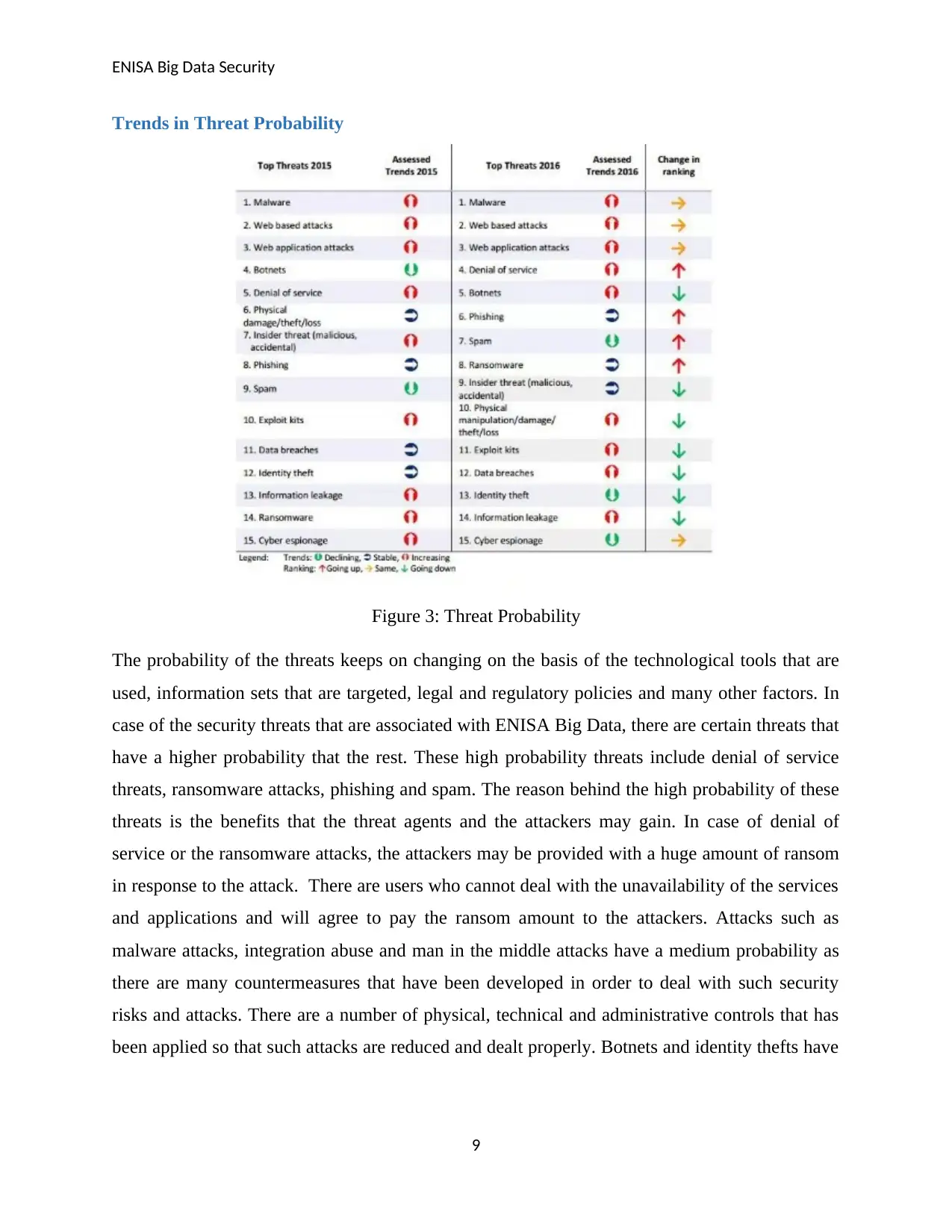
Trends in Threat Probability
Figure 3: Threat Probability
The probability of the threats keeps on changing on the basis of the technological tools that are
used, information sets that are targeted, legal and regulatory policies and many other factors. In
case of the security threats that are associated with ENISA Big Data, there are certain threats that
have a higher probability that the rest. These high probability threats include denial of service
threats, ransomware attacks, phishing and spam. The reason behind the high probability of these
threats is the benefits that the threat agents and the attackers may gain. In case of denial of
service or the ransomware attacks, the attackers may be provided with a huge amount of ransom
in response to the attack. There are users who cannot deal with the unavailability of the services
and applications and will agree to pay the ransom amount to the attackers. Attacks such as
malware attacks, integration abuse and man in the middle attacks have a medium probability as
there are many countermeasures that have been developed in order to deal with such security
risks and attacks. There are a number of physical, technical and administrative controls that has
been applied so that such attacks are reduced and dealt properly. Botnets and identity thefts have
9
Trends in Threat Probability
Figure 3: Threat Probability
The probability of the threats keeps on changing on the basis of the technological tools that are
used, information sets that are targeted, legal and regulatory policies and many other factors. In
case of the security threats that are associated with ENISA Big Data, there are certain threats that
have a higher probability that the rest. These high probability threats include denial of service
threats, ransomware attacks, phishing and spam. The reason behind the high probability of these
threats is the benefits that the threat agents and the attackers may gain. In case of denial of
service or the ransomware attacks, the attackers may be provided with a huge amount of ransom
in response to the attack. There are users who cannot deal with the unavailability of the services
and applications and will agree to pay the ransom amount to the attackers. Attacks such as
malware attacks, integration abuse and man in the middle attacks have a medium probability as
there are many countermeasures that have been developed in order to deal with such security
risks and attacks. There are a number of physical, technical and administrative controls that has
been applied so that such attacks are reduced and dealt properly. Botnets and identity thefts have
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ENISA Big Data Security
a low probability due to enhanced authentication and access control that is being used in ENISA
(Nichols, 2016).
Improvements in ETL Processes
There are various improvements that can be made in the ETL process so as to prevent, detect and
control the Big Data security threats and issues.
There are many different mechanisms that are in use by ENISA so that the overall security
architecture is improved and the frequency of the threats and attacks is reduced. In case of Big
Data, there is a huge variety of data and massive data volumes that are involved. It is, therefore,
recommended to make sure of the security measures that are as per the latest technological
developments and enhancements.
Encryption of the data files in the database and one the cloud is necessary. It is being done at
present; however, there are several advancements that gave been made in this area. These
advancements include the use of advanced encryption algorithms along with the hashing
algorithms that may be used and applied for enhanced protection of the information. In such a
manner, the attackers will not be able to misuse the information even if they succeed in the
attempt to breach the information.
It is also necessary to reduce the attacking window and attacking surface in order to avoid and
prevent the security risks and attacks. This can be done by frequently updating the applications
and services so that the version specific attacks are avoided. Also, the data and information shall
be re-located so that the attackers may not target a particular address for attacking the
information.
There are various errors and steps that the users and employees take that result in the execution
of the threats and attacks. These can be controlled by promoting user awareness and providing
training sessions to the employees. In this manner, the security threats and attacks due to an
operational mistake or a human error will be avoided (Microsoft, 2016).
Challenging Threats for ENISA
The primary focus for the ETL processes should be on the high probability attacks and the ones
that may have a huge impact. There are certain forms of the threats and attacks that are difficult
10
a low probability due to enhanced authentication and access control that is being used in ENISA
(Nichols, 2016).
Improvements in ETL Processes
There are various improvements that can be made in the ETL process so as to prevent, detect and
control the Big Data security threats and issues.
There are many different mechanisms that are in use by ENISA so that the overall security
architecture is improved and the frequency of the threats and attacks is reduced. In case of Big
Data, there is a huge variety of data and massive data volumes that are involved. It is, therefore,
recommended to make sure of the security measures that are as per the latest technological
developments and enhancements.
Encryption of the data files in the database and one the cloud is necessary. It is being done at
present; however, there are several advancements that gave been made in this area. These
advancements include the use of advanced encryption algorithms along with the hashing
algorithms that may be used and applied for enhanced protection of the information. In such a
manner, the attackers will not be able to misuse the information even if they succeed in the
attempt to breach the information.
It is also necessary to reduce the attacking window and attacking surface in order to avoid and
prevent the security risks and attacks. This can be done by frequently updating the applications
and services so that the version specific attacks are avoided. Also, the data and information shall
be re-located so that the attackers may not target a particular address for attacking the
information.
There are various errors and steps that the users and employees take that result in the execution
of the threats and attacks. These can be controlled by promoting user awareness and providing
training sessions to the employees. In this manner, the security threats and attacks due to an
operational mistake or a human error will be avoided (Microsoft, 2016).
Challenging Threats for ENISA
The primary focus for the ETL processes should be on the high probability attacks and the ones
that may have a huge impact. There are certain forms of the threats and attacks that are difficult
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ENISA Big Data Security
to track and control. For instance, in case of a use of an unsecure network by the end-user outside
the infrastructure of ENISA, then it would be challenging to apply security controls and
protocols (Panetta, 2016). The access control shall therefore be applied by making use of the
advanced access control measures such as attribute based and role based access control.
There are also challenges that may come up in the attacks that are associated with the internal
employees of the organization. There must be ethical and professional codes of conduct that
must be discussed with them so that the deliberate and intentional threats are avoided.
With the aid of an amalgamation of technical, physical and administrative controls, it would be
possible to put a check on the ENISA Big Data security threats and attacks.
Current IT Security State of ENISA – Recommendations & Conclusion
ENISA has taken a lot many steps to make sure that the security risks and attacks are avoided,
prevented and controlled. However, in spite of so many attempts and measures that have been
taken by ENISA, the frequency of the security occurrences and events is still high. It is due to
this reason that ENISA should not be satisfied with the present state of its IT security structure.
There are newer forms of security risks and threats that are being created by the attackers and the
Big Data that is associated with ENISA is exposed to such risks and attacks. There are a huge
number of unintentional attacks that take place in association with Big Data which should not
happen. There are six different types of threat agents, viz. cyber criminals, cyber terrorists,
employees, script kiddies, nation states and online social hackers that act as carriers to the risk
and attacks. Most of these threat agents give shape to the attacks that are deliberate and
intentional in nature. There is only application of strong security policies and controls that can
stop these attacks (Aws, 2016).
The primary requirement is therefore to improve the IT security state by introducing enhanced
measures for the security of IT infrastructure and architecture. These enhancements shall be done
in the form of technical controls, logical controls along with the administrative policies and
controls. It is also necessary to make sure that the employees of the organizations are aware of
the ethical standards and professional codes of conduct to be followed. The users must also be
made aware of the common security attacks and the safety measures that they may take.
11
to track and control. For instance, in case of a use of an unsecure network by the end-user outside
the infrastructure of ENISA, then it would be challenging to apply security controls and
protocols (Panetta, 2016). The access control shall therefore be applied by making use of the
advanced access control measures such as attribute based and role based access control.
There are also challenges that may come up in the attacks that are associated with the internal
employees of the organization. There must be ethical and professional codes of conduct that
must be discussed with them so that the deliberate and intentional threats are avoided.
With the aid of an amalgamation of technical, physical and administrative controls, it would be
possible to put a check on the ENISA Big Data security threats and attacks.
Current IT Security State of ENISA – Recommendations & Conclusion
ENISA has taken a lot many steps to make sure that the security risks and attacks are avoided,
prevented and controlled. However, in spite of so many attempts and measures that have been
taken by ENISA, the frequency of the security occurrences and events is still high. It is due to
this reason that ENISA should not be satisfied with the present state of its IT security structure.
There are newer forms of security risks and threats that are being created by the attackers and the
Big Data that is associated with ENISA is exposed to such risks and attacks. There are a huge
number of unintentional attacks that take place in association with Big Data which should not
happen. There are six different types of threat agents, viz. cyber criminals, cyber terrorists,
employees, script kiddies, nation states and online social hackers that act as carriers to the risk
and attacks. Most of these threat agents give shape to the attacks that are deliberate and
intentional in nature. There is only application of strong security policies and controls that can
stop these attacks (Aws, 2016).
The primary requirement is therefore to improve the IT security state by introducing enhanced
measures for the security of IT infrastructure and architecture. These enhancements shall be done
in the form of technical controls, logical controls along with the administrative policies and
controls. It is also necessary to make sure that the employees of the organizations are aware of
the ethical standards and professional codes of conduct to be followed. The users must also be
made aware of the common security attacks and the safety measures that they may take.
11

ENISA Big Data Security
References
Amato, N. (2016). The hidden costs of a data breach. Journal of Accountancy. Retrieved 8
September 2017, from http://www.journalofaccountancy.com/news/2016/jul/hidden-costs-
of-data-breach-201614870.html
Aws,. (2016). Overview of Security Processes. Retrieved 8 September 2017, from
https://d0.awsstatic.com/whitepapers/aws-security-whitepaper.pdf
Casey, T., Koeberl, P., & Vishik, C. (2010). Threat agents. Proceedings Of The Sixth Annual
Workshop On Cyber Security And Information Intelligence Research - CSIIRW '10.
http://dx.doi.org/10.1145/1852666.1852728
Enisa. (2016). Big Data Threat Landscape — ENISA. Enisa.europa.eu. Retrieved 8 September
2017, from https://www.enisa.europa.eu/publications/bigdata-threat-landscape
Ko, M. & Dorantes, C. (2016). The impact of information security breaches on financial
performance of the breached firms: An empirical investigation. Retrieved 8 September
2017, from http://jitm.ubalt.edu/XVII-2/article2.pdf
Microsoft,. (2016). Microsoft Core Infrastructure Optimization: IT & Security Processes - Best
Practices for Business IT. Microsoft.com. Retrieved 8 September 2017, from
https://www.microsoft.com/india/infrastructure/capabilities/itprocesses.mspx
Nichols, A. (2016). A Perspective on Threats in the Risk Analysis Process. Sans.org. Retrieved 8
September 2017, from
https://www.sans.org/reading-room/whitepapers/auditing/perspective-threats-risk-analysis-
process-63
Panetta, K. (2016). Gartner's Top 10 Security Predictions 2016 - Smarter With Gartner. Smarter
With Gartner. Retrieved 8 September 2017, from
http://www.gartner.com/smarterwithgartner/top-10-security-predictions-2016/
Wood, P. (2016). Social hacking: The easy way to breach network security. ComputerWeekly.
Retrieved 8 September 2017, from http://www.computerweekly.com/tip/Social-hacking-
The-easy-way-to-breach-network-security
12
References
Amato, N. (2016). The hidden costs of a data breach. Journal of Accountancy. Retrieved 8
September 2017, from http://www.journalofaccountancy.com/news/2016/jul/hidden-costs-
of-data-breach-201614870.html
Aws,. (2016). Overview of Security Processes. Retrieved 8 September 2017, from
https://d0.awsstatic.com/whitepapers/aws-security-whitepaper.pdf
Casey, T., Koeberl, P., & Vishik, C. (2010). Threat agents. Proceedings Of The Sixth Annual
Workshop On Cyber Security And Information Intelligence Research - CSIIRW '10.
http://dx.doi.org/10.1145/1852666.1852728
Enisa. (2016). Big Data Threat Landscape — ENISA. Enisa.europa.eu. Retrieved 8 September
2017, from https://www.enisa.europa.eu/publications/bigdata-threat-landscape
Ko, M. & Dorantes, C. (2016). The impact of information security breaches on financial
performance of the breached firms: An empirical investigation. Retrieved 8 September
2017, from http://jitm.ubalt.edu/XVII-2/article2.pdf
Microsoft,. (2016). Microsoft Core Infrastructure Optimization: IT & Security Processes - Best
Practices for Business IT. Microsoft.com. Retrieved 8 September 2017, from
https://www.microsoft.com/india/infrastructure/capabilities/itprocesses.mspx
Nichols, A. (2016). A Perspective on Threats in the Risk Analysis Process. Sans.org. Retrieved 8
September 2017, from
https://www.sans.org/reading-room/whitepapers/auditing/perspective-threats-risk-analysis-
process-63
Panetta, K. (2016). Gartner's Top 10 Security Predictions 2016 - Smarter With Gartner. Smarter
With Gartner. Retrieved 8 September 2017, from
http://www.gartner.com/smarterwithgartner/top-10-security-predictions-2016/
Wood, P. (2016). Social hacking: The easy way to breach network security. ComputerWeekly.
Retrieved 8 September 2017, from http://www.computerweekly.com/tip/Social-hacking-
The-easy-way-to-breach-network-security
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





