ENISA Big Data Security Infrastructure: Threats and Solutions
VerifiedAdded on 2020/02/19
|13
|3109
|112
Report
AI Summary
This report provides a detailed analysis of ENISA's big data security infrastructure, focusing on the threat landscape of 2014 and its implications. It explores the key threats, including web-based attacks, clickjacking, and the vulnerabilities associated with emerging technologies like IoT and big data. The report identifies and discusses key threat agents, such as cyber terrorists, hackers, and insider threats, offering solutions to minimize their impact through stronger passwords, multi-factor authentication, and security guidelines. It also examines the ETL process, suggesting improvements to enhance its efficiency, and concludes with an assessment of ENISA's current state of IT security. The report emphasizes the importance of proactive security measures, robust access controls, and continuous monitoring to combat cyber threats effectively. It also highlights the need for improved awareness and training to mitigate the risks associated with negligence and evolving cyber security challenges.

RUNNING HEAD: ENISA BIG DATA SECURITY INFRASTRUCTURE 1
ENISA BIG DATA SECURITY INFRASTRUCTURE
Student Name
Institute Name
ENISA BIG DATA SECURITY INFRASTRUCTURE
Student Name
Institute Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ENISA BIG DATA SECURITY INFRASTRUCTURE 2
Contents
Overview of the case study..............................................................................................................3
Diagram for the ENISA Big Data security infrastructure...............................................................5
Top threats.......................................................................................................................................7
Identify and discuss the key Threat Agents. What could be done to minimize their impact on the
system?............................................................................................................................................8
How could the ETL process be improved? Discuss........................................................................9
To sum up, should ENISA be satisfied with its current state of IT Security? Why?....................11
Reference.......................................................................................................................................12
Contents
Overview of the case study..............................................................................................................3
Diagram for the ENISA Big Data security infrastructure...............................................................5
Top threats.......................................................................................................................................7
Identify and discuss the key Threat Agents. What could be done to minimize their impact on the
system?............................................................................................................................................8
How could the ETL process be improved? Discuss........................................................................9
To sum up, should ENISA be satisfied with its current state of IT Security? Why?....................11
Reference.......................................................................................................................................12

ENISA BIG DATA SECURITY INFRASTRUCTURE 3
Overview of the case study
The report discuss in detail about the ENISA threat which is based on a landscape of 2014 that is
able to provide a detailed explanation associated with the threat based intelligence that consist of
cyber related threats and the associated trends. It further discusses about the breach of
information that took place in 2014 and done by utilized the weakness connected with the
security and many cyber threat agents that can be misused in the business (Olesen, 2016). There
is plenty of sloppiness as well and one of the main factors for most of issue in cyber security is
also covered here. One can easily find that in many cases there are around fifty percent of the
times is because of the case of sloppiness. Thirty four percent of the system functions without
any proper base for security control that is one of the important challenges. According to the
report, emergences of the technologies like IOT, CPS and mobile based computing along with
big data will also make an influence on the landscape of the current threat. It is important to
understand here that by cautiously avoiding the usage of big data along mobile based computing
for future threats can be ignored quite easily (Skopik et al, 2016).
ENISA can further be defined as European Union Agency for Network and Information Security.
The system is based on various threats based landscape and as discussed it happened in the year
2014. The whole revelation was about the threat that came along with lots of complex issues. It
further attributed to the modifications and success based function that have been conducted by
the number of forces in security concern in addition to the proper mobilization of the current
cyber society (Weber & Studer, 2016). The actions taken were outstanding and following is the
detailed discussion: -
Overview of the case study
The report discuss in detail about the ENISA threat which is based on a landscape of 2014 that is
able to provide a detailed explanation associated with the threat based intelligence that consist of
cyber related threats and the associated trends. It further discusses about the breach of
information that took place in 2014 and done by utilized the weakness connected with the
security and many cyber threat agents that can be misused in the business (Olesen, 2016). There
is plenty of sloppiness as well and one of the main factors for most of issue in cyber security is
also covered here. One can easily find that in many cases there are around fifty percent of the
times is because of the case of sloppiness. Thirty four percent of the system functions without
any proper base for security control that is one of the important challenges. According to the
report, emergences of the technologies like IOT, CPS and mobile based computing along with
big data will also make an influence on the landscape of the current threat. It is important to
understand here that by cautiously avoiding the usage of big data along mobile based computing
for future threats can be ignored quite easily (Skopik et al, 2016).
ENISA can further be defined as European Union Agency for Network and Information Security.
The system is based on various threats based landscape and as discussed it happened in the year
2014. The whole revelation was about the threat that came along with lots of complex issues. It
further attributed to the modifications and success based function that have been conducted by
the number of forces in security concern in addition to the proper mobilization of the current
cyber society (Weber & Studer, 2016). The actions taken were outstanding and following is the
detailed discussion: -
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ENISA BIG DATA SECURITY INFRASTRUCTURE 4
1) The complete process is related with botnet Zeus which is later stopped with an infection
and the different kind of campaigns to interact especially with number of C&C centers.
2) The arrest of the developer of Black hole in 2013 there was major reduction and is done
to exploit the overall usage of the kit.
3) Any kind of decrease is also based on amplifying the NTP along with DDoS that usually
is an outcome of the overall reduction from the current set of servers. It is usually based
on the overall awareness that arises from the community (Rogers et al, 2016).
4) The reduction is also based on the injections of SQL with improving in the development
knowledge of web.
5) The present demolition of Silk Road with profound based of web based services have
also been in some kind of impact especially by the current TOR along with the main
attacker of the network.
There are many kinds of black spot where the system of SSL as well as TLS has been constantly
operating for the sake of securing the small nucleus present on the internet. They are also
influenced by the diverse mistakes like execution on HEARTBLEED and many others. There is
also some mass level of data theft with elements like shellshock based on vulnerability of shell.
The most important influence has been on the elements that can be used with the older type with
some engrained software (Leenen & Meyer, 2016). There is also violation of privacy as well
with the help of media based channels that have a finished reduction in the trust of the users with
the help of multiple media based channels with complete amount of reduction in the level of trust
of the client using varied internet services. The analysis also says that the documents are also
associated with the learning that are crucial and significant for the successful level of attacks.
These are primarily because some kind of negligence in the present cyber security issues. The
1) The complete process is related with botnet Zeus which is later stopped with an infection
and the different kind of campaigns to interact especially with number of C&C centers.
2) The arrest of the developer of Black hole in 2013 there was major reduction and is done
to exploit the overall usage of the kit.
3) Any kind of decrease is also based on amplifying the NTP along with DDoS that usually
is an outcome of the overall reduction from the current set of servers. It is usually based
on the overall awareness that arises from the community (Rogers et al, 2016).
4) The reduction is also based on the injections of SQL with improving in the development
knowledge of web.
5) The present demolition of Silk Road with profound based of web based services have
also been in some kind of impact especially by the current TOR along with the main
attacker of the network.
There are many kinds of black spot where the system of SSL as well as TLS has been constantly
operating for the sake of securing the small nucleus present on the internet. They are also
influenced by the diverse mistakes like execution on HEARTBLEED and many others. There is
also some mass level of data theft with elements like shellshock based on vulnerability of shell.
The most important influence has been on the elements that can be used with the older type with
some engrained software (Leenen & Meyer, 2016). There is also violation of privacy as well
with the help of media based channels that have a finished reduction in the trust of the users with
the help of multiple media based channels with complete amount of reduction in the level of trust
of the client using varied internet services. The analysis also says that the documents are also
associated with the learning that are crucial and significant for the successful level of attacks.
These are primarily because some kind of negligence in the present cyber security issues. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
ENISA BIG DATA SECURITY INFRASTRUCTURE 5
complete aim has been on creating awareness where the level of negligence can be further
reduced. This is done especially when the society has the ability to work for the overall
improvement of the complicated technical knowledge for people who work with some kind of
inferiority complex about the information (Chaudhuri, 2016). There are also different kinds of
violations in privacy matter that can be seen in the case of varied media based channels with the
consumers that have been using or depending on the internet services. Any kind of successful
attack is usually because of the level of negligence that is an important challenge of the cyber
security. It is also important to understand here that one may need to pay more attention on the
improvement of the level of awareness where this kind of negligence can also be decreased with
some kind of improvement while passing on complicated technology based information.
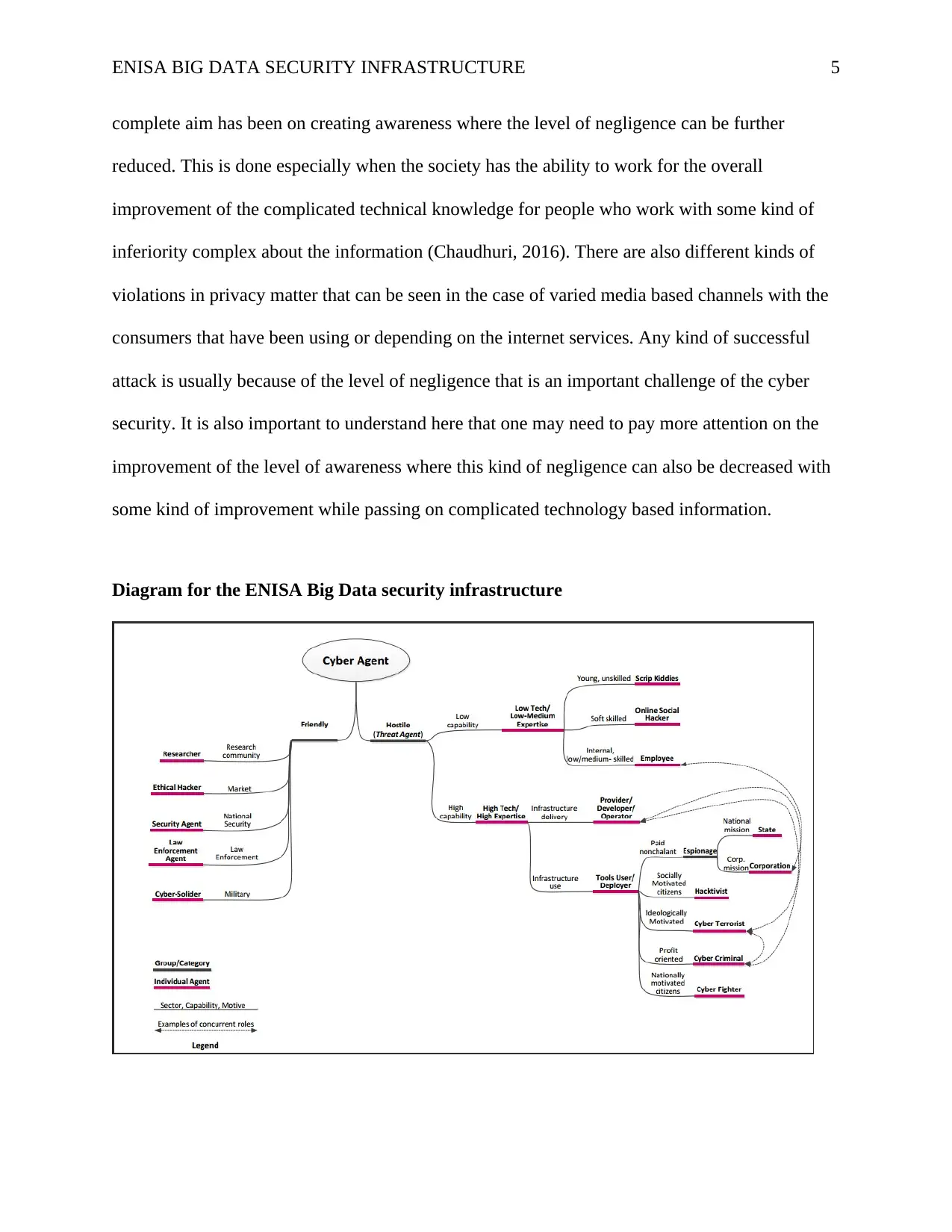
Diagram for the ENISA Big Data security infrastructure
complete aim has been on creating awareness where the level of negligence can be further
reduced. This is done especially when the society has the ability to work for the overall
improvement of the complicated technical knowledge for people who work with some kind of
inferiority complex about the information (Chaudhuri, 2016). There are also different kinds of
violations in privacy matter that can be seen in the case of varied media based channels with the
consumers that have been using or depending on the internet services. Any kind of successful
attack is usually because of the level of negligence that is an important challenge of the cyber
security. It is also important to understand here that one may need to pay more attention on the
improvement of the level of awareness where this kind of negligence can also be decreased with
some kind of improvement while passing on complicated technology based information.
Diagram for the ENISA Big Data security infrastructure
ENISA BIG DATA SECURITY INFRASTRUCTURE 6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ENISA BIG DATA SECURITY INFRASTRUCTURE 7
Top threats
There are so many critical as well as complicated top threats in picture which consist of the
major part of the company where the amount of risk is based on handling the digital level of
handloom with the options to obtain data. The electronic or the web based software is also found
to be important where the attack from web has been because of the program. The main attention
has been on helplessness of the program with so many unsafe options that exist in light of the
current facts. There has been no requirement to work on initiating the process of download for
the small or vindictive kind of elements (Buse, 2017). The attack that happens online is for click
jacking the whole process where the routine is maligned and mainly based on the overall control
on the sites of consumers to function with the activities where the whole structure aim on the
undetectable edges from the client. It is also important to understand that all the pop ups is
mainly because of showcasing the pernicious kind of elements and is also based on tapping only
with particular part which further will lead to small or sensitive elements. The company working
on the web actually functions with the proximity of high risk. This risk is there because of
getting stuck so that that level of threat is actually for the matters of affiliation (César &
Debussche, 2017).
There are other threats which are related to the cyber threats which need to handle the attack
patterns and the tools that are targeted based on the emerging big data and the Internet of Things
(IoT). ENISA works on the center of the network and the information security where EU works
on the private sector. The groups are mainly to develop the advice with the recommendations set
for the information security. It also includes the details of the advanced malicious tools with
other striking powers with cooperation and the reaction to cyber threats.
Top threats
There are so many critical as well as complicated top threats in picture which consist of the
major part of the company where the amount of risk is based on handling the digital level of
handloom with the options to obtain data. The electronic or the web based software is also found
to be important where the attack from web has been because of the program. The main attention
has been on helplessness of the program with so many unsafe options that exist in light of the
current facts. There has been no requirement to work on initiating the process of download for
the small or vindictive kind of elements (Buse, 2017). The attack that happens online is for click
jacking the whole process where the routine is maligned and mainly based on the overall control
on the sites of consumers to function with the activities where the whole structure aim on the
undetectable edges from the client. It is also important to understand that all the pop ups is
mainly because of showcasing the pernicious kind of elements and is also based on tapping only
with particular part which further will lead to small or sensitive elements. The company working
on the web actually functions with the proximity of high risk. This risk is there because of
getting stuck so that that level of threat is actually for the matters of affiliation (César &
Debussche, 2017).
There are other threats which are related to the cyber threats which need to handle the attack
patterns and the tools that are targeted based on the emerging big data and the Internet of Things
(IoT). ENISA works on the center of the network and the information security where EU works
on the private sector. The groups are mainly to develop the advice with the recommendations set
for the information security. It also includes the details of the advanced malicious tools with
other striking powers with cooperation and the reaction to cyber threats.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ENISA BIG DATA SECURITY INFRASTRUCTURE 8
Identify and discuss the key Threat Agents. What could be done to minimize their impact
on the system?
It is important to understand that cyber terrorists are a reality and criminal and there are many
hackers also online along with employees. A person can very easily reduce the influence on the
complete system by developing a more difficult and stronger password and also making sure that
it for the factor based on varied authentication process. The two-important factor of
authentication is actually for sending the code to tab so that one can easily enter into any kind of
account. The update from number of software is actually with the actions that are also
counteractive in order to clean up right after there is break in the security or there is attack on the
web as well. There are security based guidelines along with the right training that has important
influence on the level of various security based system associations (Jacobs et al, 2016). The
number of times is to take accountability of the customers is associated with danger and the kind
of work on the overall contribution for number of variables with clears kind of pace. The chances
in the current security system is also developing and growing where there is complete ignorance
toward sending the personal level of data with the help of email and also aware people with the
issues like phishing. It actually associated with website of the company and also based on
designing that is among the threat agents. This further tries to hack the overall or the current
system.
In the first place, the threats are the actually the one that started with the consumer who is
present in the network and those elements which cannot be detected easily IDS and also detect
the actions of insider with main challenge is that the issue actually remain completely undetected
for a very long period of time. The threat also has a legal access and it is most importantly harder
to identify and with the usage of the restrictions insider that can mishandles the advantages and
Identify and discuss the key Threat Agents. What could be done to minimize their impact
on the system?
It is important to understand that cyber terrorists are a reality and criminal and there are many
hackers also online along with employees. A person can very easily reduce the influence on the
complete system by developing a more difficult and stronger password and also making sure that
it for the factor based on varied authentication process. The two-important factor of
authentication is actually for sending the code to tab so that one can easily enter into any kind of
account. The update from number of software is actually with the actions that are also
counteractive in order to clean up right after there is break in the security or there is attack on the
web as well. There are security based guidelines along with the right training that has important
influence on the level of various security based system associations (Jacobs et al, 2016). The
number of times is to take accountability of the customers is associated with danger and the kind
of work on the overall contribution for number of variables with clears kind of pace. The chances
in the current security system is also developing and growing where there is complete ignorance
toward sending the personal level of data with the help of email and also aware people with the
issues like phishing. It actually associated with website of the company and also based on
designing that is among the threat agents. This further tries to hack the overall or the current
system.
In the first place, the threats are the actually the one that started with the consumer who is
present in the network and those elements which cannot be detected easily IDS and also detect
the actions of insider with main challenge is that the issue actually remain completely undetected
for a very long period of time. The threat also has a legal access and it is most importantly harder
to identify and with the usage of the restrictions insider that can mishandles the advantages and

ENISA BIG DATA SECURITY INFRASTRUCTURE 9
use the knowledge to steal the information (Grobler et al, 2016). In order to overcome different
kinds of threats, companies should execute the effective level of security measures to detect any
kinds of threats. Strategy is based on combating the level of security based threats consist of
associations that requires to execute clear kind security strategies and with rules to reduce the
overall risks. There is robust kind of access based control is actually one of the impactful control
utilized by the companies to overcome the threats and it assists to save all the auditing activities.
Another crucial strategy is based on detecting the threat for the auditing with number of security
logs. It also assists to collect and test the data in saving the potential level of attack. The threats
should be the one that can be started by the applicants in the current network. These further
cannot be easily detected by any kind of firewalls or anti-virus. Therefore, in order to overcome
the companies are functioning on the strategy to combat the threats for security. It is usually
going through the execution of right kind of strategy of clear base of security which can reduce
the risks also. The robust level of control is crucial and impactful for the company to assist in
handling the process of auditing activities (Grobler et al, 2016). The complete strategy is
primarily due to detecting the threat with auditing based security measures along with collection
and evaluating the data to save the potential of number of cyber-attack. The overall danger
should be real with hard level patterns with perceived intentions where the overall misuse on the
restrictions and the usage of the insight is crucial for the correct data. It functions on the overall
access that is compelled and can be comfortably used by the company to safely impact the
abilities.
How could the ETL process be improved? Discuss.
In order to function on the level of improvement of the process of ETL and there should be a
need to pay attention on the level of execution in addition with ensuring that there is specific
use the knowledge to steal the information (Grobler et al, 2016). In order to overcome different
kinds of threats, companies should execute the effective level of security measures to detect any
kinds of threats. Strategy is based on combating the level of security based threats consist of
associations that requires to execute clear kind security strategies and with rules to reduce the
overall risks. There is robust kind of access based control is actually one of the impactful control
utilized by the companies to overcome the threats and it assists to save all the auditing activities.
Another crucial strategy is based on detecting the threat for the auditing with number of security
logs. It also assists to collect and test the data in saving the potential level of attack. The threats
should be the one that can be started by the applicants in the current network. These further
cannot be easily detected by any kind of firewalls or anti-virus. Therefore, in order to overcome
the companies are functioning on the strategy to combat the threats for security. It is usually
going through the execution of right kind of strategy of clear base of security which can reduce
the risks also. The robust level of control is crucial and impactful for the company to assist in
handling the process of auditing activities (Grobler et al, 2016). The complete strategy is
primarily due to detecting the threat with auditing based security measures along with collection
and evaluating the data to save the potential of number of cyber-attack. The overall danger
should be real with hard level patterns with perceived intentions where the overall misuse on the
restrictions and the usage of the insight is crucial for the correct data. It functions on the overall
access that is compelled and can be comfortably used by the company to safely impact the
abilities.
How could the ETL process be improved? Discuss.
In order to function on the level of improvement of the process of ETL and there should be a
need to pay attention on the level of execution in addition with ensuring that there is specific
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ENISA BIG DATA SECURITY INFRASTRUCTURE 10
kind of bottlenecks. In addition, there are also options to function on the questioning of the
implementation patterns that are based on CPU. The speed of purchasing with the finishing of
the usage of cash is the best procedure to improvise the process of ETL. The current database
also motors and can be known where the implementation of knowledge is actually based on the
trade with the use that does not function on intricate level of details that are specifically for a
particular pattern (Grobler et al, 2016). The usage of SQL based insert also claims about the
overall mass patterns that are right along with being more liable. The performance removed
along with conceived change with loads in order to handle the overall memory.
The ETL process is based on the emerging trends where the approach is based on the collection
and the collation of the available information to produce the cyber threat assessment. The ERL
includes the reporting with the contribution to work on the availability factors with the growth
that includes the proper reporting periods. The ETL works with the ENISA that has been
performed with the use-cases of threat intelligence. The standards are set with the use of the
threat analysis, with the demonstration that includes the stakeholders in the identification of the
issues. ETL processes is based on the groups with the threat analysis which include the
stakeholder requirements and state-of-the-art. The policy is based on the contribution towards the
achievement of the objective with the formulation that provides the high document. The sources
are set with the emerging technology with the good “entry point” that is subjected to the threat
intelligence for the non-experts. ETL also focus on the strategic and the tactical information
collection, aggregation and the analysis, which is based on the different types of the information.
ENISA works on the threat landscape with the various stakeholder groups where the material
targets about the wider public which includes the policy makers, end users, and the hostile
agents. The advancement is based on the emerging areas with the software defined network and
kind of bottlenecks. In addition, there are also options to function on the questioning of the
implementation patterns that are based on CPU. The speed of purchasing with the finishing of
the usage of cash is the best procedure to improvise the process of ETL. The current database
also motors and can be known where the implementation of knowledge is actually based on the
trade with the use that does not function on intricate level of details that are specifically for a
particular pattern (Grobler et al, 2016). The usage of SQL based insert also claims about the
overall mass patterns that are right along with being more liable. The performance removed
along with conceived change with loads in order to handle the overall memory.
The ETL process is based on the emerging trends where the approach is based on the collection
and the collation of the available information to produce the cyber threat assessment. The ERL
includes the reporting with the contribution to work on the availability factors with the growth
that includes the proper reporting periods. The ETL works with the ENISA that has been
performed with the use-cases of threat intelligence. The standards are set with the use of the
threat analysis, with the demonstration that includes the stakeholders in the identification of the
issues. ETL processes is based on the groups with the threat analysis which include the
stakeholder requirements and state-of-the-art. The policy is based on the contribution towards the
achievement of the objective with the formulation that provides the high document. The sources
are set with the emerging technology with the good “entry point” that is subjected to the threat
intelligence for the non-experts. ETL also focus on the strategic and the tactical information
collection, aggregation and the analysis, which is based on the different types of the information.
ENISA works on the threat landscape with the various stakeholder groups where the material
targets about the wider public which includes the policy makers, end users, and the hostile
agents. The advancement is based on the emerging areas with the software defined network and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ENISA BIG DATA SECURITY INFRASTRUCTURE 11
the big data. The identification of the good practices is for the protection with the identification
of the security gaps. The structuring is based on the information security with the cyber threats.
The development forms are set with the threat agents with the increased patterns of the attacks
and the tools. The cyber activities with the development of the capabilities to handle the infiltrate
the different kinds of the target.
To sum up, should ENISA be satisfied with its current state of IT Security? Why?
The process of ENISA is unable to save the state of information technology where there should
be a requirement to handle the capacities along with the growth of different issues in security
measure. The level of competition is that are based on number of attackers to handle the security
in cyber space along with protecting data. To completely get over with the number threats and
there is also proper adaptation towards the technology when the data can be stored properly
(Grobler et al, 2016). It is also crucial to ensure that are specific and proper level of precautions
that can accessed comfortably and hand for the sensitive level of data. It also requires saving the
firewall with blocking the access. The system of ENISA should also work on the powers with
various points that are for some level of quality and there is also requirement to function on the
securing the data with number of European commission to also ensure the control that can be
well presented for diverse motive and never impact the security of the company (Grobler et al,
2016).
the big data. The identification of the good practices is for the protection with the identification
of the security gaps. The structuring is based on the information security with the cyber threats.
The development forms are set with the threat agents with the increased patterns of the attacks
and the tools. The cyber activities with the development of the capabilities to handle the infiltrate
the different kinds of the target.
To sum up, should ENISA be satisfied with its current state of IT Security? Why?
The process of ENISA is unable to save the state of information technology where there should
be a requirement to handle the capacities along with the growth of different issues in security
measure. The level of competition is that are based on number of attackers to handle the security
in cyber space along with protecting data. To completely get over with the number threats and
there is also proper adaptation towards the technology when the data can be stored properly
(Grobler et al, 2016). It is also crucial to ensure that are specific and proper level of precautions
that can accessed comfortably and hand for the sensitive level of data. It also requires saving the
firewall with blocking the access. The system of ENISA should also work on the powers with
various points that are for some level of quality and there is also requirement to function on the
securing the data with number of European commission to also ensure the control that can be
well presented for diverse motive and never impact the security of the company (Grobler et al,
2016).

ENISA BIG DATA SECURITY INFRASTRUCTURE 12
Reference
Buse, M. (2017). EUROPEAN UNION CYBER SECURITY IN A GLOBALIZED WORLD.
In International Scientific Conference" Strategies XXI" (Vol. 1, p. 159). " Carol I"
National Defence University.
César, J., & Debussche, J. (2017). Novel EU Legal Requirements in Big Data Security.
Chaudhuri, A. (2016). Internet of things data protection and privacy in the era of the General
Data Protection Regulation. Journal of Data Protection & Privacy, 1(1), 64-75.
Grobler, M., Jacobs, P., & van Niekerk, B. (2016). Cyber Security Centres for Threat Detection
and Mitigation. Threat Mitigation and Detection of Cyber Warfare and Terrorism
Activities, 21.
Jacobs, V., Bulters, J., & van Wieren, M. (2016, June). Modeling the Impact of Cyber Risk for
Major Dutch Organizations. In ECCWS2016-Proceedings fo the 15th European
Conference on Cyber Warfare and Security (p. 145). Academic Conferences and
publishing limited.
Leenen, L., & Meyer, T. (2016). Semantic technologies and big data analytics for cyber defence.
Olesen, N. (2016). European Public-Private Partnerships on Cybersecurity-An Instrument to
Support the Fight Against Cybercrime and Cyberterrorism. In Combatting Cybercrime
and Cyberterrorism (pp. 259-278). Springer International Publishing.
Rogers, R., Apeh, E., & Richardson, C. J. (2016, December). Resilience of the Internet of Things
(IoT) from an Information Assurance (IA) perspective. In Software, Knowledge,
Reference
Buse, M. (2017). EUROPEAN UNION CYBER SECURITY IN A GLOBALIZED WORLD.
In International Scientific Conference" Strategies XXI" (Vol. 1, p. 159). " Carol I"
National Defence University.
César, J., & Debussche, J. (2017). Novel EU Legal Requirements in Big Data Security.
Chaudhuri, A. (2016). Internet of things data protection and privacy in the era of the General
Data Protection Regulation. Journal of Data Protection & Privacy, 1(1), 64-75.
Grobler, M., Jacobs, P., & van Niekerk, B. (2016). Cyber Security Centres for Threat Detection
and Mitigation. Threat Mitigation and Detection of Cyber Warfare and Terrorism
Activities, 21.
Jacobs, V., Bulters, J., & van Wieren, M. (2016, June). Modeling the Impact of Cyber Risk for
Major Dutch Organizations. In ECCWS2016-Proceedings fo the 15th European
Conference on Cyber Warfare and Security (p. 145). Academic Conferences and
publishing limited.
Leenen, L., & Meyer, T. (2016). Semantic technologies and big data analytics for cyber defence.
Olesen, N. (2016). European Public-Private Partnerships on Cybersecurity-An Instrument to
Support the Fight Against Cybercrime and Cyberterrorism. In Combatting Cybercrime
and Cyberterrorism (pp. 259-278). Springer International Publishing.
Rogers, R., Apeh, E., & Richardson, C. J. (2016, December). Resilience of the Internet of Things
(IoT) from an Information Assurance (IA) perspective. In Software, Knowledge,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





