Comprehensive IT Risk Management Report: ENISA Big Data Security
VerifiedAdded on 2019/11/19
|14
|3571
|182
Report
AI Summary
This report provides a comprehensive analysis of IT risk management, specifically focusing on the challenges and threats associated with ENISA's big data infrastructure. The report begins with an overview of the ENISA case study, highlighting the importance of big data in modern applications and the associated security concerns. It then identifies and discusses the top threats, including data leaks, denial-of-service attacks, malicious software, and the use of unauthorized certificates, with a focus on the most significant threat. The report further examines threat agents, their potential impact, and the probability of occurrence, categorizing them as corporations, cybercriminals, cyber terrorists, script kiddies, employees, and nation states. It also proposes strategies for minimizing the impact of these threats, such as access control, data categorization, cryptographic functions, and network traffic monitoring. The report concludes with an overview of the current state of IT security, emphasizing the need for proactive measures to protect big data assets. The report provides a detailed analysis of the ENISA case study, offering insights into risk management processes and strategies for mitigating risks associated with big data technologies.

Running head: IT RISK MANAGEMENT
IT RISK MANAGEMENT
Name of the Student
Name of the University
Author Note
IT RISK MANAGEMENT
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT RISK MANAGEMENT
Table of Contents
Introduction................................................................................................................................2
1. Overview and ENISA big data Infrastructure........................................................................2
1.1 Overview..........................................................................................................................2
2. Top Threats associated with ENISA and their significance...................................................5
2.1. Most significant Threat...................................................................................................6
3. Threat agents, impact and threat probability..........................................................................7
3.1. Minimization of the Impact of the Threat.......................................................................8
3.2. Threat and Probability trends..........................................................................................9
4. Improving ETL process..........................................................................................................9
5. Current State of IT security..................................................................................................10
Conclusion................................................................................................................................10
References................................................................................................................................11
IT RISK MANAGEMENT
Table of Contents
Introduction................................................................................................................................2
1. Overview and ENISA big data Infrastructure........................................................................2
1.1 Overview..........................................................................................................................2
2. Top Threats associated with ENISA and their significance...................................................5
2.1. Most significant Threat...................................................................................................6
3. Threat agents, impact and threat probability..........................................................................7
3.1. Minimization of the Impact of the Threat.......................................................................8
3.2. Threat and Probability trends..........................................................................................9
4. Improving ETL process..........................................................................................................9
5. Current State of IT security..................................................................................................10
Conclusion................................................................................................................................10
References................................................................................................................................11

2
IT RISK MANAGEMENT
Introduction
The case study, which has been studied for the development of this report mainly,
deals with the issues concerned with the storage of huge amount of data, which is there to be
accesses by public for the use in their business. The proper use of a Big Data analysis and
storage server will be able to significantly benefit the organization. However, there are
several security issues present with the use and accessibility of big data that ultimately ends
with the cause of data breach and loss in data . The case study has been compiled to deal with
the threats and issues, which are faced by ENISA (Wu et al., 2014). The key threat agents of
ENISA has also been discussed in the case study. This report discusses the procedures to
implement to eliminate the threats from the data system and the various security issues
associated with ENISA (Inukollu, Arsi & Ravuri, 2014). The treat infrastructure of ENISA
and the key threat agents of the organization has also been discussed. A detailed analysis of
the ENISA case study has been discussed in the following sections.
1. Overview and ENISA big data Infrastructure
The following is a brief overview of the ENISA case study and provides an
infrastructure diagram of the ENISA:
1.1 Overview
The ENISA case study is focused on the broader topic of big data with the
implementation procedure and the threats associated with the use of big data. The rise in the
problems associated with the security and data breaches is a matter of huge concern in
today’s world and thus proper measures has to be taken to minimize such risks and breaches.
The case study deals with the different threats associated with the use of big data in today’s
technology and the significant roles, which are present in various aspects of the society
IT RISK MANAGEMENT
Introduction
The case study, which has been studied for the development of this report mainly,
deals with the issues concerned with the storage of huge amount of data, which is there to be
accesses by public for the use in their business. The proper use of a Big Data analysis and
storage server will be able to significantly benefit the organization. However, there are
several security issues present with the use and accessibility of big data that ultimately ends
with the cause of data breach and loss in data . The case study has been compiled to deal with
the threats and issues, which are faced by ENISA (Wu et al., 2014). The key threat agents of
ENISA has also been discussed in the case study. This report discusses the procedures to
implement to eliminate the threats from the data system and the various security issues
associated with ENISA (Inukollu, Arsi & Ravuri, 2014). The treat infrastructure of ENISA
and the key threat agents of the organization has also been discussed. A detailed analysis of
the ENISA case study has been discussed in the following sections.
1. Overview and ENISA big data Infrastructure
The following is a brief overview of the ENISA case study and provides an
infrastructure diagram of the ENISA:
1.1 Overview
The ENISA case study is focused on the broader topic of big data with the
implementation procedure and the threats associated with the use of big data. The rise in the
problems associated with the security and data breaches is a matter of huge concern in
today’s world and thus proper measures has to be taken to minimize such risks and breaches.
The case study deals with the different threats associated with the use of big data in today’s
technology and the significant roles, which are present in various aspects of the society
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IT RISK MANAGEMENT
(Wright & De Hert, 2012). For a large data driven economical business the use of big data is
of huge significance. In recent times big data has found its usage in the field of military
institutions to fight terrorism and in the field of research work. Thus, it can be said that the
technology offers a large number of advantages and can be considered a major source of data
and information. However the large source of information has been found to be exposed to a
number of threats and has also received attacks form subsequent threat agents (Gonzalez et
al., 2012). The systems associated with the big data can also be used in a wide range of
applications. The case study has been constructed to understand the different threats already
present in the system and the possible steps that can be taken to eliminate the threat agents
associated with the use of big data. The case study also provides an overview of the risk
management process and strategies for the elimination of the risks associated with the use of
the big data technology (Theoharidou et al., 2013). The case study emphasizes the cloud
storages as a major storage place for the big data. Cloud storage has always been considered
to be associated with different types of risks and problems which needs to be eliminated for
the safety of the data breach and for the minimization of data loss (Tan et al., 2014). The case
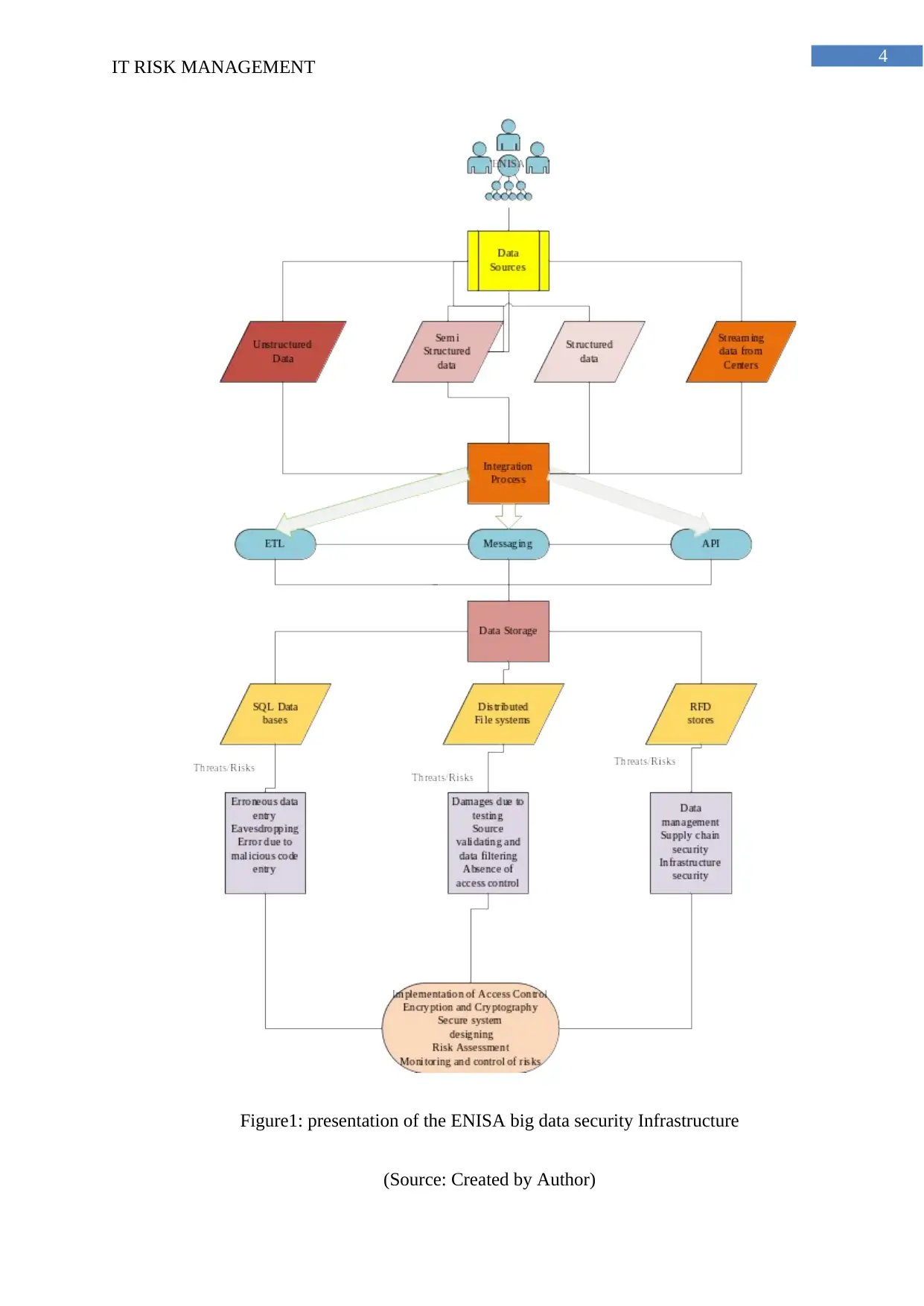
study also provides a detailed description of the infrastructure architecture of the big data
storage modules, which comprises of a high-leveled conceptual model. The prominent layers
in the big data architecture consists of the data sources, storage modules, computing models
and the presentation layers. The big data taxonomy discussed in the case study provides a
brief overview of the assets and the structure associated with big data (Theoharidou, Tsalis &
Gritzalis, 2013). The major components of any big data server is the analytics, data security
and the structure to be followed for the privacy of the data. The infrastructure of the ENISA
has been discussed below in the form of a diagram:
IT RISK MANAGEMENT
(Wright & De Hert, 2012). For a large data driven economical business the use of big data is
of huge significance. In recent times big data has found its usage in the field of military
institutions to fight terrorism and in the field of research work. Thus, it can be said that the
technology offers a large number of advantages and can be considered a major source of data
and information. However the large source of information has been found to be exposed to a
number of threats and has also received attacks form subsequent threat agents (Gonzalez et
al., 2012). The systems associated with the big data can also be used in a wide range of
applications. The case study has been constructed to understand the different threats already
present in the system and the possible steps that can be taken to eliminate the threat agents
associated with the use of big data. The case study also provides an overview of the risk
management process and strategies for the elimination of the risks associated with the use of
the big data technology (Theoharidou et al., 2013). The case study emphasizes the cloud
storages as a major storage place for the big data. Cloud storage has always been considered
to be associated with different types of risks and problems which needs to be eliminated for
the safety of the data breach and for the minimization of data loss (Tan et al., 2014). The case
study also provides a detailed description of the infrastructure architecture of the big data
storage modules, which comprises of a high-leveled conceptual model. The prominent layers
in the big data architecture consists of the data sources, storage modules, computing models
and the presentation layers. The big data taxonomy discussed in the case study provides a
brief overview of the assets and the structure associated with big data (Theoharidou, Tsalis &
Gritzalis, 2013). The major components of any big data server is the analytics, data security
and the structure to be followed for the privacy of the data. The infrastructure of the ENISA
has been discussed below in the form of a diagram:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
IT RISK MANAGEMENT
Figure1: presentation of the ENISA big data security Infrastructure
(Source: Created by Author)
IT RISK MANAGEMENT
Figure1: presentation of the ENISA big data security Infrastructure
(Source: Created by Author)

5
IT RISK MANAGEMENT
2. Top Threats associated with ENISA and their significance
Security threats gets associated with any form of data storage. Hackers try to launch
attacks on the data servers to gain access to a large amount of information (Seshardi et al.,
2012). The following is the list of top threats, which are associated with the ENISA data
servers:
1. Leak in data servers due to the use of unsecure APIs – big data servers are often built with
less amount of security measure, which makes the attack based on the use of unsecure
API causes data breaches. Direct injection of scripts are launched through the unsecured
API and therefore are considered one of the major threats in the big data implementation.
The assets, which are targeted by the hackers, are mainly big data analytics, computing
and software models (Pearson, 2013).
2. Lack in the designing of the security system of the big data servers can lead to a number
of threats. The breaches make the data sets are filed up with redundant data
representation, which makes the management of the data sources to be impossible. This
redundancy clouds the fact that if any kind of data had been stolen from the data set or
not. The targeted assets mainly include the applications and data from large organization
(Pearson, 2013).
3. Denial of service attack – the denial of service attack is mainly aimed at making the
available resources to be blocked by the use of unauthorized access into the system and
generating random requests to different pages. The acknowledgements congest out the
whole network and the network eventually breaks down. The attack also decreases the
performance of the system. They are mainly attacked on the servers and the network
which the organization is connected to (Pearson, 2013).
4. Malicious software and code activity – apart from all the threats that has been discussed
the attack-generated form a malicious software or a malicious code produces the greatest
IT RISK MANAGEMENT
2. Top Threats associated with ENISA and their significance
Security threats gets associated with any form of data storage. Hackers try to launch
attacks on the data servers to gain access to a large amount of information (Seshardi et al.,
2012). The following is the list of top threats, which are associated with the ENISA data
servers:
1. Leak in data servers due to the use of unsecure APIs – big data servers are often built with
less amount of security measure, which makes the attack based on the use of unsecure
API causes data breaches. Direct injection of scripts are launched through the unsecured
API and therefore are considered one of the major threats in the big data implementation.
The assets, which are targeted by the hackers, are mainly big data analytics, computing
and software models (Pearson, 2013).
2. Lack in the designing of the security system of the big data servers can lead to a number
of threats. The breaches make the data sets are filed up with redundant data
representation, which makes the management of the data sources to be impossible. This
redundancy clouds the fact that if any kind of data had been stolen from the data set or
not. The targeted assets mainly include the applications and data from large organization
(Pearson, 2013).
3. Denial of service attack – the denial of service attack is mainly aimed at making the
available resources to be blocked by the use of unauthorized access into the system and
generating random requests to different pages. The acknowledgements congest out the
whole network and the network eventually breaks down. The attack also decreases the
performance of the system. They are mainly attacked on the servers and the network
which the organization is connected to (Pearson, 2013).
4. Malicious software and code activity – apart from all the threats that has been discussed
the attack-generated form a malicious software or a malicious code produces the greatest
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
IT RISK MANAGEMENT
threat to the data server. This is due to the fat that the malicious code could be
programmed to do any kind of harm to the system without the knowledge of the user. The
threats come in the form of small files and programs, which initiate the working process
on its own and spreads throughput the network. These threats should be eliminated with
highest priority (Roberts, Indermaur & Spiranovic, 2013).
5. Using unauthorized certificates – generation of a set of unauthorized certificates and
using them to gain access to the network can lead to a significant amount of data breach
and data loss. They mainly target the software and hardware associated data (Roberts,
Indermaur & Spiranovic, 2013).
6. Eavesdropping of the network – intercepting the data flow in the network could lead to
the form of data breach. These include login credentials and back end services (Roberts,
Indermaur & Spiranovic, 2013).
7. Identity fraud – accessing of sensitive information while being posed as someone else can
be a form of data breach. This issue mainly deals with the loss in the personal
information.
2.1. Most significant Threat
Out of the threats discussed in the above section, the threats due to the use of
unauthorized certificates can be stated as the potential top threat in the big data server
scenario. This has been stated as the major threat because the data security officer who is in
charge of the whole system does not always check the use of certificates (Chen & Zhao,
2012). This causes the data breach to get unnoticed until it is thoroughly checked. Moreover,
the main target of this type of attack are the hardware and the software. These two are the
main components in the system. It they get compromised the whole data system is
compromised. The security manager should check this and proper measures should be
implemented to reduce the security risks (Pavlyushchik, 2014). The general target of these
IT RISK MANAGEMENT
threat to the data server. This is due to the fat that the malicious code could be
programmed to do any kind of harm to the system without the knowledge of the user. The
threats come in the form of small files and programs, which initiate the working process
on its own and spreads throughput the network. These threats should be eliminated with
highest priority (Roberts, Indermaur & Spiranovic, 2013).
5. Using unauthorized certificates – generation of a set of unauthorized certificates and
using them to gain access to the network can lead to a significant amount of data breach
and data loss. They mainly target the software and hardware associated data (Roberts,
Indermaur & Spiranovic, 2013).
6. Eavesdropping of the network – intercepting the data flow in the network could lead to
the form of data breach. These include login credentials and back end services (Roberts,
Indermaur & Spiranovic, 2013).
7. Identity fraud – accessing of sensitive information while being posed as someone else can
be a form of data breach. This issue mainly deals with the loss in the personal
information.
2.1. Most significant Threat
Out of the threats discussed in the above section, the threats due to the use of
unauthorized certificates can be stated as the potential top threat in the big data server
scenario. This has been stated as the major threat because the data security officer who is in
charge of the whole system does not always check the use of certificates (Chen & Zhao,
2012). This causes the data breach to get unnoticed until it is thoroughly checked. Moreover,
the main target of this type of attack are the hardware and the software. These two are the
main components in the system. It they get compromised the whole data system is
compromised. The security manager should check this and proper measures should be
implemented to reduce the security risks (Pavlyushchik, 2014). The general target of these
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IT RISK MANAGEMENT
type of attacks are the high profile companies and organizations. Big data has found
increasing use in modern technology and thus security protocols should be improvised
3. Threat agents, impact and threat probability
The major top threat agents that are associated with use of big data servers and the
threats probability of the situation is discussed in the following list:
1. Corporation – the major threat concern of nay organization is the security concern of the
big data in large corporation who target their competitors to gain knowledge of their
strategies. They steal information form their servers and use them to gain profit from the
loss of their competitors.
2. Cyber criminals- thee most dangerous threat with the security of the big data for all
organization is the threat from cyber criminals. They gain access to the big data servers
with the help of the network. They mainly do this to benefit from the financial point of
view. Thus proper intrusion management system can help in the elimination of such
threats (Taylor, Fritsch & Liederbach, 2014).
3. Cyber terrorist – cyber terrorist are very much similar to the cyber criminals with the only
difference between them is that they do not pertain to a small area of attack. Their range
of attack is wide spread. They mainly target important infrastructures like electricity
distribution plant and military bases. This would in turn cause a wide spread panic attack
on the nation.
4. Script kiddies – these are amateur hackers who has very little knowledge about the
working of a hacking system. They play with small scripts which they inject into the
network or the system and execute small attacks (Taylor, Fritsch & Liederbach, 2014).
5. Employees- working employees of an organization poses a serious threat for the
organization. They always get access to all the important document and information of
IT RISK MANAGEMENT
type of attacks are the high profile companies and organizations. Big data has found
increasing use in modern technology and thus security protocols should be improvised
3. Threat agents, impact and threat probability
The major top threat agents that are associated with use of big data servers and the
threats probability of the situation is discussed in the following list:
1. Corporation – the major threat concern of nay organization is the security concern of the
big data in large corporation who target their competitors to gain knowledge of their
strategies. They steal information form their servers and use them to gain profit from the
loss of their competitors.
2. Cyber criminals- thee most dangerous threat with the security of the big data for all
organization is the threat from cyber criminals. They gain access to the big data servers
with the help of the network. They mainly do this to benefit from the financial point of
view. Thus proper intrusion management system can help in the elimination of such
threats (Taylor, Fritsch & Liederbach, 2014).
3. Cyber terrorist – cyber terrorist are very much similar to the cyber criminals with the only
difference between them is that they do not pertain to a small area of attack. Their range
of attack is wide spread. They mainly target important infrastructures like electricity
distribution plant and military bases. This would in turn cause a wide spread panic attack
on the nation.
4. Script kiddies – these are amateur hackers who has very little knowledge about the
working of a hacking system. They play with small scripts which they inject into the
network or the system and execute small attacks (Taylor, Fritsch & Liederbach, 2014).
5. Employees- working employees of an organization poses a serious threat for the
organization. They always get access to all the important document and information of

8
IT RISK MANAGEMENT
the organization and thus can launch an attack silently by leaking out sensitive
information to the hackers who would benefit from the details.
6. Nation states – these are by far the most dangerous type of threat agent in the world. They
have all types of resources in their hand and can launch an attack on any of the other
nations without the nation even knowing about it. They are highly skilled and have the
best tools at their dispose (Taylor, Fritsch & Liederbach, 2014).
3.1. Minimization of the Impact of the Threat
To minimize the threats in the organization the following steps can be followed:
Have an authorized access control for all the information present in the data server of the
organization. As the storage of the informations are done on a cloud-based server, the
information should be categorized into level wise distribution. This would enable the
monitoring of the information easy for the security experts.
Enabling of the use of cryptographic functions to store data in the server and during the
transmission of data within the organizations network system. Use of proper
cryptographic functions will disable the hackers from knowing the content of the
information even if they are able to take out packets from the network stream.
Implementation of better and innovative network systems in the organization would help
them to control the inflow and outflow of the network traffic. Adding a network packet
checker in the data stream of the organization will help them to monitor which is the
unrequired packet that is being shared by the employees of the organization.
Scheduled training of the training staff of the organization is important to make them
understand the working procedure of the organization. They should be made known that
keeping the information of the organization safe from the hands of the hackers is the top
most priority.
IT RISK MANAGEMENT
the organization and thus can launch an attack silently by leaking out sensitive
information to the hackers who would benefit from the details.
6. Nation states – these are by far the most dangerous type of threat agent in the world. They
have all types of resources in their hand and can launch an attack on any of the other
nations without the nation even knowing about it. They are highly skilled and have the
best tools at their dispose (Taylor, Fritsch & Liederbach, 2014).
3.1. Minimization of the Impact of the Threat
To minimize the threats in the organization the following steps can be followed:
Have an authorized access control for all the information present in the data server of the
organization. As the storage of the informations are done on a cloud-based server, the
information should be categorized into level wise distribution. This would enable the
monitoring of the information easy for the security experts.
Enabling of the use of cryptographic functions to store data in the server and during the
transmission of data within the organizations network system. Use of proper
cryptographic functions will disable the hackers from knowing the content of the
information even if they are able to take out packets from the network stream.
Implementation of better and innovative network systems in the organization would help
them to control the inflow and outflow of the network traffic. Adding a network packet
checker in the data stream of the organization will help them to monitor which is the
unrequired packet that is being shared by the employees of the organization.
Scheduled training of the training staff of the organization is important to make them
understand the working procedure of the organization. They should be made known that
keeping the information of the organization safe from the hands of the hackers is the top
most priority.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT RISK MANAGEMENT
3.2. Threat and Probability trends
The different threats that is associated with the use of big data servers and technology
as attackers are planning new ways to attack the data servers in order to steal the data from
the organizations. The threats and the probability of them occurring in the system needs to be
reduced by the organization or they might suffer a huge loss of information and profit.
Different security measures can be taken up by the organization to safe guard the data
servers. For the complete elimination of the threats, the root cause of all these problems must
be found and attended to.
4. Improving ETL process
The ENISA threat landscape or ETL has discussed about the different threats that is
associated with the organization. The repost has a specific topic of discussion mainly the
threats, which is associated with the information technology used by the organization
(ENISA, 2017). The major drawback of the report is that there is only discussion about the
threats, which is associated with the big data servers and the data sets. It is advisable to
include a more detailed structure and information about the different risks, which has evolved
over time. The ETL can be improved with the addition of different threats already associated
with the big data servers and its mitigation remedies. The ENISA can follow the following
recommendation to improve their ETL-
Storing of any kind of small information, which may be useful during the documentation
process (ENISA, 2017).
Load data into the system systematically. However, it would take longer than usual, but
would help in able to store the complete set of data without any mistakes.
IT RISK MANAGEMENT
3.2. Threat and Probability trends
The different threats that is associated with the use of big data servers and technology
as attackers are planning new ways to attack the data servers in order to steal the data from
the organizations. The threats and the probability of them occurring in the system needs to be
reduced by the organization or they might suffer a huge loss of information and profit.
Different security measures can be taken up by the organization to safe guard the data
servers. For the complete elimination of the threats, the root cause of all these problems must
be found and attended to.
4. Improving ETL process
The ENISA threat landscape or ETL has discussed about the different threats that is
associated with the organization. The repost has a specific topic of discussion mainly the
threats, which is associated with the information technology used by the organization
(ENISA, 2017). The major drawback of the report is that there is only discussion about the
threats, which is associated with the big data servers and the data sets. It is advisable to
include a more detailed structure and information about the different risks, which has evolved
over time. The ETL can be improved with the addition of different threats already associated
with the big data servers and its mitigation remedies. The ENISA can follow the following
recommendation to improve their ETL-
Storing of any kind of small information, which may be useful during the documentation
process (ENISA, 2017).
Load data into the system systematically. However, it would take longer than usual, but
would help in able to store the complete set of data without any mistakes.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT RISK MANAGEMENT
The organization should move onto use the Apache Hadoop software which provides a
set of tools useful for the implementation of the data analysis and to understand the data
that has already been collected (Cherdantseva et al,. 2016).
5. Current State of IT security
The ENISA organization has been found to be not satisfied with the information
structure that they are following. Threats associated with the security system still pertains to
the same level (Von Solms & Van Niekerk, 2013). The security features of the organization
needs to be upgraded and different features and protocols needs to be included in the system
to keep the data safe form the hands of the hackers. The report has discussed a number of
different security measures, which can be implemented. One of the major threat that is
associated with the use of big data servers is that the redundancy of information is not always
checked. This could help in reducing the storage space, which in turn would make the
management of the information easy (Albakri et al., 2014). The use of unsecured API also
should be avoided with highest priority. Moreover, to be on the safe side proper intrusion
detection system should also be implemented into the system to have an extra layer of
security.
Conclusion
Form the above discussion it can be started that the ENISA big data infrastructure
should go under the thorough checking of the security protocols and the measures that has
already been taken in the organization. The report has identified major threats that are
associated with the big data system. The report also suggests the different techniques that are
used for the minimization of the risks. Big data has found increasing use in modern
technology and thus security protocols should be improvised.
IT RISK MANAGEMENT
The organization should move onto use the Apache Hadoop software which provides a
set of tools useful for the implementation of the data analysis and to understand the data
that has already been collected (Cherdantseva et al,. 2016).
5. Current State of IT security
The ENISA organization has been found to be not satisfied with the information
structure that they are following. Threats associated with the security system still pertains to
the same level (Von Solms & Van Niekerk, 2013). The security features of the organization
needs to be upgraded and different features and protocols needs to be included in the system
to keep the data safe form the hands of the hackers. The report has discussed a number of
different security measures, which can be implemented. One of the major threat that is
associated with the use of big data servers is that the redundancy of information is not always
checked. This could help in reducing the storage space, which in turn would make the
management of the information easy (Albakri et al., 2014). The use of unsecured API also
should be avoided with highest priority. Moreover, to be on the safe side proper intrusion
detection system should also be implemented into the system to have an extra layer of
security.
Conclusion
Form the above discussion it can be started that the ENISA big data infrastructure
should go under the thorough checking of the security protocols and the measures that has
already been taken in the organization. The report has identified major threats that are
associated with the big data system. The report also suggests the different techniques that are
used for the minimization of the risks. Big data has found increasing use in modern
technology and thus security protocols should be improvised.

11
IT RISK MANAGEMENT
References
Albakri, S. H., Shanmugam, B., Samy, G. N., Idris, N. B., & Ahmed, A. (2014). Security risk
assessment framework for cloud computing environments. Security and
Communication Networks, 7(11), 2114-2124.
Big Data Threat Landscape — ENISA. (2017). Enisa.europa.eu. Retrieved 6 September
2017, from https://www.enisa.europa.eu/publications/bigdata-threat-landscape
Brucker, A. D., Hang, I., Lückemeyer, G., & Ruparel, R. (2012, June). SecureBPMN:
Modeling and enforcing access control requirements in business processes. In
Proceedings of the 17th ACM symposium on Access Control Models and
Technologies (pp. 123-126). ACM.
Chen, D., & Zhao, H. (2012, March). Data security and privacy protection issues in cloud
computing. In Computer Science and Electronics Engineering (ICCSEE), 2012
International Conference on (Vol. 1, pp. 647-651). IEEE.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H., & Stoddart, K.
(2016). A review of cyber security risk assessment methods for SCADA systems.
computers & security, 56, 1-27.
Gonzalez, N., Miers, C., Redigolo, F., Simplicio, M., Carvalho, T., Näslund, M., &
Pourzandi, M. (2012). A quantitative analysis of current security concerns and
solutions for cloud computing. Journal of Cloud Computing: Advances, Systems and
Applications, 1(1), 11.
IT RISK MANAGEMENT
References
Albakri, S. H., Shanmugam, B., Samy, G. N., Idris, N. B., & Ahmed, A. (2014). Security risk
assessment framework for cloud computing environments. Security and
Communication Networks, 7(11), 2114-2124.
Big Data Threat Landscape — ENISA. (2017). Enisa.europa.eu. Retrieved 6 September
2017, from https://www.enisa.europa.eu/publications/bigdata-threat-landscape
Brucker, A. D., Hang, I., Lückemeyer, G., & Ruparel, R. (2012, June). SecureBPMN:
Modeling and enforcing access control requirements in business processes. In
Proceedings of the 17th ACM symposium on Access Control Models and
Technologies (pp. 123-126). ACM.
Chen, D., & Zhao, H. (2012, March). Data security and privacy protection issues in cloud
computing. In Computer Science and Electronics Engineering (ICCSEE), 2012
International Conference on (Vol. 1, pp. 647-651). IEEE.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H., & Stoddart, K.
(2016). A review of cyber security risk assessment methods for SCADA systems.
computers & security, 56, 1-27.
Gonzalez, N., Miers, C., Redigolo, F., Simplicio, M., Carvalho, T., Näslund, M., &
Pourzandi, M. (2012). A quantitative analysis of current security concerns and
solutions for cloud computing. Journal of Cloud Computing: Advances, Systems and
Applications, 1(1), 11.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





