Risk Analysis and Security in Big Data: ENISA Case Study Report
VerifiedAdded on 2019/11/20
|17
|3802
|351
Report
AI Summary
This report provides a comprehensive analysis of the ENISA case study, focusing on risk analysis and security within its big data infrastructure. It begins with an overview of the ENISA case study and presents a diagram illustrating the big data security infrastructure. The report then delves into the top threats faced by ENISA, categorizing them and providing examples. Key threat agents, such as technological vulnerabilities, human errors, and design flaws, are identified, along with potential impact reduction options. The report also discusses the improvement of the ETL (Extract, Transform, Load) process and justifies the importance of IT security within ENISA. The analysis covers various aspects of big data security, including data sources, storage, analytics, and presentation layers, along with the security functions and protocols employed. The report concludes by emphasizing the significance of proactive risk management and security measures in the context of big data operations.

Running head: RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
Risk Analysis and Security: ENISA case study
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Risk Analysis and Security: ENISA case study
Name of the Student:
Student ID:
Name of the University:
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
Table of Contents
Introduction......................................................................................................................................2
1. Scenario and diagram of Big Data security infrastructure...........................................................2
1.1 Overview of ENISA case study.................................................................................................2
1.2 ENISA Big Data Security Infrastructure Diagram....................................................................3
2. Explanation of the Top Threat in the ENISA..............................................................................7
3. Key Threat Agents and their Impact Reduction Options.............................................................9
4. Improvement of ETL process....................................................................................................12
5. Justification of IT security in ENISA........................................................................................13
Conclusion.....................................................................................................................................13
References......................................................................................................................................14
Table of Contents
Introduction......................................................................................................................................2
1. Scenario and diagram of Big Data security infrastructure...........................................................2
1.1 Overview of ENISA case study.................................................................................................2
1.2 ENISA Big Data Security Infrastructure Diagram....................................................................3
2. Explanation of the Top Threat in the ENISA..............................................................................7
3. Key Threat Agents and their Impact Reduction Options.............................................................9
4. Improvement of ETL process....................................................................................................12
5. Justification of IT security in ENISA........................................................................................13
Conclusion.....................................................................................................................................13
References......................................................................................................................................14

2RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
Introduction
Risk analysis as well as security is considered as crucial for enterprises in order to deploy
effective operations along with integration of development of the system. In this perspective,
development of the project would assist to integrate the process of development of operations as
well as apply effective functions within the particular organization. Moreover, operational
processing can be implied in order to form analysis risks associated with the organization. The
operational processing can be implied in order to form analysis of risks might be faced by the
organizations at the time of performing operations as well as functions based on development of
operations for integration of functions for procedures of the enterprise.
The report would assist the process of integrating the functions and operations of the
organization in order to develop risk assessment as well as analysis. In addition, it would tend
evaluating the role of technology for implementation of effective risk through analysing the case
study of ENISA. Practicing big data strategy would enhance operations within the organization.
On the other hand, the use of big data in the organization has identified the issues as well as
threats of security for the enterprise. Thus, analysis of threats of Big data strategy for ENISA
would describe agents of threats.
1. Scenario and diagram of Big Data security infrastructure
1.1 Overview of ENISA case study
The organization had implemented big data analytics in order to develop effective
operations as well as growth of the organization. ENISA implied big data strategy inside the
organization in order to gain competitive advantages. In this perspective, risks as well as threat
management need to be implied for developing effective growth of operations. Big data threats
Introduction
Risk analysis as well as security is considered as crucial for enterprises in order to deploy
effective operations along with integration of development of the system. In this perspective,
development of the project would assist to integrate the process of development of operations as
well as apply effective functions within the particular organization. Moreover, operational
processing can be implied in order to form analysis risks associated with the organization. The
operational processing can be implied in order to form analysis of risks might be faced by the
organizations at the time of performing operations as well as functions based on development of
operations for integration of functions for procedures of the enterprise.
The report would assist the process of integrating the functions and operations of the
organization in order to develop risk assessment as well as analysis. In addition, it would tend
evaluating the role of technology for implementation of effective risk through analysing the case
study of ENISA. Practicing big data strategy would enhance operations within the organization.
On the other hand, the use of big data in the organization has identified the issues as well as
threats of security for the enterprise. Thus, analysis of threats of Big data strategy for ENISA
would describe agents of threats.
1. Scenario and diagram of Big Data security infrastructure
1.1 Overview of ENISA case study
The organization had implemented big data analytics in order to develop effective
operations as well as growth of the organization. ENISA implied big data strategy inside the
organization in order to gain competitive advantages. In this perspective, risks as well as threat
management need to be implied for developing effective growth of operations. Big data threats
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
would result in development of occasional threats for ENISA in integrating the system within the
organization. The enterprise is considered as one of the effective operation system, which is
capable monitoring flow of the operations within the enterprise as well as imply efficient security
system inside the enterprise(Chen, Mao& Liu, 2014). However, privacy in big data is considered
as major factor playing a crucial role in implantation of development model for ENISA. In this
perspective, operations of the enterprise would be highly enhanced through utilization of big data
strategy inside the organization.
On the other hand, ENSIA had applied ICT solutions improving security functions in
order to manage big data strategy in the enterprise (Demchenko et al.,2013).Various owners are
providing various models for the transformation of the ICT devices in the organisation including
data owners, data transformers and computation(Kshetri, 2014). These models helps in providing
effective management if the data and security to the data and information. There are various
practices that are analytics in the organisation for managing threat and management of data used
y the organisation. The process of operating in the organizations implied in the risk management
for acquiring the security of information and data in the organisation. Therefore, the
development of the risk management assessment helps in maintaining security of data as well as
information in the enterprise.
1.2 ENISA Big Data Security Infrastructure Diagram
The framework of the ENISA has been properly structured of operating effectively in the
big data strategy. Therefore, the big data infrastructure helped in maintaining the data sources,
data storage and analytics with computing models under the presentation layer. In addition, the
would result in development of occasional threats for ENISA in integrating the system within the
organization. The enterprise is considered as one of the effective operation system, which is
capable monitoring flow of the operations within the enterprise as well as imply efficient security
system inside the enterprise(Chen, Mao& Liu, 2014). However, privacy in big data is considered
as major factor playing a crucial role in implantation of development model for ENISA. In this
perspective, operations of the enterprise would be highly enhanced through utilization of big data
strategy inside the organization.
On the other hand, ENSIA had applied ICT solutions improving security functions in
order to manage big data strategy in the enterprise (Demchenko et al.,2013).Various owners are
providing various models for the transformation of the ICT devices in the organisation including
data owners, data transformers and computation(Kshetri, 2014). These models helps in providing
effective management if the data and security to the data and information. There are various
practices that are analytics in the organisation for managing threat and management of data used
y the organisation. The process of operating in the organizations implied in the risk management
for acquiring the security of information and data in the organisation. Therefore, the
development of the risk management assessment helps in maintaining security of data as well as
information in the enterprise.
1.2 ENISA Big Data Security Infrastructure Diagram
The framework of the ENISA has been properly structured of operating effectively in the
big data strategy. Therefore, the big data infrastructure helped in maintaining the data sources,
data storage and analytics with computing models under the presentation layer. In addition, the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
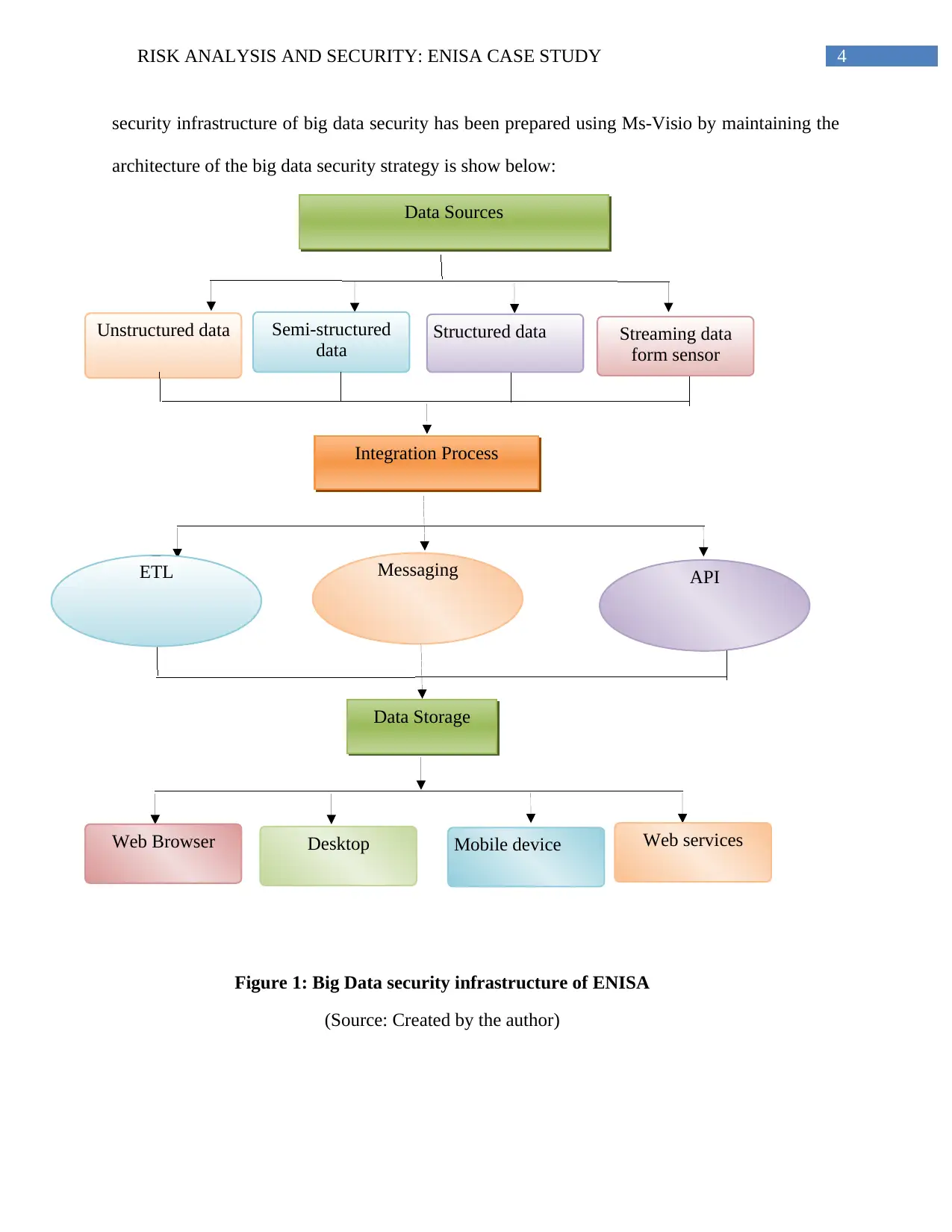
4RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
security infrastructure of big data security has been prepared using Ms-Visio by maintaining the
architecture of the big data security strategy is show below:
Data Sources
Unstructured data Semi-structured
data
Structured data Streaming data
form sensor
Integration Process
ETL Messaging API
Data Storage
Desktop Web servicesWeb Browser Mobile device
Figure 1: Big Data security infrastructure of ENISA
(Source: Created by the author)
security infrastructure of big data security has been prepared using Ms-Visio by maintaining the
architecture of the big data security strategy is show below:
Data Sources
Unstructured data Semi-structured
data
Structured data Streaming data
form sensor
Integration Process
ETL Messaging API
Data Storage
Desktop Web servicesWeb Browser Mobile device
Figure 1: Big Data security infrastructure of ENISA
(Source: Created by the author)
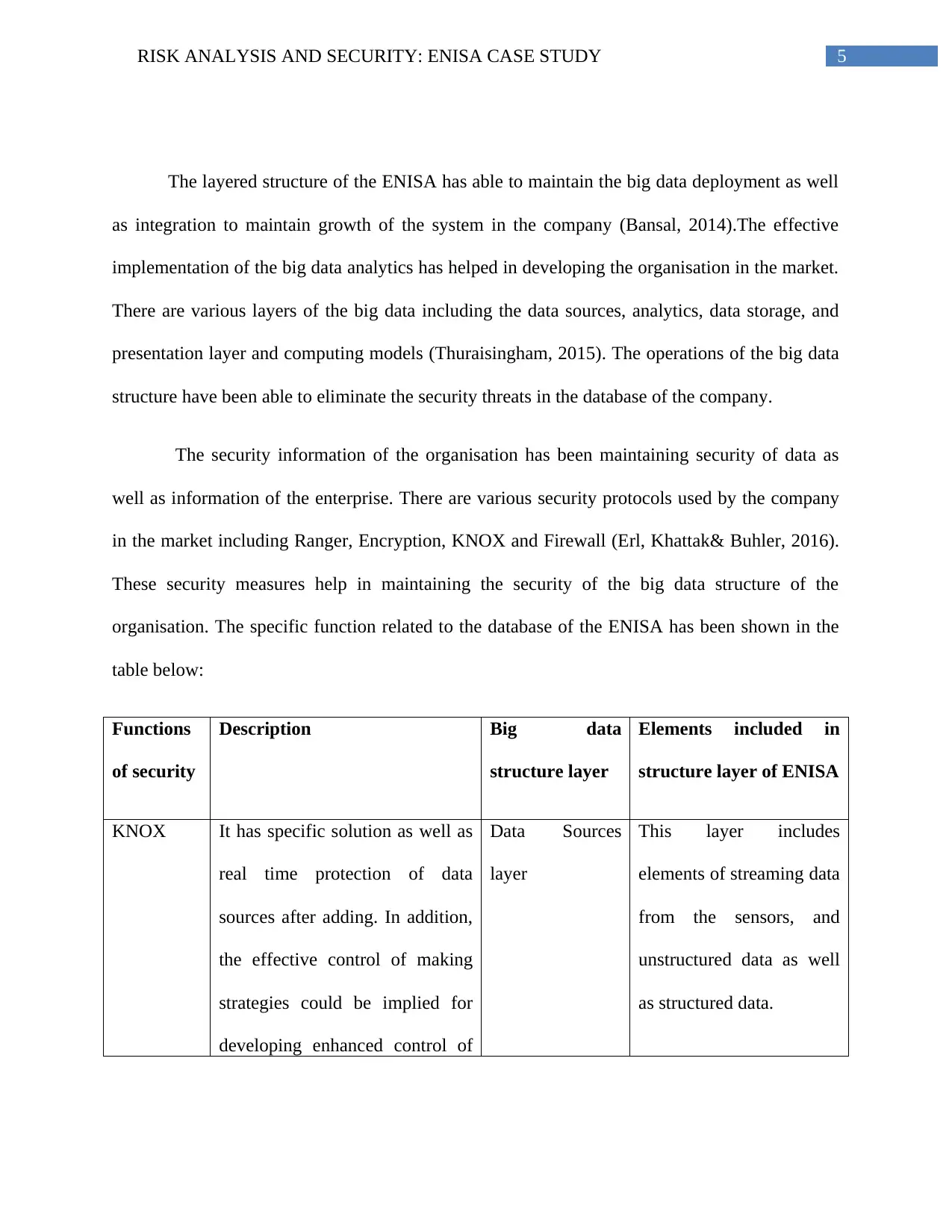
5RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
The layered structure of the ENISA has able to maintain the big data deployment as well
as integration to maintain growth of the system in the company (Bansal, 2014).The effective
implementation of the big data analytics has helped in developing the organisation in the market.
There are various layers of the big data including the data sources, analytics, data storage, and
presentation layer and computing models (Thuraisingham, 2015). The operations of the big data
structure have been able to eliminate the security threats in the database of the company.
The security information of the organisation has been maintaining security of data as
well as information of the enterprise. There are various security protocols used by the company
in the market including Ranger, Encryption, KNOX and Firewall (Erl, Khattak& Buhler, 2016).
These security measures help in maintaining the security of the big data structure of the
organisation. The specific function related to the database of the ENISA has been shown in the
table below:
Functions
of security
Description Big data
structure layer
Elements included in
structure layer of ENISA
KNOX It has specific solution as well as
real time protection of data
sources after adding. In addition,
the effective control of making
strategies could be implied for
developing enhanced control of
Data Sources
layer
This layer includes
elements of streaming data
from the sensors, and
unstructured data as well
as structured data.
The layered structure of the ENISA has able to maintain the big data deployment as well
as integration to maintain growth of the system in the company (Bansal, 2014).The effective
implementation of the big data analytics has helped in developing the organisation in the market.
There are various layers of the big data including the data sources, analytics, data storage, and
presentation layer and computing models (Thuraisingham, 2015). The operations of the big data
structure have been able to eliminate the security threats in the database of the company.
The security information of the organisation has been maintaining security of data as
well as information of the enterprise. There are various security protocols used by the company
in the market including Ranger, Encryption, KNOX and Firewall (Erl, Khattak& Buhler, 2016).
These security measures help in maintaining the security of the big data structure of the
organisation. The specific function related to the database of the ENISA has been shown in the
table below:
Functions
of security
Description Big data
structure layer
Elements included in
structure layer of ENISA
KNOX It has specific solution as well as
real time protection of data
sources after adding. In addition,
the effective control of making
strategies could be implied for
developing enhanced control of
Data Sources
layer
This layer includes
elements of streaming data
from the sensors, and
unstructured data as well
as structured data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
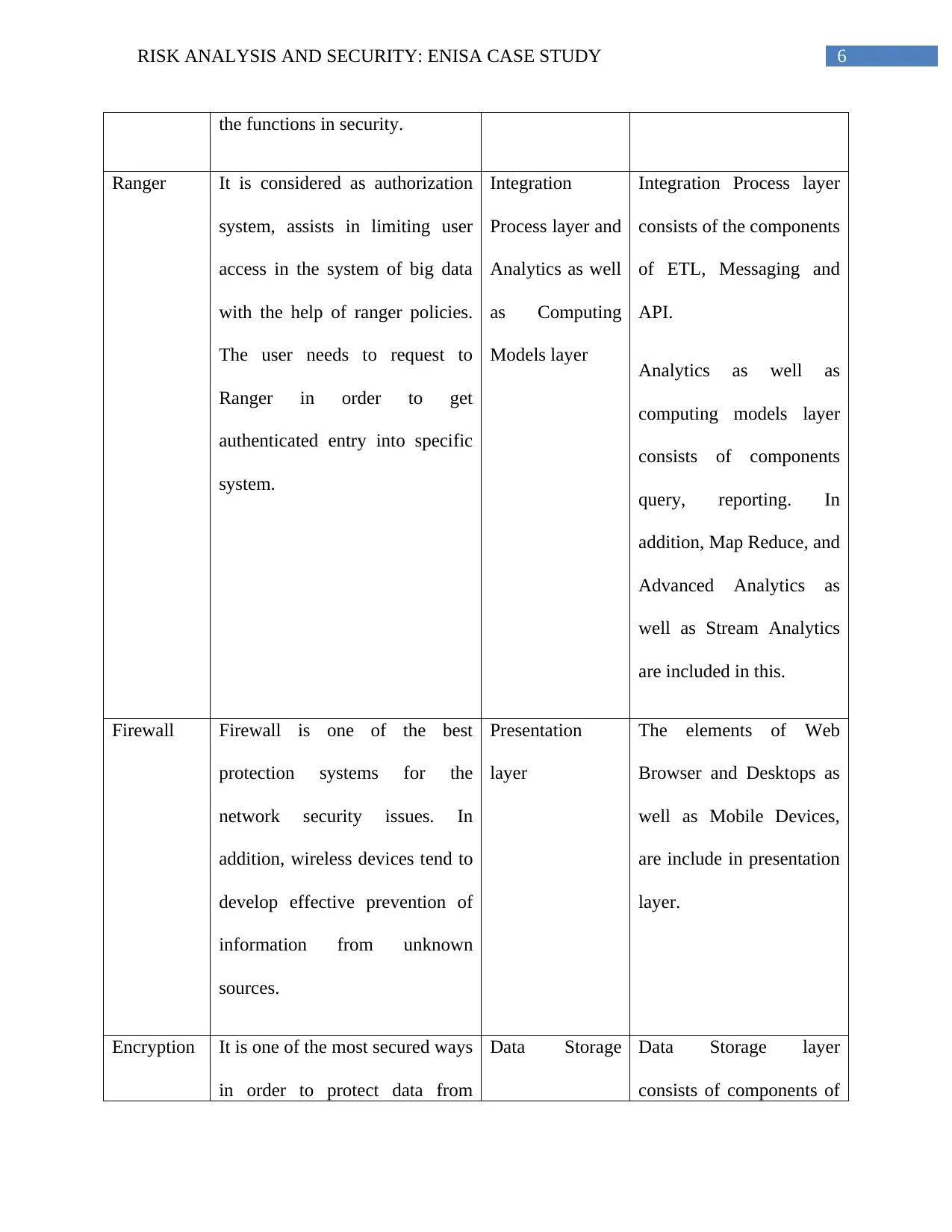
6RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
the functions in security.
Ranger It is considered as authorization
system, assists in limiting user
access in the system of big data
with the help of ranger policies.
The user needs to request to
Ranger in order to get
authenticated entry into specific
system.
Integration
Process layer and
Analytics as well
as Computing
Models layer
Integration Process layer
consists of the components
of ETL, Messaging and
API.
Analytics as well as
computing models layer
consists of components
query, reporting. In
addition, Map Reduce, and
Advanced Analytics as
well as Stream Analytics
are included in this.
Firewall Firewall is one of the best
protection systems for the
network security issues. In
addition, wireless devices tend to
develop effective prevention of
information from unknown
sources.
Presentation
layer
The elements of Web
Browser and Desktops as
well as Mobile Devices,
are include in presentation
layer.
Encryption It is one of the most secured ways
in order to protect data from
Data Storage Data Storage layer
consists of components of
the functions in security.
Ranger It is considered as authorization
system, assists in limiting user
access in the system of big data
with the help of ranger policies.
The user needs to request to
Ranger in order to get
authenticated entry into specific
system.
Integration
Process layer and
Analytics as well
as Computing
Models layer
Integration Process layer
consists of the components
of ETL, Messaging and
API.
Analytics as well as
computing models layer
consists of components
query, reporting. In
addition, Map Reduce, and
Advanced Analytics as
well as Stream Analytics
are included in this.
Firewall Firewall is one of the best
protection systems for the
network security issues. In
addition, wireless devices tend to
develop effective prevention of
information from unknown
sources.
Presentation
layer
The elements of Web
Browser and Desktops as
well as Mobile Devices,
are include in presentation
layer.
Encryption It is one of the most secured ways
in order to protect data from
Data Storage Data Storage layer
consists of components of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
unknown as well as
unauthenticated source. In this
perspective, the data would be
modified utilizing cryptography
technique so that it becomes
useless for different users.
layer No/New SQL databases
and Distributed File
System as well as RDF
stores
Table 1: Various Security functions for ENISA Big Data System
(Source: Bansal &Kagemann, 2015)
2. Explanation of the Top Threat in the ENISA
The threats to the ENISA big data strategy of the company have been depicted by the
accidental threats, technological threats, threats to the organisation and different legal treats.
These types of threats are very common in the organisation (Lu et al., 2014). Therefore, there are
various strategies made to mitigate these issues in the organisation. The hindrance to the normal
management of the company has been maintained by the operations in the market (Baumer,
2017). There are various risks and threats for the ENISA has been provided in the tabular format
below:
Threat Types Examples of the Risk Classification
Accidental Threats Some examples of accidental threats are considered as
destruction of records as well as leaks of data through web
application and loss of device along with of sensitive data as
well as loss of cloud information. In addition, penetration and
unknown as well as
unauthenticated source. In this
perspective, the data would be
modified utilizing cryptography
technique so that it becomes
useless for different users.
layer No/New SQL databases
and Distributed File
System as well as RDF
stores
Table 1: Various Security functions for ENISA Big Data System
(Source: Bansal &Kagemann, 2015)
2. Explanation of the Top Threat in the ENISA
The threats to the ENISA big data strategy of the company have been depicted by the
accidental threats, technological threats, threats to the organisation and different legal treats.
These types of threats are very common in the organisation (Lu et al., 2014). Therefore, there are
various strategies made to mitigate these issues in the organisation. The hindrance to the normal
management of the company has been maintained by the operations in the market (Baumer,
2017). There are various risks and threats for the ENISA has been provided in the tabular format
below:
Threat Types Examples of the Risk Classification
Accidental Threats Some examples of accidental threats are considered as
destruction of records as well as leaks of data through web
application and loss of device along with of sensitive data as
well as loss of cloud information. In addition, penetration and
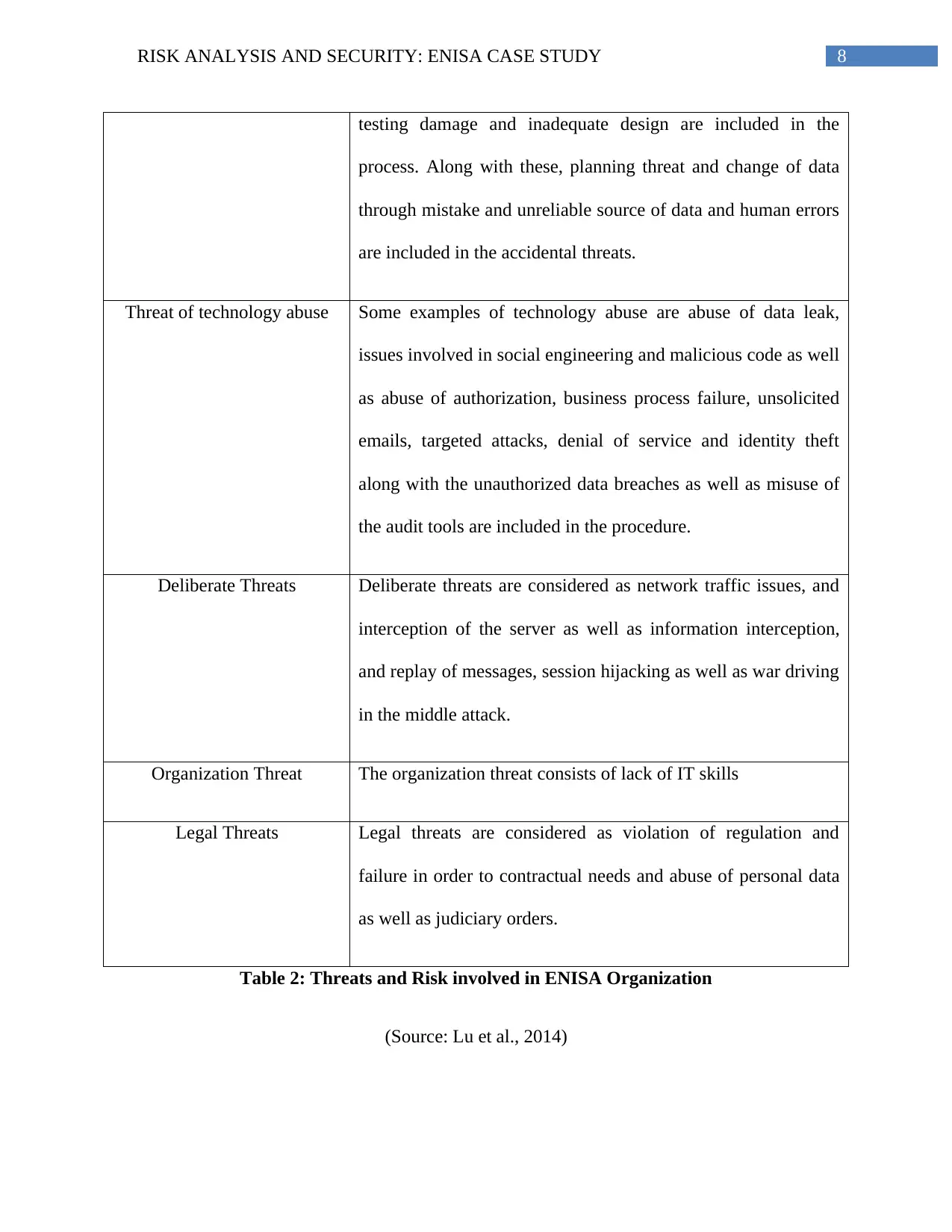
8RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
testing damage and inadequate design are included in the
process. Along with these, planning threat and change of data
through mistake and unreliable source of data and human errors
are included in the accidental threats.
Threat of technology abuse Some examples of technology abuse are abuse of data leak,
issues involved in social engineering and malicious code as well
as abuse of authorization, business process failure, unsolicited
emails, targeted attacks, denial of service and identity theft
along with the unauthorized data breaches as well as misuse of
the audit tools are included in the procedure.
Deliberate Threats Deliberate threats are considered as network traffic issues, and
interception of the server as well as information interception,
and replay of messages, session hijacking as well as war driving
in the middle attack.
Organization Threat The organization threat consists of lack of IT skills
Legal Threats Legal threats are considered as violation of regulation and
failure in order to contractual needs and abuse of personal data
as well as judiciary orders.
Table 2: Threats and Risk involved in ENISA Organization
(Source: Lu et al., 2014)
testing damage and inadequate design are included in the
process. Along with these, planning threat and change of data
through mistake and unreliable source of data and human errors
are included in the accidental threats.
Threat of technology abuse Some examples of technology abuse are abuse of data leak,
issues involved in social engineering and malicious code as well
as abuse of authorization, business process failure, unsolicited
emails, targeted attacks, denial of service and identity theft
along with the unauthorized data breaches as well as misuse of
the audit tools are included in the procedure.
Deliberate Threats Deliberate threats are considered as network traffic issues, and
interception of the server as well as information interception,
and replay of messages, session hijacking as well as war driving
in the middle attack.
Organization Threat The organization threat consists of lack of IT skills
Legal Threats Legal threats are considered as violation of regulation and
failure in order to contractual needs and abuse of personal data
as well as judiciary orders.
Table 2: Threats and Risk involved in ENISA Organization
(Source: Lu et al., 2014)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
The threat technology is a critical threat for the company in the market. The threats to the
big data analysis in the company have been a major threat for the company the market. The
threat of technology includes leak of information, brute force, and failure of business failures,
authorisation abuse and malicious code generation in the company. These threats can be also
categorised by targeted attacks, fraud, and email hacking and identity theft in the company.
Therefore, there are several strategies prepared for maintaining the security from these threats on
the company. The threat technology abuse has been the most critical threat for the ENISA in the
market (Chen & Zhang, 2014). The cyber world has been suffered from this threat all over the
world. The lea of the information has caused much loss to the company in the market. The
sensitivity if the data and information has been proactive in the company that have caused threats
to the data and information of the organization in the market. The unauthorised access to the
database of the company has been causing the loss of data of the organization in the market.
3. Key Threat Agents and their Impact Reduction Options
The technological abuse threat in the ENISA has been depicted by the leak if the
information, social engineering issues, brute force, denial of service, targeted attacks and
manipulation of information in the company (Kim, Trimi& Chung, 2014). The key threats of the
ENISA are Human errors, personal gain, designing errors and technology. These agents help in
the deployment of the hindrances and detection of threat developing extortion of the procedure as
well as enhancement of the issues in the enterprise.
Technology
The technology is considered as important factor in the growth of the effective operations
in the ENISA. The improvement in the technological domain of the company might help in
The threat technology is a critical threat for the company in the market. The threats to the
big data analysis in the company have been a major threat for the company the market. The
threat of technology includes leak of information, brute force, and failure of business failures,
authorisation abuse and malicious code generation in the company. These threats can be also
categorised by targeted attacks, fraud, and email hacking and identity theft in the company.
Therefore, there are several strategies prepared for maintaining the security from these threats on
the company. The threat technology abuse has been the most critical threat for the ENISA in the
market (Chen & Zhang, 2014). The cyber world has been suffered from this threat all over the
world. The lea of the information has caused much loss to the company in the market. The
sensitivity if the data and information has been proactive in the company that have caused threats
to the data and information of the organization in the market. The unauthorised access to the
database of the company has been causing the loss of data of the organization in the market.
3. Key Threat Agents and their Impact Reduction Options
The technological abuse threat in the ENISA has been depicted by the leak if the
information, social engineering issues, brute force, denial of service, targeted attacks and
manipulation of information in the company (Kim, Trimi& Chung, 2014). The key threats of the
ENISA are Human errors, personal gain, designing errors and technology. These agents help in
the deployment of the hindrances and detection of threat developing extortion of the procedure as
well as enhancement of the issues in the enterprise.
Technology
The technology is considered as important factor in the growth of the effective operations
in the ENISA. The improvement in the technological domain of the company might help in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
securing the data and information of the organization in the market. The technological
deployment of the leak of information in the organisation has able to maintain the diplomacy of
the strategies (Wu et al., 2014). The implication of the technological issues in the company has
provided influential development in the effective flow of operation s in the company. The
identified technological issues in the company has been properly analysed for the finding the
strategies to mitigate them.
Human Errors
The human errors are the major factors in the form of the hindrances in the company. The
system-integrated operations have able to manage the security risks involved in the management
of the company (Patil & Seshadri, 2014). The errors that are made by the human cohesiveness
are creating issues for the company. There are various human errors including information
interception, replay if messages, hijacking, unauthorised data breaches and manipulation of
hardware. The human including the employees and other staffs of the company manipulates
these errors.
Designing Errors
The designing errors are depicted for systematic faults in the enterprise. These designing
errors are confirmed by the implication of operational processing. These errors are prepared for
the critical evaluation for the development of the organisation. Therefore, the business operations
are reliable to the management of the company. For example, threat in planning, change of data,
unreliable sources of information and failure in the business process.
securing the data and information of the organization in the market. The technological
deployment of the leak of information in the organisation has able to maintain the diplomacy of
the strategies (Wu et al., 2014). The implication of the technological issues in the company has
provided influential development in the effective flow of operation s in the company. The
identified technological issues in the company has been properly analysed for the finding the
strategies to mitigate them.
Human Errors
The human errors are the major factors in the form of the hindrances in the company. The
system-integrated operations have able to manage the security risks involved in the management
of the company (Patil & Seshadri, 2014). The errors that are made by the human cohesiveness
are creating issues for the company. There are various human errors including information
interception, replay if messages, hijacking, unauthorised data breaches and manipulation of
hardware. The human including the employees and other staffs of the company manipulates
these errors.
Designing Errors
The designing errors are depicted for systematic faults in the enterprise. These designing
errors are confirmed by the implication of operational processing. These errors are prepared for
the critical evaluation for the development of the organisation. Therefore, the business operations
are reliable to the management of the company. For example, threat in planning, change of data,
unreliable sources of information and failure in the business process.
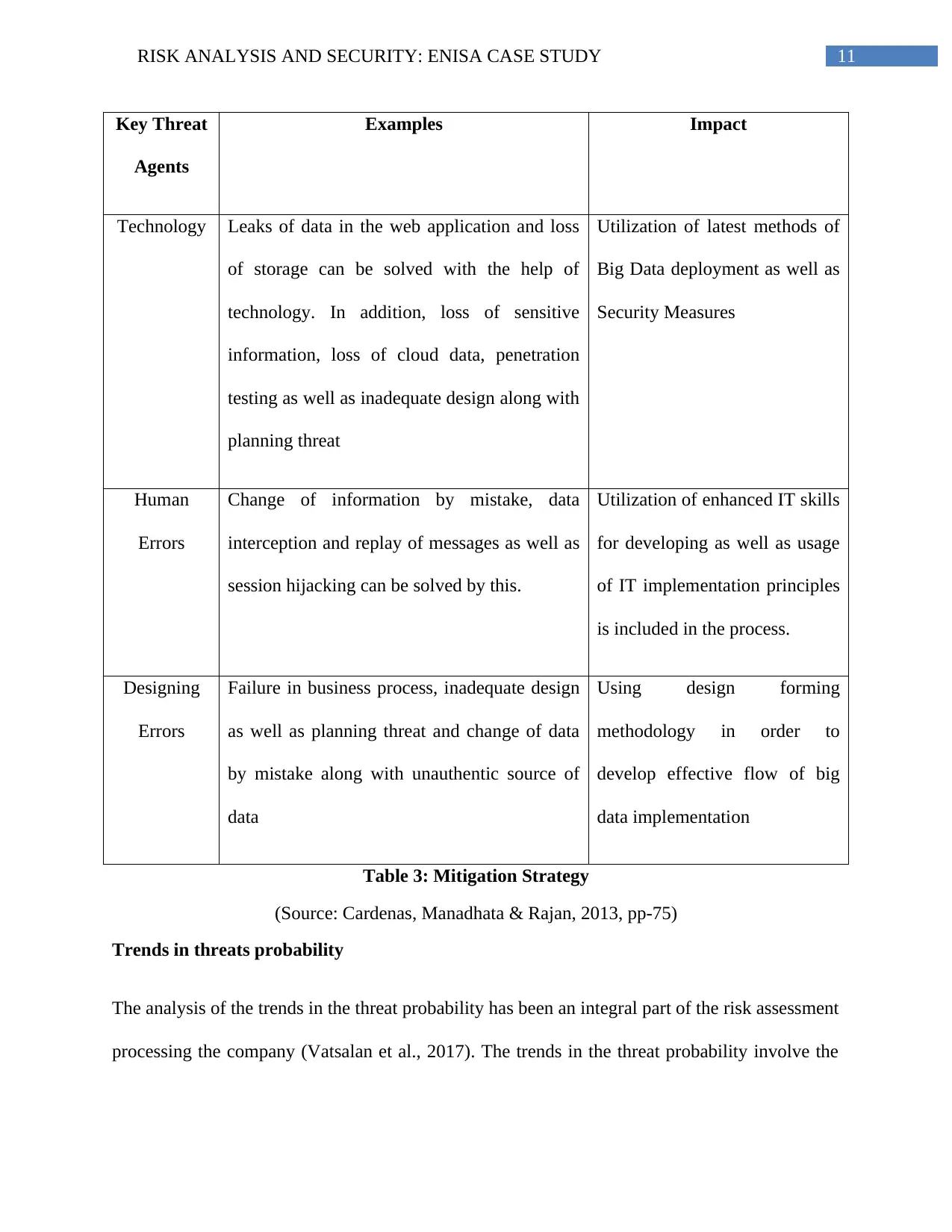
11RISK ANALYSIS AND SECURITY: ENISA CASE STUDY
Key Threat
Agents
Examples Impact
Technology Leaks of data in the web application and loss
of storage can be solved with the help of
technology. In addition, loss of sensitive
information, loss of cloud data, penetration
testing as well as inadequate design along with
planning threat
Utilization of latest methods of
Big Data deployment as well as
Security Measures
Human
Errors
Change of information by mistake, data
interception and replay of messages as well as
session hijacking can be solved by this.
Utilization of enhanced IT skills
for developing as well as usage
of IT implementation principles
is included in the process.
Designing
Errors
Failure in business process, inadequate design
as well as planning threat and change of data
by mistake along with unauthentic source of
data
Using design forming
methodology in order to
develop effective flow of big
data implementation
Table 3: Mitigation Strategy
(Source: Cardenas, Manadhata & Rajan, 2013, pp-75)
Trends in threats probability
The analysis of the trends in the threat probability has been an integral part of the risk assessment
processing the company (Vatsalan et al., 2017). The trends in the threat probability involve the
Key Threat
Agents
Examples Impact
Technology Leaks of data in the web application and loss
of storage can be solved with the help of
technology. In addition, loss of sensitive
information, loss of cloud data, penetration
testing as well as inadequate design along with
planning threat
Utilization of latest methods of
Big Data deployment as well as
Security Measures
Human
Errors
Change of information by mistake, data
interception and replay of messages as well as
session hijacking can be solved by this.
Utilization of enhanced IT skills
for developing as well as usage
of IT implementation principles
is included in the process.
Designing
Errors
Failure in business process, inadequate design
as well as planning threat and change of data
by mistake along with unauthentic source of
data
Using design forming
methodology in order to
develop effective flow of big
data implementation
Table 3: Mitigation Strategy
(Source: Cardenas, Manadhata & Rajan, 2013, pp-75)
Trends in threats probability
The analysis of the trends in the threat probability has been an integral part of the risk assessment
processing the company (Vatsalan et al., 2017). The trends in the threat probability involve the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





