Comprehensive Analysis of ENISA Big Data Security Infrastructure Case
VerifiedAdded on 2019/11/29
|14
|3382
|215
Report
AI Summary
This report analyzes a case study related to the European Union Agency for the Network and Information Security (ENISA), focusing on big data security infrastructure. It examines various aspects, including an overview of the case, the identification of significant threats (particularly web-based attacks and malware), key threat agents (such as cybercriminals and hacktivists), and strategies to minimize their impact. The report also discusses potential improvements to the ETL (Extract, Transform, Load) process, emphasizing the importance of data consistency, security measures, and the agency's role in supporting member states and private sectors. The analysis highlights the evolving nature of cyber threats and the need for proactive security measures to protect information systems and data from various vulnerabilities and attacks. The report underscores the importance of training, monitoring, and strategic planning to combat insider threats and maintain robust cybersecurity standards.
report
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction......................................................................................................................................2
Answer 1:.........................................................................................................................................2
Answer 2:.........................................................................................................................................3
Answer 3:.........................................................................................................................................5
Answer 4:.........................................................................................................................................6
Answer 5:.........................................................................................................................................8
Conclusion.......................................................................................................................................9
References......................................................................................................................................10
Introduction......................................................................................................................................2
Answer 1:.........................................................................................................................................2
Answer 2:.........................................................................................................................................3
Answer 3:.........................................................................................................................................5
Answer 4:.........................................................................................................................................6
Answer 5:.........................................................................................................................................8
Conclusion.......................................................................................................................................9
References......................................................................................................................................10

Introduction
The case is related to the European Union Agency for the Network and Information Security
which includes the centres for the combination and the detailed security as well. The
identification of the strategies with the combating of the insider threats help in determining all
the important threats which are included in the brief discussion below (Payton et al., 2014).
Answer 1:
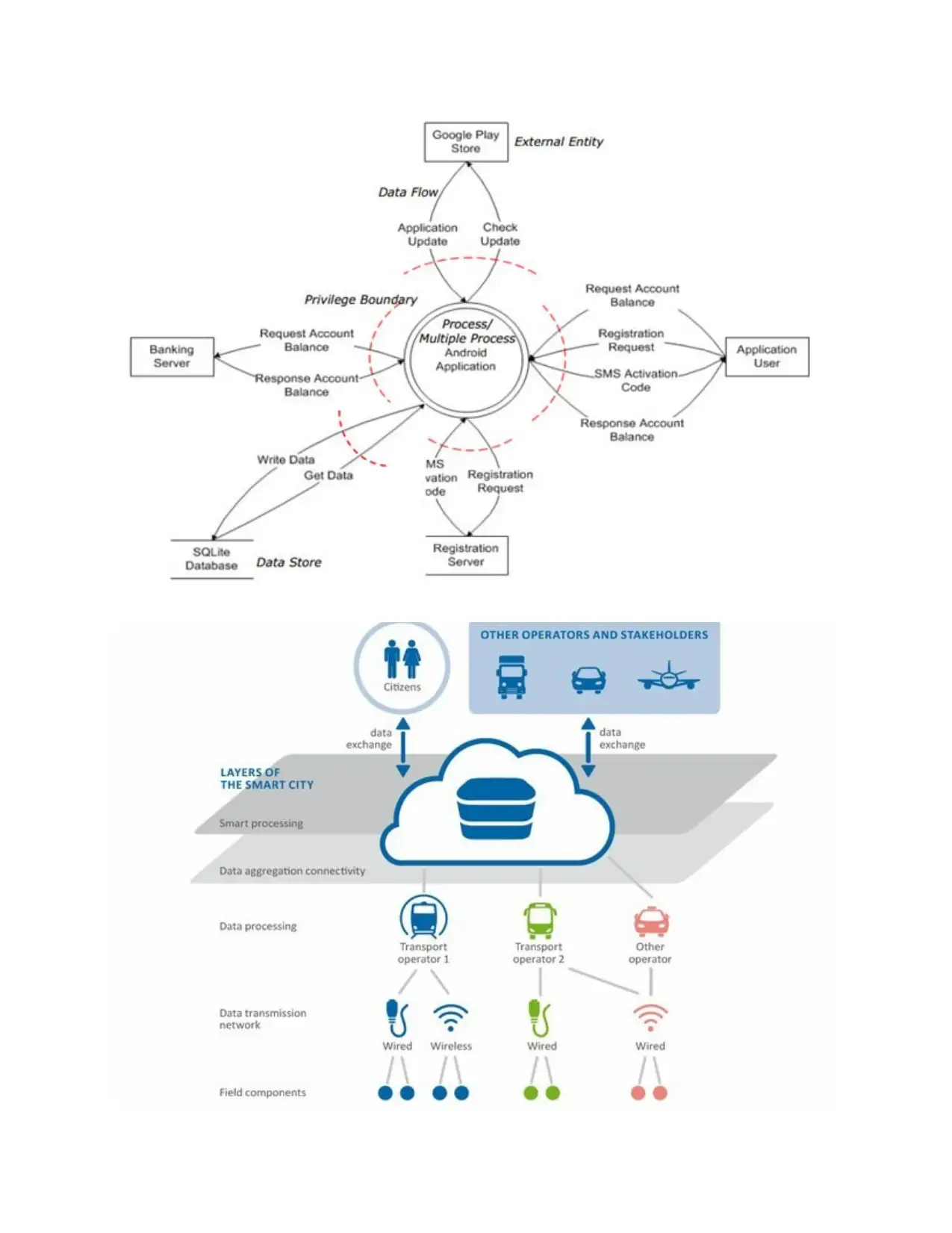
1) Provide a brief overview of the case study and prepare a diagram for the ENISA Big
Data security infrastructure.
As per the given case, the focus is on handling the networking tools of ENISA which needs to
handle the information technology systems with the proper control of the information which is
set with the cyber threats, data duplication and the security analysis. The emerging kinds of the
threat analysis is based on working over the cyber threats with the world-wide patterns that
include the assigning of the central roles which are for the practical security incident and the
event management. There are different organisation which work on the management of the
software with the cyber security and the access is based on the organisational activities as well
(Van Dijck, 2014). The forms and the standards match the limits related to the data that is based
on the threat intelligence. The consistency is important for the collection and working on the
aggregation and the data correlation. This will be important for the end user protection and
reducing the threats which are mainly related to the information systems. The provisions of the
security are mainly to match with the cases that relate to different organisations and how ENISA
is able to handle the cyber security measures (Soria et al., 2016). The cases have been about
making use of the threat information with involvement of the target assets to manage the security
The case is related to the European Union Agency for the Network and Information Security
which includes the centres for the combination and the detailed security as well. The
identification of the strategies with the combating of the insider threats help in determining all
the important threats which are included in the brief discussion below (Payton et al., 2014).
Answer 1:
1) Provide a brief overview of the case study and prepare a diagram for the ENISA Big
Data security infrastructure.
As per the given case, the focus is on handling the networking tools of ENISA which needs to
handle the information technology systems with the proper control of the information which is
set with the cyber threats, data duplication and the security analysis. The emerging kinds of the
threat analysis is based on working over the cyber threats with the world-wide patterns that
include the assigning of the central roles which are for the practical security incident and the
event management. There are different organisation which work on the management of the
software with the cyber security and the access is based on the organisational activities as well
(Van Dijck, 2014). The forms and the standards match the limits related to the data that is based
on the threat intelligence. The consistency is important for the collection and working on the
aggregation and the data correlation. This will be important for the end user protection and
reducing the threats which are mainly related to the information systems. The provisions of the
security are mainly to match with the cases that relate to different organisations and how ENISA
is able to handle the cyber security measures (Soria et al., 2016). The cases have been about
making use of the threat information with involvement of the target assets to manage the security
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

standards involving the targets. The management of the security factors with the creation of a
better planning for removing any vulnerability is relevant with the controlled analysis which
includes the application for the effective strategy measures and for cleaning the system. The case
is related to the web based attacks and how the malware defiance need to work on the
applications which are related to ENISA networking and security measures. The measures set for
the security standards are also related to handle the requirements with the organisational forms
and the services, which are mainly due to the application processes that could be understood with
the use of SQL. The forms of the report and the testing is done in the web application
vulnerability which tends to increase gradually (Payton et al., 2014).
The security standards of ENISA is based on working over the current tools of IT and technology
is based on the significant impact patterns which includes the organisation planning. The
standards are set to protect and meet the different objectives that will overcome the threats
related to the loss of data (Perera et al., 2015). The security standards are set to involve the
different aspects of the business models which have a major impact on the business networking
and the cyber security.
better planning for removing any vulnerability is relevant with the controlled analysis which
includes the application for the effective strategy measures and for cleaning the system. The case
is related to the web based attacks and how the malware defiance need to work on the
applications which are related to ENISA networking and security measures. The measures set for
the security standards are also related to handle the requirements with the organisational forms
and the services, which are mainly due to the application processes that could be understood with
the use of SQL. The forms of the report and the testing is done in the web application
vulnerability which tends to increase gradually (Payton et al., 2014).
The security standards of ENISA is based on working over the current tools of IT and technology
is based on the significant impact patterns which includes the organisation planning. The
standards are set to protect and meet the different objectives that will overcome the threats
related to the loss of data (Perera et al., 2015). The security standards are set to involve the
different aspects of the business models which have a major impact on the business networking
and the cyber security.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Answer 2:
2) Out of the ‘’Top threats’’ which threat would you regard to be the most significant and
why?
The IT systems and the software works on the probability forms where the threats are affecting
the activities of the data. This also includes the higher level of security of information in the
organisation. The management is based on matching with the different standards which combat
the insider threat with the different strategies that could be for the funding and proper planning.
There are different issues related to the top threats which are including the web based attacks
based on the standards set for revealing the information to the competitors (Fabian et al., 2015).
The web based attacks are covered with the allotted techniques that include the redirection of the
web browser. This includes the infected web sites like the malware infections that take place
which corrupt the whole system. The threat also tends to cover the wider networks in the website
with the deployment of the other additional methods which includes the mobile devices and the
different web applications (Soria-Comas & Damingo, 2016). The top threats are related to the
efficiency with operating systems that covers the spacing of the computer. The malware is linked
with the URL websites with the standards that are set for the automatic installation in the
systems, with the designing spaces. The software tends to decline any of the available
vulnerabilities with the exploitation in the systems. The major focus is on covering the world
system and reducing the efficacy of the operating systems with attaching all the operating
websites (Jerome, 2013). With this, around 145 million people have the unique which is
recognized as malicious with the means over 40% of the URL which infects the malware
(Pedrosa et al., 2014). The standards are set with the significant threats in the world, where the
2) Out of the ‘’Top threats’’ which threat would you regard to be the most significant and
why?
The IT systems and the software works on the probability forms where the threats are affecting
the activities of the data. This also includes the higher level of security of information in the
organisation. The management is based on matching with the different standards which combat
the insider threat with the different strategies that could be for the funding and proper planning.
There are different issues related to the top threats which are including the web based attacks
based on the standards set for revealing the information to the competitors (Fabian et al., 2015).
The web based attacks are covered with the allotted techniques that include the redirection of the
web browser. This includes the infected web sites like the malware infections that take place
which corrupt the whole system. The threat also tends to cover the wider networks in the website
with the deployment of the other additional methods which includes the mobile devices and the
different web applications (Soria-Comas & Damingo, 2016). The top threats are related to the
efficiency with operating systems that covers the spacing of the computer. The malware is linked
with the URL websites with the standards that are set for the automatic installation in the
systems, with the designing spaces. The software tends to decline any of the available
vulnerabilities with the exploitation in the systems. The major focus is on covering the world
system and reducing the efficacy of the operating systems with attaching all the operating
websites (Jerome, 2013). With this, around 145 million people have the unique which is
recognized as malicious with the means over 40% of the URL which infects the malware
(Pedrosa et al., 2014). The standards are set with the significant threats in the world, where the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

global issues that works on the infected files which is important for the business development.
The web based attacks are set with the positions that are set in threat landscape of America and
Europe. The major focus is on helping the organisation and working on determining the assets
with defined risks for protecting the assets from insiders and outsiders. The training and
monitoring is based on the insider security threat with the organisation working on the use of
strategy that offers the training to staff with the policy and proper use of the technology to
achieve the higher standards to avoid the errors (Michael & Michal, 2013). The situation is based
on the threats and the technology which exists for the infractions.
Answer 3:
3) Identify and discuss the key Threat Agents. What could be done to minimize their
impact on the system? Based on the data provided, discuss the trends in threat probability.
The threats are related to the functioning and handling the different security issues, where the
cyber-attacks are considered to be of the higher probability measures. It includes the agents of
threat who easily lead to the damage with the organisation working on the collection of
important information (Pedrosa et al., 2014). The sharing of the information and working on the
threat agents is important for the organisation so that all the information from the users is
properly kept. The cyber criminals are efficient with the handling of malicious tools with the
attacking methods as well. The threat agents are related to the functioning which includes how
the biggest threat has a major impact on the management with the security standards set for the
organisation and its development (Kasper, 2014).
The web based attacks are set with the positions that are set in threat landscape of America and
Europe. The major focus is on helping the organisation and working on determining the assets
with defined risks for protecting the assets from insiders and outsiders. The training and
monitoring is based on the insider security threat with the organisation working on the use of
strategy that offers the training to staff with the policy and proper use of the technology to
achieve the higher standards to avoid the errors (Michael & Michal, 2013). The situation is based
on the threats and the technology which exists for the infractions.
Answer 3:
3) Identify and discuss the key Threat Agents. What could be done to minimize their
impact on the system? Based on the data provided, discuss the trends in threat probability.
The threats are related to the functioning and handling the different security issues, where the
cyber-attacks are considered to be of the higher probability measures. It includes the agents of
threat who easily lead to the damage with the organisation working on the collection of
important information (Pedrosa et al., 2014). The sharing of the information and working on the
threat agents is important for the organisation so that all the information from the users is
properly kept. The cyber criminals are efficient with the handling of malicious tools with the
attacking methods as well. The threat agents are related to the functioning which includes how
the biggest threat has a major impact on the management with the security standards set for the
organisation and its development (Kasper, 2014).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The threat agents like the cyber criminals, working with the hired persons, cyber criminals work
on the group of agents and the major objective is based on earning the profits with the illegal
activities that work on the online means. The major focus is on the motivation with money and
intelligence. The online cybercrime criminals works on the standards through the unethical
means which includes the suitability standards to match with the large amount of the time and
money. The focus is also on the hacktivists where the threat agents focus on the generation of the
attention of media with the politically motivated activists. Here, the focus is on the activities
which relate to handle the set groups and the structures that could be used for viewing the
different time of the riots. The elections and the other major events are mainly to create the
international attention (Beardsley et al., 2016). The cyber fighters are also the people with the
motivation focusing on the power striking with the handling of the different results that include
the boundaries that infect the people of the national and the international standards. With this, the
focus is also on how the social hacking issues could be resolved where there are threats that
could be mainly for controlling the use of the loggers, waste of the data or the social media
patterns. The high techniques are for the handling of the social hackers to hack the social
platforms which includes the creation of the threats to the organisation. The different kinds of
groups work on the privacy standards with the major focus on the personalised data and the user
document, cyber maltreatment. The usability forms are related to work with the social workers
which play an important role in the website hacking process. The standards set for the
operational activities is based on working over the different goals and standards, where the attack
of the website, fraud or the cyber espionage. This includes the collection of the information
which is set with the aggregation of data (Ramic et al, 2011). The focus is mainly on working
over the end-user protection and then reducing the threats which are related to the security of the
on the group of agents and the major objective is based on earning the profits with the illegal
activities that work on the online means. The major focus is on the motivation with money and
intelligence. The online cybercrime criminals works on the standards through the unethical
means which includes the suitability standards to match with the large amount of the time and
money. The focus is also on the hacktivists where the threat agents focus on the generation of the
attention of media with the politically motivated activists. Here, the focus is on the activities
which relate to handle the set groups and the structures that could be used for viewing the
different time of the riots. The elections and the other major events are mainly to create the
international attention (Beardsley et al., 2016). The cyber fighters are also the people with the
motivation focusing on the power striking with the handling of the different results that include
the boundaries that infect the people of the national and the international standards. With this, the
focus is also on how the social hacking issues could be resolved where there are threats that
could be mainly for controlling the use of the loggers, waste of the data or the social media
patterns. The high techniques are for the handling of the social hackers to hack the social
platforms which includes the creation of the threats to the organisation. The different kinds of
groups work on the privacy standards with the major focus on the personalised data and the user
document, cyber maltreatment. The usability forms are related to work with the social workers
which play an important role in the website hacking process. The standards set for the
operational activities is based on working over the different goals and standards, where the attack
of the website, fraud or the cyber espionage. This includes the collection of the information
which is set with the aggregation of data (Ramic et al, 2011). The focus is mainly on working
over the end-user protection and then reducing the threats which are related to the security of the

information and the other areas of working. It also includes the maintenance of the different
provisions of security and then working on the improvement of the maturity with threat removal
as well.
Answer 4:
4) How could the ETL process be improved? Discuss.
The high amount of the data is based on the ETL processing with the handling of the
performance with smoothing the processes. For this, the focus is on:
a. The loading processes where there are only rows that need to be changed. ETL focus on
the collaboration with the contribution to improve the cyber security standards. It
includes the focus on the supporting roles with the member states and the other private
sectors that are for the proper handling of the information and the security measures. The
agency focuses on the deals which are related to the security of the cyber environment
with the production of certain recommendations, support with the policy development
and the implementation (Maksimovic et al., 2015).
b. ETL works on the overviewing of the threats and then working over the assess for the
threat exposure. The standards are set to measure the compilation with the focus on the
different means and the application areas. This will help in improving the support for the
security breach with the cross border functions. The standards are set to define the
processes with the EU network for the large scale cyber incidents. The forms and the
cooperation with the member states also require to focus on the different technological
aspects.
provisions of security and then working on the improvement of the maturity with threat removal
as well.
Answer 4:
4) How could the ETL process be improved? Discuss.
The high amount of the data is based on the ETL processing with the handling of the
performance with smoothing the processes. For this, the focus is on:
a. The loading processes where there are only rows that need to be changed. ETL focus on
the collaboration with the contribution to improve the cyber security standards. It
includes the focus on the supporting roles with the member states and the other private
sectors that are for the proper handling of the information and the security measures. The
agency focuses on the deals which are related to the security of the cyber environment
with the production of certain recommendations, support with the policy development
and the implementation (Maksimovic et al., 2015).
b. ETL works on the overviewing of the threats and then working over the assess for the
threat exposure. The standards are set to measure the compilation with the focus on the
different means and the application areas. This will help in improving the support for the
security breach with the cross border functions. The standards are set to define the
processes with the EU network for the large scale cyber incidents. The forms and the
cooperation with the member states also require to focus on the different technological
aspects.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

c. The measures like cryptography, privacy enhancement of the technologies need to handle
the readiness of the system with the proper policy law maker so that the community
development with the easy guidance is provided to the different data controllers
(Chakraborty et al., 2014). The emerging technologies like the big data and the mobile
computing is set with the data protection of the agencies which are working over the
protection to remain active in the area with the breach notifications.
ETL works on the improvement of the sophisticated threats with the law enforcement that
includes the coordinated efforts. The standards are set based on the system functioning with the
cybercrime that focus on the major impact of the system. ENISA focus on the highlights of the
encryption libraries and the applications which are set in the different factors where the report is
also about the leakage incidents that are classified by the security community. ETL also works
on the malicious codes and then work on the threat trends that include the overall security
infrastructure (Ramic et al., 2011). ETL works on the processes with the evaluation of the
emerging strategy which works towards the individual and the organisations by adapting to the
different counter measures. The standards are set for the developers with the security guides and
the policy makers. It includes the different human resources with the threats that depend on the
sources like the physical attacks, failure or the malfunctioning of the system. The unintentional
damage, nefarious activities are considered to be illegal which need to be improved as well.
(D'Acquisto et al., 2015)
the readiness of the system with the proper policy law maker so that the community
development with the easy guidance is provided to the different data controllers
(Chakraborty et al., 2014). The emerging technologies like the big data and the mobile
computing is set with the data protection of the agencies which are working over the
protection to remain active in the area with the breach notifications.
ETL works on the improvement of the sophisticated threats with the law enforcement that
includes the coordinated efforts. The standards are set based on the system functioning with the
cybercrime that focus on the major impact of the system. ENISA focus on the highlights of the
encryption libraries and the applications which are set in the different factors where the report is
also about the leakage incidents that are classified by the security community. ETL also works
on the malicious codes and then work on the threat trends that include the overall security
infrastructure (Ramic et al., 2011). ETL works on the processes with the evaluation of the
emerging strategy which works towards the individual and the organisations by adapting to the
different counter measures. The standards are set for the developers with the security guides and
the policy makers. It includes the different human resources with the threats that depend on the
sources like the physical attacks, failure or the malfunctioning of the system. The unintentional
damage, nefarious activities are considered to be illegal which need to be improved as well.
(D'Acquisto et al., 2015)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Answer 5:
5) To sum up, should ENISA be satisfied with its current state of IT Security? Why? Or
Why not?
The research is based on working over the different parameters where ENISA need to focus on
the levels of the current state and how the IT security need to work on the security measures. The
focus should be mainly on the prioritization of the threats with the applications that are related to
work on the different injection attacks. The injections attacks are namely the phishing,
scareware, malicious codes etc. It is important to focus on the measures with ENISA not only
working over the reduced effects but also on the threats that are considered to be proven best for
the secured data patterns (Benndorf e al., 2017). The easy transfer of the data and the working
without any major interference can be possible only with the improvement of the processes in
ENISA. The process also include the extraction and working over how the rows are inserted and
modified which leads to the change in the operations depending upon the standard processes. It
works with the threats that are related to function on the areas of the embedded systems and how
the hardware devices are able to solve the issues related to the components and the attacks. The
threats are mainly related to the issues which include the breach of the data and so for that a
strong password need to be used with the proper networks. It includes the data breaching
measures which occurs when there is a vulnerability to the network, or there is any incorrect
form of the user authentication. For this, the tampering and the insider threats are required to
manage the issues which are then related to handle the information leakage processes. The
introduction of the high security and the secured passwords with firewall settings will allow the
system with the easy processing. The check is on the software defined data pattern and the
5) To sum up, should ENISA be satisfied with its current state of IT Security? Why? Or
Why not?
The research is based on working over the different parameters where ENISA need to focus on
the levels of the current state and how the IT security need to work on the security measures. The
focus should be mainly on the prioritization of the threats with the applications that are related to
work on the different injection attacks. The injections attacks are namely the phishing,
scareware, malicious codes etc. It is important to focus on the measures with ENISA not only
working over the reduced effects but also on the threats that are considered to be proven best for
the secured data patterns (Benndorf e al., 2017). The easy transfer of the data and the working
without any major interference can be possible only with the improvement of the processes in
ENISA. The process also include the extraction and working over how the rows are inserted and
modified which leads to the change in the operations depending upon the standard processes. It
works with the threats that are related to function on the areas of the embedded systems and how
the hardware devices are able to solve the issues related to the components and the attacks. The
threats are mainly related to the issues which include the breach of the data and so for that a
strong password need to be used with the proper networks. It includes the data breaching
measures which occurs when there is a vulnerability to the network, or there is any incorrect
form of the user authentication. For this, the tampering and the insider threats are required to
manage the issues which are then related to handle the information leakage processes. The
introduction of the high security and the secured passwords with firewall settings will allow the
system with the easy processing. The check is on the software defined data pattern and the

network visualisation processes that include the centralised control over the networks. For this,
there are forms of the management with the working that includes the flow of the data and the
other attacks that relate to the network components as well as centralising the control functions.
Conclusion
As per the security standards ENISA focus mainly on providing the best support for the
networking and improving the system of the cyber security. It includes the major influence and
the working of the different processes that are for handling the operations based on the
processing of the IT sector (Chibba et al., 2015). The reports have been mainly about the
handling of different strategies and working over the combating of insider threats with the top
threats. The case is also about the system functions and the analysis where the threats have a
major impact on the operational security measures as well. Hence, the part includes the working,
where the threat agents and the social hacking issues need to be handled in a proper manner.
References
Beardsley, S., Enriquez, L., Grijpink, F., Sandoval, S., Spittaels, S., & Strandell-Jansson, M. (2014).
Building Trust: The Role of Regulation in Unlocking the Value of Big Data. The Global Information
Technology Report 2014, 73.
Benndorf, V., & Normann, H. T. (2017). The willingness to sell personal data. The Scandinavian Journal
of Economics.
Chakraborty, N., & Gonnade, S. (2014). Big data and big data mining: Study of approaches, issues and
future scope. International Journal of Engineering Trends and Technology (IJETT)–Volume, 18.
there are forms of the management with the working that includes the flow of the data and the
other attacks that relate to the network components as well as centralising the control functions.
Conclusion
As per the security standards ENISA focus mainly on providing the best support for the
networking and improving the system of the cyber security. It includes the major influence and
the working of the different processes that are for handling the operations based on the
processing of the IT sector (Chibba et al., 2015). The reports have been mainly about the
handling of different strategies and working over the combating of insider threats with the top
threats. The case is also about the system functions and the analysis where the threats have a
major impact on the operational security measures as well. Hence, the part includes the working,
where the threat agents and the social hacking issues need to be handled in a proper manner.
References
Beardsley, S., Enriquez, L., Grijpink, F., Sandoval, S., Spittaels, S., & Strandell-Jansson, M. (2014).
Building Trust: The Role of Regulation in Unlocking the Value of Big Data. The Global Information
Technology Report 2014, 73.
Benndorf, V., & Normann, H. T. (2017). The willingness to sell personal data. The Scandinavian Journal
of Economics.
Chakraborty, N., & Gonnade, S. (2014). Big data and big data mining: Study of approaches, issues and
future scope. International Journal of Engineering Trends and Technology (IJETT)–Volume, 18.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





