System Risk Management Report: Analyzing ENISA Big Data Security
VerifiedAdded on 2019/11/26
|16
|3810
|174
Report
AI Summary
This report provides an in-depth analysis of system risk management, using the ENISA case study as a primary example. It begins with an overview of the ENISA big data security infrastructure, illustrating its design and functionality. The report then identifies and categorizes the top threats within the ENISA framework, including unintentional threats, interception, nefarious activities, legal threats, and organizational threats, with a particular emphasis on the dangers posed by malicious code. Furthermore, it explores the key threat agents, such as corporations, cybercriminals, and cyber terrorists, detailing their motivations and methods, and suggests strategies to minimize their impact. The report also delves into ETL process improvement and the overall IT security of ENISA, offering recommendations for enhancing data security. The report concludes with a summary of the findings and a discussion of the importance of proactive risk management in big data environments.

Running head: SYSTEM RISK MANAGEMENT
System Risk Management
Name of the Student
Student ID
Name of the University
Author’s note:
System Risk Management
Name of the Student
Student ID
Name of the University
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SYSTEM RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................2
1. Overview of ENISA Case Study and Illustration of ENISA Big Data Security Infrastructure. 2
2. Top Threats in ENISA.................................................................................................................4
3. Key Threat Agents and Ways to Minimize their Impact.............................................................8
4. ETL Process Improvement........................................................................................................10
5. IT Security of ENISA...............................................................................................................10
Conclusion.....................................................................................................................................11
References......................................................................................................................................12
Table of Contents
Introduction......................................................................................................................................2
1. Overview of ENISA Case Study and Illustration of ENISA Big Data Security Infrastructure. 2
2. Top Threats in ENISA.................................................................................................................4
3. Key Threat Agents and Ways to Minimize their Impact.............................................................8
4. ETL Process Improvement........................................................................................................10
5. IT Security of ENISA...............................................................................................................10
Conclusion.....................................................................................................................................11
References......................................................................................................................................12

2SYSTEM RISK MANAGEMENT
Introduction
Big data consists of large amount of data for the purpose of analyzing the data set and
determine patterns. Data assets are identified followed by a process of exposure analysis. Risks
and vulnerabilities are shown in this case study (Mahajan, Gaba & Chauhan, 2016). The asset
classes of big data are identified and then level of risk exposure of the assets is assessed.
This report talks about the different threats as well as the key threat agents (Kao et al.
2014). The methods that can be used to minimize the impact of the threats are discussed in this
report. It also explains how ETL process can be improved.
1. Overview of ENISA Case Study and Illustration of ENISA Big Data
Security Infrastructure
Big data consists of large amount of data for the purpose of analyzing the data set and
determine patterns. Human behavior and preferences can be identified by analyzing big data. The
usage of big data is gaining importance with time. This case study provides information about
the security threats. Attackers are mostly targeting big data systems. Data assets are identified
followed by a process of exposure analysis. Risks and vulnerabilities are shown n this case study.
The asset classes of big data are identified and then level of risk exposure of the assets is
assessed (Enisa.europa.eu, 2017). The security threats as well as their agents are also classified in
this case study. The threats of the big data are all the ordinary data threats but are not limited to
these threats (Patil & Seshadri, 2014). There are also new kinds of breach like degradation and
leakage of data that are specific in case of Big Data. There is significant impact of the data
protection as well as privacy. There can be conflict among the several asset owners because their
Introduction
Big data consists of large amount of data for the purpose of analyzing the data set and
determine patterns. Data assets are identified followed by a process of exposure analysis. Risks
and vulnerabilities are shown in this case study (Mahajan, Gaba & Chauhan, 2016). The asset
classes of big data are identified and then level of risk exposure of the assets is assessed.
This report talks about the different threats as well as the key threat agents (Kao et al.
2014). The methods that can be used to minimize the impact of the threats are discussed in this
report. It also explains how ETL process can be improved.
1. Overview of ENISA Case Study and Illustration of ENISA Big Data
Security Infrastructure
Big data consists of large amount of data for the purpose of analyzing the data set and
determine patterns. Human behavior and preferences can be identified by analyzing big data. The
usage of big data is gaining importance with time. This case study provides information about
the security threats. Attackers are mostly targeting big data systems. Data assets are identified
followed by a process of exposure analysis. Risks and vulnerabilities are shown n this case study.
The asset classes of big data are identified and then level of risk exposure of the assets is
assessed (Enisa.europa.eu, 2017). The security threats as well as their agents are also classified in
this case study. The threats of the big data are all the ordinary data threats but are not limited to
these threats (Patil & Seshadri, 2014). There are also new kinds of breach like degradation and
leakage of data that are specific in case of Big Data. There is significant impact of the data
protection as well as privacy. There can be conflict among the several asset owners because their
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SYSTEM RISK MANAGEMENT
choices might not be aligned with everyone. The use of information and communication
technology will lead to several privacy and security threat issues. There is a presentation of gap
analysis that compares between the threats of the big data along with the countermeasures that
can be taken in order to overcome and avoid these threats. This case study shows that there is
gap in the countermeasure of big data (Vatsalan et al., 2017). The trend of the recent
countermeasures is explained. Data threats that are traditional in nature are mainly data oriented.
Recommendations and suggestions are given for the countermeasures that can be taken in the
next generation. Current system and data should be replaced by big data so that there are specific
solutions of it. The loopholes in the existing system must be checked and resolved. This case
study talks about the environment of big data, its architecture, assets of the big data and their
taxonomy. It also describes the threats and its agents. Good practices are also given along with
gap analysis.
choices might not be aligned with everyone. The use of information and communication
technology will lead to several privacy and security threat issues. There is a presentation of gap
analysis that compares between the threats of the big data along with the countermeasures that
can be taken in order to overcome and avoid these threats. This case study shows that there is
gap in the countermeasure of big data (Vatsalan et al., 2017). The trend of the recent
countermeasures is explained. Data threats that are traditional in nature are mainly data oriented.
Recommendations and suggestions are given for the countermeasures that can be taken in the
next generation. Current system and data should be replaced by big data so that there are specific
solutions of it. The loopholes in the existing system must be checked and resolved. This case
study talks about the environment of big data, its architecture, assets of the big data and their
taxonomy. It also describes the threats and its agents. Good practices are also given along with
gap analysis.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
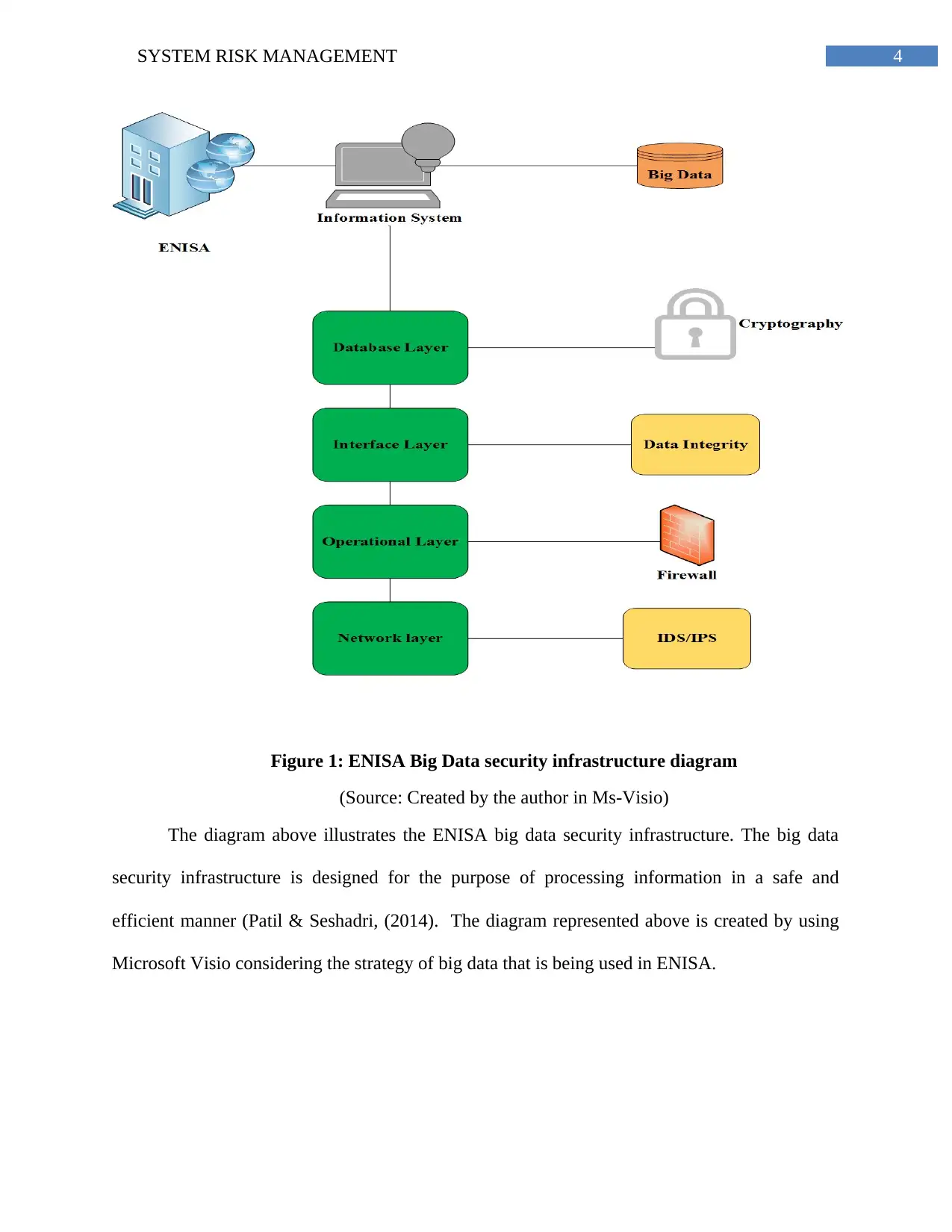
4SYSTEM RISK MANAGEMENT
Figure 1: ENISA Big Data security infrastructure diagram
(Source: Created by the author in Ms-Visio)
The diagram above illustrates the ENISA big data security infrastructure. The big data
security infrastructure is designed for the purpose of processing information in a safe and
efficient manner (Patil & Seshadri, (2014). The diagram represented above is created by using
Microsoft Visio considering the strategy of big data that is being used in ENISA.
Figure 1: ENISA Big Data security infrastructure diagram
(Source: Created by the author in Ms-Visio)
The diagram above illustrates the ENISA big data security infrastructure. The big data
security infrastructure is designed for the purpose of processing information in a safe and
efficient manner (Patil & Seshadri, (2014). The diagram represented above is created by using
Microsoft Visio considering the strategy of big data that is being used in ENISA.

5SYSTEM RISK MANAGEMENT
2. Top Threats in ENISA
There are several threats that are discussed in this case study of ENISA (Wu et al., 2014).
There are five threat groups described in the ENISA case study. They are described as follows:
1. Unintentional Threat: These security threats are caused because of some kind of
errors committed by humans. These errors are caused due to some mistake. There are no wrong
intentions behind these types of threats (Hashem et al., 2015). These errors can be rectified after
identification. Some of the threats that fall under this category are:
Leakage of information: These threats are accidental in nature. Human errors can
lead to these problems. There can be misconfiguration issues, clerical errors and
mistakes like when the software is not updated (Erl, Khattak & Buhler, 2016).
Recent studies have shown that the improper administration of the system has led
to the leakage of various data. Several agents are included in these types of
threats. The assets that are affected are data. Disclosure of data can lead to several
problems of the organization.
Data Leakage through applications of the Web: The threat agents playing role in
this case is everyone. This is caused by unsecure API. The effect of this leakage
can disclose data to the harmful people that can exploit the organization. The
models of storage infrastructure are affected along with the data. Data can be
modified or deleted in this case.
Inadequate Design: Sometimes the system design is not adequate enough and
attracts several threats. There is problem seen in the planning process of the
infrastructural design. Improper adaptation can also attract security threats. There
is huge probability of data leakage in this case (Kim, Trimi & Chung, 2014). The
2. Top Threats in ENISA
There are several threats that are discussed in this case study of ENISA (Wu et al., 2014).
There are five threat groups described in the ENISA case study. They are described as follows:
1. Unintentional Threat: These security threats are caused because of some kind of
errors committed by humans. These errors are caused due to some mistake. There are no wrong
intentions behind these types of threats (Hashem et al., 2015). These errors can be rectified after
identification. Some of the threats that fall under this category are:
Leakage of information: These threats are accidental in nature. Human errors can
lead to these problems. There can be misconfiguration issues, clerical errors and
mistakes like when the software is not updated (Erl, Khattak & Buhler, 2016).
Recent studies have shown that the improper administration of the system has led
to the leakage of various data. Several agents are included in these types of
threats. The assets that are affected are data. Disclosure of data can lead to several
problems of the organization.
Data Leakage through applications of the Web: The threat agents playing role in
this case is everyone. This is caused by unsecure API. The effect of this leakage
can disclose data to the harmful people that can exploit the organization. The
models of storage infrastructure are affected along with the data. Data can be
modified or deleted in this case.
Inadequate Design: Sometimes the system design is not adequate enough and
attracts several threats. There is problem seen in the planning process of the
infrastructural design. Improper adaptation can also attract security threats. There
is huge probability of data leakage in this case (Kim, Trimi & Chung, 2014). The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SYSTEM RISK MANAGEMENT
assets that are affected in this category of threat are software, data, storage
infrastructure, computing infrastructure and big data analytics. This is the most
typical type of threat for big data. Weakness of any system is its redundancy.
2. Interception, Eavesdropping and Hijacking: This group of threat involves
manipulation or alteration of the process of communication among the parties. Additional tools
are not needed on the infrastructure of the victim.
Information Interception: ICT infrastructure often faces this issue of
communication interception between the nodes. The tools of big data are not
secured most of the times. There is lack of proper protocols for maintaining
integrity and confidentiality among the communicating applications. The back
end servers as well as applications are affected by this issue.
3. Nefarious Activity and Abuse: This is a type of deliberate attack where the attacker
tries to alter the ICT infrastructure of the victim (Chen & Zhang, 2014). They use specific
software and tools. There several threats under this category:
Identity Fraud: The system of big data stores financial information and personal
details of the user like the information about credit card. These sensitive data are
targeted by the hackers. Getting an access to such sensitive data will give the
hacker a power over the over the organization. Most of these attacks involve the
act of social engineering. The targeted assets are applications, back end services
as well as personal identifiable information.
Denial of Service: The components of big data are mostly under the threat of
denial of service attacks. This type of attacks exhausts the resources that are
assets that are affected in this category of threat are software, data, storage
infrastructure, computing infrastructure and big data analytics. This is the most
typical type of threat for big data. Weakness of any system is its redundancy.
2. Interception, Eavesdropping and Hijacking: This group of threat involves
manipulation or alteration of the process of communication among the parties. Additional tools
are not needed on the infrastructure of the victim.
Information Interception: ICT infrastructure often faces this issue of
communication interception between the nodes. The tools of big data are not
secured most of the times. There is lack of proper protocols for maintaining
integrity and confidentiality among the communicating applications. The back
end servers as well as applications are affected by this issue.
3. Nefarious Activity and Abuse: This is a type of deliberate attack where the attacker
tries to alter the ICT infrastructure of the victim (Chen & Zhang, 2014). They use specific
software and tools. There several threats under this category:
Identity Fraud: The system of big data stores financial information and personal
details of the user like the information about credit card. These sensitive data are
targeted by the hackers. Getting an access to such sensitive data will give the
hacker a power over the over the organization. Most of these attacks involve the
act of social engineering. The targeted assets are applications, back end services
as well as personal identifiable information.
Denial of Service: The components of big data are mostly under the threat of
denial of service attacks. This type of attacks exhausts the resources that are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SYSTEM RISK MANAGEMENT
limited. It keeps the server busy so that the actual tasks are not done. The assets
that are under the target of this threat are servers and networks.
Malicious software or code: ICT components are affected by the generic threats.
Malicious codes or programs are built and injected in a system to affect the
system. Viruses and worms are types of malware. Trojan horses are also under
this category. This Trojan horse allows remote attackers to access the system.
Spoofing is another type of attack where the attacker pretends to be someone else
and gets access to the sensitive data of the victim. Backdoors are a type of
undocumented points from where the attackers come in. There is another category
of threat like web attacks. This attack takes place through the applications of the
internet.
Business process failure: Damage of the business assets can take place when
proper execution of the business process does not take place. The data leak can
take place due to mismanagement of the business processes.
4. Legal Threat: Threats can also take place due to legal implications. Violation of
regulations, laws and legislations can take place. The organization can fail to meet the criteria of
legal contract.
5. Organizational Threats: This type of threat occurs due to some kind of issue that take
place in the organization. There can be certain issues like shortage of skills that leads to the
organizational threat. If the employees of the company are not properly skilled and there is lack
of training then it can affect the productivity of the company as a whole. The employees must
learn to handle different situations that take place in the company. The researchers and managers
limited. It keeps the server busy so that the actual tasks are not done. The assets
that are under the target of this threat are servers and networks.
Malicious software or code: ICT components are affected by the generic threats.
Malicious codes or programs are built and injected in a system to affect the
system. Viruses and worms are types of malware. Trojan horses are also under
this category. This Trojan horse allows remote attackers to access the system.
Spoofing is another type of attack where the attacker pretends to be someone else
and gets access to the sensitive data of the victim. Backdoors are a type of
undocumented points from where the attackers come in. There is another category
of threat like web attacks. This attack takes place through the applications of the
internet.
Business process failure: Damage of the business assets can take place when
proper execution of the business process does not take place. The data leak can
take place due to mismanagement of the business processes.
4. Legal Threat: Threats can also take place due to legal implications. Violation of
regulations, laws and legislations can take place. The organization can fail to meet the criteria of
legal contract.
5. Organizational Threats: This type of threat occurs due to some kind of issue that take
place in the organization. There can be certain issues like shortage of skills that leads to the
organizational threat. If the employees of the company are not properly skilled and there is lack
of training then it can affect the productivity of the company as a whole. The employees must
learn to handle different situations that take place in the company. The researchers and managers

8SYSTEM RISK MANAGEMENT
in the organization need to be well skilled. The targeted asset in this case is the different roles
played by the employees of the organization.
The most significant threat is the threat of malware or malicious code or programs.
Malicious software is extremely harmful for the organization. They are not accidental threats.
They are deliberate threats. Intentional actions are taken to harm the system of an organization.
The ICT components of the infrastructure of the company are affected by the malicious codes.
These codes are extremely harmful because they modify the data in the system. These codes can
also remove or delete sensitive information from the system (Kshetri, 2014). Sometimes these
threats can just misuse the sensitive information to harm the company. Exploit kits are
responsible for the infecting any system with virus and worms. Worms are responsible for
copying important documents of a system and passing it to another network or system. Trojan
horses ate another type of malware that keeps the network busy and utilizes the resources and
makes the server slow. Later on this network is unable to perform the required function.
Backdoors are another type of threat under this category that infects a computer through
undocumented entry. Spoofing is done by an attacker who masks himself and hides his identity
to gain access to the system. They use sensitive data and take advantage of it. Some of the
attacks are through web applications. Some infected codes are injected that lead to this type of
threat. The malicious codes are first injected in the system and then it harms the system.
Malicious code attack is considered to be the most harmful threat or significant threat
because the intention of the attacker in this case is wrong. It is not an accidental threat. This
threat is deliberate threat. The risk exposure of deliberate threat is extremely high because it
cannot be rectified. In case of accidental threats like human error, the mistakes can be rectified
after identification. One big example of malicious software attack is the fault in the logging
in the organization need to be well skilled. The targeted asset in this case is the different roles
played by the employees of the organization.
The most significant threat is the threat of malware or malicious code or programs.
Malicious software is extremely harmful for the organization. They are not accidental threats.
They are deliberate threats. Intentional actions are taken to harm the system of an organization.
The ICT components of the infrastructure of the company are affected by the malicious codes.
These codes are extremely harmful because they modify the data in the system. These codes can
also remove or delete sensitive information from the system (Kshetri, 2014). Sometimes these
threats can just misuse the sensitive information to harm the company. Exploit kits are
responsible for the infecting any system with virus and worms. Worms are responsible for
copying important documents of a system and passing it to another network or system. Trojan
horses ate another type of malware that keeps the network busy and utilizes the resources and
makes the server slow. Later on this network is unable to perform the required function.
Backdoors are another type of threat under this category that infects a computer through
undocumented entry. Spoofing is done by an attacker who masks himself and hides his identity
to gain access to the system. They use sensitive data and take advantage of it. Some of the
attacks are through web applications. Some infected codes are injected that lead to this type of
threat. The malicious codes are first injected in the system and then it harms the system.
Malicious code attack is considered to be the most harmful threat or significant threat
because the intention of the attacker in this case is wrong. It is not an accidental threat. This
threat is deliberate threat. The risk exposure of deliberate threat is extremely high because it
cannot be rectified. In case of accidental threats like human error, the mistakes can be rectified
after identification. One big example of malicious software attack is the fault in the logging
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SYSTEM RISK MANAGEMENT
system of Hadoop. Intentional threats are dangerous and affect the system in a severe manner.
Malicious codes fall under this category and protective measures need to be taken so avoid such
threats.
3. Key Threat Agents and Ways to Minimize their Impact
Key threat agents are responsible for affecting an organization or system (Lu et al.,
2014). Someone who has the capability to exploit the weakness of the system and take advantage
of it is called key threat agent. The key threat agents are given as follows:
Corporation: These organizations are involved in any type of tactics that are
offensive. They act as a key threat agent.
Cyber criminals: These types of agents are hostile nature. The motive behind this
type of agent is the gain of financial data. Cybercriminals can attack locally,
nationally as well as internationally.
Cyber terrorists: These type of threat agents are growing at a fast pace and they
are responsible for most of the cyber attacks that take place. Their motive can be
political or regional. They aim to harm the public infrastructure and the
telecommunication sector.
Script kiddies: These agents are not skilled. They use the programs and scripts
that are developed by different attackers to attack the system or networks.
Hacktivists: These are individuals that get their motivation from a political or
social source. They use the information systems to place their opinions and
protest regarding certain matter. They target websites that have high profile,
military institutes as well as intelligence agencies.
system of Hadoop. Intentional threats are dangerous and affect the system in a severe manner.
Malicious codes fall under this category and protective measures need to be taken so avoid such
threats.
3. Key Threat Agents and Ways to Minimize their Impact
Key threat agents are responsible for affecting an organization or system (Lu et al.,
2014). Someone who has the capability to exploit the weakness of the system and take advantage
of it is called key threat agent. The key threat agents are given as follows:
Corporation: These organizations are involved in any type of tactics that are
offensive. They act as a key threat agent.
Cyber criminals: These types of agents are hostile nature. The motive behind this
type of agent is the gain of financial data. Cybercriminals can attack locally,
nationally as well as internationally.
Cyber terrorists: These type of threat agents are growing at a fast pace and they
are responsible for most of the cyber attacks that take place. Their motive can be
political or regional. They aim to harm the public infrastructure and the
telecommunication sector.
Script kiddies: These agents are not skilled. They use the programs and scripts
that are developed by different attackers to attack the system or networks.
Hacktivists: These are individuals that get their motivation from a political or
social source. They use the information systems to place their opinions and
protest regarding certain matter. They target websites that have high profile,
military institutes as well as intelligence agencies.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10SYSTEM RISK MANAGEMENT
Employees: The company employees are also threat agent. The staffs, contractors
as well as all the operational staffs are key threat agents. They have the access to
the sensitive information and details of the company. They can reveal the
sensitive data to their competitors and harm the company in a severe manner.
Nation states: They have great capability to harm any organization.
Ways to Minimize the Impact: Cryptographic algorithm can be used in order to protect
the system. Encrypting sensitive data can be of great help in order to protect the system from any
unauthorized access. Regular check of data integrity can be done in order to protect the system
(Thuraisingham, 2015). Strong security policies can be used in order to protect the information
from any harmful effect. A trusted platform must be implemented to secure the network. The
access control methods must be made more secured (Cardenas, Manadhata & Rajan, 2013).
Implementation of prevention controls will help the organization to become stronger in terms of
security.
Threat Probability Trend: It can be seen from the case study that each threat has a type
probability trend. The threat agent employees can be responsible for the information leak, design
problem, identity fraud, malware as well as the failure of the business process. The probability of
the involvement of threat agents like corporation, cyber criminals are high in case of information
interception (Chen, Mao & Liu, 2014). The identity threat can involve the engagement of all the
threat agents. Proper risk management needs to be carried out for effective functioning of the
organization (Demchenko et al., 2013). The probability of threat trends are increasing at a fast
pace and can be minimized by strong security policies.
Employees: The company employees are also threat agent. The staffs, contractors
as well as all the operational staffs are key threat agents. They have the access to
the sensitive information and details of the company. They can reveal the
sensitive data to their competitors and harm the company in a severe manner.
Nation states: They have great capability to harm any organization.
Ways to Minimize the Impact: Cryptographic algorithm can be used in order to protect
the system. Encrypting sensitive data can be of great help in order to protect the system from any
unauthorized access. Regular check of data integrity can be done in order to protect the system
(Thuraisingham, 2015). Strong security policies can be used in order to protect the information
from any harmful effect. A trusted platform must be implemented to secure the network. The
access control methods must be made more secured (Cardenas, Manadhata & Rajan, 2013).
Implementation of prevention controls will help the organization to become stronger in terms of
security.
Threat Probability Trend: It can be seen from the case study that each threat has a type
probability trend. The threat agent employees can be responsible for the information leak, design
problem, identity fraud, malware as well as the failure of the business process. The probability of
the involvement of threat agents like corporation, cyber criminals are high in case of information
interception (Chen, Mao & Liu, 2014). The identity threat can involve the engagement of all the
threat agents. Proper risk management needs to be carried out for effective functioning of the
organization (Demchenko et al., 2013). The probability of threat trends are increasing at a fast
pace and can be minimized by strong security policies.

11SYSTEM RISK MANAGEMENT
4. ETL Process Improvement
Huge number of information is present in big data. This leads to several security threats
that can be mitigated by many methods. ETL stands for extract transform and load. This process
is very helpful in the analysis of big data (Bansal, 2014). The following are the steps to improve
the ETL process:
Minimum data can be utilized. Batch processing tends to consume a huge amount
of database storage space (Bansal & Kagemann, 2015). If only important and
required data are extracted then this will improve the system performance
The row by row lookup can be avoided for efficient performance of data
operations (Baumer, 2017). It is much better than the process of bulk loading.
5. IT Security of ENISA
ENISA does not seem to be satisfied with the current state of the security system. There
are several reasons behind this. There are several threats and key threat agents existing. This case
study points out all the major threats that exist in the organization. The most significant threat is
malicious software. There are several types of threats under this category like spoofing, Trojan
horses and backdoor attacks. These threats can affect the system and misuse the information of
the organization. Encryption or cryptography is the most effective solution to overcome the
problems of security threats. Firewalls can also be implemented in order to protect the private
network from any external intrusion. IPS can also help to protect the network by infiltration by
preventing any unauthorized database access of ENISA.
4. ETL Process Improvement
Huge number of information is present in big data. This leads to several security threats
that can be mitigated by many methods. ETL stands for extract transform and load. This process
is very helpful in the analysis of big data (Bansal, 2014). The following are the steps to improve
the ETL process:
Minimum data can be utilized. Batch processing tends to consume a huge amount
of database storage space (Bansal & Kagemann, 2015). If only important and
required data are extracted then this will improve the system performance
The row by row lookup can be avoided for efficient performance of data
operations (Baumer, 2017). It is much better than the process of bulk loading.
5. IT Security of ENISA
ENISA does not seem to be satisfied with the current state of the security system. There
are several reasons behind this. There are several threats and key threat agents existing. This case
study points out all the major threats that exist in the organization. The most significant threat is
malicious software. There are several types of threats under this category like spoofing, Trojan
horses and backdoor attacks. These threats can affect the system and misuse the information of
the organization. Encryption or cryptography is the most effective solution to overcome the
problems of security threats. Firewalls can also be implemented in order to protect the private
network from any external intrusion. IPS can also help to protect the network by infiltration by
preventing any unauthorized database access of ENISA.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





