ENISA Case Study: Big Data Security and Threats Analysis
VerifiedAdded on 2019/11/12
|13
|3228
|258
Case Study
AI Summary
This case study report analyzes the ENISA's big data security infrastructure, addressing various privacy concerns and security measures. The report examines key threats, including web-based attacks and malware, and identifies threat agents like cyber terrorists and criminals. It explores the ETL process and suggests improvements, highlighting the importance of data loading and batching. The report concludes by evaluating ENISA's current state of IT security, emphasizing the need for continuous improvement in response to evolving threats and vulnerabilities. The analysis covers topics like data manipulation attacks, the impact of malware, and the role of ENISA in addressing these challenges. The report also discusses the trends in threat probability and how ENISA can improve its processes.

ENISA
CASE
STUDY
Report
CASE
STUDY
Report
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Question 1:.......................................................................................................................................2
Question 2:.......................................................................................................................................2
Question 3:.......................................................................................................................................2
Question 4:.......................................................................................................................................2
Question 5:.......................................................................................................................................2
References........................................................................................................................................3
Question 1:.......................................................................................................................................2
Question 2:.......................................................................................................................................2
Question 3:.......................................................................................................................................2
Question 4:.......................................................................................................................................2
Question 5:.......................................................................................................................................2
References........................................................................................................................................3

Question 1:
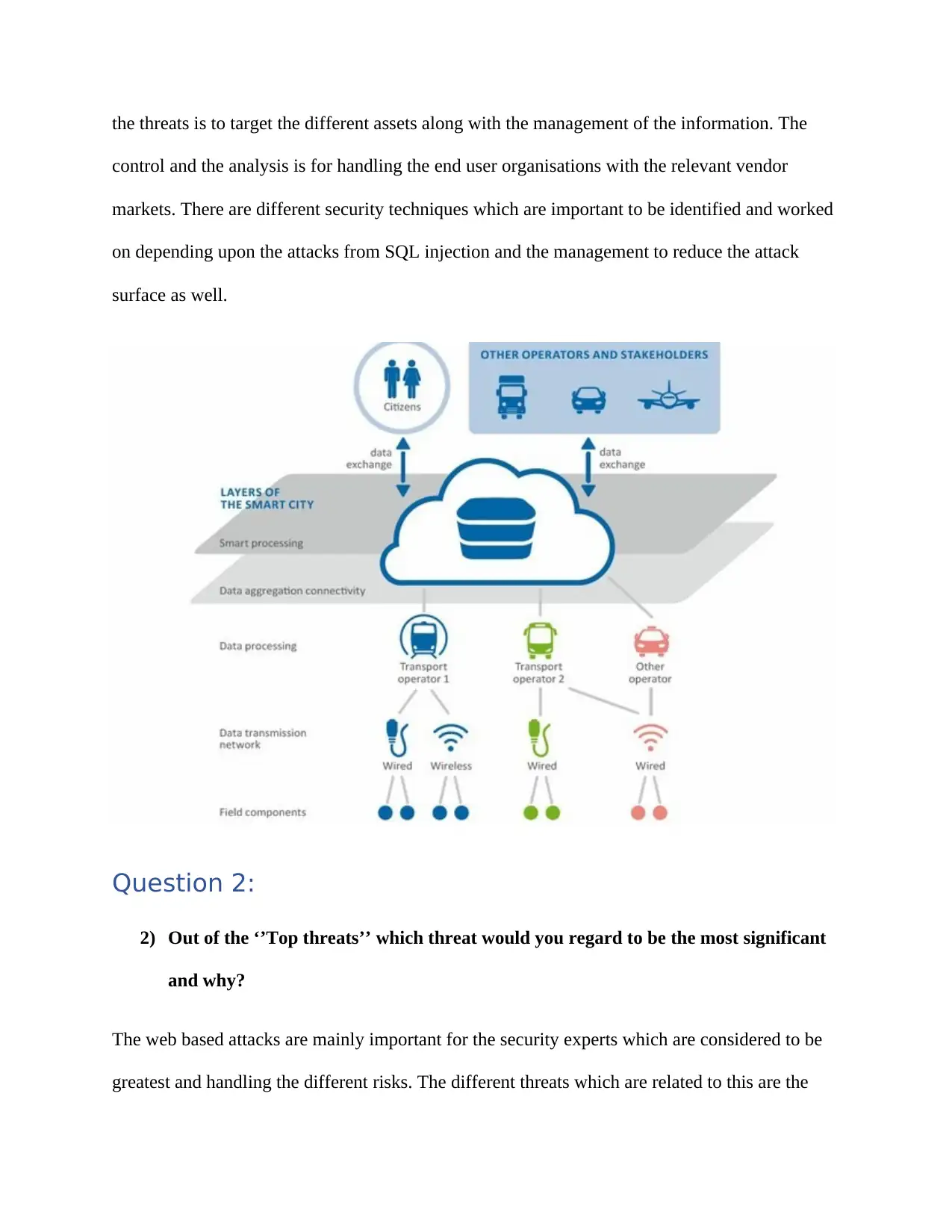
1) Provide a brief overview of the case study and prepare a diagram for the ENISA Big
Data security infrastructure.
The extensive collection is based on the data processes with the big data analytics that include
the different and serious privacy concerns. The wider scale impacts of the surveillance, profiling
is based on allowing the benefits without any invasion of the individual private spheres. The
appraise big data is to integrate and focus on the protection of the data safeguards which aim at
the support to handle the legal obligations. (Marions et al., 2012). ENISA works on the
categorisation and the challenges which are used for the three cases mainly for the advancement
in the Security Incident Event Management, the industrial control systems and the other
telecoms. The privacy by the designing in big data is for processing the information with the big
data analytics that have also given rise to the serious privacy concerns as well. The scale of the
electronic surveillance, profiling and the other disclosures of the data is mainly to handle the
integration with the data protection safeguards that are set to work on addressing the different
opportunities of the technology for privacy (Gorton, 2015).
The security measures that have been taken are mainly for the smart grids which enable the
efficient use of the energy. Along with this, ENISA works on the smart grid patterns where the
analysis is for the risks assessment and to handle the set of the different theories (Barnard, 2014).
The certification of the components and the meta-schemes are related to handle the supply chain
view of the smart grid where the support comes from the dialogue among the stakeholders.
ENISA works on the security network tools which have been used for the management of the
technology and to handle the cyber security and for the data duplication. Here, the balancing of
1) Provide a brief overview of the case study and prepare a diagram for the ENISA Big
Data security infrastructure.
The extensive collection is based on the data processes with the big data analytics that include
the different and serious privacy concerns. The wider scale impacts of the surveillance, profiling
is based on allowing the benefits without any invasion of the individual private spheres. The
appraise big data is to integrate and focus on the protection of the data safeguards which aim at
the support to handle the legal obligations. (Marions et al., 2012). ENISA works on the
categorisation and the challenges which are used for the three cases mainly for the advancement
in the Security Incident Event Management, the industrial control systems and the other
telecoms. The privacy by the designing in big data is for processing the information with the big
data analytics that have also given rise to the serious privacy concerns as well. The scale of the
electronic surveillance, profiling and the other disclosures of the data is mainly to handle the
integration with the data protection safeguards that are set to work on addressing the different
opportunities of the technology for privacy (Gorton, 2015).
The security measures that have been taken are mainly for the smart grids which enable the
efficient use of the energy. Along with this, ENISA works on the smart grid patterns where the
analysis is for the risks assessment and to handle the set of the different theories (Barnard, 2014).
The certification of the components and the meta-schemes are related to handle the supply chain
view of the smart grid where the support comes from the dialogue among the stakeholders.
ENISA works on the security network tools which have been used for the management of the
technology and to handle the cyber security and for the data duplication. Here, the balancing of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
the threats is to target the different assets along with the management of the information. The
control and the analysis is for handling the end user organisations with the relevant vendor
markets. There are different security techniques which are important to be identified and worked
on depending upon the attacks from SQL injection and the management to reduce the attack
surface as well.
Question 2:
2) Out of the ‘’Top threats’’ which threat would you regard to be the most significant
and why?
The web based attacks are mainly important for the security experts which are considered to be
greatest and handling the different risks. The different threats which are related to this are the
control and the analysis is for handling the end user organisations with the relevant vendor
markets. There are different security techniques which are important to be identified and worked
on depending upon the attacks from SQL injection and the management to reduce the attack
surface as well.
Question 2:
2) Out of the ‘’Top threats’’ which threat would you regard to be the most significant
and why?
The web based attacks are mainly important for the security experts which are considered to be
greatest and handling the different risks. The different threats which are related to this are the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

traditional penetration testing which includes the exercising of the network with the attack target.
The web based attacks mainly focus on the applications with the functional layers (Louis, 2013).
Here, the web based attack is considered to be the major attack which leads to the malicious end
user activity to breach the system protection mechanism. Along with this, there is a possibility
that it includes the information gathered from the social security numbers and the other identity
thefts which leads to the loss of information of ENISA (Fransen et al., 2015). Hence, for this, it
is important that all the web application attacks are compromised or modified depending upon
the parameters which are based on checking or handling the instruction spoofing. It includes the
denial of service attack which includes the generation of the attack by the malicious users with
the competitors and the script kiddies. Hence, it is also important to work on the authorisation
control which is reliable and requisite based on guarding the sensitive information. The standards
are set to meet the intellectual property rights with protecting the products of the intellect that
includes the commercialised laws and the other literary or the artistic works. The business
methods include the functioning and the standards set for the industrial purposes with different
aspects of the attacks that are being conducted by an individual. It is important to focus on the
applications with the attacks based on the target systems and associate with the suspected
vulnerable applications. The applications also include the versions of the detection which could
easily be performed through the banner grabbing (ENISA, 2013). The banner grabbing methods
include the intrusion detection system and the preventive systems that are for the detective and
the reactive devices which are set for the network and the other applications which include the
targeted attacks. The standards are also set for the deployment of the demilitarized zones of the
corporate networks and how it is easy to filter or block the attacks at the application layer
services. The data manipulation attacks on the applications with the privileges on hosts relate to
The web based attacks mainly focus on the applications with the functional layers (Louis, 2013).
Here, the web based attack is considered to be the major attack which leads to the malicious end
user activity to breach the system protection mechanism. Along with this, there is a possibility
that it includes the information gathered from the social security numbers and the other identity
thefts which leads to the loss of information of ENISA (Fransen et al., 2015). Hence, for this, it
is important that all the web application attacks are compromised or modified depending upon
the parameters which are based on checking or handling the instruction spoofing. It includes the
denial of service attack which includes the generation of the attack by the malicious users with
the competitors and the script kiddies. Hence, it is also important to work on the authorisation
control which is reliable and requisite based on guarding the sensitive information. The standards
are set to meet the intellectual property rights with protecting the products of the intellect that
includes the commercialised laws and the other literary or the artistic works. The business
methods include the functioning and the standards set for the industrial purposes with different
aspects of the attacks that are being conducted by an individual. It is important to focus on the
applications with the attacks based on the target systems and associate with the suspected
vulnerable applications. The applications also include the versions of the detection which could
easily be performed through the banner grabbing (ENISA, 2013). The banner grabbing methods
include the intrusion detection system and the preventive systems that are for the detective and
the reactive devices which are set for the network and the other applications which include the
targeted attacks. The standards are also set for the deployment of the demilitarized zones of the
corporate networks and how it is easy to filter or block the attacks at the application layer
services. The data manipulation attacks on the applications with the privileges on hosts relate to

the different failures of the unauthorised logins and the access is done to the sensitive data as
well. The malware is also another threat which can lead to the damages in the system which is
considered to be the major global issue for the organisation. It also affects the system and the
important files of the business where there is no possibility to recover them as well. The
information could be set with the malware that are linked with URL of the websites and then it is
installed in the systems. The software brings a major damage to the system (Theoharidou et al.,
2013).
Question 3:
3) Identify and discuss the key Threat Agents. What could be done to minimize their
impact on the system? Based on the data provided, discuss the trends in threat probability.
The threats are related to the media attention with the successful cyber-attacks, which creates the
higher adaptability for the criminals. There are other agents like the cyber terrorists and the cyber
criminals include the use of the Internet to conduct the different violent acts which leads to the
threatening of the body. There are different terrorist activities which includes the use and relation
to the deployment of disruption against the information system or primary purpose for creating
alarms. This includes the use of the computer, network and the other public internet resources
which leads to the failure and distribution for the personal objectives as well. The issues and the
major concern is about the instances of cyberterrorism which includes the utilisation of the
internet to connect and communicate with the supporters and even to recruit the different new
members. The cybercrime is related to the computer or the network which includes the offences
mainly related to the criminal motives to harm the reputation of the victim and then cause the
well. The malware is also another threat which can lead to the damages in the system which is
considered to be the major global issue for the organisation. It also affects the system and the
important files of the business where there is no possibility to recover them as well. The
information could be set with the malware that are linked with URL of the websites and then it is
installed in the systems. The software brings a major damage to the system (Theoharidou et al.,
2013).
Question 3:
3) Identify and discuss the key Threat Agents. What could be done to minimize their
impact on the system? Based on the data provided, discuss the trends in threat probability.
The threats are related to the media attention with the successful cyber-attacks, which creates the
higher adaptability for the criminals. There are other agents like the cyber terrorists and the cyber
criminals include the use of the Internet to conduct the different violent acts which leads to the
threatening of the body. There are different terrorist activities which includes the use and relation
to the deployment of disruption against the information system or primary purpose for creating
alarms. This includes the use of the computer, network and the other public internet resources
which leads to the failure and distribution for the personal objectives as well. The issues and the
major concern is about the instances of cyberterrorism which includes the utilisation of the
internet to connect and communicate with the supporters and even to recruit the different new
members. The cybercrime is related to the computer or the network which includes the offences
mainly related to the criminal motives to harm the reputation of the victim and then cause the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

physical and mental harm. There is a major loss which threatens the person with the national
security and the financial health (Furnell et al., 2015). The governmental and the non-state actors
engage in cybercrime which includes the financial theft and the other criminal cross borders. The
standards are set with the altering, destroying or supressing mainly that leads to the concealing of
any unauthorised transactions. The alterations or the deletion of the stored data has a major
impact on the internet scam which includes the phishing and the social engineering effects,
which includes the target on the consumers and the business. The cyberterrorism occurs on the
website which includes the increased attacks on the corporate websites and how it includes the
ability to operate and demand for the payments (Hopkins et al., 2015). The computer viruses,
denial of service attacks and malware is considered to be the major issue which involves the
lesser expertise in technical approach. The fraud and the identity theft is also considered to be the
major issue which includes the use of the malware and the other hacking or the phishing targets.
The tool includes the obscene with the offensive content that is mainly due to the
communications done in between the people. ENISA focus on handling the harassment with
taking hold of the self-motivated groups who work on the exploitation of the politics in the
country. The cyber terrorists are also targeting all the large-scale sabotages with the national and
the international security in the country. There are issues with the different trends which include
the cyber maltreatment and how the identity theft or the collection of the private information, or
the personalised data is set through the different operational activities (Levy et al., 2015).
Question 4:
4) How could the ETL process be improved? Discuss.
security and the financial health (Furnell et al., 2015). The governmental and the non-state actors
engage in cybercrime which includes the financial theft and the other criminal cross borders. The
standards are set with the altering, destroying or supressing mainly that leads to the concealing of
any unauthorised transactions. The alterations or the deletion of the stored data has a major
impact on the internet scam which includes the phishing and the social engineering effects,
which includes the target on the consumers and the business. The cyberterrorism occurs on the
website which includes the increased attacks on the corporate websites and how it includes the
ability to operate and demand for the payments (Hopkins et al., 2015). The computer viruses,
denial of service attacks and malware is considered to be the major issue which involves the
lesser expertise in technical approach. The fraud and the identity theft is also considered to be the
major issue which includes the use of the malware and the other hacking or the phishing targets.
The tool includes the obscene with the offensive content that is mainly due to the
communications done in between the people. ENISA focus on handling the harassment with
taking hold of the self-motivated groups who work on the exploitation of the politics in the
country. The cyber terrorists are also targeting all the large-scale sabotages with the national and
the international security in the country. There are issues with the different trends which include
the cyber maltreatment and how the identity theft or the collection of the private information, or
the personalised data is set through the different operational activities (Levy et al., 2015).
Question 4:
4) How could the ETL process be improved? Discuss.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The process of ELS could be handled through the loading process which includes how the data is
changed with the reduced forms of the categories that work on speeding up the higher volume of
the ETL processes. With this, it also includes the different rows and the columns which includes
the creation of the extra tables that tends to hold the data from any of the previous ETL
processes. The use of the batching process could also be helpful in improving the performance
where the standards are set to meet the data communication and handling the load on the network
or any conflicts which are on the performing of the database. The flow of the user SQL Server
Destination in the Data Flow Task need to work on the SQL patterns with handling the ETL
processes by reducing any limitations and then working on the increased benefits. This will lead
to the facilitation scenario and how communication could be done.
From ETL 2013 to ETL 2015, it has been seen that there are different sets of the comprehensive
information collection that is based on the source material. It includes the contexts and the other
identification of the relevant content, like the threats or the agents and the trends. It includes how
the ETL in 2014, works on the consolidation of the framework and check for the improvement of
the different technological standards and the application areas (Prislan, 2014). This includes the
references which works for the sources that are for the decision making, security and the other
navigation processes through the threat landscape. In 2015, and in 2016, ETL has been working
on the improvement of the system with smoother advancement of the maturity. Through this,
there is a possibility to work on increased cooperation and the reactions for the cyber threats.
This also works with the advancement of the malicious tools with obfuscation and striking
power. Here, the objective is mainly to handle the provisions and work towards the identification
and improving the processes (Skrzewski, 2014). It includes the leverages on the synergies and
the use of the open source approaches, tools and the data. The objective is based on the project to
changed with the reduced forms of the categories that work on speeding up the higher volume of
the ETL processes. With this, it also includes the different rows and the columns which includes
the creation of the extra tables that tends to hold the data from any of the previous ETL
processes. The use of the batching process could also be helpful in improving the performance
where the standards are set to meet the data communication and handling the load on the network
or any conflicts which are on the performing of the database. The flow of the user SQL Server
Destination in the Data Flow Task need to work on the SQL patterns with handling the ETL
processes by reducing any limitations and then working on the increased benefits. This will lead
to the facilitation scenario and how communication could be done.
From ETL 2013 to ETL 2015, it has been seen that there are different sets of the comprehensive
information collection that is based on the source material. It includes the contexts and the other
identification of the relevant content, like the threats or the agents and the trends. It includes how
the ETL in 2014, works on the consolidation of the framework and check for the improvement of
the different technological standards and the application areas (Prislan, 2014). This includes the
references which works for the sources that are for the decision making, security and the other
navigation processes through the threat landscape. In 2015, and in 2016, ETL has been working
on the improvement of the system with smoother advancement of the maturity. Through this,
there is a possibility to work on increased cooperation and the reactions for the cyber threats.
This also works with the advancement of the malicious tools with obfuscation and striking
power. Here, the objective is mainly to handle the provisions and work towards the identification
and improving the processes (Skrzewski, 2014). It includes the leverages on the synergies and
the use of the open source approaches, tools and the data. The objective is based on the project to

work on the implementation of the improvement options with the ENISA working over the threat
analysis procedures.
Along with this, it is important for ENISA to focus on improving and handling the threats which
are mainly through the deep research and from the references which includes the denial of
service attacks. With this, ETL also includes the complex issues where there is a physical coating
of the hardware devices. One need to identity the significant assets and the other assessments
based on the standardised device interfaces. This includes the networks with the virtualisation
that includes the centralised control over the networks, which includes the management of the
network and the issues that relate to the data flow (Mayer et al., 2013). The attack is mainly on
the component of the network with the major effect on the centralised control functions with the
coupling that is over the data transmission through switches. The malware like the Trojans and
worms are considered to be the challenging threats.
Question 5:
5) To sum up, should ENISA be satisfied with its current state of IT Security? Why? Or
Why not?
This research is based on the conclusions where ENISA works towards the current state of the IT
security standards which works on the different threats. This includes the prioritisation with the
focus on the attack surfaces and how the injection attacks lead to the exploitation of the kits,
spam and the phishing. The measures are mainly obtained through the ENISA which not only
includes the reduced effects of the threats but also focus on the working over the security of the
data. Here, the ETL processes are based on improving the data extraction and working on the
analysis procedures.
Along with this, it is important for ENISA to focus on improving and handling the threats which
are mainly through the deep research and from the references which includes the denial of
service attacks. With this, ETL also includes the complex issues where there is a physical coating
of the hardware devices. One need to identity the significant assets and the other assessments
based on the standardised device interfaces. This includes the networks with the virtualisation
that includes the centralised control over the networks, which includes the management of the
network and the issues that relate to the data flow (Mayer et al., 2013). The attack is mainly on
the component of the network with the major effect on the centralised control functions with the
coupling that is over the data transmission through switches. The malware like the Trojans and
worms are considered to be the challenging threats.
Question 5:
5) To sum up, should ENISA be satisfied with its current state of IT Security? Why? Or
Why not?
This research is based on the conclusions where ENISA works towards the current state of the IT
security standards which works on the different threats. This includes the prioritisation with the
focus on the attack surfaces and how the injection attacks lead to the exploitation of the kits,
spam and the phishing. The measures are mainly obtained through the ENISA which not only
includes the reduced effects of the threats but also focus on the working over the security of the
data. Here, the ETL processes are based on improving the data extraction and working on the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

insertion, and the medication patterns. This includes how the smoothening of the operations is
possible with the different ETL processes (Furnell et al., 2015). The threats are generally related
to the functioning which includes the embedded systems and how the hardware devices work on
easy handling of the different components. This is based on the attacks and the breach of the data
security measures. It is important to handle the information leakage with the standards that
include the higher security measures and the higher better security passwords which will help in
easy and fast access of the information as well. With this, the study is also on how ENISA focus
on the security framework which is based on providing and supporting with the better
networking components (Bora et al., 2013). This includes the influence that comes with the
processing and the working of the operations. The analysis is based on working over the security
patterns and how it is easy to operate the functions based on the detailed information and the
Threat agents. The social hacking issues also need to be resolved without any effect on the
organisation. This is only possible, when there is a proper setup of the security tools and the
impact of the services works on handling the current security standards and providing the brief.
The strategies are based on the combating of the Insider Threats with the focus on how to handle
the social hacking issues. The report discusses about the data that is related to the improvement
of the ETL processes. This works on the handling of the balances of the security and then
improving the maturity of the threat removal. It includes the proper balance of the threat and how
the security measures can be handled along with working on the controlled analysis patterns. The
strategies are depending upon the end-user organisations with the focus on improving the cyber
terrorism activities and handle the big data with the secured passwords. ENISA need to work on
the improvement with the firewall and Intrusion detection system. This will help in balancing
and setting all the controlled analysis with the relevant marketing standards in the secured
possible with the different ETL processes (Furnell et al., 2015). The threats are generally related
to the functioning which includes the embedded systems and how the hardware devices work on
easy handling of the different components. This is based on the attacks and the breach of the data
security measures. It is important to handle the information leakage with the standards that
include the higher security measures and the higher better security passwords which will help in
easy and fast access of the information as well. With this, the study is also on how ENISA focus
on the security framework which is based on providing and supporting with the better
networking components (Bora et al., 2013). This includes the influence that comes with the
processing and the working of the operations. The analysis is based on working over the security
patterns and how it is easy to operate the functions based on the detailed information and the
Threat agents. The social hacking issues also need to be resolved without any effect on the
organisation. This is only possible, when there is a proper setup of the security tools and the
impact of the services works on handling the current security standards and providing the brief.
The strategies are based on the combating of the Insider Threats with the focus on how to handle
the social hacking issues. The report discusses about the data that is related to the improvement
of the ETL processes. This works on the handling of the balances of the security and then
improving the maturity of the threat removal. It includes the proper balance of the threat and how
the security measures can be handled along with working on the controlled analysis patterns. The
strategies are depending upon the end-user organisations with the focus on improving the cyber
terrorism activities and handle the big data with the secured passwords. ENISA need to work on
the improvement with the firewall and Intrusion detection system. This will help in balancing
and setting all the controlled analysis with the relevant marketing standards in the secured
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

manner in the organisation (Weber et al., 2016). The effective coding practices with the proper
reports are mainly for the improvement in the standards of the system.
reports are mainly for the improvement in the standards of the system.

References
Barnard-Wills, D. (2014). ENISA Threat Landscape and Good Practice Guide for Smart Home and
Converged Media. ENISA (The European Network and Information Security Agency).
Bora, M. S., & Singh, A. (2013). Cyber Threats and Security for Wireless Devices. Journal of
Environmental Science, Computer Science and Engineering & Technology (JECET), 2(2), 277-
284.
ENISA, E. T. L. (2013). Overview of current and emerging cyber-threats. European Union Agency for
network and information security.
Fransen, F., Smulders, A., & Kerkdijk, R. (2015). Cyber security information exchange to gain insight into
the effects of cyber threats and incidents. e & i Elektrotechnik und Informationstechnik, 132(2),
106-112.
Furnell, S., Emm, D., & Papadaki, M. (2015). The challenge of measuring cyber-dependent
crimes. Computer Fraud & Security, 2015(10), 5-12.
Gorton, D. (2015). IncidentResponseSim: An agent-based simulation tool for risk management of online
Fraud. In Secure IT Systems (pp. 172-187). Springer, Cham.
Hopkins, M., & Dehghantanha, A. (2015, November). Exploit kits: the production line of the cybercrime
economy?. In Information Security and Cyber Forensics (InfoSec), 2015 Second International
Conference on (pp. 23-27). IEEE.
Lévy-Bencheton, C., Marinos, L., Mattioli, R., King, T., Dietzel, C., & Stumpf, J. (2015). Threat landscape
and good practice guide for internet infrastructure. Report, European Union Agency for Network
and Information Security (ENISA).
Louis Marinos, E. N. I. S. A. (2013). ENISA Threat Landscape 2013. European Network and Information
Security Agency.
Barnard-Wills, D. (2014). ENISA Threat Landscape and Good Practice Guide for Smart Home and
Converged Media. ENISA (The European Network and Information Security Agency).
Bora, M. S., & Singh, A. (2013). Cyber Threats and Security for Wireless Devices. Journal of
Environmental Science, Computer Science and Engineering & Technology (JECET), 2(2), 277-
284.
ENISA, E. T. L. (2013). Overview of current and emerging cyber-threats. European Union Agency for
network and information security.
Fransen, F., Smulders, A., & Kerkdijk, R. (2015). Cyber security information exchange to gain insight into
the effects of cyber threats and incidents. e & i Elektrotechnik und Informationstechnik, 132(2),
106-112.
Furnell, S., Emm, D., & Papadaki, M. (2015). The challenge of measuring cyber-dependent
crimes. Computer Fraud & Security, 2015(10), 5-12.
Gorton, D. (2015). IncidentResponseSim: An agent-based simulation tool for risk management of online
Fraud. In Secure IT Systems (pp. 172-187). Springer, Cham.
Hopkins, M., & Dehghantanha, A. (2015, November). Exploit kits: the production line of the cybercrime
economy?. In Information Security and Cyber Forensics (InfoSec), 2015 Second International
Conference on (pp. 23-27). IEEE.
Lévy-Bencheton, C., Marinos, L., Mattioli, R., King, T., Dietzel, C., & Stumpf, J. (2015). Threat landscape
and good practice guide for internet infrastructure. Report, European Union Agency for Network
and Information Security (ENISA).
Louis Marinos, E. N. I. S. A. (2013). ENISA Threat Landscape 2013. European Network and Information
Security Agency.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





