ENISA Threat Landscape Analysis
VerifiedAdded on 2019/10/16
|8
|1588
|308
Homework Assignment
AI Summary
This assignment analyzes the ENISA Threat Landscape report, focusing on various cyber threats and their impact. It addresses different threat agents, including cybercriminals, social hackers, and hacktivists, and explores mitigation strategies. The analysis covers various attack vectors such as web-based attacks, insider threats (malicious code, data breaches, phishing), and the significance of each. The assignment also discusses the improvement of the ETL process and the overall satisfaction with the current state of IT security based on ENISA's findings. The solutions provided include using strong passwords, avoiding unknown links, regular auditing, and secure data handling practices. The references cited include relevant research papers and reports on cybersecurity threats and mitigation strategies.
enisa threat landscape
[Document subtitle]
[Document subtitle]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1
ANSWER 1
The case was about the ENISA which highlighted the variation in the system of information
technology in the year 2014. The report was published as ETL i.e. ENISA Threat Landscape.
ENISA is the center of expertise in cyber security in Europe. In the report, the cyber threat has
been identified. ETL demonstrated the information about the threat of landscape, the agents of
threat and the attack vectors (Marinos, 2013). The motive of ENISA behind issuing the report
was to contribute to the execution of the strategy of EU cyber security by using the attainable
information on the evolution of cyber. The report of ETL provides guidance and on that basis,
the management can make decisions and can implement policies related to the protection of
asset.
ANSWER 2
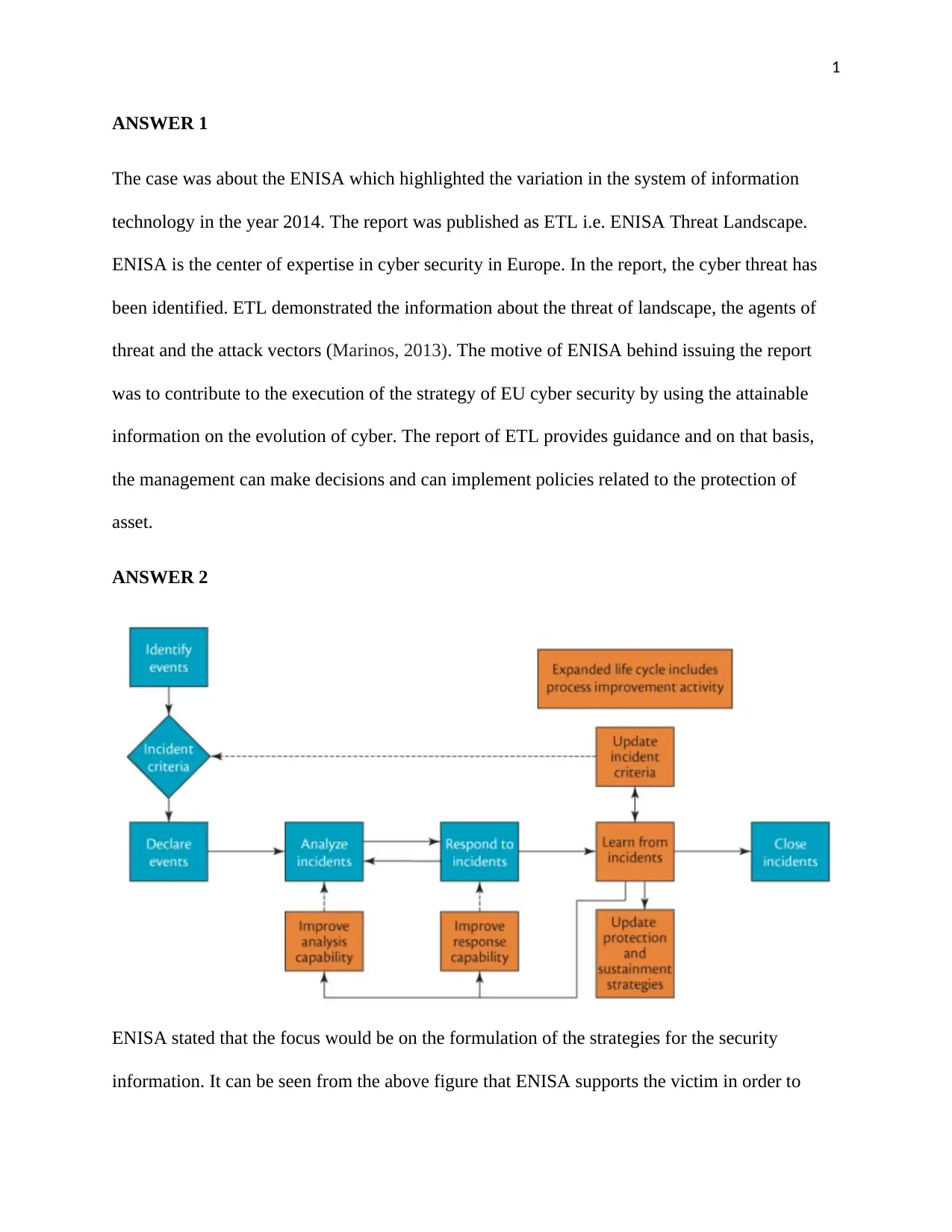
ENISA stated that the focus would be on the formulation of the strategies for the security
information. It can be seen from the above figure that ENISA supports the victim in order to
ANSWER 1
The case was about the ENISA which highlighted the variation in the system of information
technology in the year 2014. The report was published as ETL i.e. ENISA Threat Landscape.
ENISA is the center of expertise in cyber security in Europe. In the report, the cyber threat has
been identified. ETL demonstrated the information about the threat of landscape, the agents of
threat and the attack vectors (Marinos, 2013). The motive of ENISA behind issuing the report
was to contribute to the execution of the strategy of EU cyber security by using the attainable
information on the evolution of cyber. The report of ETL provides guidance and on that basis,
the management can make decisions and can implement policies related to the protection of
asset.
ANSWER 2
ENISA stated that the focus would be on the formulation of the strategies for the security
information. It can be seen from the above figure that ENISA supports the victim in order to

2
solve the problems of security. The organizations and people get the benefit from the usage of
the infrastructure of security. The guidelines for security are given which help the people to
remain safe from the threats of technology. The areas which demand more attention are smart
grids, cities, transport system, etc. The compromise cannot be done with these areas. The
articulation of the infrastructure of security support in mobilizing the community of cyber
security in an effective manner (ENISA, 2013).
ANSWER 3
The insider threats are the mixture of some threats like physical damage, data breach, phishing,
malicious code, etc. There are some strategies which will help in combatting the insider threats
are:
The tool of protection i.e. DDoS can handle the attacks of DDoS effectively with the help
of fire blades.
The practice of auditing on the regular basis will help in solving the problem affiliated to
SQL injection.
The problem of the data breach can be resolved if the sharing of data from one device to
another gets reduced.
The media which provide intelligence to the attackers should not be downloaded.
The file should be shared and transferred before the disposition of equipment of storage
as it retrieves the data if the formatting is done.
ANSWER 4
The web-based attack is the most significant as compared to the other threats as their main target
is the host. It pays more attention to the OSI system. It provides susceptibility of various
solve the problems of security. The organizations and people get the benefit from the usage of
the infrastructure of security. The guidelines for security are given which help the people to
remain safe from the threats of technology. The areas which demand more attention are smart
grids, cities, transport system, etc. The compromise cannot be done with these areas. The
articulation of the infrastructure of security support in mobilizing the community of cyber
security in an effective manner (ENISA, 2013).
ANSWER 3
The insider threats are the mixture of some threats like physical damage, data breach, phishing,
malicious code, etc. There are some strategies which will help in combatting the insider threats
are:
The tool of protection i.e. DDoS can handle the attacks of DDoS effectively with the help
of fire blades.
The practice of auditing on the regular basis will help in solving the problem affiliated to
SQL injection.
The problem of the data breach can be resolved if the sharing of data from one device to
another gets reduced.
The media which provide intelligence to the attackers should not be downloaded.
The file should be shared and transferred before the disposition of equipment of storage
as it retrieves the data if the formatting is done.
ANSWER 4
The web-based attack is the most significant as compared to the other threats as their main target
is the host. It pays more attention to the OSI system. It provides susceptibility of various
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
applications in order to misuse the personal information of the users like name, contact number,
date of birth, etc. The web-based attack badly impacted the areas like mobile computing, big
data, cloud computing, etc. the number of attacks are increasing by each passing day. The
number of attacks of web-based is very high in Europe and North America because of the
increase in online services. Therefore, the web-based attack is the most significant.
ANSWER 5
The following are the key threat agents and the measures that can be taken in order to reduce
their impact (Bologna, 2014):
Cybercriminals- the motive of this agent is to maximize the profit from the criminal
activities. The password can be used which cannot be accessed easily in order to reduce
the cyber crimes
Online social hackers- this deploys the cyber threat. They have the skills of engineering,
and they can study the psychology of their targets. It is required no to click the links to
the unknown sources in order to remain protected from the hackers.
Hacktivists- this group gets the attention of media, and the impact can be reduced by
improving the system security.
ANSWER 6
Steven stated that the two principles i.e. mistrust of authority and freedom of information are
related to the security system. This helps the hackers to identify themselves as a hat of black or
white. In a white hat, the freedom of information relies on such things like the exposure of
vulnerabilities (Nagpal, 2014). Some people had the large volume of data which was available
online, and this has been devised during the articulation of ethnic. Some aspects of testing of
applications in order to misuse the personal information of the users like name, contact number,
date of birth, etc. The web-based attack badly impacted the areas like mobile computing, big
data, cloud computing, etc. the number of attacks are increasing by each passing day. The
number of attacks of web-based is very high in Europe and North America because of the
increase in online services. Therefore, the web-based attack is the most significant.
ANSWER 5
The following are the key threat agents and the measures that can be taken in order to reduce
their impact (Bologna, 2014):
Cybercriminals- the motive of this agent is to maximize the profit from the criminal
activities. The password can be used which cannot be accessed easily in order to reduce
the cyber crimes
Online social hackers- this deploys the cyber threat. They have the skills of engineering,
and they can study the psychology of their targets. It is required no to click the links to
the unknown sources in order to remain protected from the hackers.
Hacktivists- this group gets the attention of media, and the impact can be reduced by
improving the system security.
ANSWER 6
Steven stated that the two principles i.e. mistrust of authority and freedom of information are
related to the security system. This helps the hackers to identify themselves as a hat of black or
white. In a white hat, the freedom of information relies on such things like the exposure of
vulnerabilities (Nagpal, 2014). Some people had the large volume of data which was available
online, and this has been devised during the articulation of ethnic. Some aspects of testing of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
penetration were established by the author in order to provide the rules for conducting the tests.
It has been seen that data piracy is also one of the biggest issues of hacking (Bologna, 2014).
ANSWER 7
In 2013, the threat which was rising on the regular basis were web- based attacks, Trojans, theft
of the identity, phishing, etc. All these threats were badly impacting the security system. The
other threats i.e. botnets and spam were stable. In the year 2014, the threats were malicious code,
phishing, denial of service, information leakage, etc. and the effect of other threats like spam,
botnets, etc. was reducing. It can be concluded that it is important to reduce the impact of threats
of 2014 in order to generate more profit in the organization and safeguard the security of the
system (Marinos, 2013).
ANSWER 8
The process of ETL can be improved by investigating the assets in order to identify the threats.
The owners of the internet infrastructure should analyze the preventive measures in order to deal
with the threats. The steps in the improvement of the process of ETL are spoofing, flooding,
routing the threats and the DNS poisoning. The owner should give all the details of the plan in
order to increase the level of safety (Mishra, 2016). ETL demand the coordination in the
networks of security of internet infrastructure. It also demands the involvement of the
authoritative and loyal employees for the security of the system.
ANSWER 9
Malicious code, phishing, and fraud are the most significant threat to the system of security.
penetration were established by the author in order to provide the rules for conducting the tests.
It has been seen that data piracy is also one of the biggest issues of hacking (Bologna, 2014).
ANSWER 7
In 2013, the threat which was rising on the regular basis were web- based attacks, Trojans, theft
of the identity, phishing, etc. All these threats were badly impacting the security system. The
other threats i.e. botnets and spam were stable. In the year 2014, the threats were malicious code,
phishing, denial of service, information leakage, etc. and the effect of other threats like spam,
botnets, etc. was reducing. It can be concluded that it is important to reduce the impact of threats
of 2014 in order to generate more profit in the organization and safeguard the security of the
system (Marinos, 2013).
ANSWER 8
The process of ETL can be improved by investigating the assets in order to identify the threats.
The owners of the internet infrastructure should analyze the preventive measures in order to deal
with the threats. The steps in the improvement of the process of ETL are spoofing, flooding,
routing the threats and the DNS poisoning. The owner should give all the details of the plan in
order to increase the level of safety (Mishra, 2016). ETL demand the coordination in the
networks of security of internet infrastructure. It also demands the involvement of the
authoritative and loyal employees for the security of the system.
ANSWER 9
Malicious code, phishing, and fraud are the most significant threat to the system of security.

5
Malicious code- this threat spreads from one system to the other with the help of the
medium. If the virus is not detected on time, then it overlaps the files of the system and
abandons the information of BIOS (Olesen, 2016).
Phishing- under this, the personal information is being accessed by the third person in
order to misuse the personal data. And the personal data is mainly accessed through the
social network.
Identity theft- under this threat, the information related to the identity is been stolen by
the hacker like personal profiling, financial identification, etc. This further causes the
financial problems to the people.
ANSWER 10
Yes, ENISA should be satisfied with the present state of the security of IT. Because, the research
conducted by ENISA helped in identifying the various solutions to the problems of security.
ENISA created awareness among people about the security of the system. The report contained
all the important aspects of cyber security infrastructure. This will help the organizations to find
the risks involved and they will make the decisions accordingly in order to generate more profit
and will increase the business value. ENISA helped in identifying the threats in an effective
manner.
Malicious code- this threat spreads from one system to the other with the help of the
medium. If the virus is not detected on time, then it overlaps the files of the system and
abandons the information of BIOS (Olesen, 2016).
Phishing- under this, the personal information is being accessed by the third person in
order to misuse the personal data. And the personal data is mainly accessed through the
social network.
Identity theft- under this threat, the information related to the identity is been stolen by
the hacker like personal profiling, financial identification, etc. This further causes the
financial problems to the people.
ANSWER 10
Yes, ENISA should be satisfied with the present state of the security of IT. Because, the research
conducted by ENISA helped in identifying the various solutions to the problems of security.
ENISA created awareness among people about the security of the system. The report contained
all the important aspects of cyber security infrastructure. This will help the organizations to find
the risks involved and they will make the decisions accordingly in order to generate more profit
and will increase the business value. ENISA helped in identifying the threats in an effective
manner.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
REFERENCES
Bologna, S., Lazari, A., & Mele, S. (2014). Improving Critical Infrastructure Protection and
Resilience against Terrorism Cyber Threats. Comprehensive Approach as" Sine Qua Non" for
Critical Infrastructure Protection, 39, 79.
ENISA, E. T. L. (2013). Overview of current and emerging cyber-threats.European Union
Agency for network and information security.
Harrop, W., & Matteson, A. (2015). Cyber Resilience: A Review of Critical National
Infrastructure and Cyber-Security Protection Measures Applied in the UK and USA. In Current
and Emerging Trends in Cyber Operations (pp. 149-166). Palgrave Macmillan UK.
Marinos, L. (2013). ENISA Threat Landscape 2013: Overview of current and emerging cyber-
threats.
Marinos, L., & Sfakianakis, A. (2012). ENISA Threat Landscape-Responding to the Evolving
Threat Environment. ENISA (The European Network and Information Security Agency)
(September 2012).
Mishra, S., Dhir, S., & Hooda, M. (2016). A Study on Cyber Security, Its Issues and Cyber
Crime Rates in India. In Innovations in Computer Science and Engineering (pp. 249-253).
Springer Singapore
Nagpal, N. B., & Nagpal, B. (2014). Preventive measures for securing web applications using
broken authentication and session management attacks A study. In International Conference on
Advances in Computer Engineering and Applications (ICACEA) (Vol. 2014)
REFERENCES
Bologna, S., Lazari, A., & Mele, S. (2014). Improving Critical Infrastructure Protection and
Resilience against Terrorism Cyber Threats. Comprehensive Approach as" Sine Qua Non" for
Critical Infrastructure Protection, 39, 79.
ENISA, E. T. L. (2013). Overview of current and emerging cyber-threats.European Union
Agency for network and information security.
Harrop, W., & Matteson, A. (2015). Cyber Resilience: A Review of Critical National
Infrastructure and Cyber-Security Protection Measures Applied in the UK and USA. In Current
and Emerging Trends in Cyber Operations (pp. 149-166). Palgrave Macmillan UK.
Marinos, L. (2013). ENISA Threat Landscape 2013: Overview of current and emerging cyber-
threats.
Marinos, L., & Sfakianakis, A. (2012). ENISA Threat Landscape-Responding to the Evolving
Threat Environment. ENISA (The European Network and Information Security Agency)
(September 2012).
Mishra, S., Dhir, S., & Hooda, M. (2016). A Study on Cyber Security, Its Issues and Cyber
Crime Rates in India. In Innovations in Computer Science and Engineering (pp. 249-253).
Springer Singapore
Nagpal, N. B., & Nagpal, B. (2014). Preventive measures for securing web applications using
broken authentication and session management attacks A study. In International Conference on
Advances in Computer Engineering and Applications (ICACEA) (Vol. 2014)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
Olesen, N. (2016). European Public-Private Partnerships on Cybersecurity-An Instrument to
Support the Fight Against Cybercrime and Cyberterrorism. In Combatting Cybercrime and
Cyberterrorism (pp. 259-278). Springer Internation
Olesen, N. (2016). European Public-Private Partnerships on Cybersecurity-An Instrument to
Support the Fight Against Cybercrime and Cyberterrorism. In Combatting Cybercrime and
Cyberterrorism (pp. 259-278). Springer Internation
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





