Network Security and Design: Wireless Network Implementation Report
VerifiedAdded on 2022/11/22
|17
|3129
|395
Report
AI Summary
This report focuses on the design and implementation of secure enterprise wireless networks. It begins by outlining the requirements for securing such networks, including network requirements, wireless network types, security mechanisms (WPA2 and RADIUS), and adherence to standards like IEEE 802.1x. The report then delves into the ethical implications of wireless networks, highlighting issues like data protection, privacy, and information theft. A network design diagram is presented to illustrate the architecture of a typical organization's wireless network, followed by an analysis of WPA2 and RADIUS security schemes, detailing their confidentiality, integrity, availability, authentication, and authorization aspects. The report also describes the implementation of WPA2 and RADIUS, including testing client connections to access points. The report concludes with a summary of the findings and recommendations for secure wireless network design and implementation.

Running head: NETWORK SECURITY AND DESIGN
Network Security and Design
Name of the Student
Name of the University
Author Note
Network Security and Design
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK SECURITY AND DESIGN
Summary
Secure enterprise wireless networks have gained significant grounds in connecting devices of
networks for both home and corporate uses. The report talks about the security and
authentication mechanisms for such networks. First the report summarises the requirements
for securing the typical wireless networks where it identifies the network requirements, the
kind of wireless network to be implemented, the security mechanisms to be configured on the
network, and the technologies and standards that the security systems should adhere by. The
report then discusses the ethical issues related to wireless networks and highlights how lack
of data protection, privacy, information theft and manipulation can affect users. Then the
report provides the network design diagram of organizations in general and explains the
network design and how the security mechanisms can be applied. Next the report makes a
thorough analysis of the security schemes and identifies their strength over the competition.
Then the report briefly describes how the security techniques can be applied on the network.
After that the report tests the connections of clients with the access points and ends with
conclusion notes.
NETWORK SECURITY AND DESIGN
Summary
Secure enterprise wireless networks have gained significant grounds in connecting devices of
networks for both home and corporate uses. The report talks about the security and
authentication mechanisms for such networks. First the report summarises the requirements
for securing the typical wireless networks where it identifies the network requirements, the
kind of wireless network to be implemented, the security mechanisms to be configured on the
network, and the technologies and standards that the security systems should adhere by. The
report then discusses the ethical issues related to wireless networks and highlights how lack
of data protection, privacy, information theft and manipulation can affect users. Then the
report provides the network design diagram of organizations in general and explains the
network design and how the security mechanisms can be applied. Next the report makes a
thorough analysis of the security schemes and identifies their strength over the competition.
Then the report briefly describes how the security techniques can be applied on the network.
After that the report tests the connections of clients with the access points and ends with
conclusion notes.

2
NETWORK SECURITY AND DESIGN
Table of Contents
Introduction................................................................................................................................4
Discussion..................................................................................................................................4
Requirements..........................................................................................................................4
Ethical Implications...............................................................................................................5
Network Design.....................................................................................................................7
WPA2 Analysis......................................................................................................................8
Confidentiality....................................................................................................................8
Integrity..............................................................................................................................8
Availability.........................................................................................................................8
Authentication....................................................................................................................9
Authorization......................................................................................................................9
RADIUS Analysis..................................................................................................................9
Confidentiality....................................................................................................................9
Integrity..............................................................................................................................9
Availability.........................................................................................................................9
Authentication..................................................................................................................10
Authorization....................................................................................................................10
Implementation of WPA2 and RADIUS..............................................................................10
Testing Connection of Clients..............................................................................................11
Conclusion................................................................................................................................12
Bibliography.............................................................................................................................14
NETWORK SECURITY AND DESIGN
Table of Contents
Introduction................................................................................................................................4
Discussion..................................................................................................................................4
Requirements..........................................................................................................................4
Ethical Implications...............................................................................................................5
Network Design.....................................................................................................................7
WPA2 Analysis......................................................................................................................8
Confidentiality....................................................................................................................8
Integrity..............................................................................................................................8
Availability.........................................................................................................................8
Authentication....................................................................................................................9
Authorization......................................................................................................................9
RADIUS Analysis..................................................................................................................9
Confidentiality....................................................................................................................9
Integrity..............................................................................................................................9
Availability.........................................................................................................................9
Authentication..................................................................................................................10
Authorization....................................................................................................................10
Implementation of WPA2 and RADIUS..............................................................................10
Testing Connection of Clients..............................................................................................11
Conclusion................................................................................................................................12
Bibliography.............................................................................................................................14
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORK SECURITY AND DESIGN
NETWORK SECURITY AND DESIGN
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORK SECURITY AND DESIGN
Introduction
It is found that secure enterprise wireless networks have come along way in
connecting devices of networks for both home and corporate use cases. The report therefore
talks about the securing and authenticating mechanisms for these networks. The report begins
by summarising the requirements for securing the typical wireless networks where it
identifies the network requirements, the kind of wireless network to be implemented, the
security mechanisms to be configured on the network, and the technologies and standards that
the security systems should adhere by. The report then discusses the ethical issues related to
wireless networks and highlights how lack of data protection, privacy, information theft and
manipulation can affect users. Then the report provides the network design diagram of
organizations in general and explains the network design and how the security mechanisms
can be applied. Next the report makes a thorough analysis of the security schemes and
identifies their strength over the competition. Then the report briefly describes how the
security techniques can be applied on the network. After that the report tests the connections
of clients with the access points and ends with conclusion notes.
Discussion
Requirements
The organization needs to set up a secured wireless network.
The security of the wireless network is to be ensured with WPA2 encryption and RADIUS
authentication.
The RADIUS authentication should use EAP methodology and follow the IEEE 802.1x
standard.
NETWORK SECURITY AND DESIGN
Introduction
It is found that secure enterprise wireless networks have come along way in
connecting devices of networks for both home and corporate use cases. The report therefore
talks about the securing and authenticating mechanisms for these networks. The report begins
by summarising the requirements for securing the typical wireless networks where it
identifies the network requirements, the kind of wireless network to be implemented, the
security mechanisms to be configured on the network, and the technologies and standards that
the security systems should adhere by. The report then discusses the ethical issues related to
wireless networks and highlights how lack of data protection, privacy, information theft and
manipulation can affect users. Then the report provides the network design diagram of
organizations in general and explains the network design and how the security mechanisms
can be applied. Next the report makes a thorough analysis of the security schemes and
identifies their strength over the competition. Then the report briefly describes how the
security techniques can be applied on the network. After that the report tests the connections
of clients with the access points and ends with conclusion notes.
Discussion
Requirements
The organization needs to set up a secured wireless network.
The security of the wireless network is to be ensured with WPA2 encryption and RADIUS
authentication.
The RADIUS authentication should use EAP methodology and follow the IEEE 802.1x
standard.

5
NETWORK SECURITY AND DESIGN
Ethical Implications
Problems that can arise from implementing any secure enterprise wireless network are
that several. Among them one key problem concerns with the lack of control residing on the
medium of communication. The property lines and where they are drawn are not factored by
the radio waves. Wireless networks are gaining popularity at a radical pace as it provides
businesses and consumers with mobility of usage as also fast and easy installation. However,
it must be noted that this transfer of radio waves or wireless signals enables any user in
accessing the connection through appropriate receivers. As a result, data protection becomes
a key area of concern. This is why several measures need to be applied to ensure the
protection of data. This can involve applying some of the security mechanisms of wired
connections as well as dedicated measures for wireless network. For otherwise the users can
suffer from privacy issues.
Since many public wireless networks are available in airports, restaurants, cafeterias,
hotels and several other public places of activity and interest, the privacy in these hotspots is
a major concern. When people use the network to create accounts in websites or complete a
transaction, they enter sensitive information like user id, password as well as important
transactional information like credit card and bank account details. Public hotspots generally
being unprotected can allow attackers in stealing such information and inflict serious
financial damages for the victim.
Another form of attack called eavesdropping is applied by attackers to track all the
unencrypted wireless networks through which data can easily be extracted and can be used
for dangerous activities. Attackers can also inject packets into a network and receive it
reversely to identify the kind of encryption applied in a said wireless network. This then lets
the attackers in devising ways to create crack the respective encryption method and thereby
succeed with accessing the network. As soon as they are able to access the network, they next
NETWORK SECURITY AND DESIGN
Ethical Implications
Problems that can arise from implementing any secure enterprise wireless network are
that several. Among them one key problem concerns with the lack of control residing on the
medium of communication. The property lines and where they are drawn are not factored by
the radio waves. Wireless networks are gaining popularity at a radical pace as it provides
businesses and consumers with mobility of usage as also fast and easy installation. However,
it must be noted that this transfer of radio waves or wireless signals enables any user in
accessing the connection through appropriate receivers. As a result, data protection becomes
a key area of concern. This is why several measures need to be applied to ensure the
protection of data. This can involve applying some of the security mechanisms of wired
connections as well as dedicated measures for wireless network. For otherwise the users can
suffer from privacy issues.
Since many public wireless networks are available in airports, restaurants, cafeterias,
hotels and several other public places of activity and interest, the privacy in these hotspots is
a major concern. When people use the network to create accounts in websites or complete a
transaction, they enter sensitive information like user id, password as well as important
transactional information like credit card and bank account details. Public hotspots generally
being unprotected can allow attackers in stealing such information and inflict serious
financial damages for the victim.
Another form of attack called eavesdropping is applied by attackers to track all the
unencrypted wireless networks through which data can easily be extracted and can be used
for dangerous activities. Attackers can also inject packets into a network and receive it
reversely to identify the kind of encryption applied in a said wireless network. This then lets
the attackers in devising ways to create crack the respective encryption method and thereby
succeed with accessing the network. As soon as they are able to access the network, they next
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORK SECURITY AND DESIGN
target the routers and access points. Although if privileges for accessing these equipment are
in place the attackers may find it difficult. Other attacks the attackers can resort to is by
interfering in wireless sessions and then disabling network communication between the
wireless access point (AP) and the network station. After this the attacker controls the
network of the users connected to the AP.
The ethical issues pertaining to wireless networks are not limited to to privacy and
hacking only. Attackers can control what content is shown when the user is browsing or
downloading files from the network. This way the attackers can create social engineering
attacks. The attackers can also make adult content pop up on any page the user chooses to
browse. Through these attempts the attackers also gain in experience and become able to
execute bigger heists in networks of organizations and can end up causing multiple
magnitudes of damages that they could on public hotspots.
NETWORK SECURITY AND DESIGN
target the routers and access points. Although if privileges for accessing these equipment are
in place the attackers may find it difficult. Other attacks the attackers can resort to is by
interfering in wireless sessions and then disabling network communication between the
wireless access point (AP) and the network station. After this the attacker controls the
network of the users connected to the AP.
The ethical issues pertaining to wireless networks are not limited to to privacy and
hacking only. Attackers can control what content is shown when the user is browsing or
downloading files from the network. This way the attackers can create social engineering
attacks. The attackers can also make adult content pop up on any page the user chooses to
browse. Through these attempts the attackers also gain in experience and become able to
execute bigger heists in networks of organizations and can end up causing multiple
magnitudes of damages that they could on public hotspots.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
NETWORK SECURITY AND DESIGN
Network Design
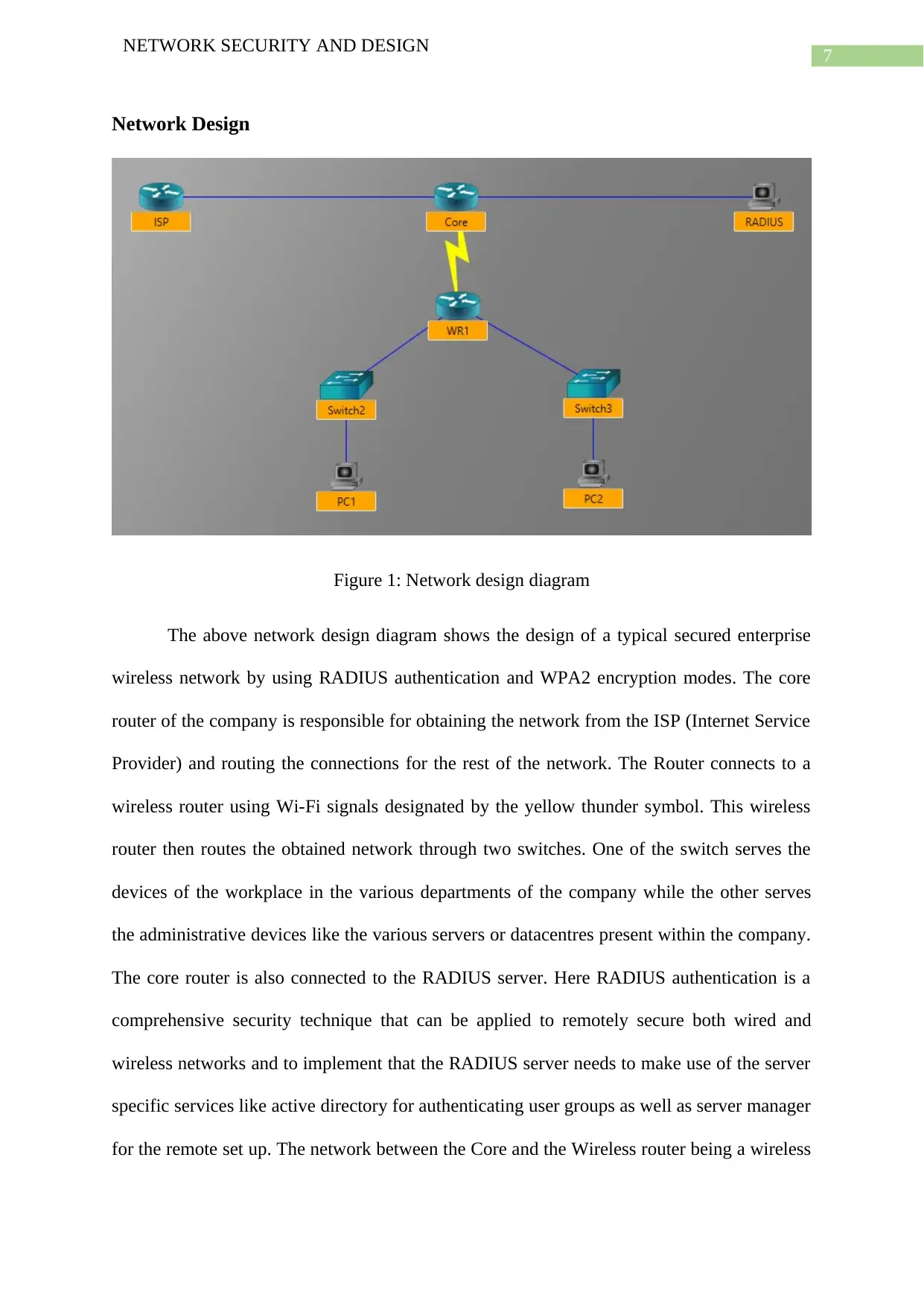
Figure 1: Network design diagram
The above network design diagram shows the design of a typical secured enterprise
wireless network by using RADIUS authentication and WPA2 encryption modes. The core
router of the company is responsible for obtaining the network from the ISP (Internet Service
Provider) and routing the connections for the rest of the network. The Router connects to a
wireless router using Wi-Fi signals designated by the yellow thunder symbol. This wireless
router then routes the obtained network through two switches. One of the switch serves the
devices of the workplace in the various departments of the company while the other serves
the administrative devices like the various servers or datacentres present within the company.
The core router is also connected to the RADIUS server. Here RADIUS authentication is a
comprehensive security technique that can be applied to remotely secure both wired and
wireless networks and to implement that the RADIUS server needs to make use of the server
specific services like active directory for authenticating user groups as well as server manager
for the remote set up. The network between the Core and the Wireless router being a wireless
NETWORK SECURITY AND DESIGN
Network Design
Figure 1: Network design diagram
The above network design diagram shows the design of a typical secured enterprise
wireless network by using RADIUS authentication and WPA2 encryption modes. The core
router of the company is responsible for obtaining the network from the ISP (Internet Service
Provider) and routing the connections for the rest of the network. The Router connects to a
wireless router using Wi-Fi signals designated by the yellow thunder symbol. This wireless
router then routes the obtained network through two switches. One of the switch serves the
devices of the workplace in the various departments of the company while the other serves
the administrative devices like the various servers or datacentres present within the company.
The core router is also connected to the RADIUS server. Here RADIUS authentication is a
comprehensive security technique that can be applied to remotely secure both wired and
wireless networks and to implement that the RADIUS server needs to make use of the server
specific services like active directory for authenticating user groups as well as server manager
for the remote set up. The network between the Core and the Wireless router being a wireless

8
NETWORK SECURITY AND DESIGN
connection can be secured by a security techniques used specifically for securing wireless
networks like WPA2 or Wi-Fi Protected Access version 2.
WPA2 Analysis
WPA2 is one of the network security techniques that are commonly being used to
ensure security wireless networks like Wi-Fi connections. It is the upgraded version of the
original Wireless Protected Access. Recently a further upgrade has been accomplished to
create the WPA3. All these three protocols and security certifications have been developed by
the Wi-Fi Alliance with the aim of securing wireless computer networks. These security
programs were introduced by Wi-Fi Alliance as responses to the alarming range of
weaknesses that were present in the previous authentication system which was known as
Wired Equivalent Privacy or WEP.
Confidentiality
The WPA2 encryption is natively supported by the routers and access points. This
makes it difficult for attackers to tap into the information being exchanged within the wireless
network.
Integrity
The WPA2 ensures that the security measures prescribed by the IEEE 802.11i
standard are met. WPA improves security provided by WEP by the means of TKIP
encryption method for applying encryption keys and verifying that it does not get altered by
the data transfer.
Availability
These are popularly used in home networks alongside the businesses and
organizations in the corporate word. Home users have been able implement these protocols as
the supported routers are relatively cheaper than other forms of encryption.
NETWORK SECURITY AND DESIGN
connection can be secured by a security techniques used specifically for securing wireless
networks like WPA2 or Wi-Fi Protected Access version 2.
WPA2 Analysis
WPA2 is one of the network security techniques that are commonly being used to
ensure security wireless networks like Wi-Fi connections. It is the upgraded version of the
original Wireless Protected Access. Recently a further upgrade has been accomplished to
create the WPA3. All these three protocols and security certifications have been developed by
the Wi-Fi Alliance with the aim of securing wireless computer networks. These security
programs were introduced by Wi-Fi Alliance as responses to the alarming range of
weaknesses that were present in the previous authentication system which was known as
Wired Equivalent Privacy or WEP.
Confidentiality
The WPA2 encryption is natively supported by the routers and access points. This
makes it difficult for attackers to tap into the information being exchanged within the wireless
network.
Integrity
The WPA2 ensures that the security measures prescribed by the IEEE 802.11i
standard are met. WPA improves security provided by WEP by the means of TKIP
encryption method for applying encryption keys and verifying that it does not get altered by
the data transfer.
Availability
These are popularly used in home networks alongside the businesses and
organizations in the corporate word. Home users have been able implement these protocols as
the supported routers are relatively cheaper than other forms of encryption.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
NETWORK SECURITY AND DESIGN
Authentication
The encryption mechanism of WPA2 is similar with the major difference being that
WPA2 uses a stronger AES encryption. WPA2 security keys can vary as in WPA2 Pre-shared
keys which are 64 hexadecimal digits in size. Sometimes home networks interchange WPA2
PSK and WPA2 personal modes but ultimately they are utilizing the same security
framework.
Authorization
The wireless network can be available for the devices to connect to, however without
input of the Pre-shared key the devices are not allowed to access the network. This kind of
authorization secures the network from devices of attackers.
RADIUS Analysis
Confidentiality
By remotely securing the network RADIUS servers make it difficult for attackers to
determine the authentication and crack it. This keeps sensitive information within the
network secure.
Integrity
These can be – the embedded systems are in general not able to handle large amounts of user
accesses and the corresponding authentication data. This require excess storage facilities that
are only available in servers. RADIUS also helps facilitate centralized administration of users
which is crucial for these security applications. Organizations can have tens of thousands of
consumers and a range of whom are periodically removed or replaced from the network and
hence centralized administration becomes an operational requirement.
NETWORK SECURITY AND DESIGN
Authentication
The encryption mechanism of WPA2 is similar with the major difference being that
WPA2 uses a stronger AES encryption. WPA2 security keys can vary as in WPA2 Pre-shared
keys which are 64 hexadecimal digits in size. Sometimes home networks interchange WPA2
PSK and WPA2 personal modes but ultimately they are utilizing the same security
framework.
Authorization
The wireless network can be available for the devices to connect to, however without
input of the Pre-shared key the devices are not allowed to access the network. This kind of
authorization secures the network from devices of attackers.
RADIUS Analysis
Confidentiality
By remotely securing the network RADIUS servers make it difficult for attackers to
determine the authentication and crack it. This keeps sensitive information within the
network secure.
Integrity
These can be – the embedded systems are in general not able to handle large amounts of user
accesses and the corresponding authentication data. This require excess storage facilities that
are only available in servers. RADIUS also helps facilitate centralized administration of users
which is crucial for these security applications. Organizations can have tens of thousands of
consumers and a range of whom are periodically removed or replaced from the network and
hence centralized administration becomes an operational requirement.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
NETWORK SECURITY AND DESIGN
Availability
Support of RADIUS authentication is very broad and is uniform across various types of
network implementations and networking equipment unlike the completion which does
always have support from all hardware vendors. This is how the RADIUS authentication has
become a standard for remote authentication and can be applied in both old and new systems.
Authentication
RADIUS authentication protocol is widely used by networks today. More specifically it is the
embedded network equipment like the routers, switches, modems and servers that use this
security technique. The RADIUS authentication technique is gaining prominence for several
reasons.
Authorization
RADIUS consistently provides various levels of protections against cyber attackers. The
RADIUS server sets up user groups in the Active Directory and configures the rules and
privileges. This is how it ensures authorization of the devices of the network.
Implementation of WPA2 and RADIUS
WPA2 can be implemented by configuring the wireless access points. In this network,
both the Core and Wireless routers are capable of supporting wireless connections. The
wireless router however come equipped with the extra advantage of providing wider
transmission of wireless signals and dedicated security features for securing wireless
networks. It is in this wireless router that the WPA2 encryption scheme is configured. The
configuration generates the Pre-shared key which is to be used by the devices the router
serves whenever they attempt to connect the network.
The RADIUS server obtains and stores the authentication information from the
network in bulk and executes the authentication tasks in batches. The authentication
NETWORK SECURITY AND DESIGN
Availability
Support of RADIUS authentication is very broad and is uniform across various types of
network implementations and networking equipment unlike the completion which does
always have support from all hardware vendors. This is how the RADIUS authentication has
become a standard for remote authentication and can be applied in both old and new systems.
Authentication
RADIUS authentication protocol is widely used by networks today. More specifically it is the
embedded network equipment like the routers, switches, modems and servers that use this
security technique. The RADIUS authentication technique is gaining prominence for several
reasons.
Authorization
RADIUS consistently provides various levels of protections against cyber attackers. The
RADIUS server sets up user groups in the Active Directory and configures the rules and
privileges. This is how it ensures authorization of the devices of the network.
Implementation of WPA2 and RADIUS
WPA2 can be implemented by configuring the wireless access points. In this network,
both the Core and Wireless routers are capable of supporting wireless connections. The
wireless router however come equipped with the extra advantage of providing wider
transmission of wireless signals and dedicated security features for securing wireless
networks. It is in this wireless router that the WPA2 encryption scheme is configured. The
configuration generates the Pre-shared key which is to be used by the devices the router
serves whenever they attempt to connect the network.
The RADIUS server obtains and stores the authentication information from the
network in bulk and executes the authentication tasks in batches. The authentication
11
NETWORK SECURITY AND DESIGN
information is generated when the users of the company network attempts to log into the
captive portal. This batch processing requires substantial processing power and storage
facilities that are only present in servers. Since the RADIUS authentication concerns
remotely securing the network. The server manager is used to remotely access the network
respective equipment. The network of the organization can server several types of users. This
is why the user groups are set up in the active directory where the rules for each group is
specified.
Testing Connection of Clients
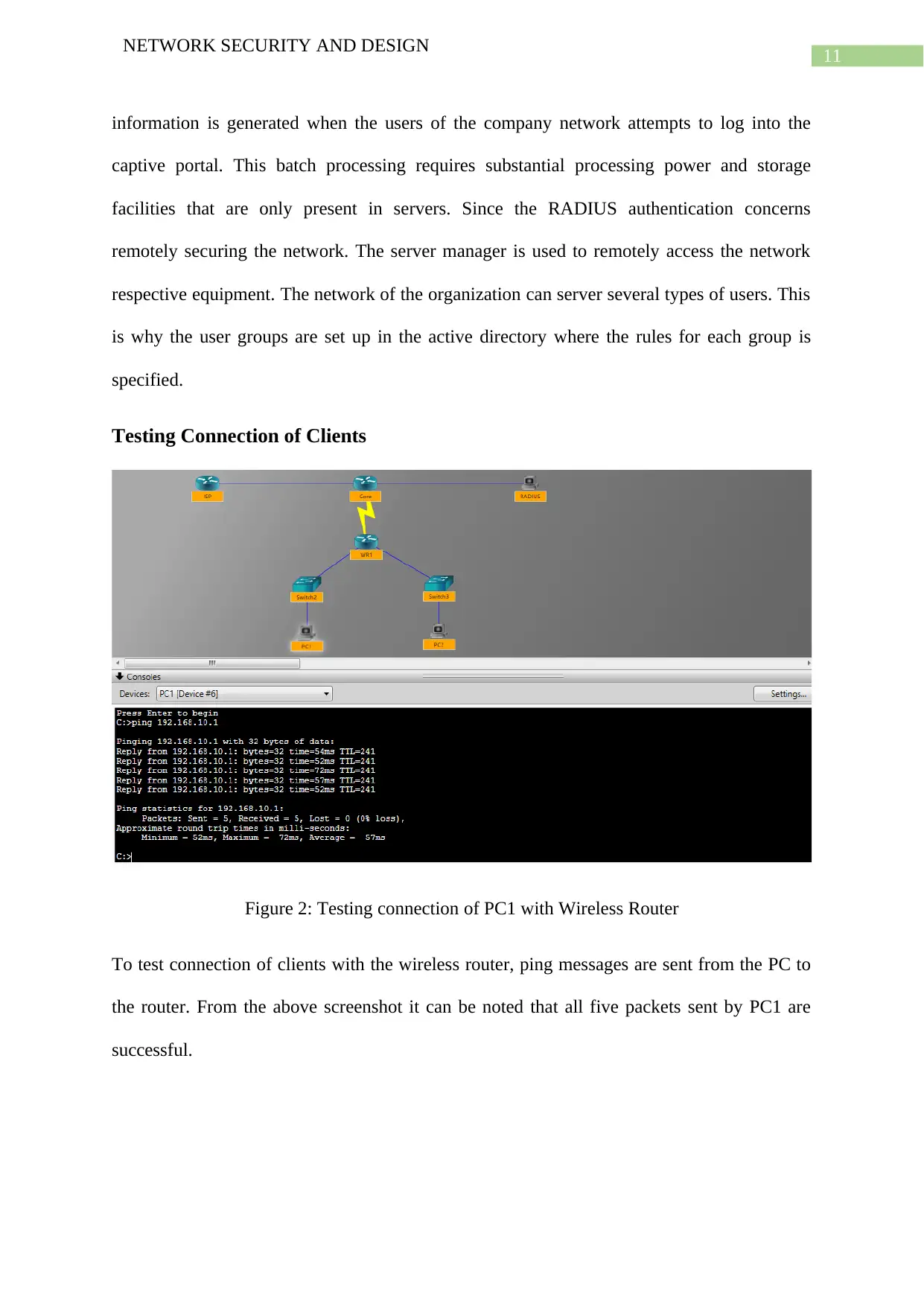
Figure 2: Testing connection of PC1 with Wireless Router
To test connection of clients with the wireless router, ping messages are sent from the PC to
the router. From the above screenshot it can be noted that all five packets sent by PC1 are
successful.
NETWORK SECURITY AND DESIGN
information is generated when the users of the company network attempts to log into the
captive portal. This batch processing requires substantial processing power and storage
facilities that are only present in servers. Since the RADIUS authentication concerns
remotely securing the network. The server manager is used to remotely access the network
respective equipment. The network of the organization can server several types of users. This
is why the user groups are set up in the active directory where the rules for each group is
specified.
Testing Connection of Clients
Figure 2: Testing connection of PC1 with Wireless Router
To test connection of clients with the wireless router, ping messages are sent from the PC to
the router. From the above screenshot it can be noted that all five packets sent by PC1 are
successful.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




