System Analysis and Design: Developing Epping Medical Centre System
VerifiedAdded on 2023/06/09
|17
|3350
|390
Report
AI Summary
This document presents a system analysis and design report for the Epping Medical Centre, detailing the system's functional and non-functional requirements, fact-finding methods employed (interview, questionnaire, observation), system development tools and methods (modeling, prototyping, structured analysis), and visual representations such as use case, context, and DFD diagrams, along with an initial ERD. The report emphasizes authentication, authorization, data storage, reporting, and communication as key functional requirements. Security, usability, and availability are highlighted as critical non-functional requirements. The analysis uses various methods to gather data, including interviews, questionnaires, and direct observation to understand the current system and inform the design of a new, automated system. The document also outlines the system development tools and methods used, including modeling and prototyping, with a focus on structured analysis. This report provides a comprehensive overview of the proposed system for the Epping Medical Centre.

Running head: SYSTEM ANALYSIS AND DESIGN
System Analysis and Design
Name of the Student
Name of the University
Author’s note
System Analysis and Design
Name of the Student
Name of the University
Author’s note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SYSTEM ANALYSIS AND DESIGN
Table of Contents
1. System Requirements:.................................................................................................................2
1.1 Functional Requirements:......................................................................................................2
1.2 Non-Functional Requirement:...............................................................................................3
2. Fact Finding Method:..................................................................................................................4
2.1 Interview:...............................................................................................................................4
2.2 Questionnaire:............................................................................................................................5
2.3 Observation:...............................................................................................................................6
3. System Development Tools and Methods:..................................................................................7
3.1 Development Tools:...............................................................................................................7
3.2 Systems Development Methods:...............................................................................................8
4. Use Case Diagram:....................................................................................................................10
5. Context Diagram:.......................................................................................................................11
6. DFD Diagram:...........................................................................................................................12
7. Initial ERD:................................................................................................................................13
Bibliography:.................................................................................................................................14
Table of Contents
1. System Requirements:.................................................................................................................2
1.1 Functional Requirements:......................................................................................................2
1.2 Non-Functional Requirement:...............................................................................................3
2. Fact Finding Method:..................................................................................................................4
2.1 Interview:...............................................................................................................................4
2.2 Questionnaire:............................................................................................................................5
2.3 Observation:...............................................................................................................................6
3. System Development Tools and Methods:..................................................................................7
3.1 Development Tools:...............................................................................................................7
3.2 Systems Development Methods:...............................................................................................8
4. Use Case Diagram:....................................................................................................................10
5. Context Diagram:.......................................................................................................................11
6. DFD Diagram:...........................................................................................................................12
7. Initial ERD:................................................................................................................................13
Bibliography:.................................................................................................................................14

2SYSTEM ANALYSIS AND DESIGN
1. System Requirements:
1.1 Functional Requirements:
Authentication: Authentication is a very factor for any information system’s security
implementation. Authentication is defined as the protocol for verifying user access to the system.
The authentication is generally implemented based on the idea of checking user id and password.
Taken as an example, if the user wants to login to the system then correct user id and password
needs to be inputted (Dabbagh and Lee 2014). In some cases, where security is high, the user
device is also checked. Taken as an example, the google sends a notification to the user if a new
device is used for log into the Gmail. The Epping Medical Centre system will provide user id and
password to the patient which can be used for getting authentication to access the system.
Authorization: Authorization is similar to authentication in basic level but has huge
difference in terms of application. Once, the user gets authenticated, the system checks which
services is accessible by the user. As an instance, the patient cannot see the medical records or
appointment list of all the other patients. Authorization is used for checking the user access to
specific services and information. Authorization is categorized into different levels. In highest
level, most of the services and information is accessible by the user such as management can
access any patient’s medical report, statement report, delete or add patient and many more.
Data Storage: Information is the most significant part of any information system. The
Epping Medical Centre system will collect data from various sources. The system will be
installed with a distributed centralized database in the core (Rahman and Ripon 2014). For
security reasons, the system cannot store any data into the database, all the data must be verified
1. System Requirements:
1.1 Functional Requirements:
Authentication: Authentication is a very factor for any information system’s security
implementation. Authentication is defined as the protocol for verifying user access to the system.
The authentication is generally implemented based on the idea of checking user id and password.
Taken as an example, if the user wants to login to the system then correct user id and password
needs to be inputted (Dabbagh and Lee 2014). In some cases, where security is high, the user
device is also checked. Taken as an example, the google sends a notification to the user if a new
device is used for log into the Gmail. The Epping Medical Centre system will provide user id and
password to the patient which can be used for getting authentication to access the system.
Authorization: Authorization is similar to authentication in basic level but has huge
difference in terms of application. Once, the user gets authenticated, the system checks which
services is accessible by the user. As an instance, the patient cannot see the medical records or
appointment list of all the other patients. Authorization is used for checking the user access to
specific services and information. Authorization is categorized into different levels. In highest
level, most of the services and information is accessible by the user such as management can
access any patient’s medical report, statement report, delete or add patient and many more.
Data Storage: Information is the most significant part of any information system. The
Epping Medical Centre system will collect data from various sources. The system will be
installed with a distributed centralized database in the core (Rahman and Ripon 2014). For
security reasons, the system cannot store any data into the database, all the data must be verified
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3SYSTEM ANALYSIS AND DESIGN
using various protocols and checks. After verifying the data, the system records those data into
desired tables. The system can retrieve data from the database after a long time.
Reporting: Reporting is an essential functional requirement of Epping Medical Centre
System. From hourly appointment report to weekly medical report, all these reports will be
accessed by the management and receptionists. The medical staff will upload the medical reports
of individual patients (Khan et al. 2016). The patient can access their medical report using the
system. The system will store the issues, a user will report, so that reports can be modified.
Communication: The patient will provide the email id and contact number during the
registration. The system will be configured in such way that it can send mail or SMS to contact
number and email respectively. This functional requirement is important for establishing
effective and efficient communication between Epping Medical Centre and patients.
1.2 Non-Functional Requirement:
Security: Securing the system is the most vital non-functional requirement. The system
will record the patient personal and bank account details along with their medical reports.
Securing this information from external entities must be followed as per the legislations implied
by state and national government (Eckhardt, Vogelsang and Fernandez 2016). The system
database and core units will be deployed in different server. The system will implement
authentication and authorization in different levels as mentioned above. In order to transmit data
from one device to another, the system will use the RSA encryption mechanism.
Usability: The business process and working procedure of the Epping Medical Centre is
based on fast response to issues. The organization cannot afford any delay in the work due to
inability of a staff understanding the system. The System UX and UI will go through several
using various protocols and checks. After verifying the data, the system records those data into
desired tables. The system can retrieve data from the database after a long time.
Reporting: Reporting is an essential functional requirement of Epping Medical Centre
System. From hourly appointment report to weekly medical report, all these reports will be
accessed by the management and receptionists. The medical staff will upload the medical reports
of individual patients (Khan et al. 2016). The patient can access their medical report using the
system. The system will store the issues, a user will report, so that reports can be modified.
Communication: The patient will provide the email id and contact number during the
registration. The system will be configured in such way that it can send mail or SMS to contact
number and email respectively. This functional requirement is important for establishing
effective and efficient communication between Epping Medical Centre and patients.
1.2 Non-Functional Requirement:
Security: Securing the system is the most vital non-functional requirement. The system
will record the patient personal and bank account details along with their medical reports.
Securing this information from external entities must be followed as per the legislations implied
by state and national government (Eckhardt, Vogelsang and Fernandez 2016). The system
database and core units will be deployed in different server. The system will implement
authentication and authorization in different levels as mentioned above. In order to transmit data
from one device to another, the system will use the RSA encryption mechanism.
Usability: The business process and working procedure of the Epping Medical Centre is
based on fast response to issues. The organization cannot afford any delay in the work due to
inability of a staff understanding the system. The System UX and UI will go through several
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SYSTEM ANALYSIS AND DESIGN
evaluation processes (Rahman and Ripon 2014). The system interface will be very user friendly
and exact. The patients will get all the required data and services in different pages so that they
can easily navigate through the system. Only interface of the unit, accessed by the management
will be complex and full of different services. That is why the management will be trained
properly before system deployment.
Availability: In healthcare industry, emergency situation can occur any time. The system
should be on and running 24*7. The patients can access the system to download medical reports
and request for appointment. The system will contain all the contact information so that patients
can directly contact them in the time of emergency.
2. Fact Finding Method:
2.1 Interview:
The interview method is utilized by the system and business analysts for collecting data
from individual or groups. The responsibility of selecting the participants of the interview lies
upon the shoulders of analysts (Bryman and Bell 2015). As per the definition of the method, the
analyst will conduct the interview face-to-face with the interviewee. The interviewer is assigned
the task of recording the responses of the interviewee for each question. The interviewer creates
the questions that he/she is going to ask in the interview and practice all the answers that they
might provide to the participants. Each interview is done at a suitable place in a specific day.
Advantages:
i. The biggest benefit of interview is that mistakes and misunderstandings can be
corrected easily. It is possible because both the interviewer and interviewee is
physically present at the location.
evaluation processes (Rahman and Ripon 2014). The system interface will be very user friendly
and exact. The patients will get all the required data and services in different pages so that they
can easily navigate through the system. Only interface of the unit, accessed by the management
will be complex and full of different services. That is why the management will be trained
properly before system deployment.
Availability: In healthcare industry, emergency situation can occur any time. The system
should be on and running 24*7. The patients can access the system to download medical reports
and request for appointment. The system will contain all the contact information so that patients
can directly contact them in the time of emergency.
2. Fact Finding Method:
2.1 Interview:
The interview method is utilized by the system and business analysts for collecting data
from individual or groups. The responsibility of selecting the participants of the interview lies
upon the shoulders of analysts (Bryman and Bell 2015). As per the definition of the method, the
analyst will conduct the interview face-to-face with the interviewee. The interviewer is assigned
the task of recording the responses of the interviewee for each question. The interviewer creates
the questions that he/she is going to ask in the interview and practice all the answers that they
might provide to the participants. Each interview is done at a suitable place in a specific day.
Advantages:
i. The biggest benefit of interview is that mistakes and misunderstandings can be
corrected easily. It is possible because both the interviewer and interviewee is
physically present at the location.

5SYSTEM ANALYSIS AND DESIGN
ii. Better relationships lead to better information finding. The increase in
understanding the mindset of the interviewee allows the analyst to determine the
real meaning of the conversation (Lazar, Feng and Hochheiser 2017). Thus, data
collection process quality is improved.
iii. The selection of suitable participants allows the analyst to collect the appropriate
data. The interviewer always remains positive about receiving authentic and
accurate data.
Disadvantages:
i. A good interview requires constant focus. If any of the participants,
interviewer or interviewee, fails to focus on the process, the data collection
process will be filled with irrelevant data.
ii. The interview process is very time consuming and often needs to be planned
way ahead of the scheduled time (Bryman and Bell 2015). So much
concentration on a single process can be inadequate for small projects.
2.2 Questionnaire:
The questionnaire is based on the idea of extracting information from a huge quantity of
people simultaneously. In contrast to the interview process, in questionnaire there is no concept
of interviewer or interviewee. The analysts create a set of questions for different people in
different position of the organization (Clark et al. 2016). The participants provide their answers
to the questions within specific deadline. Each of the questions are related to different aspects of
the system. The participants are generally the users of the system. However, in special cases, the
ii. Better relationships lead to better information finding. The increase in
understanding the mindset of the interviewee allows the analyst to determine the
real meaning of the conversation (Lazar, Feng and Hochheiser 2017). Thus, data
collection process quality is improved.
iii. The selection of suitable participants allows the analyst to collect the appropriate
data. The interviewer always remains positive about receiving authentic and
accurate data.
Disadvantages:
i. A good interview requires constant focus. If any of the participants,
interviewer or interviewee, fails to focus on the process, the data collection
process will be filled with irrelevant data.
ii. The interview process is very time consuming and often needs to be planned
way ahead of the scheduled time (Bryman and Bell 2015). So much
concentration on a single process can be inadequate for small projects.
2.2 Questionnaire:
The questionnaire is based on the idea of extracting information from a huge quantity of
people simultaneously. In contrast to the interview process, in questionnaire there is no concept
of interviewer or interviewee. The analysts create a set of questions for different people in
different position of the organization (Clark et al. 2016). The participants provide their answers
to the questions within specific deadline. Each of the questions are related to different aspects of
the system. The participants are generally the users of the system. However, in special cases, the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SYSTEM ANALYSIS AND DESIGN
analysts can consider few stakeholders as participants. Questionnaire is very cheap and quickest
process among all the fact-finding processes.
Advantages:
i. This process is highly cost efficient for collecting quantitative data from the
participants. Outsourcing market research organization would cost higher than
most of the fact-finding methods.
ii. The process is flexible along with being cheap. This process of collecting data is
also practical (Stanton et al. 2017). Each set of questions can be created a group
thus improving the quality of the questionnaire management.
iii. The outcomes can be gathered very quickly using online and mobile tools. The
results can be obtained at any time of the day.
iv. The questionnaire is very popular for being able to access information from
various sources.
Disadvantages:
i. If the participants are not honest, the findings from the questionnaire will surely
full of errors (Clark et al. 2016).
ii. There is no way to be sure that the participant has understood the question and
provided an authentic answer. The participant may provide biased answer.
2.3 Observation:
Observation is quite different from other fact-finding methods. To conduct this method,
the analysts have to visit Epping Medical Centre and understand the information flow. They have
to unwrap the underlying methods behind the existing system in Epping Medical Centre. They
analysts can consider few stakeholders as participants. Questionnaire is very cheap and quickest
process among all the fact-finding processes.
Advantages:
i. This process is highly cost efficient for collecting quantitative data from the
participants. Outsourcing market research organization would cost higher than
most of the fact-finding methods.
ii. The process is flexible along with being cheap. This process of collecting data is
also practical (Stanton et al. 2017). Each set of questions can be created a group
thus improving the quality of the questionnaire management.
iii. The outcomes can be gathered very quickly using online and mobile tools. The
results can be obtained at any time of the day.
iv. The questionnaire is very popular for being able to access information from
various sources.
Disadvantages:
i. If the participants are not honest, the findings from the questionnaire will surely
full of errors (Clark et al. 2016).
ii. There is no way to be sure that the participant has understood the question and
provided an authentic answer. The participant may provide biased answer.
2.3 Observation:
Observation is quite different from other fact-finding methods. To conduct this method,
the analysts have to visit Epping Medical Centre and understand the information flow. They have
to unwrap the underlying methods behind the existing system in Epping Medical Centre. They
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SYSTEM ANALYSIS AND DESIGN
will analyze the working procedures of the staff and identify their requirements. Observation has
huge impact of planning the system automation (Dumais et al. 2016). Through observation, the
analysts can recognize which processes are needed to be processed automatically and which not.
The observation process needs an experienced analyst who has some knowledge about that
industry. They must know which fact to be highlighted.
Advantages:
i. The observation allows the analyst to access to that data/information which are
not possible to collect through questionnaire or interview.
ii. The analyst can get to know how the staff work in real life situation (Ricci,
Rokach and Shapira 2015)
iii. The system analyst can have in-depth understanding of processes followed in the
organization
Disadvantages:
i. The finding of the observation method can be subjective and can be strenuous for
other project team members to understand (Dumais et al. 2016)
ii. The findings are hugely depended on the experience and quality of the analyst
3. System Development Tools and Methods:
3.1 Development Tools:
Modeling: Graphical representation of the system concept or processes are called models.
Modelling is the process of creating the models of a system. These models are created for
evaluating, testing and modifying. It is easier to describe a system by creating the business, data,
UML, network, UX and UI models rather than creating the real system. This way the project
will analyze the working procedures of the staff and identify their requirements. Observation has
huge impact of planning the system automation (Dumais et al. 2016). Through observation, the
analysts can recognize which processes are needed to be processed automatically and which not.
The observation process needs an experienced analyst who has some knowledge about that
industry. They must know which fact to be highlighted.
Advantages:
i. The observation allows the analyst to access to that data/information which are
not possible to collect through questionnaire or interview.
ii. The analyst can get to know how the staff work in real life situation (Ricci,
Rokach and Shapira 2015)
iii. The system analyst can have in-depth understanding of processes followed in the
organization
Disadvantages:
i. The finding of the observation method can be subjective and can be strenuous for
other project team members to understand (Dumais et al. 2016)
ii. The findings are hugely depended on the experience and quality of the analyst
3. System Development Tools and Methods:
3.1 Development Tools:
Modeling: Graphical representation of the system concept or processes are called models.
Modelling is the process of creating the models of a system. These models are created for
evaluating, testing and modifying. It is easier to describe a system by creating the business, data,
UML, network, UX and UI models rather than creating the real system. This way the project

8SYSTEM ANALYSIS AND DESIGN
manager can save a lot of time by just verifying the models as creating and modifying the models
are much easier and these provide an exact idea of the proposed system (Baumann, Hahn and
Hubbuch 2015). The business models are used for collecting and verifying the business-related
needs and constraints. After critical analysis of the business model, the requirement models are
created. The data model is used for showing the flow of data, data structure and design of the
data storage system. The object model illustrates the objects that are combination of procedures
and data.
Prototyping: The prototyping is used for evaluating the concepts of the system to offer
the opportunity for examining the input, user interface and output of the proposed system. Based
on the analysis and findings on the prototypes, the final decisions regarding the system are made.
The prototype is an early functioning version of the system. The prototypes are done using the
current requirements found in the analysis phase. These prototypes are used as benchmark for
analyzing the final product of a system development project (Thum et al. 2014). If the
requirement finding procedure accurate then the prototype can be developed as the final product.
There is a disadvantage with the prototyping that project manager or system analyst may take an
important decision at early stage without having proper information. The prototypes are used
when client organization needs a functioning system that can handle some of the business
operations.
3.2 Systems Development Methods:
Structured Analysis: This is a conventional information system implementation
procedure. This system development method is easily understandable and time-tested. The
structured analysis utilizes a sequence of stages, called system development life cycle, for
analysing the requirements, creating design, implement and deploy the system (Da Silva 2015).
manager can save a lot of time by just verifying the models as creating and modifying the models
are much easier and these provide an exact idea of the proposed system (Baumann, Hahn and
Hubbuch 2015). The business models are used for collecting and verifying the business-related
needs and constraints. After critical analysis of the business model, the requirement models are
created. The data model is used for showing the flow of data, data structure and design of the
data storage system. The object model illustrates the objects that are combination of procedures
and data.
Prototyping: The prototyping is used for evaluating the concepts of the system to offer
the opportunity for examining the input, user interface and output of the proposed system. Based
on the analysis and findings on the prototypes, the final decisions regarding the system are made.
The prototype is an early functioning version of the system. The prototypes are done using the
current requirements found in the analysis phase. These prototypes are used as benchmark for
analyzing the final product of a system development project (Thum et al. 2014). If the
requirement finding procedure accurate then the prototype can be developed as the final product.
There is a disadvantage with the prototyping that project manager or system analyst may take an
important decision at early stage without having proper information. The prototypes are used
when client organization needs a functioning system that can handle some of the business
operations.
3.2 Systems Development Methods:
Structured Analysis: This is a conventional information system implementation
procedure. This system development method is easily understandable and time-tested. The
structured analysis utilizes a sequence of stages, called system development life cycle, for
analysing the requirements, creating design, implement and deploy the system (Da Silva 2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SYSTEM ANALYSIS AND DESIGN
The structured system development method has evolved tremendously based on the requirement
of the business and complexity of the market. However, this system development method has
been a dominant technique in the ICT industry. The structure method uses the modelling process
of graphically represent the proposed system’s different elements. The structured method is
consisted of several processes that are useful in terms of converting the gathered raw data into
useful information. For this reason, this method is also called as the process-centred technique.
Object Oriented Analysis: in contrast to the structured system development method, the
object oriented or O-O method do not consider the processes and data as different components of
the system. The objects are considered as the core component of the system. This method is used
by the project managers to model the real-world business operations and procedures. The
outcome of the object-oriented method is the representation of real world elements, people,
events and transactions (Koller et al. 2017). The O-O programs are coded with the idea of
creating object for every element in the system. These objects are the members of a definite
class, defined in the system. A class can have different objects, but a object can be created based
on one class. The objects have various properties, called characteristics of the object. These
properties are defined within the class and at the time of object creation these properties are
assigned.
The structured system development method has evolved tremendously based on the requirement
of the business and complexity of the market. However, this system development method has
been a dominant technique in the ICT industry. The structure method uses the modelling process
of graphically represent the proposed system’s different elements. The structured method is
consisted of several processes that are useful in terms of converting the gathered raw data into
useful information. For this reason, this method is also called as the process-centred technique.
Object Oriented Analysis: in contrast to the structured system development method, the
object oriented or O-O method do not consider the processes and data as different components of
the system. The objects are considered as the core component of the system. This method is used
by the project managers to model the real-world business operations and procedures. The
outcome of the object-oriented method is the representation of real world elements, people,
events and transactions (Koller et al. 2017). The O-O programs are coded with the idea of
creating object for every element in the system. These objects are the members of a definite
class, defined in the system. A class can have different objects, but a object can be created based
on one class. The objects have various properties, called characteristics of the object. These
properties are defined within the class and at the time of object creation these properties are
assigned.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10SYSTEM ANALYSIS AND DESIGN
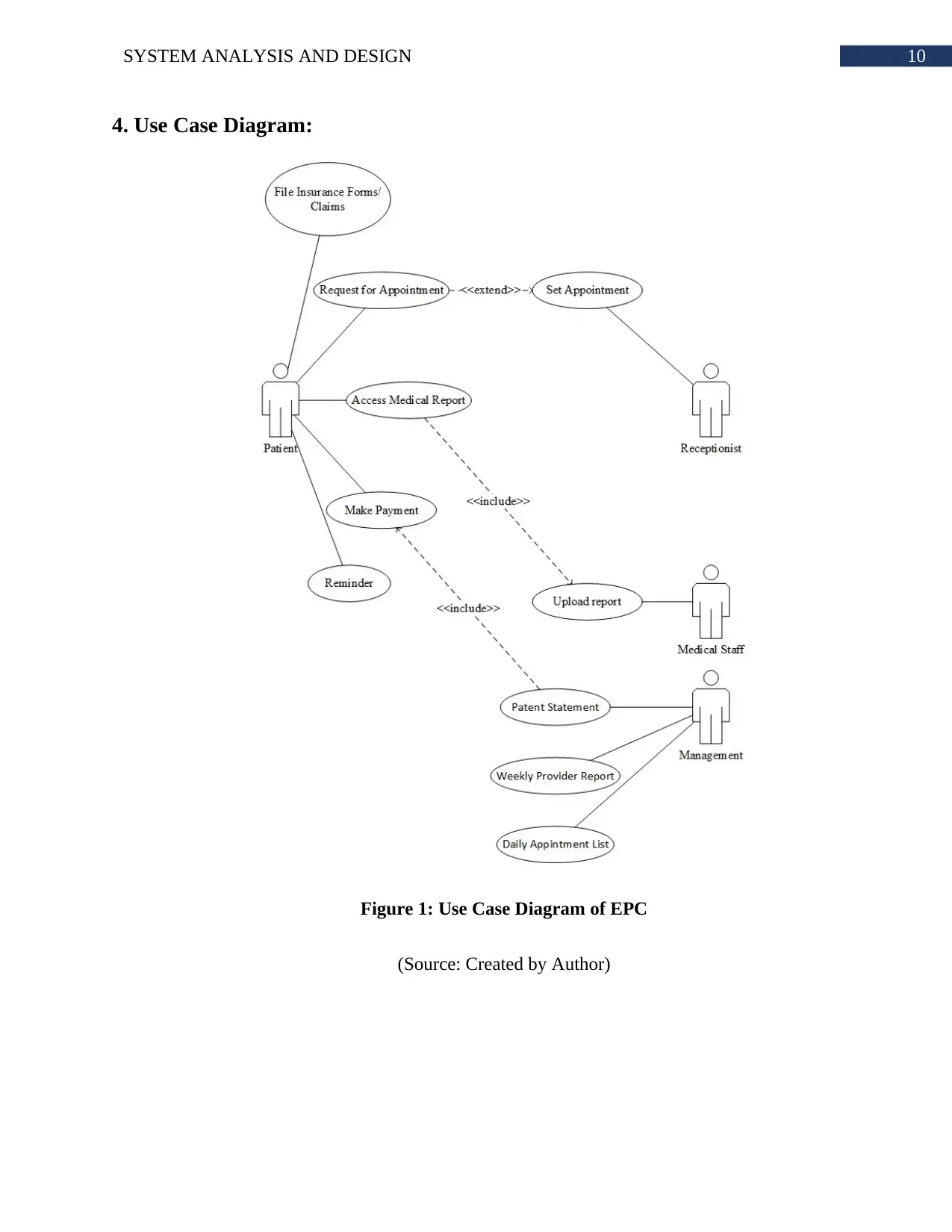
4. Use Case Diagram:
Figure 1: Use Case Diagram of EPC
(Source: Created by Author)
4. Use Case Diagram:
Figure 1: Use Case Diagram of EPC
(Source: Created by Author)
11SYSTEM ANALYSIS AND DESIGN
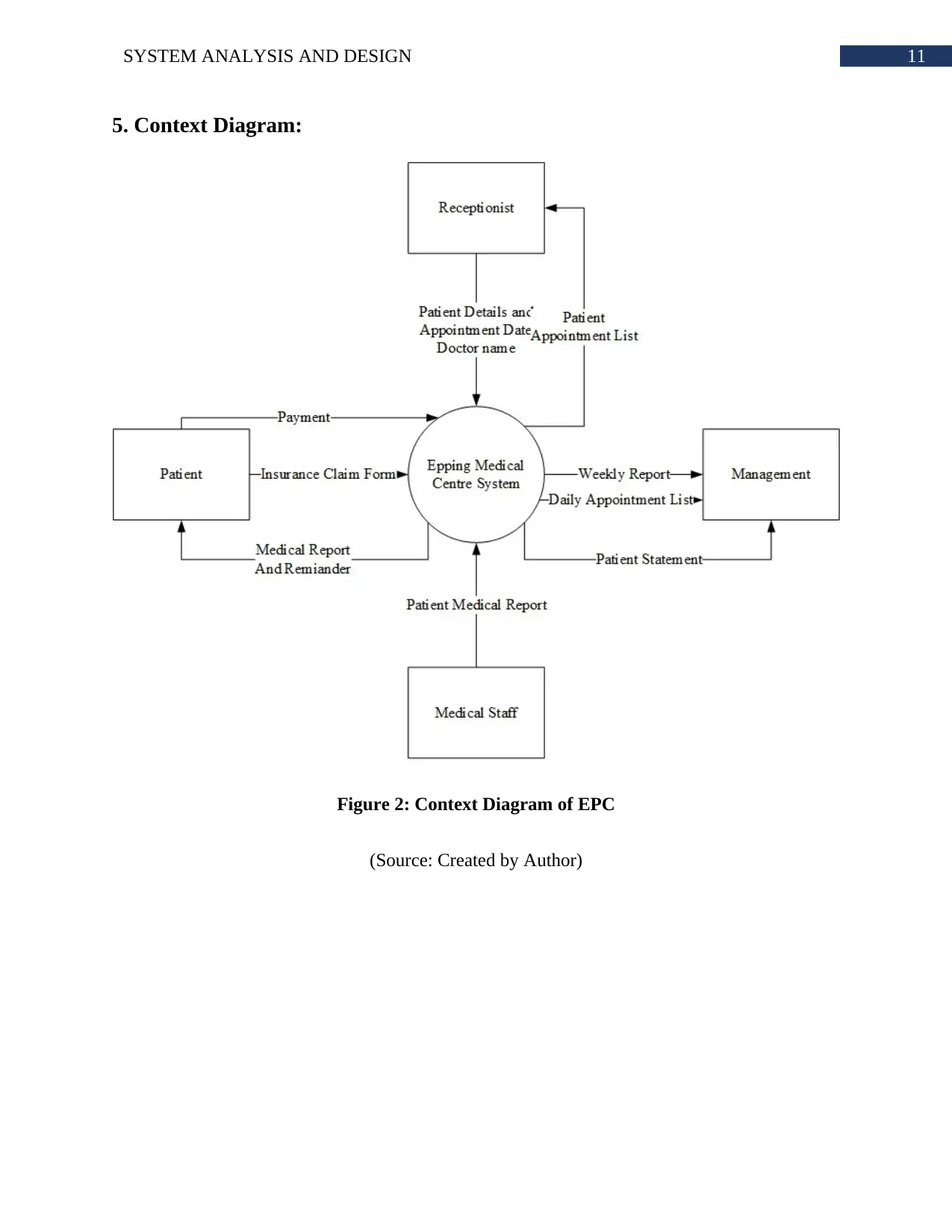
5. Context Diagram:
Figure 2: Context Diagram of EPC
(Source: Created by Author)
5. Context Diagram:
Figure 2: Context Diagram of EPC
(Source: Created by Author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





