ICT Ethical Perspectives: Analysis of Atlanta Ransomware Attack
VerifiedAdded on 2023/06/09
|15
|4393
|401
Essay
AI Summary
This essay analyzes the ethical implications of the ransomware attack on the city of Atlanta in March 2018, using three distinct perspectives of applied ethics: professional, philosophical, and sociological/descriptive ethics. The analysis begins by introducing the Atlanta ransomware incident, where malicious hackers held the city's data hostage, demanding a ransom for its release. From a professional ethics standpoint, the essay discusses the violation of professional standards by the attackers, who breached data security and engaged in unauthorized access. It emphasizes the responsibility of ICT professionals to protect data and prevent malicious activities. The philosophical ethics perspective explores the moral implications of the attack, questioning the justification of causing harm and economic loss to the city. It contrasts the perspectives of the attackers and those responsible for protecting the city's data. Finally, the sociological/descriptive ethics perspective examines the broader societal impact of the attack, including the ethical considerations of the developers who created the ransomware and the decisions made by Atlanta authorities in response. The essay concludes by highlighting the importance of ethical considerations in ICT and the need for robust security measures to prevent future attacks. Desklib provides similar essays and solved assignments for students.

Assessment item 1
Three Distinct Perspectives of Applied Ethics
Value: 10%
Due Date: 05-Aug-2018
Length: 1400-1500
Task
Proceed according to the following instructions.
Identify a recent (within the last six (6) months) ethical dilemma or ethically
questionable situation relating to ICT that you are familiar with. This situation can be
either in the media (for example one you have sourced from a newspaper, or online
through social media) or through your workplace.
o a. If using a workplace example, to maintain confidentiality, do not use real
names.
o b. If you use a media article you must include the link to the media article in
the references list of your assignment.
Identify the key ethical issues contained in your chosen case and use the three distinct
perspectives of applied ethics including professional, philosophical,
sociological/descriptive ethics to analyse the ethical issues involved in the case. The
word limit should be between 1400-1500 words. Note: Headings, citations, references
and any appendices do not count towards your word limit, but quotations do. At the
start of the assignment indicates in brackets the word count of your assignment
excluding those items mentioned above.
Include a Reference list at the end of your work, in the correct APA referencing style,
corresponding to in-text citations. You must include at least THREE (3) quality
academic references (one for each ethical perspective) from different sources. Please
note that these references are in addition to those provided to you through this subject
(for example, you still must reference, Tavani textbook, the Interact subject lecture
notes etc BUT these references cannot be used as one of your three quality academic
references from different sources). Only include references that have been cited in the
body of your assignment and ones that support what you have presented in your
assignment.
Three Distinct Perspectives of Applied Ethics
Value: 10%
Due Date: 05-Aug-2018
Length: 1400-1500
Task
Proceed according to the following instructions.
Identify a recent (within the last six (6) months) ethical dilemma or ethically
questionable situation relating to ICT that you are familiar with. This situation can be
either in the media (for example one you have sourced from a newspaper, or online
through social media) or through your workplace.
o a. If using a workplace example, to maintain confidentiality, do not use real
names.
o b. If you use a media article you must include the link to the media article in
the references list of your assignment.
Identify the key ethical issues contained in your chosen case and use the three distinct
perspectives of applied ethics including professional, philosophical,
sociological/descriptive ethics to analyse the ethical issues involved in the case. The
word limit should be between 1400-1500 words. Note: Headings, citations, references
and any appendices do not count towards your word limit, but quotations do. At the
start of the assignment indicates in brackets the word count of your assignment
excluding those items mentioned above.
Include a Reference list at the end of your work, in the correct APA referencing style,
corresponding to in-text citations. You must include at least THREE (3) quality
academic references (one for each ethical perspective) from different sources. Please
note that these references are in addition to those provided to you through this subject
(for example, you still must reference, Tavani textbook, the Interact subject lecture
notes etc BUT these references cannot be used as one of your three quality academic
references from different sources). Only include references that have been cited in the
body of your assignment and ones that support what you have presented in your
assignment.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Template
[Type the company name]
[Type the document title]
Student name
Student Number
Word Count:
[Type the company name]
[Type the document title]
Student name
Student Number
Word Count:

1. Introduction
In March 2018, a ransomware attack carried out by malicious hackers affected the whole
city of Atlanta. The hackers kept an eye on various data which affected the whole nation.
The city was suffering from the effects of attack even after several months have passed. It
ultimately created an issue since data hostage demanded a lump sum amount of money
after the attack (Peters, 2015). It ultimately becomes a vital matter for various authorities
to pay the ransom value or not. According to the ICT solution, the given situation can be
analyzed for various ethical issues. The analysis will be done with the help of major
factors of applied ethics. In the coming pages, some important aspects of the report that is
professional ethics, philosophical ethics, and sociological ethics have been discussed in
details.
2. Professional Ethics Perspectives
Corporate development professionals are focused to maintain their professional ethics. It
is generally expected that the person working the corporate platform will follow the same
standard throughout their lifetime service (Sorokin, 2017). The professional aspect of
personal behavior should be just considered as a part of the project only. This ultimately
relates to the fact that professionalism should not perform any kind of activities which
will harm the organization, people or their profession.
Various professionals around the globe have to pass through training procedures before
getting into professions. This ultimately relates to the fact behavior performance of an
individual should be just towards their profession only. That particular individual should
be prepared for any step which would benefit his profession. The professional implication
can be stated as the protection of an individual. A professional should have a positive
attitude towards his profession (Christians et al., 2015). Activities which can harm the
In March 2018, a ransomware attack carried out by malicious hackers affected the whole
city of Atlanta. The hackers kept an eye on various data which affected the whole nation.
The city was suffering from the effects of attack even after several months have passed. It
ultimately created an issue since data hostage demanded a lump sum amount of money
after the attack (Peters, 2015). It ultimately becomes a vital matter for various authorities
to pay the ransom value or not. According to the ICT solution, the given situation can be
analyzed for various ethical issues. The analysis will be done with the help of major
factors of applied ethics. In the coming pages, some important aspects of the report that is
professional ethics, philosophical ethics, and sociological ethics have been discussed in
details.
2. Professional Ethics Perspectives
Corporate development professionals are focused to maintain their professional ethics. It
is generally expected that the person working the corporate platform will follow the same
standard throughout their lifetime service (Sorokin, 2017). The professional aspect of
personal behavior should be just considered as a part of the project only. This ultimately
relates to the fact that professionalism should not perform any kind of activities which
will harm the organization, people or their profession.
Various professionals around the globe have to pass through training procedures before
getting into professions. This ultimately relates to the fact behavior performance of an
individual should be just towards their profession only. That particular individual should
be prepared for any step which would benefit his profession. The professional implication
can be stated as the protection of an individual. A professional should have a positive
attitude towards his profession (Christians et al., 2015). Activities which can harm the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

profession of the individual should be banned or abandoned. People who are associated
with the respective organization should be barred as per the professional ethics.
In this case, attackers have gained an accesses to computers which have provided them
with activities of the whole city. It has ultimately break various ethical implication
imposed by professional ethics. Ransomware transfer is a major kind of ethical
implication which should be kept away from developing for malicious attackers that
breach out data and are not authorized to use (Bertrand, 2018). Every professional should
come up with sole ownership of authorized use and professional ethics so that no one else
should be able to use it in a proper way. Every personal data should come up with sole
ownership of an authorized user. By professional ethics, no one should have an easy
access to them. By this method, a proper balance is maintained between the user and all
of the substrate for which data has been working. In this case, all the professional codes
of ethics have been violated as a ransomware attack has victimized all the people who are
associated with the profession. A hacker is the only guy responsible for a data breach.
Any developer should have a positive intention for creating a software which can be used
for providing benefits to the associated organization. Ransomware developer, develop
software which can not only harm other but can help in gaining financial ransom in
exchange of data provided. It ultimately defines the laws of professional ethics in the
much better way (Gupta, Agrawal & Yamaguchi, 2016). Apart from this, various
organization or authorities should be careful regarding the fact of handling the enormous
value of data. Along with this, they must understand the confidentiality of data. If there is
a failure against the protection of data against hacking can be considered as the disobey of
professional ethics.
3. Philosophical Ethics Perspectives
with the respective organization should be barred as per the professional ethics.
In this case, attackers have gained an accesses to computers which have provided them
with activities of the whole city. It has ultimately break various ethical implication
imposed by professional ethics. Ransomware transfer is a major kind of ethical
implication which should be kept away from developing for malicious attackers that
breach out data and are not authorized to use (Bertrand, 2018). Every professional should
come up with sole ownership of authorized use and professional ethics so that no one else
should be able to use it in a proper way. Every personal data should come up with sole
ownership of an authorized user. By professional ethics, no one should have an easy
access to them. By this method, a proper balance is maintained between the user and all
of the substrate for which data has been working. In this case, all the professional codes
of ethics have been violated as a ransomware attack has victimized all the people who are
associated with the profession. A hacker is the only guy responsible for a data breach.
Any developer should have a positive intention for creating a software which can be used
for providing benefits to the associated organization. Ransomware developer, develop
software which can not only harm other but can help in gaining financial ransom in
exchange of data provided. It ultimately defines the laws of professional ethics in the
much better way (Gupta, Agrawal & Yamaguchi, 2016). Apart from this, various
organization or authorities should be careful regarding the fact of handling the enormous
value of data. Along with this, they must understand the confidentiality of data. If there is
a failure against the protection of data against hacking can be considered as the disobey of
professional ethics.
3. Philosophical Ethics Perspectives
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Professional ethics can be easily stated as delicate human professionals which will make
the various professionals to easily question their activities. It mainly checks the fact
whether it is justified or unjust as per the human morals (Buczak & Guven, 2016). For
proper professional conduct an individual need to be morally correct. While carrying out
their task every individual should be true to their moral laws. A philosophical ethics is
not generally limited to professional and professions. It also focuses on the fact that
individuals should be true to the profession and their life. Now if a profession of a given
person does not allow him to morally justified then the rest of life would be justified as
the rest of the life. Then its implication is not justified as per the various professional
ethics (Gordon et al., 2015). It also addresses the fact that a person cannot provide
justification against morality which is given towards profession life or personal life. He or
she cannot overlook their philosophical ethics towards anyone of them.
Now coming to the given scenario of philosophical ethics which took place in the city of
Atlanta with respect to ransomware attack. There is mainly perspective in the given
scenario. The first one is the perspective of the attackers who caused the attack and
another one is the various person who is in charge of protecting confidential and
important data of the city. Along with these, they are involved in protecting and
controlling the system of the entire city (Kharraz et al., 2015). Both this two perspective
can be controlled by the help of professional ethics.
Ethical choices are considered to be one toughest choice during the entire professional
life cycles. Experiences in-person life help in having an idea regarding between right and
wrong. The effect or consequence of right and wrong totally depends on the perspective
of an individual that is it varies from one person to another. Causing any kind of harm
cannot be justified at any point of view. Ransomware attack which can be carried out by
various malicious developer needs to be carried in the whole city of Atlanta. It mainly
the various professionals to easily question their activities. It mainly checks the fact
whether it is justified or unjust as per the human morals (Buczak & Guven, 2016). For
proper professional conduct an individual need to be morally correct. While carrying out
their task every individual should be true to their moral laws. A philosophical ethics is
not generally limited to professional and professions. It also focuses on the fact that
individuals should be true to the profession and their life. Now if a profession of a given
person does not allow him to morally justified then the rest of life would be justified as
the rest of the life. Then its implication is not justified as per the various professional
ethics (Gordon et al., 2015). It also addresses the fact that a person cannot provide
justification against morality which is given towards profession life or personal life. He or
she cannot overlook their philosophical ethics towards anyone of them.
Now coming to the given scenario of philosophical ethics which took place in the city of
Atlanta with respect to ransomware attack. There is mainly perspective in the given
scenario. The first one is the perspective of the attackers who caused the attack and
another one is the various person who is in charge of protecting confidential and
important data of the city. Along with these, they are involved in protecting and
controlling the system of the entire city (Kharraz et al., 2015). Both this two perspective
can be controlled by the help of professional ethics.
Ethical choices are considered to be one toughest choice during the entire professional
life cycles. Experiences in-person life help in having an idea regarding between right and
wrong. The effect or consequence of right and wrong totally depends on the perspective
of an individual that is it varies from one person to another. Causing any kind of harm
cannot be justified at any point of view. Ransomware attack which can be carried out by
various malicious developer needs to be carried in the whole city of Atlanta. It mainly

focuses on the bargain of the whole network of the city (Maurya et al., 2018). The
hackers have demanded a ransom value of 6,800 USD per system along with a sum value
of 51,0000 USD in bitcoins for unlocking each and every system of the city. It is totally
unjust as per any kind of philosophical effect which will not harm the city Atlanta for
their confidential data which can result in huge economic loss towards Atlanta City.
4. Sociological/Descriptive Ethics Perspectives
In any phenomenon, there are many cases or aspects of an ethical perspective. These can
be easily differentiated into ethics, descriptive ethics, meta-ethics and lastly applied
ethics. Normative ethics are mainly applied to a large number of ways which can be used
for maintaining ethical implications. On the other hand, meta-ethics mainly describes the
actual kind of ethics which are related to ethical implication behind the behavior action of
an individual (Quinkert et al., 2018). The idea of descriptive ethics establishes a bridge
between the two aspects regarding the behavior of an individual with respect to
professional. It is to be noted that the ethics perspective should be taken into
consideration which is important for empirical research. It totally depends on the attitude
of various people which analyzes ethical implication towards their professions.
In this situation, various malicious developers require software which comes up with the
ability to stop any access to the system and make data hostage. The developers mainly
targeted the whole city of Atlanta and their devices which gained an access to confidential
data of the whole city. It was the sole decision of the group to easily develop and transfer
various kinds of a variant of the given software over the given network. It has resulted in
various kinds of implications which can bring networks users in this particular city
(Mohurle & Patil, 2017). The important work may be hampered just because of this
which have continued to work with malicious codes. It mainly focused on the fact how
hackers have demanded a ransom value of 6,800 USD per system along with a sum value
of 51,0000 USD in bitcoins for unlocking each and every system of the city. It is totally
unjust as per any kind of philosophical effect which will not harm the city Atlanta for
their confidential data which can result in huge economic loss towards Atlanta City.
4. Sociological/Descriptive Ethics Perspectives
In any phenomenon, there are many cases or aspects of an ethical perspective. These can
be easily differentiated into ethics, descriptive ethics, meta-ethics and lastly applied
ethics. Normative ethics are mainly applied to a large number of ways which can be used
for maintaining ethical implications. On the other hand, meta-ethics mainly describes the
actual kind of ethics which are related to ethical implication behind the behavior action of
an individual (Quinkert et al., 2018). The idea of descriptive ethics establishes a bridge
between the two aspects regarding the behavior of an individual with respect to
professional. It is to be noted that the ethics perspective should be taken into
consideration which is important for empirical research. It totally depends on the attitude
of various people which analyzes ethical implication towards their professions.
In this situation, various malicious developers require software which comes up with the
ability to stop any access to the system and make data hostage. The developers mainly
targeted the whole city of Atlanta and their devices which gained an access to confidential
data of the whole city. It was the sole decision of the group to easily develop and transfer
various kinds of a variant of the given software over the given network. It has resulted in
various kinds of implications which can bring networks users in this particular city
(Mohurle & Patil, 2017). The important work may be hampered just because of this
which have continued to work with malicious codes. It mainly focused on the fact how
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

hacker’s morals were affected due to ethical laws which addressed to them have ransom
from various authorities.
On another hand, after the attack, Atlanta authorities have agreed to provide their ransom.
Apart from this, they asked various municipal authorities to shut down their system. It
was done to ensure that the fact virus attack does not bring any of harm to the city.
Taking account of the fact that this would be helpful in the propagation of work
throughout the city for a given certain amount of time (Chong, 2017). It is the only
measures to remove attacks from any kind of hacking of data in the computer. It will
ultimately lead to collateral damage which is mainly done for improvement.
from various authorities.
On another hand, after the attack, Atlanta authorities have agreed to provide their ransom.
Apart from this, they asked various municipal authorities to shut down their system. It
was done to ensure that the fact virus attack does not bring any of harm to the city.
Taking account of the fact that this would be helpful in the propagation of work
throughout the city for a given certain amount of time (Chong, 2017). It is the only
measures to remove attacks from any kind of hacking of data in the computer. It will
ultimately lead to collateral damage which is mainly done for improvement.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5. References
Bertrand, C. J. (2018). Media ethics and accountability systems. Routledge.
Buczak, A. L., & Guven, E. (2016). A survey of data mining and machine learning methods
for cyber security intrusion detection. IEEE Communications Surveys &
Tutorials, 18(2), 1153-1176.
Chong, H. (2017). SeCBD: The Application Idea from Study Evaluation of Ransomware
Attack Method in Big Data Architecture. Procedia Computer Science, 116, 358-364.
Christians, C. G., Richardson, K. B., Fackler, M., Kreshel, P., & Woods, R. H. (2015). Media
Ethics: Cases and Moral Reasoning, CourseSmart eTextbook. Routledge.
Gordon, L. A., Loeb, M. P., Lucyshyn, W., & Zhou, L. (2015). Externalities and the
magnitude of cyber security underinvestment by private sector firms: a modification
of the Gordon-Loeb model. Journal of Information Security, 6(1), 24.
Gupta, B., Agrawal, D. P., & Yamaguchi, S. (Eds.). (2016). Handbook of research on
modern cryptographic solutions for computer and cyber security. IGI Global.
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L., & Kirda, E. (2015, July). Cutting the
gordian knot: A look under the hood of ransomware attacks. In International
Conference on Detection of Intrusions and Malware, and Vulnerability
Assessment (pp. 3-24). Springer, Cham.
Maurya, A. K., Kumar, N., Agrawal, A., & Khan, R. A. (2018). Ransomware: Evolution,
Target and Safety Measures.
Mohurle, S., & Patil, M. (2017). A brief study of wannacry threat: Ransomware attack
2017. International Journal of Advanced Research in Computer Science, 8(5).
Peters, R. S. (2015). Ethics and Education (Routledge Revivals). Routledge.
Bertrand, C. J. (2018). Media ethics and accountability systems. Routledge.
Buczak, A. L., & Guven, E. (2016). A survey of data mining and machine learning methods
for cyber security intrusion detection. IEEE Communications Surveys &
Tutorials, 18(2), 1153-1176.
Chong, H. (2017). SeCBD: The Application Idea from Study Evaluation of Ransomware
Attack Method in Big Data Architecture. Procedia Computer Science, 116, 358-364.
Christians, C. G., Richardson, K. B., Fackler, M., Kreshel, P., & Woods, R. H. (2015). Media
Ethics: Cases and Moral Reasoning, CourseSmart eTextbook. Routledge.
Gordon, L. A., Loeb, M. P., Lucyshyn, W., & Zhou, L. (2015). Externalities and the
magnitude of cyber security underinvestment by private sector firms: a modification
of the Gordon-Loeb model. Journal of Information Security, 6(1), 24.
Gupta, B., Agrawal, D. P., & Yamaguchi, S. (Eds.). (2016). Handbook of research on
modern cryptographic solutions for computer and cyber security. IGI Global.
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L., & Kirda, E. (2015, July). Cutting the
gordian knot: A look under the hood of ransomware attacks. In International
Conference on Detection of Intrusions and Malware, and Vulnerability
Assessment (pp. 3-24). Springer, Cham.
Maurya, A. K., Kumar, N., Agrawal, A., & Khan, R. A. (2018). Ransomware: Evolution,
Target and Safety Measures.
Mohurle, S., & Patil, M. (2017). A brief study of wannacry threat: Ransomware attack
2017. International Journal of Advanced Research in Computer Science, 8(5).
Peters, R. S. (2015). Ethics and Education (Routledge Revivals). Routledge.
Quinkert, F., Holz, T., Hossain, K. S. M., Ferrara, E., & Lerman, K. (2018). RAPTOR:
Ransomware Attack PredicTOR. arXiv preprint arXiv:1803.01598.
Sorokin, P. (2017). Social and cultural dynamics: A study of change in major systems of art,
truth, ethics, law and social relationships. Routledge.
Video link: https://www.youtube.com/watch?v=v5M7ohdZ6qA
Ransomware Attack PredicTOR. arXiv preprint arXiv:1803.01598.
Sorokin, P. (2017). Social and cultural dynamics: A study of change in major systems of art,
truth, ethics, law and social relationships. Routledge.
Video link: https://www.youtube.com/watch?v=v5M7ohdZ6qA
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
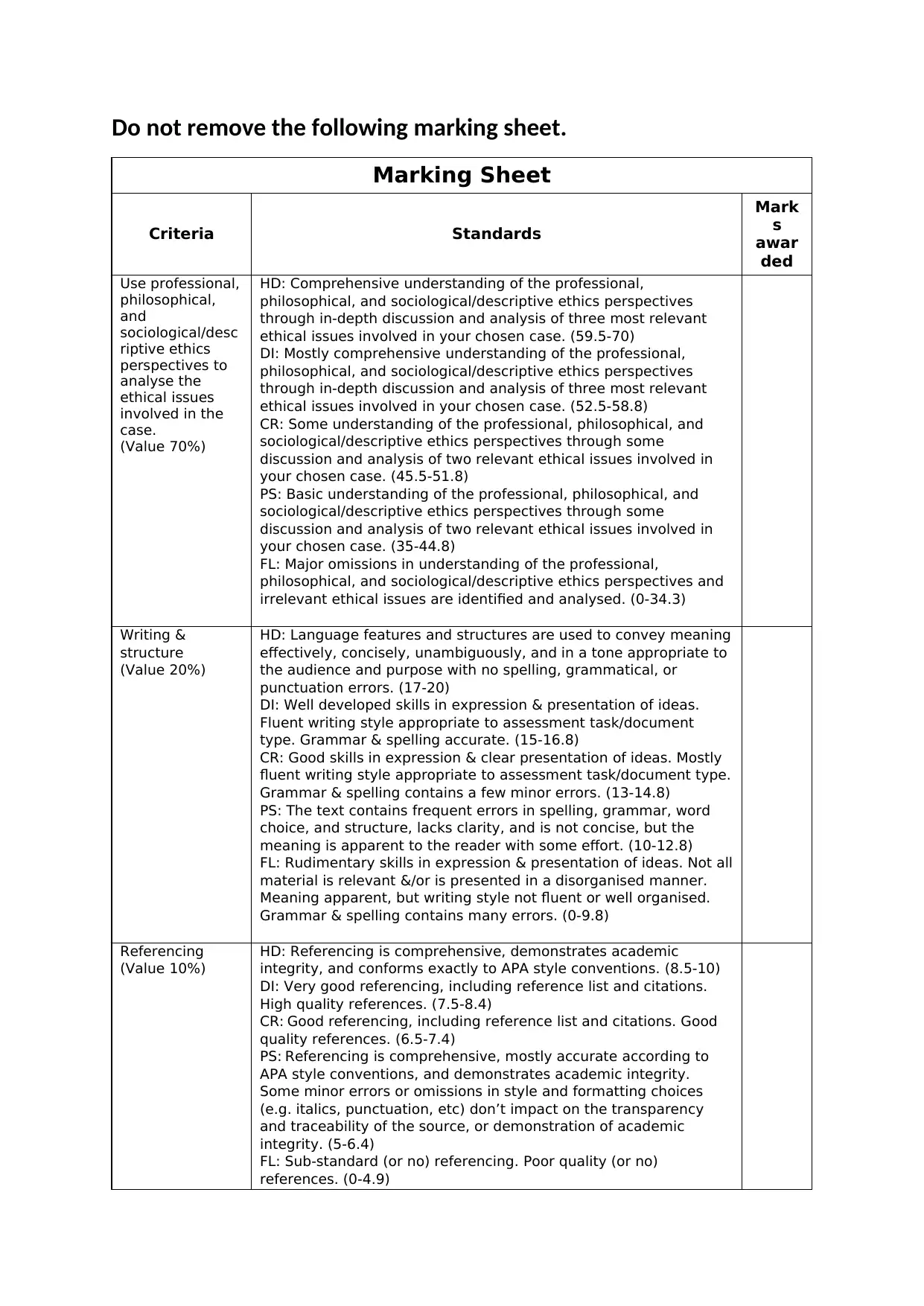
Do not remove the following marking sheet.
Marking Sheet
Criteria Standards
Mark
s
awar
ded
Use professional,
philosophical,
and
sociological/desc
riptive ethics
perspectives to
analyse the
ethical issues
involved in the
case.
(Value 70%)
HD: Comprehensive understanding of the professional,
philosophical, and sociological/descriptive ethics perspectives
through in-depth discussion and analysis of three most relevant
ethical issues involved in your chosen case. (59.5-70)
DI: Mostly comprehensive understanding of the professional,
philosophical, and sociological/descriptive ethics perspectives
through in-depth discussion and analysis of three most relevant
ethical issues involved in your chosen case. (52.5-58.8)
CR: Some understanding of the professional, philosophical, and
sociological/descriptive ethics perspectives through some
discussion and analysis of two relevant ethical issues involved in
your chosen case. (45.5-51.8)
PS: Basic understanding of the professional, philosophical, and
sociological/descriptive ethics perspectives through some
discussion and analysis of two relevant ethical issues involved in
your chosen case. (35-44.8)
FL: Major omissions in understanding of the professional,
philosophical, and sociological/descriptive ethics perspectives and
irrelevant ethical issues are identified and analysed. (0-34.3)
Writing &
structure
(Value 20%)
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to
the audience and purpose with no spelling, grammatical, or
punctuation errors. (17-20)
DI: Well developed skills in expression & presentation of ideas.
Fluent writing style appropriate to assessment task/document
type. Grammar & spelling accurate. (15-16.8)
CR: Good skills in expression & clear presentation of ideas. Mostly
fluent writing style appropriate to assessment task/document type.
Grammar & spelling contains a few minor errors. (13-14.8)
PS: The text contains frequent errors in spelling, grammar, word
choice, and structure, lacks clarity, and is not concise, but the
meaning is apparent to the reader with some effort. (10-12.8)
FL: Rudimentary skills in expression & presentation of ideas. Not all
material is relevant &/or is presented in a disorganised manner.
Meaning apparent, but writing style not fluent or well organised.
Grammar & spelling contains many errors. (0-9.8)
Referencing
(Value 10%)
HD: Referencing is comprehensive, demonstrates academic
integrity, and conforms exactly to APA style conventions. (8.5-10)
DI: Very good referencing, including reference list and citations.
High quality references. (7.5-8.4)
CR: Good referencing, including reference list and citations. Good
quality references. (6.5-7.4)
PS: Referencing is comprehensive, mostly accurate according to
APA style conventions, and demonstrates academic integrity.
Some minor errors or omissions in style and formatting choices
(e.g. italics, punctuation, etc) don’t impact on the transparency
and traceability of the source, or demonstration of academic
integrity. (5-6.4)
FL: Sub-standard (or no) referencing. Poor quality (or no)
references. (0-4.9)
Marking Sheet
Criteria Standards
Mark
s
awar
ded
Use professional,
philosophical,
and
sociological/desc
riptive ethics
perspectives to
analyse the
ethical issues
involved in the
case.
(Value 70%)
HD: Comprehensive understanding of the professional,
philosophical, and sociological/descriptive ethics perspectives
through in-depth discussion and analysis of three most relevant
ethical issues involved in your chosen case. (59.5-70)
DI: Mostly comprehensive understanding of the professional,
philosophical, and sociological/descriptive ethics perspectives
through in-depth discussion and analysis of three most relevant
ethical issues involved in your chosen case. (52.5-58.8)
CR: Some understanding of the professional, philosophical, and
sociological/descriptive ethics perspectives through some
discussion and analysis of two relevant ethical issues involved in
your chosen case. (45.5-51.8)
PS: Basic understanding of the professional, philosophical, and
sociological/descriptive ethics perspectives through some
discussion and analysis of two relevant ethical issues involved in
your chosen case. (35-44.8)
FL: Major omissions in understanding of the professional,
philosophical, and sociological/descriptive ethics perspectives and
irrelevant ethical issues are identified and analysed. (0-34.3)
Writing &
structure
(Value 20%)
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to
the audience and purpose with no spelling, grammatical, or
punctuation errors. (17-20)
DI: Well developed skills in expression & presentation of ideas.
Fluent writing style appropriate to assessment task/document
type. Grammar & spelling accurate. (15-16.8)
CR: Good skills in expression & clear presentation of ideas. Mostly
fluent writing style appropriate to assessment task/document type.
Grammar & spelling contains a few minor errors. (13-14.8)
PS: The text contains frequent errors in spelling, grammar, word
choice, and structure, lacks clarity, and is not concise, but the
meaning is apparent to the reader with some effort. (10-12.8)
FL: Rudimentary skills in expression & presentation of ideas. Not all
material is relevant &/or is presented in a disorganised manner.
Meaning apparent, but writing style not fluent or well organised.
Grammar & spelling contains many errors. (0-9.8)
Referencing
(Value 10%)
HD: Referencing is comprehensive, demonstrates academic
integrity, and conforms exactly to APA style conventions. (8.5-10)
DI: Very good referencing, including reference list and citations.
High quality references. (7.5-8.4)
CR: Good referencing, including reference list and citations. Good
quality references. (6.5-7.4)
PS: Referencing is comprehensive, mostly accurate according to
APA style conventions, and demonstrates academic integrity.
Some minor errors or omissions in style and formatting choices
(e.g. italics, punctuation, etc) don’t impact on the transparency
and traceability of the source, or demonstration of academic
integrity. (5-6.4)
FL: Sub-standard (or no) referencing. Poor quality (or no)
references. (0-4.9)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Total Marks
SSCHOOL OF COMPUTING AND MATHS, CHARLES STURT UNIVERSITY
Sample assignment
Assignment 1: Professional and Philosophical Ethics
Maninder Kalsi
11340114
SSCHOOL OF COMPUTING AND MATHS, CHARLES STURT UNIVERSITY
Sample assignment
Assignment 1: Professional and Philosophical Ethics
Maninder Kalsi
11340114

Word Count: 1167
1. Introduction
Applied ethics is the branch of ethics which consists of the analysis of specific, controversial moral
issues. These controversial moral issues can be approached through three distinct perspectives of
applied ethics: professional ethics, philosophical ethics and sociological ethics. In this essay,
normative inquiries: professional and philosophical ethics perspectives are used to analyse the
ethical issues involved in the chosen video, ‘Early Launch’.
Video1: https://www.youtube.com/watch?v=v5M7ohdZ6qA
2. Professional Ethics Perspectives
Issues of ethical responsibility in the ICT workplace are at the forefront of discussion whilst
discussing professional ethics perspectives. Tavani (2013, p.18) states that “professional ethics
issues typically involve concerns of responsibility and obligation affecting individuals as
members of certain profession”.
In the video ‘early launch’, the Project Manager has been asked by the company Program
Director to consider options for delivery of the software before the deadline date. This can be
achieved by delivering the software solution to the client without encryption. The company
CEO thinks that this might help with securing the next contract with the client.
Meeting client expectations should be the main priority and if system reliability is
compromised, it raises serious questions about the professional and moral ethics that exist
in the company. Some of the professional ethical issues that should be considered are:
honesty, accountability and integrity towards the customers and system reliability. The
system that is not reliable or a system that does not meet the requirements as desired by the
client, amounts to deception on part of the supplier.
If the company decides to deliver the software solution without encryption, it may lead to
various implications for the company. One of the biggest concern is the professional approach
of the management towards the client. It raises serious questions about the working culture
in the company. Is the management honest in their approach? What about the accountability
and integrity towards the client. If the client finds out about this shortcut approach, they may
accuse the company of deception. It needs to be noted here that client is not the only
stakeholder affected by this, but the company will also be affected in the long run losing its
goodwill and reputation. The thought of delivering incomplete solution to the client, should
not have arisen if professional code of ethics existed or followed by the company. Professional
code of ethics is a set of guidelines that outlines the expected behaviour of workers. It exists
to ensure that clients’ rights are protected and to ensure that there is consistency and
credibility in professional practice.
Bynum and Rogerson (2004), state that ‘codes inspire members of the profession by identifying
values and ideals to which members can aspire. It needs to be noted here that codes need to
be broad enough to cover vast majority of ethical conflicts that might exist.
1. Introduction
Applied ethics is the branch of ethics which consists of the analysis of specific, controversial moral
issues. These controversial moral issues can be approached through three distinct perspectives of
applied ethics: professional ethics, philosophical ethics and sociological ethics. In this essay,
normative inquiries: professional and philosophical ethics perspectives are used to analyse the
ethical issues involved in the chosen video, ‘Early Launch’.
Video1: https://www.youtube.com/watch?v=v5M7ohdZ6qA
2. Professional Ethics Perspectives
Issues of ethical responsibility in the ICT workplace are at the forefront of discussion whilst
discussing professional ethics perspectives. Tavani (2013, p.18) states that “professional ethics
issues typically involve concerns of responsibility and obligation affecting individuals as
members of certain profession”.
In the video ‘early launch’, the Project Manager has been asked by the company Program
Director to consider options for delivery of the software before the deadline date. This can be
achieved by delivering the software solution to the client without encryption. The company
CEO thinks that this might help with securing the next contract with the client.
Meeting client expectations should be the main priority and if system reliability is
compromised, it raises serious questions about the professional and moral ethics that exist
in the company. Some of the professional ethical issues that should be considered are:
honesty, accountability and integrity towards the customers and system reliability. The
system that is not reliable or a system that does not meet the requirements as desired by the
client, amounts to deception on part of the supplier.
If the company decides to deliver the software solution without encryption, it may lead to
various implications for the company. One of the biggest concern is the professional approach
of the management towards the client. It raises serious questions about the working culture
in the company. Is the management honest in their approach? What about the accountability
and integrity towards the client. If the client finds out about this shortcut approach, they may
accuse the company of deception. It needs to be noted here that client is not the only
stakeholder affected by this, but the company will also be affected in the long run losing its
goodwill and reputation. The thought of delivering incomplete solution to the client, should
not have arisen if professional code of ethics existed or followed by the company. Professional
code of ethics is a set of guidelines that outlines the expected behaviour of workers. It exists
to ensure that clients’ rights are protected and to ensure that there is consistency and
credibility in professional practice.
Bynum and Rogerson (2004), state that ‘codes inspire members of the profession by identifying
values and ideals to which members can aspire. It needs to be noted here that codes need to
be broad enough to cover vast majority of ethical conflicts that might exist.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


![Analyzing ICT Ethical Issues Using Ethical Theories - [Course Name]](/_next/image/?url=https%3A%2F%2Fdesklib.com%2Fmedia%2Fimages%2Fe29ab4a5fdcc4564af0c176e1c8c64ca.jpg&w=256&q=75)

