IT Ethical Dilemma Case Study: ITC506 Early Launch Assignment 1
VerifiedAdded on 2021/04/21
|9
|2019
|217
Case Study
AI Summary
This case study examines an ethical dilemma in IT, specifically the decision to deliver software without encryption to meet an early delivery deadline. The analysis, performed using the "Doing Ethics Technique," addresses the core issue of compromised software security due to the lack of encryption, the potential vulnerabilities, and the ethical implications of such a decision. It identifies stakeholders, outlines ethical issues, and evaluates various options, such as delaying the project to implement encryption or delivering the software with a security patch later. The study emphasizes the importance of prioritizing security and the potential consequences of data breaches. The student concludes that the best course of action is to ignore the project manager's suggestion and ensure the software has proper encryption before delivery, to maintain the organization's reputation and protect client data.

SCHOOL OF COMPUTING AND MATHS, Charles Sturt University
IT Ethical Dilemma / Early Launch
Assignment 1: Doing Ethics Technique
Your Name
Student Number
Word Count: 1000
IT Ethical Dilemma / Early Launch
Assignment 1: Doing Ethics Technique
Your Name
Student Number
Word Count: 1000
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Title of you case study/scenario
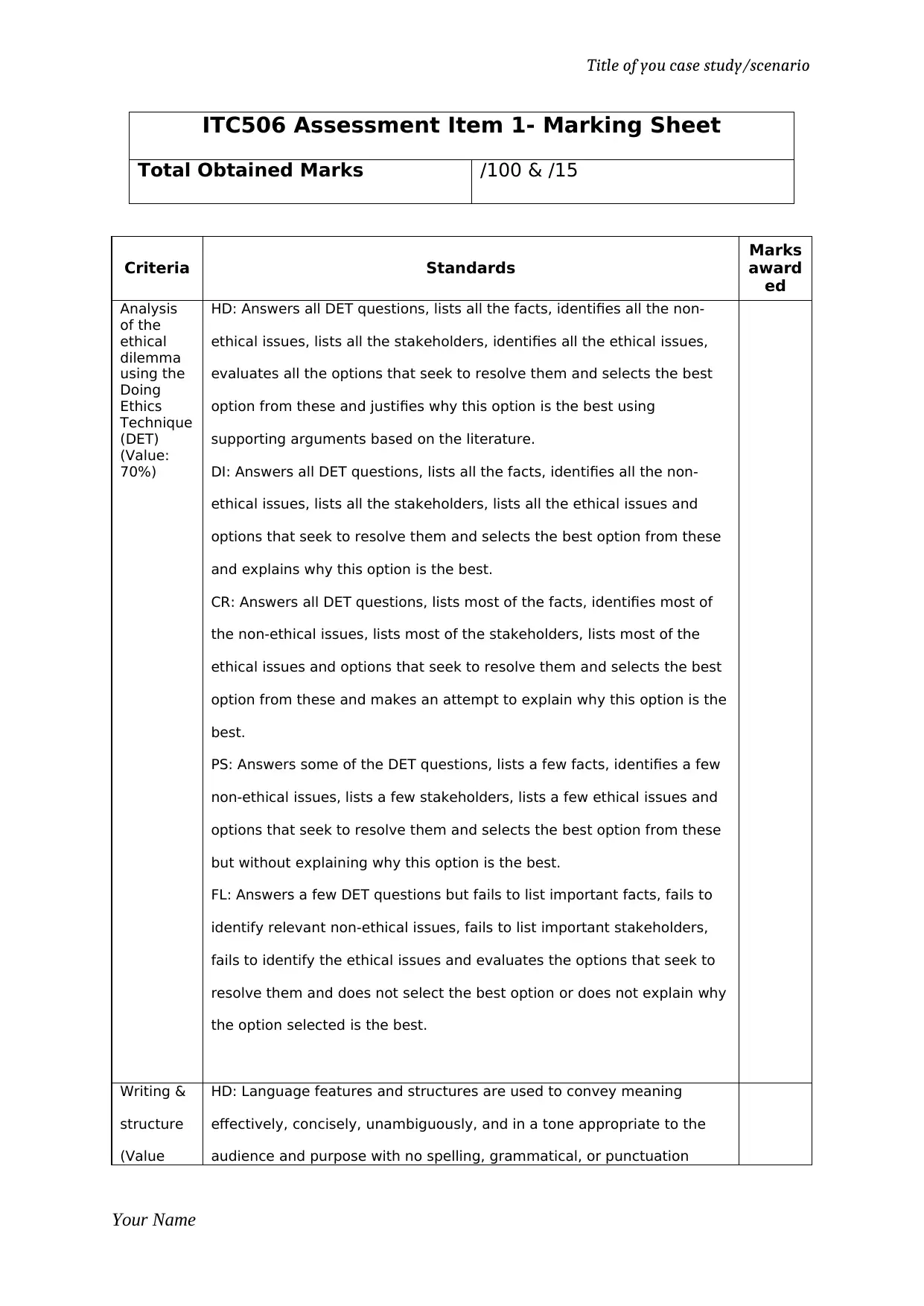
ITC506 Assessment Item 1- Marking Sheet
Total Obtained Marks /100 & /15
Criteria Standards
Marks
award
ed
Analysis
of the
ethical
dilemma
using the
Doing
Ethics
Technique
(DET)
(Value:
70%)
HD: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, identifies all the ethical issues,
evaluates all the options that seek to resolve them and selects the best
option from these and justifies why this option is the best using
supporting arguments based on the literature.
DI: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, lists all the ethical issues and
options that seek to resolve them and selects the best option from these
and explains why this option is the best.
CR: Answers all DET questions, lists most of the facts, identifies most of
the non-ethical issues, lists most of the stakeholders, lists most of the
ethical issues and options that seek to resolve them and selects the best
option from these and makes an attempt to explain why this option is the
best.
PS: Answers some of the DET questions, lists a few facts, identifies a few
non-ethical issues, lists a few stakeholders, lists a few ethical issues and
options that seek to resolve them and selects the best option from these
but without explaining why this option is the best.
FL: Answers a few DET questions but fails to list important facts, fails to
identify relevant non-ethical issues, fails to list important stakeholders,
fails to identify the ethical issues and evaluates the options that seek to
resolve them and does not select the best option or does not explain why
the option selected is the best.
Writing &
structure
(Value
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to the
audience and purpose with no spelling, grammatical, or punctuation
Your Name
ITC506 Assessment Item 1- Marking Sheet
Total Obtained Marks /100 & /15
Criteria Standards
Marks
award
ed
Analysis
of the
ethical
dilemma
using the
Doing
Ethics
Technique
(DET)
(Value:
70%)
HD: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, identifies all the ethical issues,
evaluates all the options that seek to resolve them and selects the best
option from these and justifies why this option is the best using
supporting arguments based on the literature.
DI: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, lists all the ethical issues and
options that seek to resolve them and selects the best option from these
and explains why this option is the best.
CR: Answers all DET questions, lists most of the facts, identifies most of
the non-ethical issues, lists most of the stakeholders, lists most of the
ethical issues and options that seek to resolve them and selects the best
option from these and makes an attempt to explain why this option is the
best.
PS: Answers some of the DET questions, lists a few facts, identifies a few
non-ethical issues, lists a few stakeholders, lists a few ethical issues and
options that seek to resolve them and selects the best option from these
but without explaining why this option is the best.
FL: Answers a few DET questions but fails to list important facts, fails to
identify relevant non-ethical issues, fails to list important stakeholders,
fails to identify the ethical issues and evaluates the options that seek to
resolve them and does not select the best option or does not explain why
the option selected is the best.
Writing &
structure
(Value
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to the
audience and purpose with no spelling, grammatical, or punctuation
Your Name
Title of you case study/scenario
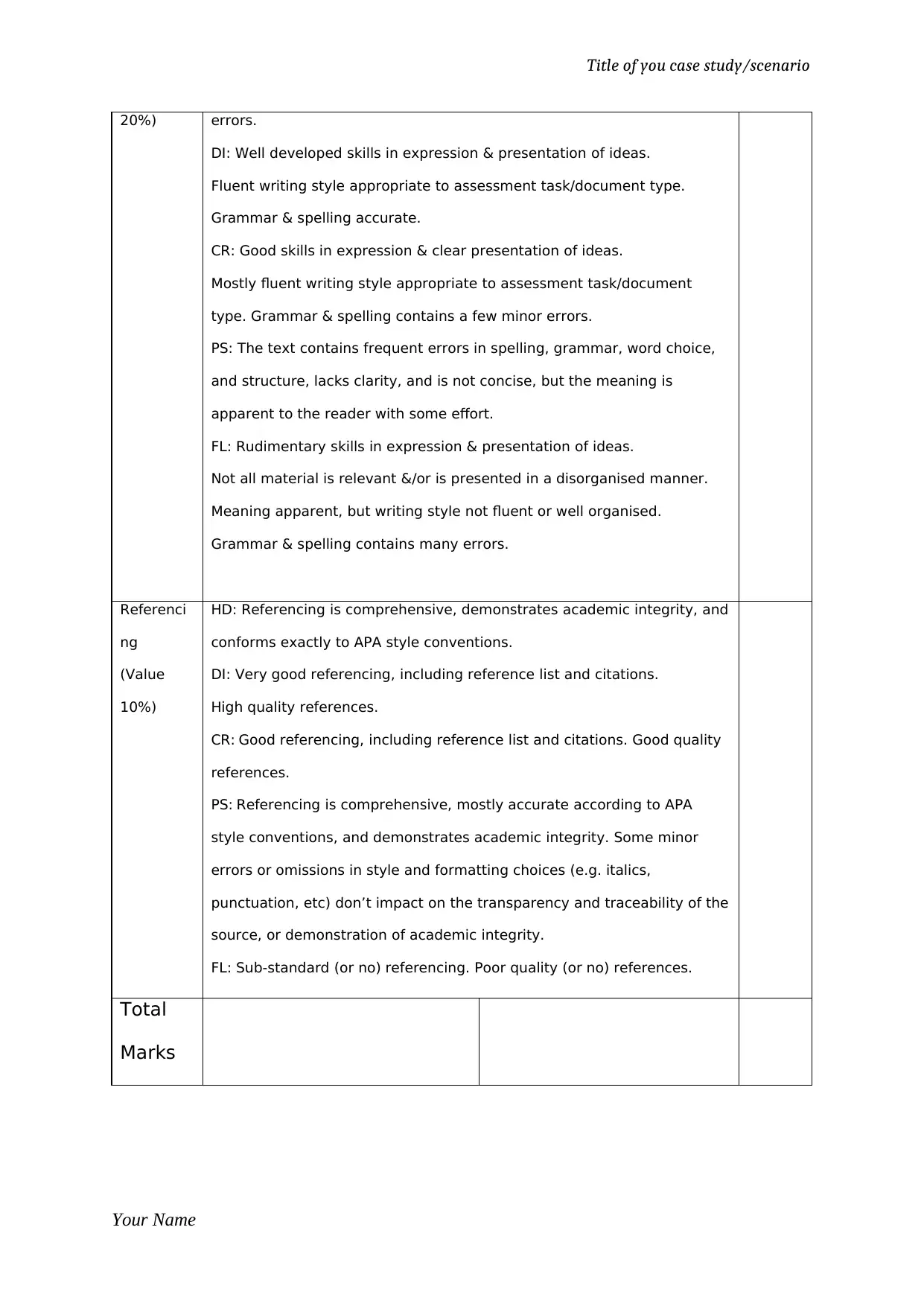
20%) errors.
DI: Well developed skills in expression & presentation of ideas.
Fluent writing style appropriate to assessment task/document type.
Grammar & spelling accurate.
CR: Good skills in expression & clear presentation of ideas.
Mostly fluent writing style appropriate to assessment task/document
type. Grammar & spelling contains a few minor errors.
PS: The text contains frequent errors in spelling, grammar, word choice,
and structure, lacks clarity, and is not concise, but the meaning is
apparent to the reader with some effort.
FL: Rudimentary skills in expression & presentation of ideas.
Not all material is relevant &/or is presented in a disorganised manner.
Meaning apparent, but writing style not fluent or well organised.
Grammar & spelling contains many errors.
Referenci
ng
(Value
10%)
HD: Referencing is comprehensive, demonstrates academic integrity, and
conforms exactly to APA style conventions.
DI: Very good referencing, including reference list and citations.
High quality references.
CR: Good referencing, including reference list and citations. Good quality
references.
PS: Referencing is comprehensive, mostly accurate according to APA
style conventions, and demonstrates academic integrity. Some minor
errors or omissions in style and formatting choices (e.g. italics,
punctuation, etc) don’t impact on the transparency and traceability of the
source, or demonstration of academic integrity.
FL: Sub-standard (or no) referencing. Poor quality (or no) references.
Total
Marks
Your Name
20%) errors.
DI: Well developed skills in expression & presentation of ideas.
Fluent writing style appropriate to assessment task/document type.
Grammar & spelling accurate.
CR: Good skills in expression & clear presentation of ideas.
Mostly fluent writing style appropriate to assessment task/document
type. Grammar & spelling contains a few minor errors.
PS: The text contains frequent errors in spelling, grammar, word choice,
and structure, lacks clarity, and is not concise, but the meaning is
apparent to the reader with some effort.
FL: Rudimentary skills in expression & presentation of ideas.
Not all material is relevant &/or is presented in a disorganised manner.
Meaning apparent, but writing style not fluent or well organised.
Grammar & spelling contains many errors.
Referenci
ng
(Value
10%)
HD: Referencing is comprehensive, demonstrates academic integrity, and
conforms exactly to APA style conventions.
DI: Very good referencing, including reference list and citations.
High quality references.
CR: Good referencing, including reference list and citations. Good quality
references.
PS: Referencing is comprehensive, mostly accurate according to APA
style conventions, and demonstrates academic integrity. Some minor
errors or omissions in style and formatting choices (e.g. italics,
punctuation, etc) don’t impact on the transparency and traceability of the
source, or demonstration of academic integrity.
FL: Sub-standard (or no) referencing. Poor quality (or no) references.
Total
Marks
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Title of you case study/scenario
Q1. What's going on?
The main issue, which is seen in the scenario, is that a software would be delivered
without any encryption process involved into it. This is mainly taking place due to the factor
that the software would be delivered to the client before the actual delivery date. The
suggestion has mainly come from the project manager to the project director. The project
manager suggests the project director that the software would be delivered to the client and
on a later phase a software update would be implemented which would provide the necessary
security of the system. it should be taken into consideration that the delivery of a project
without proper security aspects can have some serious impact on the overall working of the
software.
Q2. What are the facts?
The aspect of security or in this case the concept of encryption can be considered to a
vital part in the working of any organization. The main facts relating to the concept is that a
system without proper encryption can make the software very much vulnerable to attacks. In
major cases, the encryption process play a vital role in the security, which safeguards the data
of the organization, which is put into its working. Another factor, which is seen in the
scenario, is that the project manager had given the project director a suggestion that there
would be a bonus given to the team if the delivery of the project is done before the actual
time of the delivery.
Q3. What are the issues?
The main issue, which is faced, is that a project without proper encryption process
involved into it can hamper the overall working of the project. The event of hacking can be
involved into the system, which would make the system vulnerable. In case the software is,
Your Name
Q1. What's going on?
The main issue, which is seen in the scenario, is that a software would be delivered
without any encryption process involved into it. This is mainly taking place due to the factor
that the software would be delivered to the client before the actual delivery date. The
suggestion has mainly come from the project manager to the project director. The project
manager suggests the project director that the software would be delivered to the client and
on a later phase a software update would be implemented which would provide the necessary
security of the system. it should be taken into consideration that the delivery of a project
without proper security aspects can have some serious impact on the overall working of the
software.
Q2. What are the facts?
The aspect of security or in this case the concept of encryption can be considered to a
vital part in the working of any organization. The main facts relating to the concept is that a
system without proper encryption can make the software very much vulnerable to attacks. In
major cases, the encryption process play a vital role in the security, which safeguards the data
of the organization, which is put into its working. Another factor, which is seen in the
scenario, is that the project manager had given the project director a suggestion that there
would be a bonus given to the team if the delivery of the project is done before the actual
time of the delivery.
Q3. What are the issues?
The main issue, which is faced, is that a project without proper encryption process
involved into it can hamper the overall working of the project. The event of hacking can be
involved into the system, which would make the system vulnerable. In case the software is,
Your Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Title of you case study/scenario
hacked vital information of the organization can be leaked which could affect the overall
working of the organization. On the other hand, it can be stated that if the software is
delivered to the client before the actual date if delivery a bonus would be given to the team.
The suggestion which was put forward to deliver a security patch later on can be sometimes
considered to be issue as it may alter the working of the overall software.
Q4. Who is affected?
The sector, which would be affected by this event, would be the organization who
would be involved in the implementation of the project. Mainly the security aspects would be
affected in case the encryption is not involved into the system. Sometimes this type of
security issue can be devastating for the organization as it could leak all the data, which is
stored in the software. It can be stated here that if the delivery of the project were done
without any proper encryption both the sector i.e. the client as well as the developers would
be affected equally.
Q5. What are the ethical issues and their implications?
The main ethical issue, which is faced, is, that if a software is delivered is delivered to
the client without any proper encryption it would directly affect the software. The effect of
the software can be in a form that if a hacker hacks into the software the data of the software
could be at a stack. The factor of bonus can be considered to be another ethical issue. This is
due to the factor that if the software were delivered to the client, the client would have an
expectation to have a complete system with all the necessary requirements involved into it.
The aspect of delivering a software update later on with all the necessary details of the
security can have some issue relating to the compatibility with the system and overall
working of the system with the security patches. The implication can sometimes be seen after
a long period and not instantly after the implementation of the software.
Your Name
hacked vital information of the organization can be leaked which could affect the overall
working of the organization. On the other hand, it can be stated that if the software is
delivered to the client before the actual date if delivery a bonus would be given to the team.
The suggestion which was put forward to deliver a security patch later on can be sometimes
considered to be issue as it may alter the working of the overall software.
Q4. Who is affected?
The sector, which would be affected by this event, would be the organization who
would be involved in the implementation of the project. Mainly the security aspects would be
affected in case the encryption is not involved into the system. Sometimes this type of
security issue can be devastating for the organization as it could leak all the data, which is
stored in the software. It can be stated here that if the delivery of the project were done
without any proper encryption both the sector i.e. the client as well as the developers would
be affected equally.
Q5. What are the ethical issues and their implications?
The main ethical issue, which is faced, is, that if a software is delivered is delivered to
the client without any proper encryption it would directly affect the software. The effect of
the software can be in a form that if a hacker hacks into the software the data of the software
could be at a stack. The factor of bonus can be considered to be another ethical issue. This is
due to the factor that if the software were delivered to the client, the client would have an
expectation to have a complete system with all the necessary requirements involved into it.
The aspect of delivering a software update later on with all the necessary details of the
security can have some issue relating to the compatibility with the system and overall
working of the system with the security patches. The implication can sometimes be seen after
a long period and not instantly after the implementation of the software.
Your Name

Title of you case study/scenario
Q6. What could have been done about it?
The main thing, which could have been done, is that the delivery of the project could
have been extended. This would directly help the system to gain the encryption process so
that any type of security issue would not be faced in the system. If ones the software is
delivered to the client and any type of security issues are faced it would directly affect the
reputation of the organization. If the security of the software is breached it would directly
affect the overall working of the organization and hamper the reputation of the developers
who basically build the software.
Q7. What are the options?
There can be different types of option available in this type of scenarios. According to
the statement, which are provided the options which are valuable are program director
surrenders to the pressure, project director ignores the recommendation of the project
manager and project director listens to the team. The options are mainly delivered from the
side of the project manager and the project director would take up the main discussion. The
project director is responsible for the overall working of the project and in this scenario; he
would take up the main discussion.
Q8. Which option is the best and why?
In this context, it can be stated that the most important sector, which should be
involved in any type of software, is the security of the software. One’s a software is delivered
to the client and it is implemented it would be a serious problem if the software is hacked.
According to the options which are stated the best option would be to ignore the suggestion
of the project manager. If the time to deliver the complete project would be more, it should be
ensured that the security aspects are dealt with the project. The concept of providing a
Your Name
Q6. What could have been done about it?
The main thing, which could have been done, is that the delivery of the project could
have been extended. This would directly help the system to gain the encryption process so
that any type of security issue would not be faced in the system. If ones the software is
delivered to the client and any type of security issues are faced it would directly affect the
reputation of the organization. If the security of the software is breached it would directly
affect the overall working of the organization and hamper the reputation of the developers
who basically build the software.
Q7. What are the options?
There can be different types of option available in this type of scenarios. According to
the statement, which are provided the options which are valuable are program director
surrenders to the pressure, project director ignores the recommendation of the project
manager and project director listens to the team. The options are mainly delivered from the
side of the project manager and the project director would take up the main discussion. The
project director is responsible for the overall working of the project and in this scenario; he
would take up the main discussion.
Q8. Which option is the best and why?
In this context, it can be stated that the most important sector, which should be
involved in any type of software, is the security of the software. One’s a software is delivered
to the client and it is implemented it would be a serious problem if the software is hacked.
According to the options which are stated the best option would be to ignore the suggestion
of the project manager. If the time to deliver the complete project would be more, it should be
ensured that the security aspects are dealt with the project. The concept of providing a
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Title of you case study/scenario
security patch later could be a problem this is due to the factor that the issue relating to the
compatibility can be seen in some cases.
Your Name
security patch later could be a problem this is due to the factor that the issue relating to the
compatibility can be seen in some cases.
Your Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Title of you case study/scenario
Bibliography
Aslett, L. J., Esperança, P. M., & Holmes, C. C. (2015). A review of homomorphic
encryption and software tools for encrypted statistical machine learning. arXiv
preprint arXiv:1508.06574.
Cabaj, K., & Mazurczyk, W. (2016). Using software-defined networking for ransomware
mitigation: the case of cryptowall. IEEE Network, 30(6), 14-20.
Piessens, F., & Verbauwhede, I. (2016, March). Software security: Vulnerabilities and
countermeasures for two attacker models. In Proceedings of the 2016 Conference on
Design, Automation & Test in Europe (pp. 990-999). EDA Consortium.
Ramachandran, M. (2016). Software security requirements management as an emerging
cloud computing service. International Journal of Information Management, 36(4),
580-590.
Sinn, R. (2015). Software security technologies. Cengage Learning.
Sultana, K. Z., Deo, A., & Williams, B. J. (2016, June). A preliminary study examining
relationships between nano-patterns and software security vulnerabilities. In
Computer Software and Applications Conference (COMPSAC), 2016 IEEE 40th
Annual (Vol. 1, pp. 257-262). IEEE.
Tetmeyer, A., Hein, D., & Saiedian, H. (2014). A tagging approach to extract security
requirements in non-traditional software development processes. International
Journal of Secure Software Engineering (IJSSE), 5(4), 31-47.
Your Name
Bibliography
Aslett, L. J., Esperança, P. M., & Holmes, C. C. (2015). A review of homomorphic
encryption and software tools for encrypted statistical machine learning. arXiv
preprint arXiv:1508.06574.
Cabaj, K., & Mazurczyk, W. (2016). Using software-defined networking for ransomware
mitigation: the case of cryptowall. IEEE Network, 30(6), 14-20.
Piessens, F., & Verbauwhede, I. (2016, March). Software security: Vulnerabilities and
countermeasures for two attacker models. In Proceedings of the 2016 Conference on
Design, Automation & Test in Europe (pp. 990-999). EDA Consortium.
Ramachandran, M. (2016). Software security requirements management as an emerging
cloud computing service. International Journal of Information Management, 36(4),
580-590.
Sinn, R. (2015). Software security technologies. Cengage Learning.
Sultana, K. Z., Deo, A., & Williams, B. J. (2016, June). A preliminary study examining
relationships between nano-patterns and software security vulnerabilities. In
Computer Software and Applications Conference (COMPSAC), 2016 IEEE 40th
Annual (Vol. 1, pp. 257-262). IEEE.
Tetmeyer, A., Hein, D., & Saiedian, H. (2014). A tagging approach to extract security
requirements in non-traditional software development processes. International
Journal of Secure Software Engineering (IJSSE), 5(4), 31-47.
Your Name

Title of you case study/scenario
Your Name
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





