Ethical Dilemmas in Cybersecurity: A Three-Perspective Analysis
VerifiedAdded on 2023/06/15
|10
|2768
|284
Essay
AI Summary
This essay explores the ethical dilemmas faced in cybersecurity by analyzing the perspectives of professional ethics, philosophical ethics, and sociological ethics. It uses the article “An ethical dilemma: operating front line of cyber security” as a basis, focusing on the challenges faced by both white hat and black hat hackers. The professional ethics perspective discusses honesty, quality of life improvement, community interest, professional growth, and professionalism in ethical hacking. The philosophical ethics perspective covers the theory of consequences, deontological perspective, virtue ethics perspective, and social contract theory. Finally, the sociological/descriptive ethics perspective uses value theory to analyze the social implications of hacking. The essay concludes by highlighting the conflicting perspectives that arise when considering hacking under the social value theory.

SCHOOL OF COMPUTING AND MATHS, Charles Sturt University
An ethical dilemma: operating from the frontline of cyber security
Assignment 1: Three Distinct Perspectives of Applied Ethics
Your Name
Student Number
Word Count: 1453
An ethical dilemma: operating from the frontline of cyber security
Assignment 1: Three Distinct Perspectives of Applied Ethics
Your Name
Student Number
Word Count: 1453
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

An ethical dilemma: operating from the frontline of cyber security
Introduction
Business ethical issues are embraced within all organization whether small or big and it is
not just a fad with the limited time period. In this context, the article “An ethical dilemma:
operating front line of cyber security” focuses on the ethical issues faced by the white hat
hackers and black hat hackers. Most of the hackers are being judged in accordance to their
work even if they are doing it for the well-being of the community and organisation (Pyper,
2017). In this aspect, the news article shows that in the Australian organization cyber security
has turned into a major issue of ethical dilemma where hackers are beginning to suffer from
an image problem. They are most of the time perceived as a group anti-social nerds hiding
away from the reality of present time hackers. On the other hand, it can be said that hackers
nowadays are more organized, and criminal assumptions are not always true. This is the
moral dilemma that is hovering over Australian organization related ICT operations.
1. Professional Ethics Perspectives
From the perspectives of ethical hackers, it can be seen that there are a group of black hat
hackers who are popularly signified as criminals. From the article it is evident that, these
hackers are those who manipulate data, dominating the mainstream bunch of hackers thereby
highlighting their ethical counterparts (Thomas, Burmeister & Low, 2017). On the contrary,
white hat hackers are those who use their technical knowledge to breach the technical issue
for mitigating the vulnerabilities present in cyber security issues other than exploiting them
(Pyper, 2017). According to the professional perspectives of ethics, there is six major
principle that is associated with they are honesty, improvement of the quality of life,
competencies, priority for the communities interest, professional growth and professionalism.
Honesty
Ethical hackers or white hat hacker's shares the same method of hacking but for an
honest purpose whereas the black hats perform the test to bypass the defence operations.
Your Name
Introduction
Business ethical issues are embraced within all organization whether small or big and it is
not just a fad with the limited time period. In this context, the article “An ethical dilemma:
operating front line of cyber security” focuses on the ethical issues faced by the white hat
hackers and black hat hackers. Most of the hackers are being judged in accordance to their
work even if they are doing it for the well-being of the community and organisation (Pyper,
2017). In this aspect, the news article shows that in the Australian organization cyber security
has turned into a major issue of ethical dilemma where hackers are beginning to suffer from
an image problem. They are most of the time perceived as a group anti-social nerds hiding
away from the reality of present time hackers. On the other hand, it can be said that hackers
nowadays are more organized, and criminal assumptions are not always true. This is the
moral dilemma that is hovering over Australian organization related ICT operations.
1. Professional Ethics Perspectives
From the perspectives of ethical hackers, it can be seen that there are a group of black hat
hackers who are popularly signified as criminals. From the article it is evident that, these
hackers are those who manipulate data, dominating the mainstream bunch of hackers thereby
highlighting their ethical counterparts (Thomas, Burmeister & Low, 2017). On the contrary,
white hat hackers are those who use their technical knowledge to breach the technical issue
for mitigating the vulnerabilities present in cyber security issues other than exploiting them
(Pyper, 2017). According to the professional perspectives of ethics, there is six major
principle that is associated with they are honesty, improvement of the quality of life,
competencies, priority for the communities interest, professional growth and professionalism.
Honesty
Ethical hackers or white hat hacker's shares the same method of hacking but for an
honest purpose whereas the black hats perform the test to bypass the defence operations.
Your Name

An ethical dilemma: operating from the frontline of cyber security
Ethical hackers, other than taking any benefits of the vulnerabilities they document the issues,
offer advice to fix the issues (Lunnay, 2015). These kinds of problems are often seen in ICT
operation owing from the improper configuration of system or flaws present within the
software.
Improvement of quality of life
Ethical hackers do not always perform it in the same way. They may have contrasted
motivation and way of hacking. There are some of the hackers who prefer to work for the
greater good for improving the quality standards of life and to seek professional growth. On
the contrary, some of the hackers are directly employed by the organizations on a
professional call (Caron et al., 2016). Many organization hire hackers to solve bug bounties,
where employees are paid to find out the vulnerabilities within the organizational system that
are growing in the United States as well as Australian organization. In this aspect, private bug
bounties offer the professional hackers to examine their skills for even more virtuous
opportunities.
Priority for the community’s interest
White hat hackers are accountable for reviewing the vulnerabilities present in the
software that are done in priority to save the community (Haug, 2015). There are several
instances when the government appoints the hackers to perform a task to save the community
from big issues such as terrorism or financial fraud case. These hackers are that point of the
time appointed to perform the task on behalf of the government to save the community.
Professional growth
Professional hackers are consistently seeking for a growth in an ethical activity to
work on a freelance basis, and are looking for a permanent career in this field. In order to
gain professional development, some of the hackers are officially gaining qualification to
evaluate their capability (Ferguson, Thornley & Gibb, 2015). There are also some training
Your Name
Ethical hackers, other than taking any benefits of the vulnerabilities they document the issues,
offer advice to fix the issues (Lunnay, 2015). These kinds of problems are often seen in ICT
operation owing from the improper configuration of system or flaws present within the
software.
Improvement of quality of life
Ethical hackers do not always perform it in the same way. They may have contrasted
motivation and way of hacking. There are some of the hackers who prefer to work for the
greater good for improving the quality standards of life and to seek professional growth. On
the contrary, some of the hackers are directly employed by the organizations on a
professional call (Caron et al., 2016). Many organization hire hackers to solve bug bounties,
where employees are paid to find out the vulnerabilities within the organizational system that
are growing in the United States as well as Australian organization. In this aspect, private bug
bounties offer the professional hackers to examine their skills for even more virtuous
opportunities.
Priority for the community’s interest
White hat hackers are accountable for reviewing the vulnerabilities present in the
software that are done in priority to save the community (Haug, 2015). There are several
instances when the government appoints the hackers to perform a task to save the community
from big issues such as terrorism or financial fraud case. These hackers are that point of the
time appointed to perform the task on behalf of the government to save the community.
Professional growth
Professional hackers are consistently seeking for a growth in an ethical activity to
work on a freelance basis, and are looking for a permanent career in this field. In order to
gain professional development, some of the hackers are officially gaining qualification to
evaluate their capability (Ferguson, Thornley & Gibb, 2015). There are also some training
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

An ethical dilemma: operating from the frontline of cyber security
courses that offer training to them available from many institutions like EC council. These
institutions are delivering a registered certificate for certified ethical hacker’s professional
skills within the competitive industry. In the current scenario, the professional certificate of
hacking is a very useful business while demonstrating the reliability and skills of the hacker
that is crucial for professional development (Sargolzaei & Nikbakht, 2017).
Professionalism
Professional ethical hackers are aware of the skills so they use it to ensure that relevant
patches are applied to the defected software system in a timely manner. For instance, a
current study by bit slight on Windows observed that the operating system was running at
20% among the 35,000 systems (Joppova, 2018). In this context, Microsoft discontinued the
use of patches for XP year ago, therefore, any device that is running on these operating
system may be threating due to external hacking. Thus, ethical hackers use professionalism
to manage these vulnerable issues.
2. Philosophical Ethics Perspectives
Theory of consequences
According to these ethical models, an act that is done for the positive outcome is
advantageous and acceptable from an ethical perspective. Again, in terms of negative
outcome for any of the involved individual the case may be termed as an unethical act (Stahl,
Timmermans & Flick, 2016).
In case of hacking when a hacker is performing hacking to protect a business, they are
expected to understand the organizational process in depth for the wellbeing of the company.
An ethical according to the theory of consequences are aware of the truth and therefore, the
consequences are expected to be positive here. To deal with the questions of ethical
consequences professionals associations like association for computing machines have
Your Name
courses that offer training to them available from many institutions like EC council. These
institutions are delivering a registered certificate for certified ethical hacker’s professional
skills within the competitive industry. In the current scenario, the professional certificate of
hacking is a very useful business while demonstrating the reliability and skills of the hacker
that is crucial for professional development (Sargolzaei & Nikbakht, 2017).
Professionalism
Professional ethical hackers are aware of the skills so they use it to ensure that relevant
patches are applied to the defected software system in a timely manner. For instance, a
current study by bit slight on Windows observed that the operating system was running at
20% among the 35,000 systems (Joppova, 2018). In this context, Microsoft discontinued the
use of patches for XP year ago, therefore, any device that is running on these operating
system may be threating due to external hacking. Thus, ethical hackers use professionalism
to manage these vulnerable issues.
2. Philosophical Ethics Perspectives
Theory of consequences
According to these ethical models, an act that is done for the positive outcome is
advantageous and acceptable from an ethical perspective. Again, in terms of negative
outcome for any of the involved individual the case may be termed as an unethical act (Stahl,
Timmermans & Flick, 2016).
In case of hacking when a hacker is performing hacking to protect a business, they are
expected to understand the organizational process in depth for the wellbeing of the company.
An ethical according to the theory of consequences are aware of the truth and therefore, the
consequences are expected to be positive here. To deal with the questions of ethical
consequences professionals associations like association for computing machines have
Your Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

An ethical dilemma: operating from the frontline of cyber security
founded their own code of ethics and professional behaviour that can help to serve as a
principle for the hackers and other organizations (Joppova, 2018).
Deontological perspective
According to the deontological perspective of ethics, every activity that has been
performed under a certain set of rules and principles are needed to be followed. The
significance here associated with the professional ICT organizational that deals with software
vulnerabilities. To be specific, operations such as web related financial issues often have
some certain professional code of conduct that needs to be followed by the hackers and the
employees for security issues (Curren, 2016). These perspectives of ethical judge's action
without hacking considered the consequences of action. It asserts that every individual has a
duty to do the rightful thing, even if the individual performs for well-being it will be assumed
as morally incorrect. Therefore, according to the theory of Kant, duty is what that is being
counted; hacking into another system to conquer knowledge of the software even if no
damage is done it will be considered as the wrong commitment of a crime.
Virtue ethics perspective
This specific perspective judges a situation or an individual on the basic values of the
individual. In this context, if the virtues are positive the act will be considered as ethical and
vice versa (Sargolzaei & Nikbakht, 2017). Therefore, in the case of hacking and considering
the current security issues in the different organization, it can be said that hacking is ethical if
it is performed for the wellbeing of the community and organization. Hackers have a legal
right to access encrypted data to recover or fix the vulnerabilities.
Social contract theory
Social contract theory asserts that the activities those are performed unethically or
ethically needs to be in the interest of other happiness as well as social wellbeing. These
should support the wellbeing of the society (Haug, 2015). However, in the case of hacking it
Your Name
founded their own code of ethics and professional behaviour that can help to serve as a
principle for the hackers and other organizations (Joppova, 2018).
Deontological perspective
According to the deontological perspective of ethics, every activity that has been
performed under a certain set of rules and principles are needed to be followed. The
significance here associated with the professional ICT organizational that deals with software
vulnerabilities. To be specific, operations such as web related financial issues often have
some certain professional code of conduct that needs to be followed by the hackers and the
employees for security issues (Curren, 2016). These perspectives of ethical judge's action
without hacking considered the consequences of action. It asserts that every individual has a
duty to do the rightful thing, even if the individual performs for well-being it will be assumed
as morally incorrect. Therefore, according to the theory of Kant, duty is what that is being
counted; hacking into another system to conquer knowledge of the software even if no
damage is done it will be considered as the wrong commitment of a crime.
Virtue ethics perspective
This specific perspective judges a situation or an individual on the basic values of the
individual. In this context, if the virtues are positive the act will be considered as ethical and
vice versa (Sargolzaei & Nikbakht, 2017). Therefore, in the case of hacking and considering
the current security issues in the different organization, it can be said that hacking is ethical if
it is performed for the wellbeing of the community and organization. Hackers have a legal
right to access encrypted data to recover or fix the vulnerabilities.
Social contract theory
Social contract theory asserts that the activities those are performed unethically or
ethically needs to be in the interest of other happiness as well as social wellbeing. These
should support the wellbeing of the society (Haug, 2015). However, in the case of hacking it
Your Name

An ethical dilemma: operating from the frontline of cyber security
has been seen that hackers are often assigned to provide financial security to organizational
while maintaining the confidentiality and security of the employees.
3. Sociological/Descriptive Ethics Perspectives
Value theory is one of the most important theories that can be implemented to gain social
and descriptive consequences of the situation. In this aspect, the theory uses several
approaches to determining the reason behind taking the decision, to identify the degree based
on individual values and things. In this context, the relationship is one of the fundamental
developing blocks of life that gives rise to strong emotions such as love, hatred jealousy as
well as happiness (Sargolzaei & Nikbakht, 2017). On the contrary, the mainstream culture
may disrespect this opinion as it is the rational outcome of love. In a nutshell, the value
theory asserts the recognizing values one expects to have from a relationship based on the
expectation from life (Thomas, Burmeister & Low, 2017). These values might be testable
when one can attempt to subjectively judge an individual to check the reality.
Considering these implications, some instances can be related when an individual in love
try to hack their other partners account for checking if that individual is dating someone else.
It may be justified but morally wrong where the individual has taken emotions placing over
rational thought. Again it has been seen that individual to check their rival company details
use hacking. These too can be rationally immoral, because the individual is performing this
act out of the sense of jealousy. Therefore, hacking here shows conflicting perspectives under
the social value theory.
Your Name
has been seen that hackers are often assigned to provide financial security to organizational
while maintaining the confidentiality and security of the employees.
3. Sociological/Descriptive Ethics Perspectives
Value theory is one of the most important theories that can be implemented to gain social
and descriptive consequences of the situation. In this aspect, the theory uses several
approaches to determining the reason behind taking the decision, to identify the degree based
on individual values and things. In this context, the relationship is one of the fundamental
developing blocks of life that gives rise to strong emotions such as love, hatred jealousy as
well as happiness (Sargolzaei & Nikbakht, 2017). On the contrary, the mainstream culture
may disrespect this opinion as it is the rational outcome of love. In a nutshell, the value
theory asserts the recognizing values one expects to have from a relationship based on the
expectation from life (Thomas, Burmeister & Low, 2017). These values might be testable
when one can attempt to subjectively judge an individual to check the reality.
Considering these implications, some instances can be related when an individual in love
try to hack their other partners account for checking if that individual is dating someone else.
It may be justified but morally wrong where the individual has taken emotions placing over
rational thought. Again it has been seen that individual to check their rival company details
use hacking. These too can be rationally immoral, because the individual is performing this
act out of the sense of jealousy. Therefore, hacking here shows conflicting perspectives under
the social value theory.
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

An ethical dilemma: operating from the frontline of cyber security
Reference list
Caron, X., Bosua, R., Maynard, S. B., & Ahmad, A. (2016). The Internet of Things (IoT) and
its impact on individual privacy: An Australian perspective. Computer law & security
review, 32(1), 4-15.
Curren, R. (2016). Aristotelian versus virtue ethical character education. Journal Of Moral
Education, 45(4), 516-526. doi: 10.1080/03057240.2016.1238820
Ferguson, S., Thornley, C., & Gibb, F. (2015). How do libraries manage the ethical and
privacy issues of RFID implementation? A qualitative investigation into the decision-
making processes of ten libraries. Journal of Librarianship and Information Science,
47(2), 117-130.
Haug, C. J. (2015). Peer-review fraud—hacking the scientific publication process. New
England Journal of Medicine, 373(25), 2393-2395.
Joppova, M. (2018). Spinozian consequentialism of ethics of social consequences. Ethics &
Bioethics, 8(1-2), 41-50. doi: 10.2478/ebce-2018-0008
Lunney, B., Borlagdan, J., McNaughton, D., & Ward, P. (2015). Ethical use of social media
to facilitate qualitative research. Qualitative Health Research, 25(1), 99-109.
Pyper, G., (31 Oct 2017). An ethical dilemma: operating from the frontline of cybersecurity.
CSO Australia (online). Retrieved on 3 August 2018. Retrieved from
https://www.cso.com.au/article/629349/an-ethical-dilemma-operating-from-frontline-
cybersecurity/
Sargolzaei, E., & Nikbakht, M. (2017). The Ethical and Social Issues of Information
Technology: A Case Study. International journal of advanced computer science and
applications, 8(10), 138-146.
Your Name
Reference list
Caron, X., Bosua, R., Maynard, S. B., & Ahmad, A. (2016). The Internet of Things (IoT) and
its impact on individual privacy: An Australian perspective. Computer law & security
review, 32(1), 4-15.
Curren, R. (2016). Aristotelian versus virtue ethical character education. Journal Of Moral
Education, 45(4), 516-526. doi: 10.1080/03057240.2016.1238820
Ferguson, S., Thornley, C., & Gibb, F. (2015). How do libraries manage the ethical and
privacy issues of RFID implementation? A qualitative investigation into the decision-
making processes of ten libraries. Journal of Librarianship and Information Science,
47(2), 117-130.
Haug, C. J. (2015). Peer-review fraud—hacking the scientific publication process. New
England Journal of Medicine, 373(25), 2393-2395.
Joppova, M. (2018). Spinozian consequentialism of ethics of social consequences. Ethics &
Bioethics, 8(1-2), 41-50. doi: 10.2478/ebce-2018-0008
Lunney, B., Borlagdan, J., McNaughton, D., & Ward, P. (2015). Ethical use of social media
to facilitate qualitative research. Qualitative Health Research, 25(1), 99-109.
Pyper, G., (31 Oct 2017). An ethical dilemma: operating from the frontline of cybersecurity.
CSO Australia (online). Retrieved on 3 August 2018. Retrieved from
https://www.cso.com.au/article/629349/an-ethical-dilemma-operating-from-frontline-
cybersecurity/
Sargolzaei, E., & Nikbakht, M. (2017). The Ethical and Social Issues of Information
Technology: A Case Study. International journal of advanced computer science and
applications, 8(10), 138-146.
Your Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

An ethical dilemma: operating from the frontline of cyber security
Stahl, B., Timmermans, J., & Flick, C. (2016). Ethics of Emerging Information and
Communication Technologies. Science And Public Policy, scw069. doi:
10.1093/scipol/scw069
Thomas, G., Burmeister, O. K., & Low, G. (2017). Issues of Implied Trust in Ethical
Hacking. In Proceedings of The 28th Australasian Conference on Information
Systems, December (pp. 4-6).
Your Name
Stahl, B., Timmermans, J., & Flick, C. (2016). Ethics of Emerging Information and
Communication Technologies. Science And Public Policy, scw069. doi:
10.1093/scipol/scw069
Thomas, G., Burmeister, O. K., & Low, G. (2017). Issues of Implied Trust in Ethical
Hacking. In Proceedings of The 28th Australasian Conference on Information
Systems, December (pp. 4-6).
Your Name
An ethical dilemma: operating from the frontline of cyber security
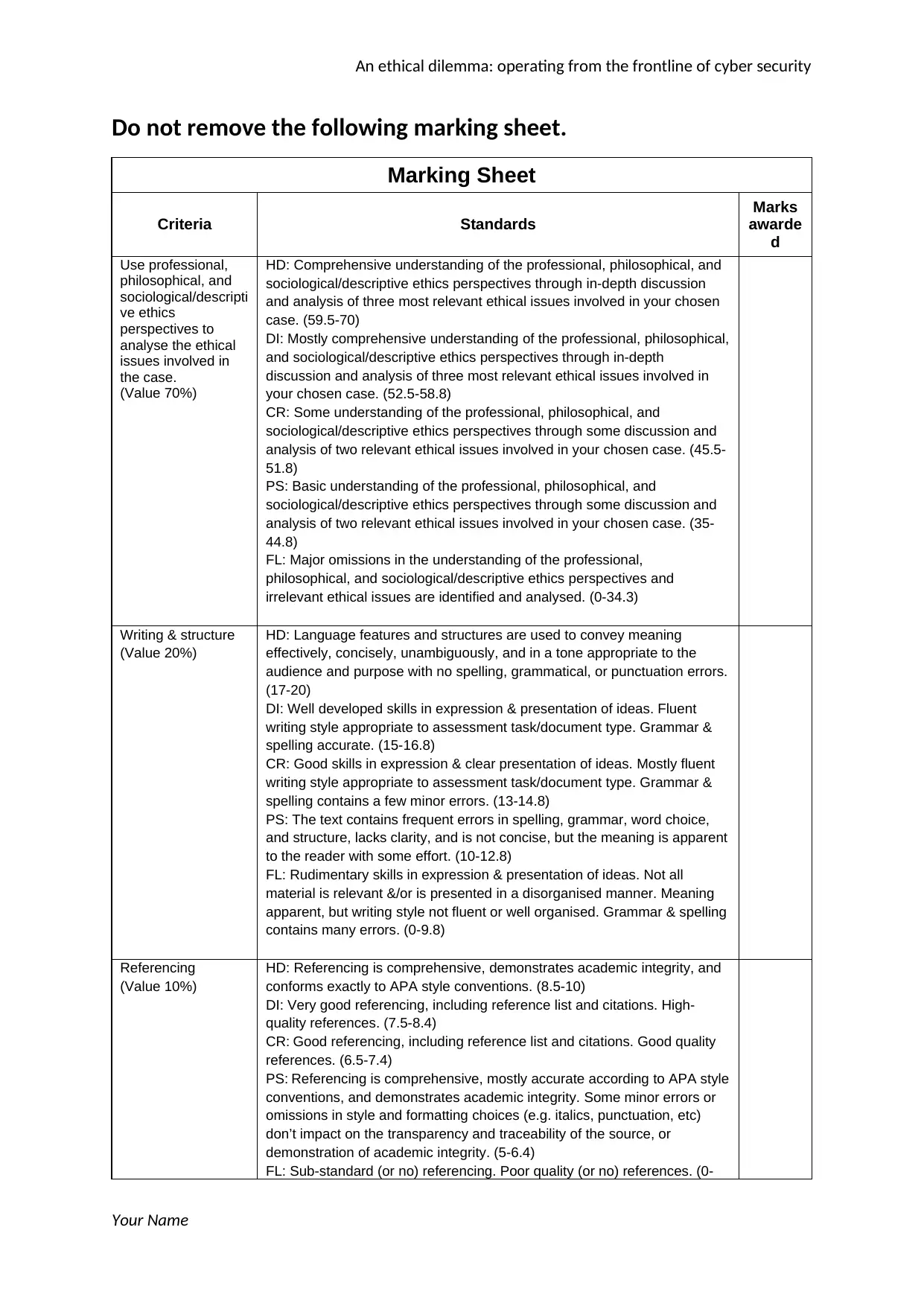
Do not remove the following marking sheet.
Marking Sheet
Criteria Standards
Marks
awarde
d
Use professional,
philosophical, and
sociological/descripti
ve ethics
perspectives to
analyse the ethical
issues involved in
the case.
(Value 70%)
HD: Comprehensive understanding of the professional, philosophical, and
sociological/descriptive ethics perspectives through in-depth discussion
and analysis of three most relevant ethical issues involved in your chosen
case. (59.5-70)
DI: Mostly comprehensive understanding of the professional, philosophical,
and sociological/descriptive ethics perspectives through in-depth
discussion and analysis of three most relevant ethical issues involved in
your chosen case. (52.5-58.8)
CR: Some understanding of the professional, philosophical, and
sociological/descriptive ethics perspectives through some discussion and
analysis of two relevant ethical issues involved in your chosen case. (45.5-
51.8)
PS: Basic understanding of the professional, philosophical, and
sociological/descriptive ethics perspectives through some discussion and
analysis of two relevant ethical issues involved in your chosen case. (35-
44.8)
FL: Major omissions in the understanding of the professional,
philosophical, and sociological/descriptive ethics perspectives and
irrelevant ethical issues are identified and analysed. (0-34.3)
Writing & structure
(Value 20%)
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to the
audience and purpose with no spelling, grammatical, or punctuation errors.
(17-20)
DI: Well developed skills in expression & presentation of ideas. Fluent
writing style appropriate to assessment task/document type. Grammar &
spelling accurate. (15-16.8)
CR: Good skills in expression & clear presentation of ideas. Mostly fluent
writing style appropriate to assessment task/document type. Grammar &
spelling contains a few minor errors. (13-14.8)
PS: The text contains frequent errors in spelling, grammar, word choice,
and structure, lacks clarity, and is not concise, but the meaning is apparent
to the reader with some effort. (10-12.8)
FL: Rudimentary skills in expression & presentation of ideas. Not all
material is relevant &/or is presented in a disorganised manner. Meaning
apparent, but writing style not fluent or well organised. Grammar & spelling
contains many errors. (0-9.8)
Referencing
(Value 10%)
HD: Referencing is comprehensive, demonstrates academic integrity, and
conforms exactly to APA style conventions. (8.5-10)
DI: Very good referencing, including reference list and citations. High-
quality references. (7.5-8.4)
CR: Good referencing, including reference list and citations. Good quality
references. (6.5-7.4)
PS: Referencing is comprehensive, mostly accurate according to APA style
conventions, and demonstrates academic integrity. Some minor errors or
omissions in style and formatting choices (e.g. italics, punctuation, etc)
don’t impact on the transparency and traceability of the source, or
demonstration of academic integrity. (5-6.4)
FL: Sub-standard (or no) referencing. Poor quality (or no) references. (0-
Your Name
Do not remove the following marking sheet.
Marking Sheet
Criteria Standards
Marks
awarde
d
Use professional,
philosophical, and
sociological/descripti
ve ethics
perspectives to
analyse the ethical
issues involved in
the case.
(Value 70%)
HD: Comprehensive understanding of the professional, philosophical, and
sociological/descriptive ethics perspectives through in-depth discussion
and analysis of three most relevant ethical issues involved in your chosen
case. (59.5-70)
DI: Mostly comprehensive understanding of the professional, philosophical,
and sociological/descriptive ethics perspectives through in-depth
discussion and analysis of three most relevant ethical issues involved in
your chosen case. (52.5-58.8)
CR: Some understanding of the professional, philosophical, and
sociological/descriptive ethics perspectives through some discussion and
analysis of two relevant ethical issues involved in your chosen case. (45.5-
51.8)
PS: Basic understanding of the professional, philosophical, and
sociological/descriptive ethics perspectives through some discussion and
analysis of two relevant ethical issues involved in your chosen case. (35-
44.8)
FL: Major omissions in the understanding of the professional,
philosophical, and sociological/descriptive ethics perspectives and
irrelevant ethical issues are identified and analysed. (0-34.3)
Writing & structure
(Value 20%)
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to the
audience and purpose with no spelling, grammatical, or punctuation errors.
(17-20)
DI: Well developed skills in expression & presentation of ideas. Fluent
writing style appropriate to assessment task/document type. Grammar &
spelling accurate. (15-16.8)
CR: Good skills in expression & clear presentation of ideas. Mostly fluent
writing style appropriate to assessment task/document type. Grammar &
spelling contains a few minor errors. (13-14.8)
PS: The text contains frequent errors in spelling, grammar, word choice,
and structure, lacks clarity, and is not concise, but the meaning is apparent
to the reader with some effort. (10-12.8)
FL: Rudimentary skills in expression & presentation of ideas. Not all
material is relevant &/or is presented in a disorganised manner. Meaning
apparent, but writing style not fluent or well organised. Grammar & spelling
contains many errors. (0-9.8)
Referencing
(Value 10%)
HD: Referencing is comprehensive, demonstrates academic integrity, and
conforms exactly to APA style conventions. (8.5-10)
DI: Very good referencing, including reference list and citations. High-
quality references. (7.5-8.4)
CR: Good referencing, including reference list and citations. Good quality
references. (6.5-7.4)
PS: Referencing is comprehensive, mostly accurate according to APA style
conventions, and demonstrates academic integrity. Some minor errors or
omissions in style and formatting choices (e.g. italics, punctuation, etc)
don’t impact on the transparency and traceability of the source, or
demonstration of academic integrity. (5-6.4)
FL: Sub-standard (or no) referencing. Poor quality (or no) references. (0-
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
An ethical dilemma: operating from the frontline of cyber security
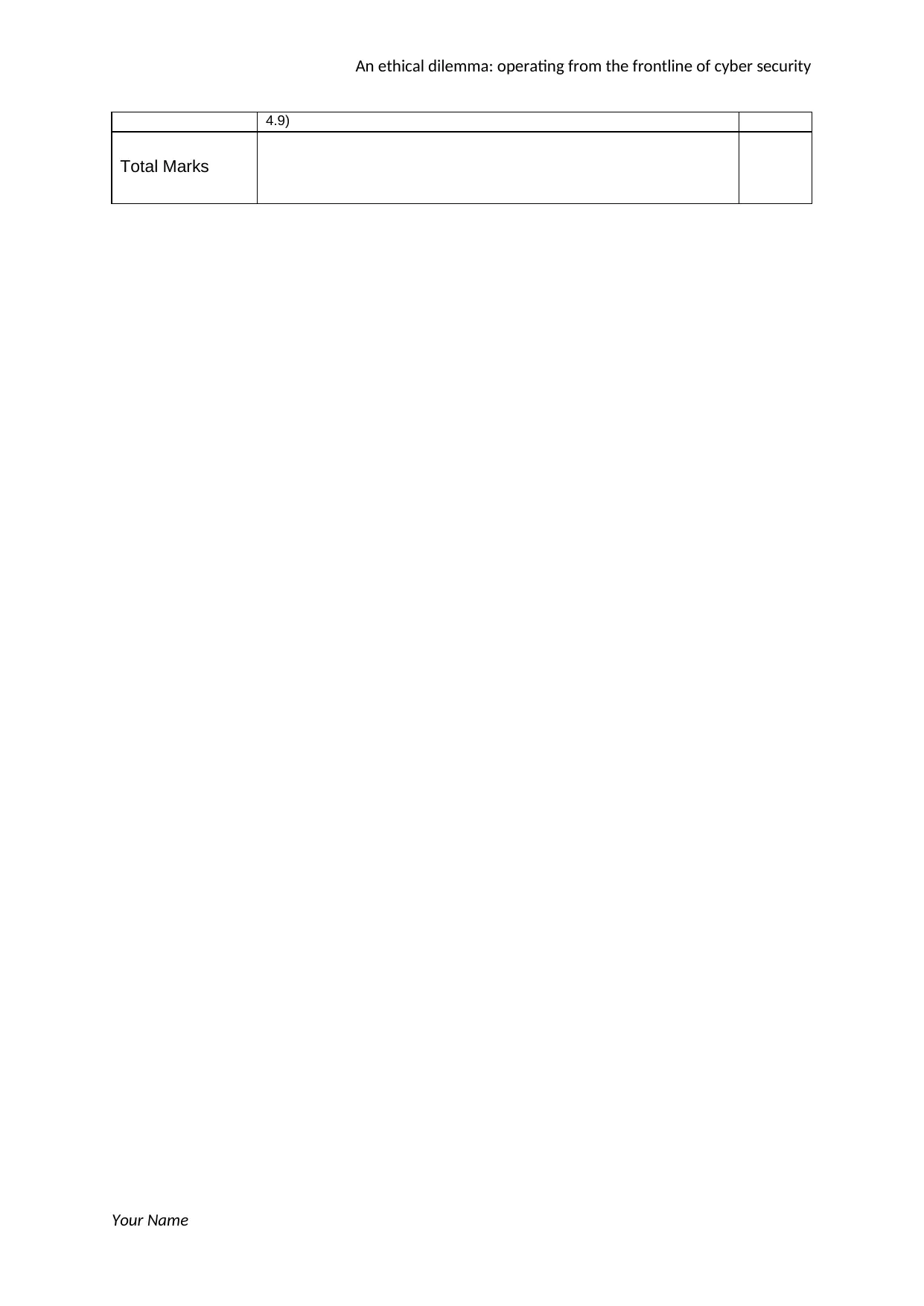
4.9)
Total Marks
Your Name
4.9)
Total Marks
Your Name
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





