Ethical Hacking as a Defense Mechanism: Computer Systems Security
VerifiedAdded on 2023/06/03
|10
|1909
|378
Report
AI Summary
This report provides an overview of cybercrimes and explores ethical hacking as a defense mechanism. It distinguishes between computer-enabled and computer-dependent crimes, highlighting techniques used by cybercriminals such as Denial-of-Service attacks, Fast Flux, botnets, and social engineering. The report discusses real-world examples, including the 2015 bank hack and the WannaCry virus attack on the NHS. It emphasizes the role of ethical hackers in identifying vulnerabilities and improving system security, concluding that ethical hacking is crucial for organizations to protect against evolving cyber threats. Desklib offers a range of study tools and solved assignments to aid students in understanding complex topics like ethical hacking and computer security.

Running head: ETHICAL HACKING AS A DEFENCE MECHANISM
ETHICAL HACKING AS A DEFENCE MECHANISM
Name of the Student
Name of the University
Author Note
ETHICAL HACKING AS A DEFENCE MECHANISM
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ETHICAL HACKING AS A DEFENCE MECHANISM
Table of Contents
1.0 Introduction..........................................................................................................................2
2.0 Cybercrimes:........................................................................................................................3
3.0 Crime cases:.........................................................................................................................4
4.0 Ethical hacking.....................................................................................................................5
5.0 Conclusion:..........................................................................................................................5
6.0 References:...........................................................................................................................7
Table of Contents
1.0 Introduction..........................................................................................................................2
2.0 Cybercrimes:........................................................................................................................3
3.0 Crime cases:.........................................................................................................................4
4.0 Ethical hacking.....................................................................................................................5
5.0 Conclusion:..........................................................................................................................5
6.0 References:...........................................................................................................................7

2ETHICAL HACKING AS A DEFENCE MECHANISM
1.0 Introduction
Computer crime, widely known as cybercrime associated with criminal activities
while utilizing network devices or computers. Majority of the cybercrime is initiated to gain
profit but some of them are designed to damage infected devices or compromise crucial data.
Mostly, cybercrimes are associated with spreading malware and illegal content. Some of the
cybercrimes involved both as Ransom ware attack, where crucial data is encrypted in the
infected system and asks for ransom to access this files. Users need to pay certain amount of
crypto currency in order to gaining access to their files. Cybercrimes can also be
distinguished into two types as computer enabled crime and computer depended crime.
Computer depended crimes are offences which can only be committed while utilizing the
computer devices or network or any application of information technology. This type of
attacks involves spreading of malware, virus and hacking and DoS attacks. On other hand,
computer enabled crimes are traditional crimes which can be improved in their reach or scale
by utilizing computers, computer network or other type of information technology. Unlike
cyber-dependent crimes, they can be committed without the use of ICT. Theft and fraud are
the two widely listed occurrences of cyber enabled crime.
This report describes about the fundamentals of cybercrimes. Cybercrime is a broad
topic which cannot be described fully within such short parameter. So, it is mainly focused on
the different kind of computer crimes. This paper explains what constitutes a crime when
using computers, how computer crimes are committed along with a broad description of
ethical hacking. The discussion is also associates with what Ethical Hacking is, what makes it
a legal activity, and what it actually is about, which is a network defence mechanism. Further,
a conclusion has been drawn from the discussion.
1.0 Introduction
Computer crime, widely known as cybercrime associated with criminal activities
while utilizing network devices or computers. Majority of the cybercrime is initiated to gain
profit but some of them are designed to damage infected devices or compromise crucial data.
Mostly, cybercrimes are associated with spreading malware and illegal content. Some of the
cybercrimes involved both as Ransom ware attack, where crucial data is encrypted in the
infected system and asks for ransom to access this files. Users need to pay certain amount of
crypto currency in order to gaining access to their files. Cybercrimes can also be
distinguished into two types as computer enabled crime and computer depended crime.
Computer depended crimes are offences which can only be committed while utilizing the
computer devices or network or any application of information technology. This type of
attacks involves spreading of malware, virus and hacking and DoS attacks. On other hand,
computer enabled crimes are traditional crimes which can be improved in their reach or scale
by utilizing computers, computer network or other type of information technology. Unlike
cyber-dependent crimes, they can be committed without the use of ICT. Theft and fraud are
the two widely listed occurrences of cyber enabled crime.
This report describes about the fundamentals of cybercrimes. Cybercrime is a broad
topic which cannot be described fully within such short parameter. So, it is mainly focused on
the different kind of computer crimes. This paper explains what constitutes a crime when
using computers, how computer crimes are committed along with a broad description of
ethical hacking. The discussion is also associates with what Ethical Hacking is, what makes it
a legal activity, and what it actually is about, which is a network defence mechanism. Further,
a conclusion has been drawn from the discussion.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ETHICAL HACKING AS A DEFENCE MECHANISM
2.0 Cybercrimes:
Computer crimes can also be describe as a very board category of wrongdoings where
some of the offenses are similar as non-computer wrongdoings such as fraud or larceny.
Other cybercrimes are associates with hacking to compromise crucial information or damage
targeted system (Shetty et al. 2017). This type of crimes includes infiltrate of any
unauthorized system while falsifying email source information, introducing a virus or other
contaminant into a computer system, using a computer in a scheme to defraud, utilizing
encryption in aid of a crime, using interfering with someone else's computer access or use,
copying, modifying, disclosing, using, damaging or taking programs or data and improperly
accessing a computer, system, or network.
Cyber criminals uses several type of techniques to infect the targeted systems. Most
cybercrimes are committed by small groups or individuals. However, large organizations are
also involved with the criminal activities such Anonymous. Anonymous is made up of an
international network of activists who purposely disrupt organizations they believe to be
morally corrupt (Peacock 2013). They are considered very dangerous and anonymous as they
are constantly developing new ways to infiltrate computers or networks while taking
advantages of internet. Criminal communities also share tools and strategies to infiltrate
computers or networks. Different criminal uses several techniques to infiltrate computers,
some of them are following:
Denial-of-Service attacks – This attacks involves flooding a server or network with high
traffic which crashes the system and cannot be used by the users.
2.0 Cybercrimes:
Computer crimes can also be describe as a very board category of wrongdoings where
some of the offenses are similar as non-computer wrongdoings such as fraud or larceny.
Other cybercrimes are associates with hacking to compromise crucial information or damage
targeted system (Shetty et al. 2017). This type of crimes includes infiltrate of any
unauthorized system while falsifying email source information, introducing a virus or other
contaminant into a computer system, using a computer in a scheme to defraud, utilizing
encryption in aid of a crime, using interfering with someone else's computer access or use,
copying, modifying, disclosing, using, damaging or taking programs or data and improperly
accessing a computer, system, or network.
Cyber criminals uses several type of techniques to infect the targeted systems. Most
cybercrimes are committed by small groups or individuals. However, large organizations are
also involved with the criminal activities such Anonymous. Anonymous is made up of an
international network of activists who purposely disrupt organizations they believe to be
morally corrupt (Peacock 2013). They are considered very dangerous and anonymous as they
are constantly developing new ways to infiltrate computers or networks while taking
advantages of internet. Criminal communities also share tools and strategies to infiltrate
computers or networks. Different criminal uses several techniques to infiltrate computers,
some of them are following:
Denial-of-Service attacks – This attacks involves flooding a server or network with high
traffic which crashes the system and cannot be used by the users.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4ETHICAL HACKING AS A DEFENCE MECHANISM
Fast Flux - Moving data quickly among the computers in a botnet to make it difficult to trace
the source of malware or phishing websites.
Zombie Computer - A computer that has been hacked into and is used to launch malicious
attacks or to become part of a botnet.
Botnet - A type of bot which is cable of spreading malware automatically over several
network.
Skimmers - Devices that take credit card information when the card is swiped through them.
After getting the card information of the user, the information sold online through a criminal
community.
Social Engineering – Utilizing manipulation and lies to identify the user’s personal
information.
Fast Flux - Moving data quickly among the computers in a botnet to make it difficult to trace
the source of malware or phishing websites.
Zombie Computer - A computer that has been hacked into and is used to launch malicious
attacks or to become part of a botnet.
Botnet - A type of bot which is cable of spreading malware automatically over several
network.
Skimmers - Devices that take credit card information when the card is swiped through them.
After getting the card information of the user, the information sold online through a criminal
community.
Social Engineering – Utilizing manipulation and lies to identify the user’s personal
information.

5ETHICAL HACKING AS A DEFENCE MECHANISM
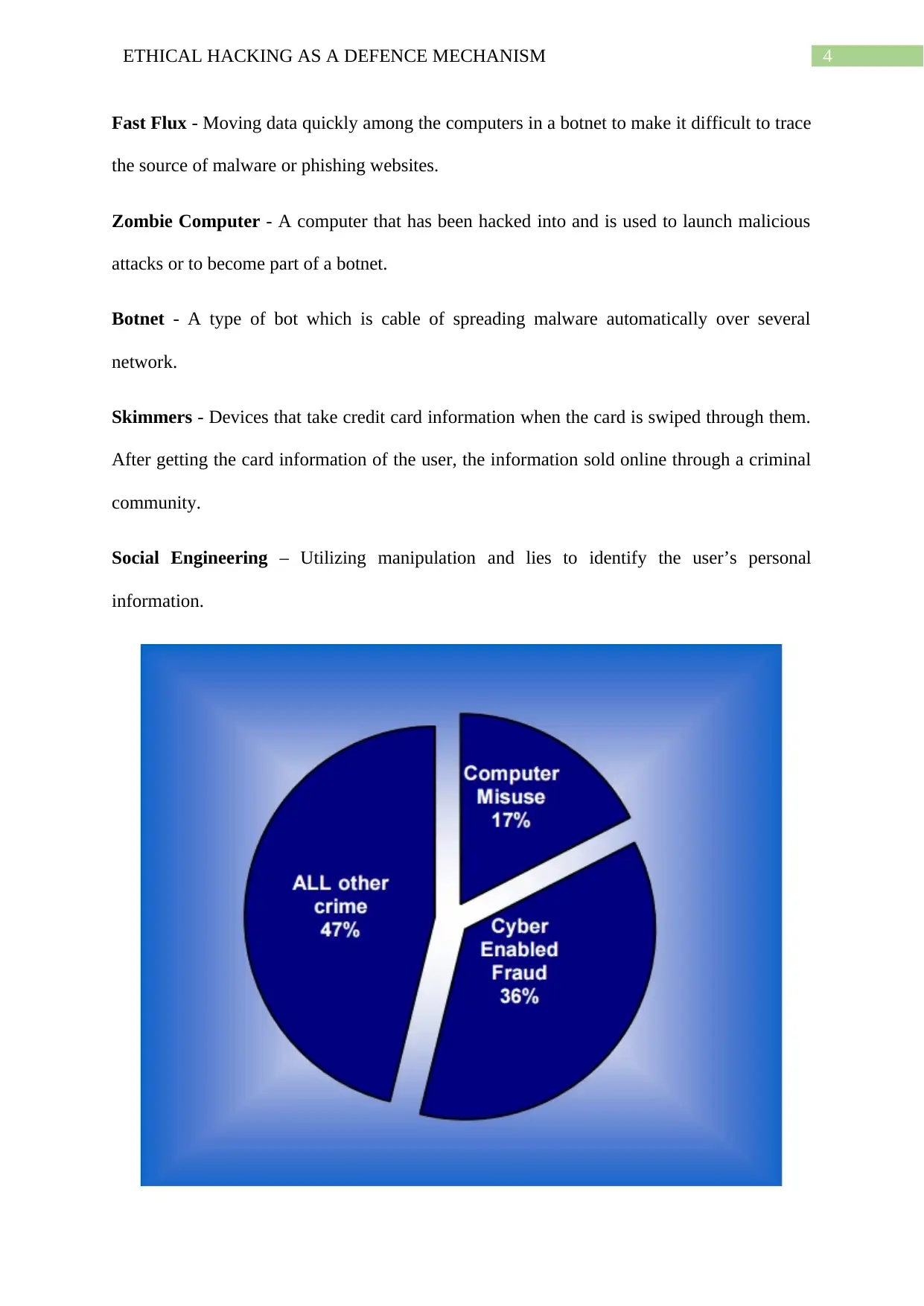
Figure 1: Cyber Crimes as a proportion
Source: (Dayanandam et al. 2013)
Some of the criminal activities are targeted to certain organizations that store people’s
personal information such as credit card companies. However, majority of the cyber threats
target home computers as it is easier to infiltrate (Xu et al. 2014). These computers are
embedded with basic security measurement such as firewall and anti-viruses comparing to the
large organization security measurement.
3.0 Crime cases:
Several cybercrimes are noted in the past years some of them are described below.
3.1 Hackers steal £650 million from global banks, 2015
This case was happened in early 2015 when some Russian hackers managed to gain
access to secure information from more than 100 institutions around the world. They utilized
malware to breach such systems in order to gain access over personal information of bank
customers (Lehrfeld and Guest 2016). They uses such information to dispense money from
impersonate online bank staff without authorized cards. They were able to steal almost 650
million euro from the financial institutions in total.
3.2 Wanna cry virus hits NHS, 2017
Recently, Wanna cry virus infiltrate the NHS’s computer system and create chaos
among UK’s medical system. Same virus is used against fedex and infected computers in 150
countries. It spreads through emails. Usually, the exploits are consisted in the mail body or
attachment (Flores 2013). When user lick on such attachments, the virus start spreading
through their systems, encrypts some files and demand money for accessing such files. It has
Figure 1: Cyber Crimes as a proportion
Source: (Dayanandam et al. 2013)
Some of the criminal activities are targeted to certain organizations that store people’s
personal information such as credit card companies. However, majority of the cyber threats
target home computers as it is easier to infiltrate (Xu et al. 2014). These computers are
embedded with basic security measurement such as firewall and anti-viruses comparing to the
large organization security measurement.
3.0 Crime cases:
Several cybercrimes are noted in the past years some of them are described below.
3.1 Hackers steal £650 million from global banks, 2015
This case was happened in early 2015 when some Russian hackers managed to gain
access to secure information from more than 100 institutions around the world. They utilized
malware to breach such systems in order to gain access over personal information of bank
customers (Lehrfeld and Guest 2016). They uses such information to dispense money from
impersonate online bank staff without authorized cards. They were able to steal almost 650
million euro from the financial institutions in total.
3.2 Wanna cry virus hits NHS, 2017
Recently, Wanna cry virus infiltrate the NHS’s computer system and create chaos
among UK’s medical system. Same virus is used against fedex and infected computers in 150
countries. It spreads through emails. Usually, the exploits are consisted in the mail body or
attachment (Flores 2013). When user lick on such attachments, the virus start spreading
through their systems, encrypts some files and demand money for accessing such files. It has
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ETHICAL HACKING AS A DEFENCE MECHANISM
bbeen reported that, the virus infiltrate over 300,000 computers and stopped when a security
researcher discovers a kill switch.
4.0 Ethical hacking
Ethical hackers are also uses same technique and tools as criminals to infiltrate certain
computers or network devices. The only difference is they tried to hack into systems with the
system’s owner permission in order to check vulnerability. The purpose of such hacking is to
identify vulnerability and evaluate the security in systems infrastructure. It has been
conducted to check whether unauthorized access is permitted or vulnerable to malicious
software such as malware (Dayanandam et al. 2013). After finding casualties in certain
system, they inform the developers to fix the issues rather taking advantage of the
vulnerability.
5.0 Conclusion:
As the technology around us is evolving day by day, enormous amount of data is
available in the web. Several criminals also want to take advantages of this as they can
compromise such information to gain certain benefits. This type of crimes includes infiltrate
of any unauthorized system while falsifying email source information, introducing a virus or
other contaminant into a computer system, using a computer in a scheme to defraud, utilizing
encryption in aid of a crime, using interfering with someone else's computer access or use,
copying, modifying, disclosing, using, damaging or taking programs or data and improperly
accessing a computer, system, or network. This report describes about the fundamentals of
cybercrimes. Cybercrime is a broad topic which cannot be described fully within such short
parameter. This report is mainly focused on the ethical hacking. Generally, hackers used
some kind of malicious software to inflate targeted system. Computer depended crimes are
offences which can only be committed while utilizing the computer devices or network or
any application of information technology. This type of attacks involves spreading of
bbeen reported that, the virus infiltrate over 300,000 computers and stopped when a security
researcher discovers a kill switch.
4.0 Ethical hacking
Ethical hackers are also uses same technique and tools as criminals to infiltrate certain
computers or network devices. The only difference is they tried to hack into systems with the
system’s owner permission in order to check vulnerability. The purpose of such hacking is to
identify vulnerability and evaluate the security in systems infrastructure. It has been
conducted to check whether unauthorized access is permitted or vulnerable to malicious
software such as malware (Dayanandam et al. 2013). After finding casualties in certain
system, they inform the developers to fix the issues rather taking advantage of the
vulnerability.
5.0 Conclusion:
As the technology around us is evolving day by day, enormous amount of data is
available in the web. Several criminals also want to take advantages of this as they can
compromise such information to gain certain benefits. This type of crimes includes infiltrate
of any unauthorized system while falsifying email source information, introducing a virus or
other contaminant into a computer system, using a computer in a scheme to defraud, utilizing
encryption in aid of a crime, using interfering with someone else's computer access or use,
copying, modifying, disclosing, using, damaging or taking programs or data and improperly
accessing a computer, system, or network. This report describes about the fundamentals of
cybercrimes. Cybercrime is a broad topic which cannot be described fully within such short
parameter. This report is mainly focused on the ethical hacking. Generally, hackers used
some kind of malicious software to inflate targeted system. Computer depended crimes are
offences which can only be committed while utilizing the computer devices or network or
any application of information technology. This type of attacks involves spreading of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7ETHICAL HACKING AS A DEFENCE MECHANISM
malware, virus and hacking and DoS attacks. On other hand, computer enabled crimes are
traditional crimes which can be improved in their reach or scale by utilizing computers,
computer network or other type of information technology. Organizations often take several
security measures to prevent such vulnerabilities. They also used ethical hackers to evaluate
their system in order to find any kind of vulnerability.
malware, virus and hacking and DoS attacks. On other hand, computer enabled crimes are
traditional crimes which can be improved in their reach or scale by utilizing computers,
computer network or other type of information technology. Organizations often take several
security measures to prevent such vulnerabilities. They also used ethical hackers to evaluate
their system in order to find any kind of vulnerability.

8ETHICAL HACKING AS A DEFENCE MECHANISM
6.0 References:
Dayanandam, G., Rao, T.V., Reddy, S.P.K. and Sruthi, R., 2013. Password Based Scheme
and Group Testing for Defending DDOS Attacks. International Journal of Network Security
& Its Applications, 5(3), p.17.
Flores, D.A., 2013. A social engineering discussion about privacy attacks and defences
considering web browsers and social networks. In 8th Congress of Science and Technology-
ESPE, Sangolquí, EC.
Lehrfeld, M. and Guest, P., 2016, March. Building an ethical hacking site for learning and
student engagement. In SoutheastCon, 2016 (pp. 1-6). IEEE.
Lokhande, P.S. and Meshram, B.B., 2016, March. Analytic Hierarchy Process (AHP) to Find
Most Probable Web Attack on an E-Commerce Site. In Proceedings of the Second
International Conference on Information and Communication Technology for Competitive
Strategies (p. 62). ACM.
Peacock, D., 2013. From underground hacking to ethical hacking (Doctoral dissertation,
Northumbria University).
Shetty, S.S., Shetty, R.R., Shetty, T.G. and D'Souza, D.J., 2017, September. Survey of
hacking techniques and it's prevention. In 2017 IEEE International Conference on Power,
Control, Signals and Instrumentation Engineering (ICPCSI) (pp. 1940-1945). IEEE.
Thomas, D.R., Pastrana, S., Hutchings, A., Clayton, R. and Beresford, A.R., 2017,
November. Ethical issues in research using datasets of illicit origin. In Proceedings of the
2017 Internet Measurement Conference (pp. 445-462). ACM.
Xu, W., Madison, K., Flinn, M. and Kwok, W., 2014. Applying virtualization technology in
security education. Procedia-Social and Behavioral Sciences, 141, pp.10-14.
6.0 References:
Dayanandam, G., Rao, T.V., Reddy, S.P.K. and Sruthi, R., 2013. Password Based Scheme
and Group Testing for Defending DDOS Attacks. International Journal of Network Security
& Its Applications, 5(3), p.17.
Flores, D.A., 2013. A social engineering discussion about privacy attacks and defences
considering web browsers and social networks. In 8th Congress of Science and Technology-
ESPE, Sangolquí, EC.
Lehrfeld, M. and Guest, P., 2016, March. Building an ethical hacking site for learning and
student engagement. In SoutheastCon, 2016 (pp. 1-6). IEEE.
Lokhande, P.S. and Meshram, B.B., 2016, March. Analytic Hierarchy Process (AHP) to Find
Most Probable Web Attack on an E-Commerce Site. In Proceedings of the Second
International Conference on Information and Communication Technology for Competitive
Strategies (p. 62). ACM.
Peacock, D., 2013. From underground hacking to ethical hacking (Doctoral dissertation,
Northumbria University).
Shetty, S.S., Shetty, R.R., Shetty, T.G. and D'Souza, D.J., 2017, September. Survey of
hacking techniques and it's prevention. In 2017 IEEE International Conference on Power,
Control, Signals and Instrumentation Engineering (ICPCSI) (pp. 1940-1945). IEEE.
Thomas, D.R., Pastrana, S., Hutchings, A., Clayton, R. and Beresford, A.R., 2017,
November. Ethical issues in research using datasets of illicit origin. In Proceedings of the
2017 Internet Measurement Conference (pp. 445-462). ACM.
Xu, W., Madison, K., Flinn, M. and Kwok, W., 2014. Applying virtualization technology in
security education. Procedia-Social and Behavioral Sciences, 141, pp.10-14.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9ETHICAL HACKING AS A DEFENCE MECHANISM
Yamini, B., Brindha, L. and DEEPANANDA ARTHI, S., 2018. PREVENTION OF DDoS
AND SQL INJECTION ATTACK BY PREPARED STATEMENT AND IP BLOCKING.
Journal on Software Engineering, 12(3).
Yamini, B., Brindha, L. and DEEPANANDA ARTHI, S., 2018. PREVENTION OF DDoS
AND SQL INJECTION ATTACK BY PREPARED STATEMENT AND IP BLOCKING.
Journal on Software Engineering, 12(3).
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





