Ethical Hacking and Defence: Analysis Plan for Security Testing
VerifiedAdded on 2022/09/21
|13
|1893
|25
Project
AI Summary
This document presents an analysis plan for a penetration testing project focused on ethical hacking and defence. The plan outlines a proposed analytical process based on the National Institute of Standards and Technology's recommendations, including phases for agreement, reconnaissance, scanning, gaining and maintaining access, exploitation, and evidence collection and reporting. It details the scope of testing, the type of test (Gray Box), ethical considerations, resources needed (tools, techniques, and timeframe), and references. The student addresses the importance of maintaining integrity and professionalism, avoiding conflicts of interest, and protecting clients. The plan also includes a vulnerable list template, demonstrating a structured approach to the penetration testing process. The assignment aims to analyze security vulnerabilities and propose actionable items for management controls.

Running head: ETHICAL HACKING AND DEFENCE 1
ETHICAL HACKING AND DEFENCE
[Author Name(s), First M. Last, Omit Titles and Degrees]
[Institutional Affiliation(s)]
Author Note
[Include any grant/funding information and a complete correspondence address.]
ETHICAL HACKING AND DEFENCE
[Author Name(s), First M. Last, Omit Titles and Degrees]
[Institutional Affiliation(s)]
Author Note
[Include any grant/funding information and a complete correspondence address.]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ETHICAL HACKING AND DEFENCE 2
Table of Contents
Introduction......................................................................................................................................1
Proposed Analytical Process............................................................................................................2
1. Agreement.............................................................................................................................2
2. Reconnaissance.....................................................................................................................3
3. Scanning...............................................................................................................................3
4. Gaining access......................................................................................................................4
5. Maintaining access................................................................................................................4
6. Exploitation...........................................................................................................................4
7. Evidence Collection and Reporting......................................................................................5
Scope............................................................................................................................................5
Type of Test.................................................................................................................................5
Ethical Consideration.......................................................................................................................6
Resources.........................................................................................................................................7
Timeframe........................................................................................................................................8
References........................................................................................................................................9
Appendix A: Vulnerable List Template........................................................................................11
Table of Contents
Introduction......................................................................................................................................1
Proposed Analytical Process............................................................................................................2
1. Agreement.............................................................................................................................2
2. Reconnaissance.....................................................................................................................3
3. Scanning...............................................................................................................................3
4. Gaining access......................................................................................................................4
5. Maintaining access................................................................................................................4
6. Exploitation...........................................................................................................................4
7. Evidence Collection and Reporting......................................................................................5
Scope............................................................................................................................................5
Type of Test.................................................................................................................................5
Ethical Consideration.......................................................................................................................6
Resources.........................................................................................................................................7
Timeframe........................................................................................................................................8
References........................................................................................................................................9
Appendix A: Vulnerable List Template........................................................................................11

ETHICAL HACKING AND DEFENCE 3
Introduction
Penetration testing is a very key technical process that is used to dig deep into the computer
systems and applications with the objective of finding the extent to which the system can be
compromised. This penetration testing plan aims at outlining the various key states that the
testers shall undertake in a bid to have more elaborate testing of the systems against established
security flaws (Tomanek & Klima, 2015). Planning the various activities shall help the tester
have control of the process to be carried out and ensure all the key vulnerabilities are well tested
against a simulated attack onto the system. The plan again outlines the key resources that will be
needed to have a successful penetration testing and outlining the time frames for each of the
penetration testing phases. This help in the control and monitoring of the progress.
Introduction
Penetration testing is a very key technical process that is used to dig deep into the computer
systems and applications with the objective of finding the extent to which the system can be
compromised. This penetration testing plan aims at outlining the various key states that the
testers shall undertake in a bid to have more elaborate testing of the systems against established
security flaws (Tomanek & Klima, 2015). Planning the various activities shall help the tester
have control of the process to be carried out and ensure all the key vulnerabilities are well tested
against a simulated attack onto the system. The plan again outlines the key resources that will be
needed to have a successful penetration testing and outlining the time frames for each of the
penetration testing phases. This help in the control and monitoring of the progress.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ETHICAL HACKING AND DEFENCE 4
Proposed Analytical Process
Based on the unique nature of the scenario, the following penetration testing phases shall be
adopted to effectively and efficiently analyze all the key vulnerabilities in the system with an aim
of recommending actionable items for management controls (Tomáš Klíma, 2016). The key
process processes below are bases on the National Institute of Standards and Technology
recommended approaches to handling the penetration for systems in these scenarios.
Phases
The penetration testing shall undergo the following distinct phrases
The individual phrase activities are explained below
1. Agreement
During this phase of the penetration planning, the two parties involved in the activities i.e
the testers and the stakeholder make some formal agreement on the proposed plan. This
agreement shall have a formal discussion on matters such as the methodology and the
scope of the test and the level of exploitation permissible during the pentest period. This
formal agreement shall act as a legal binding between the stakeholder and the testers. The
output of this phase shall be the nondisclosure agreement signed by both parties (Stephan,
Kaul, & Villinger, 2015).
Proposed Analytical Process
Based on the unique nature of the scenario, the following penetration testing phases shall be
adopted to effectively and efficiently analyze all the key vulnerabilities in the system with an aim
of recommending actionable items for management controls (Tomáš Klíma, 2016). The key
process processes below are bases on the National Institute of Standards and Technology
recommended approaches to handling the penetration for systems in these scenarios.
Phases
The penetration testing shall undergo the following distinct phrases
The individual phrase activities are explained below
1. Agreement
During this phase of the penetration planning, the two parties involved in the activities i.e
the testers and the stakeholder make some formal agreement on the proposed plan. This
agreement shall have a formal discussion on matters such as the methodology and the
scope of the test and the level of exploitation permissible during the pentest period. This
formal agreement shall act as a legal binding between the stakeholder and the testers. The
output of this phase shall be the nondisclosure agreement signed by both parties (Stephan,
Kaul, & Villinger, 2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ETHICAL HACKING AND DEFENCE 5
2. Reconnaissance
During this phase, the testers shall gather as much information as possible about the
target system and company. The information gathered at this phase shall include but not
limited to the IP address of the systems and servers, the domain name of the company,
the mail server details, the type of network topology. This phase shall take most of the
time to allow much information to be retrieved as possible (Sarraute, Buffet, &
Hoffmann, 2013).
3. Scanning
During this phase, the testers shall have an interaction with the target system and
applications with an aim of identifying any vulnerabilities within the target system, This
shall be achieved by means of sending probes to the target systems and have the
responses given by the target system recorded when various inputs are given. This phase
shall rely heavily on network scanning tools, vulnerability scanning tools, services
running on the target, ports used by the various services. The aim of this phase is to
identify any key libraries, services and the logic implemented onto the target. Such
information shall be used to identify any known or unknown vulnerabilities. The output
of this phase is the vulnerability report (Ross, Baji, & Barnett, 2019)
4. Gaining access
Once the scanning is done and vulnerabilities identified and recorded, this phase shall be
used to actually try and exploit the documented vulnerabilities with an objective of
successfully gaining unauthorized access into the target system. This phase shall exploit
2. Reconnaissance
During this phase, the testers shall gather as much information as possible about the
target system and company. The information gathered at this phase shall include but not
limited to the IP address of the systems and servers, the domain name of the company,
the mail server details, the type of network topology. This phase shall take most of the
time to allow much information to be retrieved as possible (Sarraute, Buffet, &
Hoffmann, 2013).
3. Scanning
During this phase, the testers shall have an interaction with the target system and
applications with an aim of identifying any vulnerabilities within the target system, This
shall be achieved by means of sending probes to the target systems and have the
responses given by the target system recorded when various inputs are given. This phase
shall rely heavily on network scanning tools, vulnerability scanning tools, services
running on the target, ports used by the various services. The aim of this phase is to
identify any key libraries, services and the logic implemented onto the target. Such
information shall be used to identify any known or unknown vulnerabilities. The output
of this phase is the vulnerability report (Ross, Baji, & Barnett, 2019)
4. Gaining access
Once the scanning is done and vulnerabilities identified and recorded, this phase shall be
used to actually try and exploit the documented vulnerabilities with an objective of
successfully gaining unauthorized access into the target system. This phase shall exploit

ETHICAL HACKING AND DEFENCE 6
the vulnerabilities in order of priority since not all vulnerabilities shall lead to
unauthorized access (Pike, 2013).
5. Maintaining access
Once the vulnerability is exploited in stage four, this stage shall be used to ensure there is
persistence in exploiting the vulnerabilities even if the target system is rebooted or
modified. This is useful to endure to ensure the vulnerabilities can be exploited
successfully from anywhere.
6. Exploitation
At this stage, the testers shall have gain access to the target and now use their information
gathered to actually cause damage to the system. This type of exploitation shall include
but not limited to accessing data, launching DDOS attacks, compromising the system.
This phase is very critical for the company hence shall be done in a much-controlled
environment to reduce its effects on the available network bandwidth. This phase shall be
made successful by the use of some dummy flags which shall be placed in some of the
critical components of the target such as the database. The aim of this phase shall be to
get the dummy flag (Naik, Kurundkar, Khamitkar, & Kalyankar, 2009).
7. Evidence Collection and Reporting
Once the pentest is completed, the final phase shall involve the collection of evidence to
ascertain the successful exploitation of the vulnerabilities and have a report compiled and
submitted to the executive management for their review and action. The report shall
the vulnerabilities in order of priority since not all vulnerabilities shall lead to
unauthorized access (Pike, 2013).
5. Maintaining access
Once the vulnerability is exploited in stage four, this stage shall be used to ensure there is
persistence in exploiting the vulnerabilities even if the target system is rebooted or
modified. This is useful to endure to ensure the vulnerabilities can be exploited
successfully from anywhere.
6. Exploitation
At this stage, the testers shall have gain access to the target and now use their information
gathered to actually cause damage to the system. This type of exploitation shall include
but not limited to accessing data, launching DDOS attacks, compromising the system.
This phase is very critical for the company hence shall be done in a much-controlled
environment to reduce its effects on the available network bandwidth. This phase shall be
made successful by the use of some dummy flags which shall be placed in some of the
critical components of the target such as the database. The aim of this phase shall be to
get the dummy flag (Naik, Kurundkar, Khamitkar, & Kalyankar, 2009).
7. Evidence Collection and Reporting
Once the pentest is completed, the final phase shall involve the collection of evidence to
ascertain the successful exploitation of the vulnerabilities and have a report compiled and
submitted to the executive management for their review and action. The report shall
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ETHICAL HACKING AND DEFENCE 7
include the recommended actions that the executives can take to avert the risks posed by
the vulnerabilities. This can be in the form of acceptance, transfer and or ignore
(LaBarge & McGuire, 2013)
Scope
The following components will be tested during the penetration testing
Web serves
Database injections
Password cracking
DDOS
Mail server
Firewall
Wireless Acces points
Type of Test
Based on the case, the testers shall use the Gray Box pentest type. The testers are given
partial information about the target and hence will use their expertise and public
knowledge about the target and company to construct the remaining information needed
to carry out the pentest successfully (Falagush, McDowell, Yu, & Bono, 2015)
include the recommended actions that the executives can take to avert the risks posed by
the vulnerabilities. This can be in the form of acceptance, transfer and or ignore
(LaBarge & McGuire, 2013)
Scope
The following components will be tested during the penetration testing
Web serves
Database injections
Password cracking
DDOS
Mail server
Firewall
Wireless Acces points
Type of Test
Based on the case, the testers shall use the Gray Box pentest type. The testers are given
partial information about the target and hence will use their expertise and public
knowledge about the target and company to construct the remaining information needed
to carry out the pentest successfully (Falagush, McDowell, Yu, & Bono, 2015)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ETHICAL HACKING AND DEFENCE 8
Ethical Consideration
The testing unit shall maintain a high level of integrity and upload professionalism during and
after the whole exercise. This is important to avoid the knowledgable information security
experts use their advanced knowledge and use them negatively against ordinary users (Čisar &
Čisar, 2018). The testers shall not engage in activities that cause a conflict of interest, provision
of any false-positive results and the false negatives shall be taken into account during the whole
process. All the test results gotten from the use of social engineering techniques shall be
delivered in the most summarized and statistical way in order to avoid complicate those involve.
This shall protect all the clients and insulate any unknown employees who might be subjects of
ridicule, embarrassment and sometimes termination of the contract as a result of the test (Georg
Thomas, Oliver Burmeister, & Gregory Low, 2019).
The testing team is ethically bound to the services of the customer. This is true even if it is in the
best interest of the customer to solicit the services of another testing company. In any such event,
the testing team should never recommend any company whatsoever to the client as such may be
a conflict of interest
Ethical Consideration
The testing unit shall maintain a high level of integrity and upload professionalism during and
after the whole exercise. This is important to avoid the knowledgable information security
experts use their advanced knowledge and use them negatively against ordinary users (Čisar &
Čisar, 2018). The testers shall not engage in activities that cause a conflict of interest, provision
of any false-positive results and the false negatives shall be taken into account during the whole
process. All the test results gotten from the use of social engineering techniques shall be
delivered in the most summarized and statistical way in order to avoid complicate those involve.
This shall protect all the clients and insulate any unknown employees who might be subjects of
ridicule, embarrassment and sometimes termination of the contract as a result of the test (Georg
Thomas, Oliver Burmeister, & Gregory Low, 2019).
The testing team is ethically bound to the services of the customer. This is true even if it is in the
best interest of the customer to solicit the services of another testing company. In any such event,
the testing team should never recommend any company whatsoever to the client as such may be
a conflict of interest

ETHICAL HACKING AND DEFENCE 9
Resources
The following tools and techniques shall be used during the various phases of the pentest
Tool Type
Nessus Vulnerability scanner
Dirbuster Directory discovery
Metasploit Hacking framework
Burp Suite Web vulnerability scanning
Kali Linux Pentest OS
Thinkpad Laptop Hardware
Acutetix Web vulnerability scanner
Wireshark Network protocol analyzer
Cain and Abel Password Cracking
Social engineering toolkit Human psychology
Nmap Platform analysis
Vmware workstation OS Virtualization
Resources
The following tools and techniques shall be used during the various phases of the pentest
Tool Type
Nessus Vulnerability scanner
Dirbuster Directory discovery
Metasploit Hacking framework
Burp Suite Web vulnerability scanning
Kali Linux Pentest OS
Thinkpad Laptop Hardware
Acutetix Web vulnerability scanner
Wireshark Network protocol analyzer
Cain and Abel Password Cracking
Social engineering toolkit Human psychology
Nmap Platform analysis
Vmware workstation OS Virtualization
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
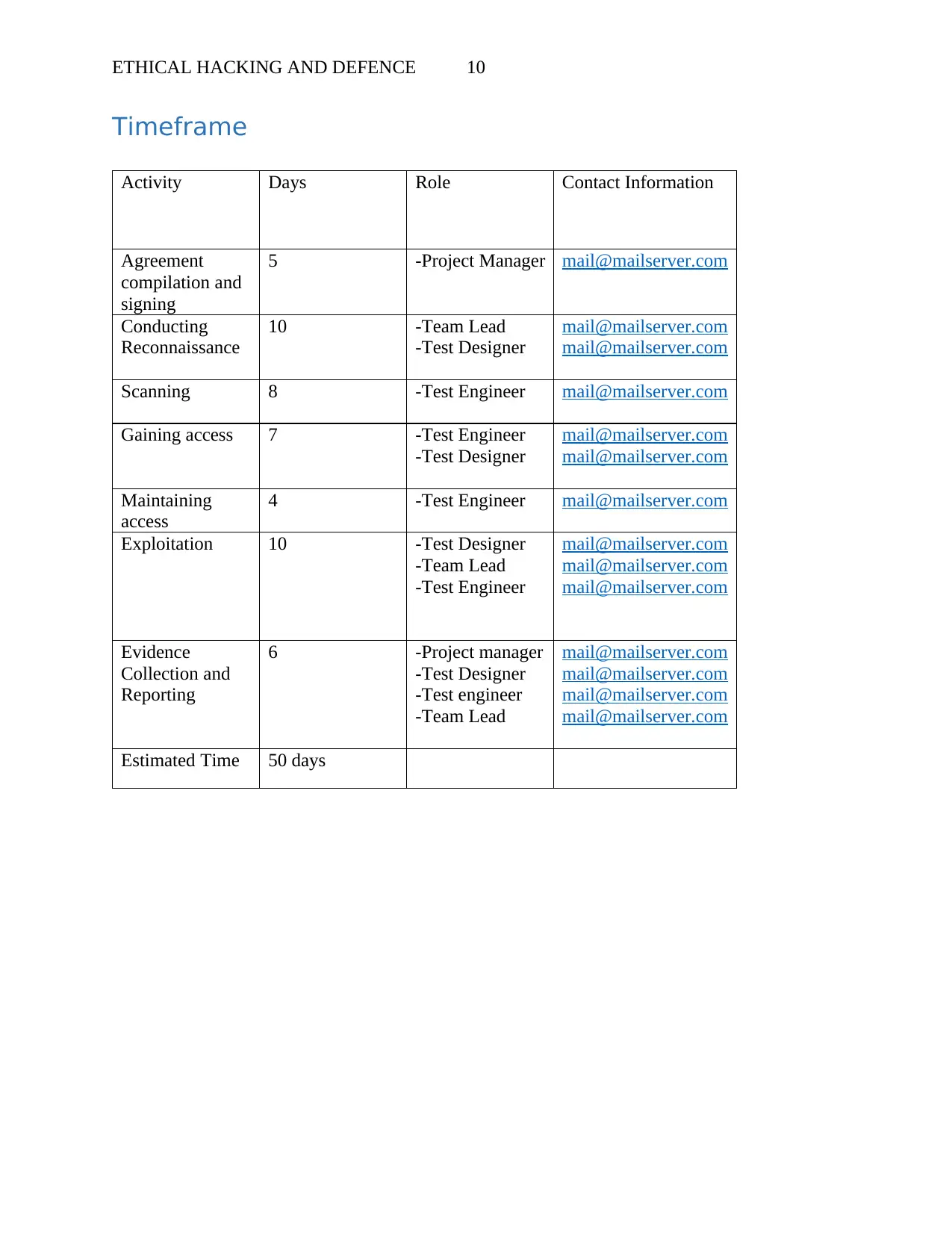
ETHICAL HACKING AND DEFENCE 10
Timeframe
Activity Days Role Contact Information
Agreement
compilation and
signing
5 -Project Manager mail@mailserver.com
Conducting
Reconnaissance
10 -Team Lead
-Test Designer
mail@mailserver.com
mail@mailserver.com
Scanning 8 -Test Engineer mail@mailserver.com
Gaining access 7 -Test Engineer
-Test Designer
mail@mailserver.com
mail@mailserver.com
Maintaining
access
4 -Test Engineer mail@mailserver.com
Exploitation 10 -Test Designer
-Team Lead
-Test Engineer
mail@mailserver.com
mail@mailserver.com
mail@mailserver.com
Evidence
Collection and
Reporting
6 -Project manager
-Test Designer
-Test engineer
-Team Lead
mail@mailserver.com
mail@mailserver.com
mail@mailserver.com
mail@mailserver.com
Estimated Time 50 days
Timeframe
Activity Days Role Contact Information
Agreement
compilation and
signing
5 -Project Manager mail@mailserver.com
Conducting
Reconnaissance
10 -Team Lead
-Test Designer
mail@mailserver.com
mail@mailserver.com
Scanning 8 -Test Engineer mail@mailserver.com
Gaining access 7 -Test Engineer
-Test Designer
mail@mailserver.com
mail@mailserver.com
Maintaining
access
4 -Test Engineer mail@mailserver.com
Exploitation 10 -Test Designer
-Team Lead
-Test Engineer
mail@mailserver.com
mail@mailserver.com
mail@mailserver.com
Evidence
Collection and
Reporting
6 -Project manager
-Test Designer
-Test engineer
-Team Lead
mail@mailserver.com
mail@mailserver.com
mail@mailserver.com
mail@mailserver.com
Estimated Time 50 days
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ETHICAL HACKING AND DEFENCE 11
References
Čisar, P., & Čisar, S. M. (2018). Ethical Hacking of Wireless Networks in Kali Linux
Environment. Annals of the Faculty of Engineering Hunedoara - International Journal of
Engineering, 16(3), 181–186.
Falagush, O., McDowell, G. R., Yu, H. S., & Bono, J. P. (2015). Discrete element modelling and
cavity expansion analysis of cone penetration testing. Granular Matter, (4), 483.
https://doi.org/10.1007/s10035-015-0570-4
Georg Thomas, Oliver Burmeister, & Gregory Low. (2019). The Importance of Ethical Conduct
by Penetration Testers in the Age of Breach Disclosure Laws. Australasian Journal of
Information Systems, (0). https://doi.org/10.3127/ajis.v23i0.1867
LaBarge, R., & McGuire, T. (2013). Cloud Penetration Testing.
https://doi.org/10.5121/ijccsa.2012.2604
Naik, N. A., Kurundkar, G. D., Khamitkar, S. D., & Kalyankar, N. V. (2009). Penetration
Testing: A Roadmap to Network Security.
Pike, R. E. (2013). The “Ethics” of Teaching Ethical Hacking. Journal of International
Technology & Information Management, 22(4), 67–75.
Ross, R., Baji, A., & Barnett, D. (2019). Inner Profile Measurement for Pipes Using Penetration
Testing. Sensors (14248220), 19(2), 237. https://doi.org/10.3390/s19020237
Sarraute, C., Buffet, O., & Hoffmann, J. (2013). POMDPs Make Better Hackers: Accounting for
Uncertainty in Penetration Testing.
Stephan, S., Kaul, N., & Villinger, H. (2015). Validation of impact penetrometer data by cone
penetration testing and shallow seismic data within the regional geology of the Southern
North Sea. Geo-Marine Letters, (3), 203. https://doi.org/10.1007/s00367-015-0401-y
References
Čisar, P., & Čisar, S. M. (2018). Ethical Hacking of Wireless Networks in Kali Linux
Environment. Annals of the Faculty of Engineering Hunedoara - International Journal of
Engineering, 16(3), 181–186.
Falagush, O., McDowell, G. R., Yu, H. S., & Bono, J. P. (2015). Discrete element modelling and
cavity expansion analysis of cone penetration testing. Granular Matter, (4), 483.
https://doi.org/10.1007/s10035-015-0570-4
Georg Thomas, Oliver Burmeister, & Gregory Low. (2019). The Importance of Ethical Conduct
by Penetration Testers in the Age of Breach Disclosure Laws. Australasian Journal of
Information Systems, (0). https://doi.org/10.3127/ajis.v23i0.1867
LaBarge, R., & McGuire, T. (2013). Cloud Penetration Testing.
https://doi.org/10.5121/ijccsa.2012.2604
Naik, N. A., Kurundkar, G. D., Khamitkar, S. D., & Kalyankar, N. V. (2009). Penetration
Testing: A Roadmap to Network Security.
Pike, R. E. (2013). The “Ethics” of Teaching Ethical Hacking. Journal of International
Technology & Information Management, 22(4), 67–75.
Ross, R., Baji, A., & Barnett, D. (2019). Inner Profile Measurement for Pipes Using Penetration
Testing. Sensors (14248220), 19(2), 237. https://doi.org/10.3390/s19020237
Sarraute, C., Buffet, O., & Hoffmann, J. (2013). POMDPs Make Better Hackers: Accounting for
Uncertainty in Penetration Testing.
Stephan, S., Kaul, N., & Villinger, H. (2015). Validation of impact penetrometer data by cone
penetration testing and shallow seismic data within the regional geology of the Southern
North Sea. Geo-Marine Letters, (3), 203. https://doi.org/10.1007/s00367-015-0401-y

ETHICAL HACKING AND DEFENCE 12
Tomanek, M., & Klima, T. (2015). Penetration Testing in Agile Software Development Projects.
https://doi.org/10.5121/ijcis.2015.5101
Tomáš Klíma. (2016). PETA: Methodology of Information Systems Security Penetration
Testing. Acta Informatica Pragensia, (2), 98. https://doi.org/10.18267/j.aip.88
Tomanek, M., & Klima, T. (2015). Penetration Testing in Agile Software Development Projects.
https://doi.org/10.5121/ijcis.2015.5101
Tomáš Klíma. (2016). PETA: Methodology of Information Systems Security Penetration
Testing. Acta Informatica Pragensia, (2), 98. https://doi.org/10.18267/j.aip.88
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





