Ethical Hacking: DNS, DHCP Attacks, Prevention Strategies using Kali
VerifiedAdded on 2023/06/12
|33
|3485
|255
Practical Assignment
AI Summary
This assignment provides a detailed exploration of ethical hacking techniques, focusing on Domain Name System (DNS) and Dynamic Host Configuration Protocol (DHCP) security. It covers DNS attacks like DNS spoofing and Distributed Denial of Service (DDOS), including step-by-step procedures for executing and preventing these attacks using Kali Linux. The document also delves into DHCP snooping, explaining its concepts, types, and configuration steps, along with methods to prevent DHCP snooping. The practical aspects are emphasized with installation steps for Kali Linux and configurations for setting up a virtual lab environment. This resource is intended to help understand countermeasures for protecting vulnerable network infrastructures.

ICT Ethical hacking
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1 Introduction.......................................................................................................................................2
2 Domain Name System........................................................................................................................2
2.1 DNS Raid....................................................................................................................................3
2.2 In what way DNS Transmission works....................................................................................3
2.3 Types of DNS attack..................................................................................................................3
2.3.1 DNS Spoofing.....................................................................................................................3
2.3.2 DDOS................................................................................................................................10
3 DHCP................................................................................................................................................15
3.1 Definition..................................................................................................................................15
3.2 How DHCP works....................................................................................................................15
3.3 DHCP snooping concepts........................................................................................................16
3.4 Types of snooping....................................................................................................................16
3.4.1 DHCP Snooping...............................................................................................................17
3.4.2 DNS starvation attack......................................................................................................19
4 Installation steps for Kali Linux.....................................................................................................25
5 Conclusion........................................................................................................................................31
6 References........................................................................................................................................31
1
1 Introduction.......................................................................................................................................2
2 Domain Name System........................................................................................................................2
2.1 DNS Raid....................................................................................................................................3
2.2 In what way DNS Transmission works....................................................................................3
2.3 Types of DNS attack..................................................................................................................3
2.3.1 DNS Spoofing.....................................................................................................................3
2.3.2 DDOS................................................................................................................................10
3 DHCP................................................................................................................................................15
3.1 Definition..................................................................................................................................15
3.2 How DHCP works....................................................................................................................15
3.3 DHCP snooping concepts........................................................................................................16
3.4 Types of snooping....................................................................................................................16
3.4.1 DHCP Snooping...............................................................................................................17
3.4.2 DNS starvation attack......................................................................................................19
4 Installation steps for Kali Linux.....................................................................................................25
5 Conclusion........................................................................................................................................31
6 References........................................................................................................................................31
1

1 Introduction
Information and communication technology is to enlarge coaching and training environments. It
permits self-training with the help of different tools like tasks. As an effect of coaching and
training, it develop into more beneficial and worthful. In this Ethical hacking, Domain Name
System will be studied. After explained that, DNS attack and its types will be revised. Then DNS
snooping will be analyzed. After that step by step procedure will be explained. And finally
prevention of DNS snooping will be explained. Dynamic Host Configuration Protocol (DHCP)
will be revised. After explaining that, Types and Step by step procedure will be analyzed. And
finally Prevention of DHCP snooping configuration will be explained.
2 Domain Name System
DNS is Domain Name System. It is used for change the domain name into their respective IP
address in TCP/IP protocols. DNS have a network protocol for memorizing host name and
address through a distributed data base. The domain name system directing the user to locate a
website with the conversion of domain name into IP address. The DNS is used for translating
human format name of site into the IP address (Zheng, 2014).
2
Information and communication technology is to enlarge coaching and training environments. It
permits self-training with the help of different tools like tasks. As an effect of coaching and
training, it develop into more beneficial and worthful. In this Ethical hacking, Domain Name
System will be studied. After explained that, DNS attack and its types will be revised. Then DNS
snooping will be analyzed. After that step by step procedure will be explained. And finally
prevention of DNS snooping will be explained. Dynamic Host Configuration Protocol (DHCP)
will be revised. After explaining that, Types and Step by step procedure will be analyzed. And
finally Prevention of DHCP snooping configuration will be explained.
2 Domain Name System
DNS is Domain Name System. It is used for change the domain name into their respective IP
address in TCP/IP protocols. DNS have a network protocol for memorizing host name and
address through a distributed data base. The domain name system directing the user to locate a
website with the conversion of domain name into IP address. The DNS is used for translating
human format name of site into the IP address (Zheng, 2014).
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2.1 DNS Raid
DNS Raid is also known as attacks on DNS. In DNS raid the attacker can change the IP address.
If the user can access that webpage, the attacker can get the information about the user. The wide
usage of internet is the main reason for DNS attack. Now a days, DNS attacks are very common.
The DNS attack is some hacker change the IP address of a website. When a user access the
website automatically the hacker can get the details of a user (Lee, Baek & Kim, 2015).
2.2 In what way DNS Transmission works
The goal of DNS server is converting or changing the domain name into the respective IP
address. It works like a mapping. When a server gets the IP address all information will start
relocating from website server to client and client to website server.
2.3 Types of DNS attack
The different categories of DNS attacks are given below.
DNS spoofing
DNS Amplification
DNS Tunneling
2.3.1 DNS Spoofing
DNS spoofing is a type of DNS attack. In this attack the hacker can change the fake website to
look like an original real website. The hacker done with the diverting traffic of the users.
Spoofing attacks can go for long time period without being detected and sometimes it may cause
serious issues. DNS spoofing is also called as DNS hijacking (Zhang & Xia, 2013) (Sridevi &
Dr.Manjaiah D.H, 2012).
3
DNS Raid is also known as attacks on DNS. In DNS raid the attacker can change the IP address.
If the user can access that webpage, the attacker can get the information about the user. The wide
usage of internet is the main reason for DNS attack. Now a days, DNS attacks are very common.
The DNS attack is some hacker change the IP address of a website. When a user access the
website automatically the hacker can get the details of a user (Lee, Baek & Kim, 2015).
2.2 In what way DNS Transmission works
The goal of DNS server is converting or changing the domain name into the respective IP
address. It works like a mapping. When a server gets the IP address all information will start
relocating from website server to client and client to website server.
2.3 Types of DNS attack
The different categories of DNS attacks are given below.
DNS spoofing
DNS Amplification
DNS Tunneling
2.3.1 DNS Spoofing
DNS spoofing is a type of DNS attack. In this attack the hacker can change the fake website to
look like an original real website. The hacker done with the diverting traffic of the users.
Spoofing attacks can go for long time period without being detected and sometimes it may cause
serious issues. DNS spoofing is also called as DNS hijacking (Zhang & Xia, 2013) (Sridevi &
Dr.Manjaiah D.H, 2012).
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
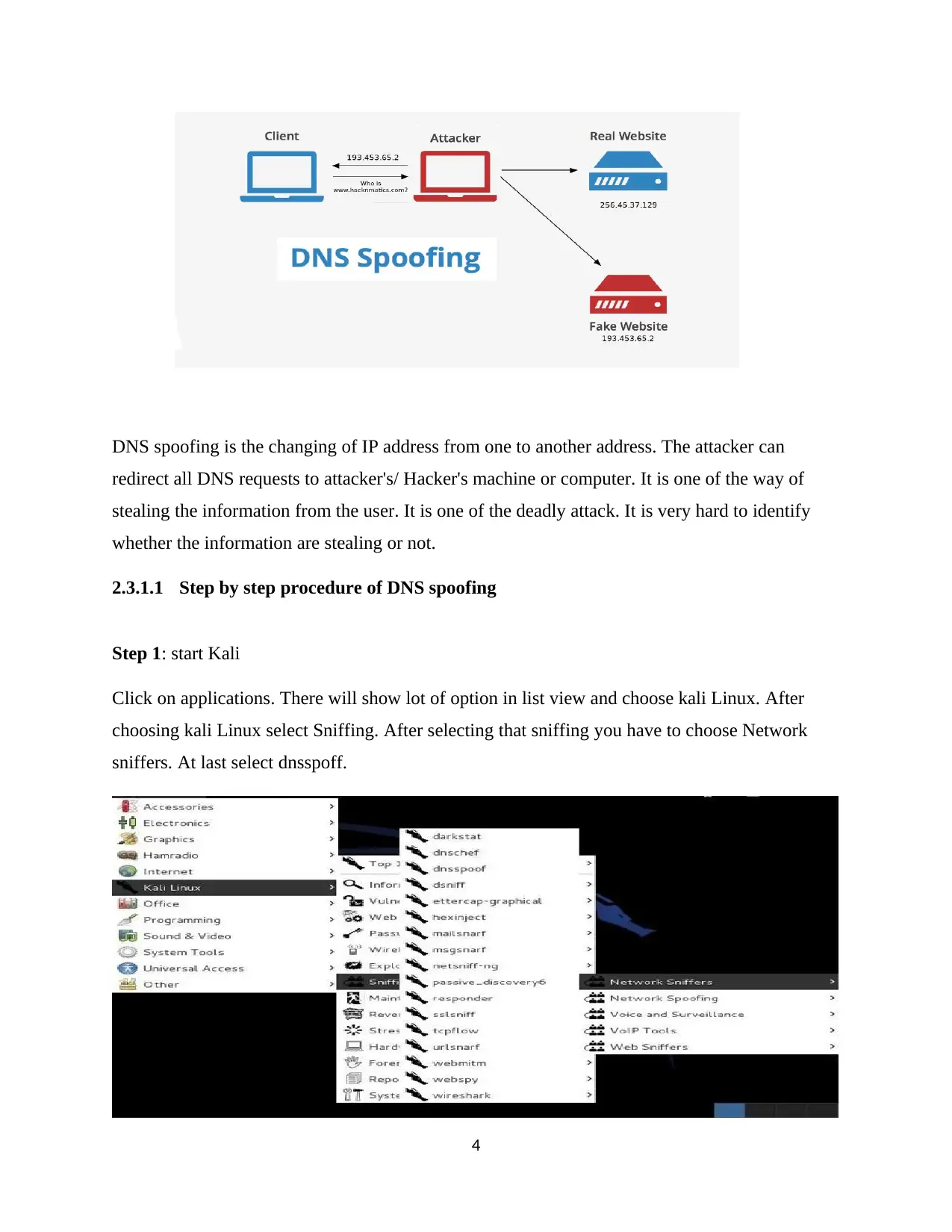
DNS spoofing is the changing of IP address from one to another address. The attacker can
redirect all DNS requests to attacker's/ Hacker's machine or computer. It is one of the way of
stealing the information from the user. It is one of the deadly attack. It is very hard to identify
whether the information are stealing or not.
2.3.1.1 Step by step procedure of DNS spoofing
Step 1: start Kali
Click on applications. There will show lot of option in list view and choose kali Linux. After
choosing kali Linux select Sniffing. After selecting that sniffing you have to choose Network
sniffers. At last select dnsspoff.
4
redirect all DNS requests to attacker's/ Hacker's machine or computer. It is one of the way of
stealing the information from the user. It is one of the deadly attack. It is very hard to identify
whether the information are stealing or not.
2.3.1.1 Step by step procedure of DNS spoofing
Step 1: start Kali
Click on applications. There will show lot of option in list view and choose kali Linux. After
choosing kali Linux select Sniffing. After selecting that sniffing you have to choose Network
sniffers. At last select dnsspoff.
4
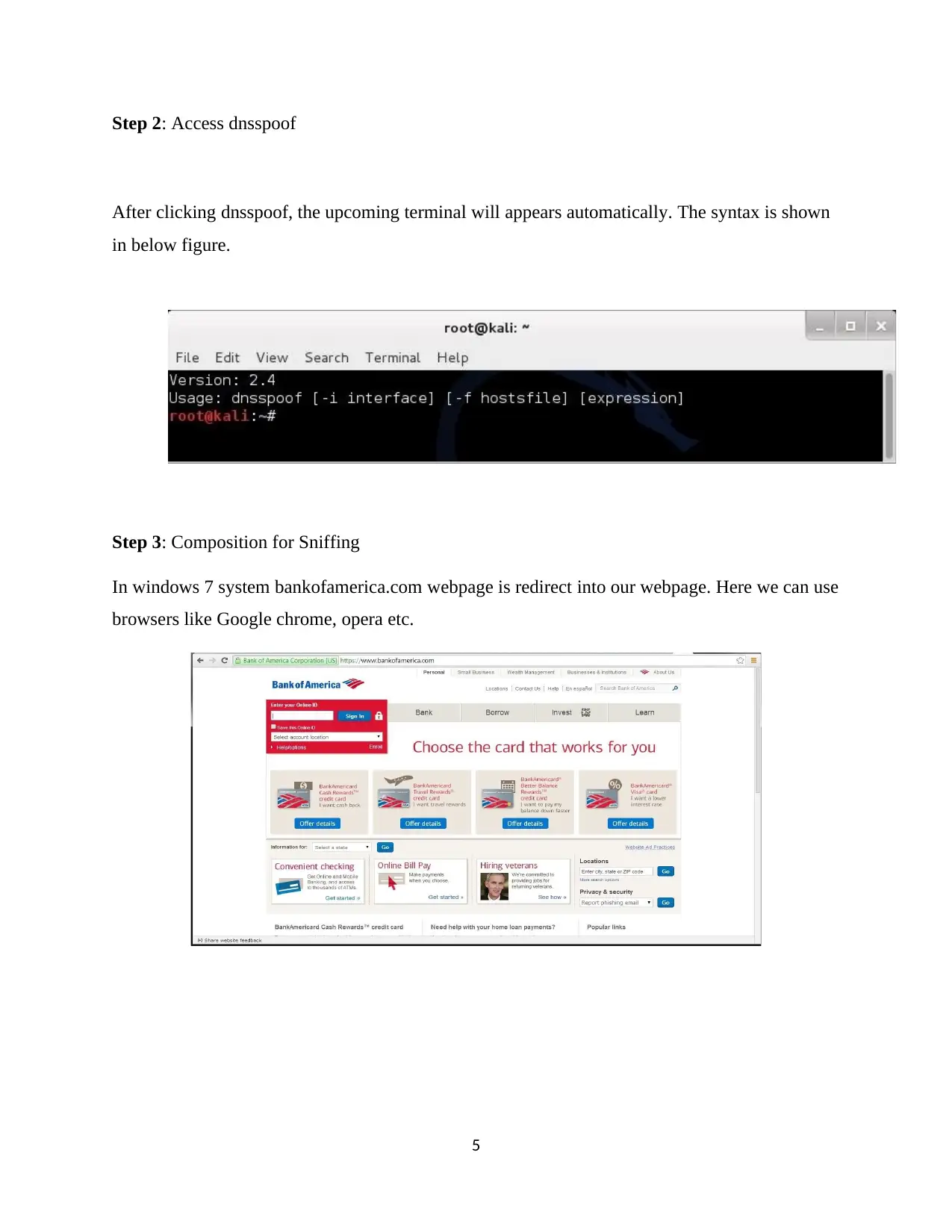
Step 2: Access dnsspoof
After clicking dnsspoof, the upcoming terminal will appears automatically. The syntax is shown
in below figure.
Step 3: Composition for Sniffing
In windows 7 system bankofamerica.com webpage is redirect into our webpage. Here we can use
browsers like Google chrome, opera etc.
5
After clicking dnsspoof, the upcoming terminal will appears automatically. The syntax is shown
in below figure.
Step 3: Composition for Sniffing
In windows 7 system bankofamerica.com webpage is redirect into our webpage. Here we can use
browsers like Google chrome, opera etc.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Step 4: Flush the DNS storehouse
The first step is DNS storehouse flushing in window 7. By this method, the client can't use the
DNS storehouse on his or her system. But in reality, this step is no need.
Terminate the browser after that type the following things:
ipconfig
The first step is make the network card on kali Linux server for accepting all packets.
ifconfig etho promisc
Then we terminate the transmission between webpage of bankof america and web server of
windows 7.
tcpkill -9 host [www.bankamerica.com]
After terminating the webpage of bankofamerica, conclude the tcpkill with the help of ctrl + c.
Step 5: creating a list of Host
The Linux on client DNS shows that the host list is acting as a fixed DNS. With the help of host
list or file we can redirect the webpage of bankofamerica instead of our webpage.
cd /usr/local
With the help of text editor we can open list of host. Here we are using Back Track methods so
kali don't have a write on it. But the kali contain graphical VIM. Graphical VIM named as gvim.
6
The first step is DNS storehouse flushing in window 7. By this method, the client can't use the
DNS storehouse on his or her system. But in reality, this step is no need.
Terminate the browser after that type the following things:
ipconfig
The first step is make the network card on kali Linux server for accepting all packets.
ifconfig etho promisc
Then we terminate the transmission between webpage of bankof america and web server of
windows 7.
tcpkill -9 host [www.bankamerica.com]
After terminating the webpage of bankofamerica, conclude the tcpkill with the help of ctrl + c.
Step 5: creating a list of Host
The Linux on client DNS shows that the host list is acting as a fixed DNS. With the help of host
list or file we can redirect the webpage of bankofamerica instead of our webpage.
cd /usr/local
With the help of text editor we can open list of host. Here we are using Back Track methods so
kali don't have a write on it. But the kali contain graphical VIM. Graphical VIM named as gvim.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
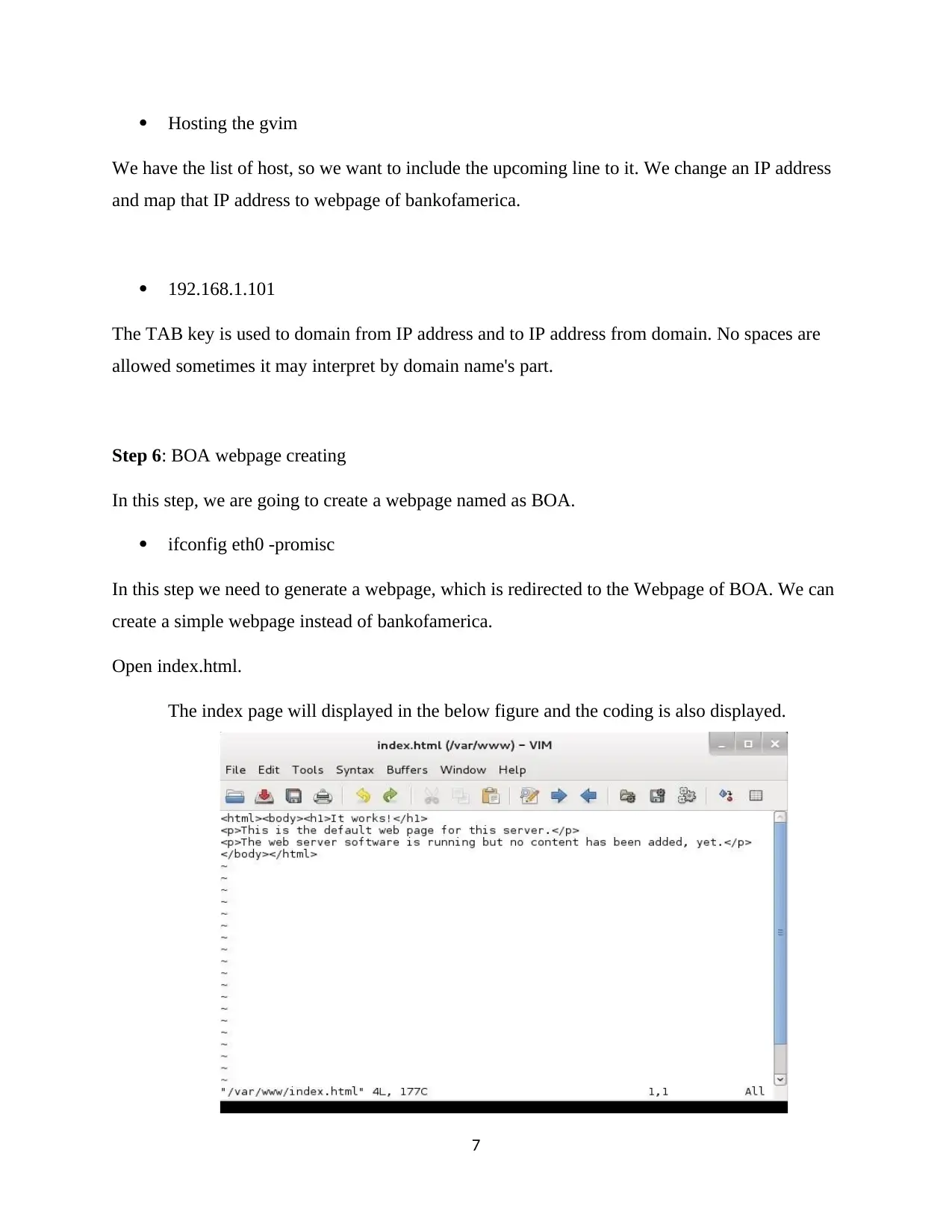
Hosting the gvim
We have the list of host, so we want to include the upcoming line to it. We change an IP address
and map that IP address to webpage of bankofamerica.
192.168.1.101
The TAB key is used to domain from IP address and to IP address from domain. No spaces are
allowed sometimes it may interpret by domain name's part.
Step 6: BOA webpage creating
In this step, we are going to create a webpage named as BOA.
ifconfig eth0 -promisc
In this step we need to generate a webpage, which is redirected to the Webpage of BOA. We can
create a simple webpage instead of bankofamerica.
Open index.html.
The index page will displayed in the below figure and the coding is also displayed.
7
We have the list of host, so we want to include the upcoming line to it. We change an IP address
and map that IP address to webpage of bankofamerica.
192.168.1.101
The TAB key is used to domain from IP address and to IP address from domain. No spaces are
allowed sometimes it may interpret by domain name's part.
Step 6: BOA webpage creating
In this step, we are going to create a webpage named as BOA.
ifconfig eth0 -promisc
In this step we need to generate a webpage, which is redirected to the Webpage of BOA. We can
create a simple webpage instead of bankofamerica.
Open index.html.
The index page will displayed in the below figure and the coding is also displayed.
7
Step 7: Starting Web server
In this step we are going to start the web server. First click on application then select kali Linux.
After selecting kali Linux some list were appear. From the appearing list you have to select
system services. Then select HTTP. At last click apache2. The web server apache2 will be
started.
8
In this step we are going to start the web server. First click on application then select kali Linux.
After selecting kali Linux some list were appear. From the appearing list you have to select
system services. Then select HTTP. At last click apache2. The web server apache2 will be
started.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
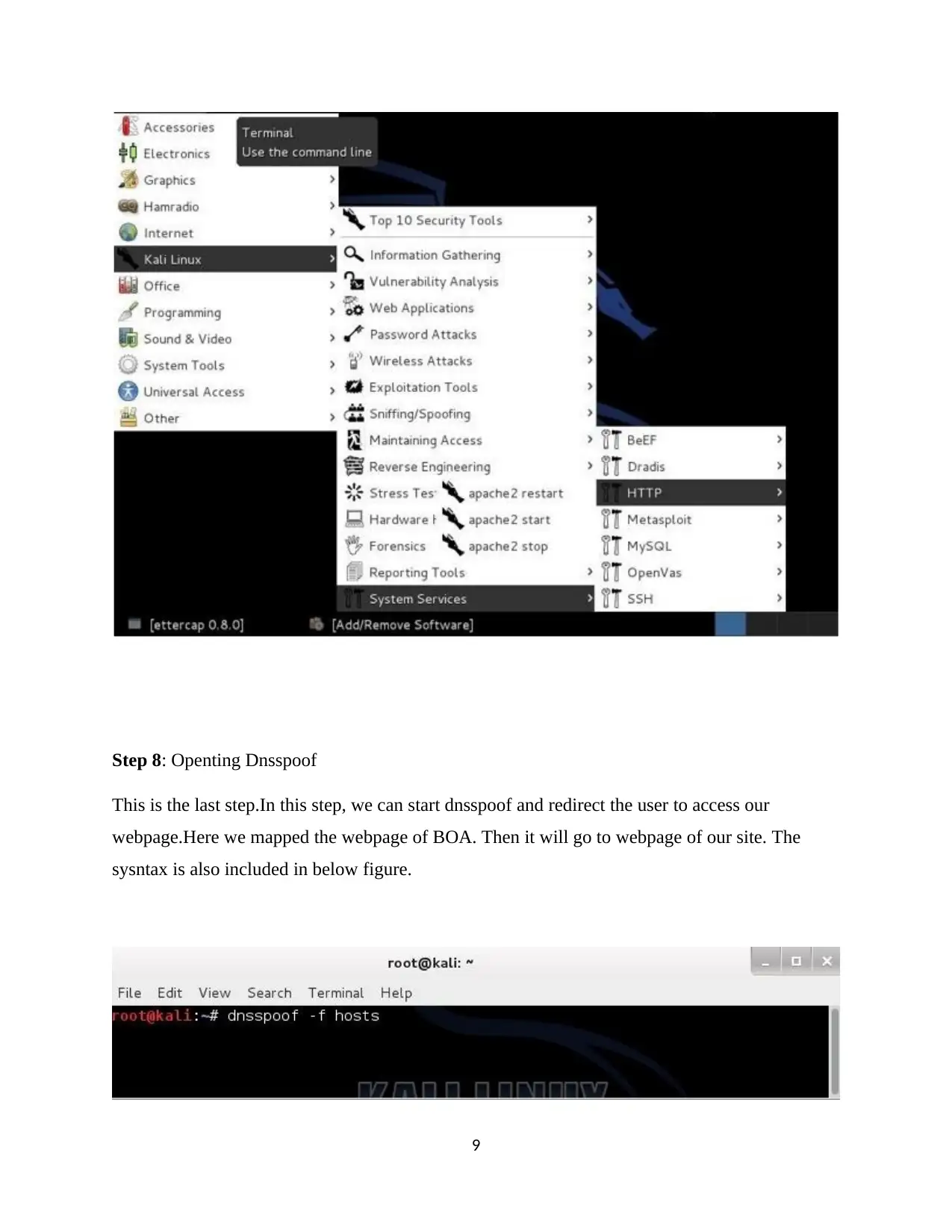
Step 8: Openting Dnsspoof
This is the last step.In this step, we can start dnsspoof and redirect the user to access our
webpage.Here we mapped the webpage of BOA. Then it will go to webpage of our site. The
sysntax is also included in below figure.
9
This is the last step.In this step, we can start dnsspoof and redirect the user to access our
webpage.Here we mapped the webpage of BOA. Then it will go to webpage of our site. The
sysntax is also included in below figure.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Step 9: Route the BOA webpage into our webpage
Now the user can type the URL bankofamerica.com this URL will redirect to our fake webpage.
2.3.1.2 Prevention of DNS spoofing:
Few idea for away from DNS spoofing. The ideas are given below
Implement of DNS spoofing detection techniques- Some product named as Xarp, which
is used to product the ARP storehouse from DNS spoofing.
Work with encrypted data networks- SSL/TLS will use for decrease the DNS spoofing by
usage of end-to-end encryption.
Use DNSSEC-DNSSEC have the digital DNS record for data security (Gupta, Kumar,
Tomar & Verma, 2016) (LI, CAO, LIU & LEI, 2011).
2.3.2 DDOS
DDOS stands distributed denial-of-service. It attack a network to become unavailable to planned
user with the help of other computers. DOS attack is done by large number of systems improve
that server usage and denial of service of that system. The server can be targeted by many
(Sridevi & Dr.Manjaiah D.H, 2012).
10
Now the user can type the URL bankofamerica.com this URL will redirect to our fake webpage.
2.3.1.2 Prevention of DNS spoofing:
Few idea for away from DNS spoofing. The ideas are given below
Implement of DNS spoofing detection techniques- Some product named as Xarp, which
is used to product the ARP storehouse from DNS spoofing.
Work with encrypted data networks- SSL/TLS will use for decrease the DNS spoofing by
usage of end-to-end encryption.
Use DNSSEC-DNSSEC have the digital DNS record for data security (Gupta, Kumar,
Tomar & Verma, 2016) (LI, CAO, LIU & LEI, 2011).
2.3.2 DDOS
DDOS stands distributed denial-of-service. It attack a network to become unavailable to planned
user with the help of other computers. DOS attack is done by large number of systems improve
that server usage and denial of service of that system. The server can be targeted by many
(Sridevi & Dr.Manjaiah D.H, 2012).
10
.
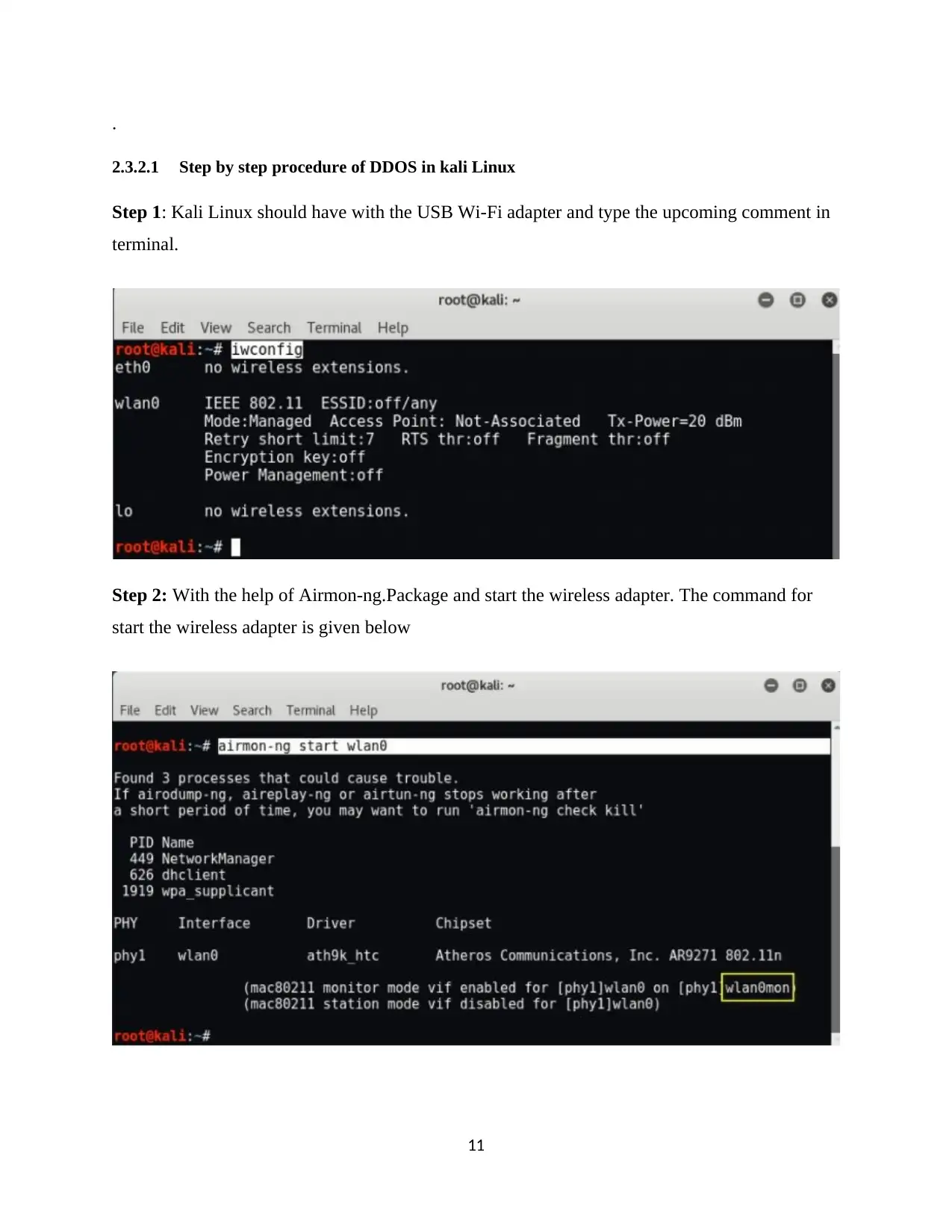
2.3.2.1 Step by step procedure of DDOS in kali Linux
Step 1: Kali Linux should have with the USB Wi-Fi adapter and type the upcoming comment in
terminal.
Step 2: With the help of Airmon-ng.Package and start the wireless adapter. The command for
start the wireless adapter is given below
11
2.3.2.1 Step by step procedure of DDOS in kali Linux
Step 1: Kali Linux should have with the USB Wi-Fi adapter and type the upcoming comment in
terminal.
Step 2: With the help of Airmon-ng.Package and start the wireless adapter. The command for
start the wireless adapter is given below
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 33
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





