CSI3208/CSI5208 Ethical Hacking: VM Case Study, Flags & Security
VerifiedAdded on 2023/06/03
|21
|2782
|194
Report
AI Summary
This report provides a detailed analysis of an ethical hacking case study involving a virtual machine. It focuses on exploiting five flags, each representing a different aspect of system compromise, including web server content evaluation, web shell analysis, password cracking, TCP port scanning, and Linux privilege escalation. The report outlines the methodologies used, the tools employed, and the steps taken to uncover vulnerabilities and obtain root-level privileges. It also includes recommendations for securing systems against similar attacks. The document is contributed by a student and available on Desklib, a platform offering study tools and resources for students.

Ethical Hacking
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
This report concentrates on the five flags, using a case study related to virtual machine. The
concept of ethical hacking is represented here to help the readers. Apart from flags, this
project contains explainstion of web server content, web shell, securing the systems from the
hackers and information related to basic Linux privilege escalation. The explanation
determines that the first flag ensures to do evaluation of web server content, by finding the
administrator's username and password. The other flags ensures to fetch knowledge in terms
of web shells, for cracking the password, for identification of the mistaken passwords
entered on the system with the help of TCP port scanner tool and the basics of Linux
privilege escalation, respectively.
1
This report concentrates on the five flags, using a case study related to virtual machine. The
concept of ethical hacking is represented here to help the readers. Apart from flags, this
project contains explainstion of web server content, web shell, securing the systems from the
hackers and information related to basic Linux privilege escalation. The explanation
determines that the first flag ensures to do evaluation of web server content, by finding the
administrator's username and password. The other flags ensures to fetch knowledge in terms
of web shells, for cracking the password, for identification of the mistaken passwords
entered on the system with the help of TCP port scanner tool and the basics of Linux
privilege escalation, respectively.
1

Table of Contents
1 Project Description...........................................................................................................2
2 Defined methodology and Testing Log...........................................................................2
Flag 1) web server................................................................................................................4
Flag 2) web shells..................................................................................................................6
Flag 3) Password cracker...................................................................................................8
Flag 4) TCP port scanner..................................................................................................14
Flag 5) Privilege..................................................................................................................17
3 Results and Recommendations......................................................................................18
References...............................................................................................................................19
2
1 Project Description...........................................................................................................2
2 Defined methodology and Testing Log...........................................................................2
Flag 1) web server................................................................................................................4
Flag 2) web shells..................................................................................................................6
Flag 3) Password cracker...................................................................................................8
Flag 4) TCP port scanner..................................................................................................14
Flag 5) Privilege..................................................................................................................17
3 Results and Recommendations......................................................................................18
References...............................................................................................................................19
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 Project Description
The idea of this project is to shed some light on a case study which talks about ethical
hacking. The requirements of this project includes that the given system has to be infiltrated
by the user for attaining root level privileges. Nearly five flags will be explained in the report
based on the virtual machine. The characters of each flag will be represented in the report,
where the flags, methods, tools and tevhbiques for ethical hacking are discussed. It is
expected that the flags help to scan the port and help with identification of wrongly entered
password, then password cracking and so on.
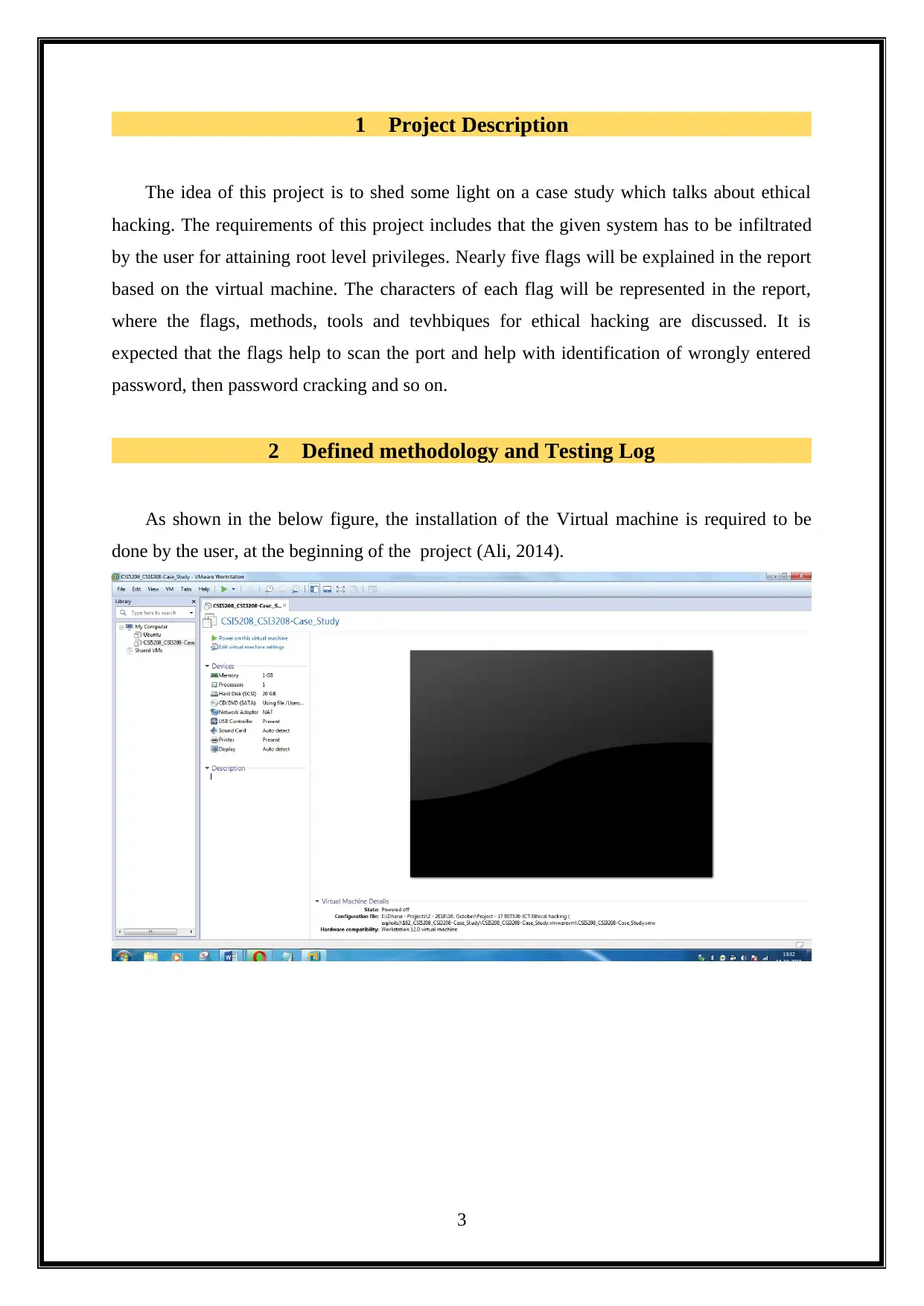
2 Defined methodology and Testing Log
As shown in the below figure, the installation of the Virtual machine is required to be
done by the user, at the beginning of the project (Ali, 2014).
3
The idea of this project is to shed some light on a case study which talks about ethical
hacking. The requirements of this project includes that the given system has to be infiltrated
by the user for attaining root level privileges. Nearly five flags will be explained in the report
based on the virtual machine. The characters of each flag will be represented in the report,
where the flags, methods, tools and tevhbiques for ethical hacking are discussed. It is
expected that the flags help to scan the port and help with identification of wrongly entered
password, then password cracking and so on.
2 Defined methodology and Testing Log
As shown in the below figure, the installation of the Virtual machine is required to be
done by the user, at the beginning of the project (Ali, 2014).
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
Flag 1) web server
Any web server needs space to store the records of the website. The records could be
such as, all the HTML reports, it's related resources, images, audio, video, CSS templates,
JavaScript documents, textual styles and recordings. It is known that such inform ation or
records might be present in the user's system (Buchanan, 2014).
The below section mentions the content of web server.
5
Any web server needs space to store the records of the website. The records could be
such as, all the HTML reports, it's related resources, images, audio, video, CSS templates,
JavaScript documents, textual styles and recordings. It is known that such inform ation or
records might be present in the user's system (Buchanan, 2014).
The below section mentions the content of web server.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Apache httpd 2.4 default layout (apache.org source package):
Apache httpd 2.2 default layout (apache.org source package):
Apache httpd 2.0 default layout (apache.org source package):
6
Apache httpd 2.2 default layout (apache.org source package):
Apache httpd 2.0 default layout (apache.org source package):
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Flag 2) web shells
A web-shell is a pernicious content utilized by an attacker with the purpose to
heighten and keeping up constant access on the bargained web application. The Web-shells
can't assault or have adventure the remote helplessness, so it is dependably the second step of
an assault. The attacker can exploit any regular vulnerabilities. For example, SQL infusion,
RFI, FTP, or even utilizes XSS as a component of social designing assault with a specific end
goal to transfer the malevolent content. The normal usefulness incorporates, however isn't
restricted to shell order execution, code execution, database count and record administration
(Halton and Weaver, n.d.).
Constant Remote Access
The web-shell for the most part contains an indirect access which enables an
aggressor to remotely get to and conceivably control the server whenever needed. This can
leave the attacker with the concern of abusing the helplessness, when each time accessing the
traded off server is required. An aggressor may likewise settle the weakness themselves,
keeping in mind the end goal to guarantee that nobody else will abuse that powerlessness.
Thus, the assailant can stay under the radar and keep away from any collaboration with the
chairman, while acquiring a similar outcome. It is additionally worth specifying that few well
known web shells utilize secret key validation and different strategies to guarantee that just
the assailant transferring the web-shell approaches it. Such strategies incorporate securing the
content to a particular custom HTTP header, particular treat esteems, particular IP addresses,
or a blend of these systems. Most web shells likewise contain code to recognize and square
7
A web-shell is a pernicious content utilized by an attacker with the purpose to
heighten and keeping up constant access on the bargained web application. The Web-shells
can't assault or have adventure the remote helplessness, so it is dependably the second step of
an assault. The attacker can exploit any regular vulnerabilities. For example, SQL infusion,
RFI, FTP, or even utilizes XSS as a component of social designing assault with a specific end
goal to transfer the malevolent content. The normal usefulness incorporates, however isn't
restricted to shell order execution, code execution, database count and record administration
(Halton and Weaver, n.d.).
Constant Remote Access
The web-shell for the most part contains an indirect access which enables an
aggressor to remotely get to and conceivably control the server whenever needed. This can
leave the attacker with the concern of abusing the helplessness, when each time accessing the
traded off server is required. An aggressor may likewise settle the weakness themselves,
keeping in mind the end goal to guarantee that nobody else will abuse that powerlessness.
Thus, the assailant can stay under the radar and keep away from any collaboration with the
chairman, while acquiring a similar outcome. It is additionally worth specifying that few well
known web shells utilize secret key validation and different strategies to guarantee that just
the assailant transferring the web-shell approaches it. Such strategies incorporate securing the
content to a particular custom HTTP header, particular treat esteems, particular IP addresses,
or a blend of these systems. Most web shells likewise contain code to recognize and square
7

web indexes from posting the shell and as a result, boycotting the area or server, where the
web application is facilitated on, as stealth is vital.
Privilege Escalation
Except if a server is misconfigured, the web shell will be keep running under the web
server's client authorizations, which are restricted. Utilizing a web-shell, an assailant can
endeavour to perform benefit acceleration assaults by abusing neighbourhood vulnerabilities
on the framework to accept root benefits, which in Linux and other UNIX-based working
frameworks is the 'super-client'. With access to the root account, the assailant can basically
do anything on the framework including introducing programming, evolving consents,
including and expelling clients, taking passwords, perusing messages and the sky is the limit
from there.
Launching and Pivoting Attacks
A web-shell can be used to rotate inside or outside the system. The attacker has to
screen the movement of the system on the framework, nect it checks the inner system for
identifying the live action of the system, and lists the firewalls and within the system sets the
switches. This type of process could need many days or several months for the attacker to be
under the radar, and retrives the minimum measure which are considered as conceivable. As
soon as the attacker's access is found, they could easily take their next action. Hence, the
traded off framework can likewise be used to attack or sweep the focuses for dwelling outside
the system. Zombie
The other utilization of web-shells indicates botnet's servers part. The botnet indicates a
system that contains the traded off frameworks which the attacker can control, either to use
themselves, or for renting it to various other offenders. The web shell is an indirect access
that has connection with the C&C server from which it could take help for execution based
on the directions or guidelines. Specifically, such a step is used in the DDoS attacks, as it
needs the sweeping measures for the transmission capacity. Therefore, the attackers will not
have any enthusiasm to hurt, or take anything off from the framework, where the web shell
was conveyed. Instead, it could use its assets at whatever point necessary, as represented in
the following image.
8
web application is facilitated on, as stealth is vital.
Privilege Escalation
Except if a server is misconfigured, the web shell will be keep running under the web
server's client authorizations, which are restricted. Utilizing a web-shell, an assailant can
endeavour to perform benefit acceleration assaults by abusing neighbourhood vulnerabilities
on the framework to accept root benefits, which in Linux and other UNIX-based working
frameworks is the 'super-client'. With access to the root account, the assailant can basically
do anything on the framework including introducing programming, evolving consents,
including and expelling clients, taking passwords, perusing messages and the sky is the limit
from there.
Launching and Pivoting Attacks
A web-shell can be used to rotate inside or outside the system. The attacker has to
screen the movement of the system on the framework, nect it checks the inner system for
identifying the live action of the system, and lists the firewalls and within the system sets the
switches. This type of process could need many days or several months for the attacker to be
under the radar, and retrives the minimum measure which are considered as conceivable. As
soon as the attacker's access is found, they could easily take their next action. Hence, the
traded off framework can likewise be used to attack or sweep the focuses for dwelling outside
the system. Zombie
The other utilization of web-shells indicates botnet's servers part. The botnet indicates a
system that contains the traded off frameworks which the attacker can control, either to use
themselves, or for renting it to various other offenders. The web shell is an indirect access
that has connection with the C&C server from which it could take help for execution based
on the directions or guidelines. Specifically, such a step is used in the DDoS attacks, as it
needs the sweeping measures for the transmission capacity. Therefore, the attackers will not
have any enthusiasm to hurt, or take anything off from the framework, where the web shell
was conveyed. Instead, it could use its assets at whatever point necessary, as represented in
the following image.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
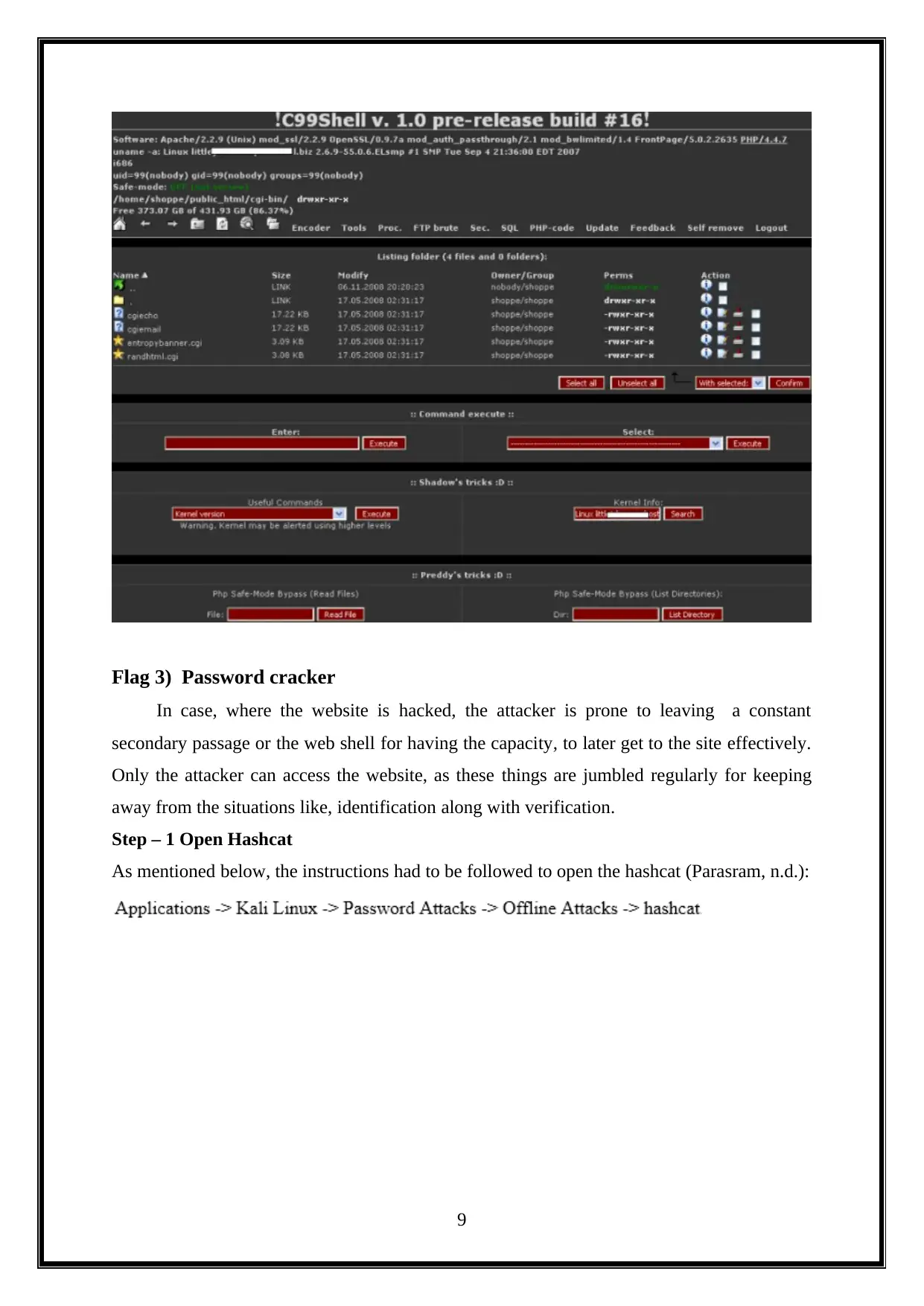
Flag 3) Password cracker
In case, where the website is hacked, the attacker is prone to leaving a constant
secondary passage or the web shell for having the capacity, to later get to the site effectively.
Only the attacker can access the website, as these things are jumbled regularly for keeping
away from the situations like, identification along with verification.
Step – 1 Open Hashcat
As mentioned below, the instructions had to be followed to open the hashcat (Parasram, n.d.):
9
In case, where the website is hacked, the attacker is prone to leaving a constant
secondary passage or the web shell for having the capacity, to later get to the site effectively.
Only the attacker can access the website, as these things are jumbled regularly for keeping
away from the situations like, identification along with verification.
Step – 1 Open Hashcat
As mentioned below, the instructions had to be followed to open the hashcat (Parasram, n.d.):
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
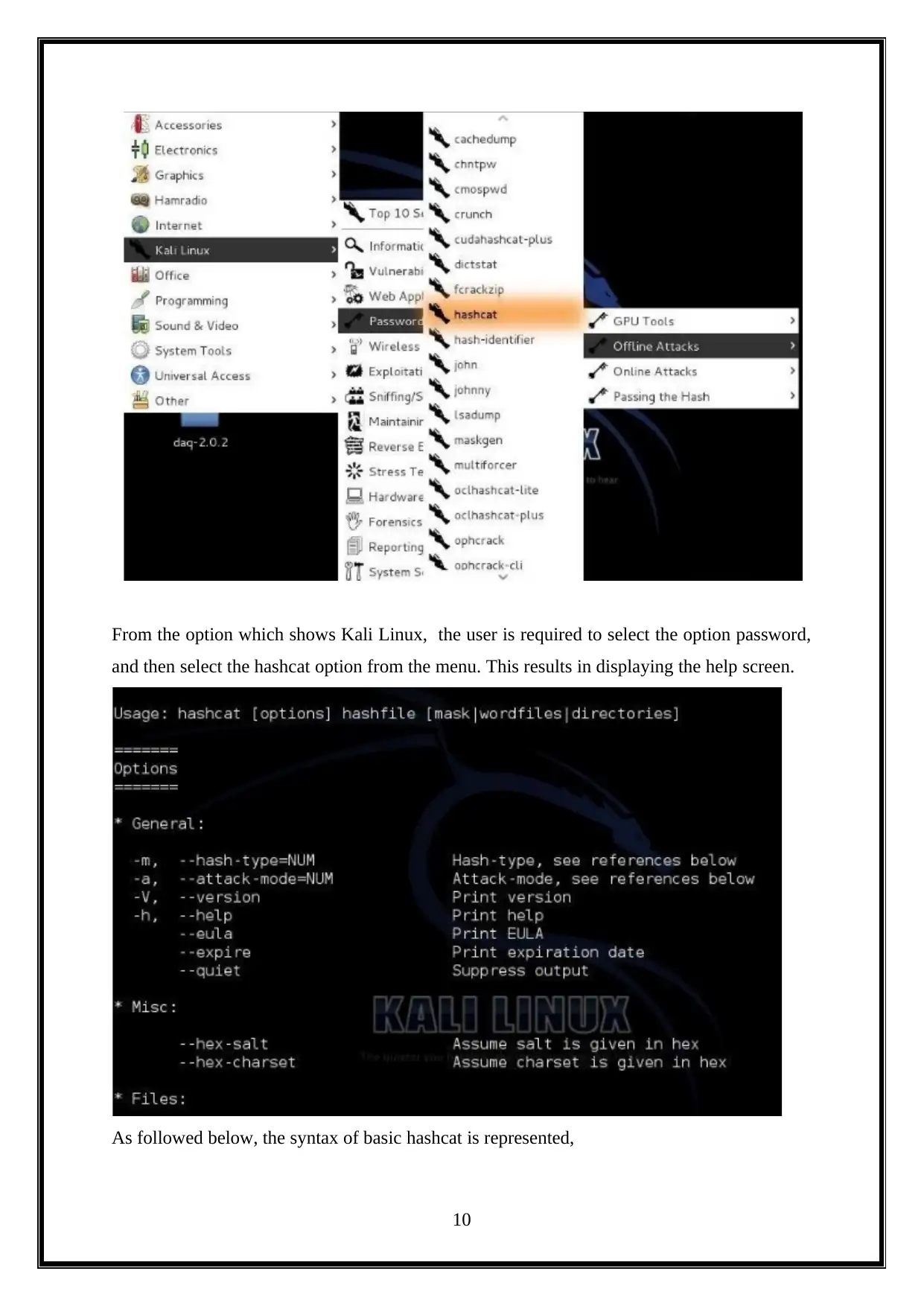
From the option which shows Kali Linux, the user is required to select the option password,
and then select the hashcat option from the menu. This results in displaying the help screen.
As followed below, the syntax of basic hashcat is represented,
10
and then select the hashcat option from the menu. This results in displaying the help screen.
As followed below, the syntax of basic hashcat is represented,
10
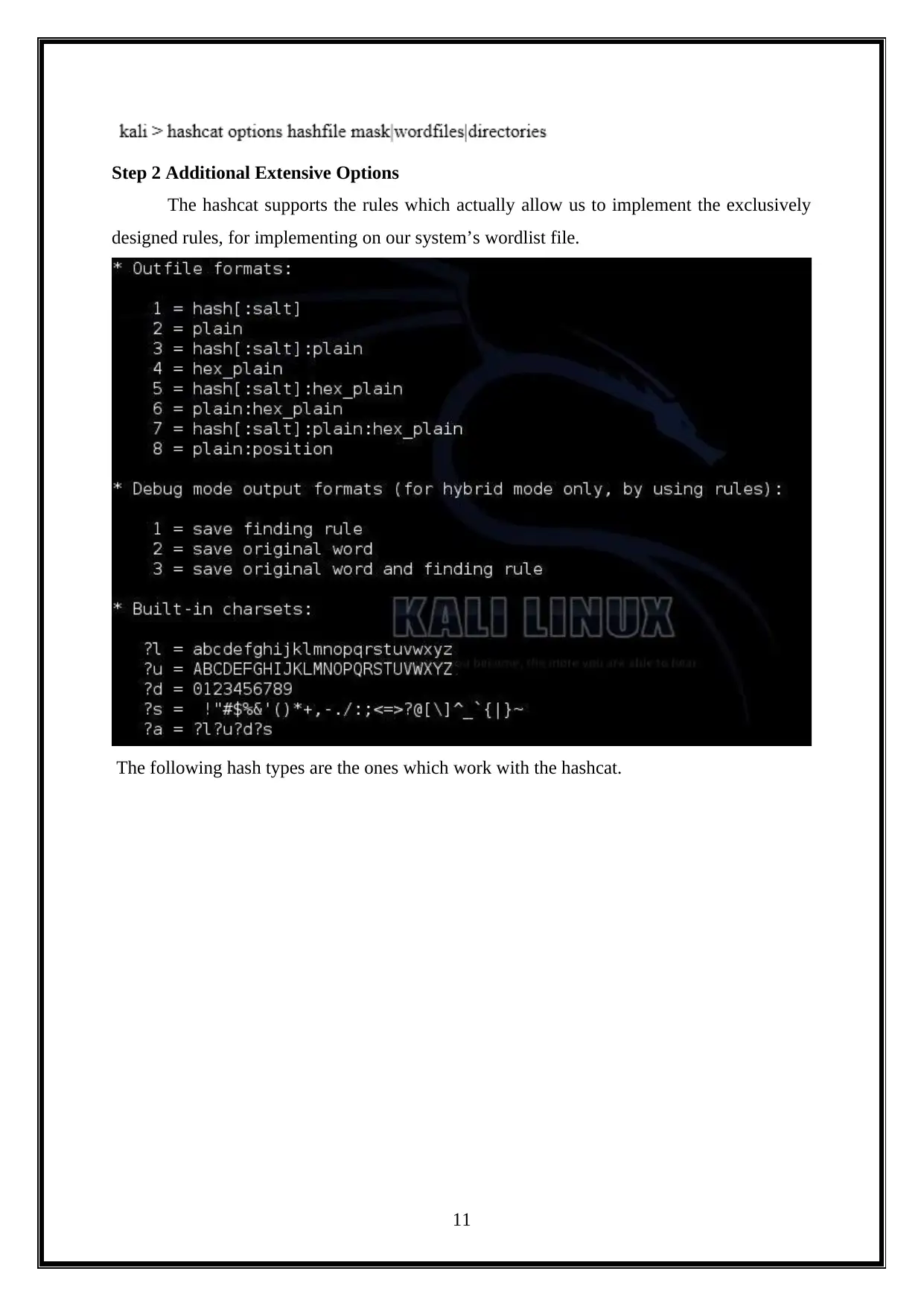
Step 2 Additional Extensive Options
The hashcat supports the rules which actually allow us to implement the exclusively
designed rules, for implementing on our system’s wordlist file.
The following hash types are the ones which work with the hashcat.
11
The hashcat supports the rules which actually allow us to implement the exclusively
designed rules, for implementing on our system’s wordlist file.
The following hash types are the ones which work with the hashcat.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





