CSI3208/CSI5208 Ethical Hacking & Defence: Comprehensive Report
VerifiedAdded on 2023/06/04
|14
|3249
|79
Report
AI Summary
This report details the methodologies and testing involved in ethical hacking and defense, focusing on identifying vulnerabilities and securing systems. It covers various aspects such as web server security, web shell analysis, password cracking, and TCP port scanning using Nmap. The report outlines techniques for privilege escalation and methods to counter potential attacks. The flags captured during the penetration testing are included, along with an analysis of system weaknesses and recommendations for improving overall security. The document provides a comprehensive overview of the ethical hacking process and its importance in protecting organizations from cyber threats.

Ethical Hacking
and Defence
and Defence
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

EXECUTIVE SUMMARY
Ethical Hacking is also referred with a term, White Hat Hacking which is practiced by the
certified ethical hacking firm or an individual for identifying the possible threats or
vulnerabilities for system security, which is exploited by the illegal hackers or also referred as
the Black Hat Hackers. Today the organizations and the government firms require ethical
hackers, for combating with the increasing IT security threats. Thus it has lead these
organizations to hire the “ethical hackers”, for exploring their company’s system and identify the
potential weaknesses. The White Hat Hackers help to know how the Black Hat Hackers damage
the system and suggests protective measures from such harms. Further, this report corresponds
with the flags, web shells and system security.
Ethical Hacking is also referred with a term, White Hat Hacking which is practiced by the
certified ethical hacking firm or an individual for identifying the possible threats or
vulnerabilities for system security, which is exploited by the illegal hackers or also referred as
the Black Hat Hackers. Today the organizations and the government firms require ethical
hackers, for combating with the increasing IT security threats. Thus it has lead these
organizations to hire the “ethical hackers”, for exploring their company’s system and identify the
potential weaknesses. The White Hat Hackers help to know how the Black Hat Hackers damage
the system and suggests protective measures from such harms. Further, this report corresponds
with the flags, web shells and system security.

Table of Contents
1. INTRODUCTION.............................................................................................................................1
2. METHODOLOGY AND TESTING................................................................................................1
Flag 1-WEB SERVER...........................................................................................................................3
Flag 2- WEB SHELLS..........................................................................................................................3
Flag 3- PASSWORD CRACKER.........................................................................................................4
Flag 4- TCP PORT SCANNER–Nmap................................................................................................6
Flag 5- PRIVILEGES............................................................................................................................9
3. CONCLUSION..................................................................................................................................9
REFERENCES........................................................................................................................................10
1. INTRODUCTION.............................................................................................................................1
2. METHODOLOGY AND TESTING................................................................................................1
Flag 1-WEB SERVER...........................................................................................................................3
Flag 2- WEB SHELLS..........................................................................................................................3
Flag 3- PASSWORD CRACKER.........................................................................................................4
Flag 4- TCP PORT SCANNER–Nmap................................................................................................6
Flag 5- PRIVILEGES............................................................................................................................9
3. CONCLUSION..................................................................................................................................9
REFERENCES........................................................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1. INTRODUCTION
Today, the organizations face constant Cyber-Attacks ("Why Businesses Need Ethical
Hackers?", 2018). This enforces the need to secure the organizations from harmful attacks and
the ethical hackers have the capacity to secure the computer and the network of the
organizations.
Hence, ethical hacking comes into picture, which is also referred with a term, White Hat Hacking
and it is practiced by the certified ethical hacking firm or an individual for identifying the
possible threats or vulnerabilities for system security, which is exploited by the illegal hackers or
also referred as the Black Hat Hackers (Gupta, 2018). The ethical hackers try their best for
determining, how the hacker will attack your network. On the other hand, they are trying their
best to figure out a way to secure your system and check whether the system is protected
effectively or not. They perform all the tests with the permission of the organizations (Hanks,
2017).
The objective of this report is to study the flags, web shells, various privileges and system
security.
2. METHODOLOGY AND TESTING
The ethical hacking is conducted which contains manual processes, such as installing the
virtual machine and so on. However, it also contains various tools for testing and for automating
several tasks. But, the general methodologies and understanding takes places behind the process
of the web server’s virtual machine.
1
Today, the organizations face constant Cyber-Attacks ("Why Businesses Need Ethical
Hackers?", 2018). This enforces the need to secure the organizations from harmful attacks and
the ethical hackers have the capacity to secure the computer and the network of the
organizations.
Hence, ethical hacking comes into picture, which is also referred with a term, White Hat Hacking
and it is practiced by the certified ethical hacking firm or an individual for identifying the
possible threats or vulnerabilities for system security, which is exploited by the illegal hackers or
also referred as the Black Hat Hackers (Gupta, 2018). The ethical hackers try their best for
determining, how the hacker will attack your network. On the other hand, they are trying their
best to figure out a way to secure your system and check whether the system is protected
effectively or not. They perform all the tests with the permission of the organizations (Hanks,
2017).
The objective of this report is to study the flags, web shells, various privileges and system
security.
2. METHODOLOGY AND TESTING
The ethical hacking is conducted which contains manual processes, such as installing the
virtual machine and so on. However, it also contains various tools for testing and for automating
several tasks. But, the general methodologies and understanding takes places behind the process
of the web server’s virtual machine.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
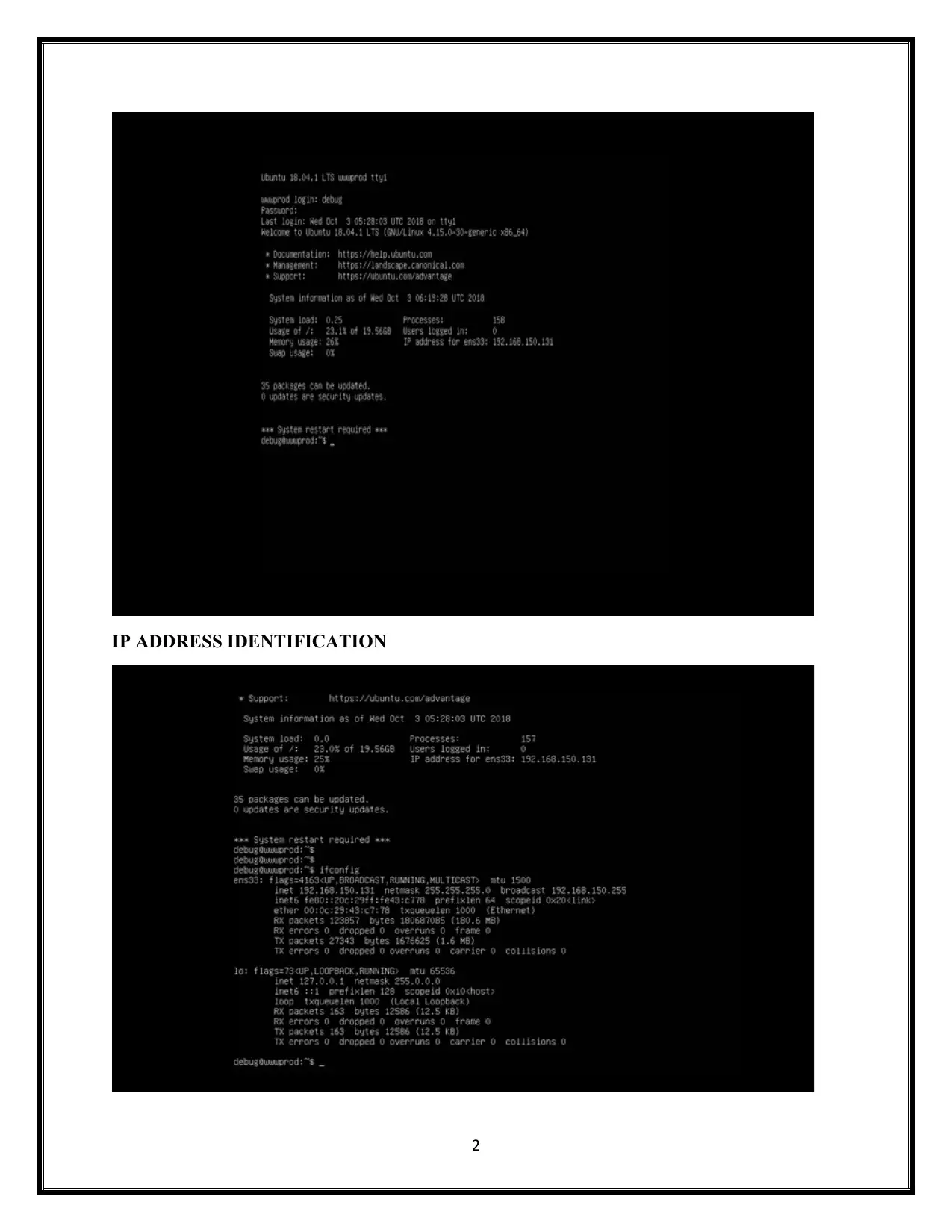
IP ADDRESS IDENTIFICATION
2
2

Flag 1-WEB SERVER
The main purpose of the web server refers to displaying the website content. It functions
depending on the requests for the website, where the requested is accepted only if request is sent
through the web browser’s URL or the web address bar. This request is sent to the internet to see
the requested web page. This process take place with the help of DNS (Domain Name Server)
which converts the provided URL into an IP address and directs to the respective web server
("Definition of Web Server", 2018).
The main objective observed here is to establish communication between various servers
available across internet, and apache has become the highly used web server these days (Rouse,
2018). The web server can face various attacks like, DOS attack, Directory Traversal, Phishing
Attack, Website Defacement and Misconfiguration attacks.
The methodology to resolve the attacks includes, vulnerability scanning, password
attacks like dictionary attacks, then the counter measures like regularly updating and fixing the
web servers, securing the configuration files, scanning applications which run on the web server,
using secure protocols, installing antivirus and updating it, updating the OS and software ("Web
Server and its Types of Attacks", 2018).
Flag 2- WEB SHELLS
The web shells are utilized by the attackers for harming the victims with malicious script,
for escalating and maintaining trusted access on the compromised web application. The web
shell has no capacity to attack the remote vulnerability thus it is the secondary attacking step
known as post-exploitation (Prodromou, 2016).
The administration of web shells for the general benefits integrate the restrictions for web
shell order execution, database count, code execution and IP address accessing records
("Everything You Need To Know About Web Shells", 2017).
Persistent Remote Access
The web shell’s details are explained here. The web shells could be utilized for obtaining
the access which is unauthorized and this could even direct to have comprise with the large
network. In such a situation, the attacker might be left helpless while trying to access the
necessary server. But, the attacker won’t stop just here, they will try their best efforts to get
3
The main purpose of the web server refers to displaying the website content. It functions
depending on the requests for the website, where the requested is accepted only if request is sent
through the web browser’s URL or the web address bar. This request is sent to the internet to see
the requested web page. This process take place with the help of DNS (Domain Name Server)
which converts the provided URL into an IP address and directs to the respective web server
("Definition of Web Server", 2018).
The main objective observed here is to establish communication between various servers
available across internet, and apache has become the highly used web server these days (Rouse,
2018). The web server can face various attacks like, DOS attack, Directory Traversal, Phishing
Attack, Website Defacement and Misconfiguration attacks.
The methodology to resolve the attacks includes, vulnerability scanning, password
attacks like dictionary attacks, then the counter measures like regularly updating and fixing the
web servers, securing the configuration files, scanning applications which run on the web server,
using secure protocols, installing antivirus and updating it, updating the OS and software ("Web
Server and its Types of Attacks", 2018).
Flag 2- WEB SHELLS
The web shells are utilized by the attackers for harming the victims with malicious script,
for escalating and maintaining trusted access on the compromised web application. The web
shell has no capacity to attack the remote vulnerability thus it is the secondary attacking step
known as post-exploitation (Prodromou, 2016).
The administration of web shells for the general benefits integrate the restrictions for web
shell order execution, database count, code execution and IP address accessing records
("Everything You Need To Know About Web Shells", 2017).
Persistent Remote Access
The web shell’s details are explained here. The web shells could be utilized for obtaining
the access which is unauthorized and this could even direct to have comprise with the large
network. In such a situation, the attacker might be left helpless while trying to access the
necessary server. But, the attacker won’t stop just here, they will try their best efforts to get
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

access and get powerful by gaining the access. However, it is required that the attackers has to be
in a radar state to be safe, when trying out their efforts and to get better results. The popularly
known web shells uses the secret key validation, to promise that the attacker is transferring the
approaches of web shell. Certain parts of the web-shell has indirect access and it allows the
attackers to remotely get access and control the server as and when required. There exists certain
web shells which uses the secret key validation and various strategies. Similar strategies help to
customize the HTTP header, especially the values and the IP addresses are treated well. The web
shells contains code which can identify the code and square web indexes. Thus, it results in
rejecting the server which has the facility of web application ("Web Shells – Threat Awareness
and Guidance", 2017).
Zombie
Botnet refers to a network of negotiated systems which the attacker controls, either for
his own need or for leasing to the other criminals. Making servers part of the botnet is the other
usage of web shells. The web shell is associated with C&C server i.e., command and control
server, which takes the commands for executing the instructions. For the distributed-denial-of-
service (DDoS) attacks, a setup is arranged that needs high bandwidth. In such a situation, the
attackers won’t have any interest to steal or harm the data of the system, when the web shell
deployment takes place. Rather, it just uses the required resources as and when there is the
necessity.
The web server that is associated with internet can access zombie which is compromised
with the attacker or the hacker, on the other hand, the program like Trojan horse or any computer
virus could be utilized for performing the malicious activities and is helpful for other remote
direction.
Pivoting Attack’s Launch
The test such as penetration test could be utilized to pivot whenever required to get
through the system, for gaining the system’s access and this continues with the rest of the system
so as to continue framework’s pivoting test. It is possible to access them for utilizing it for the
pivoting avenues. This report presents the 5 basically utilized tests which helps in examining the
4
in a radar state to be safe, when trying out their efforts and to get better results. The popularly
known web shells uses the secret key validation, to promise that the attacker is transferring the
approaches of web shell. Certain parts of the web-shell has indirect access and it allows the
attackers to remotely get access and control the server as and when required. There exists certain
web shells which uses the secret key validation and various strategies. Similar strategies help to
customize the HTTP header, especially the values and the IP addresses are treated well. The web
shells contains code which can identify the code and square web indexes. Thus, it results in
rejecting the server which has the facility of web application ("Web Shells – Threat Awareness
and Guidance", 2017).
Zombie
Botnet refers to a network of negotiated systems which the attacker controls, either for
his own need or for leasing to the other criminals. Making servers part of the botnet is the other
usage of web shells. The web shell is associated with C&C server i.e., command and control
server, which takes the commands for executing the instructions. For the distributed-denial-of-
service (DDoS) attacks, a setup is arranged that needs high bandwidth. In such a situation, the
attackers won’t have any interest to steal or harm the data of the system, when the web shell
deployment takes place. Rather, it just uses the required resources as and when there is the
necessity.
The web server that is associated with internet can access zombie which is compromised
with the attacker or the hacker, on the other hand, the program like Trojan horse or any computer
virus could be utilized for performing the malicious activities and is helpful for other remote
direction.
Pivoting Attack’s Launch
The test such as penetration test could be utilized to pivot whenever required to get
through the system, for gaining the system’s access and this continues with the rest of the system
so as to continue framework’s pivoting test. It is possible to access them for utilizing it for the
pivoting avenues. This report presents the 5 basically utilized tests which helps in examining the
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

access of pivoting for forwarding the SSH local port, SSH local port forwarding, Net cat relays,
bad proxy HTTP of the relatively difficult and for following the attack back to its source.
Privilege Escalations
Under the user permission, the web shell will run till the server is misconfigured, where
the permissions must be limited. With the utilization of web-shell, the attacker tries to perform
the privilege escalation attacks where the system's local vulnerabilities are exploited with the
assumption of the root privileges. But, in the Linux and the other UNIX-based OS has the ‘super-
user’. If the attackers have the access of the root account, they could do possibly any activity on
the victim's system such as, software installation, permission changes, accessing and reading the
emails, password theft, addition and removal of users etc (Prodromou, 2016).
The web shell server is the misconfigured it will keep the client authorizations of the web
server which the restricted. The web shells they can utilizing the vulnerabilities of neighborhood
of the framework to accept the UNIX based on the working on the 'super-client'. The framework
that includes the expelling clients, taking passwords, perusing messages and the sky is the limit
from there. Once we have a limited shell it is useful to escalate that shell privileges.
Flag 3- PASSWORD CRACKER
Here, at the end of the day, the client can amend the secret key as it's a specialty of
acquiring the offered access to the framework which could confirmation the strategies for the
secured access. For instance, the making of Chanel indicator, her the strength of the secret
password are utilized, while setting the passwords. The strength of the secret password is
represented in the following image, where it has every single passwords that are recorded. It is
then possible to store the hashes in the database we can look at the secret key hashed in the
database. At that point, it is needed to have the secret password key, if a match is discovered and
the database of the secret password cracking system.
The web shell is deobfuscated here.
The preg_replace consists of 3 contentions such as, the regex, subject of the substitution
and it contains the modifier that could access everything in the substitution as the PHP code.
This subsequently looks like the following code, preg_replace ("/.*/", eval("\x65\x76\x61… \
x29\x3B"), ".");
5
bad proxy HTTP of the relatively difficult and for following the attack back to its source.
Privilege Escalations
Under the user permission, the web shell will run till the server is misconfigured, where
the permissions must be limited. With the utilization of web-shell, the attacker tries to perform
the privilege escalation attacks where the system's local vulnerabilities are exploited with the
assumption of the root privileges. But, in the Linux and the other UNIX-based OS has the ‘super-
user’. If the attackers have the access of the root account, they could do possibly any activity on
the victim's system such as, software installation, permission changes, accessing and reading the
emails, password theft, addition and removal of users etc (Prodromou, 2016).
The web shell server is the misconfigured it will keep the client authorizations of the web
server which the restricted. The web shells they can utilizing the vulnerabilities of neighborhood
of the framework to accept the UNIX based on the working on the 'super-client'. The framework
that includes the expelling clients, taking passwords, perusing messages and the sky is the limit
from there. Once we have a limited shell it is useful to escalate that shell privileges.
Flag 3- PASSWORD CRACKER
Here, at the end of the day, the client can amend the secret key as it's a specialty of
acquiring the offered access to the framework which could confirmation the strategies for the
secured access. For instance, the making of Chanel indicator, her the strength of the secret
password are utilized, while setting the passwords. The strength of the secret password is
represented in the following image, where it has every single passwords that are recorded. It is
then possible to store the hashes in the database we can look at the secret key hashed in the
database. At that point, it is needed to have the secret password key, if a match is discovered and
the database of the secret password cracking system.
The web shell is deobfuscated here.
The preg_replace consists of 3 contentions such as, the regex, subject of the substitution
and it contains the modifier that could access everything in the substitution as the PHP code.
This subsequently looks like the following code, preg_replace ("/.*/", eval("\x65\x76\x61… \
x29\x3B"), ".");
5

Whereas, the second parameter could easily access the whole PHP code. This is by virtue
of these announcements we can break game plans to interpret the PHP, and the character of the
hexadecimal documentation. . For example, \x65 would be an e since it says so in the ASCII
table. Physically changing over this string would be a touch of work, so we let PHP do it:
Echo "\x65\x76\x61… \x29\x3B";
Verification of Bypassing
The first code contains $auth_pass for web shell's validation.
Here, the MD5 accomplishes over the posted pass parameter, and it monitors the
$auth_pass. The Plain MD5s are basically not extremely secure method for storing the
passwords. However, most importantly, the MD5 provides instance access and helps to register
hashes almost in billions, for every single second and it attempts to save the power of the secret
password. Along with this, the MD5 aggregates for some, powerless passwords is as of now on
the web and can be found by a brisk Google look (Aulds, 2016).
Our software engineer has picked a very nice mystery password, and I was not capable
part it. Regardless, there is another way to deal with access the web shell now that we have the
source code. As it ought to be clear in the code it sets a specific treat when you get the mystery
word right. It checks the treat and if you have it wrong it considers wsoLogin to show to you a
login page and leave the substance. Else it continues with the web shell code. The treat accepted
have the MD5 of the hostname as key, and the $auth_pass substance as substance. Luckily, we
know both these characteristics and can make our own treat to get to the web shell.
6
of these announcements we can break game plans to interpret the PHP, and the character of the
hexadecimal documentation. . For example, \x65 would be an e since it says so in the ASCII
table. Physically changing over this string would be a touch of work, so we let PHP do it:
Echo "\x65\x76\x61… \x29\x3B";
Verification of Bypassing
The first code contains $auth_pass for web shell's validation.
Here, the MD5 accomplishes over the posted pass parameter, and it monitors the
$auth_pass. The Plain MD5s are basically not extremely secure method for storing the
passwords. However, most importantly, the MD5 provides instance access and helps to register
hashes almost in billions, for every single second and it attempts to save the power of the secret
password. Along with this, the MD5 aggregates for some, powerless passwords is as of now on
the web and can be found by a brisk Google look (Aulds, 2016).
Our software engineer has picked a very nice mystery password, and I was not capable
part it. Regardless, there is another way to deal with access the web shell now that we have the
source code. As it ought to be clear in the code it sets a specific treat when you get the mystery
word right. It checks the treat and if you have it wrong it considers wsoLogin to show to you a
login page and leave the substance. Else it continues with the web shell code. The treat accepted
have the MD5 of the hostname as key, and the $auth_pass substance as substance. Luckily, we
know both these characteristics and can make our own treat to get to the web shell.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

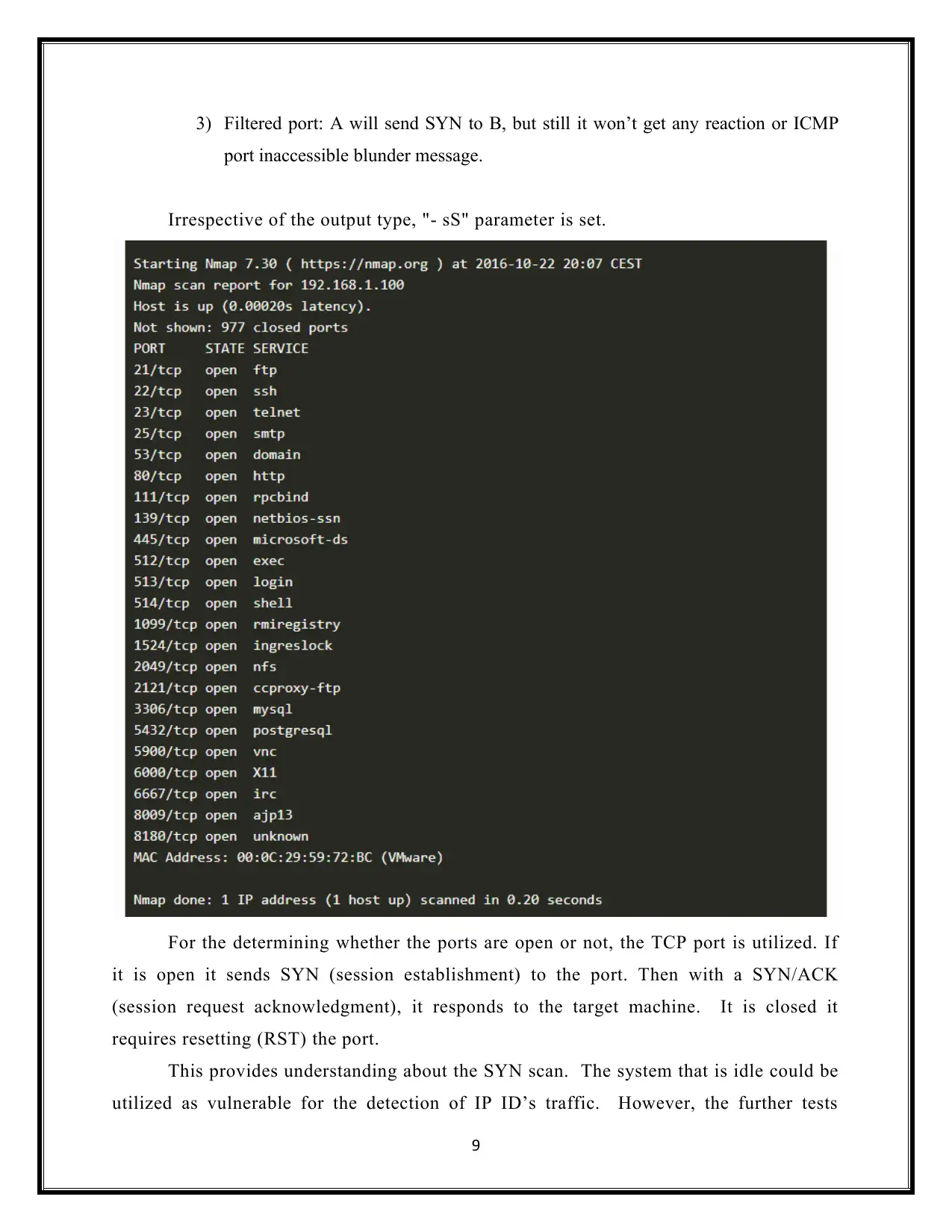
Flag 4- TCP PORT SCANNER–Nmap
Here, the Nmap tool is a web interface which is popular for executing with
appropriate parameters for maximizing both speeding up and increasing the accuracy.
The every single port is scanned where it sends the packets which listens to its
replies and completes the port’s scan. The method of scanning is exclaimed to be 'SYN
scan. This actually sends each of the port’s address to the TCP SYN packet.
The inventory UDP ports is used to support Nmap. Along with UDP scan, -sU
option is activated. It is possible to combine TCP scan type like SYN scan (-sS), for
checking the protocol at run time.
The targeted ports which contain the UDP scan works by sending a every UDP
packets on the scanner port.
TCP 3-Way Handshake
7
Here, the Nmap tool is a web interface which is popular for executing with
appropriate parameters for maximizing both speeding up and increasing the accuracy.
The every single port is scanned where it sends the packets which listens to its
replies and completes the port’s scan. The method of scanning is exclaimed to be 'SYN
scan. This actually sends each of the port’s address to the TCP SYN packet.
The inventory UDP ports is used to support Nmap. Along with UDP scan, -sU
option is activated. It is possible to combine TCP scan type like SYN scan (-sS), for
checking the protocol at run time.
The targeted ports which contain the UDP scan works by sending a every UDP
packets on the scanner port.
TCP 3-Way Handshake
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

For understanding such a sweep it requires to be supportive for reviving the TCP’s
3 step handshake hypothesis as it communicates in a way that the correlation of TCP
starts. It is observed that the TCP/IP network connection is beneficial and helps to
establish communication with the three-way handshake method. This method is utilized
by the local host/client and server.
The TCP’s 3 step handshake needs the actual data communication of the server
and the client, for start exchanging the packets of SYN and ACK. Hence for the
establishment of connection, the TCP makes use of this method, which further establishes
SYN connection. It is established when the client sends the open active SYN for the
server. A rainbow value such as A is set for the clients which has a sequenced number of
segment that could be used by the clients. As soon as A receives the flag, the ACK is sent
to B and finally the ACK is sent to the B and forms the TCP connection attachment. In
case where the A framework requires setting up connection with the B framework, here
SYN is sent by A framework to the B framework and as B receives this it immediately
forwards it to A framework that gets SYN-ACK.
TCP Scan
The following takes place at the time of TCP scanning:
1) Open port: A will send SYN to B, then B reacts with SYN-ACK;
2) Closed port: A will send SYN to B and then B reacts with RST-ACK (Reset-
Acknowledgment);
8
3 step handshake hypothesis as it communicates in a way that the correlation of TCP
starts. It is observed that the TCP/IP network connection is beneficial and helps to
establish communication with the three-way handshake method. This method is utilized
by the local host/client and server.
The TCP’s 3 step handshake needs the actual data communication of the server
and the client, for start exchanging the packets of SYN and ACK. Hence for the
establishment of connection, the TCP makes use of this method, which further establishes
SYN connection. It is established when the client sends the open active SYN for the
server. A rainbow value such as A is set for the clients which has a sequenced number of
segment that could be used by the clients. As soon as A receives the flag, the ACK is sent
to B and finally the ACK is sent to the B and forms the TCP connection attachment. In
case where the A framework requires setting up connection with the B framework, here
SYN is sent by A framework to the B framework and as B receives this it immediately
forwards it to A framework that gets SYN-ACK.
TCP Scan
The following takes place at the time of TCP scanning:
1) Open port: A will send SYN to B, then B reacts with SYN-ACK;
2) Closed port: A will send SYN to B and then B reacts with RST-ACK (Reset-
Acknowledgment);
8
3) Filtered port: A will send SYN to B, but still it won’t get any reaction or ICMP
port inaccessible blunder message.
Irrespective of the output type, "- sS" parameter is set.
For the determining whether the ports are open or not, the TCP port is utilized. If
it is open it sends SYN (session establishment) to the port. Then with a SYN/ACK
(session request acknowledgment), it responds to the target machine. It is closed it
requires resetting (RST) the port.
This provides understanding about the SYN scan. The system that is idle could be
utilized as vulnerable for the detection of IP ID’s traffic. However, the further tests
9
port inaccessible blunder message.
Irrespective of the output type, "- sS" parameter is set.
For the determining whether the ports are open or not, the TCP port is utilized. If
it is open it sends SYN (session establishment) to the port. Then with a SYN/ACK
(session request acknowledgment), it responds to the target machine. It is closed it
requires resetting (RST) the port.
This provides understanding about the SYN scan. The system that is idle could be
utilized as vulnerable for the detection of IP ID’s traffic. However, the further tests
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




