Deakin University SIT379 Ethical Hacking Pentest Report: Group Task
VerifiedAdded on 2022/12/29
|7
|1139
|93
Report
AI Summary
This report details the findings of an ethical hacking penetration test conducted on the digital infrastructure of Digital Assets. The penetration testing approach involved a black box system, simulating an external attack with limited prior knowledge. The report identifies and analyzes vulnerabilities discovered on ports 1521 (Oracle SQL), 5800 (VNC), and 1433 (MySQL), providing percentages for each. The discussion section explains the potential risks associated with each vulnerability, including the ability to shut down the database or remotely control a system. A risk assessment matrix is presented to evaluate the severity and likelihood of each threat. The report concludes with recommendations for mitigating the identified vulnerabilities, such as restricting port access, assigning passwords, and installing software patches to enhance overall system security. This report is contributed by a student and published on Desklib.

Ethical Hacking 1
DEAKIN UNIVERSITY
ETHICAL HACKING
On Track Submission
Task 8.1P Pentest report- Group Task
submitted By”
Ameer Hussain Mohamed Shibly
Tutor:
Rahul Ramdas
Group Members
Bomori Brian Boaz Omori
Sfrehman Syed Faiq Ur Rehman
Ahmohame Ameer Hussain Mohamed Shibly
DEAKIN UNIVERSITY
ETHICAL HACKING
On Track Submission
Task 8.1P Pentest report- Group Task
submitted By”
Ameer Hussain Mohamed Shibly
Tutor:
Rahul Ramdas
Group Members
Bomori Brian Boaz Omori
Sfrehman Syed Faiq Ur Rehman
Ahmohame Ameer Hussain Mohamed Shibly
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Ethical Hacking 2
Ethical Hacking
Introduction
Ethical hacking, also called penetration testing, intrusion or red teaming is a security
control practice that seeks to penetrate into a computer systems without malicious intentions.
Different from what hackers do- aiming at stealing, manipulating, taking control and denying
services to legitimate systems users, ethical hacking is conducted with a sole aim of identifying
and correcting any system’s loopholes. It is a legal activity since it is used by organizations to
strengthen their security posture at the advent of increased sophistication and magnitude of
security incidences. The purpose of this paper is to describe ethical hacking with by
demonstrating practical skills used to conduct penetration testing in digital infrastructures of
Digital Assets. It seeks to find system vulnerabilities that could be successfully exploited by
system hackers and providing mitigation strategies for the same.
Pen Testing Approach
Ethical Hacking
Introduction
Ethical hacking, also called penetration testing, intrusion or red teaming is a security
control practice that seeks to penetrate into a computer systems without malicious intentions.
Different from what hackers do- aiming at stealing, manipulating, taking control and denying
services to legitimate systems users, ethical hacking is conducted with a sole aim of identifying
and correcting any system’s loopholes. It is a legal activity since it is used by organizations to
strengthen their security posture at the advent of increased sophistication and magnitude of
security incidences. The purpose of this paper is to describe ethical hacking with by
demonstrating practical skills used to conduct penetration testing in digital infrastructures of
Digital Assets. It seeks to find system vulnerabilities that could be successfully exploited by
system hackers and providing mitigation strategies for the same.
Pen Testing Approach

Ethical Hacking 3
To access Digital Assets’ digital infrastructure a login was made on the VMLab and pod
booked in the SIT 379 Pentest Project. The testing environment as shown in the diagram above
comprised of a firewall application that demarcate the organization’s intranet with the public
internet. The intranet had an external machine learning on Kali Linux VM machine, while the
internal system comprised of a DVL, Win12r2, Ubuntu, Win16 and Secondo-running machines.
A black box system was conducted on the system. Black box pen-testing is a type of
external penetration test that is done with zero knowledge about the network system. The testers
in this case are required to acquire or learn about the network by applying penetration testing
tools or using the social engineering techniques. As an external penetration test, it is used to
unmask vulnerabilities seen over the internet, that is, threats and vulnerabilities originating from
external networks. Apart from knowing the network addresses 192.168.1.0/24 and 10.1.1.0/28,
no other information we had through prior to the test. Conducting a black box pen-testing implies
that the only access we had was to the hacker’s box (external Kali VM) to remotely exploit
vulnerabilities in the Digital Assets’ digital infrastructure.
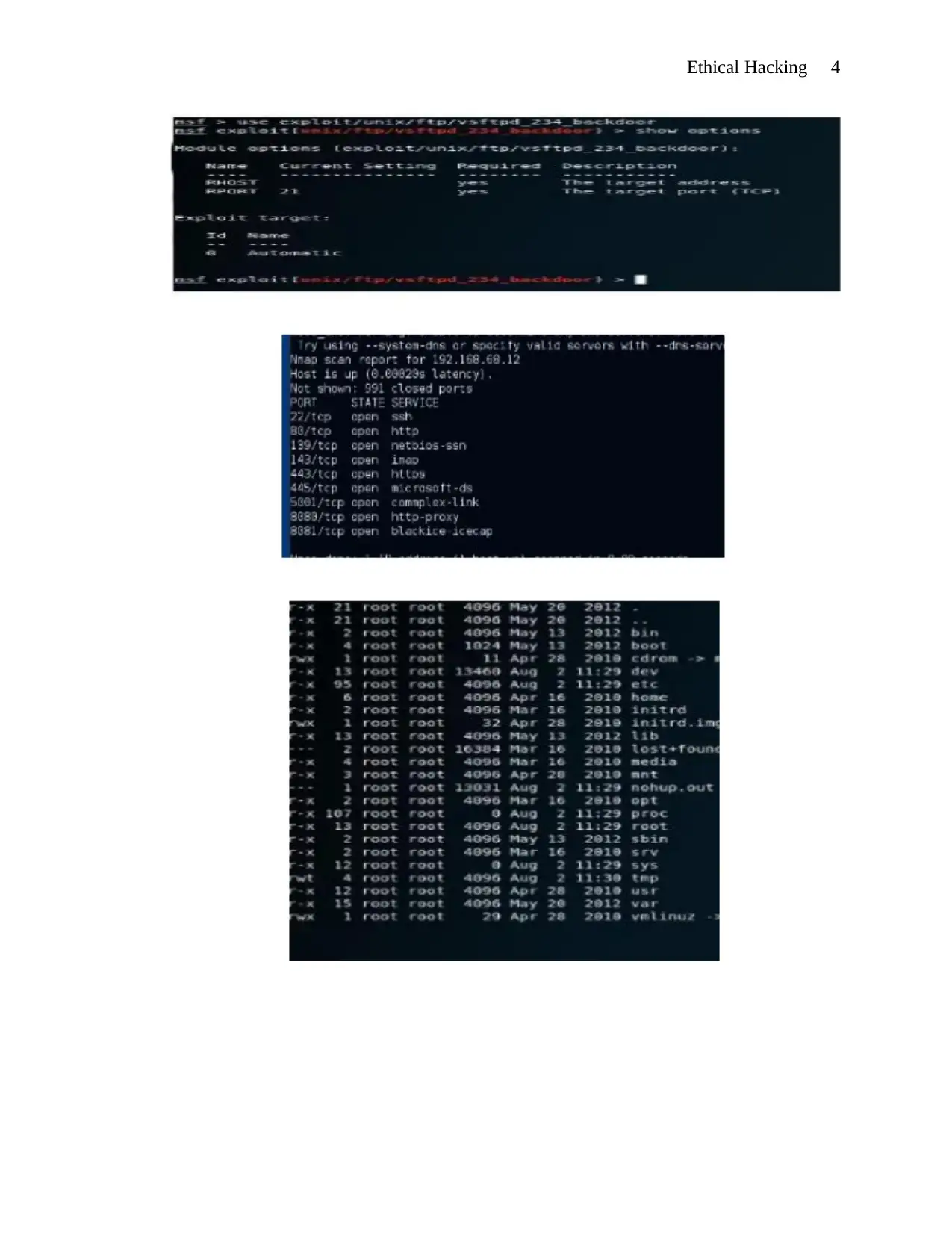
To discover and exploit the network’s vulnerabilities, the command search vsftpd was
run on hacker’s VM machine. This command helped in the location of the exploitations. The
show options from the terminal search were used to locate these vulnerabilities to their
directories. After this, a point of victim machine was setup using the command set RHOST. This
was in a bid to further exploit the vulnerabilities and discover whether all security conditions
were met. Finally, the exploits were run to gain access to the victim machine and points prone to
attacks were identified and accessed through the open ports. The below diagrams visually
represent this procedure.
To access Digital Assets’ digital infrastructure a login was made on the VMLab and pod
booked in the SIT 379 Pentest Project. The testing environment as shown in the diagram above
comprised of a firewall application that demarcate the organization’s intranet with the public
internet. The intranet had an external machine learning on Kali Linux VM machine, while the
internal system comprised of a DVL, Win12r2, Ubuntu, Win16 and Secondo-running machines.
A black box system was conducted on the system. Black box pen-testing is a type of
external penetration test that is done with zero knowledge about the network system. The testers
in this case are required to acquire or learn about the network by applying penetration testing
tools or using the social engineering techniques. As an external penetration test, it is used to
unmask vulnerabilities seen over the internet, that is, threats and vulnerabilities originating from
external networks. Apart from knowing the network addresses 192.168.1.0/24 and 10.1.1.0/28,
no other information we had through prior to the test. Conducting a black box pen-testing implies
that the only access we had was to the hacker’s box (external Kali VM) to remotely exploit
vulnerabilities in the Digital Assets’ digital infrastructure.
To discover and exploit the network’s vulnerabilities, the command search vsftpd was
run on hacker’s VM machine. This command helped in the location of the exploitations. The
show options from the terminal search were used to locate these vulnerabilities to their
directories. After this, a point of victim machine was setup using the command set RHOST. This
was in a bid to further exploit the vulnerabilities and discover whether all security conditions
were met. Finally, the exploits were run to gain access to the victim machine and points prone to
attacks were identified and accessed through the open ports. The below diagrams visually
represent this procedure.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Ethical Hacking 4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Ethical Hacking 5
Results and Findings
The following vulnerabilities and respective percentages were identified.
1. On port 1521 ET POLICY inbound to the Oracle SQL server- an 11.76 percentage.
2. Port 5800 potential VNC attack, scan 5800 with a percentage of 5.882
3. Port 1433 had suspicious inbound to MYSQL
Vulnerability Location
a. Oracle SQL on port 1521
b. VNC scan on port 500
c. MYSQL on port 1433
Discussion
Port 1521 Vulnerability
By default, whenever an Oracle server is installed, TNS listener is located on
Transmission Control Protocol (TCP port 1521). This port handles all network resources that are
to be passed to a database instance. If nor properly secured, commands sent to the listener may
cause a force shut down or illegally query the database. Port 1521 is one of the most vulnerable
ports in the server computing world as many hackers use it as their main target through which
they can gain complete control of a system.
Suspicious inbounds on port 1433
By default, the User datagram protocol (UDP) port 1433 is used for SQL server and is the
official Internet Assigned Number Authority for SQL server. Clients and hosts use this port to
connect or access database engines, while the SQL server management studio (SSMS) uses the
Results and Findings
The following vulnerabilities and respective percentages were identified.
1. On port 1521 ET POLICY inbound to the Oracle SQL server- an 11.76 percentage.
2. Port 5800 potential VNC attack, scan 5800 with a percentage of 5.882
3. Port 1433 had suspicious inbound to MYSQL
Vulnerability Location
a. Oracle SQL on port 1521
b. VNC scan on port 500
c. MYSQL on port 1433
Discussion
Port 1521 Vulnerability
By default, whenever an Oracle server is installed, TNS listener is located on
Transmission Control Protocol (TCP port 1521). This port handles all network resources that are
to be passed to a database instance. If nor properly secured, commands sent to the listener may
cause a force shut down or illegally query the database. Port 1521 is one of the most vulnerable
ports in the server computing world as many hackers use it as their main target through which
they can gain complete control of a system.
Suspicious inbounds on port 1433
By default, the User datagram protocol (UDP) port 1433 is used for SQL server and is the
official Internet Assigned Number Authority for SQL server. Clients and hosts use this port to
connect or access database engines, while the SQL server management studio (SSMS) uses the

Ethical Hacking 6
same port to manage all SQL server instances across the network. The suspicious inbounds
imply that there is malicious persons listening to all server-clients connections and the Tabular
Data Stream Protocol is at risk of being compromised.
VNC scan on port 5800
In virtual network computing, server machines supply connected hosts and machines with
data and applications. Additionally, the technology creates a virtual computing environment in
such a way that people do not need to carry any computing devices with them to gain acess to
their desktops. Port 5800 is in most cases with VNC protocol to allow system users have remote
control over their computing devices. When wrongly configured, telnet and SSH could be used
to remotely launch attacks on a system. A network analysis through black-box testing indicated
that the system is open to unauthorised illegal access.
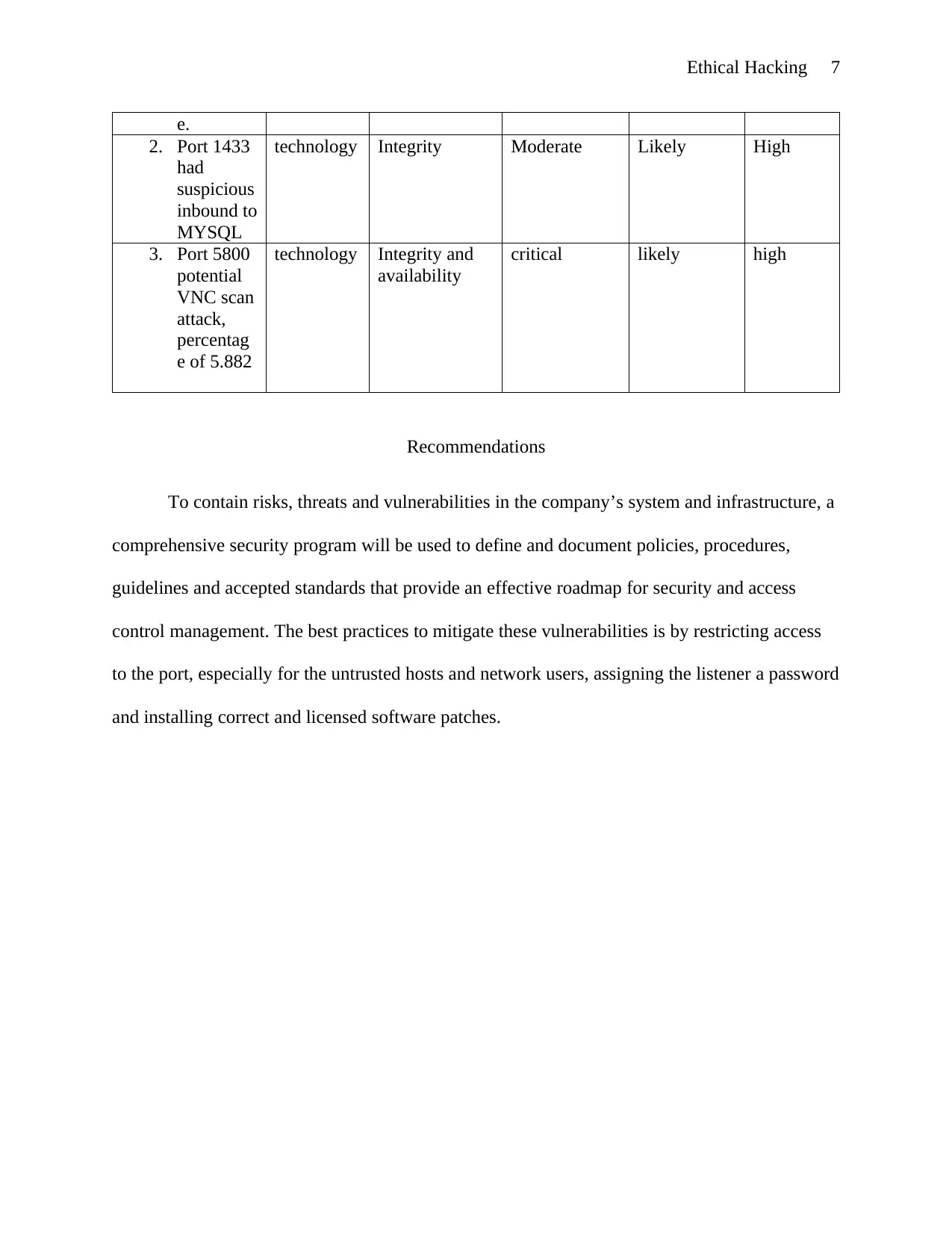
Risk Assessment Matrix
Risk assessment matrices are powerful tools that are used to identify, assess and control
organizational IT risks besides providing corrective actions and procedures to mitigate each risk.
The statement “establishing baselines and identifying an acceptable level of risk across the
environment provides a starting point for the actual audit” is a true statement that every risk
manager should comply with. Risk management is a continuous process whose main objective is
to minimize the number of risks and prevent them from escalating to issues.
Risk Security
mantra
Threat type Consequence Likelihood Risk
rating
1. On port
1521 ET
POLICY
inbound to
the Oracle
SQL
percentag
technology integrity Moderate Likely High
same port to manage all SQL server instances across the network. The suspicious inbounds
imply that there is malicious persons listening to all server-clients connections and the Tabular
Data Stream Protocol is at risk of being compromised.
VNC scan on port 5800
In virtual network computing, server machines supply connected hosts and machines with
data and applications. Additionally, the technology creates a virtual computing environment in
such a way that people do not need to carry any computing devices with them to gain acess to
their desktops. Port 5800 is in most cases with VNC protocol to allow system users have remote
control over their computing devices. When wrongly configured, telnet and SSH could be used
to remotely launch attacks on a system. A network analysis through black-box testing indicated
that the system is open to unauthorised illegal access.
Risk Assessment Matrix
Risk assessment matrices are powerful tools that are used to identify, assess and control
organizational IT risks besides providing corrective actions and procedures to mitigate each risk.
The statement “establishing baselines and identifying an acceptable level of risk across the
environment provides a starting point for the actual audit” is a true statement that every risk
manager should comply with. Risk management is a continuous process whose main objective is
to minimize the number of risks and prevent them from escalating to issues.
Risk Security
mantra
Threat type Consequence Likelihood Risk
rating
1. On port
1521 ET
POLICY
inbound to
the Oracle
SQL
percentag
technology integrity Moderate Likely High
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Ethical Hacking 7
e.
2. Port 1433
had
suspicious
inbound to
MYSQL
technology Integrity Moderate Likely High
3. Port 5800
potential
VNC scan
attack,
percentag
e of 5.882
technology Integrity and
availability
critical likely high
Recommendations
To contain risks, threats and vulnerabilities in the company’s system and infrastructure, a
comprehensive security program will be used to define and document policies, procedures,
guidelines and accepted standards that provide an effective roadmap for security and access
control management. The best practices to mitigate these vulnerabilities is by restricting access
to the port, especially for the untrusted hosts and network users, assigning the listener a password
and installing correct and licensed software patches.
e.
2. Port 1433
had
suspicious
inbound to
MYSQL
technology Integrity Moderate Likely High
3. Port 5800
potential
VNC scan
attack,
percentag
e of 5.882
technology Integrity and
availability
critical likely high
Recommendations
To contain risks, threats and vulnerabilities in the company’s system and infrastructure, a
comprehensive security program will be used to define and document policies, procedures,
guidelines and accepted standards that provide an effective roadmap for security and access
control management. The best practices to mitigate these vulnerabilities is by restricting access
to the port, especially for the untrusted hosts and network users, assigning the listener a password
and installing correct and licensed software patches.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





