ECU - Ethical Hacking: Web Shells, System Privilege & Flag Analysis
VerifiedAdded on 2023/06/04
|18
|1965
|111
Report
AI Summary
This report details an ethical hacking exercise focused on infiltrating a system to gain root-level privileges and recover five flags, utilizing a provided virtual machine. The methodology involves analyzing Apache server configurations, understanding web shells (like c99), employing password cracking tools like Hashcat, utilizing Nmap for network scanning, and performing Linux privilege escalation. Each flag represents a milestone in the system compromise, with the report outlining the steps taken, tools used, and vulnerabilities exploited to achieve the objectives. The report also includes recommendations based on the findings of the ethical hacking assessment.

Ethical Hacking
1
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
This report gives information related to web shell and related to ethical hacking. The virtual
machine case study is used throughout this report. This report explains and discusses
important details about the five flags, followed by Apache server, Nmap and much more.
Each flag is explained clearly with steps and instructions, where it will mention about the
flags usage, it's impact and the tool it uses to conduct various processes.
2
This report gives information related to web shell and related to ethical hacking. The virtual
machine case study is used throughout this report. This report explains and discusses
important details about the five flags, followed by Apache server, Nmap and much more.
Each flag is explained clearly with steps and instructions, where it will mention about the
flags usage, it's impact and the tool it uses to conduct various processes.
2

Table of Contents
1 Goal of the Project............................................................................................................1
2 Defined methodology and Testing Log...........................................................................1
Flag 1)....................................................................................................................................2
Flag 2)....................................................................................................................................4
Flag 3)....................................................................................................................................5
Flag 4)..................................................................................................................................11
Flag 5)..................................................................................................................................13
3 Results and Recommendations......................................................................................13
3
1 Goal of the Project............................................................................................................1
2 Defined methodology and Testing Log...........................................................................1
Flag 1)....................................................................................................................................2
Flag 2)....................................................................................................................................4
Flag 3)....................................................................................................................................5
Flag 4)..................................................................................................................................11
Flag 5)..................................................................................................................................13
3 Results and Recommendations......................................................................................13
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1 Aim of the Project
This is the project which discussed about ethical hacking. To proceed this a case study
which is already provided. There are certain things which the user has to have for infiltrating
the system which is given. Moreover, it is requested to get the root level privileges. This
report will mainly talk about five flags. These five flags are completed using the provided
case study of virtual machine. Each flag will be explained clearly, where it will mention
about the flags usage, it's impact and the tool it uses to conduct various processes. Therefore,
here the flags will be analysed and discussed in detail.
2 Defined methodology and Testing Log
The testing log process starts with the installation of Virtual machine. This looks exactly
as illustrated in the following image (Allen, Heriyanto & Ali, 2014).
4
This is the project which discussed about ethical hacking. To proceed this a case study
which is already provided. There are certain things which the user has to have for infiltrating
the system which is given. Moreover, it is requested to get the root level privileges. This
report will mainly talk about five flags. These five flags are completed using the provided
case study of virtual machine. Each flag will be explained clearly, where it will mention
about the flags usage, it's impact and the tool it uses to conduct various processes. Therefore,
here the flags will be analysed and discussed in detail.
2 Defined methodology and Testing Log
The testing log process starts with the installation of Virtual machine. This looks exactly
as illustrated in the following image (Allen, Heriyanto & Ali, 2014).
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Flag 1
Here, let us get to know about Apache. It refers to a web server which is supports most of the
major platforms. The Apache server is stored in the operating system's different directory.
This is because of it's efforts for finding the file's whenever required (Buchanan, 2014).
Hence, for identifying the apache configuration file there exists certain methods which can
swiftly locate and complete the process with ease. It gives the details of Apache installation's
5
Here, let us get to know about Apache. It refers to a web server which is supports most of the
major platforms. The Apache server is stored in the operating system's different directory.
This is because of it's efforts for finding the file's whenever required (Buchanan, 2014).
Hence, for identifying the apache configuration file there exists certain methods which can
swiftly locate and complete the process with ease. It gives the details of Apache installation's
5

directory structure for all the major platforms or the OSes. The following indicates the web
server content.
The following table indicates the Apache httpd 2.4 default layout (apache.org source
package):
The following table denotes the Apache httpd 2.2 default layout (apache.org source
package):
6
server content.
The following table indicates the Apache httpd 2.4 default layout (apache.org source
package):
The following table denotes the Apache httpd 2.2 default layout (apache.org source
package):
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The following table represents the layout of Apache httpd 2.0 default layout (apache.org
source package):
Flag 2
The flag 2 introduces the web shells are small programs or scripts which can be
uploaded to the vulnerable server and it can be opened from the browser, to provide a web
based interface to run the system commands. Generally, the web shells are the backdoors
which run from the browser (Eliot, 2016). The suitable or supporting programming language is
used for the web server's, web shell script. Here, php language is utilixed. The web shells
provides a quick graphical user interface for performing the following activities:
Travelling across the directories, viewing the files, editing the files, downloading the files,
deleting the files, uploading the files, executing MySQL queries or the commands, bypassing
the mod_security, giving permissions to the directory/folders and executing the shell
commands.
c99 web shell
The other web shell we are going to introduce here is, c99. This specific web shell for pho is
so popular and it is just due to it's supportive and effective features. (Engebretson, 2013).
Certain powerful features include, file browsing, uploading, deleting, executing commands,
viewing the system details, viewing all the running processes, running the php code etc.
7
source package):
Flag 2
The flag 2 introduces the web shells are small programs or scripts which can be
uploaded to the vulnerable server and it can be opened from the browser, to provide a web
based interface to run the system commands. Generally, the web shells are the backdoors
which run from the browser (Eliot, 2016). The suitable or supporting programming language is
used for the web server's, web shell script. Here, php language is utilixed. The web shells
provides a quick graphical user interface for performing the following activities:
Travelling across the directories, viewing the files, editing the files, downloading the files,
deleting the files, uploading the files, executing MySQL queries or the commands, bypassing
the mod_security, giving permissions to the directory/folders and executing the shell
commands.
c99 web shell
The other web shell we are going to introduce here is, c99. This specific web shell for pho is
so popular and it is just due to it's supportive and effective features. (Engebretson, 2013).
Certain powerful features include, file browsing, uploading, deleting, executing commands,
viewing the system details, viewing all the running processes, running the php code etc.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The following screenshot represents c99 web shell.
Flag 3
In flag 3, hashcat will be discussed because at present it is the finest password
cracker available.
Step – 1 Open Hashcat
For opening hashcat the following instructions must be followed (Ethical hacking and
countermeasures, 2017):
8
Flag 3
In flag 3, hashcat will be discussed because at present it is the finest password
cracker available.
Step – 1 Open Hashcat
For opening hashcat the following instructions must be followed (Ethical hacking and
countermeasures, 2017):
8

Applications -> Kali Linux -> Password Attacks -> Offline Attacks -> hashcat
Go to the menu item of hashcat, it will open the help screen.
The above screen displays the basic hashcat syntax, as follows,
kali > hashcat options hashfile mask|wordfiles|directories
9
Go to the menu item of hashcat, it will open the help screen.
The above screen displays the basic hashcat syntax, as follows,
kali > hashcat options hashfile mask|wordfiles|directories
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
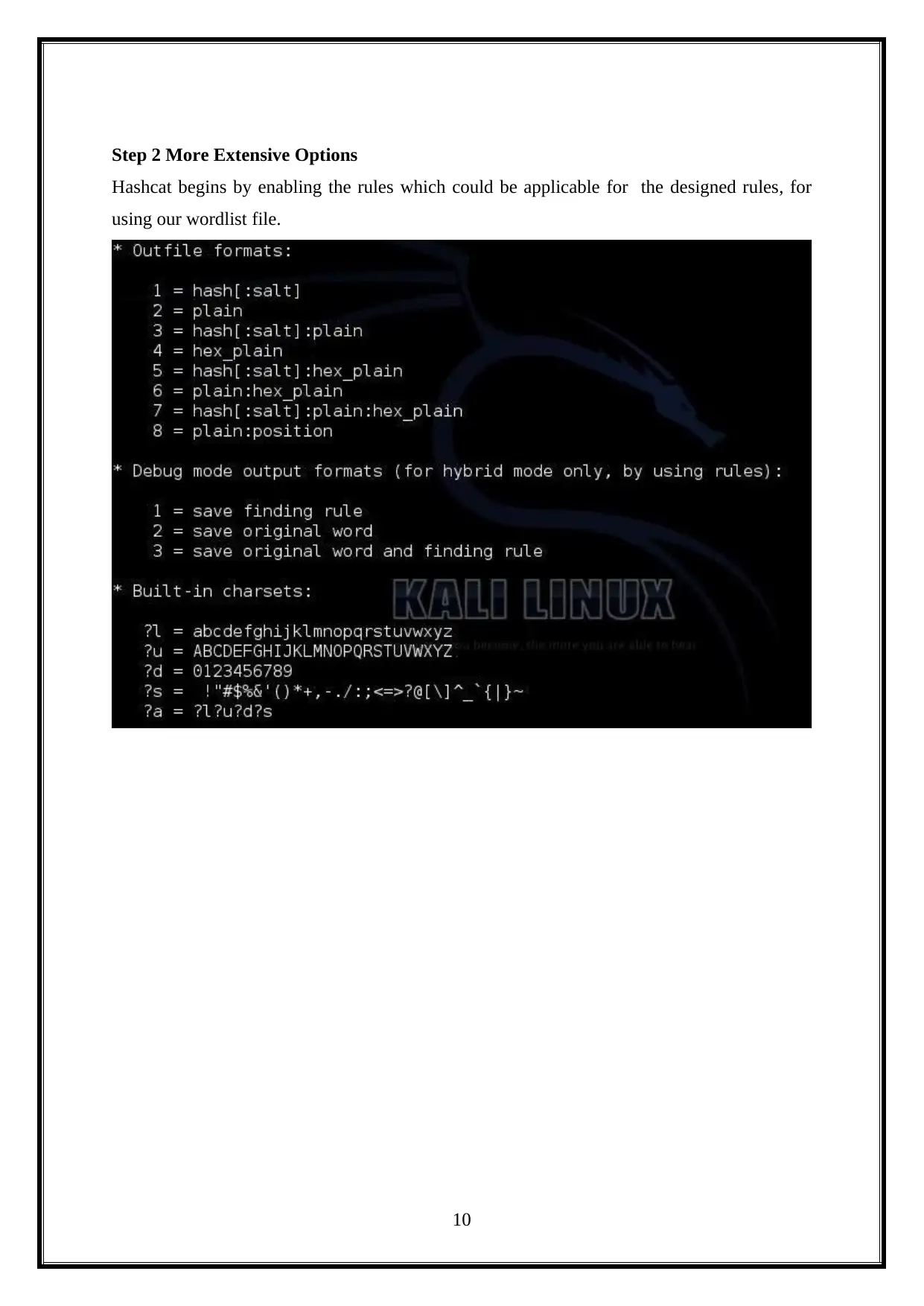
Step 2 More Extensive Options
Hashcat begins by enabling the rules which could be applicable for the designed rules, for
using our wordlist file.
10
Hashcat begins by enabling the rules which could be applicable for the designed rules, for
using our wordlist file.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
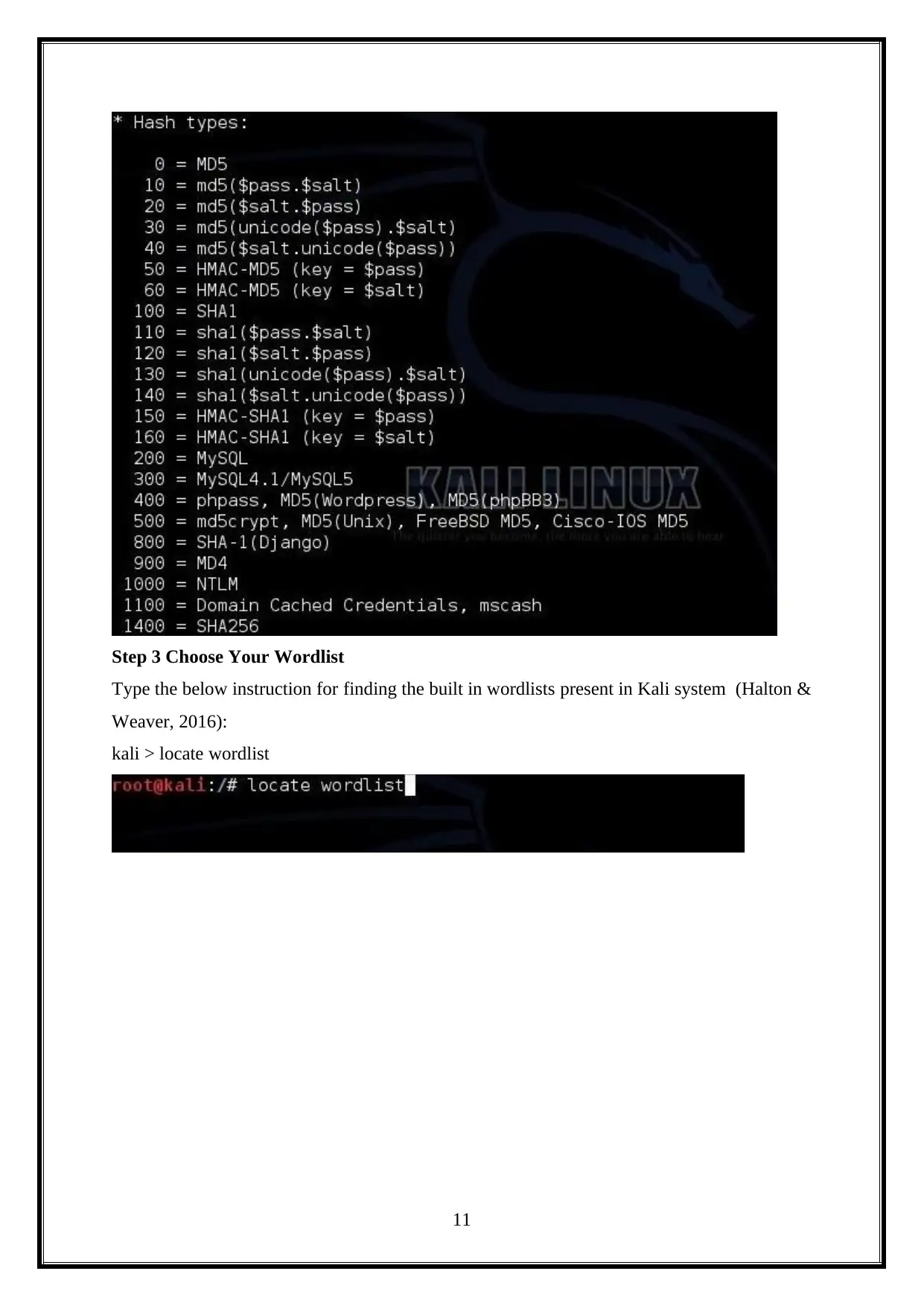
Step 3 Choose Your Wordlist
Type the below instruction for finding the built in wordlists present in Kali system (Halton &
Weaver, 2016):
kali > locate wordlist
11
Type the below instruction for finding the built in wordlists present in Kali system (Halton &
Weaver, 2016):
kali > locate wordlist
11

Step 4 Grab the Hashes
Here, on the Kali system grab all the hashes. It is required to view the hashes for grabbing
them and this possible when the user is logged in as the root. But, the difference in Linux
system is that the hashes will be stored in the following directory,
/etc/shadow file
Hence, type as shown below.
kali > tail /etc/shadow
12
Here, on the Kali system grab all the hashes. It is required to view the hashes for grabbing
them and this possible when the user is logged in as the root. But, the difference in Linux
system is that the hashes will be stored in the following directory,
/etc/shadow file
Hence, type as shown below.
kali > tail /etc/shadow
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




