Ethics Report: Analysis of Cyber Security Issues and Data Breaches
VerifiedAdded on 2022/05/19
|10
|2400
|24
Report
AI Summary
This report provides a comprehensive overview of cyber security ethics, particularly focusing on the ethical implications of data breaches. It begins by introducing the significance of cyber security in the modern era, emphasizing the increasing reliance on the internet for various services and the resultant data collection. The report then delves into a specific case study, the 'Collection 1' data breach, highlighting the exposure of millions of email addresses and passwords. It discusses the ethical issues arising from such breaches, including unauthorized access to personal information and the potential for cybercrimes. The report incorporates background knowledge on cyber security measures, such as those implemented by Australian businesses, and the role of the Australian Cyber Security Centre (ACSC) in providing warnings and guidelines. It further explores ethical theories, particularly Utilitarianism, in the context of data privacy. The report also examines different types of cyber-attacks and their impact on businesses, and the economy. It concludes with recommendations for businesses, emphasizing the importance of data security, staff training, and adherence to ethical standards and relevant laws. The report draws on various sources, including news articles and academic research, to support its analysis and recommendations.
Running Head: ETHICS 0 | P a g e
Ethics
Report
Student name
Ethics
Report
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Ethics 1 | P a g e
Table of Contents
Introduction:....................................................................................................................................2
Background Knowledge:.................................................................................................................2
Ethical issues in article:...................................................................................................................4
Ethical Decision...........................................................................................................................6
Conclusion:......................................................................................................................................7
References........................................................................................................................................8
Table of Contents
Introduction:....................................................................................................................................2
Background Knowledge:.................................................................................................................2
Ethical issues in article:...................................................................................................................4
Ethical Decision...........................................................................................................................6
Conclusion:......................................................................................................................................7
References........................................................................................................................................8

Ethics 2 | P a g e
Introduction:
Cyber security is a major issue of present era. From last two decades, internet is highly used for
data transfers and different services. Internet is a base of many industries, such as share market,
retails, hospitality, education, and healthcare. Everyone is using internet in their daily life for
different purposes, such as shopping, travelling (Cab Services), education, and many others
(ACSC, 2017).
Data is a raw material, which is collected from different things. It is processed then it gets
converted into information. Information is a confidential and important element which can be
used for illegal purposes. There are many issues with the personal information of customers
(BWISE, 2018).
This report will explain about the ‘Collection 1’ data breach in which a file distributed on
hacking websites. That file is having unique email addresses of 773 million people and more
than 22 million passwords. It will also explain about the ethical theories and their uses in
different situations.
These data are used for marketing and cybercrimes. It is an unethical way to access email
accounts of different persons (Andrijcic & Horowitz, 2016). This report will describe about the
article “Business hack warning as 'honey pots of data' targeted” of The Sydney Morning Herald
new paper, which is published on 22 January 2019 by Emma Koehn ( Koehn, 2019).
Background Knowledge:
Present era is majorly based on the computer systems. Most of the organizations require internet
and other things for different services. For an example, during travelling, cab services require
internet connection. There are many things, which require personal data for login or sign-in in a
system. That personal data is stored in database of that particular system. However, every system
is providing full security to that personal data ( Matteo & Floridi, 2009).
Australian businesses have cyber security facility in their systems for securing customer’s
information. It they are warned for it and they must inform about breaches to the cyber security
help lines. The Australia Cyber Security Centre (ACSC) has announced about a hack in which
Introduction:
Cyber security is a major issue of present era. From last two decades, internet is highly used for
data transfers and different services. Internet is a base of many industries, such as share market,
retails, hospitality, education, and healthcare. Everyone is using internet in their daily life for
different purposes, such as shopping, travelling (Cab Services), education, and many others
(ACSC, 2017).
Data is a raw material, which is collected from different things. It is processed then it gets
converted into information. Information is a confidential and important element which can be
used for illegal purposes. There are many issues with the personal information of customers
(BWISE, 2018).
This report will explain about the ‘Collection 1’ data breach in which a file distributed on
hacking websites. That file is having unique email addresses of 773 million people and more
than 22 million passwords. It will also explain about the ethical theories and their uses in
different situations.
These data are used for marketing and cybercrimes. It is an unethical way to access email
accounts of different persons (Andrijcic & Horowitz, 2016). This report will describe about the
article “Business hack warning as 'honey pots of data' targeted” of The Sydney Morning Herald
new paper, which is published on 22 January 2019 by Emma Koehn ( Koehn, 2019).
Background Knowledge:
Present era is majorly based on the computer systems. Most of the organizations require internet
and other things for different services. For an example, during travelling, cab services require
internet connection. There are many things, which require personal data for login or sign-in in a
system. That personal data is stored in database of that particular system. However, every system
is providing full security to that personal data ( Matteo & Floridi, 2009).
Australian businesses have cyber security facility in their systems for securing customer’s
information. It they are warned for it and they must inform about breaches to the cyber security
help lines. The Australia Cyber Security Centre (ACSC) has announced about a hack in which
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Ethics 3 | P a g e
emails and passwords are shared with the hacking websites. That file is having email addresses
of 773 million accounts (ACSC, 2017).
The cyber security centre has issued a message to all the owners of that accounts to change their
passwords and practice good password hygiene.
Source: (www.stanfieldit.com, 2019)
According to the ACSE, passwords should be changes on regular basis and in combination of
different things, which makes is stronger. Users are advises by the ACSC that implement multi-
factor authentication on their personal accounts for more security (ACSC, 2017).
Staff members of University of the Sunshine Coast are requested to regularly update passwords
by the professor of cyber security.
A program is started by the nation’s cyber security centre for reducing fear of third part hackers.
It has a name that is ‘managed service providers’. It was raised in 2017 first time at international
level. The Australian Government is serious after the APT10 (a group into China).
Australian businesses have warned about the reporting of data breaches in to office of the
information commissioner. Managed service providers are having a responsibility for carry out
emails and passwords are shared with the hacking websites. That file is having email addresses
of 773 million accounts (ACSC, 2017).
The cyber security centre has issued a message to all the owners of that accounts to change their
passwords and practice good password hygiene.
Source: (www.stanfieldit.com, 2019)
According to the ACSE, passwords should be changes on regular basis and in combination of
different things, which makes is stronger. Users are advises by the ACSC that implement multi-
factor authentication on their personal accounts for more security (ACSC, 2017).
Staff members of University of the Sunshine Coast are requested to regularly update passwords
by the professor of cyber security.
A program is started by the nation’s cyber security centre for reducing fear of third part hackers.
It has a name that is ‘managed service providers’. It was raised in 2017 first time at international
level. The Australian Government is serious after the APT10 (a group into China).
Australian businesses have warned about the reporting of data breaches in to office of the
information commissioner. Managed service providers are having a responsibility for carry out
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Ethics 4 | P a g e
an assessment if any personal information of Australian is compromised in data breaches. It was
stated by the commissioner’s office statement.
Small businesses are taking facilities from the third parties, which are having their customer’s
data in their server. Therefore, it must be follow term and condition by that vendors that are
related to the personal information (Symantec, 2018).
Ethical issues in article:
Data breaches are an unethical thing and it is illegal according to cyber security laws and
regulations. Australian’s mandatory data breach laws mean Australian businesses must report
about the affected individuals and carry out assessment within 30 days at commissioner’s office.
Data mangers should have this responsibility to report about it ( Norén, 2016).
Data breach is an unethical condition. No one can use personal information of a user without his
or her permission for his or her personal uses. Every organization is having their code of
conducts and each staff members must follow it. Data must be secure by the user as well as small
businesses. IT industry must follow the ethics for securing the personal data of customers
( Reynolds, 2018).
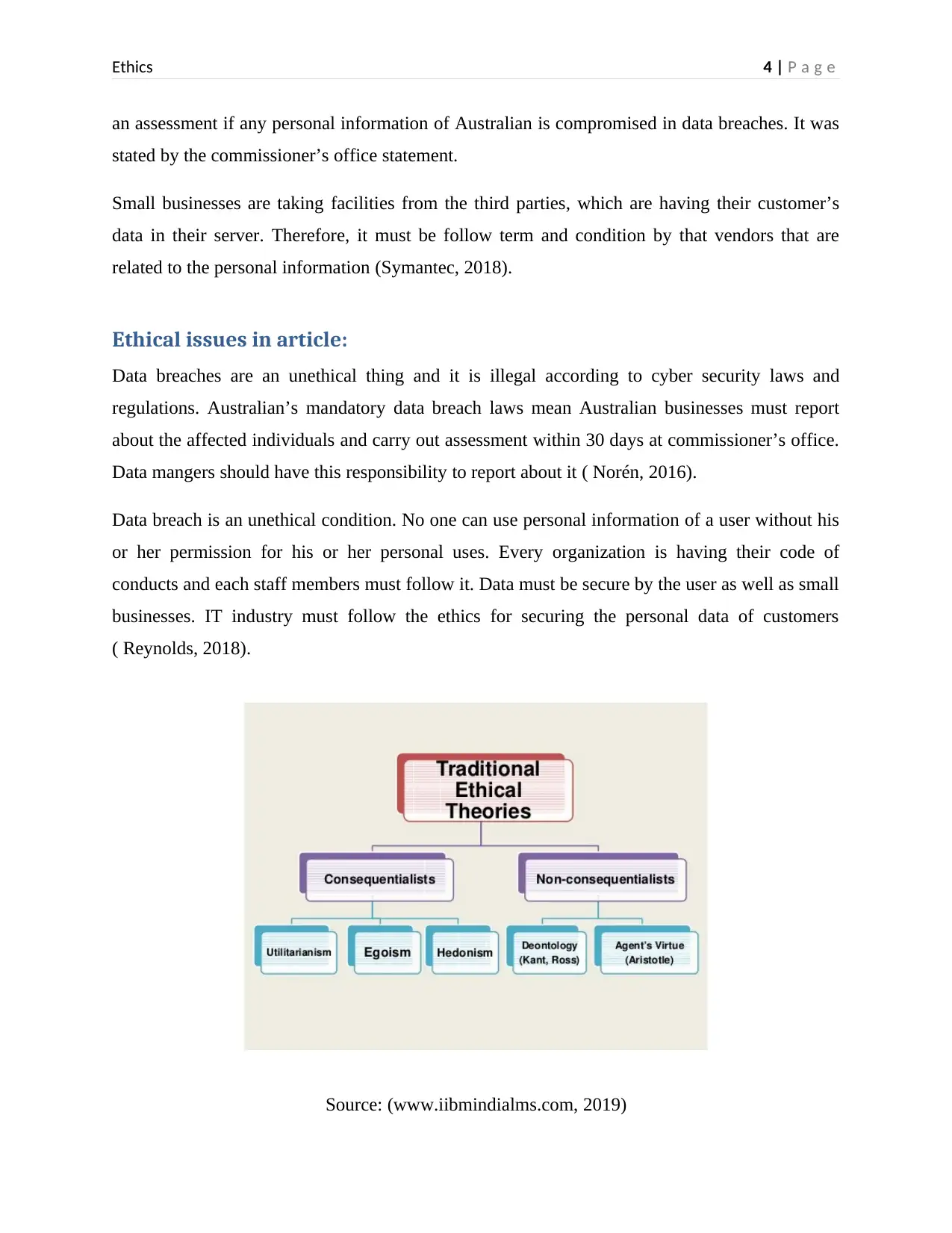
Source: (www.iibmindialms.com, 2019)
an assessment if any personal information of Australian is compromised in data breaches. It was
stated by the commissioner’s office statement.
Small businesses are taking facilities from the third parties, which are having their customer’s
data in their server. Therefore, it must be follow term and condition by that vendors that are
related to the personal information (Symantec, 2018).
Ethical issues in article:
Data breaches are an unethical thing and it is illegal according to cyber security laws and
regulations. Australian’s mandatory data breach laws mean Australian businesses must report
about the affected individuals and carry out assessment within 30 days at commissioner’s office.
Data mangers should have this responsibility to report about it ( Norén, 2016).
Data breach is an unethical condition. No one can use personal information of a user without his
or her permission for his or her personal uses. Every organization is having their code of
conducts and each staff members must follow it. Data must be secure by the user as well as small
businesses. IT industry must follow the ethics for securing the personal data of customers
( Reynolds, 2018).
Source: (www.iibmindialms.com, 2019)

Ethics 5 | P a g e
Ethical theories are classified in five parts, which are as showing in above diagram. In this
scenario, Utilitarianism ethical theory is applied as it is a social issue that personal data is
important for a person and it is not shared without permission of that person.
Information sharing is not a bad thing but use that information for illegal work is not legal.
Therefore, different laws and regulations are created for stopping data breaches. Cyber-attacks
can change many things at huge levels. Data breaches can be a reason of financial loss of many
businesses. Many businesses are based on the customer’s information. It can also damage
reputation of an organization at global level. It is affecting the productivity of business (Arlitsch
& Edelman, 2014).
There is much vulnerability for cyber-attacks. It is depending on three things mainly, which are
weakness of system, access of system, and ability to exploit it. Every organization is having their
data on their system. It is also sensitive and confidential in terms of business. Attackers are
intercepting the data form organization server (De George, 2011).
Sources: (www.stanfieldit.com, 2019)
Above figure is showing data about the cyber-attacks in 2019. It affects the economy of country
also in term of cost and time. Australian government is creating some standards for cyber
security to manage the working all the small businesses. However, large-scale businesses are
Ethical theories are classified in five parts, which are as showing in above diagram. In this
scenario, Utilitarianism ethical theory is applied as it is a social issue that personal data is
important for a person and it is not shared without permission of that person.
Information sharing is not a bad thing but use that information for illegal work is not legal.
Therefore, different laws and regulations are created for stopping data breaches. Cyber-attacks
can change many things at huge levels. Data breaches can be a reason of financial loss of many
businesses. Many businesses are based on the customer’s information. It can also damage
reputation of an organization at global level. It is affecting the productivity of business (Arlitsch
& Edelman, 2014).
There is much vulnerability for cyber-attacks. It is depending on three things mainly, which are
weakness of system, access of system, and ability to exploit it. Every organization is having their
data on their system. It is also sensitive and confidential in terms of business. Attackers are
intercepting the data form organization server (De George, 2011).
Sources: (www.stanfieldit.com, 2019)
Above figure is showing data about the cyber-attacks in 2019. It affects the economy of country
also in term of cost and time. Australian government is creating some standards for cyber
security to manage the working all the small businesses. However, large-scale businesses are
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Ethics 6 | P a g e
having a strong cyber security for their system. They also implement International standards for
company, such as ISO 27001. In addition, The Australia federal government did not allow small
businesses to store customer’s data for their uses (Arlitsch & Edelman, 2014).
There are different frameworks are designed for stopping the cyber-attacks, such as ISO270001
standard. In 2019, Australian businesses have warned about the data breaches and they must
inform at commissioner’s office immediately (Wright, 2011). Owner of organization should
appoint a specialist, which inform about data breaches (Rossouw & Vuuren, 2017).
According to Koehn, Troy Hunt exposed the breach, which is known as “Collection 1”. Troy
Hunt is a cyber-security expert. The data is sensitive as it is having emails and passwords of
users. That data can helpful for hacking baking account of users for hackers. It is so crucial for
security companies (University, 2018).
There are different types of cyber-attacks on the personal information of customers, which are
saved in the vendor’s servers. Malware are having different types, such as virus, Trojans,
ransomware, worms, and spyware. They all are having malicious codes, which corrupt
information of the system (Von Solms & Van Niekerk, 2013).
Phishing attacks are used emails for sending a form for filling personal information. They used
that information for accessing bank accounts. It is an easy process to identifying phishing
attacks. Banking industries never send such types of emails. Distributed Denial of Service
(DDOS) is an attack that creates distortion in the network and all services are disrupting from it
(WARREN, 2011).
There are other cyber-attacks are disrupt the persona information, such as rogue software, Brute
Force attack, Watering Hole attack, Social media threats and man in the middle (Weiss, 2014). It
can be control through two levels, first is personal level, in which user cannot believe on anyone
and did not share personal information either offline or online. Second is cyber security
departments must have records about the data breaches and inform to all businesses for reporting
them.
having a strong cyber security for their system. They also implement International standards for
company, such as ISO 27001. In addition, The Australia federal government did not allow small
businesses to store customer’s data for their uses (Arlitsch & Edelman, 2014).
There are different frameworks are designed for stopping the cyber-attacks, such as ISO270001
standard. In 2019, Australian businesses have warned about the data breaches and they must
inform at commissioner’s office immediately (Wright, 2011). Owner of organization should
appoint a specialist, which inform about data breaches (Rossouw & Vuuren, 2017).
According to Koehn, Troy Hunt exposed the breach, which is known as “Collection 1”. Troy
Hunt is a cyber-security expert. The data is sensitive as it is having emails and passwords of
users. That data can helpful for hacking baking account of users for hackers. It is so crucial for
security companies (University, 2018).
There are different types of cyber-attacks on the personal information of customers, which are
saved in the vendor’s servers. Malware are having different types, such as virus, Trojans,
ransomware, worms, and spyware. They all are having malicious codes, which corrupt
information of the system (Von Solms & Van Niekerk, 2013).
Phishing attacks are used emails for sending a form for filling personal information. They used
that information for accessing bank accounts. It is an easy process to identifying phishing
attacks. Banking industries never send such types of emails. Distributed Denial of Service
(DDOS) is an attack that creates distortion in the network and all services are disrupting from it
(WARREN, 2011).
There are other cyber-attacks are disrupt the persona information, such as rogue software, Brute
Force attack, Watering Hole attack, Social media threats and man in the middle (Weiss, 2014). It
can be control through two levels, first is personal level, in which user cannot believe on anyone
and did not share personal information either offline or online. Second is cyber security
departments must have records about the data breaches and inform to all businesses for reporting
them.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Ethics 7 | P a g e
Ethical Decision
I suggest to all the businesses of Australia that they support data security, as it is a moral
phenomenon to cooperate always and everywhere. Cyber security service is easily available for
business purposes in low cost. However, it is for benefits, such as health benefits. Data breaches
are a problem, which is faced at international level. Therefore, it should be control by the
governments as well as businesses with the help of IT-services.
Employer must provide training to all staff members for securing the personal information of
their customers. Staff can stop these types of incidents in their workplaces in an awareness
process. They must know about right and wrong in case of sharing personal information of
customers for their personal uses.
Australia is having a strong economy and it is a good thing to stopped bad things of technology
and innovations. Data breach is an example of lack of security or lack of information. Everyone
must know about the laws, ethics and morals in case of personal information.
According my opinion, Australian businesses have to use cyber security and make them up to
date. Preventing of data is a good exercise for the different businesses.
Conclusion:
It is concluded from above paragraphs of this report that cyber security is essential for all of the
Australian businesses, as they often deal with their customer’s personal information. Thus, the
ACSC has warned to all Australian businesses that they have to report within 30 days at
commissioner’s office, if they detect any data breaches at their end.
Cyber security is a main concern for small as well as large businesses, as they use third party soft
wares. This report has successfully discussed about strong passwords of users of their personal
accounts at different domains. This report has included ethical theories for explaining ethics and
moral of a person that are related to the personal information.
Finally, it is concluded that all vendors in their businesses should follow cyber security terms and
conditions. Australian businesses must follow the data security terms and conditions for the sake
of security of personal info of customers.
Ethical Decision
I suggest to all the businesses of Australia that they support data security, as it is a moral
phenomenon to cooperate always and everywhere. Cyber security service is easily available for
business purposes in low cost. However, it is for benefits, such as health benefits. Data breaches
are a problem, which is faced at international level. Therefore, it should be control by the
governments as well as businesses with the help of IT-services.
Employer must provide training to all staff members for securing the personal information of
their customers. Staff can stop these types of incidents in their workplaces in an awareness
process. They must know about right and wrong in case of sharing personal information of
customers for their personal uses.
Australia is having a strong economy and it is a good thing to stopped bad things of technology
and innovations. Data breach is an example of lack of security or lack of information. Everyone
must know about the laws, ethics and morals in case of personal information.
According my opinion, Australian businesses have to use cyber security and make them up to
date. Preventing of data is a good exercise for the different businesses.
Conclusion:
It is concluded from above paragraphs of this report that cyber security is essential for all of the
Australian businesses, as they often deal with their customer’s personal information. Thus, the
ACSC has warned to all Australian businesses that they have to report within 30 days at
commissioner’s office, if they detect any data breaches at their end.
Cyber security is a main concern for small as well as large businesses, as they use third party soft
wares. This report has successfully discussed about strong passwords of users of their personal
accounts at different domains. This report has included ethical theories for explaining ethics and
moral of a person that are related to the personal information.
Finally, it is concluded that all vendors in their businesses should follow cyber security terms and
conditions. Australian businesses must follow the data security terms and conditions for the sake
of security of personal info of customers.

Ethics 8 | P a g e
References
Koehn, E., 2019. Business hack warning as 'honey pots of data' targeted. [Online]
Available at: https://www.smh.com.au/business/small-business/business-hack-warning-as-
honey-pots-of-data-targeted-20190121-p50sle.html
[Accessed 24 January 2019].
Matteo, T. & Floridi, L., 2009. The ethics of information transparency. Ethics and Information
Technology, 11(2), pp. 105-112.
Norén, L., 2016. Law and Ethics for Data Managers. [Online]
Available at: https://cds.nyu.edu/law-ethics-data-managers-spring-2016-ds-ga-3001-003/
Reynolds, G., 2018. Ethics in Information Technology. 6th ed. Boston: Cengage Learning.
ACSC, 2017. Australian Cyber Security Centre. [Online]
Available at: https://www.acsc.gov.au/publications/ACSC_Threat_Report_2017.pdf
[Accessed 12 December 2018].
Andrijcic, E. & Horowitz, B., 2016. A Macro‐Economic Framework for Evaluation of Cyber
Security Risks Related to Protection of Intellectual Property. Risk analysis, 26(4), pp. 907-923.
Arlitsch, K. & Edelman, A., 2014. Staying safe: Cyber security for people and organizations.
Journal of Library Administration, 54(1), pp. 46-56.
BWISE, 2018. nist cyber security framework. [Online]
Available at: https://www.bwise.com/solutions/frameworks/nist-framework
De George, R. T., 2011. Business ethics.. New Delhi: Pearson Education India..
Rossouw, D. & Vuuren, L. V., 2017. Business ethics.. London: Oxford University Press..
Symantec, 2018. 10 cyber security facts and statistics for 2018. [Online]
Available at: https://us.norton.com/internetsecurity-emerging-threats-10-facts-about-todays-
cybersecurity-landscape-that-you-should-know.html
[Accessed 11 December 2018].
References
Koehn, E., 2019. Business hack warning as 'honey pots of data' targeted. [Online]
Available at: https://www.smh.com.au/business/small-business/business-hack-warning-as-
honey-pots-of-data-targeted-20190121-p50sle.html
[Accessed 24 January 2019].
Matteo, T. & Floridi, L., 2009. The ethics of information transparency. Ethics and Information
Technology, 11(2), pp. 105-112.
Norén, L., 2016. Law and Ethics for Data Managers. [Online]
Available at: https://cds.nyu.edu/law-ethics-data-managers-spring-2016-ds-ga-3001-003/
Reynolds, G., 2018. Ethics in Information Technology. 6th ed. Boston: Cengage Learning.
ACSC, 2017. Australian Cyber Security Centre. [Online]
Available at: https://www.acsc.gov.au/publications/ACSC_Threat_Report_2017.pdf
[Accessed 12 December 2018].
Andrijcic, E. & Horowitz, B., 2016. A Macro‐Economic Framework for Evaluation of Cyber
Security Risks Related to Protection of Intellectual Property. Risk analysis, 26(4), pp. 907-923.
Arlitsch, K. & Edelman, A., 2014. Staying safe: Cyber security for people and organizations.
Journal of Library Administration, 54(1), pp. 46-56.
BWISE, 2018. nist cyber security framework. [Online]
Available at: https://www.bwise.com/solutions/frameworks/nist-framework
De George, R. T., 2011. Business ethics.. New Delhi: Pearson Education India..
Rossouw, D. & Vuuren, L. V., 2017. Business ethics.. London: Oxford University Press..
Symantec, 2018. 10 cyber security facts and statistics for 2018. [Online]
Available at: https://us.norton.com/internetsecurity-emerging-threats-10-facts-about-todays-
cybersecurity-landscape-that-you-should-know.html
[Accessed 11 December 2018].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Ethics 9 | P a g e
University, U., 2018. Ethics in IT. [Online]
Available at: http://www.it.uu.se/research/project/itethics
[Accessed 18 September 2018].
Von Solms, R. & Van Niekerk, J., 2013. From information security to cyber security. computers
& security, Volume 38, pp. 97-102.
WARREN, E., 2011. Legal, Ethical, and Professional Issues in Information Security. [Online]
Available at: https://www.cengage.com/resource_uploads/downloads/1111138214_259148.pdf
Weiss, J. W., 2014. Business ethics: A stakeholder and issues management approach.. London:
Berrett-Koehler Publishers.
Wright, D., 2011. A framework for the ethical impact assessment of information technology.
Ethics and information technology, 13(3), pp. 199-226.
www.iibmindialms.com, 2019. Ethical theories Framework. [Online]
Available at: http://www.iibmindialms.com/library/human-resources-management/ethics-in-
business/ethical-theories-framework/
[Accessed 26 January 2019].
www.stanfieldit.com, 2019. Cyber Security in a Nutshell. [Online]
Available at: https://www.stanfieldit.com/cyber-security/
[Accessed 24 January 2019].
University, U., 2018. Ethics in IT. [Online]
Available at: http://www.it.uu.se/research/project/itethics
[Accessed 18 September 2018].
Von Solms, R. & Van Niekerk, J., 2013. From information security to cyber security. computers
& security, Volume 38, pp. 97-102.
WARREN, E., 2011. Legal, Ethical, and Professional Issues in Information Security. [Online]
Available at: https://www.cengage.com/resource_uploads/downloads/1111138214_259148.pdf
Weiss, J. W., 2014. Business ethics: A stakeholder and issues management approach.. London:
Berrett-Koehler Publishers.
Wright, D., 2011. A framework for the ethical impact assessment of information technology.
Ethics and information technology, 13(3), pp. 199-226.
www.iibmindialms.com, 2019. Ethical theories Framework. [Online]
Available at: http://www.iibmindialms.com/library/human-resources-management/ethics-in-
business/ethical-theories-framework/
[Accessed 26 January 2019].
www.stanfieldit.com, 2019. Cyber Security in a Nutshell. [Online]
Available at: https://www.stanfieldit.com/cyber-security/
[Accessed 24 January 2019].
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




