Ethical Hacking and Penetration Testing: Concepts and Methods
VerifiedAdded on 2022/08/12
|10
|689
|39
Presentation
AI Summary
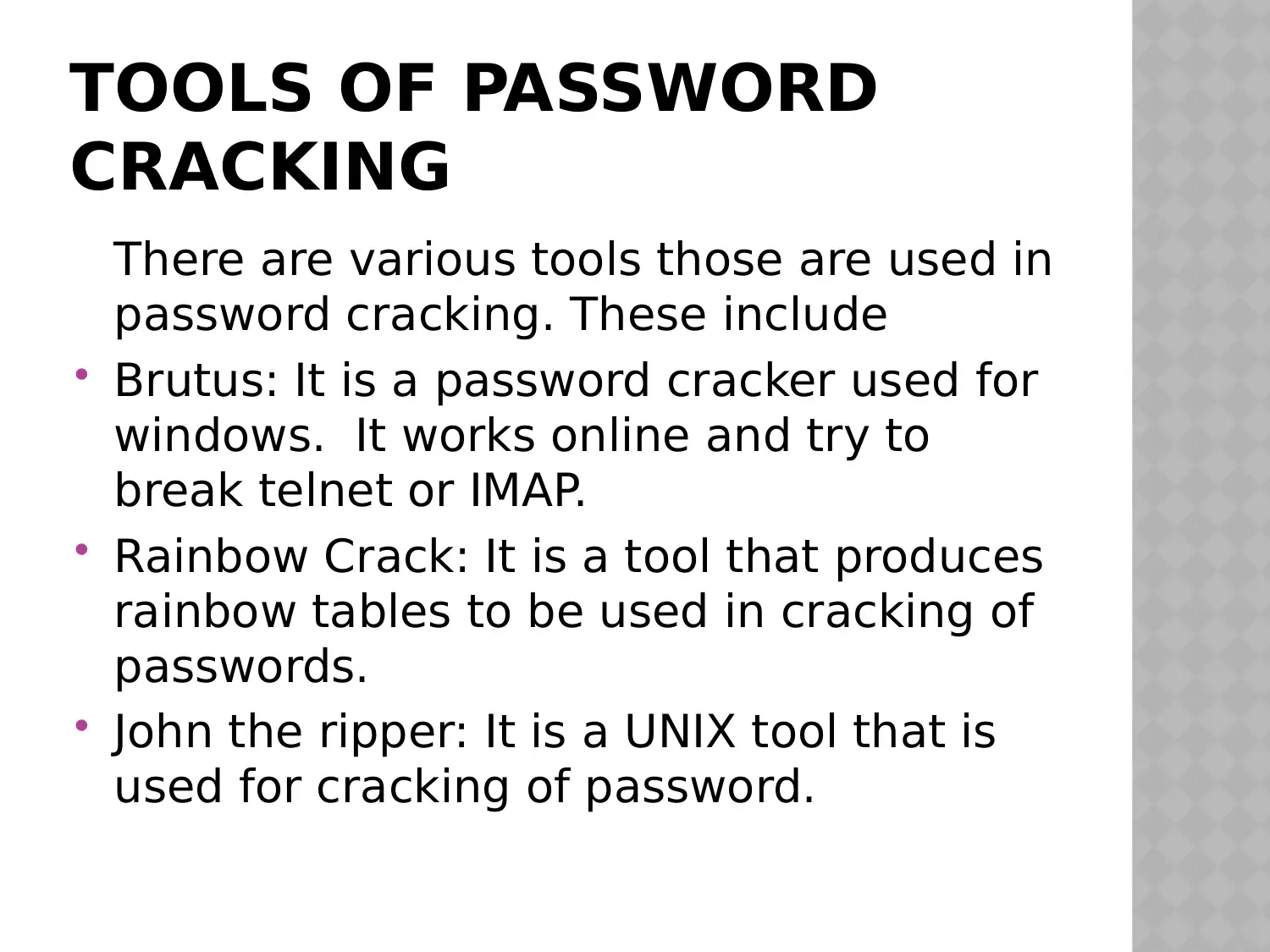
This presentation provides an overview of ethical hacking and penetration testing, covering essential concepts, tools, and techniques. It begins by defining ethical hacking and its significance, then delves into password security, including where passwords are stored in different operating systems like UNIX, Windows, and Mac OSX. The presentation explores various methods for viewing passwords and details the process of password cracking, including formulation, encryption, and comparison. It also examines different types of attacks, such as dictionary attacks, brute force attacks, and the use of rainbow tables. Furthermore, it lists and explains various password cracking tools like Brutus, Rainbow Crack, and John the Ripper. The presentation is concluded with a bibliography of relevant sources.
1 out of 10














![[object Object]](/_next/static/media/star-bottom.7253800d.svg)