IT Ethical Issues: Ethical Analysis of Spoofing Applications, CSU
VerifiedAdded on 2022/12/05
|7
|1706
|198
Essay
AI Summary
This essay delves into the ethical issues associated with spoofing applications, focusing on their potential harm to users and their data. The essay begins by outlining four key ethical theories: utilitarianism, deontology, virtue ethics, and social ethics. It then analyzes how these theories apply to the actions of spoofing apps, such as the use of push advertisements, data collection, and impersonation. The essay argues that spoofing apps often violate ethical principles by prioritizing third-party interests over user privacy and security. The essay examines how these apps can violate utilitarian principles by promoting advertisements that benefit third parties while potentially harming users. It also discusses how the apps breach deontology by collecting and using data without user consent. The essay also highlights how spoofing apps compromise virtue ethics by dishonesty and how they violate social ethics by violating societal norms. The essay concludes by emphasizing the potential dangers of spoofing apps and the importance of considering ethical implications when developing and using such applications.

Running Head: IT ETHICAL ISSUES
IT ETHICAL ISSUES
Name of the Student
Name of the University
Author Note
IT ETHICAL ISSUES
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1IT ETHICAL ISSUES
Introduction
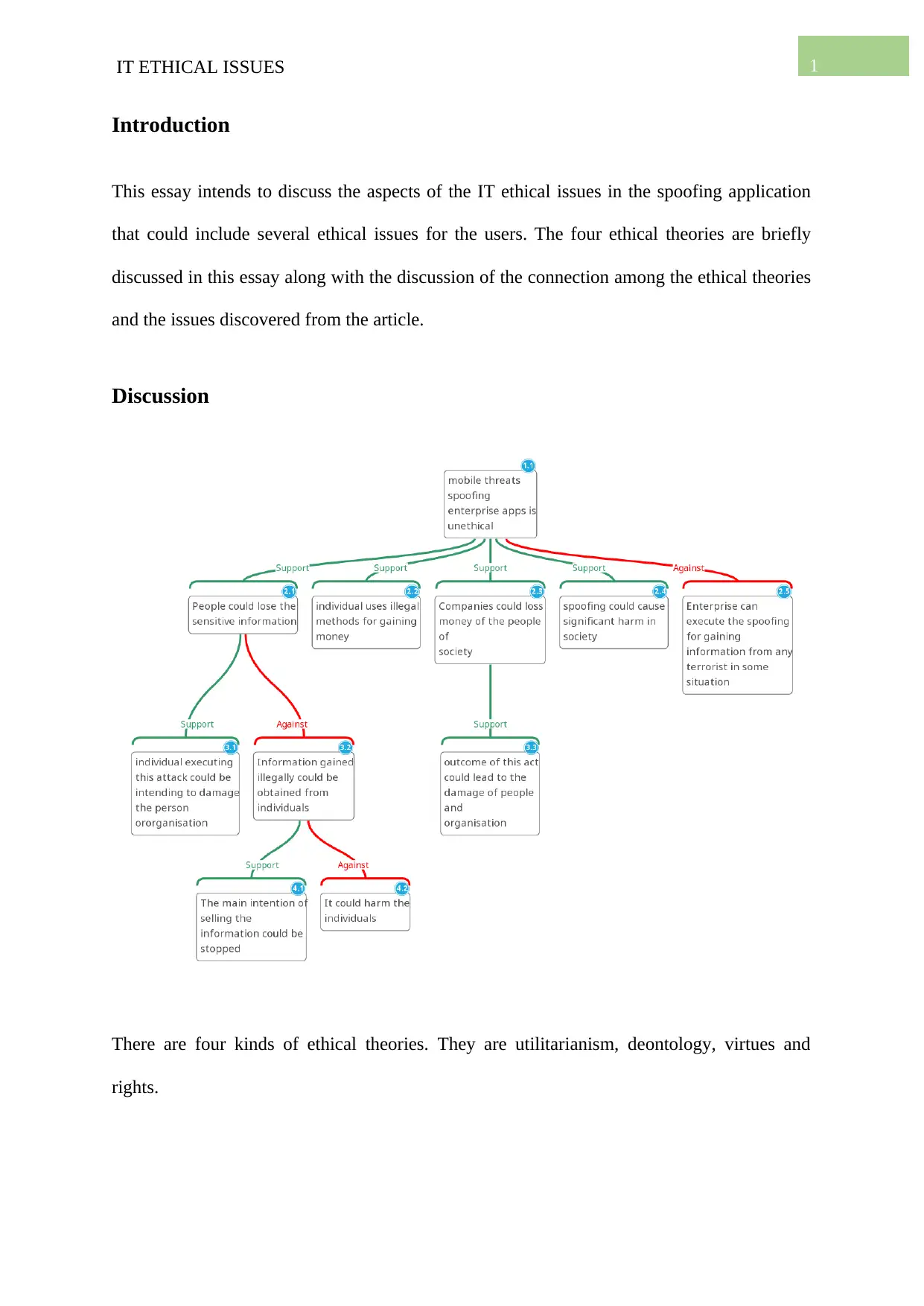
This essay intends to discuss the aspects of the IT ethical issues in the spoofing application
that could include several ethical issues for the users. The four ethical theories are briefly
discussed in this essay along with the discussion of the connection among the ethical theories
and the issues discovered from the article.
Discussion
There are four kinds of ethical theories. They are utilitarianism, deontology, virtues and
rights.
Introduction
This essay intends to discuss the aspects of the IT ethical issues in the spoofing application
that could include several ethical issues for the users. The four ethical theories are briefly
discussed in this essay along with the discussion of the connection among the ethical theories
and the issues discovered from the article.
Discussion
There are four kinds of ethical theories. They are utilitarianism, deontology, virtues and
rights.

2IT ETHICAL ISSUES
Utilitarianism approach of ethics involves the idea of consequentiality ethical theory
which encourages the idea of maximizing utility. Utilitarianism is in the normative ethical
theory class, which dictates that consequences of the action are the sole stakes to measure
right and wrong. In other words, the theory fosters the idea of greatest amount of good for the
greater count of individuals (Monteverde, 2014). Utilitarianism promotes pleasure and
happiness and rejects any kind of actions that lead to unhappiness or cause harm. When the
theory is considered in making decisions related to social, political and economical arena, the
aim is to better the society. Right produces happiness and the wrong reverses the process of
happiness and leads to sadness (Peters, 2015). Greatest happiness is the principle of
utilitarianism. In the political arena, it is believed that laws and regulations are fostered for
the well-being of maximum number of people. There are two parts to utilitarianism theory,
act utilitarianism and rule utilitarianism. Act utilitarianism principle is directly applied to the
action choice in a situation. The action which brings out the best result (minimizing bad
actions) out from the situation is considered the right act. Rule utilitarianism principle
defines the utility used in determining the validity of moral principle or the moral order of
conduct. For example, promise keeping- where in this contemporary word people easily
breaks promises and there are others who keep them. The right and wrong of the deed will be
defined by breaking or following rules. Ooqqxx application promotes advertisements, which
shows push ads on notification bars, pop up ads and ads when downloading something.
Advertisements promote products which are advantageous for the third party but can cause
problem for user. Utilitarian theory is followed as maximum utility is drawn and helps in
promotion of the third party. The ac can be considered good as the outcome is positive
Deontology theory of ethics can be simply defined as duty based non consequential
ethics. The decision making for this theory of ethics is non-consequential, which means
actions of an individual are not defined by consequences. The principle of the theory is
Utilitarianism approach of ethics involves the idea of consequentiality ethical theory
which encourages the idea of maximizing utility. Utilitarianism is in the normative ethical
theory class, which dictates that consequences of the action are the sole stakes to measure
right and wrong. In other words, the theory fosters the idea of greatest amount of good for the
greater count of individuals (Monteverde, 2014). Utilitarianism promotes pleasure and
happiness and rejects any kind of actions that lead to unhappiness or cause harm. When the
theory is considered in making decisions related to social, political and economical arena, the
aim is to better the society. Right produces happiness and the wrong reverses the process of
happiness and leads to sadness (Peters, 2015). Greatest happiness is the principle of
utilitarianism. In the political arena, it is believed that laws and regulations are fostered for
the well-being of maximum number of people. There are two parts to utilitarianism theory,
act utilitarianism and rule utilitarianism. Act utilitarianism principle is directly applied to the
action choice in a situation. The action which brings out the best result (minimizing bad
actions) out from the situation is considered the right act. Rule utilitarianism principle
defines the utility used in determining the validity of moral principle or the moral order of
conduct. For example, promise keeping- where in this contemporary word people easily
breaks promises and there are others who keep them. The right and wrong of the deed will be
defined by breaking or following rules. Ooqqxx application promotes advertisements, which
shows push ads on notification bars, pop up ads and ads when downloading something.
Advertisements promote products which are advantageous for the third party but can cause
problem for user. Utilitarian theory is followed as maximum utility is drawn and helps in
promotion of the third party. The ac can be considered good as the outcome is positive
Deontology theory of ethics can be simply defined as duty based non consequential
ethics. The decision making for this theory of ethics is non-consequential, which means
actions of an individual are not defined by consequences. The principle of the theory is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT ETHICAL ISSUES
concerned with the rightness of the action and not how good or bad the outcome is.
Deontology theory states that the means are important (Broad, 2014). Actions are considered
right if it is the right thing to do with being concerned of the possible outcome. The wrong
actions are avoided simply because it is not the right thing to do. Actions cannot be called
right actions just because they are showing a good consequence, that is the very reason it is
called non- consequential. The theory dictates that certain actions are moral (right) or
immoral (wrong) because that is how things are, and individuals are obliged to act in
accordance without regarding the consequences which can be both good and bad (Cannaerts,
Gastmans & Casterlé, 2014). Individual who follows this theory should take the right action
even if his or action produces harm or cause less good than taking a wrong action.
Individuals should perform the right duties irrespective of the results. If action is morally
right, then the person is performing good duty. Spoofing and impersonating apps breaches the
deontology theory of ethics. The apps impersonate itself and collects information from the
system it is present. The duty does not justify the consequences . The apps secretly steal data
and sends to the third party user. This leads to stealing of sensitive data and using it against
the person or the organization. Certain apps illegally send messages and also have the
capability to spam to contact lists. This function of the app could be violating the deontology
ethics.
Virtue ethical theory defines the morality of an individual and judges the individual
on his or her character. The actions of the person are not considered when his moral character
is judged as actions can cause deviation in the person’s normal behavior. The personal
character of the person is measured on the basis of reputation, motivation and moral. The
theory dictates to hold integrity and be honest in every action performed. The person is
expected to hold high morals (Norheim, 2016). The fundamental conditions for this theory of
ethics is virtue and vice. Virtue is a significant trait in a character. It is expected to practice
concerned with the rightness of the action and not how good or bad the outcome is.
Deontology theory states that the means are important (Broad, 2014). Actions are considered
right if it is the right thing to do with being concerned of the possible outcome. The wrong
actions are avoided simply because it is not the right thing to do. Actions cannot be called
right actions just because they are showing a good consequence, that is the very reason it is
called non- consequential. The theory dictates that certain actions are moral (right) or
immoral (wrong) because that is how things are, and individuals are obliged to act in
accordance without regarding the consequences which can be both good and bad (Cannaerts,
Gastmans & Casterlé, 2014). Individual who follows this theory should take the right action
even if his or action produces harm or cause less good than taking a wrong action.
Individuals should perform the right duties irrespective of the results. If action is morally
right, then the person is performing good duty. Spoofing and impersonating apps breaches the
deontology theory of ethics. The apps impersonate itself and collects information from the
system it is present. The duty does not justify the consequences . The apps secretly steal data
and sends to the third party user. This leads to stealing of sensitive data and using it against
the person or the organization. Certain apps illegally send messages and also have the
capability to spam to contact lists. This function of the app could be violating the deontology
ethics.
Virtue ethical theory defines the morality of an individual and judges the individual
on his or her character. The actions of the person are not considered when his moral character
is judged as actions can cause deviation in the person’s normal behavior. The personal
character of the person is measured on the basis of reputation, motivation and moral. The
theory dictates to hold integrity and be honest in every action performed. The person is
expected to hold high morals (Norheim, 2016). The fundamental conditions for this theory of
ethics is virtue and vice. Virtue is a significant trait in a character. It is expected to practice
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IT ETHICAL ISSUES
honesty and one should cheat the people who one is working with. A virtuous person is
honest, respected and hold better disposition than others to whom he is compared with.
Considering spoofing apps in mobile phones breaches the virtue ethics of conduct. Spoofing
apps roots a device and it is designed and developed to install itself in the system partition.
This makes it difficult to remove for the system (Drolet & Hudon, 2015). If the action of the
software is related to the virtue of ethics, it can be said that it breaches the theory as it
dishonestly configures itself into the system leading to further installations of malware apps.
Apps also impersonate organizational apps and rips off the package name and app’s name.
The apps also cause data risk. Accessing location secretly is unethical and breaches the
principle of virtue ethics.
Social ethics- This theory of ethics defines the rights and rules which has been set as
per societal norms. The rules and rights are regarded highly in the society and protections of
the rules are also observed (Dörr & Hollnbuchner, 2017). The rights are considered valid
ethically because a large number of individuals follows and endorses it in the society.
Society exercises and enacts rules to determine right and makes sure that the goals and ethical
priorities are also considered in determining the rights (Albert, Reynolds & Turan, 2015).
Individuals can exercise rights on their own and it is considered to be ethical. Apps like
AndroRat allows third party controlling of the device and collection of sensitive information.
Call logs, device location, messages and audio are accessed. The data acquired is maliciously
used by intruders which act against the right ethics. Hidden access leads easy access of data
and attackers can infiltrate into an enterprise’s database and network channel and cause
chaos.
honesty and one should cheat the people who one is working with. A virtuous person is
honest, respected and hold better disposition than others to whom he is compared with.
Considering spoofing apps in mobile phones breaches the virtue ethics of conduct. Spoofing
apps roots a device and it is designed and developed to install itself in the system partition.
This makes it difficult to remove for the system (Drolet & Hudon, 2015). If the action of the
software is related to the virtue of ethics, it can be said that it breaches the theory as it
dishonestly configures itself into the system leading to further installations of malware apps.
Apps also impersonate organizational apps and rips off the package name and app’s name.
The apps also cause data risk. Accessing location secretly is unethical and breaches the
principle of virtue ethics.
Social ethics- This theory of ethics defines the rights and rules which has been set as
per societal norms. The rules and rights are regarded highly in the society and protections of
the rules are also observed (Dörr & Hollnbuchner, 2017). The rights are considered valid
ethically because a large number of individuals follows and endorses it in the society.
Society exercises and enacts rules to determine right and makes sure that the goals and ethical
priorities are also considered in determining the rights (Albert, Reynolds & Turan, 2015).
Individuals can exercise rights on their own and it is considered to be ethical. Apps like
AndroRat allows third party controlling of the device and collection of sensitive information.
Call logs, device location, messages and audio are accessed. The data acquired is maliciously
used by intruders which act against the right ethics. Hidden access leads easy access of data
and attackers can infiltrate into an enterprise’s database and network channel and cause
chaos.

5IT ETHICAL ISSUES
Conclusion
Therefore, it can be concluded that the spoofing app could pose several unethical issues that
could be harmful for the customers and the users as it could endanger their life and the data of
the individuals. From the discussion of the ethical theories it could be concluded that the
theories are explicitly defined for determining the act on the basis of the associated ethical
issues. The apps secretly steal data and sends to the third party user. This leads to stealing of
sensitive data and using it against the person or the organization. Certain apps illegally send
messages and also have the capability to spam to contact lists. Virtue ethical theory defines
the morality of an individual and judges the individual on his or her character. The actions of
the person are not considered when his moral character is judged as actions can cause
deviation in the person’s normal behavior.
Conclusion
Therefore, it can be concluded that the spoofing app could pose several unethical issues that
could be harmful for the customers and the users as it could endanger their life and the data of
the individuals. From the discussion of the ethical theories it could be concluded that the
theories are explicitly defined for determining the act on the basis of the associated ethical
issues. The apps secretly steal data and sends to the third party user. This leads to stealing of
sensitive data and using it against the person or the organization. Certain apps illegally send
messages and also have the capability to spam to contact lists. Virtue ethical theory defines
the morality of an individual and judges the individual on his or her character. The actions of
the person are not considered when his moral character is judged as actions can cause
deviation in the person’s normal behavior.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6IT ETHICAL ISSUES
References
Albert, L. S., Reynolds, S. J., & Turan, B. (2015). Turning inward or focusing out?
Navigating theories of interpersonal and ethical cognitions to understand ethical
decision-making. Journal of Business Ethics, 130(2), 467-484.
Broad, C. D. (2014). Five types of ethical theory. Routledge.
Cannaerts, N., Gastmans, C., & Casterlé, B. D. D. (2014). Contribution of ethics education to
the ethical competence of nursing students: Educators’ and students’
perceptions. Nursing ethics, 21(8), 861-878.
Dörr, K. N., & Hollnbuchner, K. (2017). Ethical challenges of algorithmic journalism. Digital
journalism, 5(4), 404-419.
Drolet, M. J., & Hudon, A. (2015). Theoretical frameworks used to discuss ethical issues in
private physiotherapy practice and proposal of a new ethical tool. Medicine, health
care and philosophy, 18(1), 51-62.
Monteverde, S. (2014). Undergraduate healthcare ethics education, moral resilience, and the
role of ethical theories. Nursing ethics, 21(4), 385-401.
Norheim, O. F. (2016). Ethical priority setting for universal health coverage: challenges in
deciding upon fair distribution of health services. BMC medicine, 14(1), 75.
Peters, R. S. (2015). Psychology and Ethical Development (Routledge Revivals): A Collection
of Articles on Psychological Theories, Ethical Development and Human
Understanding. Routledge.
References
Albert, L. S., Reynolds, S. J., & Turan, B. (2015). Turning inward or focusing out?
Navigating theories of interpersonal and ethical cognitions to understand ethical
decision-making. Journal of Business Ethics, 130(2), 467-484.
Broad, C. D. (2014). Five types of ethical theory. Routledge.
Cannaerts, N., Gastmans, C., & Casterlé, B. D. D. (2014). Contribution of ethics education to
the ethical competence of nursing students: Educators’ and students’
perceptions. Nursing ethics, 21(8), 861-878.
Dörr, K. N., & Hollnbuchner, K. (2017). Ethical challenges of algorithmic journalism. Digital
journalism, 5(4), 404-419.
Drolet, M. J., & Hudon, A. (2015). Theoretical frameworks used to discuss ethical issues in
private physiotherapy practice and proposal of a new ethical tool. Medicine, health
care and philosophy, 18(1), 51-62.
Monteverde, S. (2014). Undergraduate healthcare ethics education, moral resilience, and the
role of ethical theories. Nursing ethics, 21(4), 385-401.
Norheim, O. F. (2016). Ethical priority setting for universal health coverage: challenges in
deciding upon fair distribution of health services. BMC medicine, 14(1), 75.
Peters, R. S. (2015). Psychology and Ethical Development (Routledge Revivals): A Collection
of Articles on Psychological Theories, Ethical Development and Human
Understanding. Routledge.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





