ICT Ethical Issue: Applying Ethical Theories to Argument Visualization
VerifiedAdded on 2023/01/23
|12
|2456
|46
Report
AI Summary
This report analyzes an ICT ethical issue, specifically focusing on the "EnforceTheOrder @FTC" case study concerning Facebook's privacy and security practices. The student uses argument visualization to illustrate the core arguments and then applies four classical ethical theories – utilitarianism, deontological ethics, social contract theory, and virtue analysis – to evaluate the case. The report discusses the FTC consent order, Facebook's security breaches, and the violation of user privacy. The student argues that the consent order is justified based on these ethical frameworks, highlighting the negative impacts of Facebook's actions on society and businesses. The report explores the strengths and weaknesses of each ethical theory in relation to the case and concludes by supporting the EPIC's decision, while acknowledging potential objections and counterarguments regarding the frequent revisions of security policies. This assignment, available on Desklib, provides an in-depth examination of ethical considerations in the context of information technology and social media.

Running head: ICT ETHICAL ISSUE
ICT Ethical Issue
Name of the Student
Name of the University
Author Note:
ICT Ethical Issue
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ICT ETHICAL ISSUE
Table of Contents
Assessment item 3: Argument visualization....................................................................................0
Assessment item 4: Applying Ethical Theory.................................................................................3
Reference.......................................................................................................................................10
Table of Contents
Assessment item 3: Argument visualization....................................................................................0
Assessment item 4: Applying Ethical Theory.................................................................................3
Reference.......................................................................................................................................10
2ICT ETHICAL ISSUE
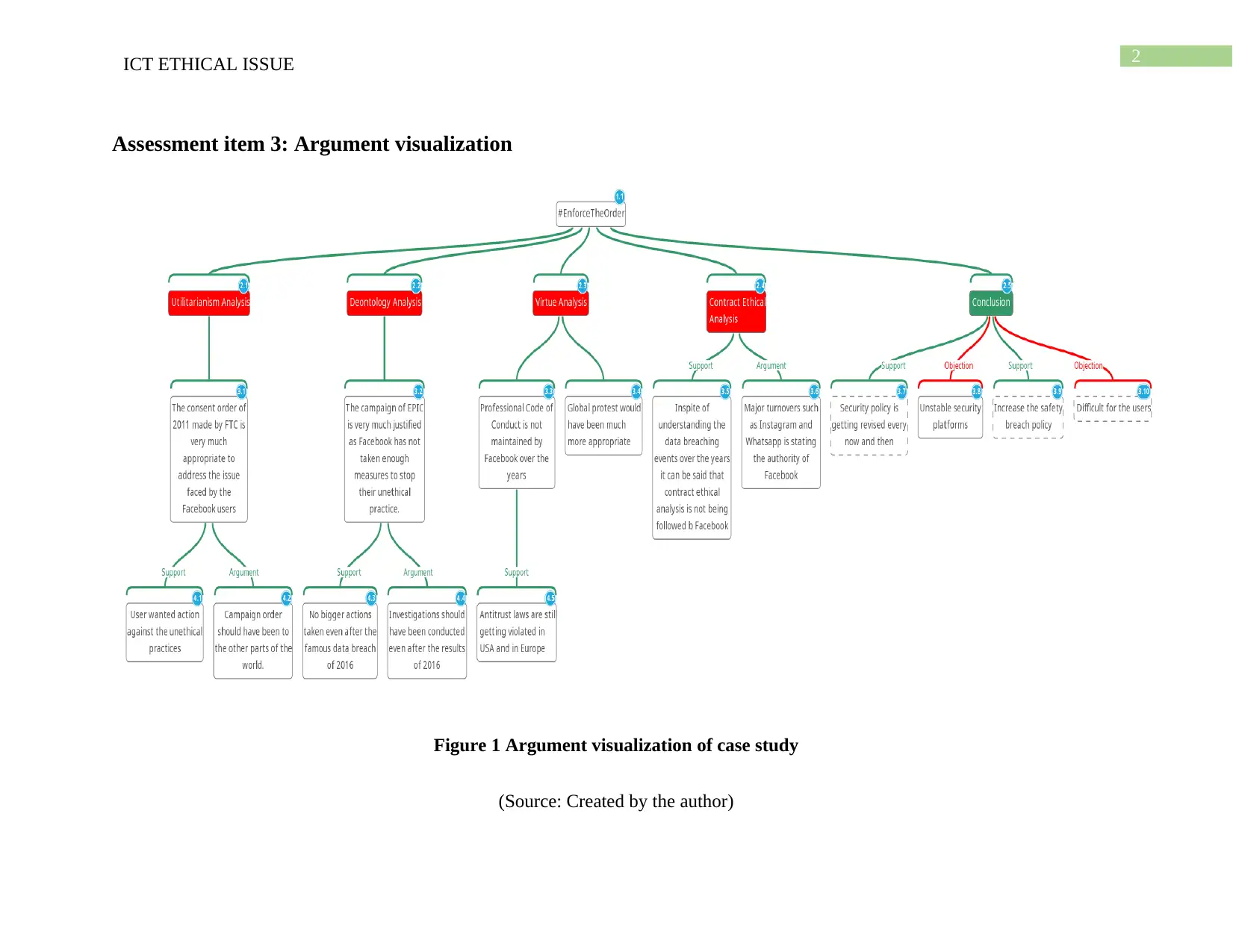
Assessment item 3: Argument visualization
Figure 1 Argument visualization of case study
(Source: Created by the author)
Assessment item 3: Argument visualization
Figure 1 Argument visualization of case study
(Source: Created by the author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ICT ETHICAL ISSUE
Assessment item 4: Applying Ethical Theory
Title of the paper: EnforceTheOrder @FTC
Introduction
The notable determination of this short essay is to focus on the argument visualization
which was presented in assessment item 4. The main objective of the essay is to explain the
argument visualization in a detailed manner with the help of four different ethical theories such
as the theory of Utilitarianism, deontological ethical theory, social contract theory and virtue
analysis.
Case study details
The case study which is focused in this paper is known as EnforceTheOrder @FTC. The
extensive developments in the field of information technology have resulted in the growth of
new technologies and platforms such as Instagram and Facebook. The application of this social
networking is increasing each day both in our society as well as in business organizations. As a
result of the wider application of Facebook, this social media platform also have few negative
impacts in our society as well in terms of the cybersecurity issues and other data breaching
events. Social engineers from different parts of the world are using Facebook as a medium for
cybersecurity threats. At the same time, it can be also said that Facebook was having a direct
negative impact in the business organizations where it was used as a communication platform.
Public wanted to have a direct action against face which is the main reason behind the passing of
the FTC consent order in the year 2009. The chief objective of the consent order is to deal with
the security and privacy issues of Facebook consumers all over the world. Even after repeated
campaigns Facebook have not revised their security policies and on top of that, this business
Assessment item 4: Applying Ethical Theory
Title of the paper: EnforceTheOrder @FTC
Introduction
The notable determination of this short essay is to focus on the argument visualization
which was presented in assessment item 4. The main objective of the essay is to explain the
argument visualization in a detailed manner with the help of four different ethical theories such
as the theory of Utilitarianism, deontological ethical theory, social contract theory and virtue
analysis.
Case study details
The case study which is focused in this paper is known as EnforceTheOrder @FTC. The
extensive developments in the field of information technology have resulted in the growth of
new technologies and platforms such as Instagram and Facebook. The application of this social
networking is increasing each day both in our society as well as in business organizations. As a
result of the wider application of Facebook, this social media platform also have few negative
impacts in our society as well in terms of the cybersecurity issues and other data breaching
events. Social engineers from different parts of the world are using Facebook as a medium for
cybersecurity threats. At the same time, it can be also said that Facebook was having a direct
negative impact in the business organizations where it was used as a communication platform.
Public wanted to have a direct action against face which is the main reason behind the passing of
the FTC consent order in the year 2009. The chief objective of the consent order is to deal with
the security and privacy issues of Facebook consumers all over the world. Even after repeated
campaigns Facebook have not revised their security policies and on top of that, this business
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4ICT ETHICAL ISSUE
organization is growing their markets in every corner of the world. Major turnovers of Facebook
such as Whats-app and Instagram has increased the probability of security attacks. Even after
major data breached event in the year 2016, no sufficient security steps were taken by Facebook
to address the privacy control of their users. The anti-trust laws of United States are getting
violated each day, at the same time it can be also said that the efforts made by the public interest
research group went in vain over the years. According to the investigative sources of United
States it was found that more than 148 million users of Facebook have been spammed in 2016.
The safeguard rules of most of the countries are regularly breached by the ethical practices of
Facebook. The anti-trust arms if each of the countries were unable to contain these unethical
breaches. It can be also said that the consent order was totally ignored by the Facebook
Corporation. The freedom of information is getting violated each day, at the same time it can be
said that the privacy control should be also revised as quickly as possible in order to deal with
the security issues of both Facebook along with its subsidiary organizations such as Whatsapp
and Instagram.
The following unit of the paper will be discussing the case study with the help of the four
classical ethical theory such as deontological ethical theory, Utilitarianism, virtue analysis and
social contract theory.
Utilitarianism theory
This classical ethical theory is very closely associated with the concept of consequentialist
ethical theory. The promotions of the actions which helps in maximizing the well-being and the
happiness of the society. The morality of society is very much related to this ethical theory. This
normative theory helps in determining the morality of actions and happiness of the people which
are supposed to be analyzed.
organization is growing their markets in every corner of the world. Major turnovers of Facebook
such as Whats-app and Instagram has increased the probability of security attacks. Even after
major data breached event in the year 2016, no sufficient security steps were taken by Facebook
to address the privacy control of their users. The anti-trust laws of United States are getting
violated each day, at the same time it can be also said that the efforts made by the public interest
research group went in vain over the years. According to the investigative sources of United
States it was found that more than 148 million users of Facebook have been spammed in 2016.
The safeguard rules of most of the countries are regularly breached by the ethical practices of
Facebook. The anti-trust arms if each of the countries were unable to contain these unethical
breaches. It can be also said that the consent order was totally ignored by the Facebook
Corporation. The freedom of information is getting violated each day, at the same time it can be
said that the privacy control should be also revised as quickly as possible in order to deal with
the security issues of both Facebook along with its subsidiary organizations such as Whatsapp
and Instagram.
The following unit of the paper will be discussing the case study with the help of the four
classical ethical theory such as deontological ethical theory, Utilitarianism, virtue analysis and
social contract theory.
Utilitarianism theory
This classical ethical theory is very closely associated with the concept of consequentialist
ethical theory. The promotions of the actions which helps in maximizing the well-being and the
happiness of the society. The morality of society is very much related to this ethical theory. This
normative theory helps in determining the morality of actions and happiness of the people which
are supposed to be analyzed.

5ICT ETHICAL ISSUE
Based on the ethical theory it can be said that the consent order which was passed in the
year 2011 is very much beneficial for our society as it was meant to fight for the rights of the
Facebook users (Chang, Liu & Shen, 2017). The casual approach of the Facebook Corporation
was having a direct negative effect on both the different types of business enterprises as well as
in our society. The passing of the FTC order could have helped the users to maintain privacy and
security as this social media platform was having a direct negative effect on the net profitability
of the business.
Most of the Facebook users all over the world were having security issues for longer
period of time and they were all aware of the security issues of Facebook along with its
subsidiary organization such as Instagram and Whatsapp (Buehler, 2017). The Facebook
Corporation was not at all taking necessary steps to counter the scenario. Thus it can be said this
theory is very much justified in this scenario.
However, it can be also said that the campaign order could have been spread to the other
parts of the world so that the effectiveness of the campaign is maintained throughout the business
area of Facebook.
Deontological theory
The deontological ethical theory can be defined as the type of theory which can be very
much helpful to maintain the morality of the action of an entity. The basis of morality is the
wrong and the rightness of the people under a series of rules. The consequences of action are not
all considered in this normative ethical theory (DeGroot & Vik, 2017). This classical theory
suggests that a set of rules and policies can be very much important for the proper functionality
Based on the ethical theory it can be said that the consent order which was passed in the
year 2011 is very much beneficial for our society as it was meant to fight for the rights of the
Facebook users (Chang, Liu & Shen, 2017). The casual approach of the Facebook Corporation
was having a direct negative effect on both the different types of business enterprises as well as
in our society. The passing of the FTC order could have helped the users to maintain privacy and
security as this social media platform was having a direct negative effect on the net profitability
of the business.
Most of the Facebook users all over the world were having security issues for longer
period of time and they were all aware of the security issues of Facebook along with its
subsidiary organization such as Instagram and Whatsapp (Buehler, 2017). The Facebook
Corporation was not at all taking necessary steps to counter the scenario. Thus it can be said this
theory is very much justified in this scenario.
However, it can be also said that the campaign order could have been spread to the other
parts of the world so that the effectiveness of the campaign is maintained throughout the business
area of Facebook.
Deontological theory
The deontological ethical theory can be defined as the type of theory which can be very
much helpful to maintain the morality of the action of an entity. The basis of morality is the
wrong and the rightness of the people under a series of rules. The consequences of action are not
all considered in this normative ethical theory (DeGroot & Vik, 2017). This classical theory
suggests that a set of rules and policies can be very much important for the proper functionality
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ICT ETHICAL ISSUE
of the system. The application of this theory is much easier as compared with the other three
classical ethical theories.
Based on the deontological ethics it can be said that the Facebook Corporation has not at
all maintained the morality of actions as the security measures are always overlooked by the
social engineers. The series of security measures which were taken by Facebook was not at all
sufficient enough to stop the unethical practices. On the basis of this classical ethical theory, it
can be said that the rule and regulations of Facebook are not at all sufficient to regulate the
unethical practices of the social engineers which use Facebook for all the data breaching
activities (Farkas & Neumayer, 2017). Thus, it can be said that the FTC consent order is very
much justified as Facebook Corporation has not taken sufficient measures to contain the data
breaching activities even after the major incident of Cambridge Analytica.
However, according to the deontological analysis, it can be said that the investigations
should have been continued in the Cambridge Analytica case which resulted in huge political
turmoil in both UK and USA and led to the fall of Barrack Obama from the White House in the
year 2016.
Contract theory
It is defined as the type of classical ethical theory which is very closely related with the
economic actors of a business organization or a similar entity (Fox & Moreland, 2015). This
theory can be successfully used in most of the business organization to manage the business
uncertainties of both the internal as well as the external stakeholders.
This classical ethical theory can be very much related with the above-discussed case study. The
connection between the law and economics in this scenario can be justified, the Facebook
of the system. The application of this theory is much easier as compared with the other three
classical ethical theories.
Based on the deontological ethics it can be said that the Facebook Corporation has not at
all maintained the morality of actions as the security measures are always overlooked by the
social engineers. The series of security measures which were taken by Facebook was not at all
sufficient enough to stop the unethical practices. On the basis of this classical ethical theory, it
can be said that the rule and regulations of Facebook are not at all sufficient to regulate the
unethical practices of the social engineers which use Facebook for all the data breaching
activities (Farkas & Neumayer, 2017). Thus, it can be said that the FTC consent order is very
much justified as Facebook Corporation has not taken sufficient measures to contain the data
breaching activities even after the major incident of Cambridge Analytica.
However, according to the deontological analysis, it can be said that the investigations
should have been continued in the Cambridge Analytica case which resulted in huge political
turmoil in both UK and USA and led to the fall of Barrack Obama from the White House in the
year 2016.
Contract theory
It is defined as the type of classical ethical theory which is very closely related with the
economic actors of a business organization or a similar entity (Fox & Moreland, 2015). This
theory can be successfully used in most of the business organization to manage the business
uncertainties of both the internal as well as the external stakeholders.
This classical ethical theory can be very much related with the above-discussed case study. The
connection between the law and economics in this scenario can be justified, the Facebook
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7ICT ETHICAL ISSUE
Corporation is not able to contain all the spamming activities even after repeated legal changes
against them (Kökciyan & Yolum, 2016). Considering this ethical theory it can be said that the
Facebook Corporation have taken no major steps to address the complaints coming from the
users regarding maintaining the privacy and security of the data which are always in a threat of
being altered or encrypted by the social engineers. On top of that, it can be also said that social
engineers are always taking innovative steps in each of their recent cybersecurity attacks (Lang
& Barton, 2015). On the basis of this scenario, it can be also said that the recruitment process of
Facebook must be revised so that there are no inefficient employees working within the
organization, this practice would be also securing the users of both WhatsApp as well as
Instagram.
However, it can be said that the major turnovers such as the Instagram and Whatsapp by
the Facebook Corporations can be the reason behind the security issues in those platforms also.
Thus, it can be said that the #EnforceTheOrder is very much justified as it may help to protect
the security and the privacy of the data of Facebook users.
Virtue analysis
It is defined as the type of ethical theory which are very much responsible for
maintaining the security and privacy of data sets. This normative ethical theory can be compared
with the deontological ethical theory as it is based on realistic events.
Based on the virtue analysis it can be said that the professional code of conduct is not all at
maintained by Facebook Corporation as the spammers and other cybercriminals are making the
most out social media platforms such as Facebook and Instagram. Facebook authorities are not
taking any kind of security steps in order to contain the issue (Miron & Ravid, 2015). The global
Corporation is not able to contain all the spamming activities even after repeated legal changes
against them (Kökciyan & Yolum, 2016). Considering this ethical theory it can be said that the
Facebook Corporation have taken no major steps to address the complaints coming from the
users regarding maintaining the privacy and security of the data which are always in a threat of
being altered or encrypted by the social engineers. On top of that, it can be also said that social
engineers are always taking innovative steps in each of their recent cybersecurity attacks (Lang
& Barton, 2015). On the basis of this scenario, it can be also said that the recruitment process of
Facebook must be revised so that there are no inefficient employees working within the
organization, this practice would be also securing the users of both WhatsApp as well as
Instagram.
However, it can be said that the major turnovers such as the Instagram and Whatsapp by
the Facebook Corporations can be the reason behind the security issues in those platforms also.
Thus, it can be said that the #EnforceTheOrder is very much justified as it may help to protect
the security and the privacy of the data of Facebook users.
Virtue analysis
It is defined as the type of ethical theory which are very much responsible for
maintaining the security and privacy of data sets. This normative ethical theory can be compared
with the deontological ethical theory as it is based on realistic events.
Based on the virtue analysis it can be said that the professional code of conduct is not all at
maintained by Facebook Corporation as the spammers and other cybercriminals are making the
most out social media platforms such as Facebook and Instagram. Facebook authorities are not
taking any kind of security steps in order to contain the issue (Miron & Ravid, 2015). The global

8ICT ETHICAL ISSUE
protest would have make this campaign much more successful as it will be making a huge point
in a global platform. Thus, it can be said that the consent order against Facebook which was
launched in the year is highly justified.
The following unit of the paper will be discussing the conclusion of this scenario with the help of
two supporting as well as two objections.
Conclusion
The conclusion of this scenario states that the decision taken by EPIC is very much justified as
the security and the privacy of the Facebook users are getting compromised very frequently since
the Cambridge Analytica (Nicholls & Rice, 2017).
Support: To support this decision it can be said that the security policy of Facebook is getting
revised very frequent every now and then.
Objection: It can be said that the the frequent revision of the scenario could have hampered the
security of the social media platform (Rathore et al., 2017).
Support: The safety breach policy of Facebook must be increased in the first place in order to
deal with the security threats of Facebook which led to the re-considering the consent order in
the year 2018.
Objection: The incorporation of the safety breach policy can have an adverse effect for the users
of Facebook as the user-friendliness of Facebook might get affected by the frequent updating
procedure.
Overall Conclusion
protest would have make this campaign much more successful as it will be making a huge point
in a global platform. Thus, it can be said that the consent order against Facebook which was
launched in the year is highly justified.
The following unit of the paper will be discussing the conclusion of this scenario with the help of
two supporting as well as two objections.
Conclusion
The conclusion of this scenario states that the decision taken by EPIC is very much justified as
the security and the privacy of the Facebook users are getting compromised very frequently since
the Cambridge Analytica (Nicholls & Rice, 2017).
Support: To support this decision it can be said that the security policy of Facebook is getting
revised very frequent every now and then.
Objection: It can be said that the the frequent revision of the scenario could have hampered the
security of the social media platform (Rathore et al., 2017).
Support: The safety breach policy of Facebook must be increased in the first place in order to
deal with the security threats of Facebook which led to the re-considering the consent order in
the year 2018.
Objection: The incorporation of the safety breach policy can have an adverse effect for the users
of Facebook as the user-friendliness of Facebook might get affected by the frequent updating
procedure.
Overall Conclusion
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9ICT ETHICAL ISSUE
The essay helps in understanding the argument visualization which are presented in the
previous assessment. The chosen media article stated about the re-launching of the consent order
against the illegal practices of Facebook. The paper is very much important to understand the
scenario with respect to the four classical ethical theories. The lack of professionalism of
Facebook can be determined from the paper as well. The importance of maintaining security and
privacy can be also determined from the paper as well.
The essay helps in understanding the argument visualization which are presented in the
previous assessment. The chosen media article stated about the re-launching of the consent order
against the illegal practices of Facebook. The paper is very much important to understand the
scenario with respect to the four classical ethical theories. The lack of professionalism of
Facebook can be determined from the paper as well. The importance of maintaining security and
privacy can be also determined from the paper as well.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10ICT ETHICAL ISSUE
Reference
Buehler, E. M. (2017). “You Shouldn’t Use Facebook for That”: Navigating Norm Violations
While Seeking Emotional Support on Facebook. Social Media+ Society, 3(3),
2056305117733225.
Chang, S. E., Liu, A. Y., & Shen, W. C. (2017). User trust in social networking services: A
comparison of Facebook and LinkedIn. Computers in Human Behavior, 69, 207-217.
DeGroot, J. M., & Vik, T. A. (2017). “We were not prepared to tell people yet”: Confidentiality
breaches and boundary turbulence on Facebook. Computers in Human Behavior, 70, 351-
359.
Farkas, J., & Neumayer, C. (2017). ‘Stop Fake Hate Profiles on Facebook’: Challenges for
crowdsourced activism on social media. First Monday, 22(9).
Fox, J., & Moreland, J. J. (2015). The dark side of social networking sites: An exploration of the
relational and psychological stressors associated with Facebook use and affordances.
Computers in Human Behavior, 45, 168-176.
Kökciyan, N., & Yolum, P. (2016). P ri g uard: A semantic approach to detect privacy violations
in online social networks. IEEE Transactions on Knowledge and Data Engineering,
28(10), 2724-2737.
Lang, C., & Barton, H. (2015). Just untag it: Exploring the management of undesirable Facebook
photos. Computers in Human Behavior, 43, 147-155.
Reference
Buehler, E. M. (2017). “You Shouldn’t Use Facebook for That”: Navigating Norm Violations
While Seeking Emotional Support on Facebook. Social Media+ Society, 3(3),
2056305117733225.
Chang, S. E., Liu, A. Y., & Shen, W. C. (2017). User trust in social networking services: A
comparison of Facebook and LinkedIn. Computers in Human Behavior, 69, 207-217.
DeGroot, J. M., & Vik, T. A. (2017). “We were not prepared to tell people yet”: Confidentiality
breaches and boundary turbulence on Facebook. Computers in Human Behavior, 70, 351-
359.
Farkas, J., & Neumayer, C. (2017). ‘Stop Fake Hate Profiles on Facebook’: Challenges for
crowdsourced activism on social media. First Monday, 22(9).
Fox, J., & Moreland, J. J. (2015). The dark side of social networking sites: An exploration of the
relational and psychological stressors associated with Facebook use and affordances.
Computers in Human Behavior, 45, 168-176.
Kökciyan, N., & Yolum, P. (2016). P ri g uard: A semantic approach to detect privacy violations
in online social networks. IEEE Transactions on Knowledge and Data Engineering,
28(10), 2724-2737.
Lang, C., & Barton, H. (2015). Just untag it: Exploring the management of undesirable Facebook
photos. Computers in Human Behavior, 43, 147-155.

11ICT ETHICAL ISSUE
Miron, E., & Ravid, G. (2015). Facebook groups as an academic teaching aid: Case study and
recommendations for educators. Journal of Educational Technology & Society, 18(4),
371-384.
Nicholls, S. B., & Rice, R. E. (2017). A dual-identity model of responses to deviance in online
groups: integrating social identity theory and expectancy violations theory.
Communication Theory, 27(3), 243-268.
Rathore, S., Sharma, P. K., Loia, V., Jeong, Y. S., & Park, J. H. (2017). Social network security:
Issues, challenges, threats, and solutions. Information sciences, 421, 43-69.
Miron, E., & Ravid, G. (2015). Facebook groups as an academic teaching aid: Case study and
recommendations for educators. Journal of Educational Technology & Society, 18(4),
371-384.
Nicholls, S. B., & Rice, R. E. (2017). A dual-identity model of responses to deviance in online
groups: integrating social identity theory and expectancy violations theory.
Communication Theory, 27(3), 243-268.
Rathore, S., Sharma, P. K., Loia, V., Jeong, Y. S., & Park, J. H. (2017). Social network security:
Issues, challenges, threats, and solutions. Information sciences, 421, 43-69.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





