Analysis of Ethical Concerns Related to Mobile Threats: A Report
VerifiedAdded on 2022/12/15
|8
|1540
|339
Report
AI Summary
This report delves into the ethical concerns arising from mobile threats, using the reopening of the Facebook investigation (#EnforceTheOrder) as a case study. The report explores the implications of Facebook's alleged privacy violations, including the gathering and leaking of health data without user consent. It applies four classical ethical theories – utilitarianism, deontology, contractual theory, and virtue theory – to analyze the ethical dimensions of the case. The report examines how each theory informs the assessment of Facebook's actions and the actions (or inactions) of the Federal Trade Commission (FTC). The analysis considers potential outcomes and proposes recommendations based on each ethical framework, ultimately concluding that adherence to security standards and maintenance of law and order are crucial for safeguarding user data and privacy within social networking platforms. The report highlights the importance of regular security revisions to maintain the stability of security platforms.

Running head: ETHICAL CONCERNS RELATED TO MOBILE THREATS
Ethical Concerns related to Mobile Threats
Name of the Student
Name of the University
Author’s note
Ethical Concerns related to Mobile Threats
Name of the Student
Name of the University
Author’s note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ETHICAL CONCERNS RELATED TO MOBILE THREATS
Table of Contents
Argument Visualisation...................................................................................................................2
1. Introduction..................................................................................................................................3
2. Discussion....................................................................................................................................3
2.1 Classical Ethical Theory........................................................................................................3
2.1.1 Utilitarianism Theory......................................................................................................3
2.1.2 Deontology Theory.........................................................................................................4
2.1.3 Contractual Theory.........................................................................................................4
2.1.4 Virtue Theory..................................................................................................................5
3. Conclusion...................................................................................................................................6
References........................................................................................................................................7
Table of Contents
Argument Visualisation...................................................................................................................2
1. Introduction..................................................................................................................................3
2. Discussion....................................................................................................................................3
2.1 Classical Ethical Theory........................................................................................................3
2.1.1 Utilitarianism Theory......................................................................................................3
2.1.2 Deontology Theory.........................................................................................................4
2.1.3 Contractual Theory.........................................................................................................4
2.1.4 Virtue Theory..................................................................................................................5
3. Conclusion...................................................................................................................................6
References........................................................................................................................................7
2ETHICAL CONCERNS RELATED TO MOBILE THREATS
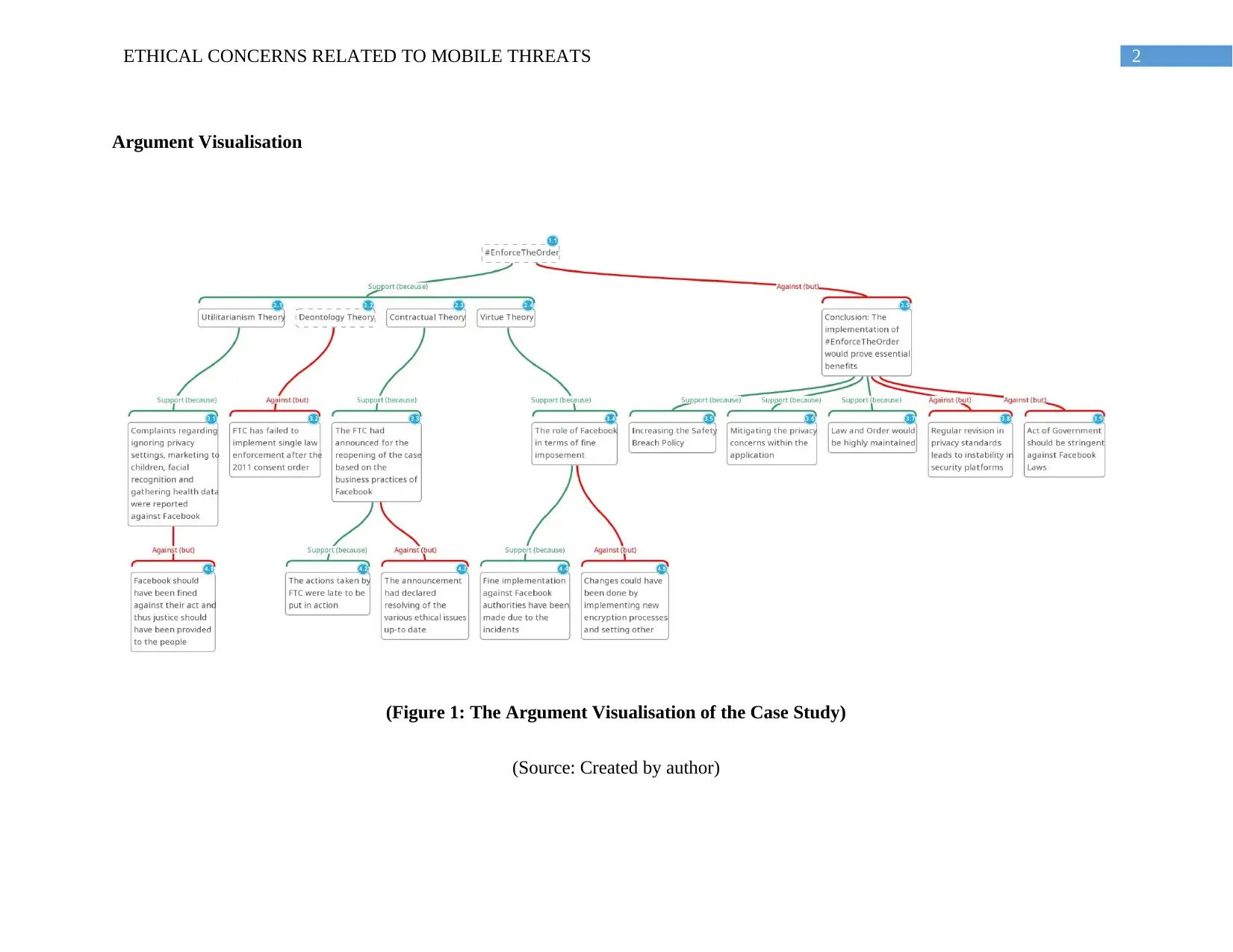
Argument Visualisation
(Figure 1: The Argument Visualisation of the Case Study)
(Source: Created by author)
Argument Visualisation
(Figure 1: The Argument Visualisation of the Case Study)
(Source: Created by author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ETHICAL CONCERNS RELATED TO MOBILE THREATS
1. Introduction
The case study is based on the reopening of the investigation over Facebook that was
named as #EnforceTheOrder. This campaign was launched by Electronic Privacy Information
Center (EPIC) in order to ensure the proper law and order within the use of the social media
platform. The primary urge of the campaign was to urge the Federal Trade Commission to
implement the act before 26th March, 2019 (FTC: Enforce the Order, 2019). The report is based
on the understanding of the case and also implementing the knowledge from the four classical
ethical theories that would be put in order to ensure the possible outcomes from the scenario.
2. Discussion
2.1 Classical Ethical Theory
2.1.1 Utilitarianism Theory
According to the Utilitarianism Theory, it defines the locus of wrong and right actions
that would mainly be the outcomes. As per the supported case, it is defined that the complaints
regarding ignorance of privacy settings had been reported to Facebook. Facebook were also
committing crimes in relation to gathering health data and also leaking them without prior
information to users. However, this could be considered as highly unethical and thus could lead
to serious implications for the people and the company (Oghuma et al., 2016). Hence, Facebook
should had been fined for their acts. A serious law should had been implicated towards the
company by the Government, which could had been helpful in bringing better outcomes for the
people.
1. Introduction
The case study is based on the reopening of the investigation over Facebook that was
named as #EnforceTheOrder. This campaign was launched by Electronic Privacy Information
Center (EPIC) in order to ensure the proper law and order within the use of the social media
platform. The primary urge of the campaign was to urge the Federal Trade Commission to
implement the act before 26th March, 2019 (FTC: Enforce the Order, 2019). The report is based
on the understanding of the case and also implementing the knowledge from the four classical
ethical theories that would be put in order to ensure the possible outcomes from the scenario.
2. Discussion
2.1 Classical Ethical Theory
2.1.1 Utilitarianism Theory
According to the Utilitarianism Theory, it defines the locus of wrong and right actions
that would mainly be the outcomes. As per the supported case, it is defined that the complaints
regarding ignorance of privacy settings had been reported to Facebook. Facebook were also
committing crimes in relation to gathering health data and also leaking them without prior
information to users. However, this could be considered as highly unethical and thus could lead
to serious implications for the people and the company (Oghuma et al., 2016). Hence, Facebook
should had been fined for their acts. A serious law should had been implicated towards the
company by the Government, which could had been helpful in bringing better outcomes for the
people.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4ETHICAL CONCERNS RELATED TO MOBILE THREATS
2.1.2 Deontology Theory
The theory can be defined as an ethical theory, which makes use of certain rules for the
purpose of distinguishing the right actions from the wrong actions. The proposed theory would
require the people to follow certain rules and thus perform their duty. From the case study, it can
be discussed that the FTC had majorly failed to launch the implementation of a particular law
(Koven, 2015). This law would be taken by a single enforcement action against the company in
order to establish law and order within the online social community. This could be thus regarded
as a negative impact as FTC did not give importance to the pleas and of the people. There is a
moral obligation of Facebook to keep up to the promises of the business and thus ensure that the
privacy of their website should be maintained (Berreby, Bourgne & Ganascia, 2017). Hence, the
FTC should had understood the complaints of the people and thus would had taken stringent
actions to deal with the raised issues.
2.1.3 Contractual Theory
According to the contractual theory, it can be defined about the ways in which
organizations and people would be able to deliver different legal agreements in critical situations.
There would also be situations that would bring unknown factors. The contractual theory could
be applied to different organisations in which there would be a principal factor (Johnson & Sohi,
2016). Other contracts or agents would also be created by a single individual or organisation that
would be able to specify the agreements between multiple parties that could also involve
contracts created by employees.
In the certain case, the FTC had announced based on the reopening of the case that would
be in relation to the several illegal practices that are occurring within the company. Based on the
contractual theory, these actions could be supported as FTC were late in taking actions against
2.1.2 Deontology Theory
The theory can be defined as an ethical theory, which makes use of certain rules for the
purpose of distinguishing the right actions from the wrong actions. The proposed theory would
require the people to follow certain rules and thus perform their duty. From the case study, it can
be discussed that the FTC had majorly failed to launch the implementation of a particular law
(Koven, 2015). This law would be taken by a single enforcement action against the company in
order to establish law and order within the online social community. This could be thus regarded
as a negative impact as FTC did not give importance to the pleas and of the people. There is a
moral obligation of Facebook to keep up to the promises of the business and thus ensure that the
privacy of their website should be maintained (Berreby, Bourgne & Ganascia, 2017). Hence, the
FTC should had understood the complaints of the people and thus would had taken stringent
actions to deal with the raised issues.
2.1.3 Contractual Theory
According to the contractual theory, it can be defined about the ways in which
organizations and people would be able to deliver different legal agreements in critical situations.
There would also be situations that would bring unknown factors. The contractual theory could
be applied to different organisations in which there would be a principal factor (Johnson & Sohi,
2016). Other contracts or agents would also be created by a single individual or organisation that
would be able to specify the agreements between multiple parties that could also involve
contracts created by employees.
In the certain case, the FTC had announced based on the reopening of the case that would
be in relation to the several illegal practices that are occurring within the company. Based on the
contractual theory, these actions could be supported as FTC were late in taking actions against

5ETHICAL CONCERNS RELATED TO MOBILE THREATS
the company (Stufflebeam & Coryn, 2014). However, the decision taken by FTC could not be
supported after they had taken actions as the late declaring of actions could not prove vital about
the ethical issues. Taking proper actions in the right time would be beneficial for the company
and the people involved within the company. The company had increased the security of the
website after the growth of such kind of statements. Hence, a lot of people were affected during
the breach. This late implementation of high security within the website had proved to be fatal
factor for the company and their reputation.
2.1.4 Virtue Theory
The virtue ethics can also be defined as normative ethical theories, which would be able
to emphasize the virtues of character and mind. The ethicists who follow the virtue theory would
be able to discuss the definition and nature of several virtues and all other forms of related
problems (DeVellis, 2016). A virtue could also be defined a character trait that could include a
habitual actions or some form of settled statement.
According to the case study, the virtue theory could be in support with the role of
Facebook as they had imposed certain actions after the crime had been committed. This
discussion could be supported in terms of virtue theory as the fine to be imposed over Facebook
would be seen as critical. The company did not make a hurry in implementing several security
measures within the organisation. This was essential as the rate at which the data was breached
was considered to be much high as compared to actions taken. On the other hand, the actions
taken under the virtue theory could be considered as against the theory (Kosters & Van der
Heijden, 2015). These changes could have been done with the implementation of various forms
of encryption processes within the system. In order to implement such kind of systems, the
company should be able to implement and set new kind of security policies as per the latest
the company (Stufflebeam & Coryn, 2014). However, the decision taken by FTC could not be
supported after they had taken actions as the late declaring of actions could not prove vital about
the ethical issues. Taking proper actions in the right time would be beneficial for the company
and the people involved within the company. The company had increased the security of the
website after the growth of such kind of statements. Hence, a lot of people were affected during
the breach. This late implementation of high security within the website had proved to be fatal
factor for the company and their reputation.
2.1.4 Virtue Theory
The virtue ethics can also be defined as normative ethical theories, which would be able
to emphasize the virtues of character and mind. The ethicists who follow the virtue theory would
be able to discuss the definition and nature of several virtues and all other forms of related
problems (DeVellis, 2016). A virtue could also be defined a character trait that could include a
habitual actions or some form of settled statement.
According to the case study, the virtue theory could be in support with the role of
Facebook as they had imposed certain actions after the crime had been committed. This
discussion could be supported in terms of virtue theory as the fine to be imposed over Facebook
would be seen as critical. The company did not make a hurry in implementing several security
measures within the organisation. This was essential as the rate at which the data was breached
was considered to be much high as compared to actions taken. On the other hand, the actions
taken under the virtue theory could be considered as against the theory (Kosters & Van der
Heijden, 2015). These changes could have been done with the implementation of various forms
of encryption processes within the system. In order to implement such kind of systems, the
company should be able to implement and set new kind of security policies as per the latest
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ETHICAL CONCERNS RELATED TO MOBILE THREATS
standards. These would be highly beneficial for the company to protect the data rights and
privacy of the data of people.
3. Conclusion
Based on the discussed factors, it could be concluded that with the implementation of
#EnforceTheOrder, it would help in proving several benefits for the people who make usage of
the social networking platform. In order to increase the safety of their platform, the company can
make use of several kind of ways that would increase the policy of safety breach. The privacy
concerns for the application could be further improved by following of exact security standards.
Law and order should also be maintained within the social networking platform as it contains
several important data of people. Regular revision of security standards would be helpful in
bringing stability of the security platforms.
standards. These would be highly beneficial for the company to protect the data rights and
privacy of the data of people.
3. Conclusion
Based on the discussed factors, it could be concluded that with the implementation of
#EnforceTheOrder, it would help in proving several benefits for the people who make usage of
the social networking platform. In order to increase the safety of their platform, the company can
make use of several kind of ways that would increase the policy of safety breach. The privacy
concerns for the application could be further improved by following of exact security standards.
Law and order should also be maintained within the social networking platform as it contains
several important data of people. Regular revision of security standards would be helpful in
bringing stability of the security platforms.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7ETHICAL CONCERNS RELATED TO MOBILE THREATS
References
Berreby, F., Bourgne, G., & Ganascia, J. G. (2017, May). A declarative modular framework for
representing and applying ethical principles. In Proceedings of the 16th conference on
autonomous agents and multiagent systems (pp. 96-104). International Foundation for
Autonomous Agents and Multiagent Systems.
DeVellis, R. F. (2016). Scale development: Theory and applications (Vol. 26). Sage
publications.
FTC: Enforce the Order. (2019). Retrieved from https://epic.org/enforce-the-order/
Johnson, J. S., & Sohi, R. S. (2016). Understanding and resolving major contractual breaches in
buyer–seller relationships: a grounded theory approach. Journal of the Academy of
Marketing Science, 44(2), 185-205.
Kosters, M., & Van der Heijden, J. (2015). From mechanism to virtue: Evaluating Nudge
theory. Evaluation, 21(3), 276-291.
Koven, S. G. (2015). Public sector ethics: Theory and applications. Routledge.
Oghuma, A. P., Libaque-Saenz, C. F., Wong, S. F., & Chang, Y. (2016). An expectation-
confirmation model of continuance intention to use mobile instant messaging. Telematics
and Informatics, 33(1), 34-47.
Stufflebeam, D. L., & Coryn, C. L. (2014). Evaluation theory, models, and applications (Vol.
50). John Wiley & Sons.
References
Berreby, F., Bourgne, G., & Ganascia, J. G. (2017, May). A declarative modular framework for
representing and applying ethical principles. In Proceedings of the 16th conference on
autonomous agents and multiagent systems (pp. 96-104). International Foundation for
Autonomous Agents and Multiagent Systems.
DeVellis, R. F. (2016). Scale development: Theory and applications (Vol. 26). Sage
publications.
FTC: Enforce the Order. (2019). Retrieved from https://epic.org/enforce-the-order/
Johnson, J. S., & Sohi, R. S. (2016). Understanding and resolving major contractual breaches in
buyer–seller relationships: a grounded theory approach. Journal of the Academy of
Marketing Science, 44(2), 185-205.
Kosters, M., & Van der Heijden, J. (2015). From mechanism to virtue: Evaluating Nudge
theory. Evaluation, 21(3), 276-291.
Koven, S. G. (2015). Public sector ethics: Theory and applications. Routledge.
Oghuma, A. P., Libaque-Saenz, C. F., Wong, S. F., & Chang, Y. (2016). An expectation-
confirmation model of continuance intention to use mobile instant messaging. Telematics
and Informatics, 33(1), 34-47.
Stufflebeam, D. L., & Coryn, C. L. (2014). Evaluation theory, models, and applications (Vol.
50). John Wiley & Sons.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





