Ethics and Professionalism in Computer Science - Anadolu University
VerifiedAdded on 2023/01/23
|14
|3407
|59
Essay
AI Summary
This essay, titled "Ethics and Professionalism in Computer Science," explores the crucial aspects of computer ethics within the context of technological advancements and the increasing reliance on Information and Communication Technologies (ICTs). The essay delves into key ethical issues such as data security, accuracy, intellectual property rights, and accessibility, highlighting their significance in the digital age. It examines the reasons behind these issues and proposes solutions based on expert insights from ICT professionals. The research, conducted through semi-structured interviews with K-8 computer educators, software experts, and computer center staff, reveals the importance of ethical conduct and professionalism in the field. The study emphasizes the need for ethical guidelines to prevent unethical practices and underscores the importance of considering the societal consequences of technological innovations. Furthermore, it references existing literature on computer ethics, including the impact of factors like age, gender, and computer experience on ethical perceptions. The essay provides a comprehensive overview of the ethical dilemmas that arise with the use of computers and the Internet, emphasizing the need for ethical awareness and adherence to professional codes of conduct within the field of computer science and the broader information society. The essay also highlights the importance of understanding proprietary software and intellectual property to protect the rights of creators.

Running head: ETHICS AND PROFESSIONALISM IN COMPUTER 1
Ethics and Professionalism in Computer
Author Name(s), First M. Last, Omit Titles and Degrees
Institutional Affiliation(s)
Author Note
Include any grant/funding information and a complete correspondence address.
Ethics and Professionalism in Computer
Author Name(s), First M. Last, Omit Titles and Degrees
Institutional Affiliation(s)
Author Note
Include any grant/funding information and a complete correspondence address.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: ETHICS AND PROFESSIONALISM IN COMPUTER 2
Abstract
Growing the use of information and correspondence headways (ICTs) help individuals to
enlighten a couple of normal issues, which used to be all the more tirelessly, logically perplexed
and monotonous. Regardless of the way that ICTs give individuals with various good conditions,
they may moreover fill in as the explanation behind a couple of societal and good issues which
move according to the particular circumstances and purposes behind ICT use. The clearest of
these issues is the security of individual information in the virtual condition, the exactness of the
information used, insightful property rights and identical access rights. These much-ignored
issues become greater persistently, which requires ICT using individuals to think about good
issues and urges masters to discuss these issues in a way to make an agreement that proceeds
with correspondence and value as for access, storing and dissemination of information. In such
way, the present examination intended to choose issues related to PC ethics with a reference to
security, precision, property, and accessibility; to look at the reasons for such issues, and to
propose proposition concerning these issues through the help of specialists who had an ICT
establishment. Emotional data was accumulated through semi-sorted out gatherings from a
deliberate case of K-8 PC educators in Eskişehir, programming pros in Anadolu University
Division of PC Based Instruction, and programming authorities in Anadolu University Computer
Center. In the wake of faltering quality and authenticity measures were taken, the substance
examination was driven trailed by the interpretation of revelations alongside direct references
from the data. It is revealed that most of the ICT professional doesn’t understand the importance
of ethics and professionalism when dealing with the client as some have been involved in giving
out incorrect PC models for the procurement to enjoy from bad deals. They gave a couple of
Abstract
Growing the use of information and correspondence headways (ICTs) help individuals to
enlighten a couple of normal issues, which used to be all the more tirelessly, logically perplexed
and monotonous. Regardless of the way that ICTs give individuals with various good conditions,
they may moreover fill in as the explanation behind a couple of societal and good issues which
move according to the particular circumstances and purposes behind ICT use. The clearest of
these issues is the security of individual information in the virtual condition, the exactness of the
information used, insightful property rights and identical access rights. These much-ignored
issues become greater persistently, which requires ICT using individuals to think about good
issues and urges masters to discuss these issues in a way to make an agreement that proceeds
with correspondence and value as for access, storing and dissemination of information. In such
way, the present examination intended to choose issues related to PC ethics with a reference to
security, precision, property, and accessibility; to look at the reasons for such issues, and to
propose proposition concerning these issues through the help of specialists who had an ICT
establishment. Emotional data was accumulated through semi-sorted out gatherings from a
deliberate case of K-8 PC educators in Eskişehir, programming pros in Anadolu University
Division of PC Based Instruction, and programming authorities in Anadolu University Computer
Center. In the wake of faltering quality and authenticity measures were taken, the substance
examination was driven trailed by the interpretation of revelations alongside direct references
from the data. It is revealed that most of the ICT professional doesn’t understand the importance
of ethics and professionalism when dealing with the client as some have been involved in giving
out incorrect PC models for the procurement to enjoy from bad deals. They gave a couple of

Running head: ETHICS AND PROFESSIONALISM IN COMPUTER 3
prudent steps to foresee deceitful PC using rehearses. Executions and suggestions for further
research were given.
Catchphrases: Computer ethics, authorized advancement, precision, insurance, accessibility
INTRODUCTION
The expansion of innovation among the developing countries has led to increased in both
mechanical and technical know-how. Among these, PCs and the Internet have been received in
all regions of the general public conveying them to a powerful and exceptional position in these
territories. The advent of PC and the Internet has revolutionized how data is stored and processed
since nowadays one doesn’t have to be techy to be somehow beginner in the data processing. It is
therefore important to have laid down ethics and professional code of conducts to ensure some
level of controls in the data processing and innovations around the data. In any case,
insufficiency of arrangements to control people while utilizing PCs to serve for more
noteworthy's benefit enables one of a kind moral issues to develop. Such issues ask all people to
consider PC morals in a progressively careful manner. PC Ethics Mistaken utilization of data
advances in a manner to bother security and property make a few moral quandaries, which lead
to moral issues in regards to innovation use. Moral issues coming from PC innovations are
fundamentally examined inside the system of PC morals. This term was first utilized in the
center of the '70s as an application field of expert morals, which was changed and fairly
crumbled through the presence of PCs. The idea of ethics has been in existence for quite some
time since the revolution of the PC and the Internet. This is evident by the huge scholarly articles
prudent steps to foresee deceitful PC using rehearses. Executions and suggestions for further
research were given.
Catchphrases: Computer ethics, authorized advancement, precision, insurance, accessibility
INTRODUCTION
The expansion of innovation among the developing countries has led to increased in both
mechanical and technical know-how. Among these, PCs and the Internet have been received in
all regions of the general public conveying them to a powerful and exceptional position in these
territories. The advent of PC and the Internet has revolutionized how data is stored and processed
since nowadays one doesn’t have to be techy to be somehow beginner in the data processing. It is
therefore important to have laid down ethics and professional code of conducts to ensure some
level of controls in the data processing and innovations around the data. In any case,
insufficiency of arrangements to control people while utilizing PCs to serve for more
noteworthy's benefit enables one of a kind moral issues to develop. Such issues ask all people to
consider PC morals in a progressively careful manner. PC Ethics Mistaken utilization of data
advances in a manner to bother security and property make a few moral quandaries, which lead
to moral issues in regards to innovation use. Moral issues coming from PC innovations are
fundamentally examined inside the system of PC morals. This term was first utilized in the
center of the '70s as an application field of expert morals, which was changed and fairly
crumbled through the presence of PCs. The idea of ethics has been in existence for quite some
time since the revolution of the PC and the Internet. This is evident by the huge scholarly articles
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: ETHICS AND PROFESSIONALISM IN COMPUTER 4
written on the subject to enlightened the concerned parties the importance of having come moral
codes and a professional code of conduct when dealing with user data processing and storage. PC
morals is neither a rundown of moral standards to comply, nor an innovation denied of specific
qualities while executing those standards. In this way, PC morals urge researchers to return to PC
innovation and its qualities. Despite the fact that PC morals re a field identified with and in the
middle of science and morals, it is a novel and comprehensive order giving standards to getting,
conceptualization and PC innovation use. Computing ethics majorly revolve around the ethical
utilization of computers to perform ethical actions which may include but not limited to ethical
processing of user data, ethical storage of user data, avoiding misusing user data for purposes not
agreed upon by the user and ensuring user privacy is not compromised. PC innovation is a
quickly creating field which makes it hard to foresee what is coming straight away.
Notwithstanding, obviously the data society and people inside this general public will continue
going up against radical innovative and societal advancements driving them to produce new
examples of conduct to oblige these improvements. In such a manner, while forming these
conduct age forms, the thought of PC morals ought to be underlined just like the idea of expert
morals. Likewise, the idea of PC morals ought not to be analyzed inside the system of ICT-
related proficient morals. Or maybe, it ought to be inspected inside the structure of individual
morals to be trailed by all people of the data society. Moral Problems of the Information Society
Improvement and rivalry in a data society is kept up by people's capacity to get to data quickly
and effectively. When it comes to innovations, some people argue the data should be collected
and used to foster the envisioned innovation regardless of how unethical the operations of the
innovations. This is particular to the Millenials who are very much ready to give up their data
which is used in the development of these innovations. It is argued however that some of the
written on the subject to enlightened the concerned parties the importance of having come moral
codes and a professional code of conduct when dealing with user data processing and storage. PC
morals is neither a rundown of moral standards to comply, nor an innovation denied of specific
qualities while executing those standards. In this way, PC morals urge researchers to return to PC
innovation and its qualities. Despite the fact that PC morals re a field identified with and in the
middle of science and morals, it is a novel and comprehensive order giving standards to getting,
conceptualization and PC innovation use. Computing ethics majorly revolve around the ethical
utilization of computers to perform ethical actions which may include but not limited to ethical
processing of user data, ethical storage of user data, avoiding misusing user data for purposes not
agreed upon by the user and ensuring user privacy is not compromised. PC innovation is a
quickly creating field which makes it hard to foresee what is coming straight away.
Notwithstanding, obviously the data society and people inside this general public will continue
going up against radical innovative and societal advancements driving them to produce new
examples of conduct to oblige these improvements. In such a manner, while forming these
conduct age forms, the thought of PC morals ought to be underlined just like the idea of expert
morals. Likewise, the idea of PC morals ought not to be analyzed inside the system of ICT-
related proficient morals. Or maybe, it ought to be inspected inside the structure of individual
morals to be trailed by all people of the data society. Moral Problems of the Information Society
Improvement and rivalry in a data society is kept up by people's capacity to get to data quickly
and effectively. When it comes to innovations, some people argue the data should be collected
and used to foster the envisioned innovation regardless of how unethical the operations of the
innovations. This is particular to the Millenials who are very much ready to give up their data
which is used in the development of these innovations. It is argued however that some of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: ETHICS AND PROFESSIONALISM IN COMPUTER 5
innovation should not be allowed to see the light as they greatly violate the principles of ethics,
privacy and the security of user data. Facebook, for example, is majorly used by the Millenials
have been in scandals over serious unethical data breaches stemming from privacy issues and
unethical practices of selling user data to analytical companies who use the data to generate
profit without user consent.
Several professional codes of conduct have been developed for professionals in the field of
computing. For example, one should not use the computer systems to cause harm to people or
other computer systems. Secondly, one should not use their computer system to interfere with the
work other or interfere with the normal functioning of another computer system hence violating
their integrity. Third, professionals should avoid snooping around other peoples computer
systems as such actions are not only violates their confidentiality rights to their data but also
seems immoral. Fourth, principles dictate that one should not use their expertise and computer
systems to steal information from other computer systems. Fifth, don’t use computer systems to
forge documents making the computer be an object used to bear false witness, The issue son
propriety software is another key area that professional must respect and avoid using the
propriety software without the license or trying to bypass the license requirement of propriety
software. This makes the individual involved in the creation of the tools and software no benefit
from their hard labor. Lastly for the professional inclined in the innovation world should always
check the social consequences of their actions before embarking on their next innovations and
some of these innovations are more capital oriented with no moral code backing them up hence
violating the societal code of ethics. The most stood up to also, muddled of moral issues is the
subject of licensed innovation rights. Data can be very exorbitant to produce in the principal
occurrence. Transmission and multiplication of the data may be dangerous as it could attack the
innovation should not be allowed to see the light as they greatly violate the principles of ethics,
privacy and the security of user data. Facebook, for example, is majorly used by the Millenials
have been in scandals over serious unethical data breaches stemming from privacy issues and
unethical practices of selling user data to analytical companies who use the data to generate
profit without user consent.
Several professional codes of conduct have been developed for professionals in the field of
computing. For example, one should not use the computer systems to cause harm to people or
other computer systems. Secondly, one should not use their computer system to interfere with the
work other or interfere with the normal functioning of another computer system hence violating
their integrity. Third, professionals should avoid snooping around other peoples computer
systems as such actions are not only violates their confidentiality rights to their data but also
seems immoral. Fourth, principles dictate that one should not use their expertise and computer
systems to steal information from other computer systems. Fifth, don’t use computer systems to
forge documents making the computer be an object used to bear false witness, The issue son
propriety software is another key area that professional must respect and avoid using the
propriety software without the license or trying to bypass the license requirement of propriety
software. This makes the individual involved in the creation of the tools and software no benefit
from their hard labor. Lastly for the professional inclined in the innovation world should always
check the social consequences of their actions before embarking on their next innovations and
some of these innovations are more capital oriented with no moral code backing them up hence
violating the societal code of ethics. The most stood up to also, muddled of moral issues is the
subject of licensed innovation rights. Data can be very exorbitant to produce in the principal
occurrence. Transmission and multiplication of the data may be dangerous as it could attack the

Running head: ETHICS AND PROFESSIONALISM IN COMPUTER 6
privileges of the makers. What's more, there may be issues in assigning the entrance to this data.
At last, availability alludes to the conditions under which an individual or an association can
have a right or benefit to acquire data. These standards comprise the beginning stage. It is
important to decide standards and standards and to make an agreement inside the general public
through directing assessments dependent on these standards
LITERATURE REVIEW
This territory discusses explore revelations on PC ethics. This trade is trailed by the effect of
unequivocal establishment factors on perceptions related to PC ethics. Particularly, the effect of
age, sexual introduction, PC experience, and budgetary status is investigated, and the opening in
PC ethics composing is spoken to. Various research inspects on PC ethics have been coordinated
in the UK propelled instruction associations in connection with various pointers of ICTs. directed
the Unethical Computer Using Behavior Scale (UECUBS) made to 559 pre-organization
instructors gave a shot the UK preparing staff. Disclosures revealed that pre-organization
instructors depicted their PC and Internet using rehearses as good. It was seen that individuals'
perceptions concerning secured advancement and net genuineness were progressively delicate
conversely with various creates. It was revealed that deceptive PC using rehearses moved by sex
and program of study (Stahl, Timmermans and Mittelstadt, 2016). Even more unequivocally,
women offered an explanation to be progressively moral in the wording of all creates of the
scale. In addition, educator students in the division of PC preparing and instructional advances
had lower scores the extent that the things watching out for information genuineness. ICTs.
Disclosures did not reveal any important differences among different ventures of study and
between high moreover, low experienced PC customers. As referenced over, the basic
privileges of the makers. What's more, there may be issues in assigning the entrance to this data.
At last, availability alludes to the conditions under which an individual or an association can
have a right or benefit to acquire data. These standards comprise the beginning stage. It is
important to decide standards and standards and to make an agreement inside the general public
through directing assessments dependent on these standards
LITERATURE REVIEW
This territory discusses explore revelations on PC ethics. This trade is trailed by the effect of
unequivocal establishment factors on perceptions related to PC ethics. Particularly, the effect of
age, sexual introduction, PC experience, and budgetary status is investigated, and the opening in
PC ethics composing is spoken to. Various research inspects on PC ethics have been coordinated
in the UK propelled instruction associations in connection with various pointers of ICTs. directed
the Unethical Computer Using Behavior Scale (UECUBS) made to 559 pre-organization
instructors gave a shot the UK preparing staff. Disclosures revealed that pre-organization
instructors depicted their PC and Internet using rehearses as good. It was seen that individuals'
perceptions concerning secured advancement and net genuineness were progressively delicate
conversely with various creates. It was revealed that deceptive PC using rehearses moved by sex
and program of study (Stahl, Timmermans and Mittelstadt, 2016). Even more unequivocally,
women offered an explanation to be progressively moral in the wording of all creates of the
scale. In addition, educator students in the division of PC preparing and instructional advances
had lower scores the extent that the things watching out for information genuineness. ICTs.
Disclosures did not reveal any important differences among different ventures of study and
between high moreover, low experienced PC customers. As referenced over, the basic
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: ETHICS AND PROFESSIONALISM IN COMPUTER 7
qualification among folks and females remained. Strikingly, revelations revealed a relationship
between sexual introduction and program of study exhibiting that the differentiation among folks
and females did not seek after a practically identical model transversely over different ventures
of study. More, specifically, females' choices with respect to PC ethics were seen to be
unfaltering across over different ventures of study while folks' choices changed by the field of
study.
A couple of examinations focused on the actuating occupation of the Internet on insightful sad
conduct whose speculative establishment in the UK was set up. Following that Internet filled in
as a ground for insightful violations, the level of consideration of UK school understudies in
academic corruption practices energized through Internet was investigated. An estimation
instrument named InternetTriggered Academic Dishonesty Scale (ITADS) was made through the
help of principles proposed by the Anadolu University Scientific Ethics Committee and The
Scientific and Technological Research Gathering of UK. Resulting in guiding the scale to 349
pre-organization teachers in a modestly populated Turkish state school, experts coordinated two-
factor examinations. The past provoked the creates involving fundamental sorts of e-beguiling
nature which were named as erroneousness, abstract robbery, bending, wrongdoing, and
unapproved help (Pimple, 2011). The second examination revealed individual and coherent
factors enacting deceptive nature which were named as individual components, institutional
methodologies, and buddy weight. As one of the groundwork inquires about concerning PC
ethics in the UK, investigated issues experienced in K-12 PC research focuses with respect to PC
security close by game plans proposed by PC instructors. The most alluded to PC security issues
were unapproved access to others' near and dear records (92%), and ousting someone else's
archives from a shared PC (82%). Revelations recommended that K-12 understudies were not
qualification among folks and females remained. Strikingly, revelations revealed a relationship
between sexual introduction and program of study exhibiting that the differentiation among folks
and females did not seek after a practically identical model transversely over different ventures
of study. More, specifically, females' choices with respect to PC ethics were seen to be
unfaltering across over different ventures of study while folks' choices changed by the field of
study.
A couple of examinations focused on the actuating occupation of the Internet on insightful sad
conduct whose speculative establishment in the UK was set up. Following that Internet filled in
as a ground for insightful violations, the level of consideration of UK school understudies in
academic corruption practices energized through Internet was investigated. An estimation
instrument named InternetTriggered Academic Dishonesty Scale (ITADS) was made through the
help of principles proposed by the Anadolu University Scientific Ethics Committee and The
Scientific and Technological Research Gathering of UK. Resulting in guiding the scale to 349
pre-organization teachers in a modestly populated Turkish state school, experts coordinated two-
factor examinations. The past provoked the creates involving fundamental sorts of e-beguiling
nature which were named as erroneousness, abstract robbery, bending, wrongdoing, and
unapproved help (Pimple, 2011). The second examination revealed individual and coherent
factors enacting deceptive nature which were named as individual components, institutional
methodologies, and buddy weight. As one of the groundwork inquires about concerning PC
ethics in the UK, investigated issues experienced in K-12 PC research focuses with respect to PC
security close by game plans proposed by PC instructors. The most alluded to PC security issues
were unapproved access to others' near and dear records (92%), and ousting someone else's
archives from a shared PC (82%). Revelations recommended that K-12 understudies were not
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: ETHICS AND PROFESSIONALISM IN COMPUTER 8
instructed sufficiently about good issues regarding ICTs. Sorts of beguiling PC using penchants
were in like manner investigated in business settings. For instance, the ethical utilization of
information propels in close to nothing and reasonable size endeavors nearby the perspectives of
directors and bad habit chiefs with respect to PC ethics was investigated. Disclosures revealed
that most of the endeavors (53.3%) used unlicensed programming. 40% of the chairmen felt that
their managers had little working data on PC ethics. The predominant part offered an explanation
to be exhibited to PC bad behaviors (86.7%). Most directors (76%) felt that controlling and
checking the substance of supervisors' messages was seriously structured. In addition, they
pondered chiefs' talking (72 %) and surfing grown-up locales (93%) in all respects severely
planned paying little heed to whether organizations did not hamper the work. Most undertakings
did not have any formal protections as for PC ethics.
Finally, an association between the guidance level and the dimension of suffering exploitative
practices couldn't be found. Some settled examinations in the field chiefly based on PC related
misdirection. For instance, an examination of 212 school understudies to look into ensured
advancement and security issues. Programming blackmail was examined under three headings:
Fraud for individual use, for allies' use and for advantage. Besides, insurance construct was
investigated under three headings, specifically, getting to PC records without scrutinizing,
getting to records with the purpose of examining the substance and getting to archives with the
purpose of adjusting the substance. Disclosures revealed that school understudies' perceptions as
for PC related deceitfulness were exceptional in connection to their acknowledgments regarding
comparable fake in various locales. Even more expressly, they were progressively mindful about
assurance issues when the archives were not on PC. In any case, with respect to getting to PC
records, the component of mindfulness was lower. It was prescribed that since getting to PC
instructed sufficiently about good issues regarding ICTs. Sorts of beguiling PC using penchants
were in like manner investigated in business settings. For instance, the ethical utilization of
information propels in close to nothing and reasonable size endeavors nearby the perspectives of
directors and bad habit chiefs with respect to PC ethics was investigated. Disclosures revealed
that most of the endeavors (53.3%) used unlicensed programming. 40% of the chairmen felt that
their managers had little working data on PC ethics. The predominant part offered an explanation
to be exhibited to PC bad behaviors (86.7%). Most directors (76%) felt that controlling and
checking the substance of supervisors' messages was seriously structured. In addition, they
pondered chiefs' talking (72 %) and surfing grown-up locales (93%) in all respects severely
planned paying little heed to whether organizations did not hamper the work. Most undertakings
did not have any formal protections as for PC ethics.
Finally, an association between the guidance level and the dimension of suffering exploitative
practices couldn't be found. Some settled examinations in the field chiefly based on PC related
misdirection. For instance, an examination of 212 school understudies to look into ensured
advancement and security issues. Programming blackmail was examined under three headings:
Fraud for individual use, for allies' use and for advantage. Besides, insurance construct was
investigated under three headings, specifically, getting to PC records without scrutinizing,
getting to records with the purpose of examining the substance and getting to archives with the
purpose of adjusting the substance. Disclosures revealed that school understudies' perceptions as
for PC related deceitfulness were exceptional in connection to their acknowledgments regarding
comparable fake in various locales. Even more expressly, they were progressively mindful about
assurance issues when the archives were not on PC. In any case, with respect to getting to PC
records, the component of mindfulness was lower. It was prescribed that since getting to PC

Running head: ETHICS AND PROFESSIONALISM IN COMPUTER 9
archives was less difficult than various types of fakeness, since the culpable didn't think about
the destructive results of their exercises, and since the manhandled didn't think about the fake,
such practices were logically ordinary.
PC customers' perceptions concerning ethics have been specially investigated by focusing on
good troubles. the meetings with 65 pre-organization teachers concerning their sentiments on
master ethics through using moral difficulties. Disclosures revealed that individuals' social
affectability and trustworthiness capacities influenced their examinations of good troubles. In the
wake of planning was given to individuals, it was revealed that individuals' choices as for good
issues were progressively helpful. It was prescribed that formal preparing concerning moral
problems affected extending individuals' theoretical and suitable learning and helping them to
unwind moral circumstances in an inexorably valuable way.
The impression of customers has in like manner been inspected as to contrasts among specialists
from different establishments. an examination in Cape Town University to investigate
differentiates between the ethical impression of information structure understudies and
specialists. It was revealed that understudies had different viewpoints concerning PC ethics
interestingly with experts viably working in the field. Even more unequivocally, understudies
were dynamically tolerant of unscrupulous practices conversely with pros.
archives was less difficult than various types of fakeness, since the culpable didn't think about
the destructive results of their exercises, and since the manhandled didn't think about the fake,
such practices were logically ordinary.
PC customers' perceptions concerning ethics have been specially investigated by focusing on
good troubles. the meetings with 65 pre-organization teachers concerning their sentiments on
master ethics through using moral difficulties. Disclosures revealed that individuals' social
affectability and trustworthiness capacities influenced their examinations of good troubles. In the
wake of planning was given to individuals, it was revealed that individuals' choices as for good
issues were progressively helpful. It was prescribed that formal preparing concerning moral
problems affected extending individuals' theoretical and suitable learning and helping them to
unwind moral circumstances in an inexorably valuable way.
The impression of customers has in like manner been inspected as to contrasts among specialists
from different establishments. an examination in Cape Town University to investigate
differentiates between the ethical impression of information structure understudies and
specialists. It was revealed that understudies had different viewpoints concerning PC ethics
interestingly with experts viably working in the field. Even more unequivocally, understudies
were dynamically tolerant of unscrupulous practices conversely with pros.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: ETHICS AND PROFESSIONALISM IN COMPUTER 10
RESEARCH QUESTIONS
Execution of this research was based on the following research questions:
1. What are the notions of ICT specialists with respect to PC ethics?
2. What are the conclusions of ICT specialists concerning four good issues of the information
society: authorized development, accuracy, security, and accessibility?
3. What sorts of game plans were prescribed by ICT specialists regarding ensured advancement,
precision, security, and accessibility issues?
METHODOLOGY
Participants
Members of the examination comprised of 20 PC experts. Ten of them were alumni of PC
training and instructional advancements divisions, who functioned as software engineering
educators in Eskişehir, what's more, the other ten were alumni of software engineering divisions
who functioned as programming specialists in Anadolu College Division of Computer-Based
Instruction, and in the Anadolu University Computer Center. All members sought after an expert
profession in data advances and software engineering. Fifteen of the members were male and
five were female. Intentional examining methodology was connected to decide members.
Likewise, PC experts volunteered to take an interest in the examination were chosen. Member
names were supplanted with nom de plumes agreement with the rule of security, and these nom
de plumes announced while deciphering the outcomes.
RESEARCH QUESTIONS
Execution of this research was based on the following research questions:
1. What are the notions of ICT specialists with respect to PC ethics?
2. What are the conclusions of ICT specialists concerning four good issues of the information
society: authorized development, accuracy, security, and accessibility?
3. What sorts of game plans were prescribed by ICT specialists regarding ensured advancement,
precision, security, and accessibility issues?
METHODOLOGY
Participants
Members of the examination comprised of 20 PC experts. Ten of them were alumni of PC
training and instructional advancements divisions, who functioned as software engineering
educators in Eskişehir, what's more, the other ten were alumni of software engineering divisions
who functioned as programming specialists in Anadolu College Division of Computer-Based
Instruction, and in the Anadolu University Computer Center. All members sought after an expert
profession in data advances and software engineering. Fifteen of the members were male and
five were female. Intentional examining methodology was connected to decide members.
Likewise, PC experts volunteered to take an interest in the examination were chosen. Member
names were supplanted with nom de plumes agreement with the rule of security, and these nom
de plumes announced while deciphering the outcomes.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: ETHICS AND PROFESSIONALISM IN COMPUTER 11
Data Collection
Semi-organized meetings were directed with members to decide their conclusions in regards to
inquire about questions. Meetings were organized independently with every member in
vacancies and spots they decided.
Information accumulation instrument comprised of a meeting structure including seven open-
finished inquiries created by the scientist. So as to ensure that the meeting structure was suitable
and adequate to address the exploration inquiries of the investigation, the specialist turned to
master conclusions given by four experts working in the field of PC training and instructional
advances. The structure was updated dependent on master assessments and made prepared for
usage as recommended by driving procedure sources in the field of subjective research.
Data Analysis and Interpretation
While exploring data, the substance examination will be completed by using continuous
reference books on the emotional research plan and data examination. In the examination, the
data will be coded, subjects will be found, the data will be planned according to codes and
points, and disclosures were deciphered. That is, the inductive coding framework will be
realized. The explanation behind existing is to portray data and reveal covered surenesses took
pleasure in by the data. The data which is portrayed, made an interpretation of, inspected as for
Data Collection
Semi-organized meetings were directed with members to decide their conclusions in regards to
inquire about questions. Meetings were organized independently with every member in
vacancies and spots they decided.
Information accumulation instrument comprised of a meeting structure including seven open-
finished inquiries created by the scientist. So as to ensure that the meeting structure was suitable
and adequate to address the exploration inquiries of the investigation, the specialist turned to
master conclusions given by four experts working in the field of PC training and instructional
advances. The structure was updated dependent on master assessments and made prepared for
usage as recommended by driving procedure sources in the field of subjective research.
Data Analysis and Interpretation
While exploring data, the substance examination will be completed by using continuous
reference books on the emotional research plan and data examination. In the examination, the
data will be coded, subjects will be found, the data will be planned according to codes and
points, and disclosures were deciphered. That is, the inductive coding framework will be
realized. The explanation behind existing is to portray data and reveal covered surenesses took
pleasure in by the data. The data which is portrayed, made an interpretation of, inspected as for
Running head: ETHICS AND PROFESSIONALISM IN COMPUTER 12
conditions and sensible outcomes associations and pulled in to a couple of finishes will be
moreover maintained with direct references to reflect individuals' contemplations authentically.
Beginning data starting from semi-composed gatherings will be sound taped, interpreted, kept an
eye on a sentence by sentence, and traded to converse with structures. Declaration structures that
occurred in the data were recorded by the examiner and a self-ruling analyst in the field to make
subjects related to inquire about inquiries.
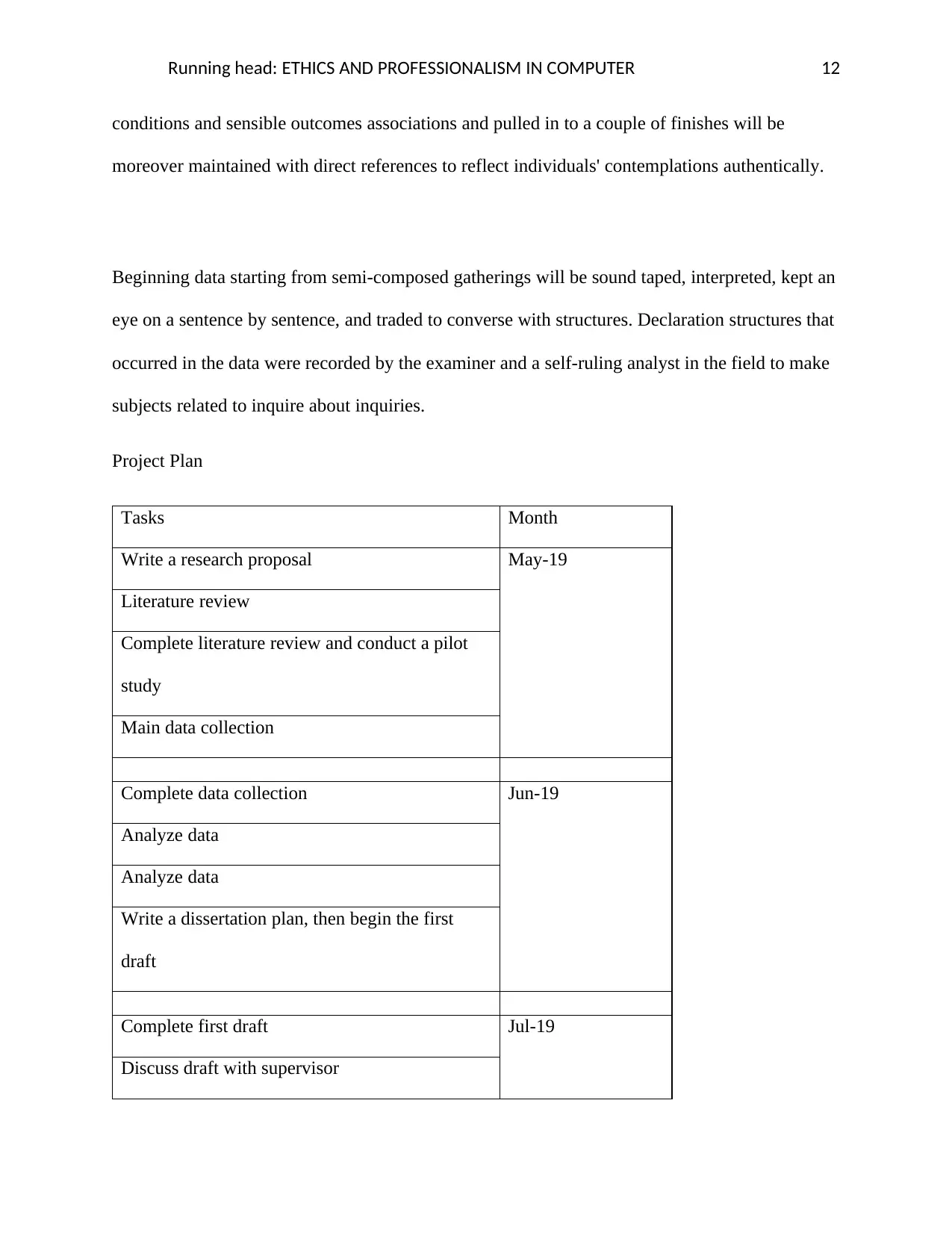
Project Plan
Tasks Month
Write a research proposal May-19
Literature review
Complete literature review and conduct a pilot
study
Main data collection
Complete data collection Jun-19
Analyze data
Analyze data
Write a dissertation plan, then begin the first
draft
Complete first draft Jul-19
Discuss draft with supervisor
conditions and sensible outcomes associations and pulled in to a couple of finishes will be
moreover maintained with direct references to reflect individuals' contemplations authentically.
Beginning data starting from semi-composed gatherings will be sound taped, interpreted, kept an
eye on a sentence by sentence, and traded to converse with structures. Declaration structures that
occurred in the data were recorded by the examiner and a self-ruling analyst in the field to make
subjects related to inquire about inquiries.
Project Plan
Tasks Month
Write a research proposal May-19
Literature review
Complete literature review and conduct a pilot
study
Main data collection
Complete data collection Jun-19
Analyze data
Analyze data
Write a dissertation plan, then begin the first
draft
Complete first draft Jul-19
Discuss draft with supervisor
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




