Big Data Threat Landscape of Europe
VerifiedAdded on 2019/11/26
|15
|3480
|152
Report
AI Summary
This report analyzes the big data threat landscape in Europe, focusing on the role of ENISA (European Union Agency for Cybersecurity). It categorizes threats into five groups: unintentional data loss, hijacking/eavesdropping, nefarious activities, legal threats, and organizational threats. The report identifies key threat agents, including corporations, cybercriminals, cyber terrorists, hacktivists, script kiddies, employees, and nation-states. Mitigation strategies are discussed, emphasizing cryptography, secure APIs, and robust infrastructure. The report also suggests improvements to the European threat landscape, such as optimizing database processes and proactively updating ETL (Extract, Transform, Load) processes to counter evolving threats. Finally, it assesses the current state of ENISA security, highlighting both its strengths and areas for improvement, such as addressing human error and technical failures.

Running head: BIG DATA THREAT LANDSCAPE OF EUROPE
Big Data Threat Landscape of Europe
Name of Student-
Name of University-
Author Note-
Big Data Threat Landscape of Europe
Name of Student-
Name of University-
Author Note-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1BIG DATA THREAT LANDSCAPE OF EUROPE
Answer to Question 1:
ENISA is known as the European Union for Network and Information Security. It is a
centre in Europe which consists of expertise of information and network security to protect the
member states, citizens of Europe and the private sector of the country. To maintain a good
practice for the security of information, ENISA gives recommendations and advices to the
organizations and the sectors. The work of ENISA is to improve the condition of critical network
and information infrastructure of Europe and helps to implement the relevant legislation of
Europe. The Europe member states are enhanced by ENISA by giving a support to the
development of communities of cross border to improve the information and network security of
Europe.
This case study deals with the Big Data Threat Landscape of Europe. Big data are used to
organize the data that are stored in the data storage of the organizations and enterprises. Big data
deals with group of algorithms, system and technology that are used to collect the data that are
unorganized and have a large variety. There are many sources of big data (Bartsch & Frey,
2017). The data providers or the generators for big data are sensors of distributed multimedia for
Internet of Things, networks and devices of mobile telecommunication, applications of web
based and processes that involve distributed business. The use of big data have increased day by
day which results in the improvement of the algorithms, system and technology that are
associated with big data so that it can reach to a higher level of maturity and development. This
case study analyses the threats of all the classes of big data asset that are identified. They are as
follows:
Answer to Question 1:
ENISA is known as the European Union for Network and Information Security. It is a
centre in Europe which consists of expertise of information and network security to protect the
member states, citizens of Europe and the private sector of the country. To maintain a good
practice for the security of information, ENISA gives recommendations and advices to the
organizations and the sectors. The work of ENISA is to improve the condition of critical network
and information infrastructure of Europe and helps to implement the relevant legislation of
Europe. The Europe member states are enhanced by ENISA by giving a support to the
development of communities of cross border to improve the information and network security of
Europe.
This case study deals with the Big Data Threat Landscape of Europe. Big data are used to
organize the data that are stored in the data storage of the organizations and enterprises. Big data
deals with group of algorithms, system and technology that are used to collect the data that are
unorganized and have a large variety. There are many sources of big data (Bartsch & Frey,
2017). The data providers or the generators for big data are sensors of distributed multimedia for
Internet of Things, networks and devices of mobile telecommunication, applications of web
based and processes that involve distributed business. The use of big data have increased day by
day which results in the improvement of the algorithms, system and technology that are
associated with big data so that it can reach to a higher level of maturity and development. This
case study analyses the threats of all the classes of big data asset that are identified. They are as
follows:

2BIG DATA THREAT LANDSCAPE OF EUROPE
Threats that are related with big data are different from the threats that that are related to
ordinary data. New type of data leakage, degradation and leakage are specific to big data are
introduced for outsourcing the frequency of computation of big data and also for replicating the
storage of big data.
Specific data protection and privacy impacts are there for the big data (Bastl, Mareš &
Tvrdá, 2105). The links for data collection is required for parallelization in big data but the data
that are additional creates data breaches and leakages.
The interest that different owners of assets which include data transformers, providers for
storage services, computation and data owners are different and they conflict within themselves
(Bendiek, 2015). This makes the situation complex where there is a need of counter measure for
security which is to be executed and planned.
Simple security and privacy practice would help to decrease the security and privacy risk
in the sector of big data. Securities that are stated by default principle can be highly embraced.
There is also a comparative study between the counter measures that are identified for big
data and the threats that are identified for big data in this case study. The drawback of present
counter measure of big data and the requirements for the development of the counter measures
that are needed in future are also discussed (Catteddu & Hogben, 2015). The trend for present
counter measures that are used to adapt the solutions that already exists against the traditional
information threats in the environment of big data which mainly focuses on the amount of data is
given briefly. The scalability issues are mainly satisfied by this method and does not suits the
peculiarities of big data.
Threats that are related with big data are different from the threats that that are related to
ordinary data. New type of data leakage, degradation and leakage are specific to big data are
introduced for outsourcing the frequency of computation of big data and also for replicating the
storage of big data.
Specific data protection and privacy impacts are there for the big data (Bastl, Mareš &
Tvrdá, 2105). The links for data collection is required for parallelization in big data but the data
that are additional creates data breaches and leakages.
The interest that different owners of assets which include data transformers, providers for
storage services, computation and data owners are different and they conflict within themselves
(Bendiek, 2015). This makes the situation complex where there is a need of counter measure for
security which is to be executed and planned.
Simple security and privacy practice would help to decrease the security and privacy risk
in the sector of big data. Securities that are stated by default principle can be highly embraced.
There is also a comparative study between the counter measures that are identified for big
data and the threats that are identified for big data in this case study. The drawback of present
counter measure of big data and the requirements for the development of the counter measures
that are needed in future are also discussed (Catteddu & Hogben, 2015). The trend for present
counter measures that are used to adapt the solutions that already exists against the traditional
information threats in the environment of big data which mainly focuses on the amount of data is
given briefly. The scalability issues are mainly satisfied by this method and does not suits the
peculiarities of big data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3BIG DATA THREAT LANDSCAPE OF EUROPE
Big data threat landscape and good practice guide gives an overall discussion about the
security that are used in the security process of big data (Christou, 2017). The assets of big data,
threats that are exposed to the assets, the agents of threats, risks and vulnerabilities and good
practices that are emerged from the researchers in field of big data are studies in this case.
The diagram that elaborates the infrastructure of big data that evolves in ENISA
(European Union for Network and Information Security) is given below.
Big data threat landscape and good practice guide gives an overall discussion about the
security that are used in the security process of big data (Christou, 2017). The assets of big data,
threats that are exposed to the assets, the agents of threats, risks and vulnerabilities and good
practices that are emerged from the researchers in field of big data are studies in this case.
The diagram that elaborates the infrastructure of big data that evolves in ENISA
(European Union for Network and Information Security) is given below.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
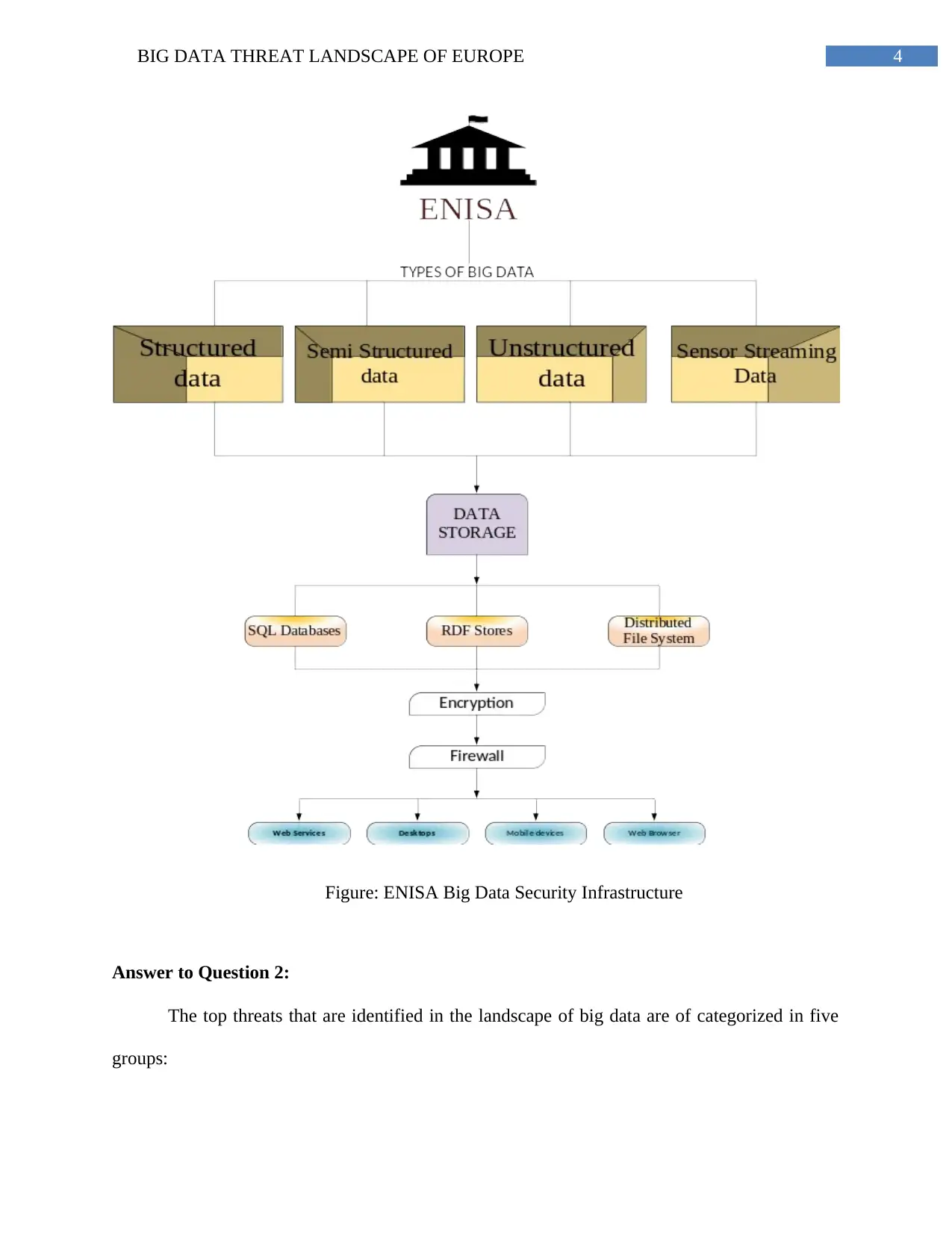
4BIG DATA THREAT LANDSCAPE OF EUROPE
Figure: ENISA Big Data Security Infrastructure
Answer to Question 2:
The top threats that are identified in the landscape of big data are of categorized in five
groups:
Figure: ENISA Big Data Security Infrastructure
Answer to Question 2:
The top threats that are identified in the landscape of big data are of categorized in five
groups:

5BIG DATA THREAT LANDSCAPE OF EUROPE
Group 1- Loss of information or the damage that is done unintentionally or IT asset
threat: The threats that are not caused intentionally are mainly under this category (Eininger,
Skopik & Fiedler, 2015). The threats that falls under this type of category are: sharing of
information or leakage of information that are caused by human errors, information leakage that
are caused due to web applications which are mainly caused by the APIs that are unsecured,
incorrect adaptation or planning and design that are inadequate.
Group 2- Hijacking, interception and eavesdropping: This threat group threat includes
changing, manipulating and alteration of communications that happens between two users or
parties. Installations of excess software or application tools are not needed for the victims to alter
the information (Exchange, 2016). The threats that falls under this category are: information
interception is most common of all the threats that are faced by big data. The inter node
communications that are related to big data are considered as unsecured that uses big data tool
for communicating.
Group 3- Nefarious activities and abuse: The threat that comes from the nefarious
activities comes under this group of threat (Hänisch & Rogge, 2017). The attacker performs
action to alter the victim’s infrastructure with the use of special tools, application or software.
The threats that falls under the nefarious activities are: identity fraud, denial of services, infected
code, activity or software, using rogue certificates and generations, audit tools that are misused,
unauthorized activities and authorization abuse, processes that fails in business.
Group 4- Legal threats: The threats of big data that comes from legal implications are
that includes regulations and violation of laws, fails to meet the requirements of the contract,
legislation of data breach, using intellectual property that are mainly unauthorized, misuse of
Group 1- Loss of information or the damage that is done unintentionally or IT asset
threat: The threats that are not caused intentionally are mainly under this category (Eininger,
Skopik & Fiedler, 2015). The threats that falls under this type of category are: sharing of
information or leakage of information that are caused by human errors, information leakage that
are caused due to web applications which are mainly caused by the APIs that are unsecured,
incorrect adaptation or planning and design that are inadequate.
Group 2- Hijacking, interception and eavesdropping: This threat group threat includes
changing, manipulating and alteration of communications that happens between two users or
parties. Installations of excess software or application tools are not needed for the victims to alter
the information (Exchange, 2016). The threats that falls under this category are: information
interception is most common of all the threats that are faced by big data. The inter node
communications that are related to big data are considered as unsecured that uses big data tool
for communicating.
Group 3- Nefarious activities and abuse: The threat that comes from the nefarious
activities comes under this group of threat (Hänisch & Rogge, 2017). The attacker performs
action to alter the victim’s infrastructure with the use of special tools, application or software.
The threats that falls under the nefarious activities are: identity fraud, denial of services, infected
code, activity or software, using rogue certificates and generations, audit tools that are misused,
unauthorized activities and authorization abuse, processes that fails in business.
Group 4- Legal threats: The threats of big data that comes from legal implications are
that includes regulations and violation of laws, fails to meet the requirements of the contract,
legislation of data breach, using intellectual property that are mainly unauthorized, misuse of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6BIG DATA THREAT LANDSCAPE OF EUROPE
data that are personal and lastly to obey the court orders and judiciary decisions (Jentzsch, 2016).
The threats that are categorized under this group are: violation of regulations and laws, personal
data abuse or legislation breach.
Group 5- Organizational threats: The threat that comes from the organizational
environment is called organizational threats (Kleineidam et al., 2017). The threat that includes in
this section is skill shortage. Huge data sets helps to analyze the decrease of innovation and
growth productivity of the company. This threat also helps to unlock significant values.
Most significant threat- The most significant threat among all five groups of threats is
the nefarious activity or abuse group (Kubicek & Diederich, 2015). The threat that comes from
the nefarious activities comes under this group of threat. The attacker performs action to alter the
victim’s infrastructure with the use of special tools, application or software. The threats that falls
under the nefarious activities are: identity fraud, denial of services, infected code, activity or
software, using rogue certificates and generations, audit tools that are misused, unauthorized
activities and authorization abuse, processes that fails in business. The attackers that target the
victims send infected code or some links that to the email ids of the victims. The infected codes
that are sent to the victims seem as if they are original code or links that are sent from a known
authorized user. The attack hides its identity (Lanfer, 2017). When the user clicks on the links or
tries to run the code on own system, the system gets affected and all the personal information and
data gets transfer to the attacker and even attacker gets the control of the victim’s system.
Sometimes, after the attack, the attacker even denies that an attack has already occurred leaving
no evidence behind. This type of attack is very difficult to identify.
data that are personal and lastly to obey the court orders and judiciary decisions (Jentzsch, 2016).
The threats that are categorized under this group are: violation of regulations and laws, personal
data abuse or legislation breach.
Group 5- Organizational threats: The threat that comes from the organizational
environment is called organizational threats (Kleineidam et al., 2017). The threat that includes in
this section is skill shortage. Huge data sets helps to analyze the decrease of innovation and
growth productivity of the company. This threat also helps to unlock significant values.
Most significant threat- The most significant threat among all five groups of threats is
the nefarious activity or abuse group (Kubicek & Diederich, 2015). The threat that comes from
the nefarious activities comes under this group of threat. The attacker performs action to alter the
victim’s infrastructure with the use of special tools, application or software. The threats that falls
under the nefarious activities are: identity fraud, denial of services, infected code, activity or
software, using rogue certificates and generations, audit tools that are misused, unauthorized
activities and authorization abuse, processes that fails in business. The attackers that target the
victims send infected code or some links that to the email ids of the victims. The infected codes
that are sent to the victims seem as if they are original code or links that are sent from a known
authorized user. The attack hides its identity (Lanfer, 2017). When the user clicks on the links or
tries to run the code on own system, the system gets affected and all the personal information and
data gets transfer to the attacker and even attacker gets the control of the victim’s system.
Sometimes, after the attack, the attacker even denies that an attack has already occurred leaving
no evidence behind. This type of attack is very difficult to identify.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7BIG DATA THREAT LANDSCAPE OF EUROPE
Answer to Question 3:
Threat Agents are those who are an individual or a group of people that helps to manifest
a threat. It is difficult to detect for the victims that from which agent the threats have actually
arrived. Threats Agents are:
Corporations:
The organizations or enterprises that are engaged with tactics or systems those are
offensive (Reuter, 2015). In this type of threat agent, the corporations are known as the agents of
hostile threat. The main motive of the corporations is to make advantages that are related to
competition over the competitors.
Cyber Criminals:
Cyber criminals are hostile naturally. The main motive of cyber criminals is to gain
financially and level of skills of cyber criminals are quite high. All the levels including local,
international and national levels are organized by cyber criminals.
Cyber Terrorists:
The activities of cyber terrorists are expanded and are engaged in cyber attack. The
motivation of cyber terrorists can be both as religious and political (Schaumüller-Bichl &
Kolberger, 2106). The capabilities of this threat agent differ from high to low. The critical
infrastructures are mainly targeted by the cyber terrorist that includes telecommunications,
energy production and public health.
Hacktivists:
Answer to Question 3:
Threat Agents are those who are an individual or a group of people that helps to manifest
a threat. It is difficult to detect for the victims that from which agent the threats have actually
arrived. Threats Agents are:
Corporations:
The organizations or enterprises that are engaged with tactics or systems those are
offensive (Reuter, 2015). In this type of threat agent, the corporations are known as the agents of
hostile threat. The main motive of the corporations is to make advantages that are related to
competition over the competitors.
Cyber Criminals:
Cyber criminals are hostile naturally. The main motive of cyber criminals is to gain
financially and level of skills of cyber criminals are quite high. All the levels including local,
international and national levels are organized by cyber criminals.
Cyber Terrorists:
The activities of cyber terrorists are expanded and are engaged in cyber attack. The
motivation of cyber terrorists can be both as religious and political (Schaumüller-Bichl &
Kolberger, 2106). The capabilities of this threat agent differ from high to low. The critical
infrastructures are mainly targeted by the cyber terrorist that includes telecommunications,
energy production and public health.
Hacktivists:

8BIG DATA THREAT LANDSCAPE OF EUROPE
These agents are mainly individuals that take the help of the computer system to promote
and protest their cause of hacking. The targets of hackers of online social media are high profile
websites, intelligence agencies, military institutions and corporations.
Script Kiddies:
Script Kiddies are agents that use the process of cyber attack just for fun. Their intention
is not to harm other but to just hack for fun. They are usually unskilled who uses programs and
scripts to attack networks and computer systems or the servers.
Employees:
Employees include contractors, organizational staffs and even the security guards of the
company (Schneider, 2017). The resource of the company is accessed by the insider employees
of the company. Employees are both hostile and non hostile agents of a company. They have
some amount of knowledge that helps to attack the assets of their company.
Nation States:
Nation States have cyber capabilities that are offensive and use these capabilities against
adversary. Due to deployment of attacks that are sophisticated, nation state agents have become
prominent. These are also known as cyber weapons.
Minimize the impact of Threat agents:
To minimize the impact of threat agents, certain mitigation processes are used. One of the
main processes to mitigate the impact of threat agents is the process of cryptography. The
cryptography process is used to prevent the access of unauthorized user and unintentional
leakage of data that are sensitive and also the systems. The impact of agents that are related to
These agents are mainly individuals that take the help of the computer system to promote
and protest their cause of hacking. The targets of hackers of online social media are high profile
websites, intelligence agencies, military institutions and corporations.
Script Kiddies:
Script Kiddies are agents that use the process of cyber attack just for fun. Their intention
is not to harm other but to just hack for fun. They are usually unskilled who uses programs and
scripts to attack networks and computer systems or the servers.
Employees:
Employees include contractors, organizational staffs and even the security guards of the
company (Schneider, 2017). The resource of the company is accessed by the insider employees
of the company. Employees are both hostile and non hostile agents of a company. They have
some amount of knowledge that helps to attack the assets of their company.
Nation States:
Nation States have cyber capabilities that are offensive and use these capabilities against
adversary. Due to deployment of attacks that are sophisticated, nation state agents have become
prominent. These are also known as cyber weapons.
Minimize the impact of Threat agents:
To minimize the impact of threat agents, certain mitigation processes are used. One of the
main processes to mitigate the impact of threat agents is the process of cryptography. The
cryptography process is used to prevent the access of unauthorized user and unintentional
leakage of data that are sensitive and also the systems. The impact of agents that are related to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9BIG DATA THREAT LANDSCAPE OF EUROPE
threats can also be minimized by using secured APIs, planning or designing inadequately,
adaptation of improper software. Using processing platforms that are trustworthy are also
recommended to mitigate the impact of threat agents (Silva, Rocha & Guimaraes, 2016). The big
data should be hosted with the ISP or the cloud provider should also be implemented to prevent
attacks to cyber space. All the infrastructure should be kept safe by the manufacturers so that the
insider threats may not affect the company’s infrastructure. Strong hashing function should be
implemented in the cloud structure instead of collision and weak prone hashing algorithm.
Answer to Question 4:
The European Threat Landscape can be improved by the following ways:
If stored processes are used In ETL processing, then a copy of all the input
parameters are to be stored in internal variables. The server of SQL often faces
parameter sniffing when it exhibits plan of query execution.
The number of joins and CTEs are to be limited while working with a single
query. The query optimizer starts to choose plans that are sub optimal in SQL
server.
The update option of auto statistics of the database that is been used should be
checked and turned on. The database should always be kept updated.
A step should be attached at the end of all the jobs so that the indexes are rebuilt
of the reporting tables. The indexes are kept sure using this process.
Parallel thread should be utilized to check the ETL logic scheduling (Stupka,
Horák & Husák, 2017) It is not suggested to all the code at the same time if the
codes are not connected to each other. This helps to save time.
threats can also be minimized by using secured APIs, planning or designing inadequately,
adaptation of improper software. Using processing platforms that are trustworthy are also
recommended to mitigate the impact of threat agents (Silva, Rocha & Guimaraes, 2016). The big
data should be hosted with the ISP or the cloud provider should also be implemented to prevent
attacks to cyber space. All the infrastructure should be kept safe by the manufacturers so that the
insider threats may not affect the company’s infrastructure. Strong hashing function should be
implemented in the cloud structure instead of collision and weak prone hashing algorithm.
Answer to Question 4:
The European Threat Landscape can be improved by the following ways:
If stored processes are used In ETL processing, then a copy of all the input
parameters are to be stored in internal variables. The server of SQL often faces
parameter sniffing when it exhibits plan of query execution.
The number of joins and CTEs are to be limited while working with a single
query. The query optimizer starts to choose plans that are sub optimal in SQL
server.
The update option of auto statistics of the database that is been used should be
checked and turned on. The database should always be kept updated.
A step should be attached at the end of all the jobs so that the indexes are rebuilt
of the reporting tables. The indexes are kept sure using this process.
Parallel thread should be utilized to check the ETL logic scheduling (Stupka,
Horák & Husák, 2017) It is not suggested to all the code at the same time if the
codes are not connected to each other. This helps to save time.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10BIG DATA THREAT LANDSCAPE OF EUROPE
The ETL code should not be operated with cursor. Cursors should not be used in
any ETL processes that are scheduled regularly.
The European Threat Landscape should be planned for long term so that it does
not get expires in short period of time.
The process of ETL should be kept updated along with the updated threats
because the agents of threats keep on improving itself with time (Unger, 2014).
New attacks are invented with every new attack that is carried out. So to cope
with those, the defenders of the attack should be kept updated
Answer to Question 5:
The current state of ENISA security provides a very good security to the organizations.
To maintain a good practice for the security of information, ENISA gives recommendations and
advices to the organizations and the sectors. The work of ENISA is to improve the condition of
critical network and information infrastructure of Europe and helps to implement the relevant
legislation of Europe (Weber & Weber, 2015). The Europe member states are enhanced by
ENISA by giving a support to the development of communities of cross border to improve the
information and network security of Europe. To minimize the impact of threat agents, certain
mitigation processes are used. One of the main processes to mitigate the impact of threat agents
is to improve the process of cryptography. The cryptography process is used to prevent the
access of unauthorized user and unintentional leakage of data that are sensitive and also the
systems. The impact of agents that are related to threats can also be minimized by using secured
APIs, planning or designing inadequately, adaptation of improper software. Using processing
platforms that are trustworthy are also recommended to mitigate the impact of threat agents. The
big data should be hosted with the ISP or the cloud provider should also be implemented to
The ETL code should not be operated with cursor. Cursors should not be used in
any ETL processes that are scheduled regularly.
The European Threat Landscape should be planned for long term so that it does
not get expires in short period of time.
The process of ETL should be kept updated along with the updated threats
because the agents of threats keep on improving itself with time (Unger, 2014).
New attacks are invented with every new attack that is carried out. So to cope
with those, the defenders of the attack should be kept updated
Answer to Question 5:
The current state of ENISA security provides a very good security to the organizations.
To maintain a good practice for the security of information, ENISA gives recommendations and
advices to the organizations and the sectors. The work of ENISA is to improve the condition of
critical network and information infrastructure of Europe and helps to implement the relevant
legislation of Europe (Weber & Weber, 2015). The Europe member states are enhanced by
ENISA by giving a support to the development of communities of cross border to improve the
information and network security of Europe. To minimize the impact of threat agents, certain
mitigation processes are used. One of the main processes to mitigate the impact of threat agents
is to improve the process of cryptography. The cryptography process is used to prevent the
access of unauthorized user and unintentional leakage of data that are sensitive and also the
systems. The impact of agents that are related to threats can also be minimized by using secured
APIs, planning or designing inadequately, adaptation of improper software. Using processing
platforms that are trustworthy are also recommended to mitigate the impact of threat agents. The
big data should be hosted with the ISP or the cloud provider should also be implemented to

11BIG DATA THREAT LANDSCAPE OF EUROPE
prevent attacks to cyber space. The entire infrastructure should be kept safe by the manufacturers
so that the insider threats may not affect the company’s infrastructure. Strong hashing function
should be implemented in the cloud structure instead of collision and weak prone hashing
algorithm (Witt & Freudenberg, 2016). The mobile internet should be kept secured which has
increased to 44 percent of the total incidents that were reported. Because of the technical failures
and system failures 70 percent of the attack occurs. The root cause of the cyber attacks are
because of technical failures and system failures. The attacks happen mainly because of stations
based on mobile and routers and switches. Human errors are also one of the main causes in
making the ENISA not a successful one. Almost accounting 2.6 million connection of user are
affected to cyber attack due to human error.
prevent attacks to cyber space. The entire infrastructure should be kept safe by the manufacturers
so that the insider threats may not affect the company’s infrastructure. Strong hashing function
should be implemented in the cloud structure instead of collision and weak prone hashing
algorithm (Witt & Freudenberg, 2016). The mobile internet should be kept secured which has
increased to 44 percent of the total incidents that were reported. Because of the technical failures
and system failures 70 percent of the attack occurs. The root cause of the cyber attacks are
because of technical failures and system failures. The attacks happen mainly because of stations
based on mobile and routers and switches. Human errors are also one of the main causes in
making the ENISA not a successful one. Almost accounting 2.6 million connection of user are
affected to cyber attack due to human error.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





