Wireless Networks and Security: Evaluation of 5G Network and Security
VerifiedAdded on 2022/09/18
|20
|2663
|31
Report
AI Summary
This report provides a detailed evaluation of 5G network technology, comparing it with previous generations like 4G, 3G, and 2G across various parameters such as communication spectrum, modulation techniques, medium access control, network speed, bandwidth utilization, and security. The report explores the architecture of 5G networks, identifies and analyzes potential security attacks, and discusses limitations, particularly concerning network coverage. It also explores solutions to these limitations. The analysis covers various aspects, including the evolution of cellular networks, the underlying architecture of 5G, and the security challenges posed by the technology, making it a valuable resource for understanding the current state and future of 5G networks.

Running head: EVALUATION OF 5G NETWORK AND THE SECURITY
EVALUATION OF 5G NETWORK AND THE SECURITY
Name of student
Name of university
Author’s note:
EVALUATION OF 5G NETWORK AND THE SECURITY
Name of student
Name of university
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
EVALUATION OF 5G NETWORK AND THE SECURITY
Table of Contents
Introduction:...............................................................................................................................2
Motivation:.................................................................................................................................2
Discussion:.................................................................................................................................2
Comparison of cellular networks:..........................................................................................2
5G Architecture:...................................................................................................................15
Identification and Analysis of 5G Attacks:..........................................................................15
Identification and Analysis of 5G limitation in network coverage:.....................................17
Conclusion:..............................................................................................................................17
EVALUATION OF 5G NETWORK AND THE SECURITY
Table of Contents
Introduction:...............................................................................................................................2
Motivation:.................................................................................................................................2
Discussion:.................................................................................................................................2
Comparison of cellular networks:..........................................................................................2
5G Architecture:...................................................................................................................15
Identification and Analysis of 5G Attacks:..........................................................................15
Identification and Analysis of 5G limitation in network coverage:.....................................17
Conclusion:..............................................................................................................................17

2
EVALUATION OF 5G NETWORK AND THE SECURITY
Introduction:
The report analyses the 5G technology in details, which include Comparison of the existing
cellular networks generations (5G, 4G, 3G, and 2G) in terms of Communication spectrum,
modulation techniques, medium access control mechanism, Network speed and bandwidth
utilization and Security techniques and risk. The report Explore the architecture of a 5G
network to provide a comprehensive overview regarding the mechanism of 5G technology.
The report then identifies and analyses the 5G attacks on the access and core networks to
describe how 5G networks are exploited which affects the security of the data that is sent and
received through this network. Along with this the report provides a detailed description
regarding the limitation of the 5G network, especially in terms of media coverage. The report
not only describes limitation of 5G technology in terms of media coverage, but it also include
solution to this limitation which is discussed along with the limitation in this context.
Motivation:
The 4G technology or LTE has already set standard of high speed mobile internet and 5G
technology will enhance this speed even further to offer truly high speed network that the
previous generation technology such as 1G, 2G, 3G and even the high speed 4G LTE
technology has not offered yet . Therefore, 5G technology is the next technological
revolution that consumers should care about as it offers context for revolutionize telecom and
other industries as well.
Discussion:
Comparison of cellular networks:
Comparison of the existing cellular networks generations (5G, 4G, 3G, and 2G) includes
analysis of:
a. spectrum for Communication
EVALUATION OF 5G NETWORK AND THE SECURITY
Introduction:
The report analyses the 5G technology in details, which include Comparison of the existing
cellular networks generations (5G, 4G, 3G, and 2G) in terms of Communication spectrum,
modulation techniques, medium access control mechanism, Network speed and bandwidth
utilization and Security techniques and risk. The report Explore the architecture of a 5G
network to provide a comprehensive overview regarding the mechanism of 5G technology.
The report then identifies and analyses the 5G attacks on the access and core networks to
describe how 5G networks are exploited which affects the security of the data that is sent and
received through this network. Along with this the report provides a detailed description
regarding the limitation of the 5G network, especially in terms of media coverage. The report
not only describes limitation of 5G technology in terms of media coverage, but it also include
solution to this limitation which is discussed along with the limitation in this context.
Motivation:
The 4G technology or LTE has already set standard of high speed mobile internet and 5G
technology will enhance this speed even further to offer truly high speed network that the
previous generation technology such as 1G, 2G, 3G and even the high speed 4G LTE
technology has not offered yet . Therefore, 5G technology is the next technological
revolution that consumers should care about as it offers context for revolutionize telecom and
other industries as well.
Discussion:
Comparison of cellular networks:
Comparison of the existing cellular networks generations (5G, 4G, 3G, and 2G) includes
analysis of:
a. spectrum for Communication
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
EVALUATION OF 5G NETWORK AND THE SECURITY
b. techniques for modulation
c. mechanism for controlling access to medium
d. speed of Network and utilization of bandwidth
e. Security techniques and risk
Topics for comparison Technology Description
spectrum for Communication [1] 1G 1G technology consider
the following spectrum
configuration for
providing service to the
consumers:
Frequency: 150MHz /
900MHz
2G 2G technology consider
the following spectrum
configuration for
providing service to the
consumers:
Frequency: 1.8GHz
(900MHz), digital
telecommunication
3G 3G technology consider
the following spectrum
configuration for
EVALUATION OF 5G NETWORK AND THE SECURITY
b. techniques for modulation
c. mechanism for controlling access to medium
d. speed of Network and utilization of bandwidth
e. Security techniques and risk
Topics for comparison Technology Description
spectrum for Communication [1] 1G 1G technology consider
the following spectrum
configuration for
providing service to the
consumers:
Frequency: 150MHz /
900MHz
2G 2G technology consider
the following spectrum
configuration for
providing service to the
consumers:
Frequency: 1.8GHz
(900MHz), digital
telecommunication
3G 3G technology consider
the following spectrum
configuration for
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
EVALUATION OF 5G NETWORK AND THE SECURITY
providing service to the
consumers:
Frequency: 1.6 – 2.0 GHz
4G 4G technology consider
the following spectrum
configuration for
providing service to the
consumers:
Frequency: 2 – 8 GHz
5G 5G technology consider
the following spectrum
configuration for
providing service to the
consumers:
Frequency: 30-300 GHz
techniques for modulation [2] 1G the modulation technique
that is considered in the
1G technology is
analog frequency
modulation
2G the modulation technique
that is considered in the
2G technology is
EVALUATION OF 5G NETWORK AND THE SECURITY
providing service to the
consumers:
Frequency: 1.6 – 2.0 GHz
4G 4G technology consider
the following spectrum
configuration for
providing service to the
consumers:
Frequency: 2 – 8 GHz
5G 5G technology consider
the following spectrum
configuration for
providing service to the
consumers:
Frequency: 30-300 GHz
techniques for modulation [2] 1G the modulation technique
that is considered in the
1G technology is
analog frequency
modulation
2G the modulation technique
that is considered in the
2G technology is
5
EVALUATION OF 5G NETWORK AND THE SECURITY
Gaussian Minimum Shift
Keying which is referred
to as Gaussian filtered
Minimum Shift Keying
3G the modulation technique
that is considered in the
3G technology is
8PSK modulation scheme
4G the modulation
techniques that are
considered in the 4G
technology are phase-
shift keying (QPSK), 16-
phase quadrature
amplitude modulation
(16QAM), or 64-state
quadrature amplitude
modulation (64QAM)
5G the modulation
techniques that are
considered in the 5G
technology are Filter
Bank Multi-Carrier
(FBMC), Universal
EVALUATION OF 5G NETWORK AND THE SECURITY
Gaussian Minimum Shift
Keying which is referred
to as Gaussian filtered
Minimum Shift Keying
3G the modulation technique
that is considered in the
3G technology is
8PSK modulation scheme
4G the modulation
techniques that are
considered in the 4G
technology are phase-
shift keying (QPSK), 16-
phase quadrature
amplitude modulation
(16QAM), or 64-state
quadrature amplitude
modulation (64QAM)
5G the modulation
techniques that are
considered in the 5G
technology are Filter
Bank Multi-Carrier
(FBMC), Universal
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
EVALUATION OF 5G NETWORK AND THE SECURITY
Filtered Multi-Carrier
(UFMC), Generalized
Frequency Division
Multiplexing (GFDM),
Filtered OFDM (f-
OFDM)
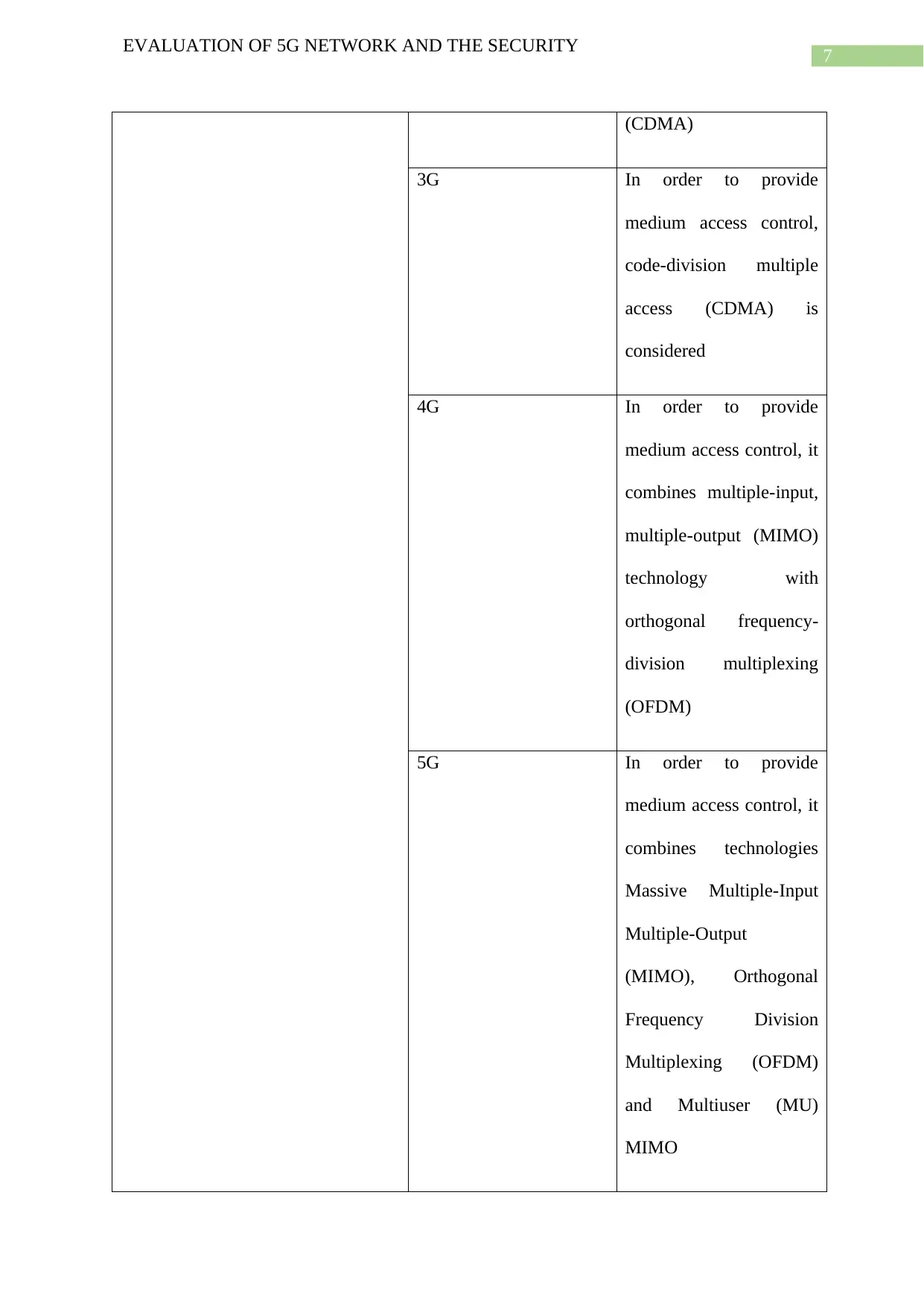
mechanism for controlling access to
medium [3]
1G In order to provide
medium access control,
the mechanism that is
used is frequency-
division multiple access
(FDMA) where the
available bandwidth is
divided into frequency
bands without
overlapping with each
other
2G In order to provide
medium access control,
the techniques that are
considered are time-
division multiple access
(TDMA) and code-
division multiple access
EVALUATION OF 5G NETWORK AND THE SECURITY
Filtered Multi-Carrier
(UFMC), Generalized
Frequency Division
Multiplexing (GFDM),
Filtered OFDM (f-
OFDM)
mechanism for controlling access to
medium [3]
1G In order to provide
medium access control,
the mechanism that is
used is frequency-
division multiple access
(FDMA) where the
available bandwidth is
divided into frequency
bands without
overlapping with each
other
2G In order to provide
medium access control,
the techniques that are
considered are time-
division multiple access
(TDMA) and code-
division multiple access
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
EVALUATION OF 5G NETWORK AND THE SECURITY
(CDMA)
3G In order to provide
medium access control,
code-division multiple
access (CDMA) is
considered
4G In order to provide
medium access control, it
combines multiple-input,
multiple-output (MIMO)
technology with
orthogonal frequency-
division multiplexing
(OFDM)
5G In order to provide
medium access control, it
combines technologies
Massive Multiple-Input
Multiple-Output
(MIMO), Orthogonal
Frequency Division
Multiplexing (OFDM)
and Multiuser (MU)
MIMO
EVALUATION OF 5G NETWORK AND THE SECURITY
(CDMA)
3G In order to provide
medium access control,
code-division multiple
access (CDMA) is
considered
4G In order to provide
medium access control, it
combines multiple-input,
multiple-output (MIMO)
technology with
orthogonal frequency-
division multiplexing
(OFDM)
5G In order to provide
medium access control, it
combines technologies
Massive Multiple-Input
Multiple-Output
(MIMO), Orthogonal
Frequency Division
Multiplexing (OFDM)
and Multiuser (MU)
MIMO

8
EVALUATION OF 5G NETWORK AND THE SECURITY
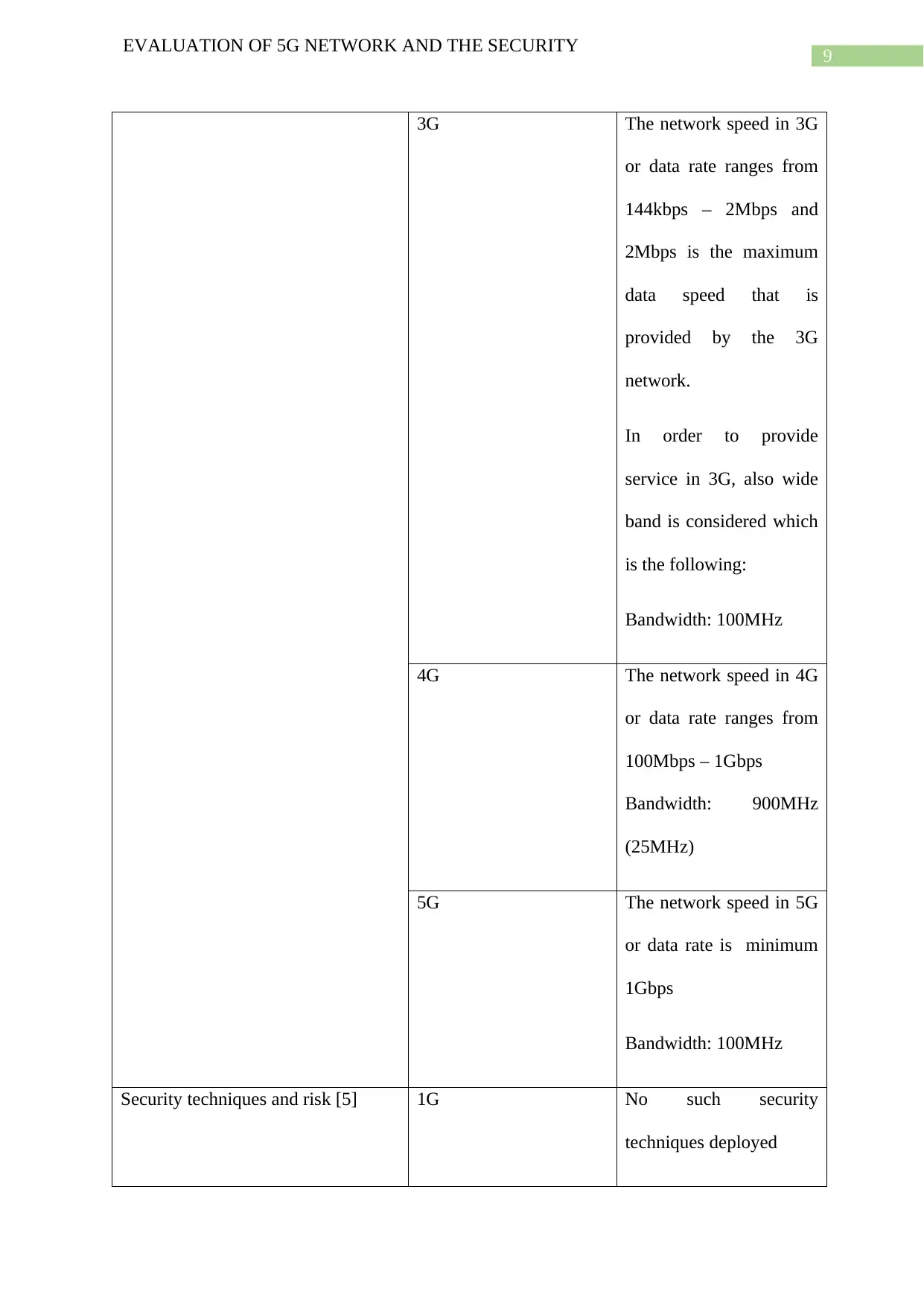
speed of Network and utilization of
bandwidth [4]
1G The network speed in 1G
also known as data rate
ranges from 2.4 Kbps to
14.4 kbps
In order to provide
service in 1G narrow
band is considered which
is the following:
Bandwidth: Analog
telecommunication
(30KHz)
2G The network speed in 2G
or data rate is 64kbps and
this is the maximum data
speed that is provided by
the 2G network.
In order to provide
service in 2G, also
narrow band is
considered which is the
following:
Bandwidth: 900MHz
(25MHz)
EVALUATION OF 5G NETWORK AND THE SECURITY
speed of Network and utilization of
bandwidth [4]
1G The network speed in 1G
also known as data rate
ranges from 2.4 Kbps to
14.4 kbps
In order to provide
service in 1G narrow
band is considered which
is the following:
Bandwidth: Analog
telecommunication
(30KHz)
2G The network speed in 2G
or data rate is 64kbps and
this is the maximum data
speed that is provided by
the 2G network.
In order to provide
service in 2G, also
narrow band is
considered which is the
following:
Bandwidth: 900MHz
(25MHz)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
EVALUATION OF 5G NETWORK AND THE SECURITY
3G The network speed in 3G
or data rate ranges from
144kbps – 2Mbps and
2Mbps is the maximum
data speed that is
provided by the 3G
network.
In order to provide
service in 3G, also wide
band is considered which
is the following:
Bandwidth: 100MHz
4G The network speed in 4G
or data rate ranges from
100Mbps – 1Gbps
Bandwidth: 900MHz
(25MHz)
5G The network speed in 5G
or data rate is minimum
1Gbps
Bandwidth: 100MHz
Security techniques and risk [5] 1G No such security
techniques deployed
EVALUATION OF 5G NETWORK AND THE SECURITY
3G The network speed in 3G
or data rate ranges from
144kbps – 2Mbps and
2Mbps is the maximum
data speed that is
provided by the 3G
network.
In order to provide
service in 3G, also wide
band is considered which
is the following:
Bandwidth: 100MHz
4G The network speed in 4G
or data rate ranges from
100Mbps – 1Gbps
Bandwidth: 900MHz
(25MHz)
5G The network speed in 5G
or data rate is minimum
1Gbps
Bandwidth: 100MHz
Security techniques and risk [5] 1G No such security
techniques deployed
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
EVALUATION OF 5G NETWORK AND THE SECURITY
2G Security features of
GSM, international
standard for 2G
technology include
authentication,
confidentiality and
anonymity.
For ensuring
authentication in GSM
A3 algorithm is used. For
encryption A5 algorithm
is used and for cipher,
key A8 algorithm is
considered.
Authentication of the
user is verified through
the random number or the
RAND that is sent to the
mobile SIM by the virtual
location register or the
VLR. Now the mobile
station sends the SRES
that is generated by the
SIM which VLR
compares with RAND.
EVALUATION OF 5G NETWORK AND THE SECURITY
2G Security features of
GSM, international
standard for 2G
technology include
authentication,
confidentiality and
anonymity.
For ensuring
authentication in GSM
A3 algorithm is used. For
encryption A5 algorithm
is used and for cipher,
key A8 algorithm is
considered.
Authentication of the
user is verified through
the random number or the
RAND that is sent to the
mobile SIM by the virtual
location register or the
VLR. Now the mobile
station sends the SRES
that is generated by the
SIM which VLR
compares with RAND.

11
EVALUATION OF 5G NETWORK AND THE SECURITY
The subscriber is verified
and authenticated only if
these two values are
same, otherwise the VLR
does not accept the
subscriber and the
subscriber is rejected.
3G In order to provide
security in 3G,
unauthorised
modification, insertion
and replay of messages is
restricted and also
consider the 128-bit
integrity key (IK) for
ensuring authentication.
Along with that, integrity
is also applied for
network layer that
consists the Radio
Resource Control (RRC)
for enhancing security
4G In 4G, security features
considered for the 2G and
3G is applied for 4G with
EVALUATION OF 5G NETWORK AND THE SECURITY
The subscriber is verified
and authenticated only if
these two values are
same, otherwise the VLR
does not accept the
subscriber and the
subscriber is rejected.
3G In order to provide
security in 3G,
unauthorised
modification, insertion
and replay of messages is
restricted and also
consider the 128-bit
integrity key (IK) for
ensuring authentication.
Along with that, integrity
is also applied for
network layer that
consists the Radio
Resource Control (RRC)
for enhancing security
4G In 4G, security features
considered for the 2G and
3G is applied for 4G with
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





