Evaluation of 5G Network and the Security - MN603, T2 2019
VerifiedAdded on 2022/09/23
|10
|2730
|25
Report
AI Summary
This report provides a comprehensive evaluation of 5G network security, comparing it with previous generations of cellular networks, including 2G, 3G, and 4G. The report delves into the architectural aspects of 5G, exploring its key features and cloud-native design. It identifies and analyzes potential 5G attacks, such as those targeting IoT devices and autonomous vehicles, and discusses associated security challenges. Furthermore, the report examines the limitations of 5G in terms of network coverage, particularly its reliance on millimeter wavelengths. The analysis proposes solutions for addressing these limitations, such as the deployment of a greater network of antennas. The report concludes by summarizing the key challenges and advantages of 5G, emphasizing its potential to revolutionize wireless communication while also highlighting the importance of addressing its security vulnerabilities and coverage limitations. The report uses various factors like communication spectrum, modulation techniques, security techniques, MAC mechanism, network speed and network bandwidth utilization for the comparison of cellular networks.

Running Head: NETWORKING
0
Networking
Evaluation of 5G Network and the Security
(Student Details: )
8/25/2019
0
Networking
Evaluation of 5G Network and the Security
(Student Details: )
8/25/2019
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking
1
Contents
Comparison of cellular networks...............................................................................................3
2G generation.........................................................................................................................3
3G generation.........................................................................................................................4
4G generation.........................................................................................................................4
5G generation.........................................................................................................................5
5G Architecture..........................................................................................................................5
Identification and Analysis of 5G Attacks.................................................................................6
Identification and Analysis of 5G limitation in-network coverage............................................7
Conclusion..................................................................................................................................7
References..................................................................................................................................8
1
Contents
Comparison of cellular networks...............................................................................................3
2G generation.........................................................................................................................3
3G generation.........................................................................................................................4
4G generation.........................................................................................................................4
5G generation.........................................................................................................................5
5G Architecture..........................................................................................................................5
Identification and Analysis of 5G Attacks.................................................................................6
Identification and Analysis of 5G limitation in-network coverage............................................7
Conclusion..................................................................................................................................7
References..................................................................................................................................8

Networking
2
Evaluation of 5G Network and the Security
Introduction
This assignment is based on an evaluation of 5G network and the security. The report is
aiming to compare the 5G wireless communication technology with the already existing
technologies within the literature. This research paper is going to evaluate the 5G network
security. In this context, 5G is the novel mobile network technology that is going to replace
the current 4G technology while offering high data rate, energy saving, reduced latency, cost
reduction, massive device connectivity as well as greater system capacity. In this era, mobile
service providers are planning to move towards 5G technology for supporting the growing
number of devices that demand internet access. It has been found that mobile service
providers require high bandwidth for functioning normally as compared to that 4G network
bandwidth 1. To do so, this discussion will compare standards-based technologies that are
utilized in various networks. In addition, in this discussion various wireless network
performances will be tested and evaluated on the basis of advanced technologies.
Motivation
In this section, the discussion on why we need 5G network for data services will take place.
The reasons why the world should move towards 5G in the future include:
5G is able to carry enormous data capacity
5G is having a higher speed than 4G
5G offers incredibly low latency
Finally, 5G marks a big step from the predecessor 2.
Recent data and research are showing that 5G mobile networks can provide boost efficiency
while unleashing the opportunities for automation. Apart from this, 5G should be used now
and in future as well because it will enable us to find advanced technologies like augmented
reality (AR) and virtual reality (VR) 3. In this way, readers must note that next-generation
network connectivity should be set for reinventing the world of business in the following
ways:
Smart cities 4.
Autonomous cars
2
Evaluation of 5G Network and the Security
Introduction
This assignment is based on an evaluation of 5G network and the security. The report is
aiming to compare the 5G wireless communication technology with the already existing
technologies within the literature. This research paper is going to evaluate the 5G network
security. In this context, 5G is the novel mobile network technology that is going to replace
the current 4G technology while offering high data rate, energy saving, reduced latency, cost
reduction, massive device connectivity as well as greater system capacity. In this era, mobile
service providers are planning to move towards 5G technology for supporting the growing
number of devices that demand internet access. It has been found that mobile service
providers require high bandwidth for functioning normally as compared to that 4G network
bandwidth 1. To do so, this discussion will compare standards-based technologies that are
utilized in various networks. In addition, in this discussion various wireless network
performances will be tested and evaluated on the basis of advanced technologies.
Motivation
In this section, the discussion on why we need 5G network for data services will take place.
The reasons why the world should move towards 5G in the future include:
5G is able to carry enormous data capacity
5G is having a higher speed than 4G
5G offers incredibly low latency
Finally, 5G marks a big step from the predecessor 2.
Recent data and research are showing that 5G mobile networks can provide boost efficiency
while unleashing the opportunities for automation. Apart from this, 5G should be used now
and in future as well because it will enable us to find advanced technologies like augmented
reality (AR) and virtual reality (VR) 3. In this way, readers must note that next-generation
network connectivity should be set for reinventing the world of business in the following
ways:
Smart cities 4.
Autonomous cars
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Networking
3
IoT technologies 5.
Immersive entertainment
Enhanced collaboration and communication
In this way, along with the business insights, the 5G network is going to help while
supporting remote working, and hence it will help colleagues to work on cloud-based
collaborative documents as well as over platforms in real-time 6.
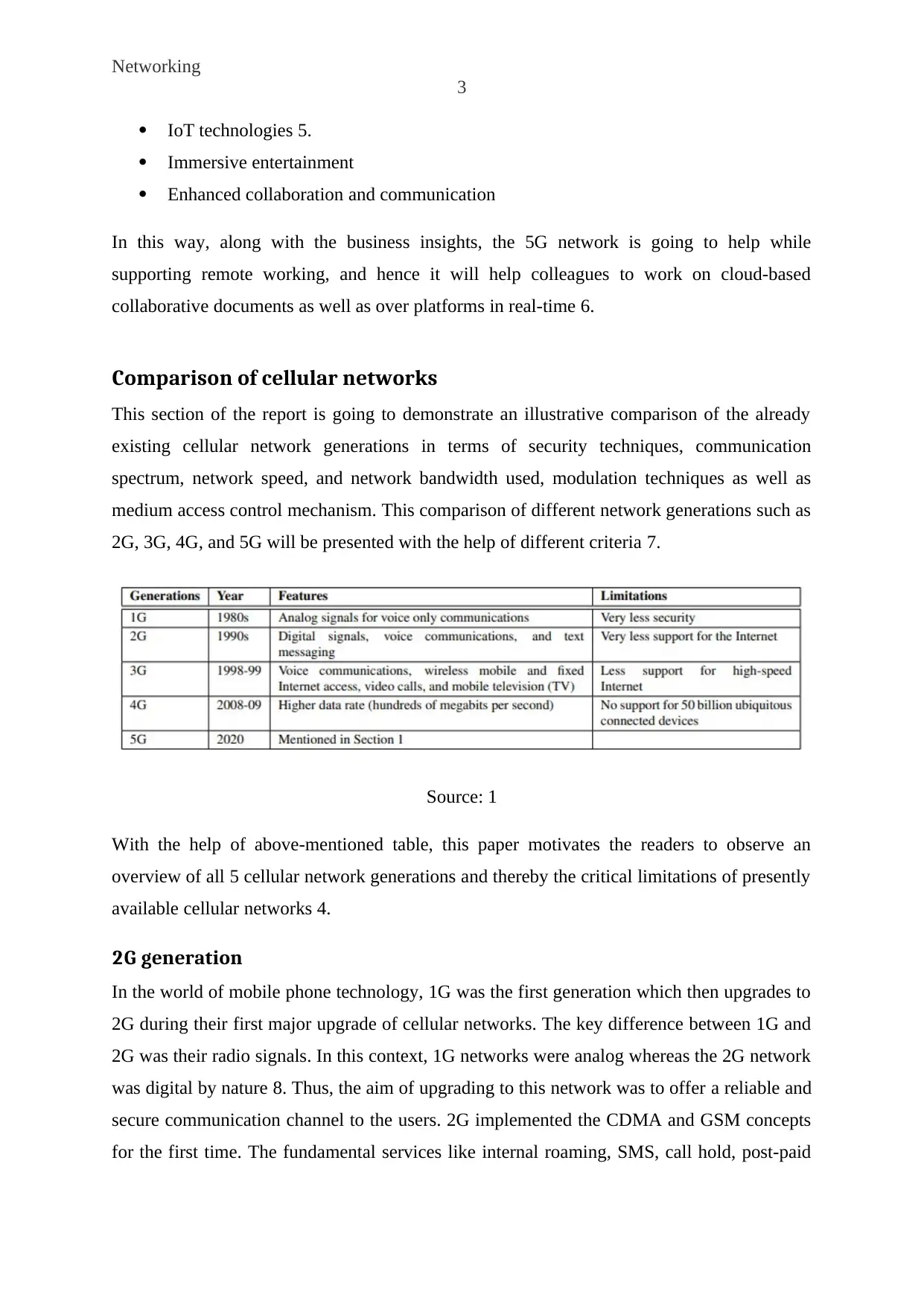
Comparison of cellular networks
This section of the report is going to demonstrate an illustrative comparison of the already
existing cellular network generations in terms of security techniques, communication
spectrum, network speed, and network bandwidth used, modulation techniques as well as
medium access control mechanism. This comparison of different network generations such as
2G, 3G, 4G, and 5G will be presented with the help of different criteria 7.
Source: 1
With the help of above-mentioned table, this paper motivates the readers to observe an
overview of all 5 cellular network generations and thereby the critical limitations of presently
available cellular networks 4.
2G generation
In the world of mobile phone technology, 1G was the first generation which then upgrades to
2G during their first major upgrade of cellular networks. The key difference between 1G and
2G was their radio signals. In this context, 1G networks were analog whereas the 2G network
was digital by nature 8. Thus, the aim of upgrading to this network was to offer a reliable and
secure communication channel to the users. 2G implemented the CDMA and GSM concepts
for the first time. The fundamental services like internal roaming, SMS, call hold, post-paid
3
IoT technologies 5.
Immersive entertainment
Enhanced collaboration and communication
In this way, along with the business insights, the 5G network is going to help while
supporting remote working, and hence it will help colleagues to work on cloud-based
collaborative documents as well as over platforms in real-time 6.
Comparison of cellular networks
This section of the report is going to demonstrate an illustrative comparison of the already
existing cellular network generations in terms of security techniques, communication
spectrum, network speed, and network bandwidth used, modulation techniques as well as
medium access control mechanism. This comparison of different network generations such as
2G, 3G, 4G, and 5G will be presented with the help of different criteria 7.
Source: 1
With the help of above-mentioned table, this paper motivates the readers to observe an
overview of all 5 cellular network generations and thereby the critical limitations of presently
available cellular networks 4.
2G generation
In the world of mobile phone technology, 1G was the first generation which then upgrades to
2G during their first major upgrade of cellular networks. The key difference between 1G and
2G was their radio signals. In this context, 1G networks were analog whereas the 2G network
was digital by nature 8. Thus, the aim of upgrading to this network was to offer a reliable and
secure communication channel to the users. 2G implemented the CDMA and GSM concepts
for the first time. The fundamental services like internal roaming, SMS, call hold, post-paid
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking
4
mobile services and conference calls were introduced for the first time with 2G. In this way,
from the communication spectrum, 2G was carrying the bandwidth of 900MHz with a
frequency of 1.8 GHz digital. As mentioned above, modulation techniques of CDMA and
GSM were used in 2G 9. The characteristics of 2G were digital which shows that
technologies like digital cellular GSM were used. Moreover, network speed and bandwidth
use for 2G is 64Kbps and 900MHz respectively.
3G generation
In this case, in order to overcome the challenges and barriers related to 2G, 3G was
introduced. The wireless network 3rd generation was typically designed for voice with data
considerations like text, internet, and multimedia access. In addition, 3G was first mobile
broadband cellular network. In this context, the standard 3G uses a novel technology known
as UMTS as their core network architecture was universal mobile telecommunication system
as UMTS. The 3rd generation was used by its users from 2000 to 2010 while providing digital
broadband as well as increased data speed. From the communication spectrum perspective,
3G used the bandwidth of 100MHz with a frequency of 1.6-2.0 GHz 10.
Apart from this, the data rate was highly improved as compared to 2G. The data rate for 3G is
144 Kbps-2Mbps which is better than those of 1G, 2G networks. In addition to that, from the
perspective of modulation techniques and MAC mechanism, 3G used CDMA, EDGE, and
UMTS for enhanced mobile network quality 11.
4G generation
The 4th generation network which is currently being used extensively all over the world is a
wireless network designed for data usage especially. 4G owns IP-based protocols which are
typically known as LTE 1. This is a true mobile broadband network that was introduced to
offer high quality, high speed as well as high capacity to its users through improving security.
The 4G technique lowered the cost of data and voice services, internet and multimedia over
IP. From the communication spectrum perspective, 4G is having a spectrum of 2-8 GHz
working since 2010 to date 12. Apart from this, data speed in 4G cellular network is
100Mbps-1Gbps with a frequency of 2-8 GHz. The major characteristics of 4G include high
data speed and all IPs. Moreover, modulation techniques and MAC mechanism for 4G
suggest that it uses technologies like WiFi and LTE extensively 13.
4
mobile services and conference calls were introduced for the first time with 2G. In this way,
from the communication spectrum, 2G was carrying the bandwidth of 900MHz with a
frequency of 1.8 GHz digital. As mentioned above, modulation techniques of CDMA and
GSM were used in 2G 9. The characteristics of 2G were digital which shows that
technologies like digital cellular GSM were used. Moreover, network speed and bandwidth
use for 2G is 64Kbps and 900MHz respectively.
3G generation
In this case, in order to overcome the challenges and barriers related to 2G, 3G was
introduced. The wireless network 3rd generation was typically designed for voice with data
considerations like text, internet, and multimedia access. In addition, 3G was first mobile
broadband cellular network. In this context, the standard 3G uses a novel technology known
as UMTS as their core network architecture was universal mobile telecommunication system
as UMTS. The 3rd generation was used by its users from 2000 to 2010 while providing digital
broadband as well as increased data speed. From the communication spectrum perspective,
3G used the bandwidth of 100MHz with a frequency of 1.6-2.0 GHz 10.
Apart from this, the data rate was highly improved as compared to 2G. The data rate for 3G is
144 Kbps-2Mbps which is better than those of 1G, 2G networks. In addition to that, from the
perspective of modulation techniques and MAC mechanism, 3G used CDMA, EDGE, and
UMTS for enhanced mobile network quality 11.
4G generation
The 4th generation network which is currently being used extensively all over the world is a
wireless network designed for data usage especially. 4G owns IP-based protocols which are
typically known as LTE 1. This is a true mobile broadband network that was introduced to
offer high quality, high speed as well as high capacity to its users through improving security.
The 4G technique lowered the cost of data and voice services, internet and multimedia over
IP. From the communication spectrum perspective, 4G is having a spectrum of 2-8 GHz
working since 2010 to date 12. Apart from this, data speed in 4G cellular network is
100Mbps-1Gbps with a frequency of 2-8 GHz. The major characteristics of 4G include high
data speed and all IPs. Moreover, modulation techniques and MAC mechanism for 4G
suggest that it uses technologies like WiFi and LTE extensively 13.
Networking
5
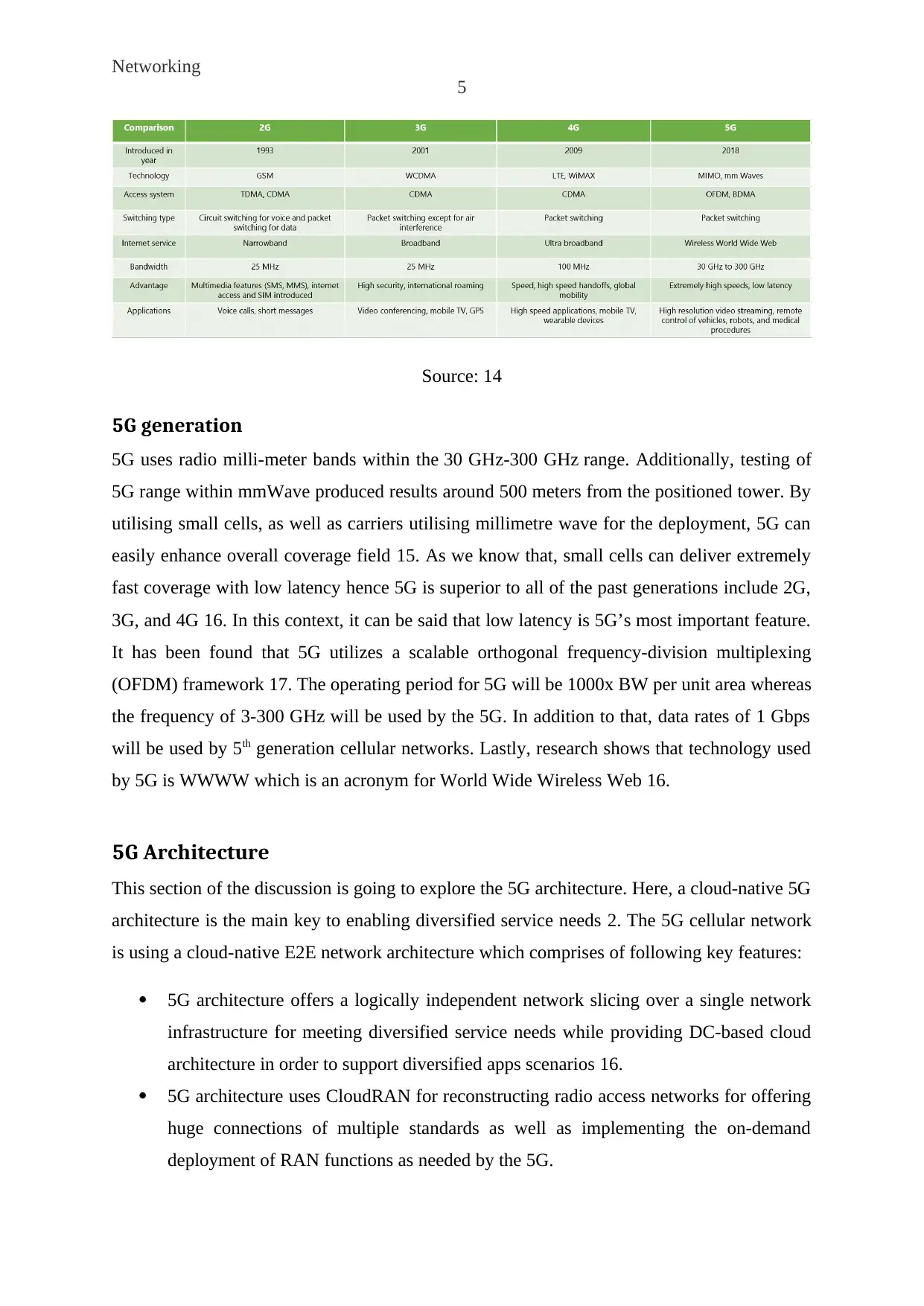
Source: 14
5G generation
5G uses radio milli-meter bands within the 30 GHz-300 GHz range. Additionally, testing of
5G range within mmWave produced results around 500 meters from the positioned tower. By
utilising small cells, as well as carriers utilising millimetre wave for the deployment, 5G can
easily enhance overall coverage field 15. As we know that, small cells can deliver extremely
fast coverage with low latency hence 5G is superior to all of the past generations include 2G,
3G, and 4G 16. In this context, it can be said that low latency is 5G’s most important feature.
It has been found that 5G utilizes a scalable orthogonal frequency-division multiplexing
(OFDM) framework 17. The operating period for 5G will be 1000x BW per unit area whereas
the frequency of 3-300 GHz will be used by the 5G. In addition to that, data rates of 1 Gbps
will be used by 5th generation cellular networks. Lastly, research shows that technology used
by 5G is WWWW which is an acronym for World Wide Wireless Web 16.
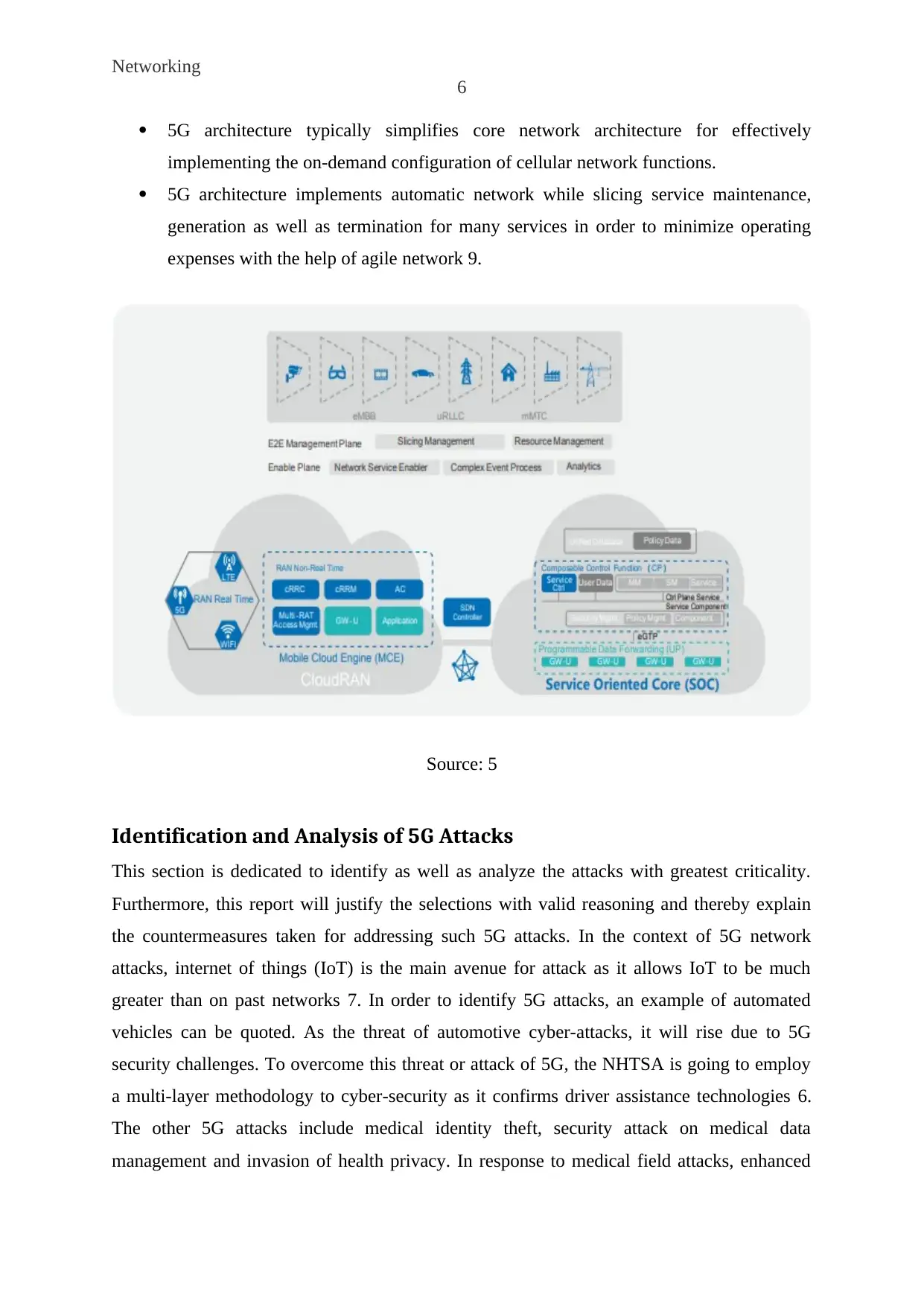
5G Architecture
This section of the discussion is going to explore the 5G architecture. Here, a cloud-native 5G
architecture is the main key to enabling diversified service needs 2. The 5G cellular network
is using a cloud-native E2E network architecture which comprises of following key features:
5G architecture offers a logically independent network slicing over a single network
infrastructure for meeting diversified service needs while providing DC-based cloud
architecture in order to support diversified apps scenarios 16.
5G architecture uses CloudRAN for reconstructing radio access networks for offering
huge connections of multiple standards as well as implementing the on-demand
deployment of RAN functions as needed by the 5G.
5
Source: 14
5G generation
5G uses radio milli-meter bands within the 30 GHz-300 GHz range. Additionally, testing of
5G range within mmWave produced results around 500 meters from the positioned tower. By
utilising small cells, as well as carriers utilising millimetre wave for the deployment, 5G can
easily enhance overall coverage field 15. As we know that, small cells can deliver extremely
fast coverage with low latency hence 5G is superior to all of the past generations include 2G,
3G, and 4G 16. In this context, it can be said that low latency is 5G’s most important feature.
It has been found that 5G utilizes a scalable orthogonal frequency-division multiplexing
(OFDM) framework 17. The operating period for 5G will be 1000x BW per unit area whereas
the frequency of 3-300 GHz will be used by the 5G. In addition to that, data rates of 1 Gbps
will be used by 5th generation cellular networks. Lastly, research shows that technology used
by 5G is WWWW which is an acronym for World Wide Wireless Web 16.
5G Architecture
This section of the discussion is going to explore the 5G architecture. Here, a cloud-native 5G
architecture is the main key to enabling diversified service needs 2. The 5G cellular network
is using a cloud-native E2E network architecture which comprises of following key features:
5G architecture offers a logically independent network slicing over a single network
infrastructure for meeting diversified service needs while providing DC-based cloud
architecture in order to support diversified apps scenarios 16.
5G architecture uses CloudRAN for reconstructing radio access networks for offering
huge connections of multiple standards as well as implementing the on-demand
deployment of RAN functions as needed by the 5G.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Networking
6
5G architecture typically simplifies core network architecture for effectively
implementing the on-demand configuration of cellular network functions.
5G architecture implements automatic network while slicing service maintenance,
generation as well as termination for many services in order to minimize operating
expenses with the help of agile network 9.
Source: 5
Identification and Analysis of 5G Attacks
This section is dedicated to identify as well as analyze the attacks with greatest criticality.
Furthermore, this report will justify the selections with valid reasoning and thereby explain
the countermeasures taken for addressing such 5G attacks. In the context of 5G network
attacks, internet of things (IoT) is the main avenue for attack as it allows IoT to be much
greater than on past networks 7. In order to identify 5G attacks, an example of automated
vehicles can be quoted. As the threat of automotive cyber-attacks, it will rise due to 5G
security challenges. To overcome this threat or attack of 5G, the NHTSA is going to employ
a multi-layer methodology to cyber-security as it confirms driver assistance technologies 6.
The other 5G attacks include medical identity theft, security attack on medical data
management and invasion of health privacy. In response to medical field attacks, enhanced
6
5G architecture typically simplifies core network architecture for effectively
implementing the on-demand configuration of cellular network functions.
5G architecture implements automatic network while slicing service maintenance,
generation as well as termination for many services in order to minimize operating
expenses with the help of agile network 9.
Source: 5
Identification and Analysis of 5G Attacks
This section is dedicated to identify as well as analyze the attacks with greatest criticality.
Furthermore, this report will justify the selections with valid reasoning and thereby explain
the countermeasures taken for addressing such 5G attacks. In the context of 5G network
attacks, internet of things (IoT) is the main avenue for attack as it allows IoT to be much
greater than on past networks 7. In order to identify 5G attacks, an example of automated
vehicles can be quoted. As the threat of automotive cyber-attacks, it will rise due to 5G
security challenges. To overcome this threat or attack of 5G, the NHTSA is going to employ
a multi-layer methodology to cyber-security as it confirms driver assistance technologies 6.
The other 5G attacks include medical identity theft, security attack on medical data
management and invasion of health privacy. In response to medical field attacks, enhanced
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking
7
IoT devices can deal with enhanced cyber-security threats in a more challenging way 14. 5G
attacks can occur on smart homes, which will need stronger tactics of authentication like
biometric identification. For example, software made by Sensory uses faces as well as voice
recognition for smart home door locks 4.
Identification and Analysis of 5G limitation in-network coverage
This section of the report is focused on identifying and analysing the issues related to 5G
network coverage. Furthermore, the discussion is going to provide reasons and hence explain
a solution used to address such limitation of network coverage. In this context, 5G utilizes
millimeter wavelengths that are lesser than 3G as well as 4G, and thereby they cannot travel
as far as 3G and 4G can. On the other hand, the 5G network coverage profile is smaller than
3G and 4G, yet the 5G signals are able to carry more data than the two networks 5. This is the
reason that remote and rural sites probably will not have 5G cellular services anytime soon.
5G is capable to provide better mobile network services as compared to the past generations
however proximity is a weakness which modern businesses must consider. In this way, for
addressing this limitation, signal carriers are continuously planning a much
greater network of antennas for effectively providing enough network coverage while using
5G 3.
Conclusion
In conclusion, this report has identified key challenges in 5G cellular network technologies as
compared to the current wireless communication network technologies. While doing so, the
discussion has successfully proposed potential solutions for addressing the 5G limitations.
Apart from this, this report has evaluated the wireless communication standards for various
wireless cyber-physical systems as well as IoT. While presenting the comparison of the
already existing cellular network generations include 2G, 3G, 4G, and 5G then the discussion
used some specific factors for the comparison. These factors were communication spectrum,
modulation techniques, security techniques, MAC mechanism, and network speed as well as
network bandwidth utilisation. In a nutshell, this research report on wireless networks and
security has successfully covered all possible aspects of 5G cellular networks for encouraging
the readers to use 5G in the future.
7
IoT devices can deal with enhanced cyber-security threats in a more challenging way 14. 5G
attacks can occur on smart homes, which will need stronger tactics of authentication like
biometric identification. For example, software made by Sensory uses faces as well as voice
recognition for smart home door locks 4.
Identification and Analysis of 5G limitation in-network coverage
This section of the report is focused on identifying and analysing the issues related to 5G
network coverage. Furthermore, the discussion is going to provide reasons and hence explain
a solution used to address such limitation of network coverage. In this context, 5G utilizes
millimeter wavelengths that are lesser than 3G as well as 4G, and thereby they cannot travel
as far as 3G and 4G can. On the other hand, the 5G network coverage profile is smaller than
3G and 4G, yet the 5G signals are able to carry more data than the two networks 5. This is the
reason that remote and rural sites probably will not have 5G cellular services anytime soon.
5G is capable to provide better mobile network services as compared to the past generations
however proximity is a weakness which modern businesses must consider. In this way, for
addressing this limitation, signal carriers are continuously planning a much
greater network of antennas for effectively providing enough network coverage while using
5G 3.
Conclusion
In conclusion, this report has identified key challenges in 5G cellular network technologies as
compared to the current wireless communication network technologies. While doing so, the
discussion has successfully proposed potential solutions for addressing the 5G limitations.
Apart from this, this report has evaluated the wireless communication standards for various
wireless cyber-physical systems as well as IoT. While presenting the comparison of the
already existing cellular network generations include 2G, 3G, 4G, and 5G then the discussion
used some specific factors for the comparison. These factors were communication spectrum,
modulation techniques, security techniques, MAC mechanism, and network speed as well as
network bandwidth utilisation. In a nutshell, this research report on wireless networks and
security has successfully covered all possible aspects of 5G cellular networks for encouraging
the readers to use 5G in the future.

Networking
8
References
x
[1] D.P. Agarwal and Q.A. Zeng, Introduction to wireless and mobile systems. USA:
Cengage Learning, 2015.
[2] M. Agiwal, A. Roy, and N. Saxena, "Next generation 5G wireless networks: A
comprehensive survey," IEEE communications surveys and tutorials, vol. 18, no. 3, pp.
1617-1655, 2016.
[3] R.N. Mitra and D.P. Agarwal, "5G mobile technology: A survey," ICT Express, vol. 1,
no. 3, pp. 132-137, 2015.
[4] T. Bakici, E. Almirall, and J. Wareham, "A smart city initiative: the case of Barcelona,"
Journal of the Knowledge Economy, vol. 4, no. 2, pp. 135-148, 2013.
[5] X. Foukas, G. Patounas, A. Elmokashfi, and M.K. Marina, "Network slicing in 5G:
Survey and challenges," IEEE Communications Magazine, vol. 55, no. 5, pp. 94-100,
2017.
[6] A. Gohil, H. Modi, and S.K. Patel, "5G technology of mobile communication: A
survey.," in International conference on intelligent systems and signal processing ISSP,
US, 2013, pp. 288-292.
[7] N. Ameen and R. Willis, "Current and future challenges facing the mobile
telecommunications industry in the Arab world," in the 3rd world congress on computer
applications and information systems, Dubai, 2016.
[8] G. Cecere, N. Corrocher, and R.D. Battaglia, "Innovation and competition in the
smartphone industry: Is there a dominant design?," Telecommunications Policy, vol. 39,
no. 3-4, pp. 162-175, 2015.
[9] A. Gupta and R.K. Jha, "A survey of 5G network: Architecture and emerging
technologies," IEEE access, vol. 3, pp. 1206-1232, 2015.
[10] Y. Huo, X. Dong, and W. Xu, "5G Cellular User Equipment: From Theory to Practical
Hardware Design," IEEE Access, vol. 5, pp. 13992-14010, 2017.
8
References
x
[1] D.P. Agarwal and Q.A. Zeng, Introduction to wireless and mobile systems. USA:
Cengage Learning, 2015.
[2] M. Agiwal, A. Roy, and N. Saxena, "Next generation 5G wireless networks: A
comprehensive survey," IEEE communications surveys and tutorials, vol. 18, no. 3, pp.
1617-1655, 2016.
[3] R.N. Mitra and D.P. Agarwal, "5G mobile technology: A survey," ICT Express, vol. 1,
no. 3, pp. 132-137, 2015.
[4] T. Bakici, E. Almirall, and J. Wareham, "A smart city initiative: the case of Barcelona,"
Journal of the Knowledge Economy, vol. 4, no. 2, pp. 135-148, 2013.
[5] X. Foukas, G. Patounas, A. Elmokashfi, and M.K. Marina, "Network slicing in 5G:
Survey and challenges," IEEE Communications Magazine, vol. 55, no. 5, pp. 94-100,
2017.
[6] A. Gohil, H. Modi, and S.K. Patel, "5G technology of mobile communication: A
survey.," in International conference on intelligent systems and signal processing ISSP,
US, 2013, pp. 288-292.
[7] N. Ameen and R. Willis, "Current and future challenges facing the mobile
telecommunications industry in the Arab world," in the 3rd world congress on computer
applications and information systems, Dubai, 2016.
[8] G. Cecere, N. Corrocher, and R.D. Battaglia, "Innovation and competition in the
smartphone industry: Is there a dominant design?," Telecommunications Policy, vol. 39,
no. 3-4, pp. 162-175, 2015.
[9] A. Gupta and R.K. Jha, "A survey of 5G network: Architecture and emerging
technologies," IEEE access, vol. 3, pp. 1206-1232, 2015.
[10] Y. Huo, X. Dong, and W. Xu, "5G Cellular User Equipment: From Theory to Practical
Hardware Design," IEEE Access, vol. 5, pp. 13992-14010, 2017.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Networking
9
[11] C.X. Mavromoustakis, G. Mastorakis, and J.M. Batalla, Internet of Things (IoT) in 5G
mobile technologies. UK: Springer, 2016.
[12] N. Panwar, S. Sharma, and A.K. Singh, "A survey on 5G: The next generation of mobile
communication," Physical Communication, vol. 18, pp. 64-84, 2016.
[13] W. Xiang, K. Zheng, and X.S. Shen, 5G mobile communications. UK: Springer, 2016.
[14] S. Bi, Y. Zeng, and R. Zhang, "Wireless powered communication networks: An
overview," IEEE Wireless Communications, vol. 23, no. 2, pp. 10-18, 2016.
[15] V.W. Wong, Key technologies for 5G wireless systems. UK: Cambridge university
press, 2017.
[16] L.C. Wang and S. Rangapillai, "A survey on green 5G cellular networks," in
International conference on Signal Processing and Comunnicatiobs SPCOM, New
York, 2012, pp. 1-5.
[17] W. Stallings, Wireless communications & networks.: Pearson Education India, 2009.
x
9
[11] C.X. Mavromoustakis, G. Mastorakis, and J.M. Batalla, Internet of Things (IoT) in 5G
mobile technologies. UK: Springer, 2016.
[12] N. Panwar, S. Sharma, and A.K. Singh, "A survey on 5G: The next generation of mobile
communication," Physical Communication, vol. 18, pp. 64-84, 2016.
[13] W. Xiang, K. Zheng, and X.S. Shen, 5G mobile communications. UK: Springer, 2016.
[14] S. Bi, Y. Zeng, and R. Zhang, "Wireless powered communication networks: An
overview," IEEE Wireless Communications, vol. 23, no. 2, pp. 10-18, 2016.
[15] V.W. Wong, Key technologies for 5G wireless systems. UK: Cambridge university
press, 2017.
[16] L.C. Wang and S. Rangapillai, "A survey on green 5G cellular networks," in
International conference on Signal Processing and Comunnicatiobs SPCOM, New
York, 2012, pp. 1-5.
[17] W. Stallings, Wireless communications & networks.: Pearson Education India, 2009.
x
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





