Digital Forensics Report: Exotic Mountain Tour Data Breach
VerifiedAdded on 2023/06/11
|19
|2730
|345
Report
AI Summary
This report details a digital forensics investigation into a potential intellectual property theft at Exotic Mountain Tour Service (EMTS). The investigation was initiated after suspicions arose that a contract travel consultant, Bob Aspen, might have shared sensitive marketing data with a competitor, violating a non-disclosure agreement with Superior Bicycles, LLC. The analysis involved examining a USB drive found on Aspen's desk and analyzing intercepted email communications. Using ProDiscover, deleted and corrupted files were recovered from the USB drive, revealing hidden HTML messages and a picture concealed within a text file. Email analysis revealed conversations between Aspen and other parties discussing the alteration of file extensions, specifically JPEG images related to new kayaks. The report outlines the steps taken to search for and analyze these files, including the use of WinHex to examine corrupted data and the identification of key email addresses involved in the suspected data breach. The findings suggest malicious activity and potential intellectual property theft, necessitating further investigation and action to protect EMTS's interests. Desklib provides this document and many other solved assignments for students.

Running head: DIGITAL FORENSICS 1
Digital forensics
Name of the Student:
Name of the Institution:
Digital forensics
Name of the Student:
Name of the Institution:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

DIGITAL FORENSICS 2
Executive Summary
Technology is fast and vast growing, and so are methods to compromise it. Data integrity is more
important to any organization that aims at achieving a high competitive edge over other firms.
Given this fact, digital forensic tools have been devised to help analyze any malicious activities
(JenningsSmith Associates, n.d.). This report summarizes a scenario that happened at Exotic
Mountain Tour Services and Superior Bicycles LLC that lead to a data breach. But given the
intensity with which the ‘attackers’ tried to hide evidence and damage any available fingertips,
extensive search and examination became necessary for the success of the analysis.
Executive Summary
Technology is fast and vast growing, and so are methods to compromise it. Data integrity is more
important to any organization that aims at achieving a high competitive edge over other firms.
Given this fact, digital forensic tools have been devised to help analyze any malicious activities
(JenningsSmith Associates, n.d.). This report summarizes a scenario that happened at Exotic
Mountain Tour Services and Superior Bicycles LLC that lead to a data breach. But given the
intensity with which the ‘attackers’ tried to hide evidence and damage any available fingertips,
extensive search and examination became necessary for the success of the analysis.

DIGITAL FORENSICS 3
Table of contents
Executive Summary.........................................................................................................................2
List of Figures..................................................................................................................................4
Introduction......................................................................................................................................5
Scope, Case analysis and Findings..................................................................................................5
Storage Media forensics..................................................................................................................6
Email Service Forensics and Findings...........................................................................................11
Conclusion.....................................................................................................................................17
Tools Used.....................................................................................................................................17
References......................................................................................................................................18
Appendix........................................................................................................................................19
Table of contents
Executive Summary.........................................................................................................................2
List of Figures..................................................................................................................................4
Introduction......................................................................................................................................5
Scope, Case analysis and Findings..................................................................................................5
Storage Media forensics..................................................................................................................6
Email Service Forensics and Findings...........................................................................................11
Conclusion.....................................................................................................................................17
Tools Used.....................................................................................................................................17
References......................................................................................................................................18
Appendix........................................................................................................................................19
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

DIGITAL FORENSICS 4
List of Figures
Figure 1: logical image capture.......................................................................................................7
Figure 2: deleted files......................................................................................................................8
Figure 3: suspicious files dinged.....................................................................................................8
Figure 4: suspicious files.................................................................................................................8
Figure 5: opening them with winhex tool........................................................................................9
Figure 6: secret files exposed..........................................................................................................9
Figure 7: html messages................................................................................................................10
Figure 8: first intercepted email.....................................................................................................12
Figure 9: second intercepted mail..................................................................................................13
List of Figures
Figure 1: logical image capture.......................................................................................................7
Figure 2: deleted files......................................................................................................................8
Figure 3: suspicious files dinged.....................................................................................................8
Figure 4: suspicious files.................................................................................................................8
Figure 5: opening them with winhex tool........................................................................................9
Figure 6: secret files exposed..........................................................................................................9
Figure 7: html messages................................................................................................................10
Figure 8: first intercepted email.....................................................................................................12
Figure 9: second intercepted mail..................................................................................................13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

DIGITAL FORENSICS 5
Digital Forensics
Introduction
The Exotic Mountain Tour Service and the Superior Bicycles (LLC) entered into a deal in
which the later was to roll out an advert of its new product, but with conjunction with the former.
The deal, it appears was supervised by a contract travel agent, Bob Aspen, and part of the deal
was not to reveal any critical information or data to outside competitors. Bob, however appears
to have breached the contract and has engaged in a series of malicious activities that have left the
management at EMTS suspicious. Key to these activities are a USB drive believed to have been
used to transfer some critical information that could be part of the deal between the two firms as
well. The web-based email filter at the EMTs systems has revealed a series of blocked
conversations that Bob could have initiated. Now that the USB has been found at a desk that was
assigned to the agent, it sends the management to undertaking a digital forensic analysis in a bid
to establish whether in actual sense, Bob entered into malicious engagements with their
competitors.
This report is step-wise analysis of the evidence given, as run in ProDiscover digital
examination tool and conclusion of the finding.
Scope, Case analysis and Findings
In forensic examination involving graphic files, locating and recovering such files from
the suspects’ drive and determining which are key to the examination is an important
undertaking, while ensuring that data is not compromised in the process of locating, recovery and
analysis, as well as presentation (Enos & H). This means that the collected evidence has to be
specially handled, and stored for both analysis and presentation purposes. Additionally, it is wise
Digital Forensics
Introduction
The Exotic Mountain Tour Service and the Superior Bicycles (LLC) entered into a deal in
which the later was to roll out an advert of its new product, but with conjunction with the former.
The deal, it appears was supervised by a contract travel agent, Bob Aspen, and part of the deal
was not to reveal any critical information or data to outside competitors. Bob, however appears
to have breached the contract and has engaged in a series of malicious activities that have left the
management at EMTS suspicious. Key to these activities are a USB drive believed to have been
used to transfer some critical information that could be part of the deal between the two firms as
well. The web-based email filter at the EMTs systems has revealed a series of blocked
conversations that Bob could have initiated. Now that the USB has been found at a desk that was
assigned to the agent, it sends the management to undertaking a digital forensic analysis in a bid
to establish whether in actual sense, Bob entered into malicious engagements with their
competitors.
This report is step-wise analysis of the evidence given, as run in ProDiscover digital
examination tool and conclusion of the finding.
Scope, Case analysis and Findings
In forensic examination involving graphic files, locating and recovering such files from
the suspects’ drive and determining which are key to the examination is an important
undertaking, while ensuring that data is not compromised in the process of locating, recovery and
analysis, as well as presentation (Enos & H). This means that the collected evidence has to be
specially handled, and stored for both analysis and presentation purposes. Additionally, it is wise

DIGITAL FORENSICS 6
to examine all materials found with the suspect, or on their premises to ascertain whether a crime
or data breach occurred or not (forensicsciencesimplified.org, 2013).
This analysis undertaking involves examination of a USB drive, to check if it contains
any sensitive data, whether hidden or not, and an analysis of two screen shots obtained from the
email-based on a web-server system. Exchangeable image file formats can be examined based on
information in the pictures/graphics since each picture, represented in pixels, contains a header
section which gives instructions and information in regard to image display, and the file format
(Philip , 2011). Although it is hard to memorize details contained in the header, it is wise to do a
comparison of the images with the suspected ones. Once this is established, examination can take
place, but one has to ensure that any fragmented files on a disk are reconstructed so as to help
identify any useful patterns used in the graphics files. Any damaged headers should be repaired
as well.
The analysis of the presented media and media device was conducted on a ProDiscover
Basic platform, and conclusions made based on the unmasking made or observed.
Storage Media forensics
Exponential growth in the field and manufacture of flash drives has been experienced
thanks to the ever evolving technology. Data stored in external and internal drives could be a
reflection of human behavior and depending on the circumstances, may be subjected to forensic
analysis (Krishnum). A USB device believed to have been used by Bob Aspen is under
investigation in this case, and this analysis will be focusing on searching for any available data
that could lead to meaningful evidence, from both allocated and unallocated disk space, or to
determine any related data was actually deleted.
to examine all materials found with the suspect, or on their premises to ascertain whether a crime
or data breach occurred or not (forensicsciencesimplified.org, 2013).
This analysis undertaking involves examination of a USB drive, to check if it contains
any sensitive data, whether hidden or not, and an analysis of two screen shots obtained from the
email-based on a web-server system. Exchangeable image file formats can be examined based on
information in the pictures/graphics since each picture, represented in pixels, contains a header
section which gives instructions and information in regard to image display, and the file format
(Philip , 2011). Although it is hard to memorize details contained in the header, it is wise to do a
comparison of the images with the suspected ones. Once this is established, examination can take
place, but one has to ensure that any fragmented files on a disk are reconstructed so as to help
identify any useful patterns used in the graphics files. Any damaged headers should be repaired
as well.
The analysis of the presented media and media device was conducted on a ProDiscover
Basic platform, and conclusions made based on the unmasking made or observed.
Storage Media forensics
Exponential growth in the field and manufacture of flash drives has been experienced
thanks to the ever evolving technology. Data stored in external and internal drives could be a
reflection of human behavior and depending on the circumstances, may be subjected to forensic
analysis (Krishnum). A USB device believed to have been used by Bob Aspen is under
investigation in this case, and this analysis will be focusing on searching for any available data
that could lead to meaningful evidence, from both allocated and unallocated disk space, or to
determine any related data was actually deleted.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
DIGITAL FORENSICS 7
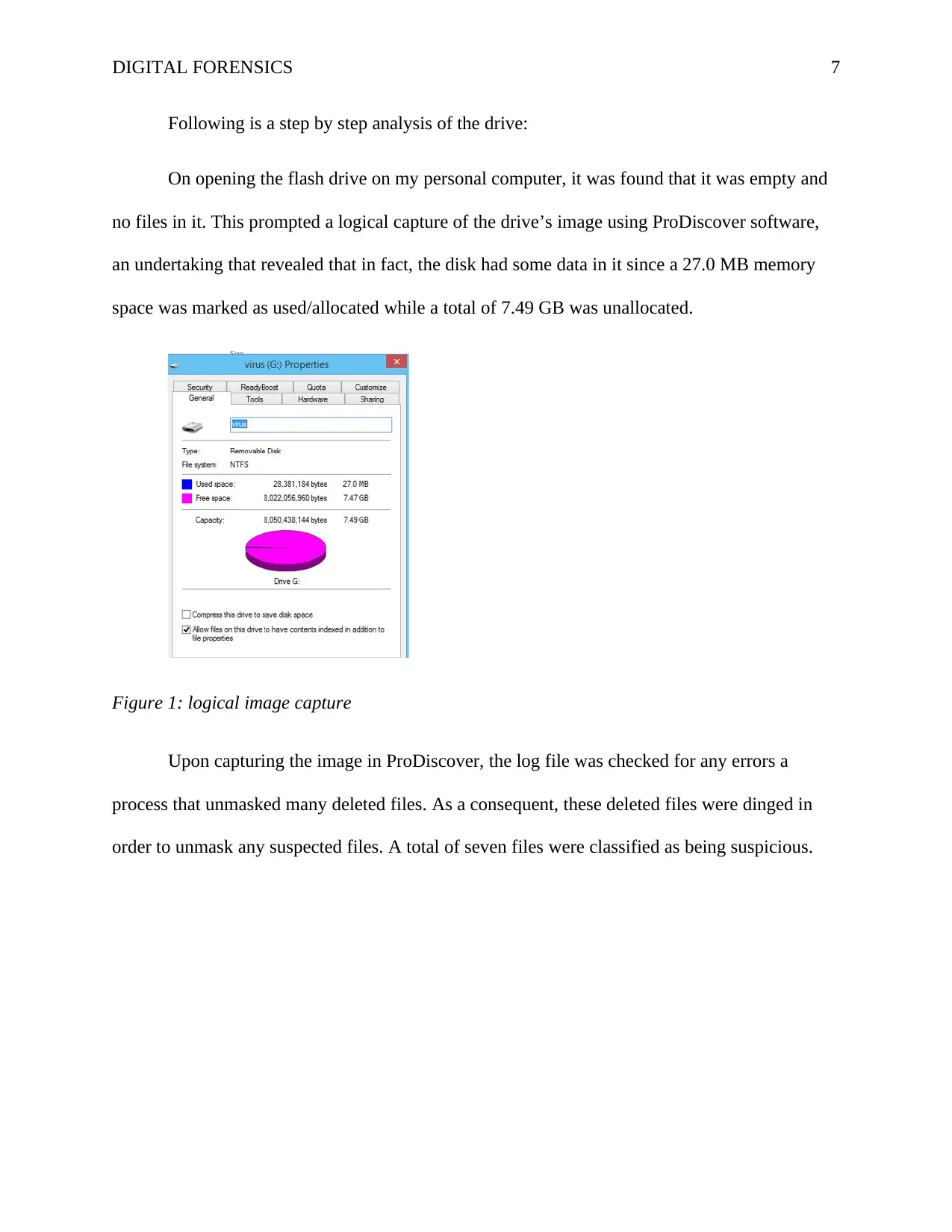
Following is a step by step analysis of the drive:
On opening the flash drive on my personal computer, it was found that it was empty and
no files in it. This prompted a logical capture of the drive’s image using ProDiscover software,
an undertaking that revealed that in fact, the disk had some data in it since a 27.0 MB memory
space was marked as used/allocated while a total of 7.49 GB was unallocated.
Figure 1: logical image capture
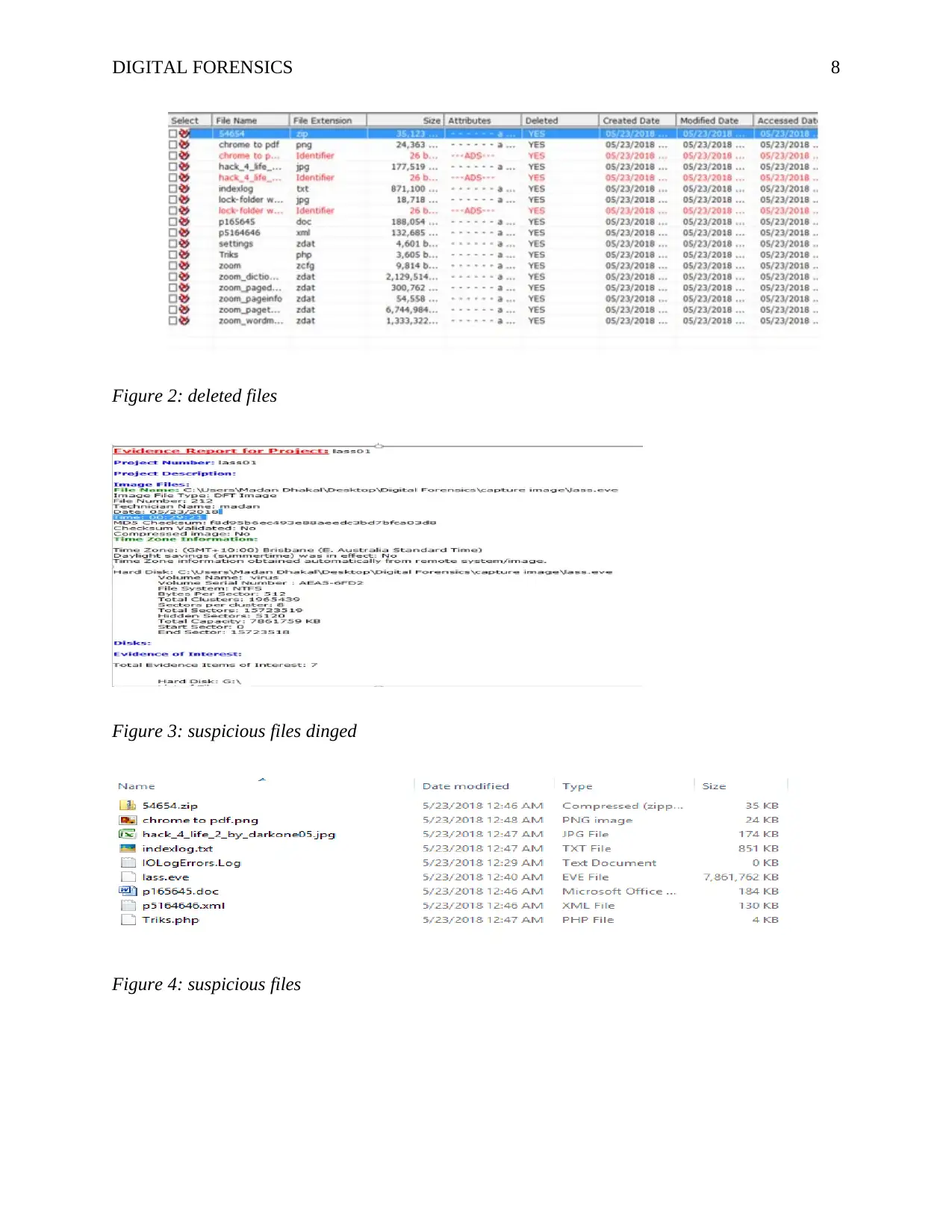
Upon capturing the image in ProDiscover, the log file was checked for any errors a
process that unmasked many deleted files. As a consequent, these deleted files were dinged in
order to unmask any suspected files. A total of seven files were classified as being suspicious.
Following is a step by step analysis of the drive:
On opening the flash drive on my personal computer, it was found that it was empty and
no files in it. This prompted a logical capture of the drive’s image using ProDiscover software,
an undertaking that revealed that in fact, the disk had some data in it since a 27.0 MB memory
space was marked as used/allocated while a total of 7.49 GB was unallocated.
Figure 1: logical image capture
Upon capturing the image in ProDiscover, the log file was checked for any errors a
process that unmasked many deleted files. As a consequent, these deleted files were dinged in
order to unmask any suspected files. A total of seven files were classified as being suspicious.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
DIGITAL FORENSICS 8
Figure 2: deleted files
Figure 3: suspicious files dinged
Figure 4: suspicious files
Figure 2: deleted files
Figure 3: suspicious files dinged
Figure 4: suspicious files
DIGITAL FORENSICS 9
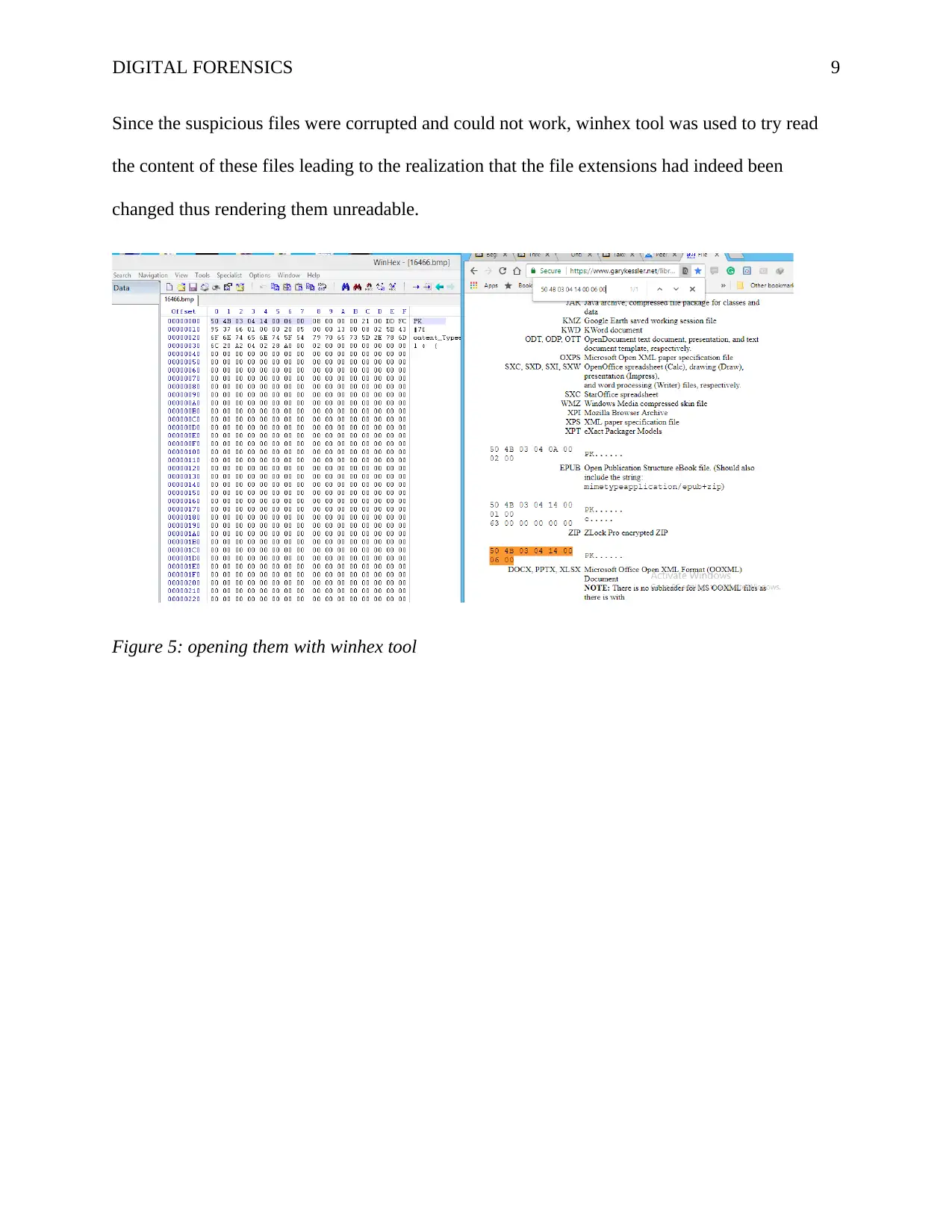
Since the suspicious files were corrupted and could not work, winhex tool was used to try read
the content of these files leading to the realization that the file extensions had indeed been
changed thus rendering them unreadable.
Figure 5: opening them with winhex tool
Since the suspicious files were corrupted and could not work, winhex tool was used to try read
the content of these files leading to the realization that the file extensions had indeed been
changed thus rendering them unreadable.
Figure 5: opening them with winhex tool
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
DIGITAL FORENSICS 10
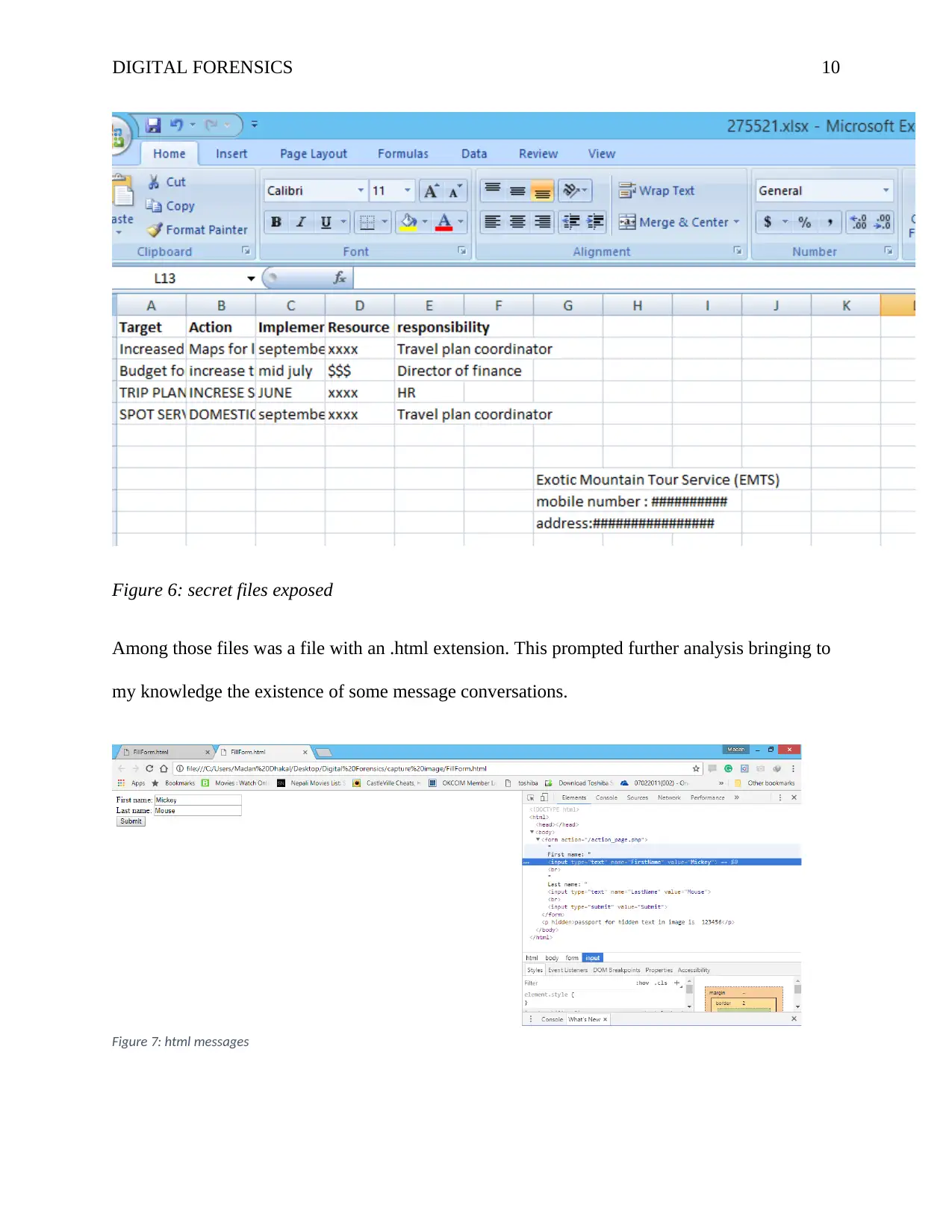
Figure 6: secret files exposed
Among those files was a file with an .html extension. This prompted further analysis bringing to
my knowledge the existence of some message conversations.
Figure 7: html messages
Figure 6: secret files exposed
Among those files was a file with an .html extension. This prompted further analysis bringing to
my knowledge the existence of some message conversations.
Figure 7: html messages
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
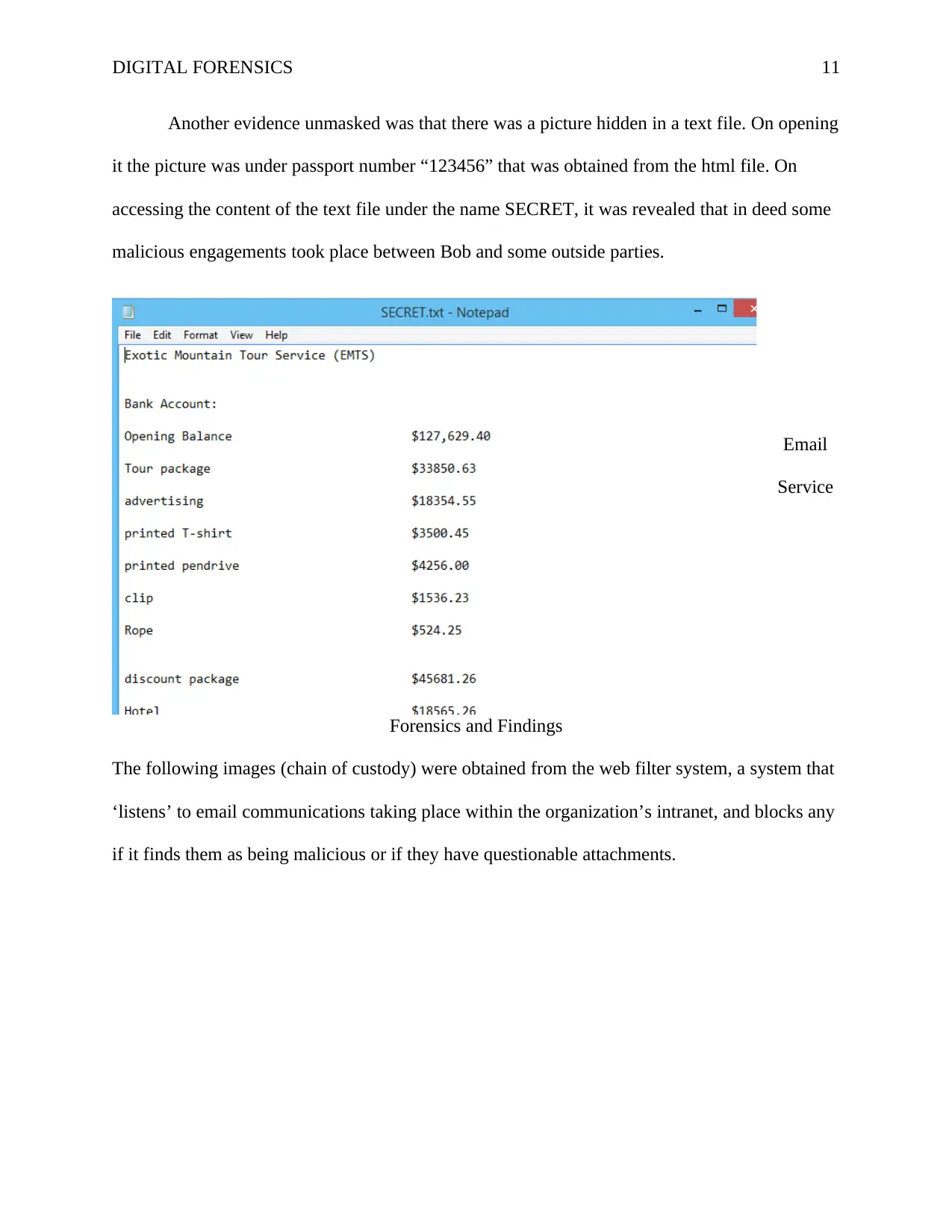
DIGITAL FORENSICS 11
Another evidence unmasked was that there was a picture hidden in a text file. On opening
it the picture was under passport number “123456” that was obtained from the html file. On
accessing the content of the text file under the name SECRET, it was revealed that in deed some
malicious engagements took place between Bob and some outside parties.
Email
Service
Forensics and Findings
The following images (chain of custody) were obtained from the web filter system, a system that
‘listens’ to email communications taking place within the organization’s intranet, and blocks any
if it finds them as being malicious or if they have questionable attachments.
Another evidence unmasked was that there was a picture hidden in a text file. On opening
it the picture was under passport number “123456” that was obtained from the html file. On
accessing the content of the text file under the name SECRET, it was revealed that in deed some
malicious engagements took place between Bob and some outside parties.
Service
Forensics and Findings
The following images (chain of custody) were obtained from the web filter system, a system that
‘listens’ to email communications taking place within the organization’s intranet, and blocks any
if it finds them as being malicious or if they have questionable attachments.

DIGITAL FORENSICS 12
Figure 8: first intercepted email
Figure 1: first intercepted capture of the email conversations
Figure 8: first intercepted email
Figure 1: first intercepted capture of the email conversations
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


