Analysis of Information Assurance Risk Report: Facebook
VerifiedAdded on 2023/01/06
|13
|528
|49
Report
AI Summary
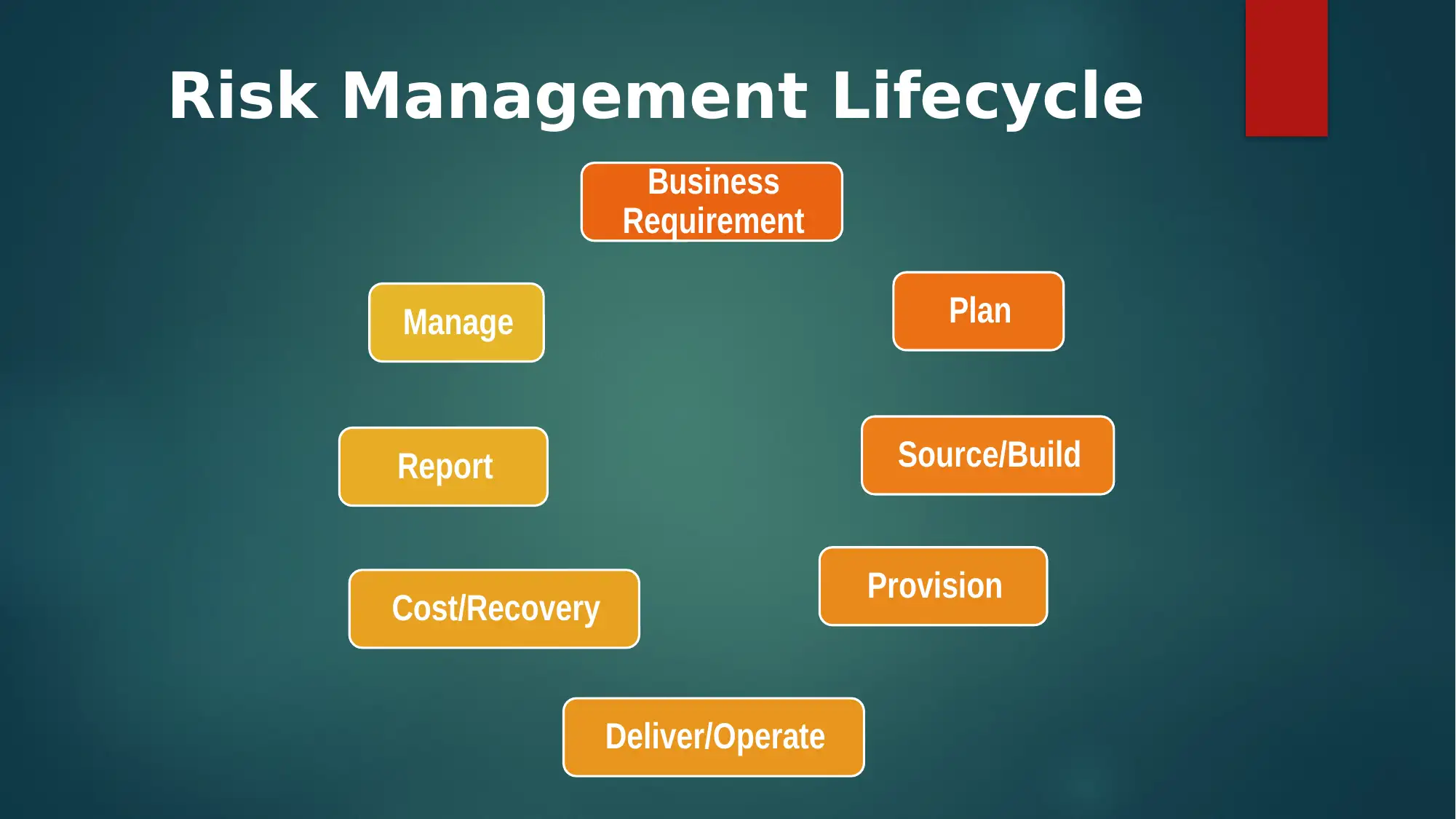
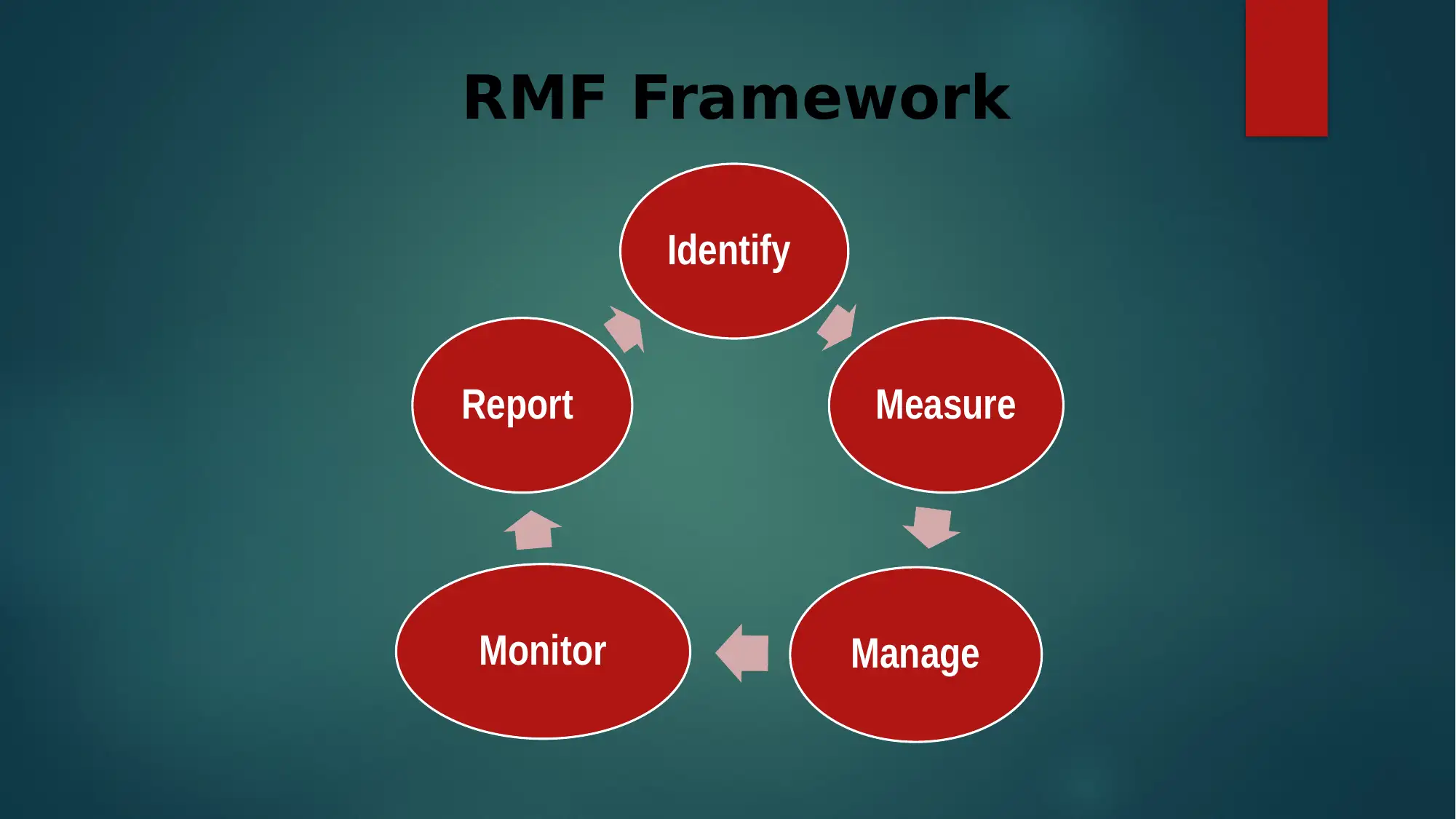
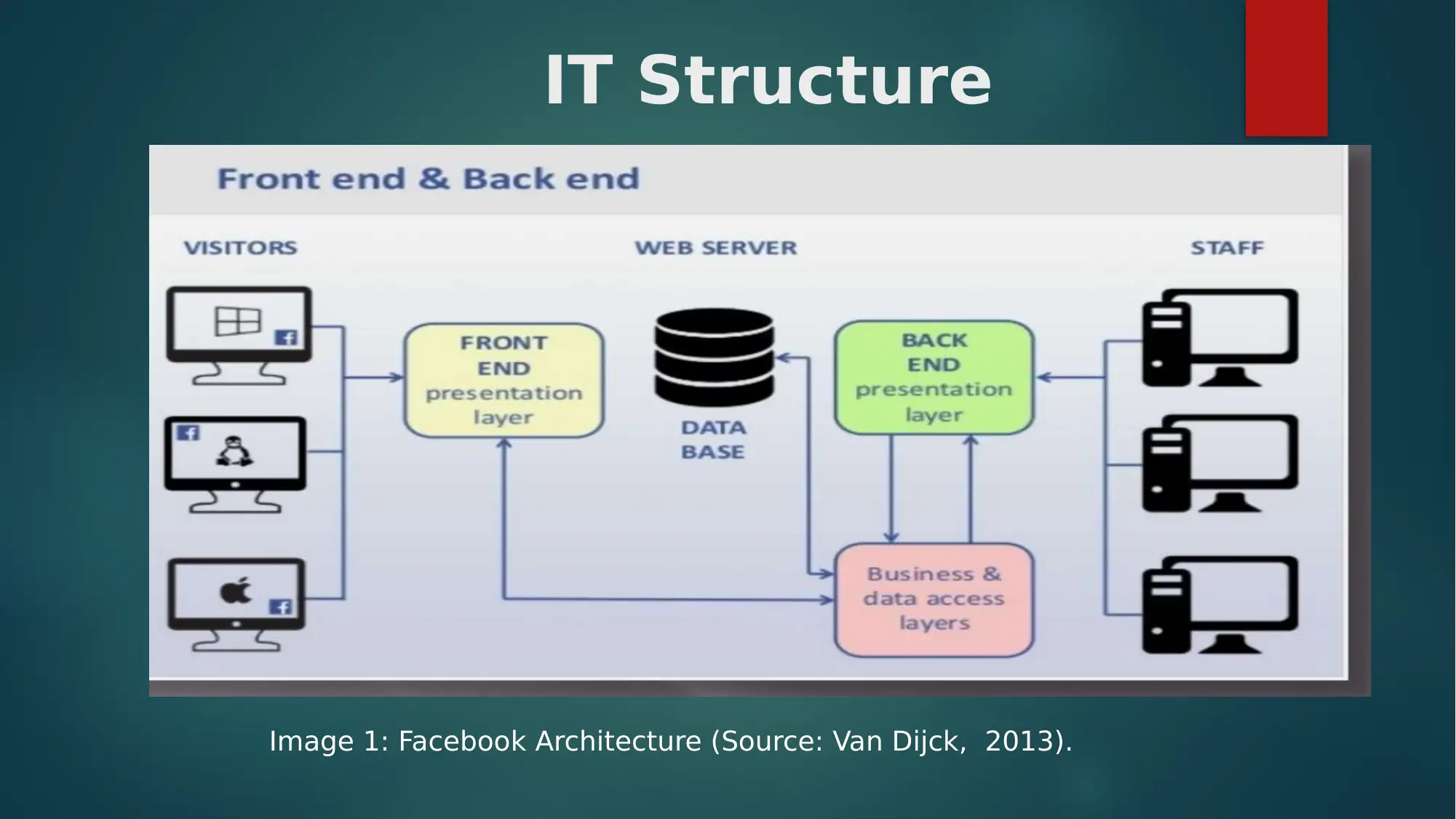
This report provides an overview of the information assurance risks associated with Facebook. It begins by outlining the context of Facebook, including its founding and core functions. The report identifies several key risks, such as third-party data sharing, privacy setting vulnerabilities, malware in advertisements, fake profiles, and the potential for hacking. It then details a risk management lifecycle, including planning, building, and operating phases. The report also lists methodologies, like classical system life cycle and data modelling, and outlines the RMF framework. It examines Facebook's policies regarding data collection, privacy, and content review, and suggests audit and testing schedules to mitigate risks. The report concludes by emphasizing the importance of proactive risk management in maintaining user trust and data security on the platform.
1 out of 13












![[object Object]](/_next/static/media/star-bottom.7253800d.svg)