Project: Strategies to Fight Future Data Thefts in MNCs (Amazon)
VerifiedAdded on 2020/05/16
|18
|3688
|36
Project
AI Summary
This project investigates the critical issue of data theft threatening multinational corporations, using Amazon as a case study. It explores the potential impacts of data breaches, including the loss of business data, market goodwill, and overall business revenue. The project outlines a comprehensive plan, the 'Future Data Protection' project, spanning six months and encompassing SWOT analysis, assessment of third-party security, identification of vulnerabilities, employee training, and the implementation of stringent security measures. It also highlights potential challenges, such as lack of historical data and customer non-cooperation, while emphasizing the project's anticipated outcomes: stronger data protection, prevention or minimization of data theft, and enhanced financial stability for Amazon. The study provides detailed recommendations, including strong passwords, employee training, and integration of central data theft detection, to mitigate future cyber threats and safeguard sensitive information.

Running head: PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Project to Fight Future Data Thefts in MNCs
Name of the Student:
Name of the University:
Author Note:
Project to Fight Future Data Thefts in MNCs
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Executive Summary:
The multinational companies all over the world are threatened by cyber threats and resultant
losses of data. The customers of these companies are also under threats because they often
use the digital portals to make online purchases and share confidential financial data. The
paper would delve into this serious threat with Amazon, the largest ecommerce company in
its background.
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Executive Summary:
The multinational companies all over the world are threatened by cyber threats and resultant
losses of data. The customers of these companies are also under threats because they often
use the digital portals to make online purchases and share confidential financial data. The
paper would delve into this serious threat with Amazon, the largest ecommerce company in
its background.

2
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Table of Contents
Introduction:...............................................................................................................................2
The issue the project would investigate:....................................................................................2
Outcome 1: Loss of business data:.........................................................................................3
Outcome 2: Loss of market goodwill:....................................................................................3
Outcome 3: Loss of business:................................................................................................4
The project plan:........................................................................................................................4
Methodology and the extent of its use in the project:................................................................7
Project highlights:......................................................................................................................7
Disappointments, setbacks and problems:.................................................................................8
Project outcomes:.......................................................................................................................8
Outcome 1: Stronger protection against data thefts:..............................................................9
Outcome 2: Prevention or at least minimisation of data theft:...............................................9
Outcome 3: Strengthen the financial position of Amazon:....................................................9
Recommendations:.....................................................................................................................9
Strong passwords:................................................................................................................10
Employee training:...............................................................................................................10
Integration of central data theft detection with host country:..............................................10
Interventions required:.............................................................................................................11
Conclusion:..............................................................................................................................11
References:...............................................................................................................................12
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Table of Contents
Introduction:...............................................................................................................................2
The issue the project would investigate:....................................................................................2
Outcome 1: Loss of business data:.........................................................................................3
Outcome 2: Loss of market goodwill:....................................................................................3
Outcome 3: Loss of business:................................................................................................4
The project plan:........................................................................................................................4
Methodology and the extent of its use in the project:................................................................7
Project highlights:......................................................................................................................7
Disappointments, setbacks and problems:.................................................................................8
Project outcomes:.......................................................................................................................8
Outcome 1: Stronger protection against data thefts:..............................................................9
Outcome 2: Prevention or at least minimisation of data theft:...............................................9
Outcome 3: Strengthen the financial position of Amazon:....................................................9
Recommendations:.....................................................................................................................9
Strong passwords:................................................................................................................10
Employee training:...............................................................................................................10
Integration of central data theft detection with host country:..............................................10
Interventions required:.............................................................................................................11
Conclusion:..............................................................................................................................11
References:...............................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Introduction:
Data theft is a serious issue in today’s world and is a great threat to data bases which
companies share with their customers. Hacking data by unauthorised identities can lead to
financial losses to companies and customers. The assignment would deal with this serious
threat with Amazon as a company of choice. The paper would first point out the issue and its
outcomes. Then it would go forward to recognise the outcomes of the project which Amazon
looks forward to gain (amazon.com, 2018). The study also contains recommendations for
Amazon regarding how it can deal with the serious issue.
The issue the project would investigate:
The project would investigate into the issue of data thefts encountered by
Amazon and its potential impacts on the company. Amazon faces threat from data hackers
due to several factors. The American multinational company is the largest internet retailer
and cloud computing services offering company in the world. The customer profile of the
company consists of government departments like defence and other multinational
corporations (Prasad & Haldar, 2015). Thus the data base of Amazon contains confidential
information of governments, multinational corporations, small enterprises and individual
customers, both rich and middle class. Hacking the data base would make huge amount of
financial information available to the illegal hackers (money.cnn.com, 2018). The company is
strengthening its internet security but the hackers are also advancing their hacking procedures
to break into the company’s confidential database. This threat is becoming even more severe
as the multinational company is expanding its business (Devdhar et al., 2016). This requires
Amazon to initiate a project to counteract the growing strength of the hackers. The following
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Introduction:
Data theft is a serious issue in today’s world and is a great threat to data bases which
companies share with their customers. Hacking data by unauthorised identities can lead to
financial losses to companies and customers. The assignment would deal with this serious
threat with Amazon as a company of choice. The paper would first point out the issue and its
outcomes. Then it would go forward to recognise the outcomes of the project which Amazon
looks forward to gain (amazon.com, 2018). The study also contains recommendations for
Amazon regarding how it can deal with the serious issue.
The issue the project would investigate:
The project would investigate into the issue of data thefts encountered by
Amazon and its potential impacts on the company. Amazon faces threat from data hackers
due to several factors. The American multinational company is the largest internet retailer
and cloud computing services offering company in the world. The customer profile of the
company consists of government departments like defence and other multinational
corporations (Prasad & Haldar, 2015). Thus the data base of Amazon contains confidential
information of governments, multinational corporations, small enterprises and individual
customers, both rich and middle class. Hacking the data base would make huge amount of
financial information available to the illegal hackers (money.cnn.com, 2018). The company is
strengthening its internet security but the hackers are also advancing their hacking procedures
to break into the company’s confidential database. This threat is becoming even more severe
as the multinational company is expanding its business (Devdhar et al., 2016). This requires
Amazon to initiate a project to counteract the growing strength of the hackers. The following
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
potential outcomes of the data thefts on the business of Amazon would shed light on the
seriousness of the issue and also pave way to project plan:
Outcome 1: Loss of business data:
Data theft would result in Amazon losing its confidential business data to illegal
entities which would put the future of the company in great risk. As pointed out the database
of Amazon is used by the users to store confidential business data including financial
information. This means that data theft would devastate the business of both Amazon and its
customers which include government departments and others MNCs as well (cutimes.com,
2018). The hackers are increasing their strength to attack the firewall and passwords which
Amazon uses to protect its data. This means that Amazon requires strengthening its security
to counteract these increasing security threats (Ablon et al., 2016).
Outcome 2: Loss of market goodwill:
Amazon offers secure electronic platform to billions of users to buy and sell products
which accounts for its market goodwill. Thousands of the multinational companies use the
cloud computing platforms Amazon provides to share, acquire and manage bulk of sensitive
business information. Thus, the strengthening security threats and resultant data theft would
lead to Amazon lose the trust of these individual and business customers. Amazon would
eventually lose these customers to its competitors. It would also lose its market goodwill and
top position it enjoys as the largest ecommerce company in the world (Jokar, Arianpoo &
Leung, 2016).
Outcome 3: Loss of business:
Data theft can cause loss of important business data and market goodwill which can
ultimately lead to business loss to Amazon. The main business of Amazon stems from
internet and ecommerce services to companies and individuals. As pointed out, data theft
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
potential outcomes of the data thefts on the business of Amazon would shed light on the
seriousness of the issue and also pave way to project plan:
Outcome 1: Loss of business data:
Data theft would result in Amazon losing its confidential business data to illegal
entities which would put the future of the company in great risk. As pointed out the database
of Amazon is used by the users to store confidential business data including financial
information. This means that data theft would devastate the business of both Amazon and its
customers which include government departments and others MNCs as well (cutimes.com,
2018). The hackers are increasing their strength to attack the firewall and passwords which
Amazon uses to protect its data. This means that Amazon requires strengthening its security
to counteract these increasing security threats (Ablon et al., 2016).
Outcome 2: Loss of market goodwill:
Amazon offers secure electronic platform to billions of users to buy and sell products
which accounts for its market goodwill. Thousands of the multinational companies use the
cloud computing platforms Amazon provides to share, acquire and manage bulk of sensitive
business information. Thus, the strengthening security threats and resultant data theft would
lead to Amazon lose the trust of these individual and business customers. Amazon would
eventually lose these customers to its competitors. It would also lose its market goodwill and
top position it enjoys as the largest ecommerce company in the world (Jokar, Arianpoo &
Leung, 2016).
Outcome 3: Loss of business:
Data theft can cause loss of important business data and market goodwill which can
ultimately lead to business loss to Amazon. The main business of Amazon stems from
internet and ecommerce services to companies and individuals. As pointed out, data theft
5
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
would result in these customers losing their data to illegal entities. These companies
consequently would shift to other companies which provide similar services. For example, as
far as cloud computing services are concerned, the users can shift to Microsoft Azure and
Google Cloud Platform (Ablon et al., 2016). The customers can shift to Alibaba and ebay to
buy goods online. This means that Amazon due to the increasing risk of data theft would lose
its customers to its competitors and which would reduce its revenue generation.
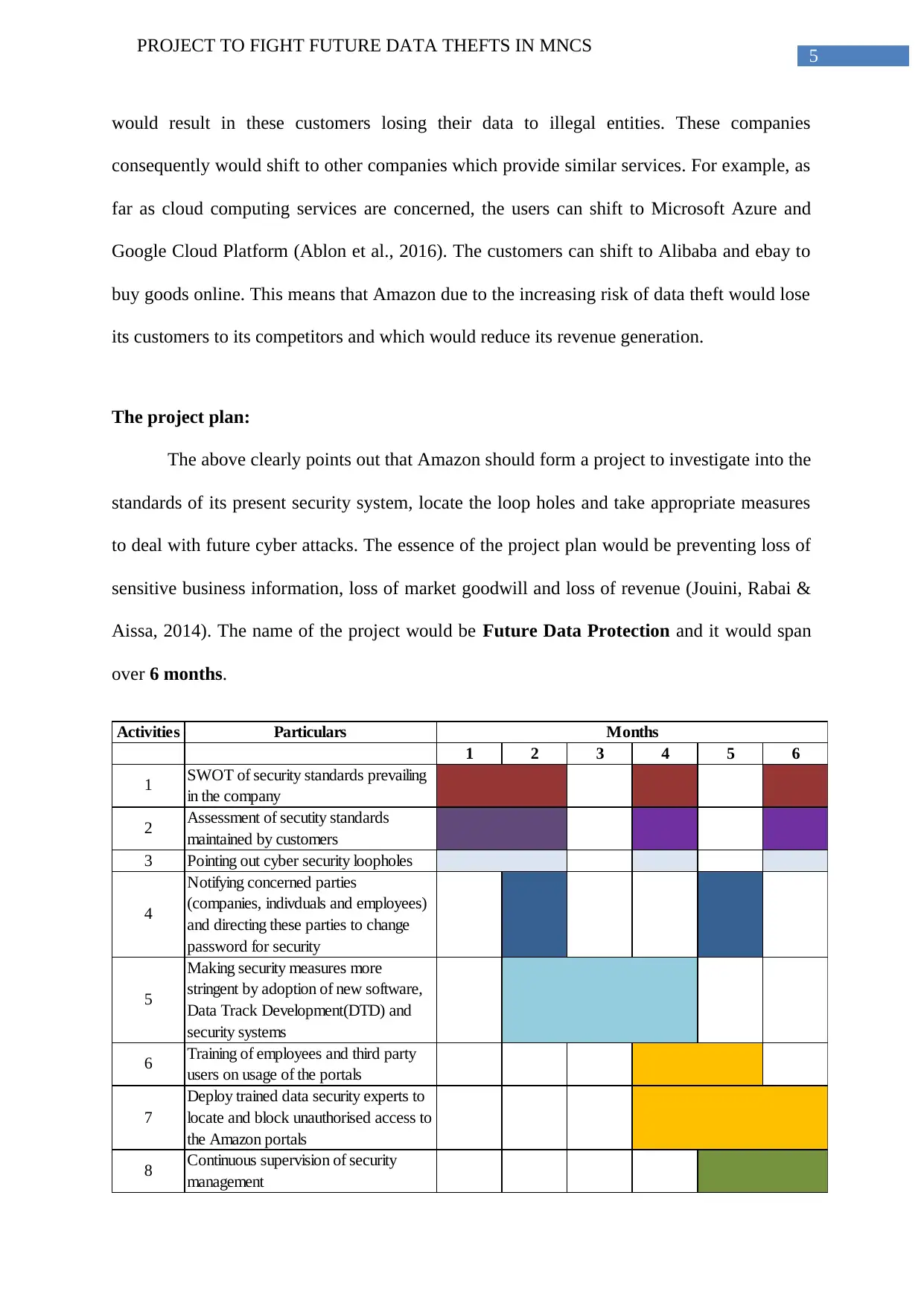
The project plan:
The above clearly points out that Amazon should form a project to investigate into the
standards of its present security system, locate the loop holes and take appropriate measures
to deal with future cyber attacks. The essence of the project plan would be preventing loss of
sensitive business information, loss of market goodwill and loss of revenue (Jouini, Rabai &
Aissa, 2014). The name of the project would be Future Data Protection and it would span
over 6 months.
Activities Particulars
1 2 3 4 5 6
1 SWOT of security standards prevailing
in the company
2 Assessment of secutity standards
maintained by customers
3 Pointing out cyber security loopholes
4
Notifying concerned parties
(companies, indivduals and employees)
and directing these parties to change
password for security
5
Making security measures more
stringent by adoption of new software,
Data Track Development(DTD) and
security systems
6 Training of employees and third party
users on usage of the portals
7
Deploy trained data security experts to
locate and block unauthorised access to
the Amazon portals
8 Continuous supervision of security
management
Months
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
would result in these customers losing their data to illegal entities. These companies
consequently would shift to other companies which provide similar services. For example, as
far as cloud computing services are concerned, the users can shift to Microsoft Azure and
Google Cloud Platform (Ablon et al., 2016). The customers can shift to Alibaba and ebay to
buy goods online. This means that Amazon due to the increasing risk of data theft would lose
its customers to its competitors and which would reduce its revenue generation.
The project plan:
The above clearly points out that Amazon should form a project to investigate into the
standards of its present security system, locate the loop holes and take appropriate measures
to deal with future cyber attacks. The essence of the project plan would be preventing loss of
sensitive business information, loss of market goodwill and loss of revenue (Jouini, Rabai &
Aissa, 2014). The name of the project would be Future Data Protection and it would span
over 6 months.
Activities Particulars
1 2 3 4 5 6
1 SWOT of security standards prevailing
in the company
2 Assessment of secutity standards
maintained by customers
3 Pointing out cyber security loopholes
4
Notifying concerned parties
(companies, indivduals and employees)
and directing these parties to change
password for security
5
Making security measures more
stringent by adoption of new software,
Data Track Development(DTD) and
security systems
6 Training of employees and third party
users on usage of the portals
7
Deploy trained data security experts to
locate and block unauthorised access to
the Amazon portals
8 Continuous supervision of security
management
Months
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Figure 1. Project plan for Future Data Protection
(Source: Author)
The above chart shows the plan for Future Data Protection which would aim to
prevent or at least minimise cyber threats and data thefts on the digital platforms of Amazon
(amazon.com, 2018). The following are detailed steps of the project:
Activity 1:
Amazon should conduct a SWOT analysis to locate the strengths, weaknesses,
opportunities and threats pertaining to its portals. This would include detecting the ways
employees use its portals to share information during the course of the business operations.
Amazon should conduct this assessment in the first two months and then resume it the fourth
and sixth month (Holtfreter et al., 2015).
Activity 2:
The second activity would consist of assessment of security standards maintained by
the third party users like the individual and corporate customers who use the portals of
Amazon. This activity should proceed simultaneously with activity 1 (Dalkir & Beaulieu,
2017). Amazon can involve customers and employees of to ensure that their activities can be
streamlined with the organisational goal of preventing data thefts and application of total
quality management (TQM).
Activity 3:
The third activity would be the outcome of the first two activities and would lead to
recognition of cyber security loop holes. The activity would proceed along with the first two
activities.
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Figure 1. Project plan for Future Data Protection
(Source: Author)
The above chart shows the plan for Future Data Protection which would aim to
prevent or at least minimise cyber threats and data thefts on the digital platforms of Amazon
(amazon.com, 2018). The following are detailed steps of the project:
Activity 1:
Amazon should conduct a SWOT analysis to locate the strengths, weaknesses,
opportunities and threats pertaining to its portals. This would include detecting the ways
employees use its portals to share information during the course of the business operations.
Amazon should conduct this assessment in the first two months and then resume it the fourth
and sixth month (Holtfreter et al., 2015).
Activity 2:
The second activity would consist of assessment of security standards maintained by
the third party users like the individual and corporate customers who use the portals of
Amazon. This activity should proceed simultaneously with activity 1 (Dalkir & Beaulieu,
2017). Amazon can involve customers and employees of to ensure that their activities can be
streamlined with the organisational goal of preventing data thefts and application of total
quality management (TQM).
Activity 3:
The third activity would be the outcome of the first two activities and would lead to
recognition of cyber security loop holes. The activity would proceed along with the first two
activities.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Activity 4:
Amazon should notify the concerned parties including employees, corporate
customers, governments and individual customers about the threats detected in their user
portals. The company should direct these parties to reset their passwords to check any further
unauthorised access into their portals (Power, Sharda & Burstein, 2015).
Activity 5:
The multinational company should make security measures more stringent and make
passwords stronger. Any unauthorised attempts to enter portal should be blocked. The data
usage should be combined with strategic human resource management (SHRM) to ensure
that the staffs of Amazon also contribute towards data theft check project.
Activity 6:
The next step which Amazon can take is to train its employees because they form
significant part of the business strategies of the company. The third party users should also be
trained to the usage of portals. The multinational company should train the parties regarding
usage of passwords while using its portal to make online purchases (Laudon & Laudon,
2016). Thus the company should combine SHRM and customer training to minimise
unauthorised entry into its portals and loss of confidential data like financial data.
Activity 7:
Amazon should deploy trained security experts to locate and block unauthorised
attempts to break the firewall and security checks of Amazon. Those experts would also be
responsible for blocking authorised entries into its portals. Thus, here again Amazon can use
SHRM to strengthen its portals and digital platforms.
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Activity 4:
Amazon should notify the concerned parties including employees, corporate
customers, governments and individual customers about the threats detected in their user
portals. The company should direct these parties to reset their passwords to check any further
unauthorised access into their portals (Power, Sharda & Burstein, 2015).
Activity 5:
The multinational company should make security measures more stringent and make
passwords stronger. Any unauthorised attempts to enter portal should be blocked. The data
usage should be combined with strategic human resource management (SHRM) to ensure
that the staffs of Amazon also contribute towards data theft check project.
Activity 6:
The next step which Amazon can take is to train its employees because they form
significant part of the business strategies of the company. The third party users should also be
trained to the usage of portals. The multinational company should train the parties regarding
usage of passwords while using its portal to make online purchases (Laudon & Laudon,
2016). Thus the company should combine SHRM and customer training to minimise
unauthorised entry into its portals and loss of confidential data like financial data.
Activity 7:
Amazon should deploy trained security experts to locate and block unauthorised
attempts to break the firewall and security checks of Amazon. Those experts would also be
responsible for blocking authorised entries into its portals. Thus, here again Amazon can use
SHRM to strengthen its portals and digital platforms.

8
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Activity 8:
Amazon should keep a strict vigil on the usage of its portals. The security protocols
and other systems should be changed from time to time to confuse the hackers.
Methodology and the extent of its use in the project:
The project experts should combine quantitative, qualitative and a combination of
both to gain information about the project. One can reflect that in order to gain information
regarding the technological advancements in the market, the company should use quantitative
methods (Zhou, Fu & Yang, 2016). Again while gaining historical information about data
thefts in the past years in Amazon or in any other ecommerce or IT companies, the company
can use qualitative data. The company can use quantitative and qualitative methods to obtain
data on the losses it has suffered to due to data thefts. This shows that the company should
use quantitative, qualitative and mixed methods to gain information about the project.
Project highlights:
The highlights of the project are as follows:
Activity1: SWOT of the security standards prevailing in the company.
Activity 2: Assessment of security standards maintained by customers both individual and
corporate customers.
Activity 3: Pointing out cyber security loopholes.
Activity 4: Notifying concerned parties about the increasing security threats and directing
them to change password for security.
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Activity 8:
Amazon should keep a strict vigil on the usage of its portals. The security protocols
and other systems should be changed from time to time to confuse the hackers.
Methodology and the extent of its use in the project:
The project experts should combine quantitative, qualitative and a combination of
both to gain information about the project. One can reflect that in order to gain information
regarding the technological advancements in the market, the company should use quantitative
methods (Zhou, Fu & Yang, 2016). Again while gaining historical information about data
thefts in the past years in Amazon or in any other ecommerce or IT companies, the company
can use qualitative data. The company can use quantitative and qualitative methods to obtain
data on the losses it has suffered to due to data thefts. This shows that the company should
use quantitative, qualitative and mixed methods to gain information about the project.
Project highlights:
The highlights of the project are as follows:
Activity1: SWOT of the security standards prevailing in the company.
Activity 2: Assessment of security standards maintained by customers both individual and
corporate customers.
Activity 3: Pointing out cyber security loopholes.
Activity 4: Notifying concerned parties about the increasing security threats and directing
them to change password for security.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Activity 5: Making security measures more stringent by adopting new methods of tracking
internet frauds.
Activity 6: Training of employees and third parties to make them aware about using portals.
Activity 7: Employ trained personnel to check data security experts to locate and block
unauthorised access.
Activity 8: Continuous supervision of security management.
Disappointments, setbacks and problems:
The disappointments that researchers would face are that all the corporate clients and
individual customers may not cooperate with the company. Moreover, some may view the
stringent security measures of the company as an invasion into their own data spaces. They as
a result may change to the other ecommerce companies like ebay. (Henisz, Dorobantu &
Nartey, 2014). The problems which Amazon may face are lack of historical data and
difficultly of access to data theft information which would prove to be a major setback for the
project. (Zhou, Fu & Yang, 2016).
Project outcomes:
Outcome 1: Future Data Protection and stronger protection against data thefts:
The project would provide stronger protection against data theft and loss of
potentially important data. This would save the company from losing confidential data of
clients and their trusts. Thus it would help Amazon to deal with the second issue, loss of
market goodwill (Holtfreter et al., 2015). The company can achieve this by using the
technological power of the company ( outcome of the SWOT analysis).
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Activity 5: Making security measures more stringent by adopting new methods of tracking
internet frauds.
Activity 6: Training of employees and third parties to make them aware about using portals.
Activity 7: Employ trained personnel to check data security experts to locate and block
unauthorised access.
Activity 8: Continuous supervision of security management.
Disappointments, setbacks and problems:
The disappointments that researchers would face are that all the corporate clients and
individual customers may not cooperate with the company. Moreover, some may view the
stringent security measures of the company as an invasion into their own data spaces. They as
a result may change to the other ecommerce companies like ebay. (Henisz, Dorobantu &
Nartey, 2014). The problems which Amazon may face are lack of historical data and
difficultly of access to data theft information which would prove to be a major setback for the
project. (Zhou, Fu & Yang, 2016).
Project outcomes:
Outcome 1: Future Data Protection and stronger protection against data thefts:
The project would provide stronger protection against data theft and loss of
potentially important data. This would save the company from losing confidential data of
clients and their trusts. Thus it would help Amazon to deal with the second issue, loss of
market goodwill (Holtfreter et al., 2015). The company can achieve this by using the
technological power of the company ( outcome of the SWOT analysis).
11
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Outcome 2: Prevention or at least minimisation of data theft:
The strengthening of the data protection would prevent the company from losing its
potentially important data due to invasion by unauthorised hackers. This would in turn
prevent loss of financially important data and help Amazon deal with the third issue, loss of
business due to loss of data (Power, Sharda & Burstein, 2015).
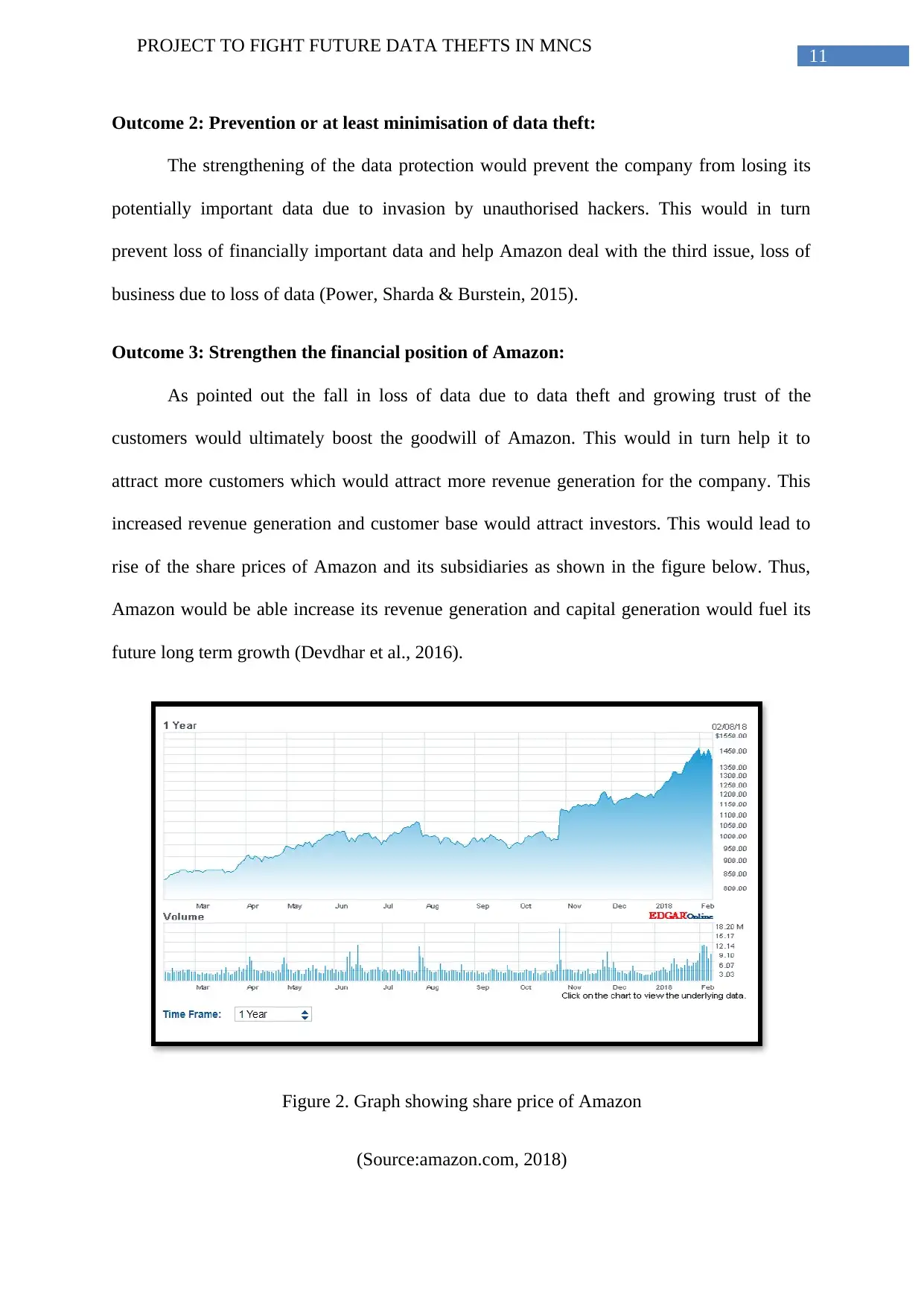
Outcome 3: Strengthen the financial position of Amazon:
As pointed out the fall in loss of data due to data theft and growing trust of the
customers would ultimately boost the goodwill of Amazon. This would in turn help it to
attract more customers which would attract more revenue generation for the company. This
increased revenue generation and customer base would attract investors. This would lead to
rise of the share prices of Amazon and its subsidiaries as shown in the figure below. Thus,
Amazon would be able increase its revenue generation and capital generation would fuel its
future long term growth (Devdhar et al., 2016).
Figure 2. Graph showing share price of Amazon
(Source:amazon.com, 2018)
PROJECT TO FIGHT FUTURE DATA THEFTS IN MNCS
Outcome 2: Prevention or at least minimisation of data theft:
The strengthening of the data protection would prevent the company from losing its
potentially important data due to invasion by unauthorised hackers. This would in turn
prevent loss of financially important data and help Amazon deal with the third issue, loss of
business due to loss of data (Power, Sharda & Burstein, 2015).
Outcome 3: Strengthen the financial position of Amazon:
As pointed out the fall in loss of data due to data theft and growing trust of the
customers would ultimately boost the goodwill of Amazon. This would in turn help it to
attract more customers which would attract more revenue generation for the company. This
increased revenue generation and customer base would attract investors. This would lead to
rise of the share prices of Amazon and its subsidiaries as shown in the figure below. Thus,
Amazon would be able increase its revenue generation and capital generation would fuel its
future long term growth (Devdhar et al., 2016).
Figure 2. Graph showing share price of Amazon
(Source:amazon.com, 2018)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




