CS213 W6 Lab 2: File Permissions and Event Viewer Report
VerifiedAdded on 2022/10/04
|11
|1177
|16
Homework Assignment
AI Summary
This assignment solution addresses file permissions and event viewer concepts in both Linux and Windows environments. Part A focuses on file permissions, including identifying files with specific access rights (read, write, execute) for owners, groups, and others, utilizing commands like 'find' and 'ls'. It explores user creation, ownership changes, and access control in both operating systems. Part B delves into the Windows Event Viewer, demonstrating how to find error logs, identify the applications causing errors, and filter for specific event types like system uptime messages. The solution includes commands, screenshots, and explanations to illustrate the concepts. The assignment also includes a bibliography of relevant research papers.

Running head: FILE PERMISSIONS AND EVENT VIEWER
File Permissions and Event Viewer
Name of the Student
Name of the University
Author Note
File Permissions and Event Viewer
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1FILE PERMISSIONS AND EVENT VIEWER
Part A: File Permissions
1. What files and directories in your Linux home directory can you (the owner)
read and write but your group and everyone else can read-only. How many such
files are there? What Linux command or pipe could you use?
Linux Ubuntu operating system is set up in Oracle VM VirtualBox
Part A: File Permissions
1. What files and directories in your Linux home directory can you (the owner)
read and write but your group and everyone else can read-only. How many such
files are there? What Linux command or pipe could you use?
Linux Ubuntu operating system is set up in Oracle VM VirtualBox
2FILE PERMISSIONS AND EVENT VIEWER
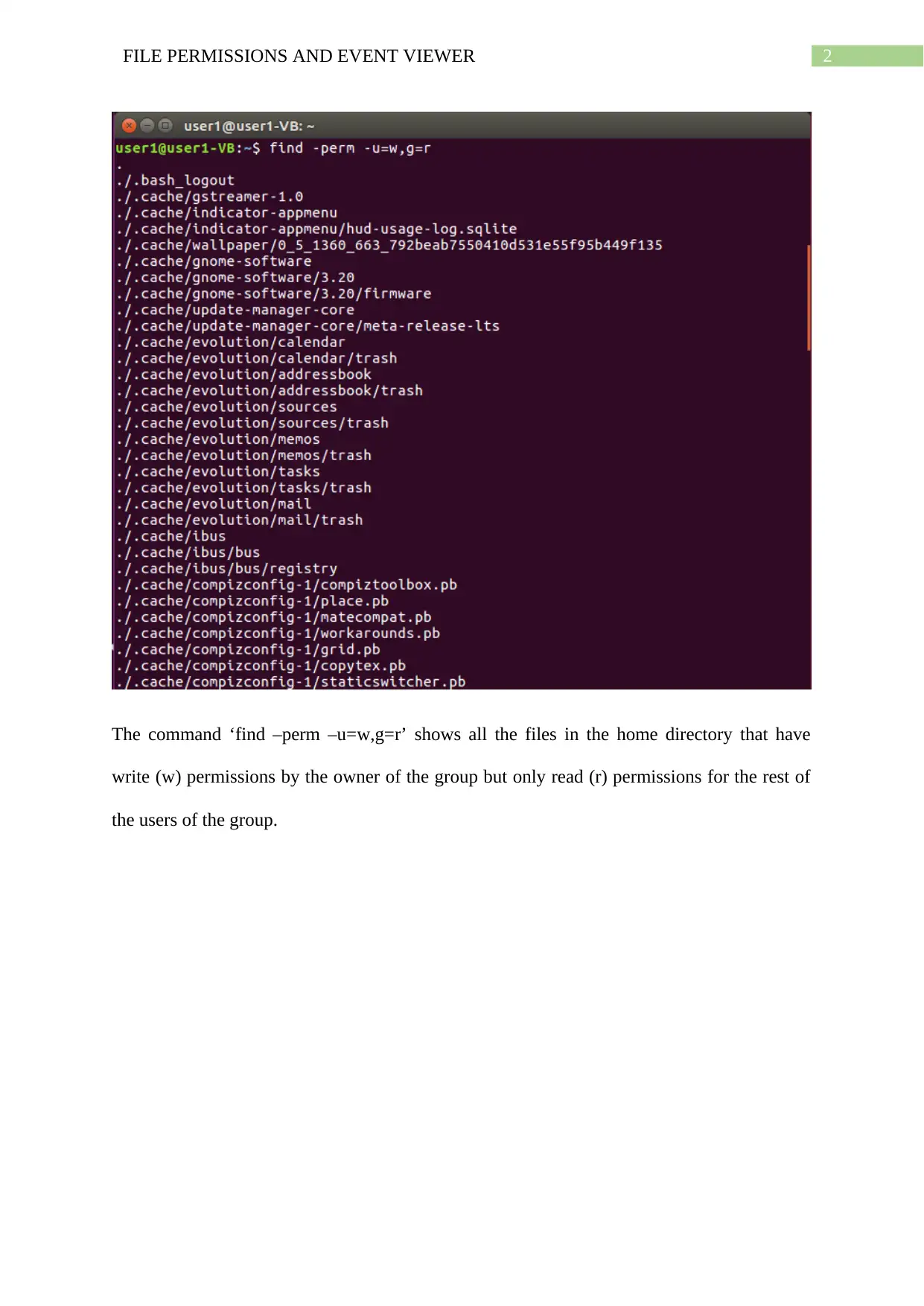
The command ‘find –perm –u=w,g=r’ shows all the files in the home directory that have
write (w) permissions by the owner of the group but only read (r) permissions for the rest of
the users of the group.
The command ‘find –perm –u=w,g=r’ shows all the files in the home directory that have
write (w) permissions by the owner of the group but only read (r) permissions for the rest of
the users of the group.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3FILE PERMISSIONS AND EVENT VIEWER
2. Find all files and directories on Linux that an owner can read and write, the
group can read-only, and everyone else is denied access. How many such files are
there? What Linux command or pipe could you use?
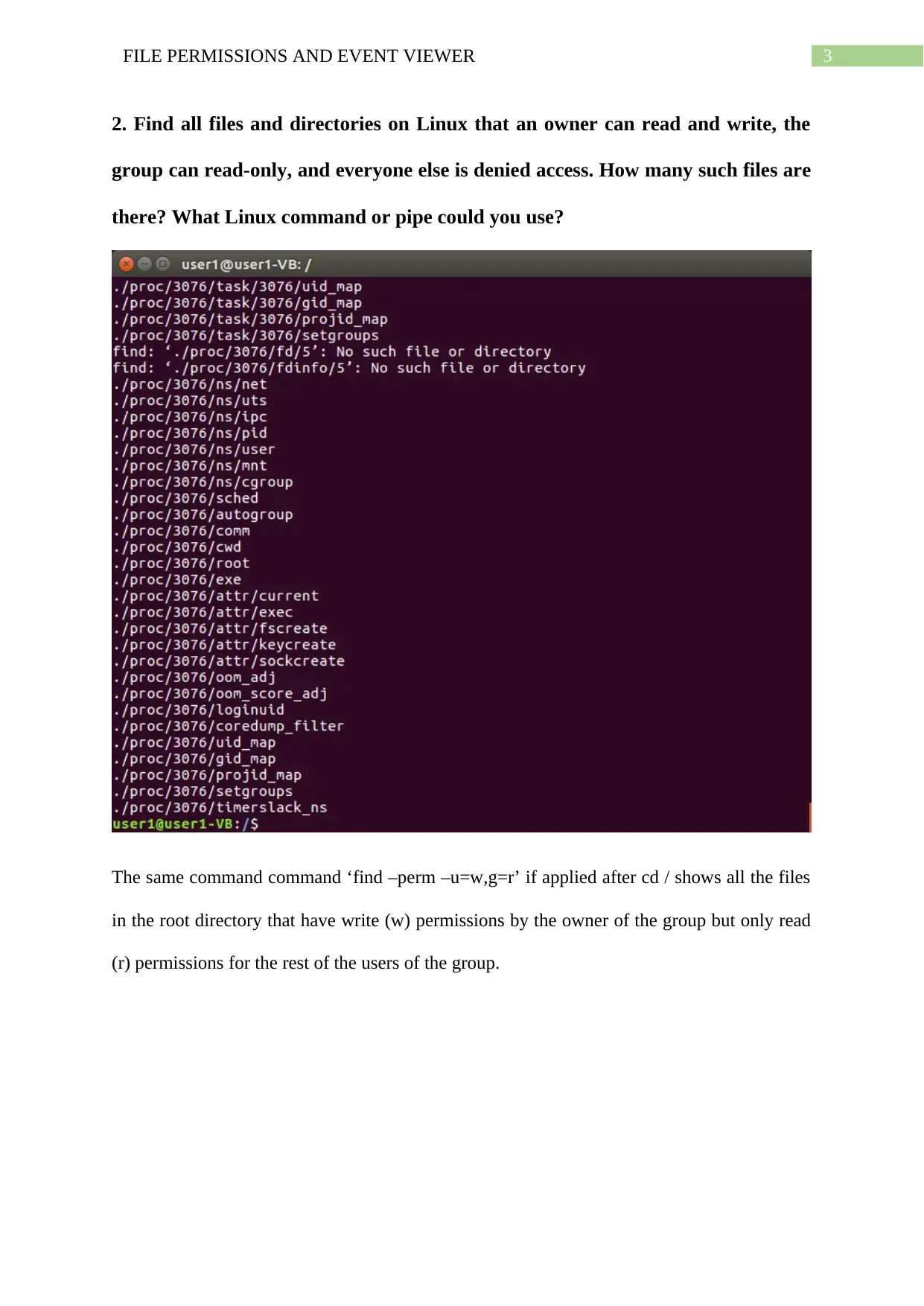
The same command command ‘find –perm –u=w,g=r’ if applied after cd / shows all the files
in the root directory that have write (w) permissions by the owner of the group but only read
(r) permissions for the rest of the users of the group.
2. Find all files and directories on Linux that an owner can read and write, the
group can read-only, and everyone else is denied access. How many such files are
there? What Linux command or pipe could you use?
The same command command ‘find –perm –u=w,g=r’ if applied after cd / shows all the files
in the root directory that have write (w) permissions by the owner of the group but only read
(r) permissions for the rest of the users of the group.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4FILE PERMISSIONS AND EVENT VIEWER
Create another Linux user and make him the owner of one of your files. What
Linux command or pipe could you use?
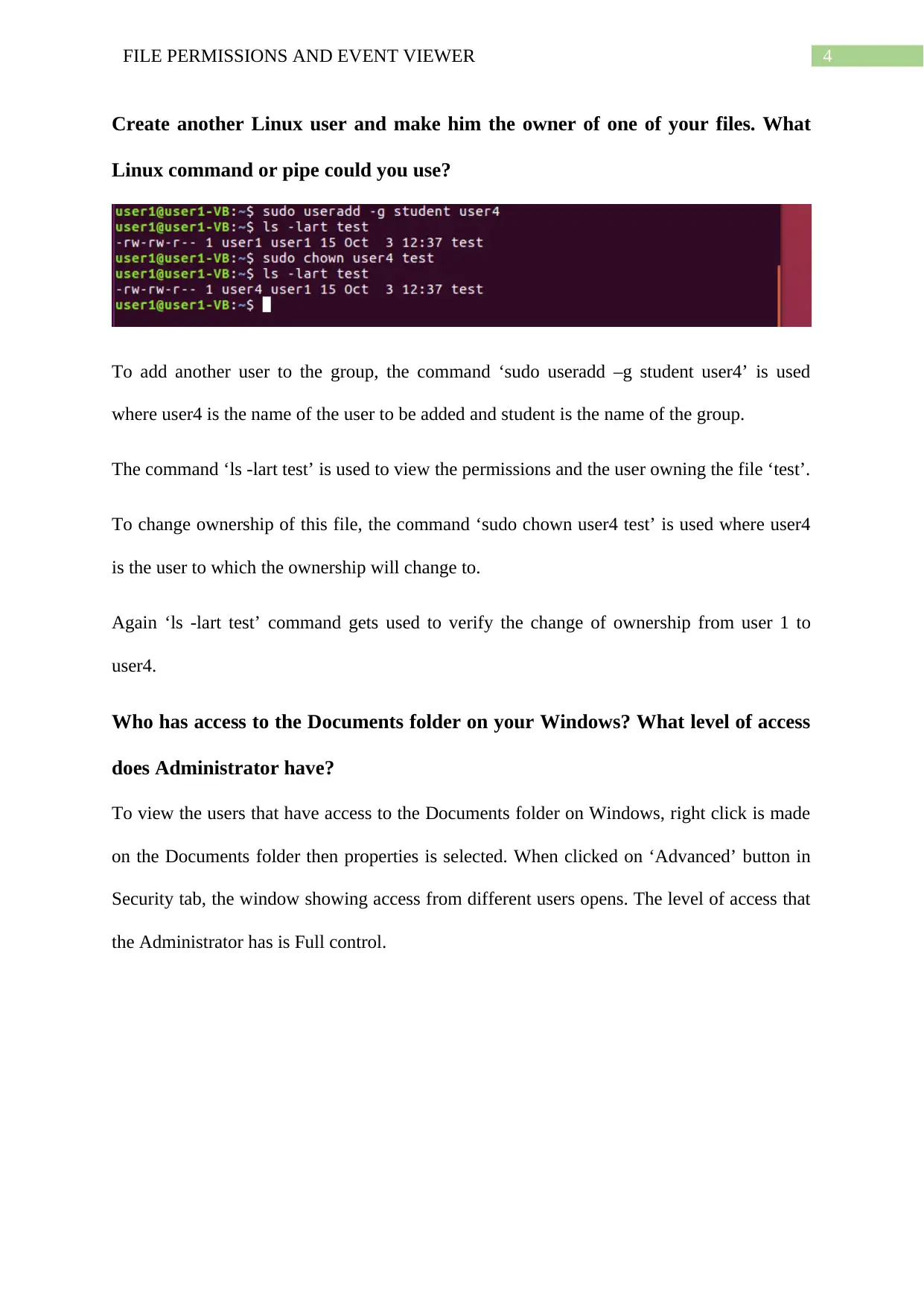
To add another user to the group, the command ‘sudo useradd –g student user4’ is used
where user4 is the name of the user to be added and student is the name of the group.
The command ‘ls -lart test’ is used to view the permissions and the user owning the file ‘test’.
To change ownership of this file, the command ‘sudo chown user4 test’ is used where user4
is the user to which the ownership will change to.
Again ‘ls -lart test’ command gets used to verify the change of ownership from user 1 to
user4.
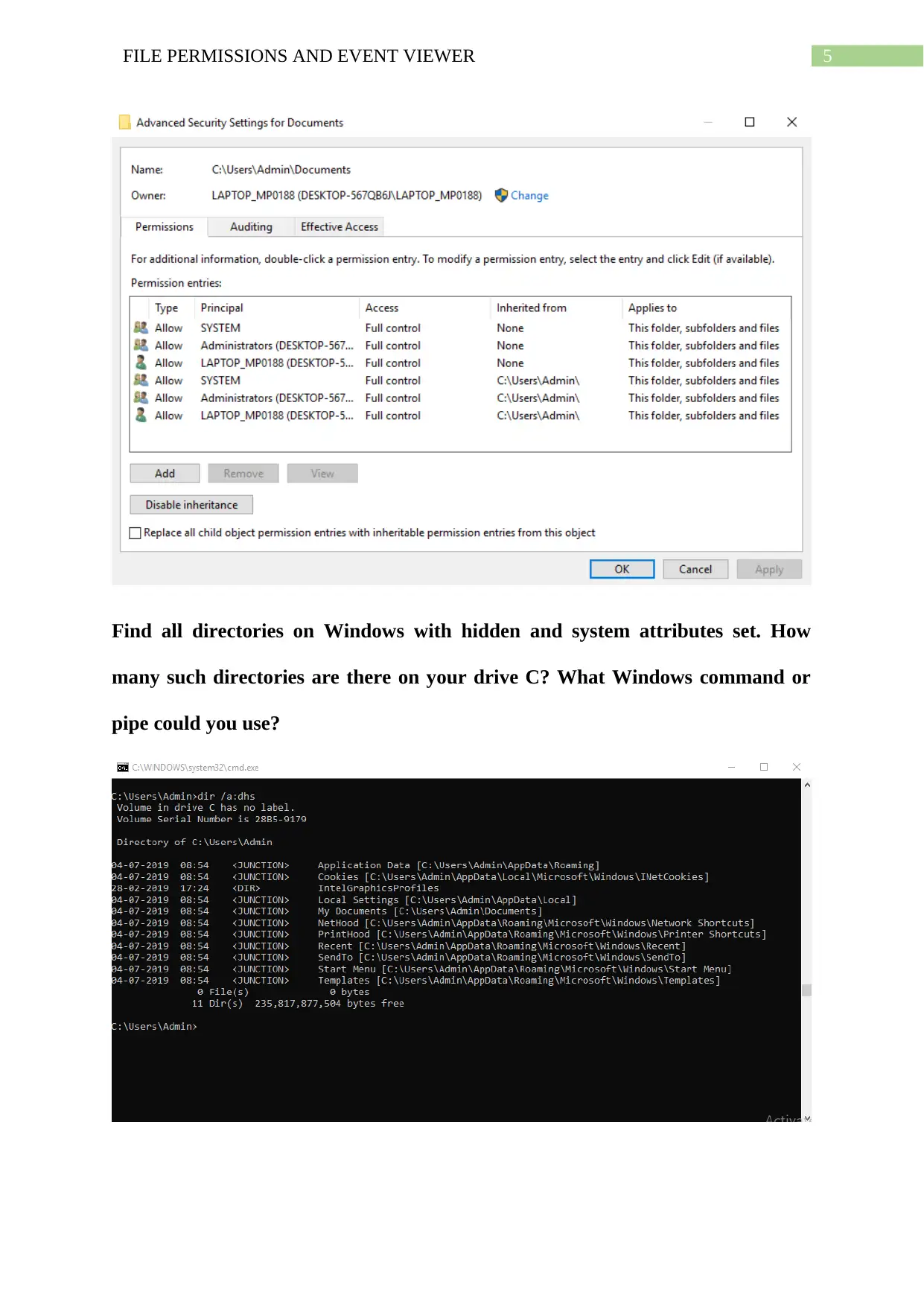
Who has access to the Documents folder on your Windows? What level of access
does Administrator have?
To view the users that have access to the Documents folder on Windows, right click is made
on the Documents folder then properties is selected. When clicked on ‘Advanced’ button in
Security tab, the window showing access from different users opens. The level of access that
the Administrator has is Full control.
Create another Linux user and make him the owner of one of your files. What
Linux command or pipe could you use?
To add another user to the group, the command ‘sudo useradd –g student user4’ is used
where user4 is the name of the user to be added and student is the name of the group.
The command ‘ls -lart test’ is used to view the permissions and the user owning the file ‘test’.
To change ownership of this file, the command ‘sudo chown user4 test’ is used where user4
is the user to which the ownership will change to.
Again ‘ls -lart test’ command gets used to verify the change of ownership from user 1 to
user4.
Who has access to the Documents folder on your Windows? What level of access
does Administrator have?
To view the users that have access to the Documents folder on Windows, right click is made
on the Documents folder then properties is selected. When clicked on ‘Advanced’ button in
Security tab, the window showing access from different users opens. The level of access that
the Administrator has is Full control.
5FILE PERMISSIONS AND EVENT VIEWER
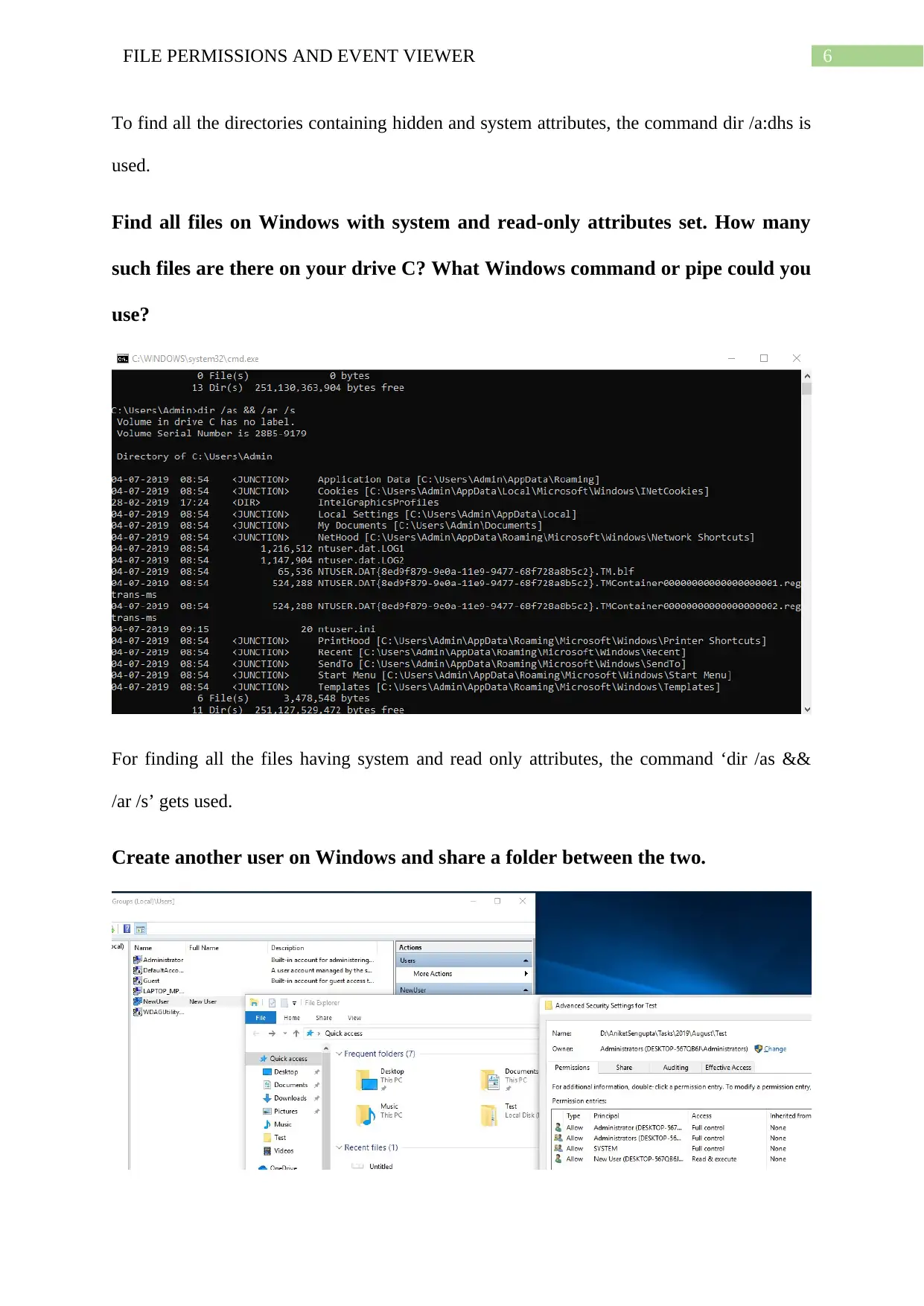
Find all directories on Windows with hidden and system attributes set. How
many such directories are there on your drive C? What Windows command or
pipe could you use?
Find all directories on Windows with hidden and system attributes set. How
many such directories are there on your drive C? What Windows command or
pipe could you use?
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6FILE PERMISSIONS AND EVENT VIEWER
To find all the directories containing hidden and system attributes, the command dir /a:dhs is
used.
Find all files on Windows with system and read-only attributes set. How many
such files are there on your drive C? What Windows command or pipe could you
use?
For finding all the files having system and read only attributes, the command ‘dir /as &&
/ar /s’ gets used.
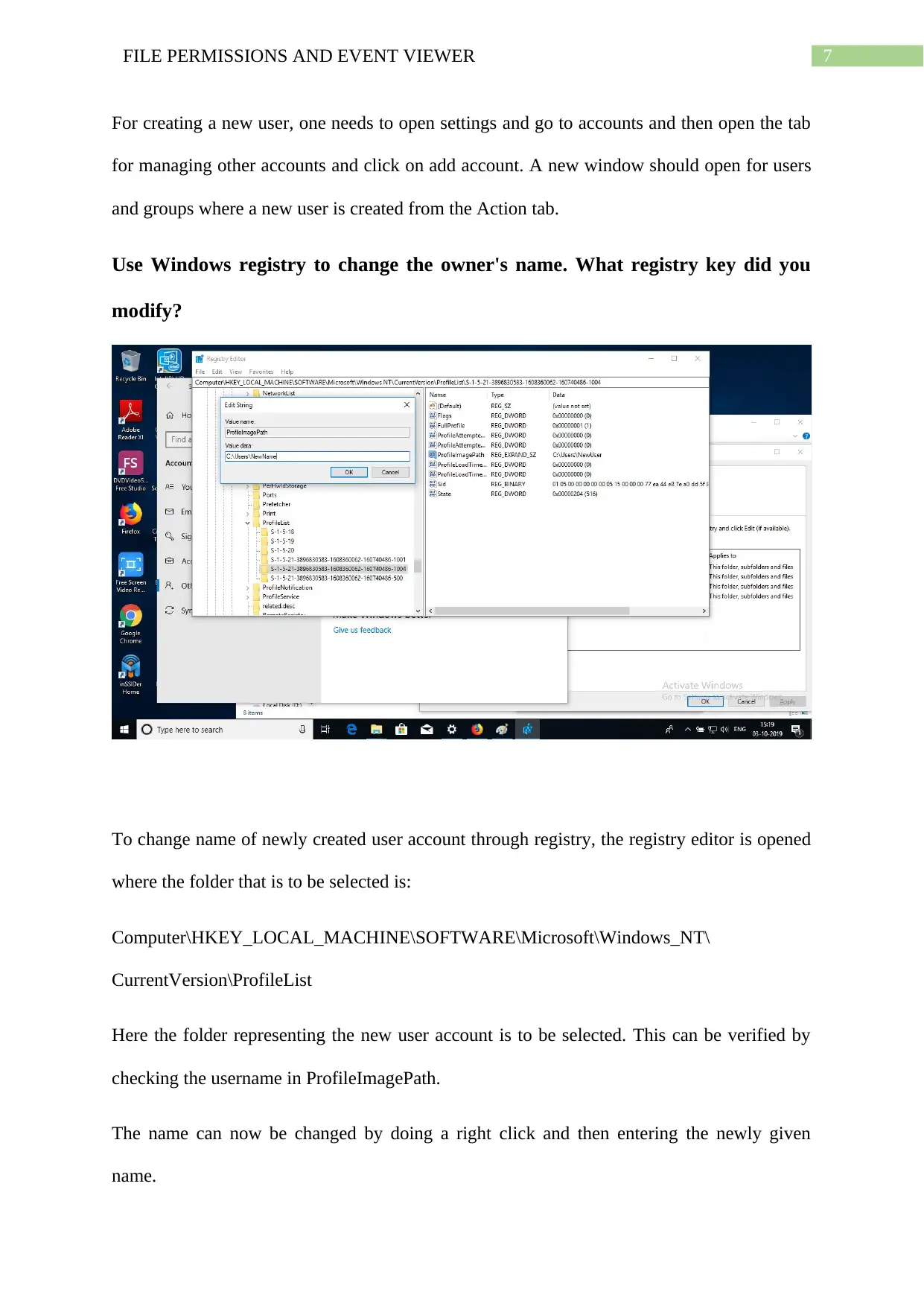
Create another user on Windows and share a folder between the two.
To find all the directories containing hidden and system attributes, the command dir /a:dhs is
used.
Find all files on Windows with system and read-only attributes set. How many
such files are there on your drive C? What Windows command or pipe could you
use?
For finding all the files having system and read only attributes, the command ‘dir /as &&
/ar /s’ gets used.
Create another user on Windows and share a folder between the two.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7FILE PERMISSIONS AND EVENT VIEWER
For creating a new user, one needs to open settings and go to accounts and then open the tab
for managing other accounts and click on add account. A new window should open for users
and groups where a new user is created from the Action tab.
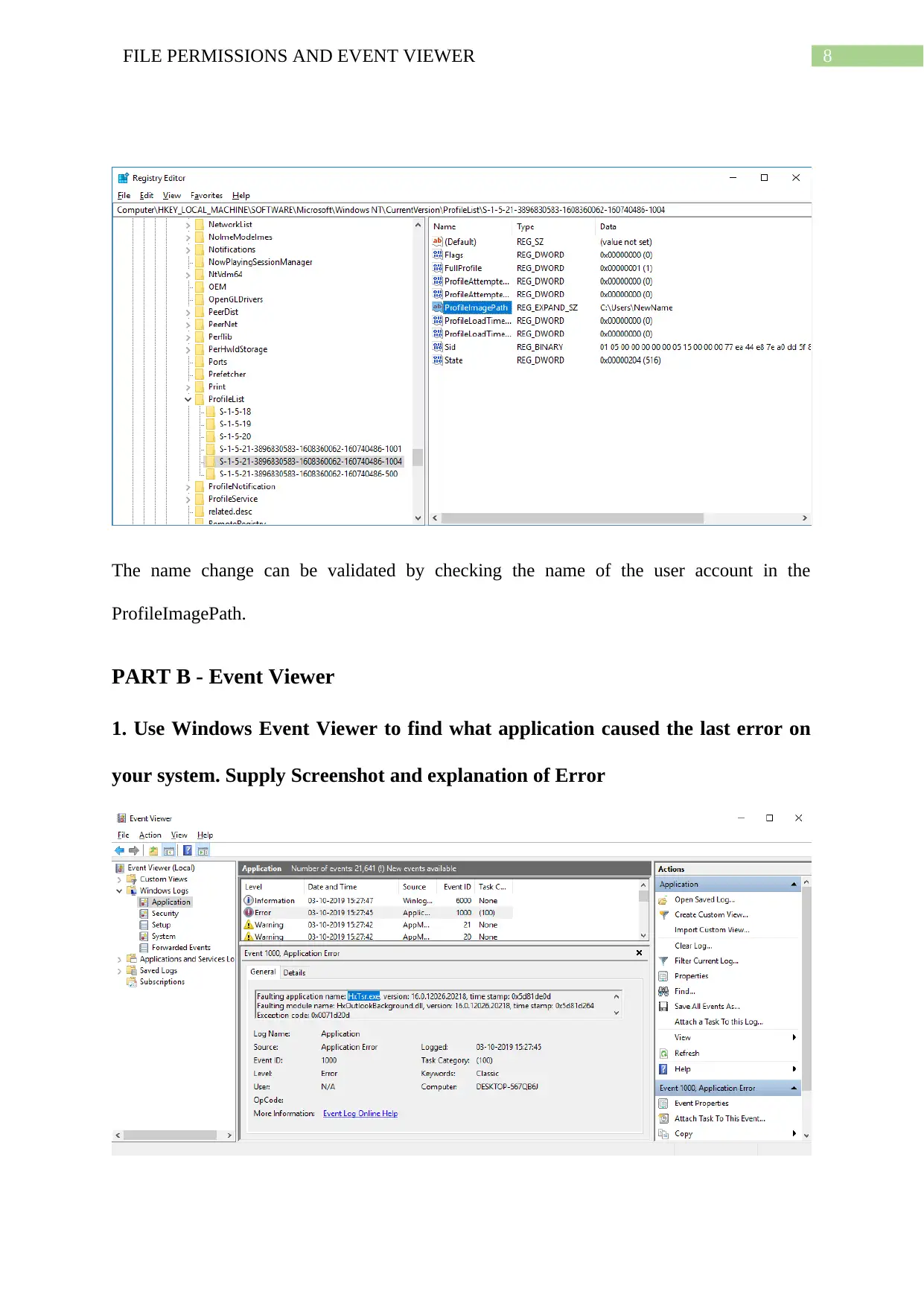
Use Windows registry to change the owner's name. What registry key did you
modify?
To change name of newly created user account through registry, the registry editor is opened
where the folder that is to be selected is:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows_NT\
CurrentVersion\ProfileList
Here the folder representing the new user account is to be selected. This can be verified by
checking the username in ProfileImagePath.
The name can now be changed by doing a right click and then entering the newly given
name.
For creating a new user, one needs to open settings and go to accounts and then open the tab
for managing other accounts and click on add account. A new window should open for users
and groups where a new user is created from the Action tab.
Use Windows registry to change the owner's name. What registry key did you
modify?
To change name of newly created user account through registry, the registry editor is opened
where the folder that is to be selected is:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows_NT\
CurrentVersion\ProfileList
Here the folder representing the new user account is to be selected. This can be verified by
checking the username in ProfileImagePath.
The name can now be changed by doing a right click and then entering the newly given
name.
8FILE PERMISSIONS AND EVENT VIEWER
The name change can be validated by checking the name of the user account in the
ProfileImagePath.
PART B - Event Viewer
1. Use Windows Event Viewer to find what application caused the last error on
your system. Supply Screenshot and explanation of Error
The name change can be validated by checking the name of the user account in the
ProfileImagePath.
PART B - Event Viewer
1. Use Windows Event Viewer to find what application caused the last error on
your system. Supply Screenshot and explanation of Error
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9FILE PERMISSIONS AND EVENT VIEWER
To view the application that has caused the last error, the event viewer is opened and
Application tab is selected from Windows Logs. It is found that the last known error has been
caused by an application by the name HxTsr.exe and the time of the error is found to be
15:27:45
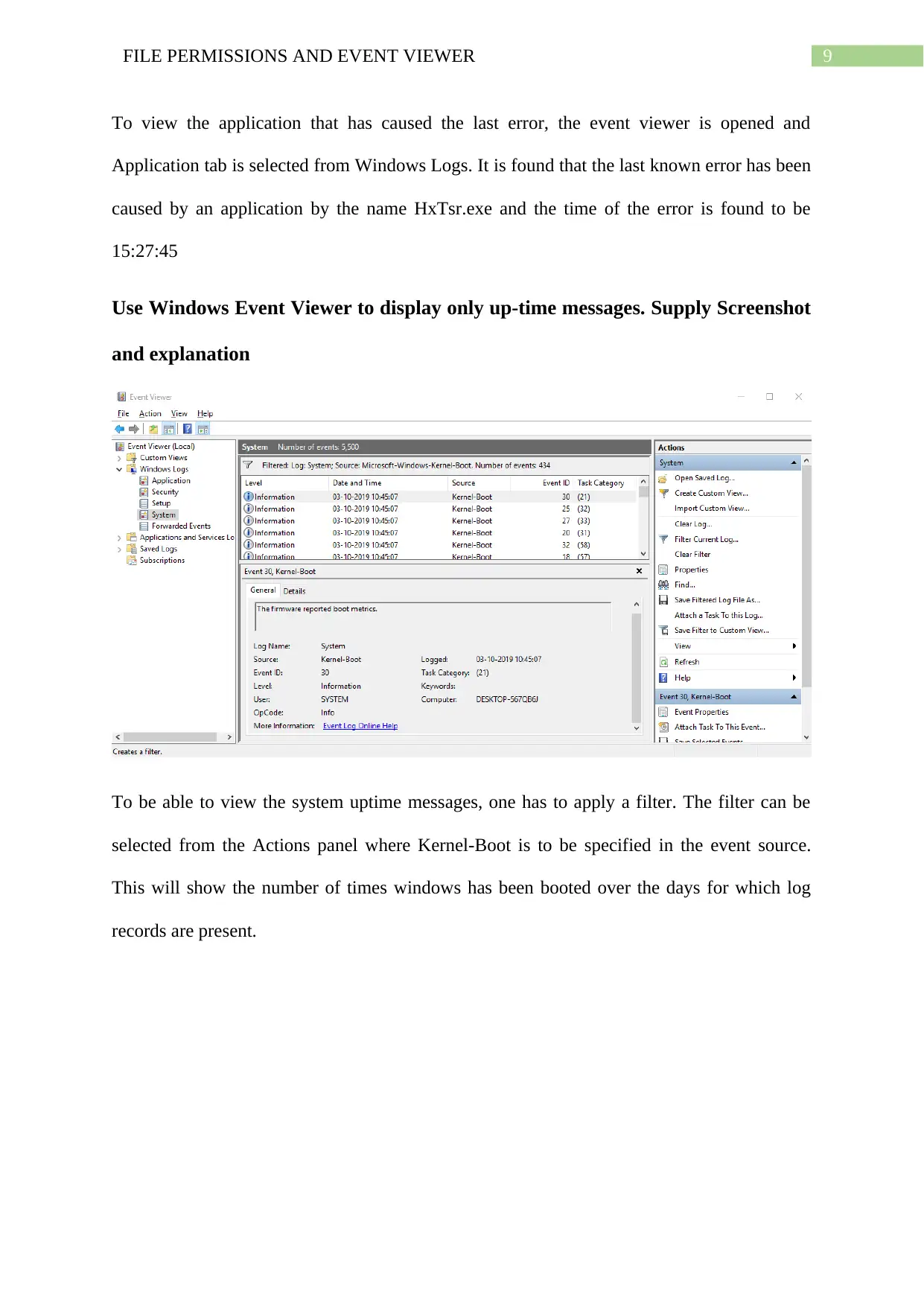
Use Windows Event Viewer to display only up-time messages. Supply Screenshot
and explanation
To be able to view the system uptime messages, one has to apply a filter. The filter can be
selected from the Actions panel where Kernel-Boot is to be specified in the event source.
This will show the number of times windows has been booted over the days for which log
records are present.
To view the application that has caused the last error, the event viewer is opened and
Application tab is selected from Windows Logs. It is found that the last known error has been
caused by an application by the name HxTsr.exe and the time of the error is found to be
15:27:45
Use Windows Event Viewer to display only up-time messages. Supply Screenshot
and explanation
To be able to view the system uptime messages, one has to apply a filter. The filter can be
selected from the Actions panel where Kernel-Boot is to be specified in the event source.
This will show the number of times windows has been booted over the days for which log
records are present.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10FILE PERMISSIONS AND EVENT VIEWER
Bibliography
Criswell, J., Zhou, J., Gravani, S. and Hu, X., 2019, June. PrivAnalyzer: Measuring the
Efficacy of Linux Privilege Use. In 2019 49th Annual IEEE/IFIP International Conference
on Dependable Systems and Networks (DSN) (pp. 593-604). IEEE.
Parkinson, S., Somaraki, V. and Ward, R., 2016. Auditing file system permissions using
association rule mining. Expert Systems with Applications, 55, pp.274-283.
Penninckx, W., Jacobs, B., Smans, J. and Mühlberg, J.T., 2019. Verification of Linux kernel
modules: Experience report.
Dinneen, J.D., Odoni, F., Frissen, I. and Julien, C.A., 2016, October. Cardinal: Novel
software for studying file management behavior. In Proceedings of the 79th ASIS&T Annual
Meeting: Creating Knowledge, Enhancing Lives through Information & Technology (p. 62).
American Society for Information Science.
Verma, R., Mendez, A.A., Park, S., Mannarswamy, S.S., Kelly, T.P. and Morrey III, C.B.,
2015. Failure-atomic updates of application data in a Linux file system. In 13th {USENIX}
Conference on File and Storage Technologies ({FAST} 15) (pp. 203-211).
Yang, T.Y., Dehghantanha, A., Choo, K.K. and Muda, Z., 2017. Investigating America
Online instant messaging application: data remnants on Windows 8.1 client machine.
In Contemporary Digital Forensic Investigations Of Cloud And Mobile Applications (pp. 21-
39). Syngress.
Bibliography
Criswell, J., Zhou, J., Gravani, S. and Hu, X., 2019, June. PrivAnalyzer: Measuring the
Efficacy of Linux Privilege Use. In 2019 49th Annual IEEE/IFIP International Conference
on Dependable Systems and Networks (DSN) (pp. 593-604). IEEE.
Parkinson, S., Somaraki, V. and Ward, R., 2016. Auditing file system permissions using
association rule mining. Expert Systems with Applications, 55, pp.274-283.
Penninckx, W., Jacobs, B., Smans, J. and Mühlberg, J.T., 2019. Verification of Linux kernel
modules: Experience report.
Dinneen, J.D., Odoni, F., Frissen, I. and Julien, C.A., 2016, October. Cardinal: Novel
software for studying file management behavior. In Proceedings of the 79th ASIS&T Annual
Meeting: Creating Knowledge, Enhancing Lives through Information & Technology (p. 62).
American Society for Information Science.
Verma, R., Mendez, A.A., Park, S., Mannarswamy, S.S., Kelly, T.P. and Morrey III, C.B.,
2015. Failure-atomic updates of application data in a Linux file system. In 13th {USENIX}
Conference on File and Storage Technologies ({FAST} 15) (pp. 203-211).
Yang, T.Y., Dehghantanha, A., Choo, K.K. and Muda, Z., 2017. Investigating America
Online instant messaging application: data remnants on Windows 8.1 client machine.
In Contemporary Digital Forensic Investigations Of Cloud And Mobile Applications (pp. 21-
39). Syngress.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



