Comprehensive Report on Fingerprint Authentication Methods
VerifiedAdded on 2023/06/04
|35
|17088
|312
Report
AI Summary
This report provides an in-depth analysis of fingerprint authentication, a biometric method widely used for person identification. It explores various fingerprint matching methods, including correlation-based, minutiae-based, and non-minutiae feature-based matching. The report also identifies and discusses fingerprinting errors such as False Rejection Rate (FRR), False Acceptance Rate (FAR), and Equal Error Rate (EER). Furthermore, it examines the transformation and integration of biometric capabilities, addressing issues and challenges in integrating these methods, including cost considerations and technological development. The research aims to provide a comprehensive overview of fingerprint authentication, its methods, associated errors, and integration aspects.

5/27/2019
Fingerprint Authentication
Student’s name
Institution Affiliation(s)
Fingerprint Authentication
Student’s name
Institution Affiliation(s)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Abstract......................................................................................................................................3
1. Introduction and Background.................................................................................................4
1.1 Introduction......................................................................................................................4
1.2 Background.......................................................................................................................5
1.3 Research Aims and Questions..........................................................................................6
2. Literature Review...................................................................................................................6
2.1. Fingerprint matching.......................................................................................................6
2.1.1. Correlation-based matching......................................................................................7
2.1.2. Minutiae-based matching..........................................................................................8
2.1.3. Non-Minutiae feature-based matching...................................................................11
2.2. Performance Evaluation................................................................................................13
2.3 Fingerprinting Errors......................................................................................................13
2.3.1. False Rejection Rate (FRR)....................................................................................14
2.3.2. False Acceptance Rate (FAR).................................................................................16
2.3.3. Equal Error Rate.....................................................................................................18
2.3.4. Zero FMR...............................................................................................................22
2.3.5. Zero FNMR.............................................................................................................24
2.4 Transforming and integrating your biometrics capability..............................................25
2.4.1. Systems integration expertise.................................................................................26
2.4.2. Issues in Integrating Biometrics.............................................................................27
2.4.3. Integrated Biometric Technology Development.....................................................27
2.4.4. Cost issues in Fingerprinting..................................................................................28
3. Proposed Method and Future Work.....................................................................................29
4. Conclusions..........................................................................................................................30
5. References............................................................................................................................31
Table of Figures
Figure 1: Types of fingerprints used as evidence.....................................................................10
Figure 2: Biometric Error Rates...............................................................................................13
Figure 3: False Accept Rate.....................................................................................................15
Figure 4: Graph showing the relationship between errors (CER, FRR, and FAR)..................17
Figure 5: Biometrics Error Rates.............................................................................................18
Figure 6: An example of FMR(t) and FNMR(t) curves...........................................................22
Figure 7: Relation between FNMR and FMR..........................................................................23
1
Abstract......................................................................................................................................3
1. Introduction and Background.................................................................................................4
1.1 Introduction......................................................................................................................4
1.2 Background.......................................................................................................................5
1.3 Research Aims and Questions..........................................................................................6
2. Literature Review...................................................................................................................6
2.1. Fingerprint matching.......................................................................................................6
2.1.1. Correlation-based matching......................................................................................7
2.1.2. Minutiae-based matching..........................................................................................8
2.1.3. Non-Minutiae feature-based matching...................................................................11
2.2. Performance Evaluation................................................................................................13
2.3 Fingerprinting Errors......................................................................................................13
2.3.1. False Rejection Rate (FRR)....................................................................................14
2.3.2. False Acceptance Rate (FAR).................................................................................16
2.3.3. Equal Error Rate.....................................................................................................18
2.3.4. Zero FMR...............................................................................................................22
2.3.5. Zero FNMR.............................................................................................................24
2.4 Transforming and integrating your biometrics capability..............................................25
2.4.1. Systems integration expertise.................................................................................26
2.4.2. Issues in Integrating Biometrics.............................................................................27
2.4.3. Integrated Biometric Technology Development.....................................................27
2.4.4. Cost issues in Fingerprinting..................................................................................28
3. Proposed Method and Future Work.....................................................................................29
4. Conclusions..........................................................................................................................30
5. References............................................................................................................................31
Table of Figures
Figure 1: Types of fingerprints used as evidence.....................................................................10
Figure 2: Biometric Error Rates...............................................................................................13
Figure 3: False Accept Rate.....................................................................................................15
Figure 4: Graph showing the relationship between errors (CER, FRR, and FAR)..................17
Figure 5: Biometrics Error Rates.............................................................................................18
Figure 6: An example of FMR(t) and FNMR(t) curves...........................................................22
Figure 7: Relation between FNMR and FMR..........................................................................23
1

Abstract
Fingerprint authentication is a biometric method that is used for a person’s
identification. The method has been widely used by security agencies such as the police or in
companies to identify employees. This research explores the various fingerprint matching
methods and in particular correlation-based matching, minutiae-based matching, and non-
minutiae feature-based matching. The report also identifies fingerprinting errors such as
False Rejection Rate, False Acceptance Rate, Equal Error Rate, Zero FMR, and Zero
FNMR. The report further explores the transformation and integration of biometric
capabilities and issues that arise when integrating these biometric methods. Integrated
biometric technology development and factors influencing fingerprint integration such as
cost have been discussed. Various tables have been provided and outline the various
literature reviews that were instrumental in carrying out this research.
Keywords: Biometric, Fingerprint, fingerprint matching, fingerprint identification, minutia,
fingerprint recognition.
2
Fingerprint authentication is a biometric method that is used for a person’s
identification. The method has been widely used by security agencies such as the police or in
companies to identify employees. This research explores the various fingerprint matching
methods and in particular correlation-based matching, minutiae-based matching, and non-
minutiae feature-based matching. The report also identifies fingerprinting errors such as
False Rejection Rate, False Acceptance Rate, Equal Error Rate, Zero FMR, and Zero
FNMR. The report further explores the transformation and integration of biometric
capabilities and issues that arise when integrating these biometric methods. Integrated
biometric technology development and factors influencing fingerprint integration such as
cost have been discussed. Various tables have been provided and outline the various
literature reviews that were instrumental in carrying out this research.
Keywords: Biometric, Fingerprint, fingerprint matching, fingerprint identification, minutia,
fingerprint recognition.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1. Introduction and Background
1.1 Introduction
Fingerprints appear at the patterns discovered on a fingertip. There are multiplicities
of methods to fingerprint authentication for example as customary police technique, by
means of pattern-matching systems or tools, plus things similar to more border patterns plus
Ultra-Sonics. This appears to be an extremely high-quality preference for in-house systems.
In the identification of fingerprints, various techniques are used, which include using
ultraviolet light which identifies a fingerprint on surfaces in which fingerprints cannot be
seen easily (Kioc, Maharjan, Adhikari, & Shrestha, 2018). Fingerprints can also be identified
using photographs, which are also done by pressing an individual finger onto an ink.
Fingerprint can be developed through a visible technique known as the ‘powder and brush’
technique where the surface is brushed with a powder that is very fine and sticky to the
droplets.
In situations where the surface may become some surfaces may absorb the powder
and make the fingerprints undistinguishable, electrostatic is used (Kioc et al., 2018). Here,
very fine powder will be placed on an electrode that is positively adjacent where it becomes
charged; hence is attracted to the specimen that is negatively charged. High voltage moves
the particles to travel quickly and stick firmly to the fingerprint. As this process continues,
the fingerprint will be sufficiently built-up. Casting is the best method of preserving plastic
fingerprint. Here, a liquid material will be poured on the fingerprint and also hardened in
order to make an impression cats. This casting method is best since it can store fingerprint for
a longer duration. Other fingerprints that are visible can be preserved using photography
(Hofer, 2018).
Fingerprints are scanned into the automated fingerprint system where ridge details
and other identifying characteristics are digitized in such in detail that the system can find a
match among the millions of fingerprints that are available in the database. This new
structure of identification has helped governments in different ways. It is vastly used in civil
identification projects like registration for elections, driving license, welfare systems et
cetera. Through this system, a government can make sure that no identity theft takes place, or
one person is not using two identities in order to vote. This kind of crime is quite common all
over the world. Sometimes a highly sensitive job requires the employer to check the
background of the candidate for the job so that all kind of risks can be avoided. This type of
identification check is mostly done for high-level posts in the government or law enforcement
agencies (Hofer, 2018).
For instance, in the United States of America, this automated system of fingerprint
identifications has the entire fingerprint collection from the country and is under the authority
of the Federal Bureau of Investigation. Other countries also have their own automated
fingerprint identification systems which have capabilities to do work like electronic image
storage, hidden searches, and the exchange of these fingerprints can also take place. It is used
for various reasons which can include identification of criminals, checking of backgrounds,
and in passport checks, it is one of the most important checks. This system is now popular
3
1.1 Introduction
Fingerprints appear at the patterns discovered on a fingertip. There are multiplicities
of methods to fingerprint authentication for example as customary police technique, by
means of pattern-matching systems or tools, plus things similar to more border patterns plus
Ultra-Sonics. This appears to be an extremely high-quality preference for in-house systems.
In the identification of fingerprints, various techniques are used, which include using
ultraviolet light which identifies a fingerprint on surfaces in which fingerprints cannot be
seen easily (Kioc, Maharjan, Adhikari, & Shrestha, 2018). Fingerprints can also be identified
using photographs, which are also done by pressing an individual finger onto an ink.
Fingerprint can be developed through a visible technique known as the ‘powder and brush’
technique where the surface is brushed with a powder that is very fine and sticky to the
droplets.
In situations where the surface may become some surfaces may absorb the powder
and make the fingerprints undistinguishable, electrostatic is used (Kioc et al., 2018). Here,
very fine powder will be placed on an electrode that is positively adjacent where it becomes
charged; hence is attracted to the specimen that is negatively charged. High voltage moves
the particles to travel quickly and stick firmly to the fingerprint. As this process continues,
the fingerprint will be sufficiently built-up. Casting is the best method of preserving plastic
fingerprint. Here, a liquid material will be poured on the fingerprint and also hardened in
order to make an impression cats. This casting method is best since it can store fingerprint for
a longer duration. Other fingerprints that are visible can be preserved using photography
(Hofer, 2018).
Fingerprints are scanned into the automated fingerprint system where ridge details
and other identifying characteristics are digitized in such in detail that the system can find a
match among the millions of fingerprints that are available in the database. This new
structure of identification has helped governments in different ways. It is vastly used in civil
identification projects like registration for elections, driving license, welfare systems et
cetera. Through this system, a government can make sure that no identity theft takes place, or
one person is not using two identities in order to vote. This kind of crime is quite common all
over the world. Sometimes a highly sensitive job requires the employer to check the
background of the candidate for the job so that all kind of risks can be avoided. This type of
identification check is mostly done for high-level posts in the government or law enforcement
agencies (Hofer, 2018).
For instance, in the United States of America, this automated system of fingerprint
identifications has the entire fingerprint collection from the country and is under the authority
of the Federal Bureau of Investigation. Other countries also have their own automated
fingerprint identification systems which have capabilities to do work like electronic image
storage, hidden searches, and the exchange of these fingerprints can also take place. It is used
for various reasons which can include identification of criminals, checking of backgrounds,
and in passport checks, it is one of the most important checks. This system is now popular
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

worldwide as it has made life much easier for law enforcement agencies to identify good
from the bad. There is a misconception that attempting to recover fingerprints from a firearm
has fewer chances of happening but this is not right because fingerprints or palm prints can be
removed from a firearm, spent cartridge, or magazine; therefore all firearms should be
checked thoroughly for evidence (Kellman et al., 2014).
In the international level, the European police agencies have now started to share its
automated fingerprint identification system with other countries in order to progress against
the war on terror or other cross border crimes that occur. This system on the investigation has
become very popular since the start of the war on terror in the world. From the year 2000
onwards this war has taken its toll, and the automated system of investigation has really
helped to decrease the criminal activities going on in the world. A lot of criminals are being
caught due to this system (Kellman et al., 2014).
1.2 Background
Biometrics have been taken as automatic detection of people foundational on their
physiological or behavioral features. Uni-modal new technologies based biometric systems
carry out person identification foundational on a single source of biometric data and are
influenced through issues similar to non-universality, noisy sensor data plus lack of
independence of the selection of the biometric attribute, lack of an invariant illustration for
the biometric feature as well as vulnerability to circumvention. A number of these issues are
able to be improved through making use of the state-of-the-art integrated biometric systems
that combine confirmation as of numerous biometric sources. Combination of proofs acquired
from numerous indication is a challenging aspect plus combining at the identical score level
is the widespread majority method for the reason that it presents the most excellent trade-off
among the information content as well as the easiness in integration (Chen, 2019).
There are numerous biometric systems and technologies to facilitate diverse kinds of
implementations. To select the correct biometric to be extremely effective for the particular
state, one has to map through several multifaceted vendor products as well as keep an eye on
future technology based plus standards enhancements. Below is an outline of biometrics
technology and systems.
Hand geometry entails assessing and analyzing plus determining the structure and
shape of the hand. It might be appropriate where there are more clients or where client access
the system occasionally. Accurateness is able to be extremely high if preferred, as well as
flexible performance tuning plus arrangement are able to contain numerous applications.
Corporations are making use of hand geometry readers in diverse scenarios, comprising
attendance and time recording (Bailey, 2018).
The retina is a biometric method and entails assessing the layer of blood vessels
located at the back of the human eye. This method entails making use of the low-intensity
light source by means of an optical coupler to scan the distinctive eye blood vessels patterns
of the eye’s retina. Retinal scanning is able to be quite perfect; however, does necessitate the
user to look into a receptacle as well as focus on a particular point inside the system.
4
from the bad. There is a misconception that attempting to recover fingerprints from a firearm
has fewer chances of happening but this is not right because fingerprints or palm prints can be
removed from a firearm, spent cartridge, or magazine; therefore all firearms should be
checked thoroughly for evidence (Kellman et al., 2014).
In the international level, the European police agencies have now started to share its
automated fingerprint identification system with other countries in order to progress against
the war on terror or other cross border crimes that occur. This system on the investigation has
become very popular since the start of the war on terror in the world. From the year 2000
onwards this war has taken its toll, and the automated system of investigation has really
helped to decrease the criminal activities going on in the world. A lot of criminals are being
caught due to this system (Kellman et al., 2014).
1.2 Background
Biometrics have been taken as automatic detection of people foundational on their
physiological or behavioral features. Uni-modal new technologies based biometric systems
carry out person identification foundational on a single source of biometric data and are
influenced through issues similar to non-universality, noisy sensor data plus lack of
independence of the selection of the biometric attribute, lack of an invariant illustration for
the biometric feature as well as vulnerability to circumvention. A number of these issues are
able to be improved through making use of the state-of-the-art integrated biometric systems
that combine confirmation as of numerous biometric sources. Combination of proofs acquired
from numerous indication is a challenging aspect plus combining at the identical score level
is the widespread majority method for the reason that it presents the most excellent trade-off
among the information content as well as the easiness in integration (Chen, 2019).
There are numerous biometric systems and technologies to facilitate diverse kinds of
implementations. To select the correct biometric to be extremely effective for the particular
state, one has to map through several multifaceted vendor products as well as keep an eye on
future technology based plus standards enhancements. Below is an outline of biometrics
technology and systems.
Hand geometry entails assessing and analyzing plus determining the structure and
shape of the hand. It might be appropriate where there are more clients or where client access
the system occasionally. Accurateness is able to be extremely high if preferred, as well as
flexible performance tuning plus arrangement are able to contain numerous applications.
Corporations are making use of hand geometry readers in diverse scenarios, comprising
attendance and time recording (Bailey, 2018).
The retina is a biometric method and entails assessing the layer of blood vessels
located at the back of the human eye. This method entails making use of the low-intensity
light source by means of an optical coupler to scan the distinctive eye blood vessels patterns
of the eye’s retina. Retinal scanning is able to be quite perfect; however, does necessitate the
user to look into a receptacle as well as focus on a particular point inside the system.
4

Iris-based technology of biometric systems entails assessing characteristics discovered
in the colored eye ring of tissue of humans that surrounds the pupil. This utilizes a reasonably
usual camera component and necessitates no close contact among the client and the reader.
Additionally, it has the power for higher than standard template matching competence (W.
Yang, Wang, Hu, Zheng, & Valli, 2019).
Face recognition based system investigations facial features. It necessitates a digital
camera to build up a facial image of the client intended for verification. For the reason that
facial scanning requires additional peripheral things that are not incorporated in fundamental
personal computers, it is more of a position marketplace intended for network verification.
Though, the casino business has capitalized on this technology to produce a human’s facial
database of scam artists intended for rapid recognition through security staff.
Signature-based authentication systems make use of the investigation the means client
signs his name. Signing features, for example, velocity, speed as well as pressure are as
significant as the complete signature's fixed shape. People are intended for signatures by
means of transaction associated characteristics confirmation (W. Yang et al., 2019).
A voice-based system that is used for the verification is foundational on voice-to-print
verification, where complex technology changes voice into text. Voice technology based
biometrics necessitates a microphone, which is accessible by means of personal computers
these days Voice biometrics is to substitute the presently employed techniques, for example,
passwords, PINs or account names. However, the voice will be a matching method intended
for finger-scan systems, as numerous people notice finger scanning like a superior
verification form (W. Yang et al., 2019).
1.3 Research Aims and Questions
This aim of this research is to explore the various fingerprint matching methods and in
particular correlation-based matching, minutiae-based matching, and non-minutiae feature-
based matching. The report also purposes to identify fingerprinting errors such as False
Rejection Rate, False Acceptance Rate, Equal Error Rate, Zero FMR, and Zero FNMR. The
research questions are given as follows:
a) What are the various methods for fingerprint matching?
b) What are the types of fingerprinting errors?
c) What are the transformation and integration of biometric capabilities and issues that
arise when integrating these biometric methods?
d) What are the factors influencing fingerprint integration?
2. Literature Review
2.1. Fingerprint matching
The fingerprint identification and matching process are used to evaluate the strange
and the recognized friction skin ridge feelings from palms or fingers. The identification helps
to ascertain if the impressions are from the identical palm or finger. The roughness of the
ridged skin is flexible meaning that there cannot be two fingerprints that are exactly similar.
Identification can also be termed as individualization. Identification occurs when an expert
5
in the colored eye ring of tissue of humans that surrounds the pupil. This utilizes a reasonably
usual camera component and necessitates no close contact among the client and the reader.
Additionally, it has the power for higher than standard template matching competence (W.
Yang, Wang, Hu, Zheng, & Valli, 2019).
Face recognition based system investigations facial features. It necessitates a digital
camera to build up a facial image of the client intended for verification. For the reason that
facial scanning requires additional peripheral things that are not incorporated in fundamental
personal computers, it is more of a position marketplace intended for network verification.
Though, the casino business has capitalized on this technology to produce a human’s facial
database of scam artists intended for rapid recognition through security staff.
Signature-based authentication systems make use of the investigation the means client
signs his name. Signing features, for example, velocity, speed as well as pressure are as
significant as the complete signature's fixed shape. People are intended for signatures by
means of transaction associated characteristics confirmation (W. Yang et al., 2019).
A voice-based system that is used for the verification is foundational on voice-to-print
verification, where complex technology changes voice into text. Voice technology based
biometrics necessitates a microphone, which is accessible by means of personal computers
these days Voice biometrics is to substitute the presently employed techniques, for example,
passwords, PINs or account names. However, the voice will be a matching method intended
for finger-scan systems, as numerous people notice finger scanning like a superior
verification form (W. Yang et al., 2019).
1.3 Research Aims and Questions
This aim of this research is to explore the various fingerprint matching methods and in
particular correlation-based matching, minutiae-based matching, and non-minutiae feature-
based matching. The report also purposes to identify fingerprinting errors such as False
Rejection Rate, False Acceptance Rate, Equal Error Rate, Zero FMR, and Zero FNMR. The
research questions are given as follows:
a) What are the various methods for fingerprint matching?
b) What are the types of fingerprinting errors?
c) What are the transformation and integration of biometric capabilities and issues that
arise when integrating these biometric methods?
d) What are the factors influencing fingerprint integration?
2. Literature Review
2.1. Fingerprint matching
The fingerprint identification and matching process are used to evaluate the strange
and the recognized friction skin ridge feelings from palms or fingers. The identification helps
to ascertain if the impressions are from the identical palm or finger. The roughness of the
ridged skin is flexible meaning that there cannot be two fingerprints that are exactly similar.
Identification can also be termed as individualization. Identification occurs when an expert
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

computer system or expert operates under threshold scoring regulations. It is used to exclude
one finger or palm from others. Sometimes differences or dissimilarities may arise from the
fingerprint identification process. These differences do not imply that there is no
identification.
2.1.1. Correlation-based matching
It is a fact that non-identification would not be possible because the print contains so
many matching characteristics; for instance, it has a total of 28 ridges structures that are
clearly observable. A print with many matching characteristics like this confirms
identification. It would thus not have any dissimilarity (Konecny, Prauzek, Tran, Martinek, &
Hlavica, 2018). The 28 ridge structures in identification are so much and efficient to confirm
the presence of identification in this scenario. Dissimilarity can only be in the prints that are
not matching. The structures are sufficient matching characteristics; hence, they can be used
to make an evaluation to remove the possibility that the giver of the latent print could be
someone else. Dissimilarity only shows that there is inadequate detail to be certain of the
detection. Uncertainty may exist in some latent print assessors who are interchanging the
terms distortion and dissimilarity (H. Liu, Wang, Tang, & Jezek, 2012). The impact of such
misunderstanding may be a loss of credibility when the latent print examiners cannot support
their results. The similarities are used to ascertain identity. However, dissimilarity proves that
two prints are not matching; hence; they are not from the same print. When matching
characteristics have been found to detect an identity, there cannot be dissimilarities. The
notion that dissimilarity can be present despite the number of matching features is not
applicable. If this were accurate, then there would forever be dissimilarity. This would
eventually mean that identification can never be made (Konecny, Prauzek, Kromer, &
Musilek, 2016).
Sometimes distortions can also change the manifestation of prints. The distortions can
also obstruct with the relationship. They are recurrent in all prints. Alteration is found in both
latent and pattern prints that have a similar origin. There are instances where the distortions
can be noticed. This is because it is never possible to fully capture all the details of the entire
print even when taking a rolled and known impression. The fingerprint identification can only
be made by the fingerprint examination experts (F. Zhao, Huang, Wang, & Gao, 2010).
Currently, the knowledge of fingerprint detection is better than all other forensic sciences.
The outline of ridges on the finger pads is unique. It is impossible to find two people whose
fingerprints are similar even if the individuals are identical twins. The print can be detected
when the fingers are oily or dirty and when they are latent. The injuries, for instance, the
scrapes and burns, cannot change the ridge structure. When a fresh skin develops in, a similar
pattern comes back. There are no similar fingerprints that have been established in the many
billions of automated computer and human comparisons (Akinyele, Sarumi, Abdulsamad, &
Green, 2018). Therefore, fingerprints are the foundation for illegal records. Hence, it has
served in all governments globally for over 100 years to detect criminals. The fingerprint
identification also continues to develop as the first method for identifying people. It also
surpasses DNA and all other human identification systems to discover additional rapists,
murderers, and serious offenders (Luo, Lorentzen, Valestrand, & Evensen, 2018).
6
one finger or palm from others. Sometimes differences or dissimilarities may arise from the
fingerprint identification process. These differences do not imply that there is no
identification.
2.1.1. Correlation-based matching
It is a fact that non-identification would not be possible because the print contains so
many matching characteristics; for instance, it has a total of 28 ridges structures that are
clearly observable. A print with many matching characteristics like this confirms
identification. It would thus not have any dissimilarity (Konecny, Prauzek, Tran, Martinek, &
Hlavica, 2018). The 28 ridge structures in identification are so much and efficient to confirm
the presence of identification in this scenario. Dissimilarity can only be in the prints that are
not matching. The structures are sufficient matching characteristics; hence, they can be used
to make an evaluation to remove the possibility that the giver of the latent print could be
someone else. Dissimilarity only shows that there is inadequate detail to be certain of the
detection. Uncertainty may exist in some latent print assessors who are interchanging the
terms distortion and dissimilarity (H. Liu, Wang, Tang, & Jezek, 2012). The impact of such
misunderstanding may be a loss of credibility when the latent print examiners cannot support
their results. The similarities are used to ascertain identity. However, dissimilarity proves that
two prints are not matching; hence; they are not from the same print. When matching
characteristics have been found to detect an identity, there cannot be dissimilarities. The
notion that dissimilarity can be present despite the number of matching features is not
applicable. If this were accurate, then there would forever be dissimilarity. This would
eventually mean that identification can never be made (Konecny, Prauzek, Kromer, &
Musilek, 2016).
Sometimes distortions can also change the manifestation of prints. The distortions can
also obstruct with the relationship. They are recurrent in all prints. Alteration is found in both
latent and pattern prints that have a similar origin. There are instances where the distortions
can be noticed. This is because it is never possible to fully capture all the details of the entire
print even when taking a rolled and known impression. The fingerprint identification can only
be made by the fingerprint examination experts (F. Zhao, Huang, Wang, & Gao, 2010).
Currently, the knowledge of fingerprint detection is better than all other forensic sciences.
The outline of ridges on the finger pads is unique. It is impossible to find two people whose
fingerprints are similar even if the individuals are identical twins. The print can be detected
when the fingers are oily or dirty and when they are latent. The injuries, for instance, the
scrapes and burns, cannot change the ridge structure. When a fresh skin develops in, a similar
pattern comes back. There are no similar fingerprints that have been established in the many
billions of automated computer and human comparisons (Akinyele, Sarumi, Abdulsamad, &
Green, 2018). Therefore, fingerprints are the foundation for illegal records. Hence, it has
served in all governments globally for over 100 years to detect criminals. The fingerprint
identification also continues to develop as the first method for identifying people. It also
surpasses DNA and all other human identification systems to discover additional rapists,
murderers, and serious offenders (Luo, Lorentzen, Valestrand, & Evensen, 2018).
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
In summary, the fingerprint identification effects further helpful identifications of
people internationally every day than other human identification processes. The little
dissatisfaction over fingerprint proof may be due to the wish to drive the resolution of
fingerprint examinations to an equal rank of conviction as that of DNA investigation. The
fingerprint society maintains the need for impartiality and continued exploration in the
vicinity of friction ridge scrutiny.
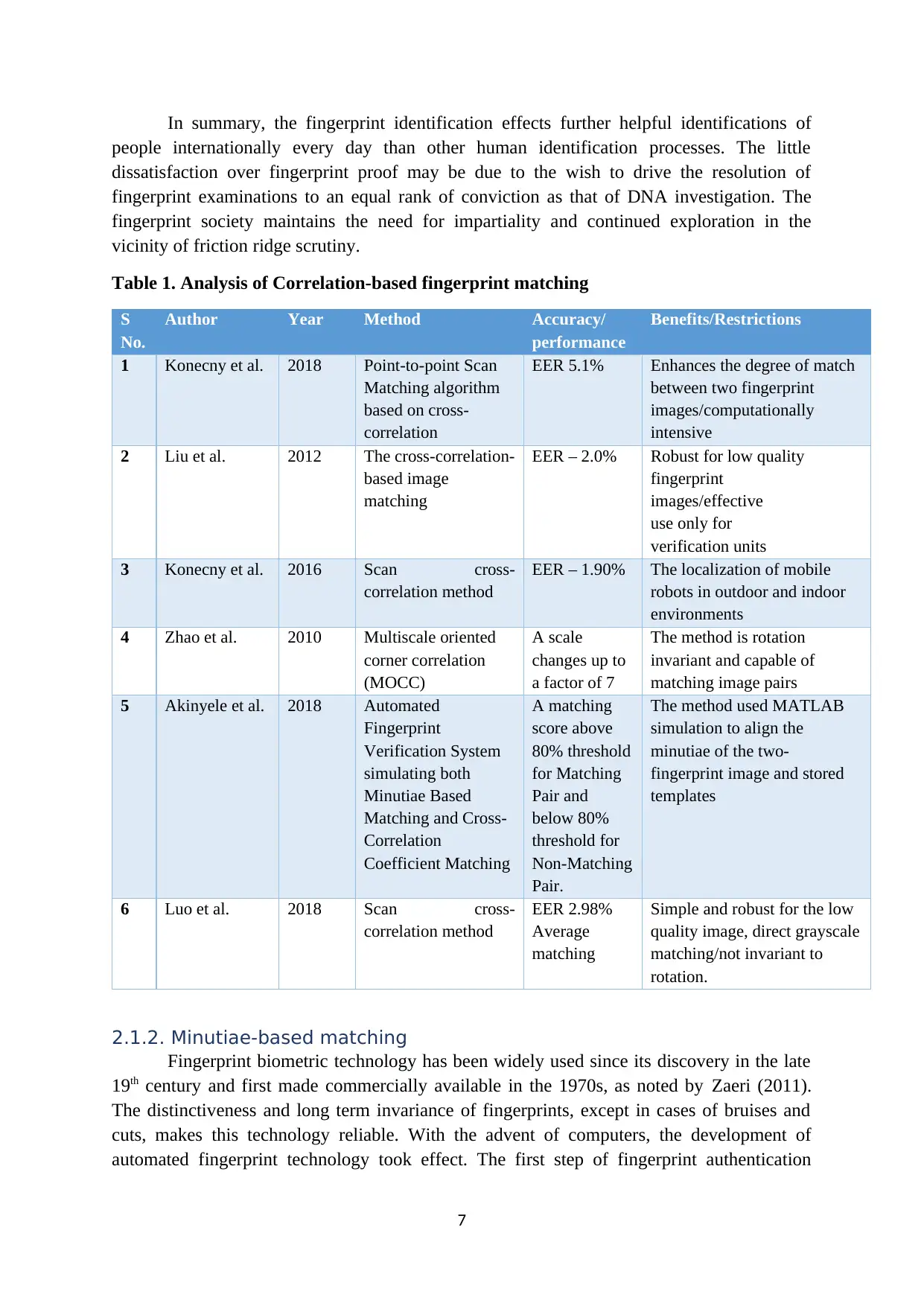
Table 1. Analysis of Correlation-based fingerprint matching
S
No.
Author Year Method Accuracy/
performance
Benefits/Restrictions
1 Konecny et al. 2018 Point-to-point Scan
Matching algorithm
based on cross-
correlation
EER 5.1% Enhances the degree of match
between two fingerprint
images/computationally
intensive
2 Liu et al. 2012 The cross-correlation-
based image
matching
EER – 2.0% Robust for low quality
fingerprint
images/effective
use only for
verification units
3 Konecny et al. 2016 Scan cross-
correlation method
EER – 1.90% The localization of mobile
robots in outdoor and indoor
environments
4 Zhao et al. 2010 Multiscale oriented
corner correlation
(MOCC)
A scale
changes up to
a factor of 7
The method is rotation
invariant and capable of
matching image pairs
5 Akinyele et al. 2018 Automated
Fingerprint
Verification System
simulating both
Minutiae Based
Matching and Cross-
Correlation
Coefficient Matching
A matching
score above
80% threshold
for Matching
Pair and
below 80%
threshold for
Non-Matching
Pair.
The method used MATLAB
simulation to align the
minutiae of the two-
fingerprint image and stored
templates
6 Luo et al. 2018 Scan cross-
correlation method
EER 2.98%
Average
matching
Simple and robust for the low
quality image, direct grayscale
matching/not invariant to
rotation.
2.1.2. Minutiae-based matching
Fingerprint biometric technology has been widely used since its discovery in the late
19th century and first made commercially available in the 1970s, as noted by Zaeri (2011).
The distinctiveness and long term invariance of fingerprints, except in cases of bruises and
cuts, makes this technology reliable. With the advent of computers, the development of
automated fingerprint technology took effect. The first step of fingerprint authentication
7
people internationally every day than other human identification processes. The little
dissatisfaction over fingerprint proof may be due to the wish to drive the resolution of
fingerprint examinations to an equal rank of conviction as that of DNA investigation. The
fingerprint society maintains the need for impartiality and continued exploration in the
vicinity of friction ridge scrutiny.
Table 1. Analysis of Correlation-based fingerprint matching
S
No.
Author Year Method Accuracy/
performance
Benefits/Restrictions
1 Konecny et al. 2018 Point-to-point Scan
Matching algorithm
based on cross-
correlation
EER 5.1% Enhances the degree of match
between two fingerprint
images/computationally
intensive
2 Liu et al. 2012 The cross-correlation-
based image
matching
EER – 2.0% Robust for low quality
fingerprint
images/effective
use only for
verification units
3 Konecny et al. 2016 Scan cross-
correlation method
EER – 1.90% The localization of mobile
robots in outdoor and indoor
environments
4 Zhao et al. 2010 Multiscale oriented
corner correlation
(MOCC)
A scale
changes up to
a factor of 7
The method is rotation
invariant and capable of
matching image pairs
5 Akinyele et al. 2018 Automated
Fingerprint
Verification System
simulating both
Minutiae Based
Matching and Cross-
Correlation
Coefficient Matching
A matching
score above
80% threshold
for Matching
Pair and
below 80%
threshold for
Non-Matching
Pair.
The method used MATLAB
simulation to align the
minutiae of the two-
fingerprint image and stored
templates
6 Luo et al. 2018 Scan cross-
correlation method
EER 2.98%
Average
matching
Simple and robust for the low
quality image, direct grayscale
matching/not invariant to
rotation.
2.1.2. Minutiae-based matching
Fingerprint biometric technology has been widely used since its discovery in the late
19th century and first made commercially available in the 1970s, as noted by Zaeri (2011).
The distinctiveness and long term invariance of fingerprints, except in cases of bruises and
cuts, makes this technology reliable. With the advent of computers, the development of
automated fingerprint technology took effect. The first step of fingerprint authentication
7

process involves the acquisition of fingerprint impression by use of an inkless scanner ( Liu,
Yang, Yin, & Wang, 2014). There are various types of scanners, including capacitive, optical,
thermal, and ultrasound sensors used to collect a digital image of the surface of a fingerprint.
According to the National Science and Technology Council, optical sensors are the most
commonly used today. The collected image would be digitized at typically 500 dots per inch
and with 256 gray levels per pixel. The digital image captures unique features of minutiae
comprising of ridge endings and bifurcations (Le, Nguyen, & Nguyen, 2018). An automated
feature extraction algorithm then locates these features from the fingerprint image with each
feature represented by its respective location and direction. The ridges would normally be
further enhanced to nullify the effect of noise. Finally, the matcher subsystem would attempt
to match these sets of features and would be expressed as a score from where a decision of
matching would be made. A decision threshold would normally be selected prior to this and
scores below the threshold would be a mismatch while those above the threshold lead to the
declaration of a correct match (Kanchana & Balakrishnan, 2015).
Consequently, fingerprint biometrics faces user acceptance challenges with the public
further raising concerns on privacy which involves the protection of their personal data
against any form of misuse including identity theft, loss of anonymity and the possibility of
obtained data revealing medical information (Peralta, García, Benitez, & Herrera, 2017).
Lerner argues that with mass biometric identification, “the big brother” would always be
watching and would use such opportunities to track dissidents and make resistance more
difficult as it happened in the 1960s and 1970s with the COINTELPRO program by the FBI
(Fu & Feng, 2015). The researcher cites the US as an example of a government that has
access to the universal biometric identifier, also used for commercial transactions like
banking (Kai Cao et al., 2012).
Similarly, fingerprints could be lifted off surfaces of glass, even from fingerprint
scanners by use of a cube of gelatin and graphite powder and used to fool scanners elsewhere.
But Chaudhari and Patil (2014) argue that the Privacy Act 1974 prohibits federal agencies
from collecting, using, or disclosing personal information, including fingerprints.
Accordingly, this act protects personal biometric information from being used by federal
agencies. Hygiene issues have also been cited with fingerprint biometric technology as those
whose identities are being identified have to place their fingers on scanners shared by all such
persons(Hajare, 2016). Diseases could be transmitted through contact in such cases. But
opponents of this argument claim the risk, in this case, to be insignificantly minimal.
Otherwise, humans would fall sick by everyday use of doorknobs at homes, workplaces, and
vehicles since the risk involved are similar (Bahaa, 2013a).
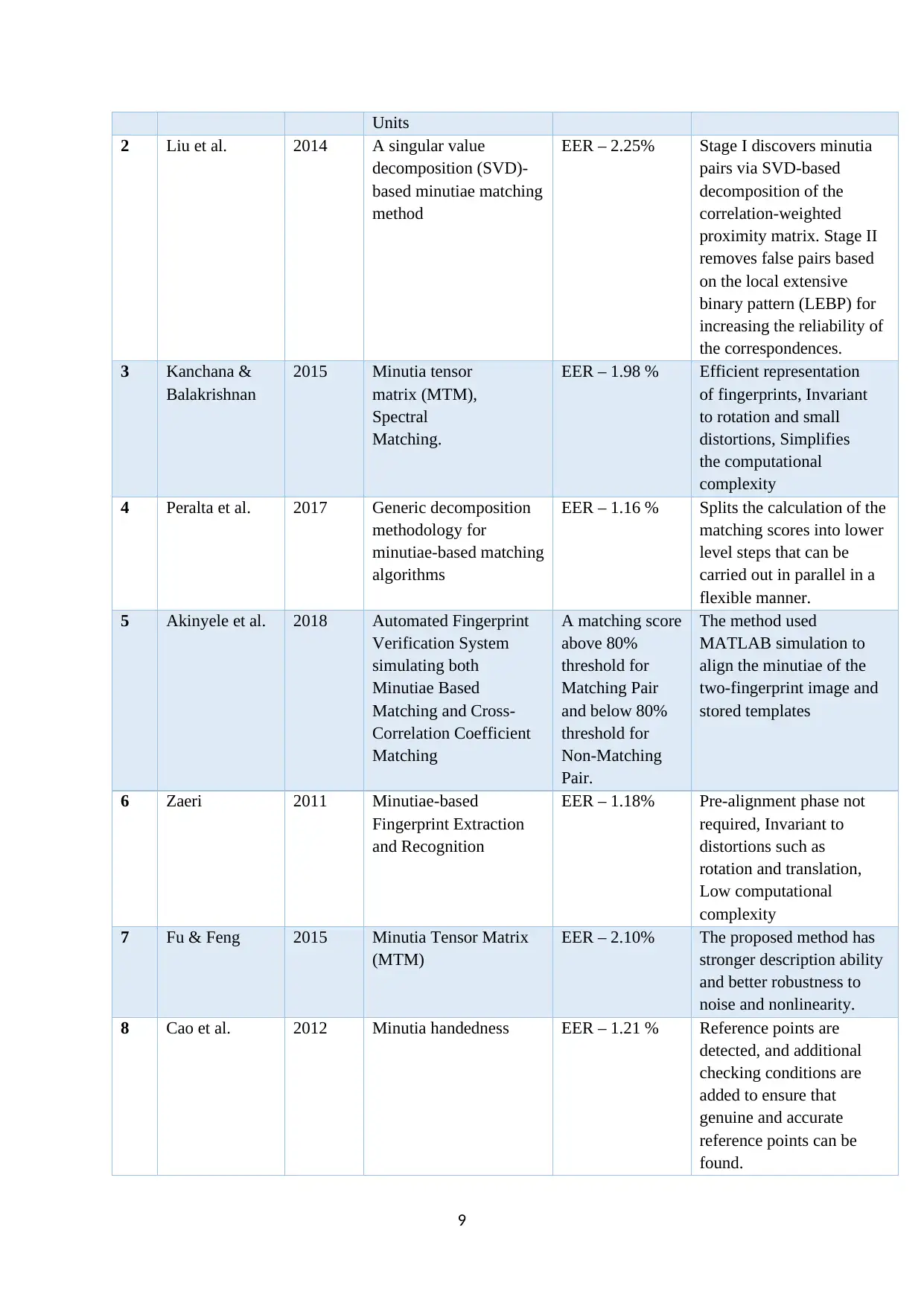
Table 2: Performance Analysis of minutiae-based fingerprint matching
S
No.
Author Year Method Accuracy/
performance
Benefits/Restrictions
1 Le et al., 2018 Fingerprint matching
algorithm based on
Minutia Cylinder-Code
on Graphics Processing
EER - 1.96% Suitable for a real-time
identification application
8
Yang, Yin, & Wang, 2014). There are various types of scanners, including capacitive, optical,
thermal, and ultrasound sensors used to collect a digital image of the surface of a fingerprint.
According to the National Science and Technology Council, optical sensors are the most
commonly used today. The collected image would be digitized at typically 500 dots per inch
and with 256 gray levels per pixel. The digital image captures unique features of minutiae
comprising of ridge endings and bifurcations (Le, Nguyen, & Nguyen, 2018). An automated
feature extraction algorithm then locates these features from the fingerprint image with each
feature represented by its respective location and direction. The ridges would normally be
further enhanced to nullify the effect of noise. Finally, the matcher subsystem would attempt
to match these sets of features and would be expressed as a score from where a decision of
matching would be made. A decision threshold would normally be selected prior to this and
scores below the threshold would be a mismatch while those above the threshold lead to the
declaration of a correct match (Kanchana & Balakrishnan, 2015).
Consequently, fingerprint biometrics faces user acceptance challenges with the public
further raising concerns on privacy which involves the protection of their personal data
against any form of misuse including identity theft, loss of anonymity and the possibility of
obtained data revealing medical information (Peralta, García, Benitez, & Herrera, 2017).
Lerner argues that with mass biometric identification, “the big brother” would always be
watching and would use such opportunities to track dissidents and make resistance more
difficult as it happened in the 1960s and 1970s with the COINTELPRO program by the FBI
(Fu & Feng, 2015). The researcher cites the US as an example of a government that has
access to the universal biometric identifier, also used for commercial transactions like
banking (Kai Cao et al., 2012).
Similarly, fingerprints could be lifted off surfaces of glass, even from fingerprint
scanners by use of a cube of gelatin and graphite powder and used to fool scanners elsewhere.
But Chaudhari and Patil (2014) argue that the Privacy Act 1974 prohibits federal agencies
from collecting, using, or disclosing personal information, including fingerprints.
Accordingly, this act protects personal biometric information from being used by federal
agencies. Hygiene issues have also been cited with fingerprint biometric technology as those
whose identities are being identified have to place their fingers on scanners shared by all such
persons(Hajare, 2016). Diseases could be transmitted through contact in such cases. But
opponents of this argument claim the risk, in this case, to be insignificantly minimal.
Otherwise, humans would fall sick by everyday use of doorknobs at homes, workplaces, and
vehicles since the risk involved are similar (Bahaa, 2013a).
Table 2: Performance Analysis of minutiae-based fingerprint matching
S
No.
Author Year Method Accuracy/
performance
Benefits/Restrictions
1 Le et al., 2018 Fingerprint matching
algorithm based on
Minutia Cylinder-Code
on Graphics Processing
EER - 1.96% Suitable for a real-time
identification application
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Units
2 Liu et al. 2014 A singular value
decomposition (SVD)-
based minutiae matching
method
EER – 2.25% Stage I discovers minutia
pairs via SVD-based
decomposition of the
correlation-weighted
proximity matrix. Stage II
removes false pairs based
on the local extensive
binary pattern (LEBP) for
increasing the reliability of
the correspondences.
3 Kanchana &
Balakrishnan
2015 Minutia tensor
matrix (MTM),
Spectral
Matching.
EER – 1.98 % Efficient representation
of fingerprints, Invariant
to rotation and small
distortions, Simplifies
the computational
complexity
4 Peralta et al. 2017 Generic decomposition
methodology for
minutiae-based matching
algorithms
EER – 1.16 % Splits the calculation of the
matching scores into lower
level steps that can be
carried out in parallel in a
flexible manner.
5 Akinyele et al. 2018 Automated Fingerprint
Verification System
simulating both
Minutiae Based
Matching and Cross-
Correlation Coefficient
Matching
A matching score
above 80%
threshold for
Matching Pair
and below 80%
threshold for
Non-Matching
Pair.
The method used
MATLAB simulation to
align the minutiae of the
two-fingerprint image and
stored templates
6 Zaeri 2011 Minutiae-based
Fingerprint Extraction
and Recognition
EER – 1.18% Pre-alignment phase not
required, Invariant to
distortions such as
rotation and translation,
Low computational
complexity
7 Fu & Feng 2015 Minutia Tensor Matrix
(MTM)
EER – 2.10% The proposed method has
stronger description ability
and better robustness to
noise and nonlinearity.
8 Cao et al. 2012 Minutia handedness EER – 1.21 % Reference points are
detected, and additional
checking conditions are
added to ensure that
genuine and accurate
reference points can be
found.
9
2 Liu et al. 2014 A singular value
decomposition (SVD)-
based minutiae matching
method
EER – 2.25% Stage I discovers minutia
pairs via SVD-based
decomposition of the
correlation-weighted
proximity matrix. Stage II
removes false pairs based
on the local extensive
binary pattern (LEBP) for
increasing the reliability of
the correspondences.
3 Kanchana &
Balakrishnan
2015 Minutia tensor
matrix (MTM),
Spectral
Matching.
EER – 1.98 % Efficient representation
of fingerprints, Invariant
to rotation and small
distortions, Simplifies
the computational
complexity
4 Peralta et al. 2017 Generic decomposition
methodology for
minutiae-based matching
algorithms
EER – 1.16 % Splits the calculation of the
matching scores into lower
level steps that can be
carried out in parallel in a
flexible manner.
5 Akinyele et al. 2018 Automated Fingerprint
Verification System
simulating both
Minutiae Based
Matching and Cross-
Correlation Coefficient
Matching
A matching score
above 80%
threshold for
Matching Pair
and below 80%
threshold for
Non-Matching
Pair.
The method used
MATLAB simulation to
align the minutiae of the
two-fingerprint image and
stored templates
6 Zaeri 2011 Minutiae-based
Fingerprint Extraction
and Recognition
EER – 1.18% Pre-alignment phase not
required, Invariant to
distortions such as
rotation and translation,
Low computational
complexity
7 Fu & Feng 2015 Minutia Tensor Matrix
(MTM)
EER – 2.10% The proposed method has
stronger description ability
and better robustness to
noise and nonlinearity.
8 Cao et al. 2012 Minutia handedness EER – 1.21 % Reference points are
detected, and additional
checking conditions are
added to ensure that
genuine and accurate
reference points can be
found.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
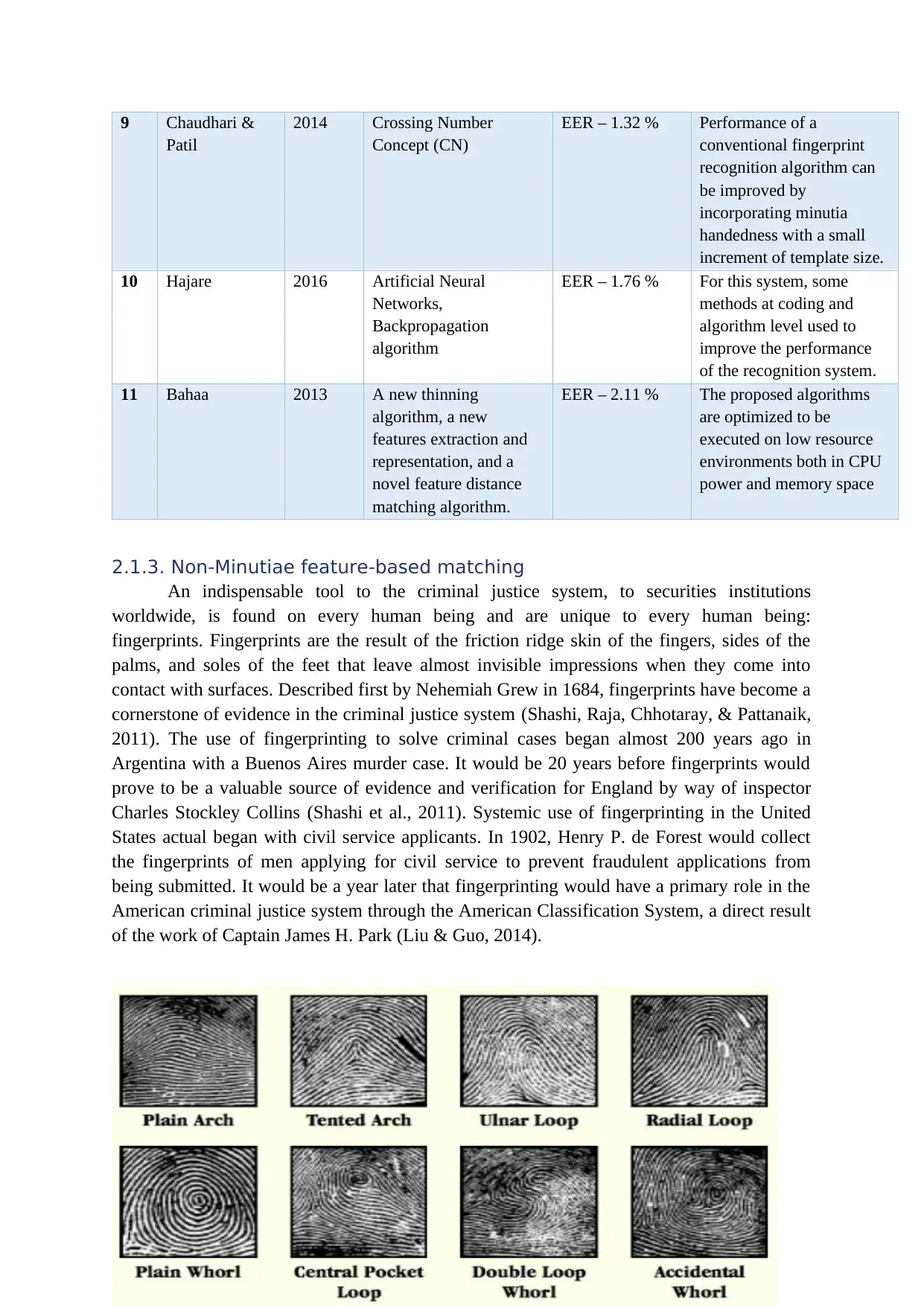
9 Chaudhari &
Patil
2014 Crossing Number
Concept (CN)
EER – 1.32 % Performance of a
conventional fingerprint
recognition algorithm can
be improved by
incorporating minutia
handedness with a small
increment of template size.
10 Hajare 2016 Artificial Neural
Networks,
Backpropagation
algorithm
EER – 1.76 % For this system, some
methods at coding and
algorithm level used to
improve the performance
of the recognition system.
11 Bahaa 2013 A new thinning
algorithm, a new
features extraction and
representation, and a
novel feature distance
matching algorithm.
EER – 2.11 % The proposed algorithms
are optimized to be
executed on low resource
environments both in CPU
power and memory space
2.1.3. Non-Minutiae feature-based matching
An indispensable tool to the criminal justice system, to securities institutions
worldwide, is found on every human being and are unique to every human being:
fingerprints. Fingerprints are the result of the friction ridge skin of the fingers, sides of the
palms, and soles of the feet that leave almost invisible impressions when they come into
contact with surfaces. Described first by Nehemiah Grew in 1684, fingerprints have become a
cornerstone of evidence in the criminal justice system (Shashi, Raja, Chhotaray, & Pattanaik,
2011). The use of fingerprinting to solve criminal cases began almost 200 years ago in
Argentina with a Buenos Aires murder case. It would be 20 years before fingerprints would
prove to be a valuable source of evidence and verification for England by way of inspector
Charles Stockley Collins (Shashi et al., 2011). Systemic use of fingerprinting in the United
States actual began with civil service applicants. In 1902, Henry P. de Forest would collect
the fingerprints of men applying for civil service to prevent fraudulent applications from
being submitted. It would be a year later that fingerprinting would have a primary role in the
American criminal justice system through the American Classification System, a direct result
of the work of Captain James H. Park (Liu & Guo, 2014).
10
Patil
2014 Crossing Number
Concept (CN)
EER – 1.32 % Performance of a
conventional fingerprint
recognition algorithm can
be improved by
incorporating minutia
handedness with a small
increment of template size.
10 Hajare 2016 Artificial Neural
Networks,
Backpropagation
algorithm
EER – 1.76 % For this system, some
methods at coding and
algorithm level used to
improve the performance
of the recognition system.
11 Bahaa 2013 A new thinning
algorithm, a new
features extraction and
representation, and a
novel feature distance
matching algorithm.
EER – 2.11 % The proposed algorithms
are optimized to be
executed on low resource
environments both in CPU
power and memory space
2.1.3. Non-Minutiae feature-based matching
An indispensable tool to the criminal justice system, to securities institutions
worldwide, is found on every human being and are unique to every human being:
fingerprints. Fingerprints are the result of the friction ridge skin of the fingers, sides of the
palms, and soles of the feet that leave almost invisible impressions when they come into
contact with surfaces. Described first by Nehemiah Grew in 1684, fingerprints have become a
cornerstone of evidence in the criminal justice system (Shashi, Raja, Chhotaray, & Pattanaik,
2011). The use of fingerprinting to solve criminal cases began almost 200 years ago in
Argentina with a Buenos Aires murder case. It would be 20 years before fingerprints would
prove to be a valuable source of evidence and verification for England by way of inspector
Charles Stockley Collins (Shashi et al., 2011). Systemic use of fingerprinting in the United
States actual began with civil service applicants. In 1902, Henry P. de Forest would collect
the fingerprints of men applying for civil service to prevent fraudulent applications from
being submitted. It would be a year later that fingerprinting would have a primary role in the
American criminal justice system through the American Classification System, a direct result
of the work of Captain James H. Park (Liu & Guo, 2014).
10
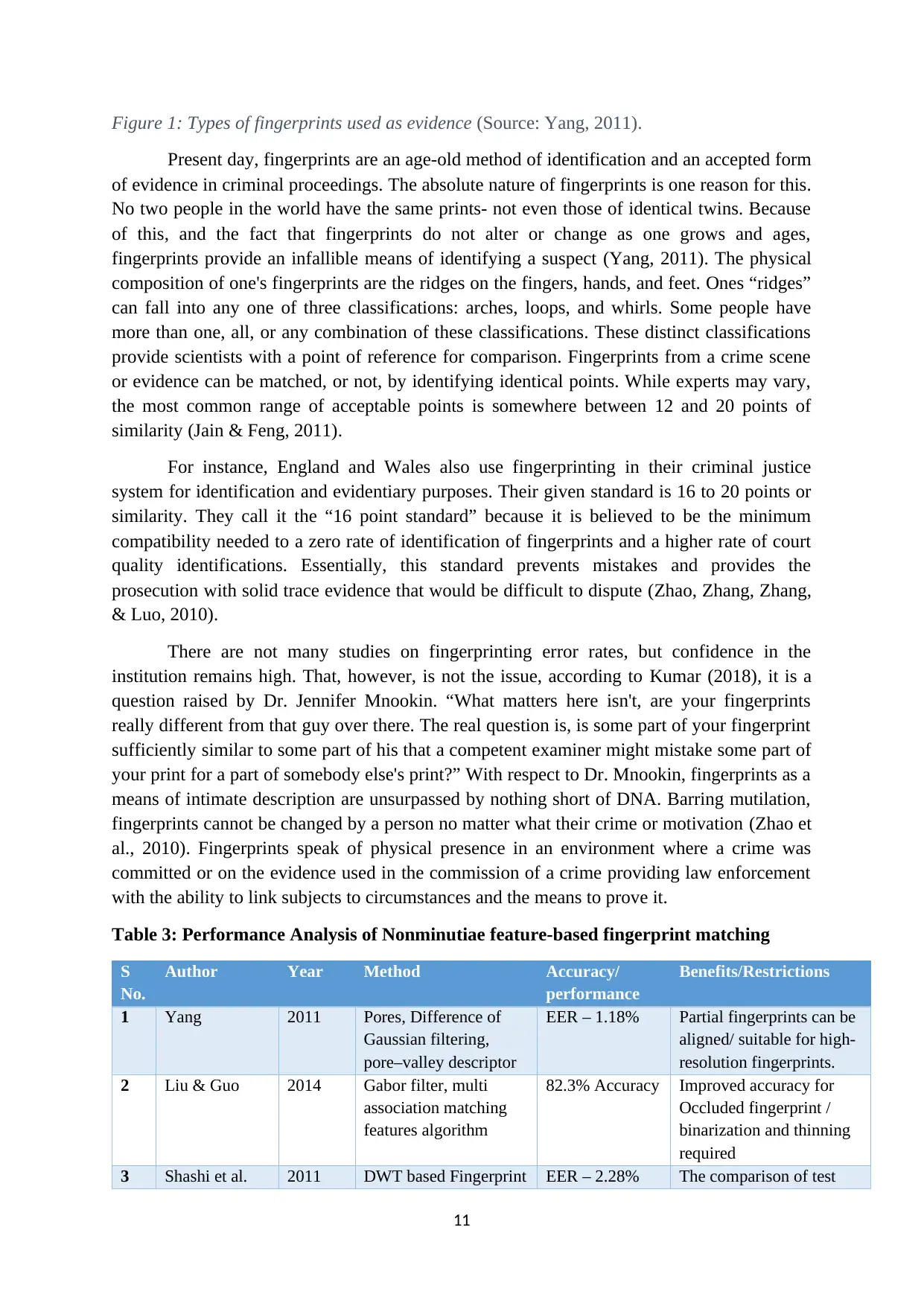
Figure 1: Types of fingerprints used as evidence (Source: Yang, 2011).
Present day, fingerprints are an age-old method of identification and an accepted form
of evidence in criminal proceedings. The absolute nature of fingerprints is one reason for this.
No two people in the world have the same prints- not even those of identical twins. Because
of this, and the fact that fingerprints do not alter or change as one grows and ages,
fingerprints provide an infallible means of identifying a suspect (Yang, 2011). The physical
composition of one's fingerprints are the ridges on the fingers, hands, and feet. Ones “ridges”
can fall into any one of three classifications: arches, loops, and whirls. Some people have
more than one, all, or any combination of these classifications. These distinct classifications
provide scientists with a point of reference for comparison. Fingerprints from a crime scene
or evidence can be matched, or not, by identifying identical points. While experts may vary,
the most common range of acceptable points is somewhere between 12 and 20 points of
similarity (Jain & Feng, 2011).
For instance, England and Wales also use fingerprinting in their criminal justice
system for identification and evidentiary purposes. Their given standard is 16 to 20 points or
similarity. They call it the “16 point standard” because it is believed to be the minimum
compatibility needed to a zero rate of identification of fingerprints and a higher rate of court
quality identifications. Essentially, this standard prevents mistakes and provides the
prosecution with solid trace evidence that would be difficult to dispute (Zhao, Zhang, Zhang,
& Luo, 2010).
There are not many studies on fingerprinting error rates, but confidence in the
institution remains high. That, however, is not the issue, according to Kumar (2018), it is a
question raised by Dr. Jennifer Mnookin. “What matters here isn't, are your fingerprints
really different from that guy over there. The real question is, is some part of your fingerprint
sufficiently similar to some part of his that a competent examiner might mistake some part of
your print for a part of somebody else's print?” With respect to Dr. Mnookin, fingerprints as a
means of intimate description are unsurpassed by nothing short of DNA. Barring mutilation,
fingerprints cannot be changed by a person no matter what their crime or motivation (Zhao et
al., 2010). Fingerprints speak of physical presence in an environment where a crime was
committed or on the evidence used in the commission of a crime providing law enforcement
with the ability to link subjects to circumstances and the means to prove it.
Table 3: Performance Analysis of Nonminutiae feature-based fingerprint matching
S
No.
Author Year Method Accuracy/
performance
Benefits/Restrictions
1 Yang 2011 Pores, Difference of
Gaussian filtering,
pore–valley descriptor
EER – 1.18% Partial fingerprints can be
aligned/ suitable for high-
resolution fingerprints.
2 Liu & Guo 2014 Gabor filter, multi
association matching
features algorithm
82.3% Accuracy Improved accuracy for
Occluded fingerprint /
binarization and thinning
required
3 Shashi et al. 2011 DWT based Fingerprint EER – 2.28% The comparison of test
11
Present day, fingerprints are an age-old method of identification and an accepted form
of evidence in criminal proceedings. The absolute nature of fingerprints is one reason for this.
No two people in the world have the same prints- not even those of identical twins. Because
of this, and the fact that fingerprints do not alter or change as one grows and ages,
fingerprints provide an infallible means of identifying a suspect (Yang, 2011). The physical
composition of one's fingerprints are the ridges on the fingers, hands, and feet. Ones “ridges”
can fall into any one of three classifications: arches, loops, and whirls. Some people have
more than one, all, or any combination of these classifications. These distinct classifications
provide scientists with a point of reference for comparison. Fingerprints from a crime scene
or evidence can be matched, or not, by identifying identical points. While experts may vary,
the most common range of acceptable points is somewhere between 12 and 20 points of
similarity (Jain & Feng, 2011).
For instance, England and Wales also use fingerprinting in their criminal justice
system for identification and evidentiary purposes. Their given standard is 16 to 20 points or
similarity. They call it the “16 point standard” because it is believed to be the minimum
compatibility needed to a zero rate of identification of fingerprints and a higher rate of court
quality identifications. Essentially, this standard prevents mistakes and provides the
prosecution with solid trace evidence that would be difficult to dispute (Zhao, Zhang, Zhang,
& Luo, 2010).
There are not many studies on fingerprinting error rates, but confidence in the
institution remains high. That, however, is not the issue, according to Kumar (2018), it is a
question raised by Dr. Jennifer Mnookin. “What matters here isn't, are your fingerprints
really different from that guy over there. The real question is, is some part of your fingerprint
sufficiently similar to some part of his that a competent examiner might mistake some part of
your print for a part of somebody else's print?” With respect to Dr. Mnookin, fingerprints as a
means of intimate description are unsurpassed by nothing short of DNA. Barring mutilation,
fingerprints cannot be changed by a person no matter what their crime or motivation (Zhao et
al., 2010). Fingerprints speak of physical presence in an environment where a crime was
committed or on the evidence used in the commission of a crime providing law enforcement
with the ability to link subjects to circumstances and the means to prove it.
Table 3: Performance Analysis of Nonminutiae feature-based fingerprint matching
S
No.
Author Year Method Accuracy/
performance
Benefits/Restrictions
1 Yang 2011 Pores, Difference of
Gaussian filtering,
pore–valley descriptor
EER – 1.18% Partial fingerprints can be
aligned/ suitable for high-
resolution fingerprints.
2 Liu & Guo 2014 Gabor filter, multi
association matching
features algorithm
82.3% Accuracy Improved accuracy for
Occluded fingerprint /
binarization and thinning
required
3 Shashi et al. 2011 DWT based Fingerprint EER – 2.28% The comparison of test
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 35
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
