Firewall: Ubuntu OS Security Design, Implementation, and Analysis
VerifiedAdded on 2022/08/27
|29
|5247
|26
Report
AI Summary
This report provides a comprehensive analysis of firewalls, particularly focusing on their implementation within the Ubuntu operating system. The study delves into the core concepts of firewall technology, including the utilization of Netfilter and IPtables as fundamental components for network security. The report examines the historical development of firewalls, their classification based on the OSI model, and the various topologies such as DMZ and VPNs. It explores the methods employed in firewall design, including the configuration of kernel settings, the creation of shell scripts, and the management of filtering rules. The experimental work and analysis section details terminal usage, rule manipulation, and application profiles. Furthermore, the report investigates the evolution of firewalls, advanced security functionalities, and the importance of firewall logs for tracking and auditing network activities. The conclusion summarizes the findings, emphasizing the critical role of firewalls in safeguarding network infrastructure and information security.

Running head: FIREWALL
FIREWALL
Name of the Student
Name of the University
Author Note
FIREWALL
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1FIREWALL
ABSTRACT
Firewalls are the most used systems of security in order to make sure networks. With the
stable development of innovation of network, network not only shows itself as a talented and
beneficial life but they are also joined by a variety of problems of network security. The
firewall is a primary technique in order to avoid the weaknesses of network and they are used
frequently in order to foresee the union that is illegal and it also isolates the network that is
situated inward from the networks those are not certain, in order to safeguard the security of
the Systems of Linux that are used in the medium and the little sized attempt.
The main content is to end the firewall capacity that depends on the working framework of
Ubuntu. The Netfilter is used as the design of firewall and the IP table. This assessment
evaluates the design of Netfilter/IPtable and the process of working of the innovation of
discovery of state that is at the point and then organizes the firewall. The functionality of the
firewall that is the firewall explore is used for checking the safety and the feasibility of the
firewall.
ABSTRACT
Firewalls are the most used systems of security in order to make sure networks. With the
stable development of innovation of network, network not only shows itself as a talented and
beneficial life but they are also joined by a variety of problems of network security. The
firewall is a primary technique in order to avoid the weaknesses of network and they are used
frequently in order to foresee the union that is illegal and it also isolates the network that is
situated inward from the networks those are not certain, in order to safeguard the security of
the Systems of Linux that are used in the medium and the little sized attempt.
The main content is to end the firewall capacity that depends on the working framework of
Ubuntu. The Netfilter is used as the design of firewall and the IP table. This assessment
evaluates the design of Netfilter/IPtable and the process of working of the innovation of
discovery of state that is at the point and then organizes the firewall. The functionality of the
firewall that is the firewall explore is used for checking the safety and the feasibility of the
firewall.

2FIREWALL
Table of Contents
1. INTRODUCTION..............................................................................................................4
2. HISTORY AND LITERATURE REVIEW.......................................................................4
2.1 Inside and Outside firewalls.............................................................................................5
2.2 Firewall Limitations.........................................................................................................5
3. Methods..............................................................................................................................6
3.1 Classification of Firewalls................................................................................................7
3.2 Firewall Topologies.........................................................................................................8
3.3 The Logs of Firewall........................................................................................................8
3.4 Initialization of Firewall...................................................................................................8
3.4.1 Configure kernel........................................................................................................9
3.4.2 Create a Shell Script..................................................................................................9
3.4.3 Delete Existing Filtering Rules.................................................................................9
3.4.4 Change Default Policy............................................................................................10
3.4.5 Reset and Stop Firewall..........................................................................................10
4. EXPERIMENTAL WORK AND ANALYSIS...............................................................10
4.1 Terminal Usage..............................................................................................................10
4.2 Working with Rules...................................................................................................12
4.3 Application Profiles.......................................................................................................17
5. Evolution of firewall........................................................................................................19
Table of Contents
1. INTRODUCTION..............................................................................................................4
2. HISTORY AND LITERATURE REVIEW.......................................................................4
2.1 Inside and Outside firewalls.............................................................................................5
2.2 Firewall Limitations.........................................................................................................5
3. Methods..............................................................................................................................6
3.1 Classification of Firewalls................................................................................................7
3.2 Firewall Topologies.........................................................................................................8
3.3 The Logs of Firewall........................................................................................................8
3.4 Initialization of Firewall...................................................................................................8
3.4.1 Configure kernel........................................................................................................9
3.4.2 Create a Shell Script..................................................................................................9
3.4.3 Delete Existing Filtering Rules.................................................................................9
3.4.4 Change Default Policy............................................................................................10
3.4.5 Reset and Stop Firewall..........................................................................................10
4. EXPERIMENTAL WORK AND ANALYSIS...............................................................10
4.1 Terminal Usage..............................................................................................................10
4.2 Working with Rules...................................................................................................12
4.3 Application Profiles.......................................................................................................17
5. Evolution of firewall........................................................................................................19
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3FIREWALL
5.1 Inspecting Your Firewall................................................................................................19
5.2 Review Advanced Security Functionalities...................................................................22
6. Conclusion........................................................................................................................22
7. BIBLIOGRAPHY............................................................................................................24
5.1 Inspecting Your Firewall................................................................................................19
5.2 Review Advanced Security Functionalities...................................................................22
6. Conclusion........................................................................................................................22
7. BIBLIOGRAPHY............................................................................................................24
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4FIREWALL
1. INTRODUCTION
With the rapid development, there are many issues of network security that are come across
in the day-to-day activities. There are large varieties of actions that break out incessantly. The
attackers use a large number of hosts in order to use the Distributed Denial of Service attack
and large numbers of hosts that are present on the network are continuing the attacks of
Distributed Denial of Service. It is a standard approach in order to prevent the attacks of
network. These are used daily in order to avoid the illegal association and then divide the
network from the networks that are not reliable. For independent organizations and
companies, there is a requirement of the firewalls of network in order to assure the security of
information of the servers. The framework of Linux is a framework that is used for open
working and it has many central points.
The primary motivation that are at the back of the channel regulations of firewalls is to make
sure the security of large business framework of Ubuntu under the working framework of
Ubuntu by using the Netfilter as then design of firewall and IPtable as a module apparatus of
space of client in order achieve the state acknowledgment capability, contrasting the attacks
of Distributed Denial of Service and records of call of the firewall of Ubuntu. This article
splits the principles of engineering of IPtable/Netfilter and the working process of the
modernism of state detection and then defines the security and sufficiency of the firewall plan
via ordering the Netfilter module of the firewall, creating the record of content, organizing
the IPtables of the firewall and many more.
2. HISTORY AND LITERATURE REVIEW
The problems of network security that has troubled the folks, the rapid development of the
network improvement of PC. The firewall is to assure the improvement of the structure and
security of network of the tools of PC or the programming systems of PC. The objects of the
1. INTRODUCTION
With the rapid development, there are many issues of network security that are come across
in the day-to-day activities. There are large varieties of actions that break out incessantly. The
attackers use a large number of hosts in order to use the Distributed Denial of Service attack
and large numbers of hosts that are present on the network are continuing the attacks of
Distributed Denial of Service. It is a standard approach in order to prevent the attacks of
network. These are used daily in order to avoid the illegal association and then divide the
network from the networks that are not reliable. For independent organizations and
companies, there is a requirement of the firewalls of network in order to assure the security of
information of the servers. The framework of Linux is a framework that is used for open
working and it has many central points.
The primary motivation that are at the back of the channel regulations of firewalls is to make
sure the security of large business framework of Ubuntu under the working framework of
Ubuntu by using the Netfilter as then design of firewall and IPtable as a module apparatus of
space of client in order achieve the state acknowledgment capability, contrasting the attacks
of Distributed Denial of Service and records of call of the firewall of Ubuntu. This article
splits the principles of engineering of IPtable/Netfilter and the working process of the
modernism of state detection and then defines the security and sufficiency of the firewall plan
via ordering the Netfilter module of the firewall, creating the record of content, organizing
the IPtables of the firewall and many more.
2. HISTORY AND LITERATURE REVIEW
The problems of network security that has troubled the folks, the rapid development of the
network improvement of PC. The firewall is to assure the improvement of the structure and
security of network of the tools of PC or the programming systems of PC. The objects of the

5FIREWALL
business firewall, the highlights those are not common of the programming those are normal,
they are directed on is not a great benefit. In this situation, it would need plan of inside
framework and the development of the firewall. The Netfilter/IPtables combines the working
systems of open source Linux in order to use a respond for the firewall. The Netfilter is run in
the work components of the Linux firewall.
The Linux is an open source innovation of firewall that has practised development.
2.1 Inside and Outside firewalls
The inner side interface of the firewall is observed regularly as they are confided in the
interface of the network, the outside of the firewall i not trusted. The class firewall that is
known as Soho that allows traffic that is going out and squares the ones that are coming. The
firewalls that are individual allow the traffic that is going out. In this way, in order to
examine the firewall, it needs to done filtering.
2.2 Firewall Limitations
It is known about firewalls that they can strengthen a strategy of network security but they
have some limitations. The main problem that climbs when the firewall are introduced is that
a large amount of time is required in order to put assets into requests in order to arrange the
approach of security properly of the network that are present nearby (Csubak and Kiss 2016).
Another problem that firewalls face is expanding and traffic that are complicated by protocol.
In spite of the fact, the goal of gag of a firewall can entirely notice at the incoming and large
number of traffic can hamper the outgoing traffic and the activity of a firewall.
Another problem, that appears is the framework those are wireless of a network situated in
the neighbourhood. In this situation, various weaknesses come up because of the objective of
association that cannot be validated as the network those are wired. Some of the firewalls
business firewall, the highlights those are not common of the programming those are normal,
they are directed on is not a great benefit. In this situation, it would need plan of inside
framework and the development of the firewall. The Netfilter/IPtables combines the working
systems of open source Linux in order to use a respond for the firewall. The Netfilter is run in
the work components of the Linux firewall.
The Linux is an open source innovation of firewall that has practised development.
2.1 Inside and Outside firewalls
The inner side interface of the firewall is observed regularly as they are confided in the
interface of the network, the outside of the firewall i not trusted. The class firewall that is
known as Soho that allows traffic that is going out and squares the ones that are coming. The
firewalls that are individual allow the traffic that is going out. In this way, in order to
examine the firewall, it needs to done filtering.
2.2 Firewall Limitations
It is known about firewalls that they can strengthen a strategy of network security but they
have some limitations. The main problem that climbs when the firewall are introduced is that
a large amount of time is required in order to put assets into requests in order to arrange the
approach of security properly of the network that are present nearby (Csubak and Kiss 2016).
Another problem that firewalls face is expanding and traffic that are complicated by protocol.
In spite of the fact, the goal of gag of a firewall can entirely notice at the incoming and large
number of traffic can hamper the outgoing traffic and the activity of a firewall.
Another problem, that appears is the framework those are wireless of a network situated in
the neighbourhood. In this situation, various weaknesses come up because of the objective of
association that cannot be validated as the network those are wired. Some of the firewalls
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6FIREWALL
deploy the problems of encryption. The packets of data that are encrypted deploy headers yet
the firewalls demonstrate limitations in dealing and perceiving with the data packets.
The File transfer protocol for example does the work by initial association from the client to
the server and vice versa. The firewalls know the way of handling those protocols but several
tasks reside as dangerous and vulnerable.
3. Methods
The firewalls are the methods of security that are planned in order to meet the objectives
those are unambiguous. At the start, the topology of network of a company requires to be
configured together in order to pass the traffic via the firewalls. The point of choking hides
the network through the approaches of security, thus, outlining the packets that are permitted
or need to be dropped. The firewall can hide an entire network and it can create a barricade
for the hackers and the attempts of hacking The operations of firewall depends on the
unambiguous controls that actualizes the structure of the network in order to do the
characteristics. These administrations deploy control of service, behaviour, direction and the
user.
The control of management is a functionality of firewall that selects the administrators that
are permitted admittance from outside of the network to the outside and vice versa. The
control of bearing deals with the traffic that is going out or coming in. This type of control
evaluates the packet’s limit, the type of administration this packet manages, the terminal that
try to reach or select to decay or permit the stream of data packets (Diekmann et al 2016).
The control of client is a functionality of firewall that controls the right to entry to the clients
that work inside the network of an organization. Sometimes, on the clients that enter an
internal structure of network from exterior.
deploy the problems of encryption. The packets of data that are encrypted deploy headers yet
the firewalls demonstrate limitations in dealing and perceiving with the data packets.
The File transfer protocol for example does the work by initial association from the client to
the server and vice versa. The firewalls know the way of handling those protocols but several
tasks reside as dangerous and vulnerable.
3. Methods
The firewalls are the methods of security that are planned in order to meet the objectives
those are unambiguous. At the start, the topology of network of a company requires to be
configured together in order to pass the traffic via the firewalls. The point of choking hides
the network through the approaches of security, thus, outlining the packets that are permitted
or need to be dropped. The firewall can hide an entire network and it can create a barricade
for the hackers and the attempts of hacking The operations of firewall depends on the
unambiguous controls that actualizes the structure of the network in order to do the
characteristics. These administrations deploy control of service, behaviour, direction and the
user.
The control of management is a functionality of firewall that selects the administrators that
are permitted admittance from outside of the network to the outside and vice versa. The
control of bearing deals with the traffic that is going out or coming in. This type of control
evaluates the packet’s limit, the type of administration this packet manages, the terminal that
try to reach or select to decay or permit the stream of data packets (Diekmann et al 2016).
The control of client is a functionality of firewall that controls the right to entry to the clients
that work inside the network of an organization. Sometimes, on the clients that enter an
internal structure of network from exterior.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
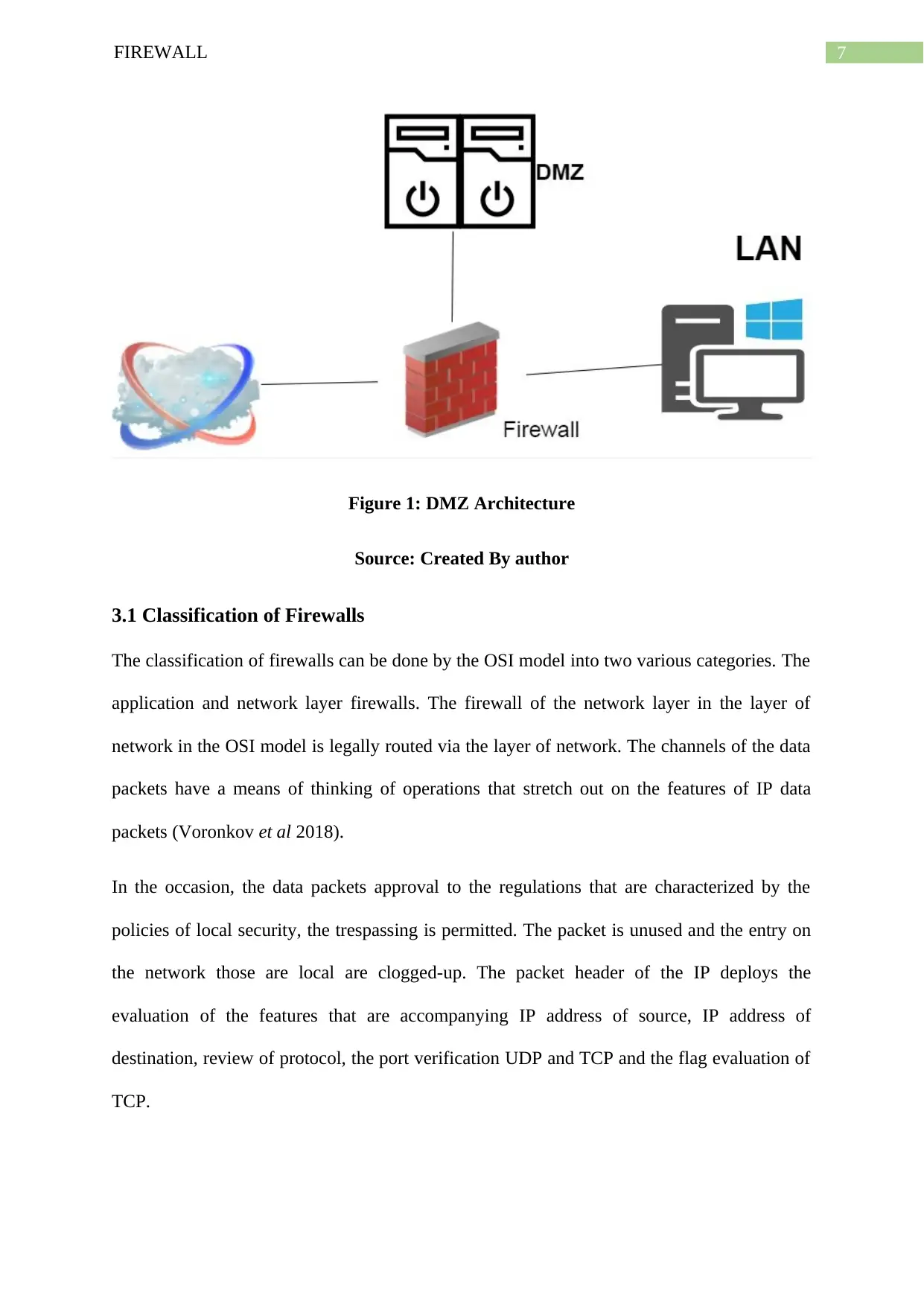
7FIREWALL
Figure 1: DMZ Architecture
Source: Created By author
3.1 Classification of Firewalls
The classification of firewalls can be done by the OSI model into two various categories. The
application and network layer firewalls. The firewall of the network layer in the layer of
network in the OSI model is legally routed via the layer of network. The channels of the data
packets have a means of thinking of operations that stretch out on the features of IP data
packets (Voronkov et al 2018).
In the occasion, the data packets approval to the regulations that are characterized by the
policies of local security, the trespassing is permitted. The packet is unused and the entry on
the network those are local are clogged-up. The packet header of the IP deploys the
evaluation of the features that are accompanying IP address of source, IP address of
destination, review of protocol, the port verification UDP and TCP and the flag evaluation of
TCP.
Figure 1: DMZ Architecture
Source: Created By author
3.1 Classification of Firewalls
The classification of firewalls can be done by the OSI model into two various categories. The
application and network layer firewalls. The firewall of the network layer in the layer of
network in the OSI model is legally routed via the layer of network. The channels of the data
packets have a means of thinking of operations that stretch out on the features of IP data
packets (Voronkov et al 2018).
In the occasion, the data packets approval to the regulations that are characterized by the
policies of local security, the trespassing is permitted. The packet is unused and the entry on
the network those are local are clogged-up. The packet header of the IP deploys the
evaluation of the features that are accompanying IP address of source, IP address of
destination, review of protocol, the port verification UDP and TCP and the flag evaluation of
TCP.

8FIREWALL
The channels of the packet are separated in to various categories of filtering. The first is the
stateful and the next is the stateless. In the filtering of packets those are stateless, the firewall
takes the decision to permit or disallow a packet by evaluating the features of the packets.
The packet filtering those are stateful is an upgraded version of the stateless filtering. The
main comparison is that it has unambiguous features of the protocol of TCP/IP.
The filtering of packets those are stateful go together with the filtering of packet hose are
dynamic, an help in which the firewall has the capability to ping the IP those are at the source
of the data packets, which is under evaluation and the examination is very good. There are
also the firewalls those are known as the Higher-layer firewalls and in this category of
firewalls, it can monitor or track the traffic of the network on the model of OSI. The
gateways those are Circuit Level and Application Level find out deployment in this group of
firewalls. The filtering of packets is a type of firewall that has an extra operation on the Layer
of Session of the OSI model. This memorizes the surveillance of handshaking that are present
between the packets for the demand in order to evaluate and select if the solicitation is legal
or illegal (Zerkane et al 2016).
3.2 Firewall Topologies
There are different kinds of topologies that can be used in order to install a firewall. The most
essential ones are the DMZ, NAT and the virtual private networks. The Demilitarized Zone is
a topology of firewall in which a detachable network is added in between the interior and the
exterior of the network (Dadheech, Choudhary and Bhatia 2018). With the help of the
architecture, the DMZ directs to provide the exterior visitors any inbound management, for
example, a server of Web. The virtual private networks are the networks those are shared and
these networks work on the networks those are open. On the machines those operate on
The channels of the packet are separated in to various categories of filtering. The first is the
stateful and the next is the stateless. In the filtering of packets those are stateless, the firewall
takes the decision to permit or disallow a packet by evaluating the features of the packets.
The packet filtering those are stateful is an upgraded version of the stateless filtering. The
main comparison is that it has unambiguous features of the protocol of TCP/IP.
The filtering of packets those are stateful go together with the filtering of packet hose are
dynamic, an help in which the firewall has the capability to ping the IP those are at the source
of the data packets, which is under evaluation and the examination is very good. There are
also the firewalls those are known as the Higher-layer firewalls and in this category of
firewalls, it can monitor or track the traffic of the network on the model of OSI. The
gateways those are Circuit Level and Application Level find out deployment in this group of
firewalls. The filtering of packets is a type of firewall that has an extra operation on the Layer
of Session of the OSI model. This memorizes the surveillance of handshaking that are present
between the packets for the demand in order to evaluate and select if the solicitation is legal
or illegal (Zerkane et al 2016).
3.2 Firewall Topologies
There are different kinds of topologies that can be used in order to install a firewall. The most
essential ones are the DMZ, NAT and the virtual private networks. The Demilitarized Zone is
a topology of firewall in which a detachable network is added in between the interior and the
exterior of the network (Dadheech, Choudhary and Bhatia 2018). With the help of the
architecture, the DMZ directs to provide the exterior visitors any inbound management, for
example, a server of Web. The virtual private networks are the networks those are shared and
these networks work on the networks those are open. On the machines those operate on
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9FIREWALL
VPNs, they direct to exchange the packets those are encrypted via the network and they are
decoded just in the time they reach the end of the network (Csubak and Kiss 2016).
3.3 The Logs of Firewall
A log is known as several operations of the objects those are defined earlier of framework
and it is a collection of outputs of operations that arrange chronologically. Every document of
log records various frameworks. A log is records that are present in a book and the client can
read the logs legally. It includes a stamp of period and other kinds of information and they are
of one type to the subsystem (Caprolu, Raponi and Di Pietro 2019). The log is essential for
the security of the framework. The client easily can check the reason of the harm that has
happened and can recuperate the hints that are left by a hacker. The main components of log
are mainly tracking and auditing.
3.4 Initialization of Firewall
The starting processes of firewall mainly have 5 stages. They are described below:
3.4.1 Configure kernel
As the table of IP is separated into the component of kernel and the segments program that
belongs to the management of the client layer, the install of the table of IP consists of
compiling and installing of kernel of Linux and the program that belongs to the level of
client. This article uses Linux-3.6.tar.bz2 in order to build up the Netfilter and then construct
the framework of Linux. The installing of the table of IP consists of compiling and installing
of the kernel of Linux and the program that belongs to the level of client.
3.4.2 Create a Shell Script
The firewall of Linux consists of the Tables of IP and its command lines and the lines of
commands are run only once. The firewalls have different regulations in order to use them.
The regulations of filtering of firewalls are composed together in to the scripts of shell
VPNs, they direct to exchange the packets those are encrypted via the network and they are
decoded just in the time they reach the end of the network (Csubak and Kiss 2016).
3.3 The Logs of Firewall
A log is known as several operations of the objects those are defined earlier of framework
and it is a collection of outputs of operations that arrange chronologically. Every document of
log records various frameworks. A log is records that are present in a book and the client can
read the logs legally. It includes a stamp of period and other kinds of information and they are
of one type to the subsystem (Caprolu, Raponi and Di Pietro 2019). The log is essential for
the security of the framework. The client easily can check the reason of the harm that has
happened and can recuperate the hints that are left by a hacker. The main components of log
are mainly tracking and auditing.
3.4 Initialization of Firewall
The starting processes of firewall mainly have 5 stages. They are described below:
3.4.1 Configure kernel
As the table of IP is separated into the component of kernel and the segments program that
belongs to the management of the client layer, the install of the table of IP consists of
compiling and installing of kernel of Linux and the program that belongs to the level of
client. This article uses Linux-3.6.tar.bz2 in order to build up the Netfilter and then construct
the framework of Linux. The installing of the table of IP consists of compiling and installing
of the kernel of Linux and the program that belongs to the level of client.
3.4.2 Create a Shell Script
The firewall of Linux consists of the Tables of IP and its command lines and the lines of
commands are run only once. The firewalls have different regulations in order to use them.
The regulations of filtering of firewalls are composed together in to the scripts of shell
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10FIREWALL
programming and it is then saved in the way for the /and so on/rc.d/rc.fw and permission for
the shell script are set.
[root@localhost linux-3.6]# touch/and so forth/rc.d/rc.fw
[root@localhost linux-3.6]# chown root:root/and so forth/rc.d/rc.fw
[root@localhost linux-3.6]# chmod u=rwx/and so forth/rc.d/rc.fw
3.4.3 Delete Existing Filtering Rules
When the arrays of channels are characterized, the first step is to delete the regulations that
already exist in the chain of standards. If this is not done then the regulations that are added
recently will get added to the rules that already exist. This will make the data packets to
match with the filtering that is already existing before matching with the regulations of
channel to the settings those are latest. This will affect the filtering of packets and the result
that will given to us will be incorrect.
3.4.4 Change Default Policy
The policy of the default firewall is to delete a message. After using this strategy, in adding
together to data packets permitted expressly by the regulations, the other packets of data will
be deleted. Differentiated to the packets that are kept as default, the policy that constructs the
packets of data should be deleted and it is successful and very safe.
3.4.5 Reset and Stop Firewall
There are some cases where the use of firewall, should be stopped not permanently but
temporarily. The firewall will stop working permanently when stop parameters will be added
to the scripts of firewall.
programming and it is then saved in the way for the /and so on/rc.d/rc.fw and permission for
the shell script are set.
[root@localhost linux-3.6]# touch/and so forth/rc.d/rc.fw
[root@localhost linux-3.6]# chown root:root/and so forth/rc.d/rc.fw
[root@localhost linux-3.6]# chmod u=rwx/and so forth/rc.d/rc.fw
3.4.3 Delete Existing Filtering Rules
When the arrays of channels are characterized, the first step is to delete the regulations that
already exist in the chain of standards. If this is not done then the regulations that are added
recently will get added to the rules that already exist. This will make the data packets to
match with the filtering that is already existing before matching with the regulations of
channel to the settings those are latest. This will affect the filtering of packets and the result
that will given to us will be incorrect.
3.4.4 Change Default Policy
The policy of the default firewall is to delete a message. After using this strategy, in adding
together to data packets permitted expressly by the regulations, the other packets of data will
be deleted. Differentiated to the packets that are kept as default, the policy that constructs the
packets of data should be deleted and it is successful and very safe.
3.4.5 Reset and Stop Firewall
There are some cases where the use of firewall, should be stopped not permanently but
temporarily. The firewall will stop working permanently when stop parameters will be added
to the scripts of firewall.

11FIREWALL
4. EXPERIMENTAL WORK AND ANALYSIS
Ubuntu implements the firewall that it has, it called as ufw, and the full form of ufw is
uncomplicated firewall. The firewall that is uncomplicated is very easy to use for the
commands of IPtables of Linux. The ufw can be easily controlled by an interface those are
graphical. The firewall of Ubuntu is planned in such a way that it can execute the activities of
firewall without the tables of IP. It does not provide all the commands of the benchmark
IPtables but it is not complex.
4.1 Terminal Usage
The firewall is not enabled from the first. In order to start the firewall, the command must be
executed from some terminals.
sudo ufw enable
It is not required to enable the firewall first. The user can add regulations even if the firewall
not online.
4. EXPERIMENTAL WORK AND ANALYSIS
Ubuntu implements the firewall that it has, it called as ufw, and the full form of ufw is
uncomplicated firewall. The firewall that is uncomplicated is very easy to use for the
commands of IPtables of Linux. The ufw can be easily controlled by an interface those are
graphical. The firewall of Ubuntu is planned in such a way that it can execute the activities of
firewall without the tables of IP. It does not provide all the commands of the benchmark
IPtables but it is not complex.
4.1 Terminal Usage
The firewall is not enabled from the first. In order to start the firewall, the command must be
executed from some terminals.
sudo ufw enable
It is not required to enable the firewall first. The user can add regulations even if the firewall
not online.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 29
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





