Network Security and Intrusion Detection Module: Firewall Placement
VerifiedAdded on 2022/11/14
|9
|1822
|431
Report
AI Summary
This report focuses on firewall placement within the network security infrastructure of ABC Company, a Sri Lankan organization with a head office in Colombo and multiple branches connected via MPLS. The assessment addresses the strategic placement of firewalls to secure the company's data center and internal network, considering the various connections, including branches, a DR site, web servers, and mobile API access. The report analyzes the current network framework and provides recommendations for firewall positioning to control access to the internal network, emphasizing the creation of security zones and the application of access control lists. A network diagram is presented to illustrate the network devices and hardware used in the MPLS network, and a justification is provided for the placement of firewalls to manage internal services. The report also explores additional security mechanisms like VPN architecture for secure data transmission between the headquarters and branches, ensuring confidentiality, integrity, and authenticity. The conclusion highlights the importance of firewall placement at the network edge, the creation of multiple zones, and the implementation of other defense mechanisms to enhance overall network security. The report also emphasizes the use of QoS options in the network and the MPLS network's ability to connect thousands of sites.

Running head: NETWORK SECURITY AND INTRUSION DETECTION MODULE
Network Security and Intrusion Detection Module
Name of the Student
Name of the University
Authors’ Note
Network Security and Intrusion Detection Module
Name of the Student
Name of the University
Authors’ Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK SECURITY AND INTRUSION DETECTION MODULE
Executive Summary
The report is prepared for ABC Company located in Sri Lanka for expansion of the current
organization and connect its head office in Colombo with the other branches. Since the company
has the datacenter in its headquarters the security of the network is an important factor and thus
multiple firewalls are needed to be deployed such that the access of the internal network of the
company can be controlled. An analysis is made on the current network framework of the
organization and suggestion is given for placing the firewall in the right position such that the
security of the network can be imported. A network diagram is prepared showing all the network
device and hardware that are used for the development of the MPLS network and a justification
is given regarding the placement for the management of the internal services for the company.
NETWORK SECURITY AND INTRUSION DETECTION MODULE
Executive Summary
The report is prepared for ABC Company located in Sri Lanka for expansion of the current
organization and connect its head office in Colombo with the other branches. Since the company
has the datacenter in its headquarters the security of the network is an important factor and thus
multiple firewalls are needed to be deployed such that the access of the internal network of the
company can be controlled. An analysis is made on the current network framework of the
organization and suggestion is given for placing the firewall in the right position such that the
security of the network can be imported. A network diagram is prepared showing all the network
device and hardware that are used for the development of the MPLS network and a justification
is given regarding the placement for the management of the internal services for the company.

2
NETWORK SECURITY AND INTRUSION DETECTION MODULE
Table of Contents
Introduction......................................................................................................................................3
Firewall Placement..........................................................................................................................3
Network Diagram............................................................................................................................5
Justification......................................................................................................................................5
Conclusion.......................................................................................................................................6
Bibliography....................................................................................................................................7
NETWORK SECURITY AND INTRUSION DETECTION MODULE
Table of Contents
Introduction......................................................................................................................................3
Firewall Placement..........................................................................................................................3
Network Diagram............................................................................................................................5
Justification......................................................................................................................................5
Conclusion.......................................................................................................................................6
Bibliography....................................................................................................................................7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORK SECURITY AND INTRUSION DETECTION MODULE
Introduction
The company ABC had its head quarter in Colombo and it has 6 different departments
and about 1000 employees working in the company. The branch offices of the company are
connected using MPLS connection and an appropriate WAN technology is needed to be applied
for management of bandwidth and connectivity such that a disaster recovery needs are fulfilled.
For connecting the DR site an appropriate internet service provider is needed to be selected and
fiber optics link is needed to be used for the connection. Both the DR site and headquarter should
have DMZ zone and same service enabled. The firewalls deployed in the network is needed to be
configured with NAT such that the server and the public IP address is present on the firewall.
The report is prepared for describing the area where the firewall can be placed and such that the
unauthorized access to the company’s internal network can be blocked and security can be
improved.
Firewall Placement
For the company the placement of the firewall in the right position is an important factor
for such that the vulnerability of the network can be reduced. The perimeter security needs and
the network devices that are needed to be secured is needed to be understood. The data center
network contains different types of network equipment’s and servers that are create complex data
flows and thus specific profile for the network traffic cannot be created. The improper
deployment of the firewall can affect the performance of the network since it would affect the
raw bandwidth (Eslava, Rojas & Pineda, 2015). The traffic requirement for the multi node
application and requirement for server virtualization is evaluated. The firewall is needed to be
installed at the entry/exit point of the network such that the interface of the firewall can act as the
NETWORK SECURITY AND INTRUSION DETECTION MODULE
Introduction
The company ABC had its head quarter in Colombo and it has 6 different departments
and about 1000 employees working in the company. The branch offices of the company are
connected using MPLS connection and an appropriate WAN technology is needed to be applied
for management of bandwidth and connectivity such that a disaster recovery needs are fulfilled.
For connecting the DR site an appropriate internet service provider is needed to be selected and
fiber optics link is needed to be used for the connection. Both the DR site and headquarter should
have DMZ zone and same service enabled. The firewalls deployed in the network is needed to be
configured with NAT such that the server and the public IP address is present on the firewall.
The report is prepared for describing the area where the firewall can be placed and such that the
unauthorized access to the company’s internal network can be blocked and security can be
improved.
Firewall Placement
For the company the placement of the firewall in the right position is an important factor
for such that the vulnerability of the network can be reduced. The perimeter security needs and
the network devices that are needed to be secured is needed to be understood. The data center
network contains different types of network equipment’s and servers that are create complex data
flows and thus specific profile for the network traffic cannot be created. The improper
deployment of the firewall can affect the performance of the network since it would affect the
raw bandwidth (Eslava, Rojas & Pineda, 2015). The traffic requirement for the multi node
application and requirement for server virtualization is evaluated. The firewall is needed to be
installed at the entry/exit point of the network such that the interface of the firewall can act as the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORK SECURITY AND INTRUSION DETECTION MODULE
doorway for entering and leaving the network. Security zones are needed to be defined and
security policy is needed to be created for the management of inter zone traffic. The creation of
the security zone help the network administrator to group the network address by creating
multiple subnet for each of the department (Addis et al., 2015). The access of the users of the
different subnet is managed with the application of access control list.
Apart from placing the firewall there are different other security mechanism that can be
applied for securing the network. The application of VPN architecture by creating a site to site
VPN for connecting the different branches of the organization can help in securely transmitting
data between the head quarter and the branch by using the public internet. A secure tunnel is
created that encapsulates each of the packet and can help in maintaining confidentiality, integrity
and authenticity for the data packet.
NETWORK SECURITY AND INTRUSION DETECTION MODULE
doorway for entering and leaving the network. Security zones are needed to be defined and
security policy is needed to be created for the management of inter zone traffic. The creation of
the security zone help the network administrator to group the network address by creating
multiple subnet for each of the department (Addis et al., 2015). The access of the users of the
different subnet is managed with the application of access control list.
Apart from placing the firewall there are different other security mechanism that can be
applied for securing the network. The application of VPN architecture by creating a site to site
VPN for connecting the different branches of the organization can help in securely transmitting
data between the head quarter and the branch by using the public internet. A secure tunnel is
created that encapsulates each of the packet and can help in maintaining confidentiality, integrity
and authenticity for the data packet.
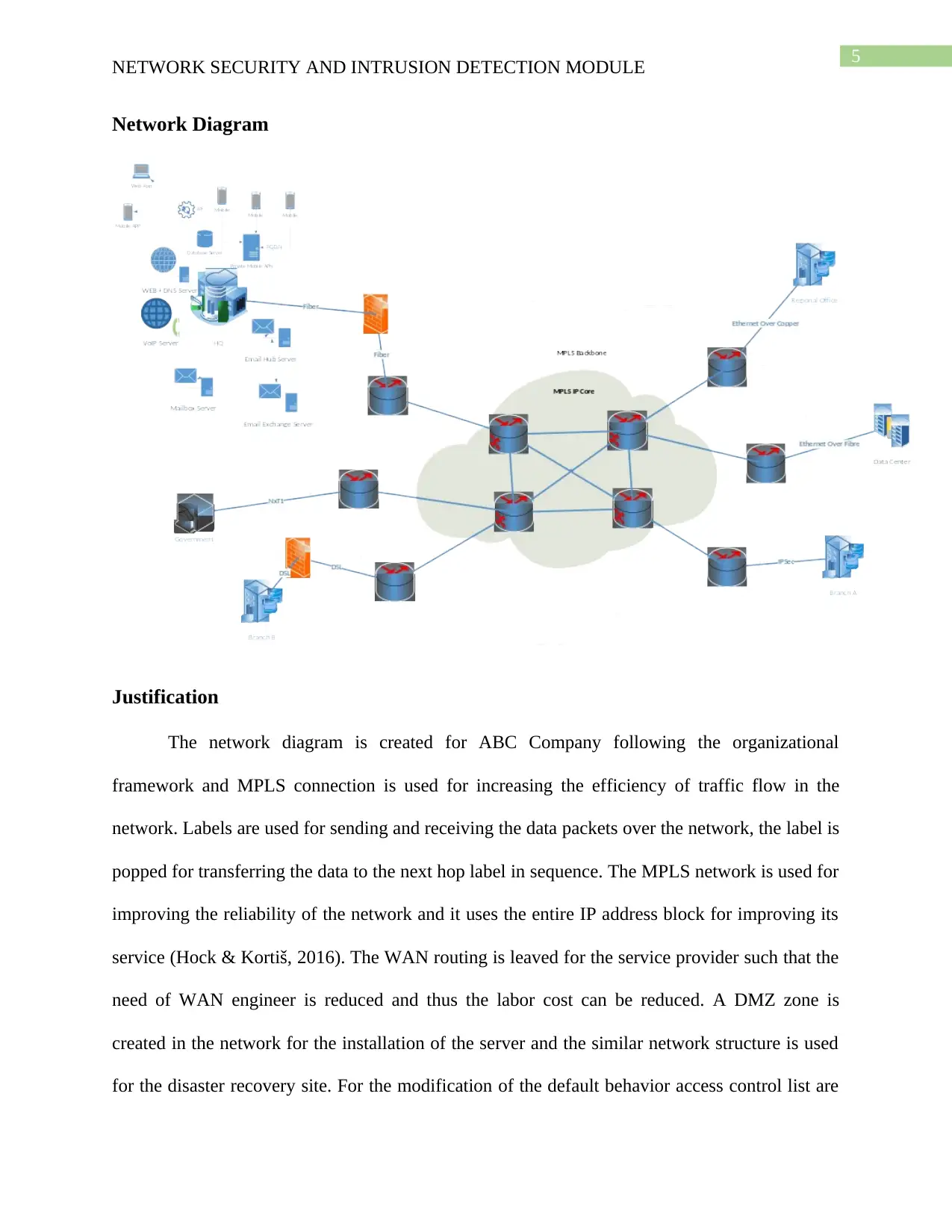
5
NETWORK SECURITY AND INTRUSION DETECTION MODULE
Network Diagram
Justification
The network diagram is created for ABC Company following the organizational
framework and MPLS connection is used for increasing the efficiency of traffic flow in the
network. Labels are used for sending and receiving the data packets over the network, the label is
popped for transferring the data to the next hop label in sequence. The MPLS network is used for
improving the reliability of the network and it uses the entire IP address block for improving its
service (Hock & Kortiš, 2016). The WAN routing is leaved for the service provider such that the
need of WAN engineer is reduced and thus the labor cost can be reduced. A DMZ zone is
created in the network for the installation of the server and the similar network structure is used
for the disaster recovery site. For the modification of the default behavior access control list are
NETWORK SECURITY AND INTRUSION DETECTION MODULE
Network Diagram
Justification
The network diagram is created for ABC Company following the organizational
framework and MPLS connection is used for increasing the efficiency of traffic flow in the
network. Labels are used for sending and receiving the data packets over the network, the label is
popped for transferring the data to the next hop label in sequence. The MPLS network is used for
improving the reliability of the network and it uses the entire IP address block for improving its
service (Hock & Kortiš, 2016). The WAN routing is leaved for the service provider such that the
need of WAN engineer is reduced and thus the labor cost can be reduced. A DMZ zone is
created in the network for the installation of the server and the similar network structure is used
for the disaster recovery site. For the modification of the default behavior access control list are
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORK SECURITY AND INTRUSION DETECTION MODULE
used. A DMZ can also be used for publishing external services with the help of the different
types of server (Datta et al., 2018). The design provides an advantage that the traffic is need to
pass through the firewall and thus the administering burden can be minimized. The firewall is
needed to work in routed mode and it can be divided into logical firewall for acting as a separate
firewall.
Conclusion
From the above report it can be concluded that the placement of the firewall in the
network is essential for improving the security of the network. The firewall is designed for
protecting the network resources inside the network and it is needed to be deployed at the edge
of the network and multiple zones are needed to be created. At least two zones are needed to be
created and they can be referred to as inside and outside and this it can be used for blocking the
network traffic coming from outside. By default the outside traffic is blocked and the inside
traffic are allowed to communicate with each other. The server whose access for the outside user
is restricted are kept in separate VLAN such that the access can be controlled from a central
location and the fault in the network can be easily troubleshoot. A service level agreement is
used for ensuring that speed and class of service would never drop like other broadband services.
The network is developed such that it can be expanded to connect thousands of sites in future
and meet the growth of the company. The MPLS network also help in interconnecting the data
center of head office with the branches located in different geographical network. It is capable of
handling any type of connection such as video or voice and allows VoIP to be used for
communicating with the internal staffs. QoS option is made available in the network such that
there is no latency for the voice packets due to congestion or collision in the network.
NETWORK SECURITY AND INTRUSION DETECTION MODULE
used. A DMZ can also be used for publishing external services with the help of the different
types of server (Datta et al., 2018). The design provides an advantage that the traffic is need to
pass through the firewall and thus the administering burden can be minimized. The firewall is
needed to work in routed mode and it can be divided into logical firewall for acting as a separate
firewall.
Conclusion
From the above report it can be concluded that the placement of the firewall in the
network is essential for improving the security of the network. The firewall is designed for
protecting the network resources inside the network and it is needed to be deployed at the edge
of the network and multiple zones are needed to be created. At least two zones are needed to be
created and they can be referred to as inside and outside and this it can be used for blocking the
network traffic coming from outside. By default the outside traffic is blocked and the inside
traffic are allowed to communicate with each other. The server whose access for the outside user
is restricted are kept in separate VLAN such that the access can be controlled from a central
location and the fault in the network can be easily troubleshoot. A service level agreement is
used for ensuring that speed and class of service would never drop like other broadband services.
The network is developed such that it can be expanded to connect thousands of sites in future
and meet the growth of the company. The MPLS network also help in interconnecting the data
center of head office with the branches located in different geographical network. It is capable of
handling any type of connection such as video or voice and allows VoIP to be used for
communicating with the internal staffs. QoS option is made available in the network such that
there is no latency for the voice packets due to congestion or collision in the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
NETWORK SECURITY AND INTRUSION DETECTION MODULE
Bibliography
Addis, B., Belabed, D., Bouet, M., & Secci, S. (2015, October). Virtual network functions
placement and routing optimization. In 2015 IEEE 4th International Conference on
Cloud Networking (CloudNet) (pp. 171-177). IEEE.
Buczak, A. L., & Guven, E. (2015). A survey of data mining and machine learning methods for
cyber security intrusion detection. IEEE Communications Surveys & Tutorials, 18(2),
1153-1176.
Datta, R., Choi, S., Chowdhary, A., & Park, Y. (2018, October). P4Guard: Designing P4 Based
Firewall. In MILCOM 2018-2018 IEEE Military Communications Conference
(MILCOM)(pp. 1-6). IEEE.
Eslava, H., Rojas, L. A., & Pineda, D. (2015). An algorithm for optimal firewall placement in
iec61850 substations. Journal of Power and Energy Engineering, 3(04), 16.
Hock, F., & Kortiš, P. (2016, November). Design, implementation and monitoring of the firewall
system for a DNS server protection. In 2016 International Conference on Emerging
eLearning Technologies and Applications (ICETA)(pp. 91-96). IEEE.
Javaid, A., Niyaz, Q., Sun, W., & Alam, M. (2016, May). A deep learning approach for network
intrusion detection system. In Proceedings of the 9th EAI International Conference on
Bio-inspired Information and Communications Technologies (formerly BIONETICS) (pp.
21-26). ICST (Institute for Computer Sciences, Social-Informatics and
Telecommunications Engineering).
NETWORK SECURITY AND INTRUSION DETECTION MODULE
Bibliography
Addis, B., Belabed, D., Bouet, M., & Secci, S. (2015, October). Virtual network functions
placement and routing optimization. In 2015 IEEE 4th International Conference on
Cloud Networking (CloudNet) (pp. 171-177). IEEE.
Buczak, A. L., & Guven, E. (2015). A survey of data mining and machine learning methods for
cyber security intrusion detection. IEEE Communications Surveys & Tutorials, 18(2),
1153-1176.
Datta, R., Choi, S., Chowdhary, A., & Park, Y. (2018, October). P4Guard: Designing P4 Based
Firewall. In MILCOM 2018-2018 IEEE Military Communications Conference
(MILCOM)(pp. 1-6). IEEE.
Eslava, H., Rojas, L. A., & Pineda, D. (2015). An algorithm for optimal firewall placement in
iec61850 substations. Journal of Power and Energy Engineering, 3(04), 16.
Hock, F., & Kortiš, P. (2016, November). Design, implementation and monitoring of the firewall
system for a DNS server protection. In 2016 International Conference on Emerging
eLearning Technologies and Applications (ICETA)(pp. 91-96). IEEE.
Javaid, A., Niyaz, Q., Sun, W., & Alam, M. (2016, May). A deep learning approach for network
intrusion detection system. In Proceedings of the 9th EAI International Conference on
Bio-inspired Information and Communications Technologies (formerly BIONETICS) (pp.
21-26). ICST (Institute for Computer Sciences, Social-Informatics and
Telecommunications Engineering).

8
NETWORK SECURITY AND INTRUSION DETECTION MODULE
Kim, J., Kim, J., Thu, H. L. T., & Kim, H. (2016, February). Long short term memory recurrent
neural network classifier for intrusion detection. In 2016 International Conference on
Platform Technology and Service (PlatCon) (pp. 1-5). IEEE.
Moustafa, N., & Slay, J. (2015, November). UNSW-NB15: a comprehensive data set for network
intrusion detection systems (UNSW-NB15 network data set). In 2015 military
communications and information systems conference (MilCIS)(pp. 1-6). IEEE.
Snapp, S. R., Brentano, J., Dias, G., Goan, T. L., Heberlein, L. T., Ho, C. L., & Levitt, K. N.
(2017). DIDS (distributed intrusion detection system)-motivation, architecture, and an
early prototype.
Song, H. M., Kim, H. R., & Kim, H. K. (2016, January). Intrusion detection system based on the
analysis of time intervals of CAN messages for in-vehicle network. In 2016 international
conference on information networking (ICOIN)(pp. 63-68). IEEE.
Tajpuriya, R., Gupta, V., & Rajput, I. J. (2017). A systematic approach for highly secure
framework for virtual firewall. International Journal For Technological Research In
Engineering, 4(8), 2347-4718.
Tang, T. A., Mhamdi, L., McLernon, D., Zaidi, S. A. R., & Ghogho, M. (2016, October). Deep
learning approach for network intrusion detection in software defined networking.
In 2016 International Conference on Wireless Networks and Mobile Communications
(WINCOM) (pp. 258-263). IEEE.
NETWORK SECURITY AND INTRUSION DETECTION MODULE
Kim, J., Kim, J., Thu, H. L. T., & Kim, H. (2016, February). Long short term memory recurrent
neural network classifier for intrusion detection. In 2016 International Conference on
Platform Technology and Service (PlatCon) (pp. 1-5). IEEE.
Moustafa, N., & Slay, J. (2015, November). UNSW-NB15: a comprehensive data set for network
intrusion detection systems (UNSW-NB15 network data set). In 2015 military
communications and information systems conference (MilCIS)(pp. 1-6). IEEE.
Snapp, S. R., Brentano, J., Dias, G., Goan, T. L., Heberlein, L. T., Ho, C. L., & Levitt, K. N.
(2017). DIDS (distributed intrusion detection system)-motivation, architecture, and an
early prototype.
Song, H. M., Kim, H. R., & Kim, H. K. (2016, January). Intrusion detection system based on the
analysis of time intervals of CAN messages for in-vehicle network. In 2016 international
conference on information networking (ICOIN)(pp. 63-68). IEEE.
Tajpuriya, R., Gupta, V., & Rajput, I. J. (2017). A systematic approach for highly secure
framework for virtual firewall. International Journal For Technological Research In
Engineering, 4(8), 2347-4718.
Tang, T. A., Mhamdi, L., McLernon, D., Zaidi, S. A. R., & Ghogho, M. (2016, October). Deep
learning approach for network intrusion detection in software defined networking.
In 2016 International Conference on Wireless Networks and Mobile Communications
(WINCOM) (pp. 258-263). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




