Firewall Design and Implementation: Bastion Host and DMZ Architectures
VerifiedAdded on 2022/10/06
|17
|1394
|368
Report
AI Summary
This report delves into the critical aspects of firewall design and implementation, focusing on enhancing network security. It begins by establishing the fundamental concepts of information security, emphasizing the importance of firewalls in protecting data confidentiality, integrity, and availability. The report explores different types of firewalls, including packet filtering, stateful inspection, application-level gateways, and next-generation firewalls, highlighting their software-defined nature and hardware implementations like bastion hosts and demilitarized zones (DMZ). The core of the report details the design and configuration of a bastion host architecture using iptables in a Linux environment, including SSH hardening techniques to fortify server security. Furthermore, it introduces a more robust DMZ architecture, discussing its three zones: trusted, DMZ, and untrusted networks, and provides practical insights into configuring an internal firewall using OPNsense. The report concludes by emphasizing the importance of firewalls in preventing unauthorized access, reducing replay attacks, DDoS attacks, and spoofing attempts, and advocates for the use of DMZ and application-level firewalls to maintain information security.
1 out of 17




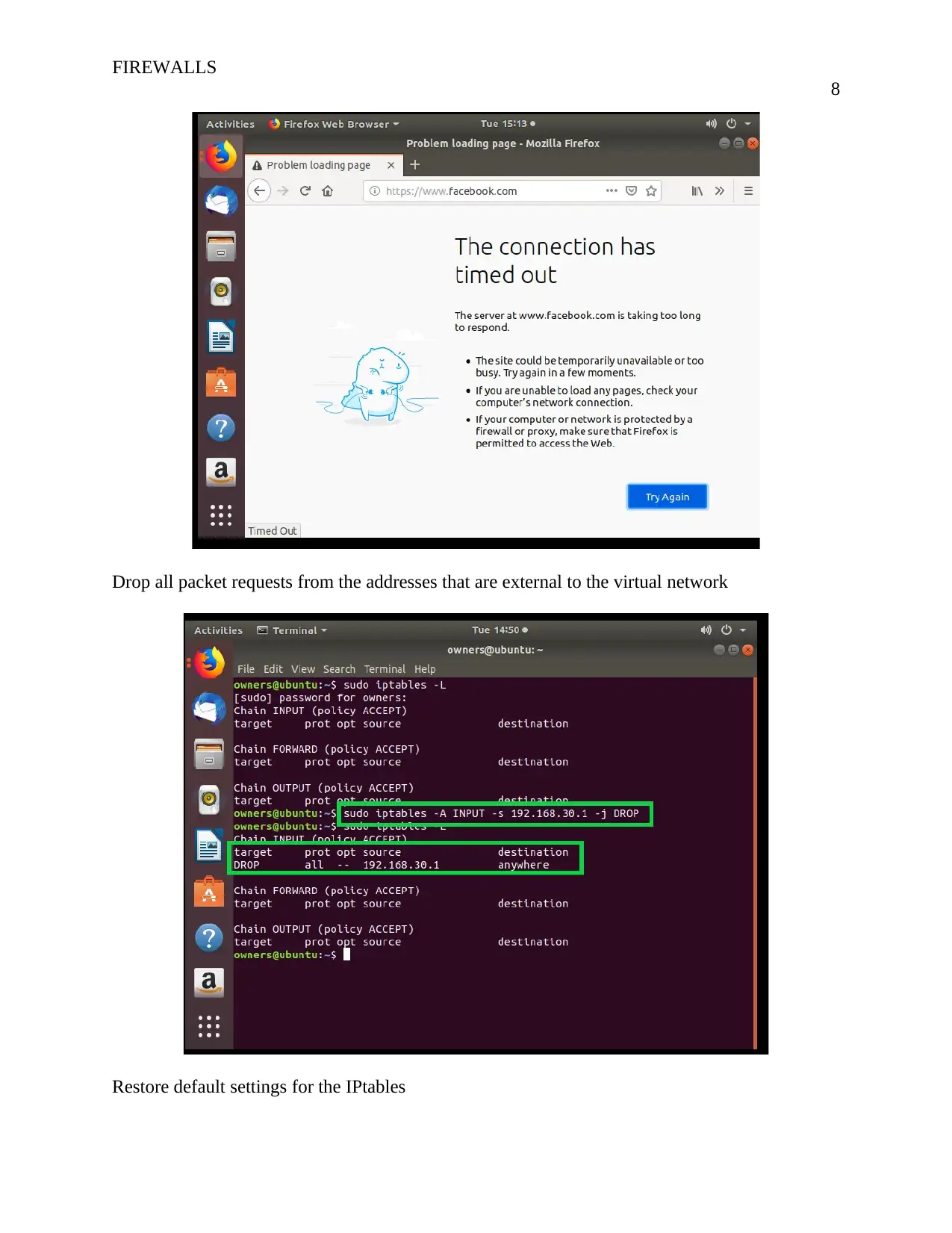
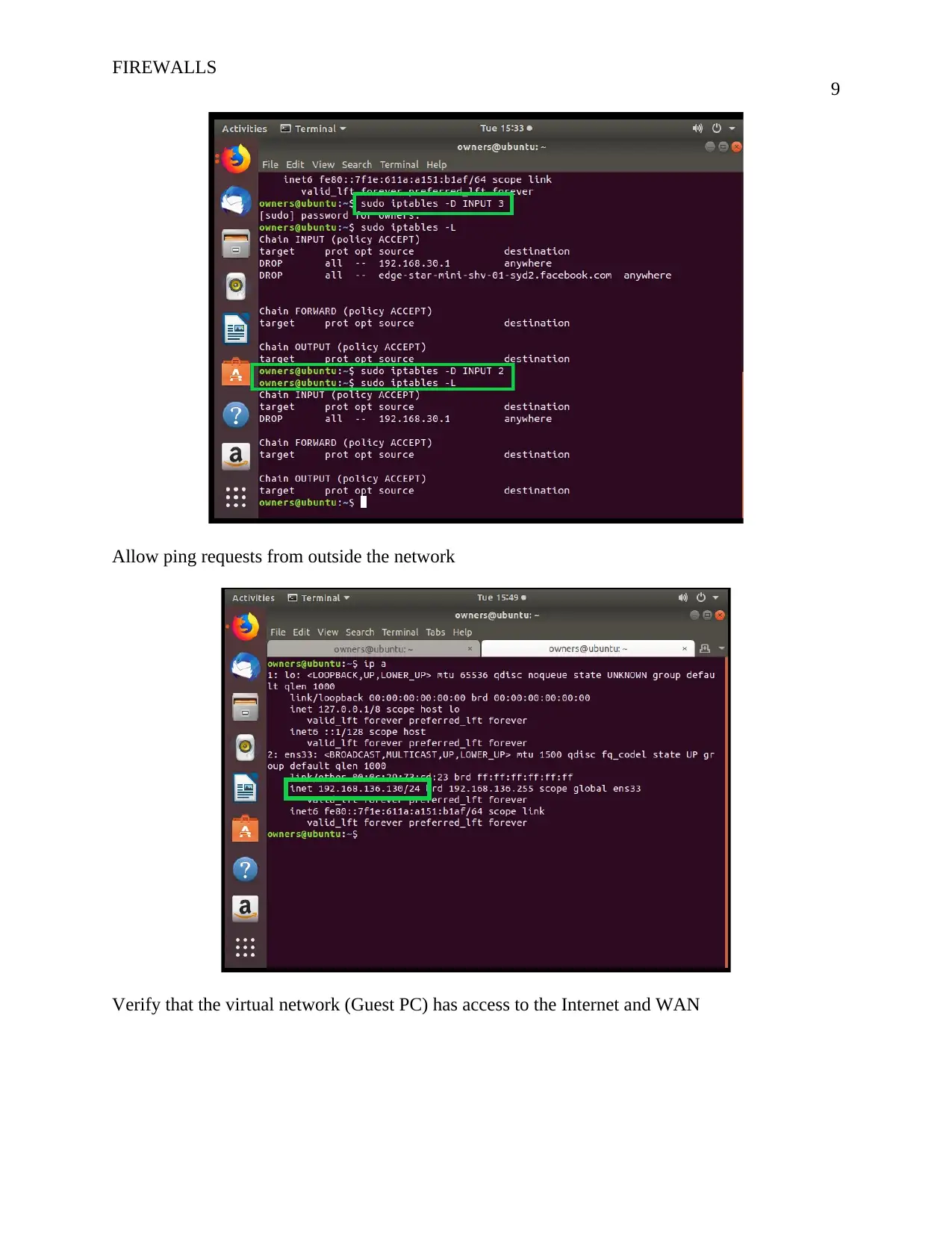
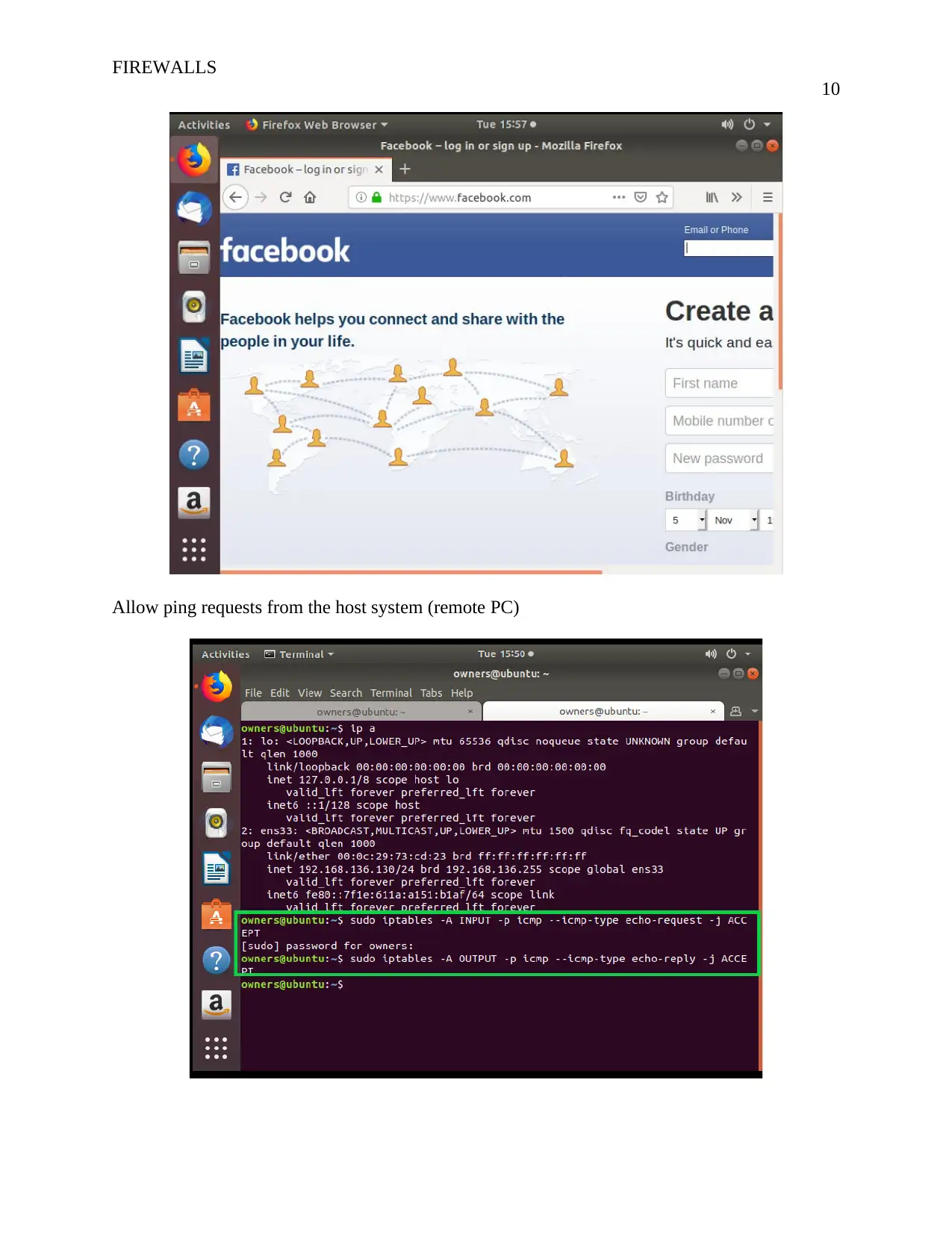
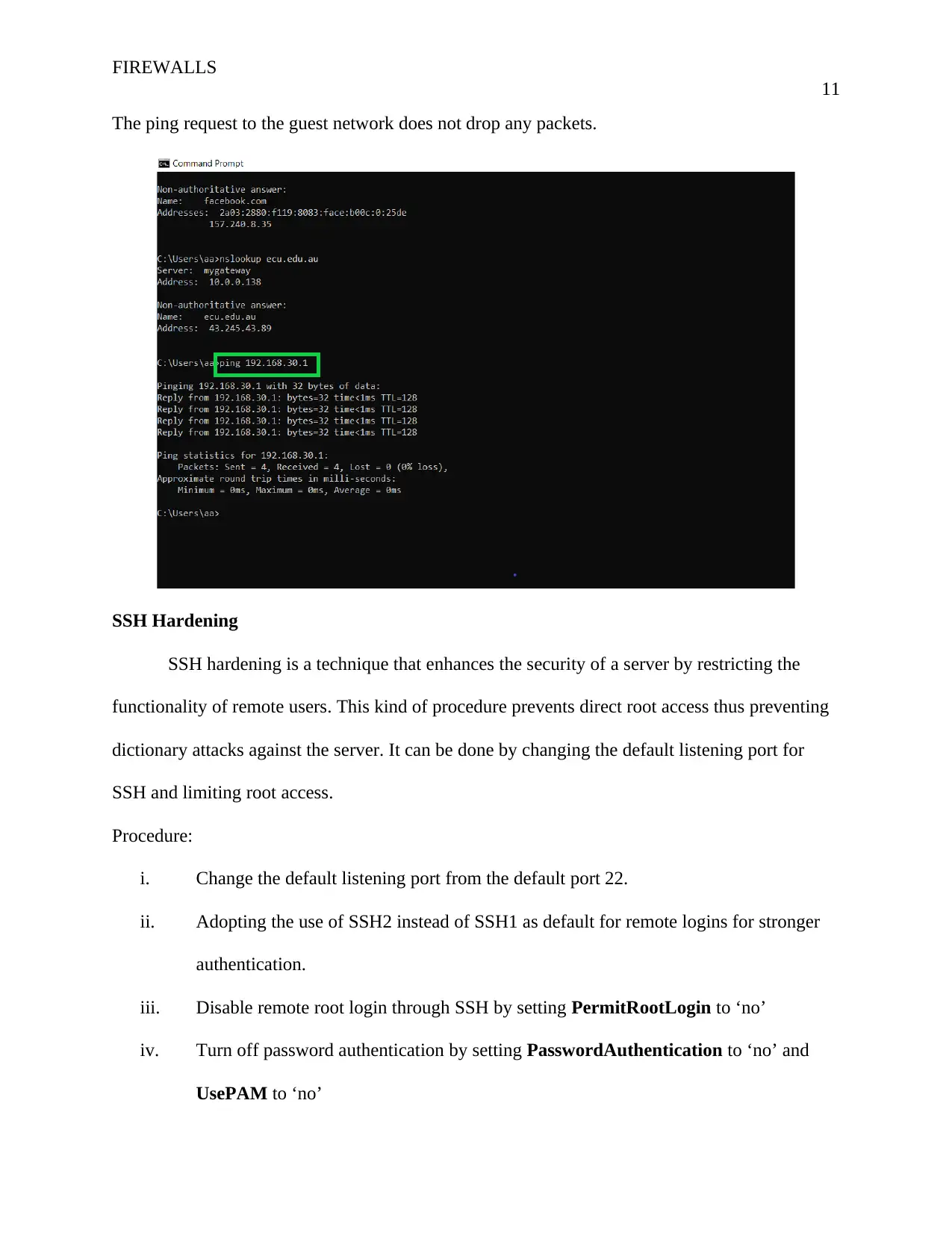



![[object Object]](/_next/static/media/star-bottom.7253800d.svg)