Firewall and IPsec Security Protocols: Assignment 2 Resit, UWL
VerifiedAdded on 2023/01/13
|5
|693
|92
Report
AI Summary
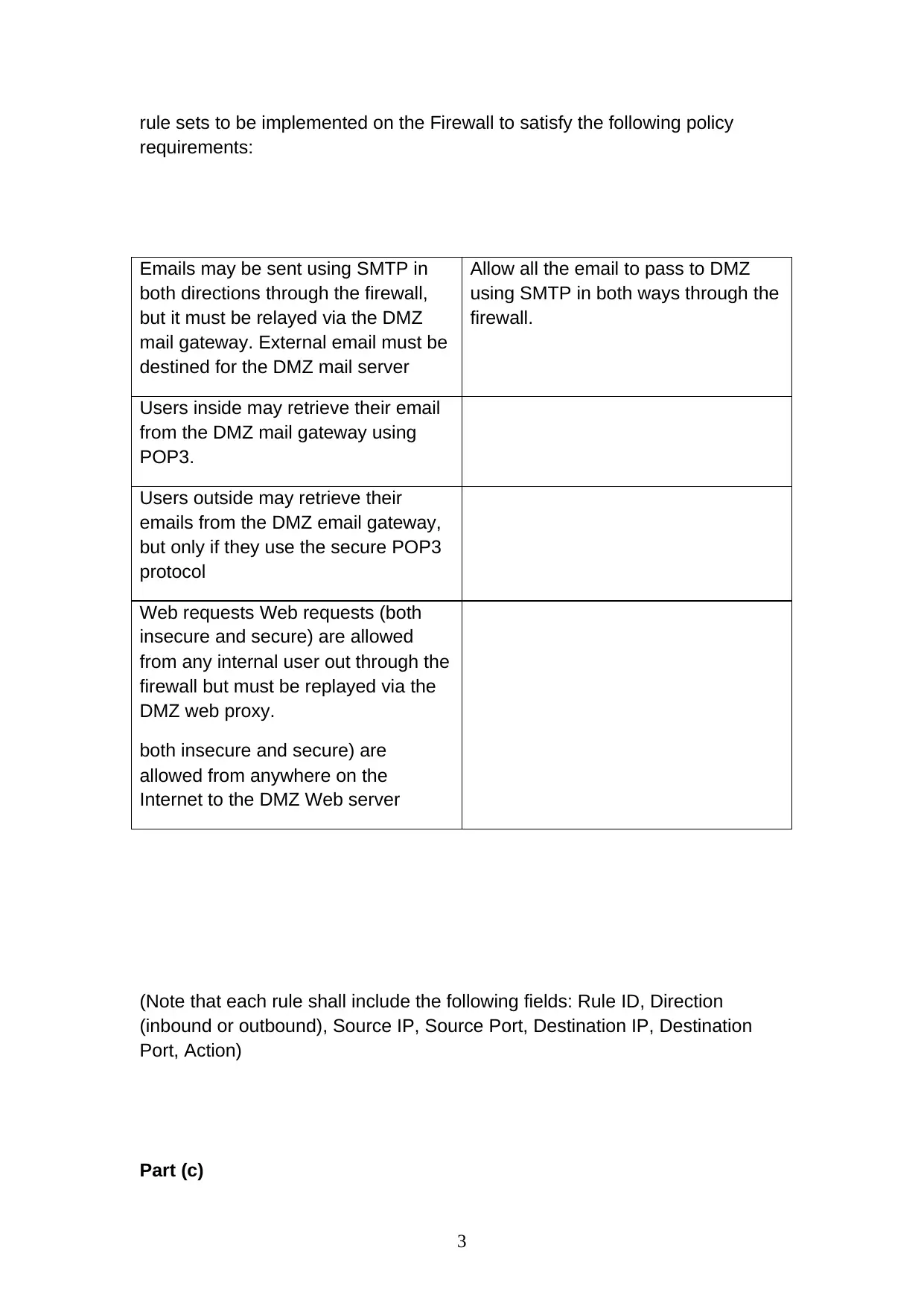
This report delves into the critical aspects of network security, focusing on firewalls and the IPsec protocol suite. The first part examines the goals of a firewall, emphasizing the importance of traffic filtering and network protection. It then explores the configuration of packet filter rule sets within a firewall, tailored to specific policy requirements, including email and web traffic management within a DMZ. The report also addresses anonymity and privacy concerns when accessing controversial websites, proposing the use of a proxy to conceal IP addresses and protect user data. The second part of the report analyzes the IPsec protocol suite, specifically examining replay attacks and the role of sequence numbers and anti-reply windows. It differentiates between Authentication Header (AH) and Encapsulating Security Payload (ESP) protocols, highlighting their respective security services and exploring the transport and tunnel modes of ESP. Finally, the report investigates the compatibility of IPsec using AH in transport mode when one of the machines is behind a Network Address Translation (NAT) box.
1 out of 5








![[object Object]](/_next/static/media/star-bottom.7253800d.svg)