Firewall and Configuration Analysis Report for Cybersecurity (ICT205)
VerifiedAdded on 2022/09/27
|22
|1741
|23
Report
AI Summary
This report, prepared for a cybersecurity course, provides a comprehensive analysis of firewall configuration and network security. It begins with an executive summary outlining the need for network security in a business context, specifically focusing on a small business with multiple locations. The report is divided into two parts: the first part details the use of Nmap, a network scanner, for host discovery, port scanning, vulnerability detection, and malware detection, including the use of NSE scripts and commands. The second part explores the use of Linux commands, particularly UFW, to check and configure firewall settings, including status checks, enabling/disabling, allowing services, and verifying firewall rules, with examples of securing a web server. The report concludes with a discussion of risk mitigation strategies and the evolution and capabilities of Nmap. The report covers various commands and their outputs, providing a practical guide for network administrators.

Firewall and Configuration 1
FIREWALL AND CONFIGURATION
By (Name)
(Class)
(Tutor)
(Institution)
(City)
(Date)
FIREWALL AND CONFIGURATION
By (Name)
(Class)
(Tutor)
(Institution)
(City)
(Date)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Firewall and Configuration 2
Executive summary
Canadian Cafe is among small business enterprise which comprises franchise at various
geographical locations. The company has the appropriate network facilities to meet its business
requirements. The major aim of the company is to secure its network across all its geographical
locations. The organization system administrator has realized that the organization network
security needs to be addressed. The company needs to impose a certain level of filtering for its
organization network to be secure. For organization network security to be achieved then the
network administrator needs to have a good understanding of various network attacks and
appropriate network attack mitigation strategies.
Outline
This report which is divided into two parts will highlight how to go about network attack
identification. The first part outlines how a network administrator can use Nmap to gather more
information about their network. Also, this paper has highlighted how network administrators
can use Nmap to detect network vulnerabilities and attacks. The second part outlines how one
can use Linux commands to gather more information about network firewall i.e. check firewall
status and its settings.
Executive summary
Canadian Cafe is among small business enterprise which comprises franchise at various
geographical locations. The company has the appropriate network facilities to meet its business
requirements. The major aim of the company is to secure its network across all its geographical
locations. The organization system administrator has realized that the organization network
security needs to be addressed. The company needs to impose a certain level of filtering for its
organization network to be secure. For organization network security to be achieved then the
network administrator needs to have a good understanding of various network attacks and
appropriate network attack mitigation strategies.
Outline
This report which is divided into two parts will highlight how to go about network attack
identification. The first part outlines how a network administrator can use Nmap to gather more
information about their network. Also, this paper has highlighted how network administrators
can use Nmap to detect network vulnerabilities and attacks. The second part outlines how one
can use Linux commands to gather more information about network firewall i.e. check firewall
status and its settings.
Firewall and Configuration 3
Part A: Nmap
1. Kali Linux on Virtual Box and Nmap running
Shown by the figure below
2. Description of Nmap
Network Mapper (Nmap) is one of free and open-source network scanner that was
created by Gordon Lynon. The tool is widely used to discover services and host on one computer
network by analyzing and sending packets. The tool comes with a number of features for probing
a computer network which includes host discovery, operating system detection, and service. The
four Nmap features include host discovery; here the tool can identify hosts on a computer
network. It does this by listing hosts which respond to ICMP and TCP requests. The second
feature is port scanning, here the tool enumerates open ports on the target hosts. The third is
version detection, the tool achieves this feature by interrogating network services on all remote
Part A: Nmap
1. Kali Linux on Virtual Box and Nmap running
Shown by the figure below
2. Description of Nmap
Network Mapper (Nmap) is one of free and open-source network scanner that was
created by Gordon Lynon. The tool is widely used to discover services and host on one computer
network by analyzing and sending packets. The tool comes with a number of features for probing
a computer network which includes host discovery, operating system detection, and service. The
four Nmap features include host discovery; here the tool can identify hosts on a computer
network. It does this by listing hosts which respond to ICMP and TCP requests. The second
feature is port scanning, here the tool enumerates open ports on the target hosts. The third is
version detection, the tool achieves this feature by interrogating network services on all remote
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Firewall and Configuration 4
devices. Forth is OS detection, the tool does this by determining the hardware and operating
characteristics of network devices. The last feature is scriptable interaction with the target where
NMap achieves this by using Nmap scripting engine (Collins, 2002, p. 116).
3. Nmap demonstration
Nmap tool is widely known for its mapping capabilities. Nmap assists in mitigating
network attacks through vulnerability scanning using NSE scripts. Together with Nmap
commands and NSE scripts then one is able to fetch the most popular Common Vulnerabilities
and Exposure (CVEs) from any target system. Also through Nmap, one has the ability to detect
backdoors and malware by running a number of extensive tests on popular OS services like
Proftpd, SMTP, SMB, Vsftpd, and Identd. The tool also has the ability to check for popular
malware signs inside remote servers (Orebaugh, 2011, p. 39).
a) Host discovery
The first step during network reconnaissance is to reduce a set of IP ranges into a list of
interesting or active hosts into a list of interesting or active hosts. Nmap tool offers a wide range
of options to customize the techniques using for host discovery. Example a sample NMAP
detection without the use of NSE scripts covered one of SSH service on port 22 using the
OpenSSH 4.3 version
Figure 1: SSH service port 22 detection using Nmap
devices. Forth is OS detection, the tool does this by determining the hardware and operating
characteristics of network devices. The last feature is scriptable interaction with the target where
NMap achieves this by using Nmap scripting engine (Collins, 2002, p. 116).
3. Nmap demonstration
Nmap tool is widely known for its mapping capabilities. Nmap assists in mitigating
network attacks through vulnerability scanning using NSE scripts. Together with Nmap
commands and NSE scripts then one is able to fetch the most popular Common Vulnerabilities
and Exposure (CVEs) from any target system. Also through Nmap, one has the ability to detect
backdoors and malware by running a number of extensive tests on popular OS services like
Proftpd, SMTP, SMB, Vsftpd, and Identd. The tool also has the ability to check for popular
malware signs inside remote servers (Orebaugh, 2011, p. 39).
a) Host discovery
The first step during network reconnaissance is to reduce a set of IP ranges into a list of
interesting or active hosts into a list of interesting or active hosts. Nmap tool offers a wide range
of options to customize the techniques using for host discovery. Example a sample NMAP
detection without the use of NSE scripts covered one of SSH service on port 22 using the
OpenSSH 4.3 version
Figure 1: SSH service port 22 detection using Nmap
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Firewall and Configuration 5
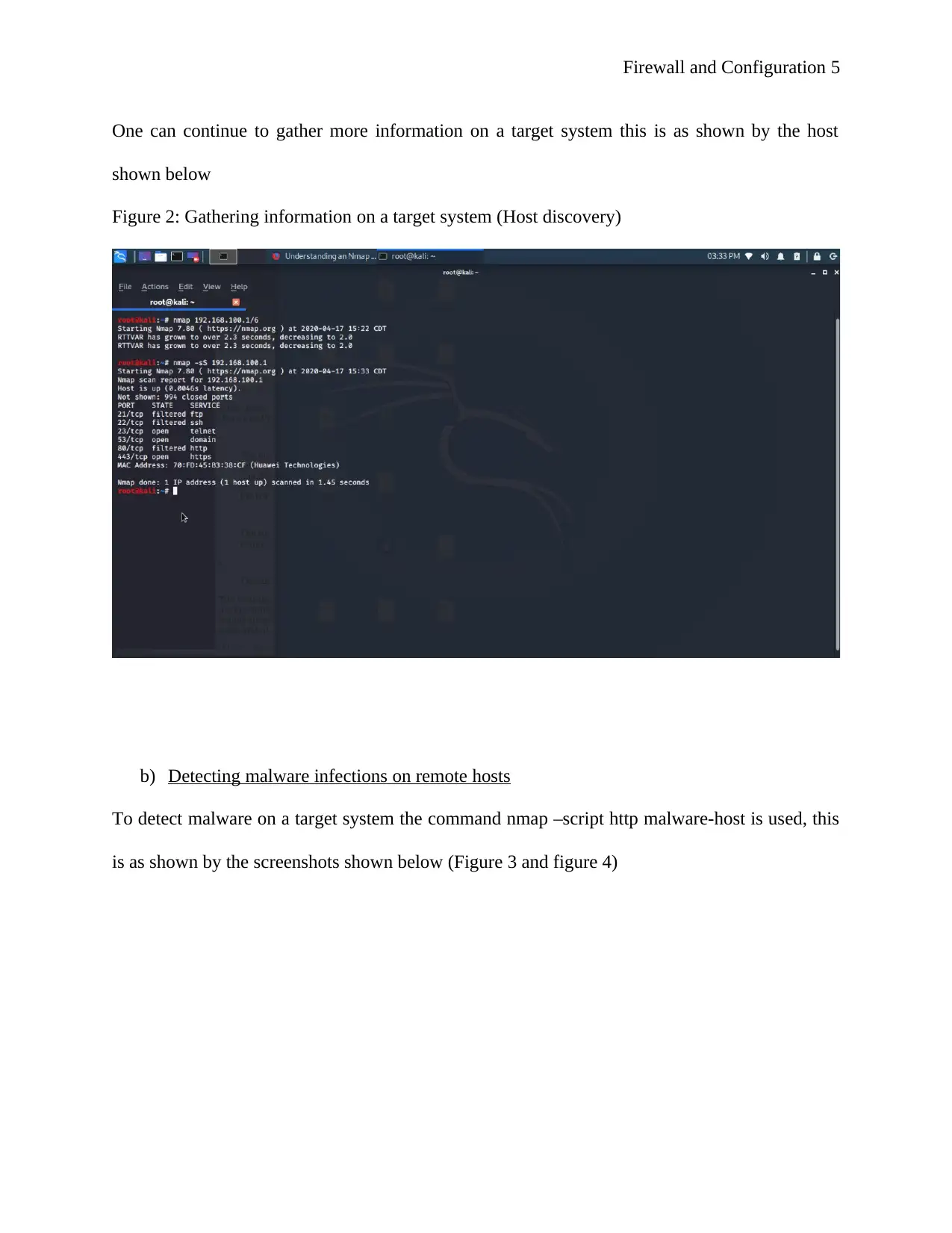
One can continue to gather more information on a target system this is as shown by the host
shown below
Figure 2: Gathering information on a target system (Host discovery)
b) Detecting malware infections on remote hosts
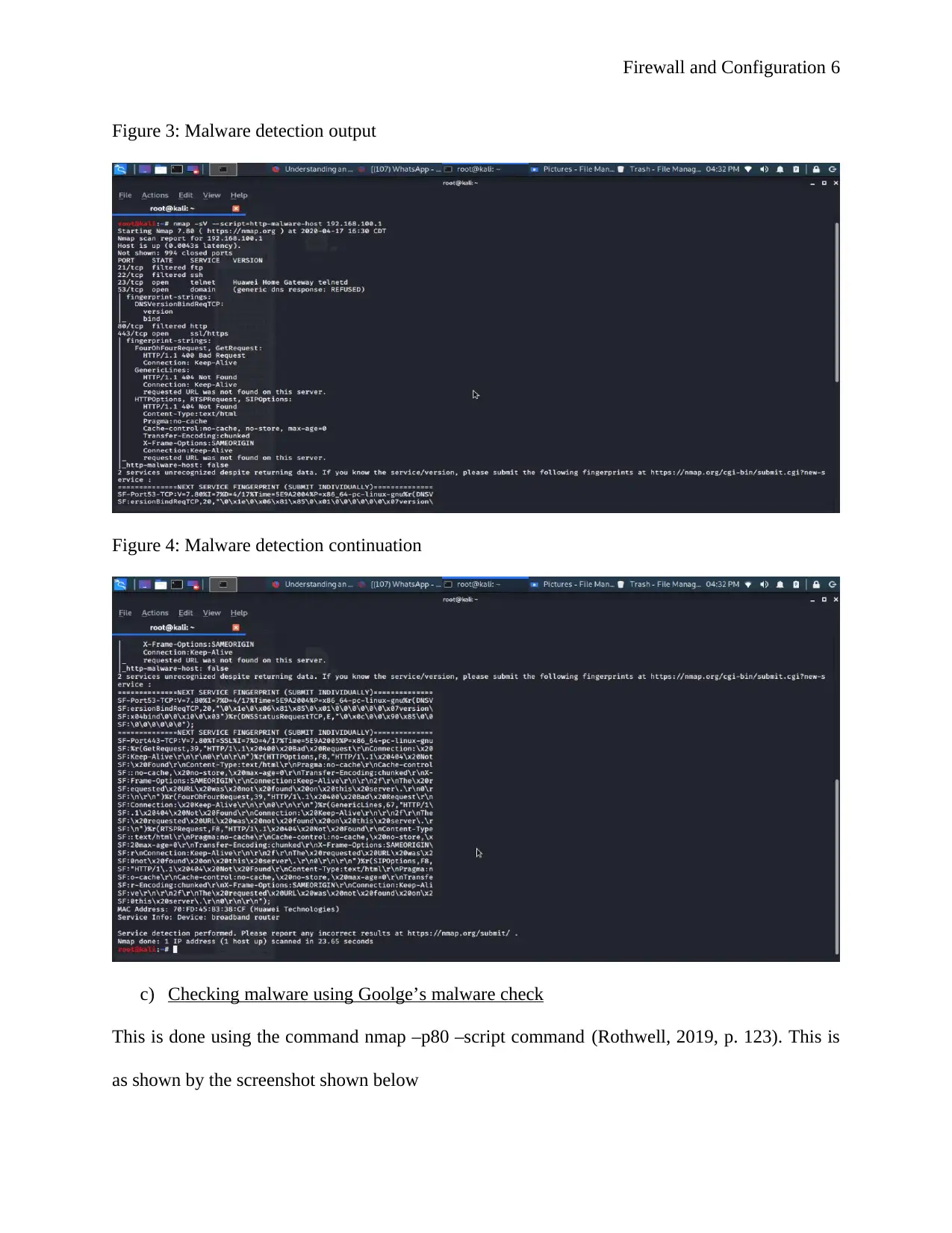
To detect malware on a target system the command nmap –script http malware-host is used, this
is as shown by the screenshots shown below (Figure 3 and figure 4)
One can continue to gather more information on a target system this is as shown by the host
shown below
Figure 2: Gathering information on a target system (Host discovery)
b) Detecting malware infections on remote hosts
To detect malware on a target system the command nmap –script http malware-host is used, this
is as shown by the screenshots shown below (Figure 3 and figure 4)
Firewall and Configuration 6
Figure 3: Malware detection output
Figure 4: Malware detection continuation
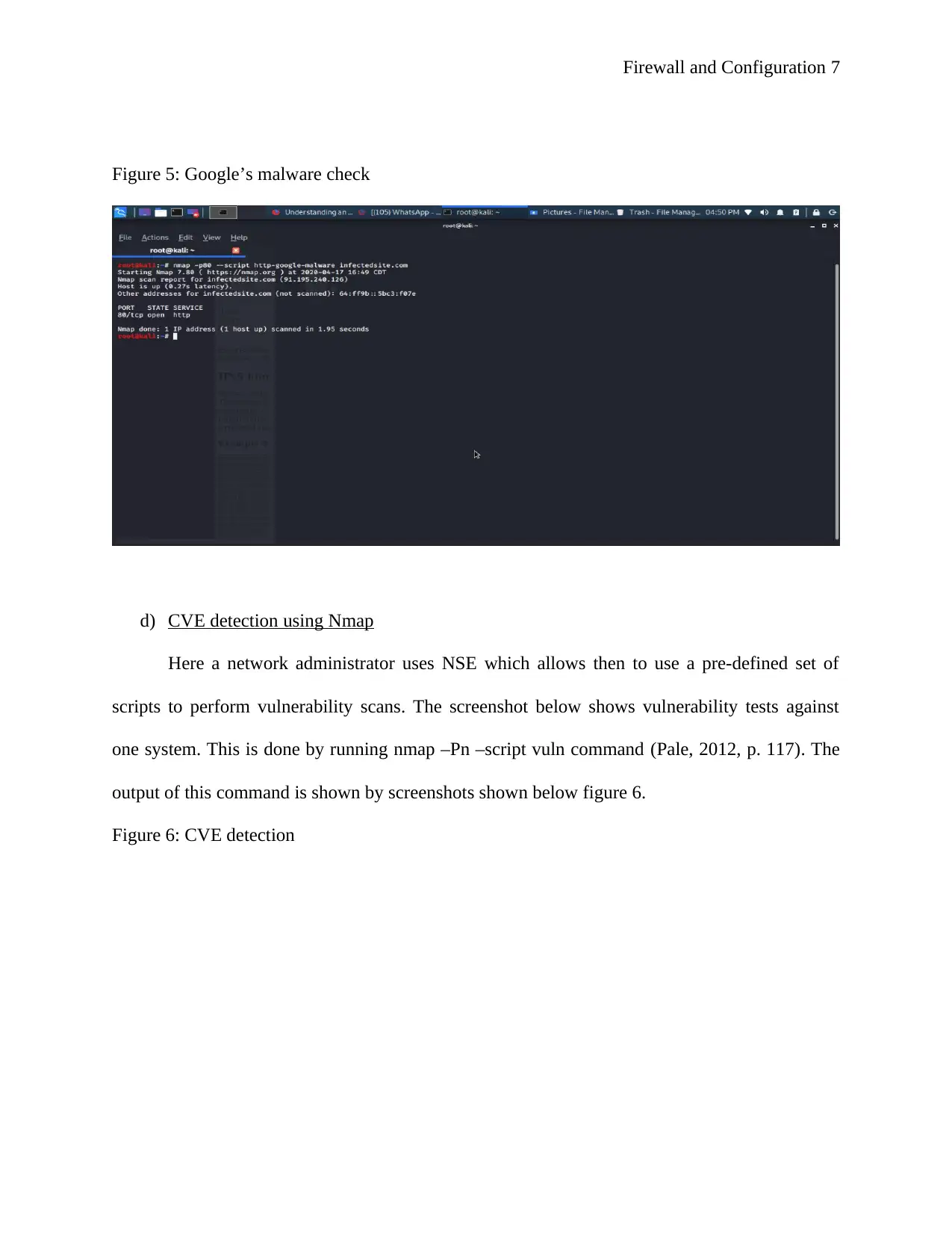
c) Checking malware using Goolge’s malware check
This is done using the command nmap –p80 –script command (Rothwell, 2019, p. 123). This is
as shown by the screenshot shown below
Figure 3: Malware detection output
Figure 4: Malware detection continuation
c) Checking malware using Goolge’s malware check
This is done using the command nmap –p80 –script command (Rothwell, 2019, p. 123). This is
as shown by the screenshot shown below
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Firewall and Configuration 7
Figure 5: Google’s malware check
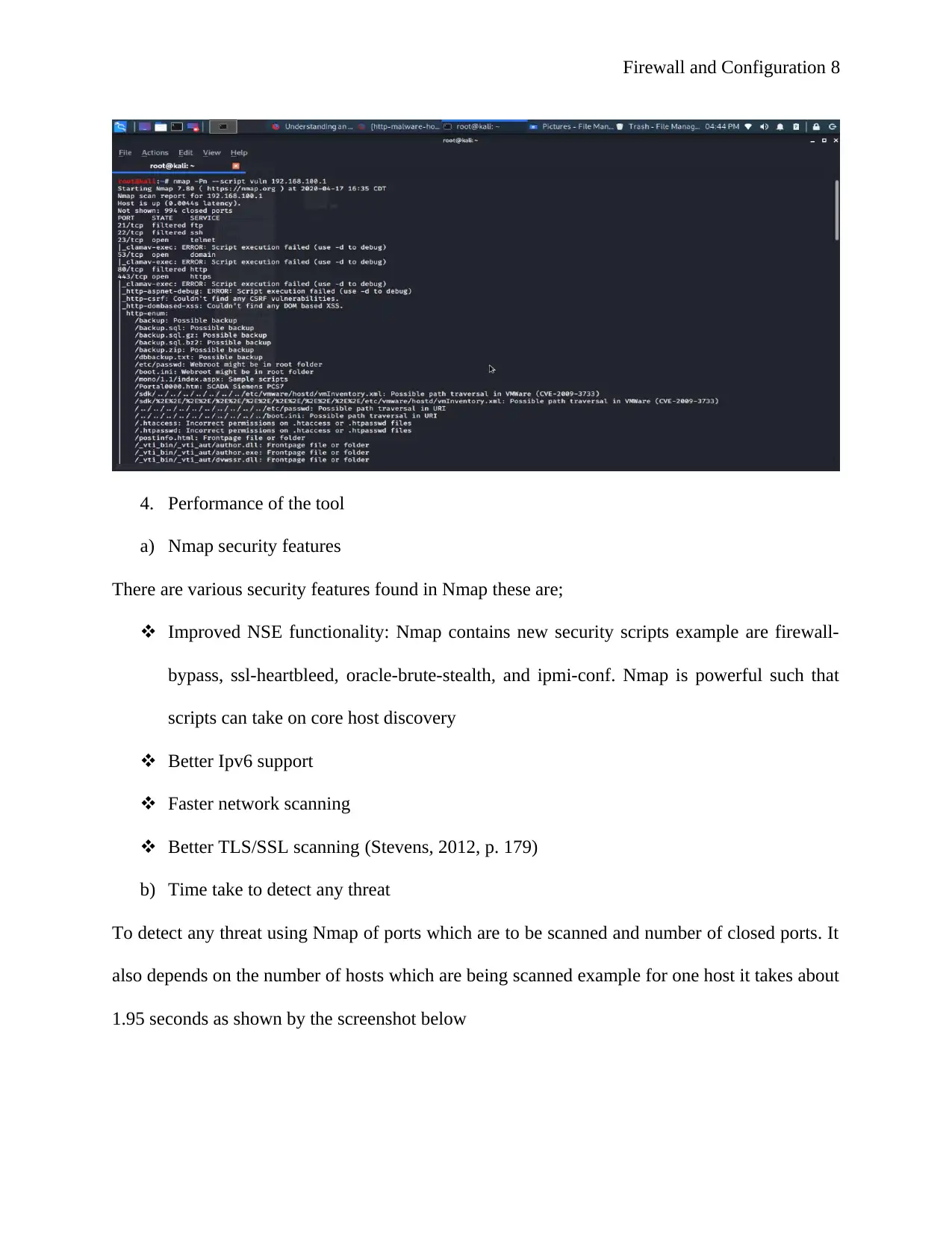
d) CVE detection using Nmap
Here a network administrator uses NSE which allows then to use a pre-defined set of
scripts to perform vulnerability scans. The screenshot below shows vulnerability tests against
one system. This is done by running nmap –Pn –script vuln command (Pale, 2012, p. 117). The
output of this command is shown by screenshots shown below figure 6.
Figure 6: CVE detection
Figure 5: Google’s malware check
d) CVE detection using Nmap
Here a network administrator uses NSE which allows then to use a pre-defined set of
scripts to perform vulnerability scans. The screenshot below shows vulnerability tests against
one system. This is done by running nmap –Pn –script vuln command (Pale, 2012, p. 117). The
output of this command is shown by screenshots shown below figure 6.
Figure 6: CVE detection
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Firewall and Configuration 8
4. Performance of the tool
a) Nmap security features
There are various security features found in Nmap these are;
Improved NSE functionality: Nmap contains new security scripts example are firewall-
bypass, ssl-heartbleed, oracle-brute-stealth, and ipmi-conf. Nmap is powerful such that
scripts can take on core host discovery
Better Ipv6 support
Faster network scanning
Better TLS/SSL scanning (Stevens, 2012, p. 179)
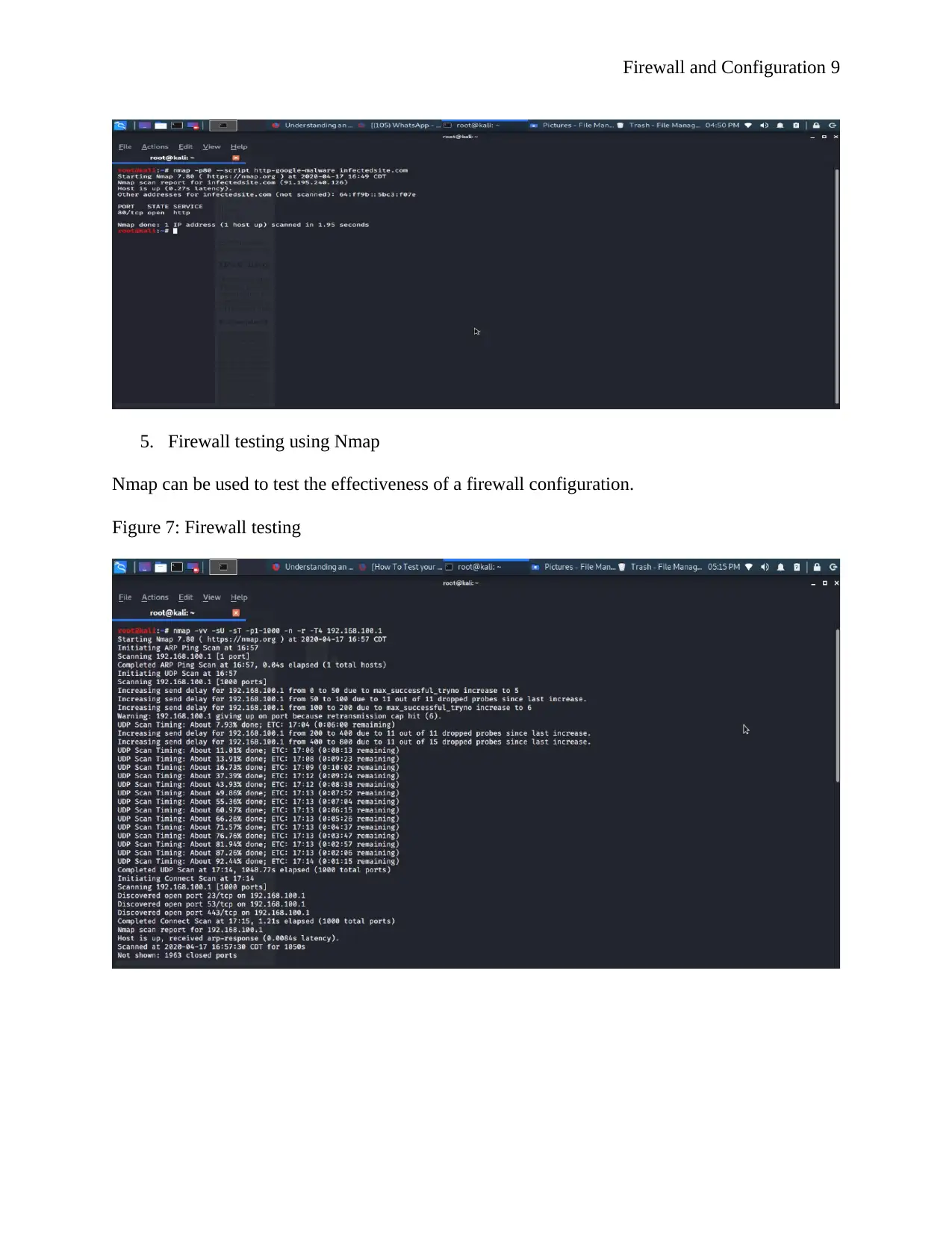
b) Time take to detect any threat
To detect any threat using Nmap of ports which are to be scanned and number of closed ports. It
also depends on the number of hosts which are being scanned example for one host it takes about
1.95 seconds as shown by the screenshot below
4. Performance of the tool
a) Nmap security features
There are various security features found in Nmap these are;
Improved NSE functionality: Nmap contains new security scripts example are firewall-
bypass, ssl-heartbleed, oracle-brute-stealth, and ipmi-conf. Nmap is powerful such that
scripts can take on core host discovery
Better Ipv6 support
Faster network scanning
Better TLS/SSL scanning (Stevens, 2012, p. 179)
b) Time take to detect any threat
To detect any threat using Nmap of ports which are to be scanned and number of closed ports. It
also depends on the number of hosts which are being scanned example for one host it takes about
1.95 seconds as shown by the screenshot below
Firewall and Configuration 9
5. Firewall testing using Nmap
Nmap can be used to test the effectiveness of a firewall configuration.
Figure 7: Firewall testing
5. Firewall testing using Nmap
Nmap can be used to test the effectiveness of a firewall configuration.
Figure 7: Firewall testing
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Firewall and Configuration 10
6. Risk Mitigation plan
Risk mitigation plan in this case is as shown by table one shown below
Plan Activities
Risk identification This done by gathering information about a
network using Nmap. Done using command
nmap (Ip address of the host)
Risk impact assessment This done by assessing the number of hosts
using command nmap –script http malware-
host.
Risk mitigation This is done by disabling all affected port
(Stevens, 2012, p. 148).
Part B: Firewall settings
It is important to note that Nmap networking tool distinguishes between ports which are
reachable but those that are not closed. The tool also assist in distinguishing those ports that are
actively filtered. Before checking firewall settings the first step is to detect both filtered and
closed TCP ports (Tanner, 2019, p. 179). One can then continue to check firewall settings as
shown by the below sections.
Figure 8: Checking firewall setting
6. Risk Mitigation plan
Risk mitigation plan in this case is as shown by table one shown below
Plan Activities
Risk identification This done by gathering information about a
network using Nmap. Done using command
nmap (Ip address of the host)
Risk impact assessment This done by assessing the number of hosts
using command nmap –script http malware-
host.
Risk mitigation This is done by disabling all affected port
(Stevens, 2012, p. 148).
Part B: Firewall settings
It is important to note that Nmap networking tool distinguishes between ports which are
reachable but those that are not closed. The tool also assist in distinguishing those ports that are
actively filtered. Before checking firewall settings the first step is to detect both filtered and
closed TCP ports (Tanner, 2019, p. 179). One can then continue to check firewall settings as
shown by the below sections.
Figure 8: Checking firewall setting
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Firewall and Configuration 11
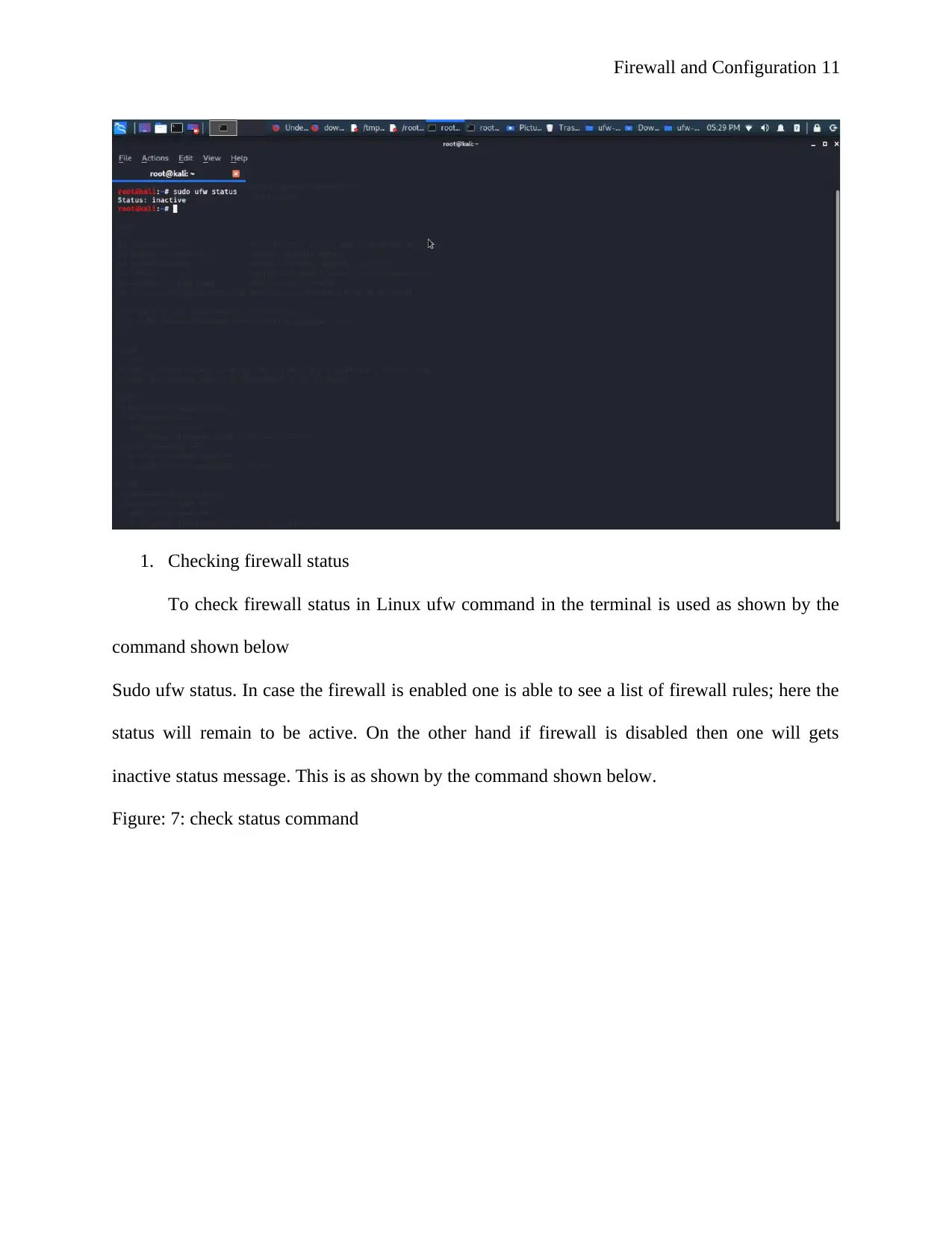
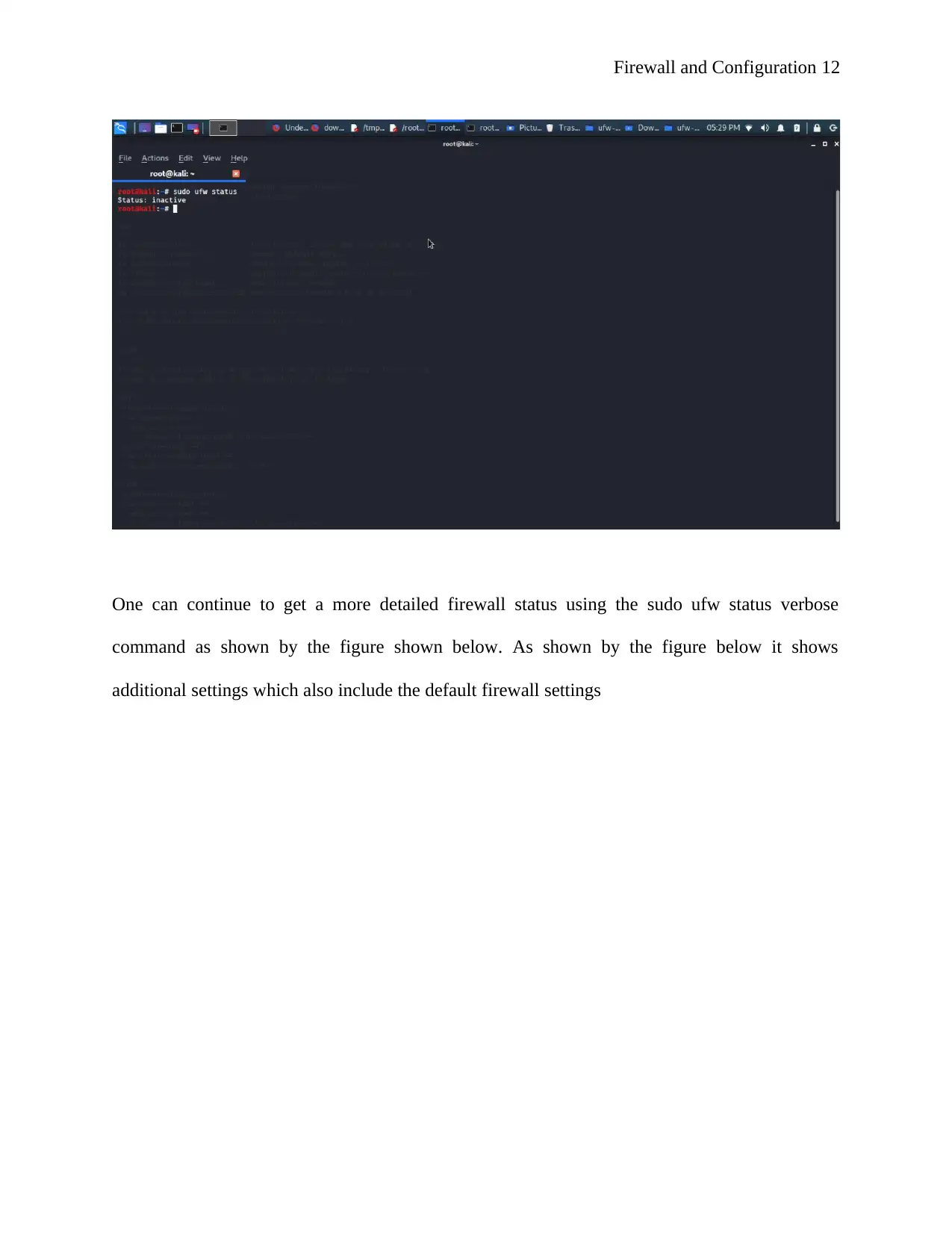
1. Checking firewall status
To check firewall status in Linux ufw command in the terminal is used as shown by the
command shown below
Sudo ufw status. In case the firewall is enabled one is able to see a list of firewall rules; here the
status will remain to be active. On the other hand if firewall is disabled then one will gets
inactive status message. This is as shown by the command shown below.
Figure: 7: check status command
1. Checking firewall status
To check firewall status in Linux ufw command in the terminal is used as shown by the
command shown below
Sudo ufw status. In case the firewall is enabled one is able to see a list of firewall rules; here the
status will remain to be active. On the other hand if firewall is disabled then one will gets
inactive status message. This is as shown by the command shown below.
Figure: 7: check status command
Firewall and Configuration 12
One can continue to get a more detailed firewall status using the sudo ufw status verbose
command as shown by the figure shown below. As shown by the figure below it shows
additional settings which also include the default firewall settings
One can continue to get a more detailed firewall status using the sudo ufw status verbose
command as shown by the figure shown below. As shown by the figure below it shows
additional settings which also include the default firewall settings
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




