King's Own Institute - ICT205 - Firewall Setup & Configuration Project
VerifiedAdded on 2022/09/09
|14
|1431
|14
Project
AI Summary
This project delves into firewall setup and configuration, assessing the understanding of firewall design and its role in mitigating security risks. It utilizes Kali Linux and the Nmap tool for penetration testing, identifying vulnerabilities, and generating a risk mitigation plan. The project is divided into two parts: Part A involves network security testing using Nmap to scan for open ports, hosts, and operating system information, followed by a risk mitigation strategy. Part B focuses on configuring a network firewall using Kali Linux commands, including UFW, to achieve the desired security levels. The project concludes with a discussion of the effectiveness of the implemented security measures and references relevant sources.

Assessment 1:Firewall Setup & Configuration
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
This project assesses the understanding of the firewall and design configuration. It also
helps to reduce the potential security risks for performing the network’s security testing, which is
used for determining threats and prepares a report on risk mitigation. The analysis is used for
securing a network, including the distributed application.
This project assesses the understanding of the firewall and design configuration. It also
helps to reduce the potential security risks for performing the network’s security testing, which is
used for determining threats and prepares a report on risk mitigation. The analysis is used for
securing a network, including the distributed application.

Table of Contents
1. Project Outline........................................................................................................................1
2. Part A.......................................................................................................................................1
2.1 Use Nmap.........................................................................................................................1
2.2 Description of Nmap.......................................................................................................3
2.3 Nmap Analysis.................................................................................................................4
2.4 Risk Mitigation Plan.......................................................................................................7
3. Part B.......................................................................................................................................8
3.1 Firewall Setup Configuration........................................................................................8
4. Conclusion.............................................................................................................................10
References.....................................................................................................................................11
1. Project Outline........................................................................................................................1
2. Part A.......................................................................................................................................1
2.1 Use Nmap.........................................................................................................................1
2.2 Description of Nmap.......................................................................................................3
2.3 Nmap Analysis.................................................................................................................4
2.4 Risk Mitigation Plan.......................................................................................................7
3. Part B.......................................................................................................................................8
3.1 Firewall Setup Configuration........................................................................................8
4. Conclusion.............................................................................................................................10
References.....................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
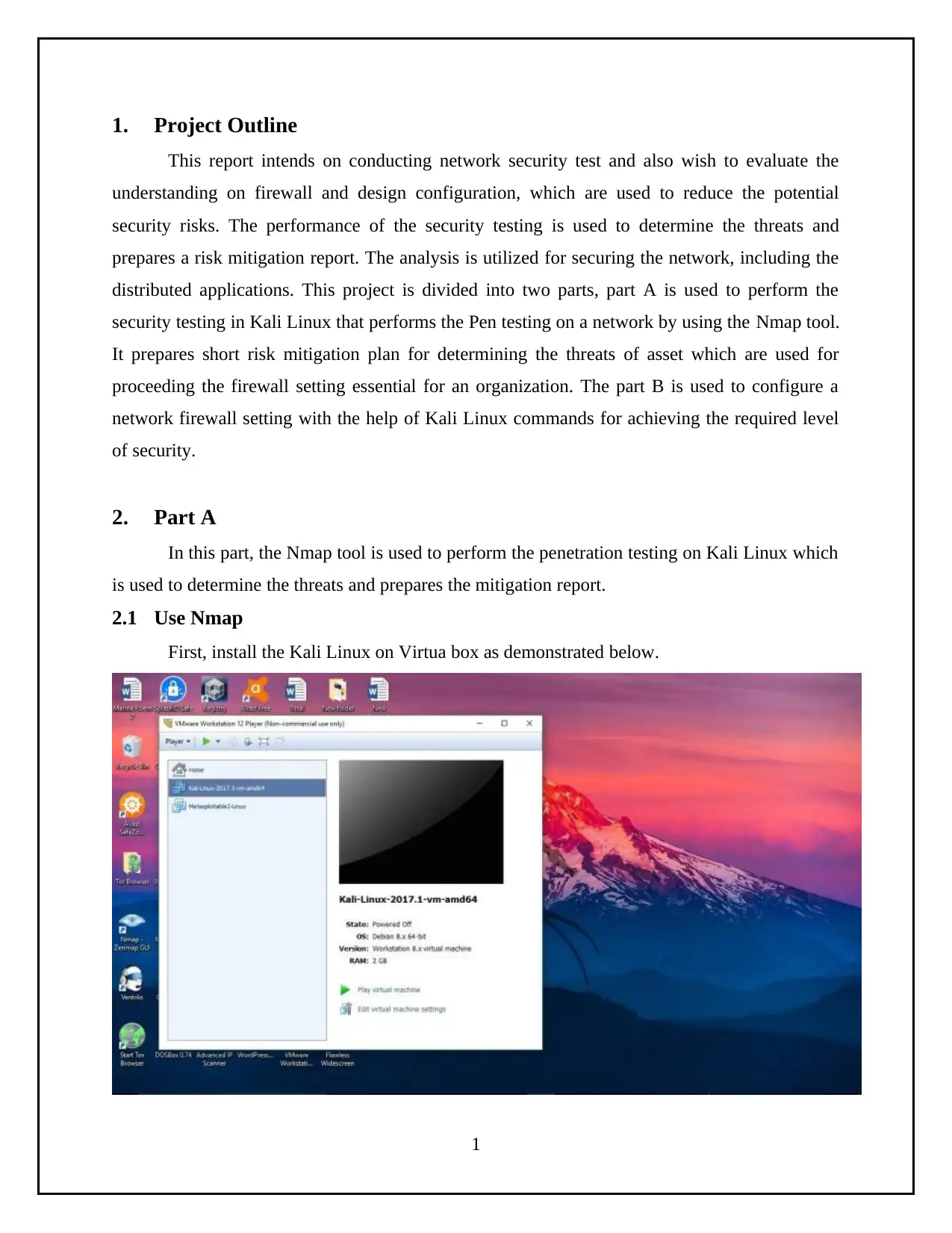
1. Project Outline
This report intends on conducting network security test and also wish to evaluate the
understanding on firewall and design configuration, which are used to reduce the potential
security risks. The performance of the security testing is used to determine the threats and
prepares a risk mitigation report. The analysis is utilized for securing the network, including the
distributed applications. This project is divided into two parts, part A is used to perform the
security testing in Kali Linux that performs the Pen testing on a network by using the Nmap tool.
It prepares short risk mitigation plan for determining the threats of asset which are used for
proceeding the firewall setting essential for an organization. The part B is used to configure a
network firewall setting with the help of Kali Linux commands for achieving the required level
of security.
2. Part A
In this part, the Nmap tool is used to perform the penetration testing on Kali Linux which
is used to determine the threats and prepares the mitigation report.
2.1 Use Nmap
First, install the Kali Linux on Virtua box as demonstrated below.
1
This report intends on conducting network security test and also wish to evaluate the
understanding on firewall and design configuration, which are used to reduce the potential
security risks. The performance of the security testing is used to determine the threats and
prepares a risk mitigation report. The analysis is utilized for securing the network, including the
distributed applications. This project is divided into two parts, part A is used to perform the
security testing in Kali Linux that performs the Pen testing on a network by using the Nmap tool.
It prepares short risk mitigation plan for determining the threats of asset which are used for
proceeding the firewall setting essential for an organization. The part B is used to configure a
network firewall setting with the help of Kali Linux commands for achieving the required level
of security.
2. Part A
In this part, the Nmap tool is used to perform the penetration testing on Kali Linux which
is used to determine the threats and prepares the mitigation report.
2.1 Use Nmap
First, install the Kali Linux on Virtua box as demonstrated below.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
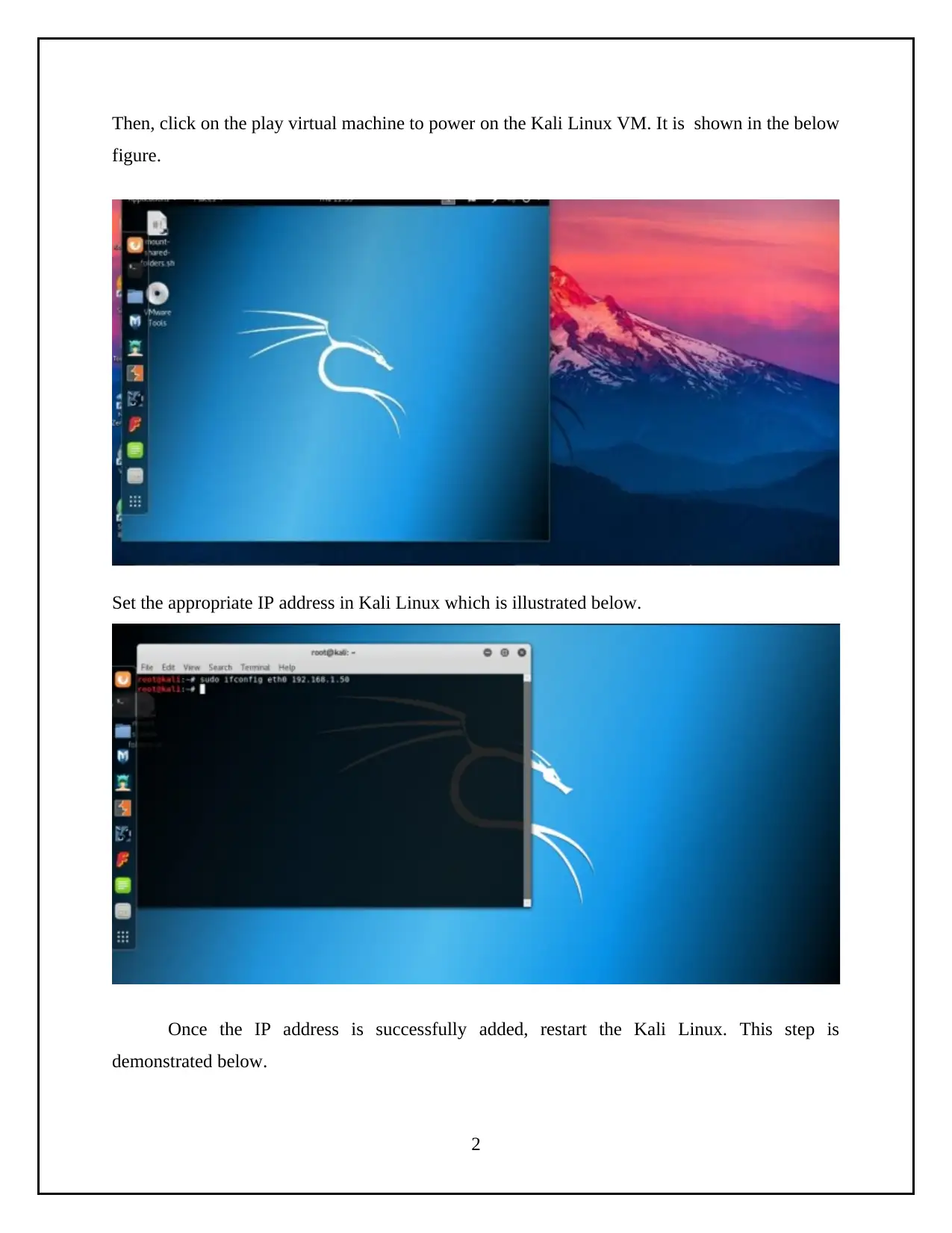
Then, click on the play virtual machine to power on the Kali Linux VM. It is shown in the below
figure.
Set the appropriate IP address in Kali Linux which is illustrated below.
Once the IP address is successfully added, restart the Kali Linux. This step is
demonstrated below.
2
figure.
Set the appropriate IP address in Kali Linux which is illustrated below.
Once the IP address is successfully added, restart the Kali Linux. This step is
demonstrated below.
2
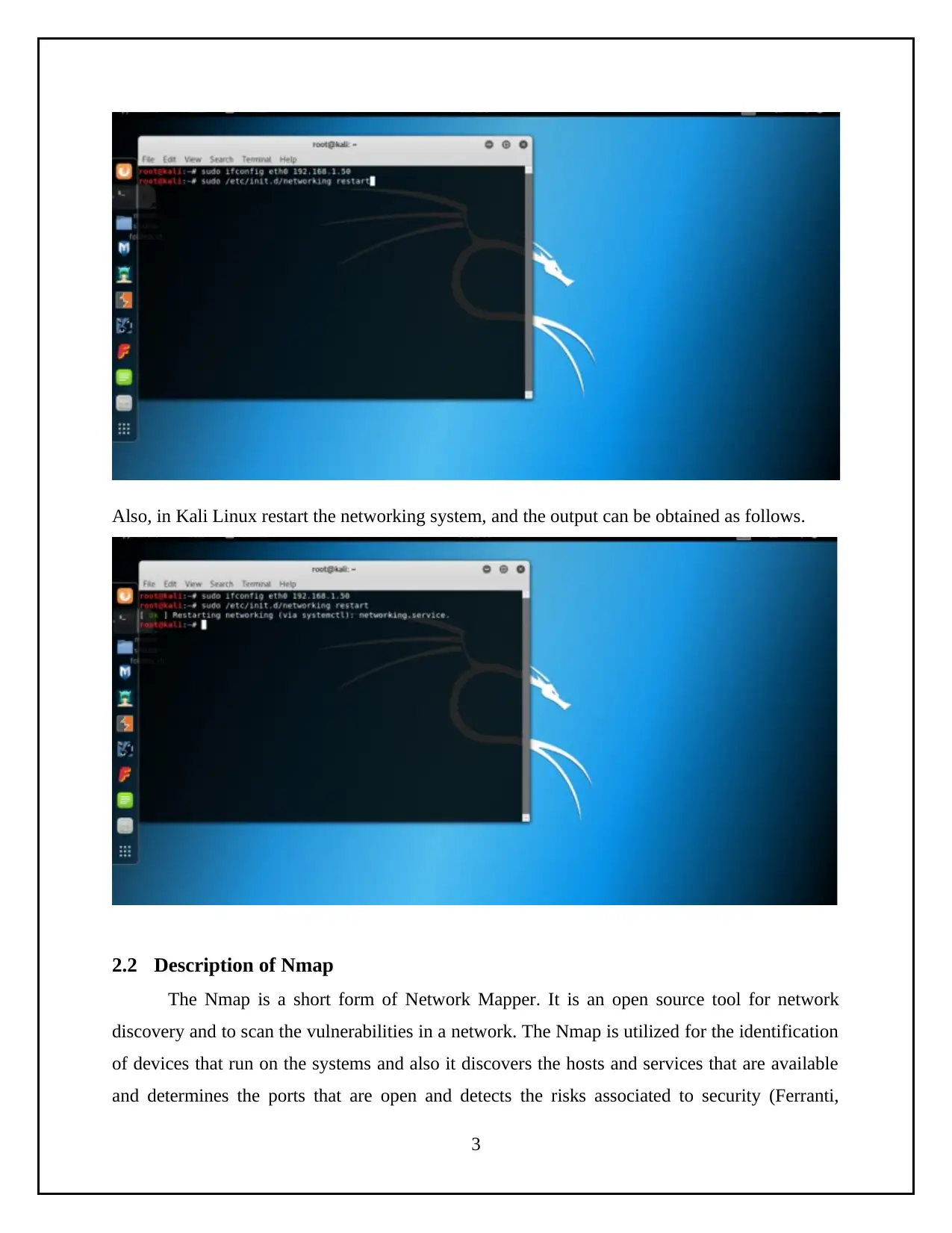
Also, in Kali Linux restart the networking system, and the output can be obtained as follows.
2.2 Description of Nmap
The Nmap is a short form of Network Mapper. It is an open source tool for network
discovery and to scan the vulnerabilities in a network. The Nmap is utilized for the identification
of devices that run on the systems and also it discovers the hosts and services that are available
and determines the ports that are open and detects the risks associated to security (Ferranti,
3
2.2 Description of Nmap
The Nmap is a short form of Network Mapper. It is an open source tool for network
discovery and to scan the vulnerabilities in a network. The Nmap is utilized for the identification
of devices that run on the systems and also it discovers the hosts and services that are available
and determines the ports that are open and detects the risks associated to security (Ferranti,
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2019). It also helps in monitoring the single hosts and the large networks which contains various
multitudes, and subnet devices.
2.3 Nmap Analysis
The analysis of Nmap includes scanning the following parts such as,
Host Scanning
Domain Scanning
Port Scanning
To do analysis on Nmap, type the following command on Terminal, nmap, it gives the
below results ("Hack Like a Pro: Advanced Nmap for Reconnaissance", 2019).
Afterwards, port scanning is done by entering the following command on a terminal,
4
multitudes, and subnet devices.
2.3 Nmap Analysis
The analysis of Nmap includes scanning the following parts such as,
Host Scanning
Domain Scanning
Port Scanning
To do analysis on Nmap, type the following command on Terminal, nmap, it gives the
below results ("Hack Like a Pro: Advanced Nmap for Reconnaissance", 2019).
Afterwards, port scanning is done by entering the following command on a terminal,
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
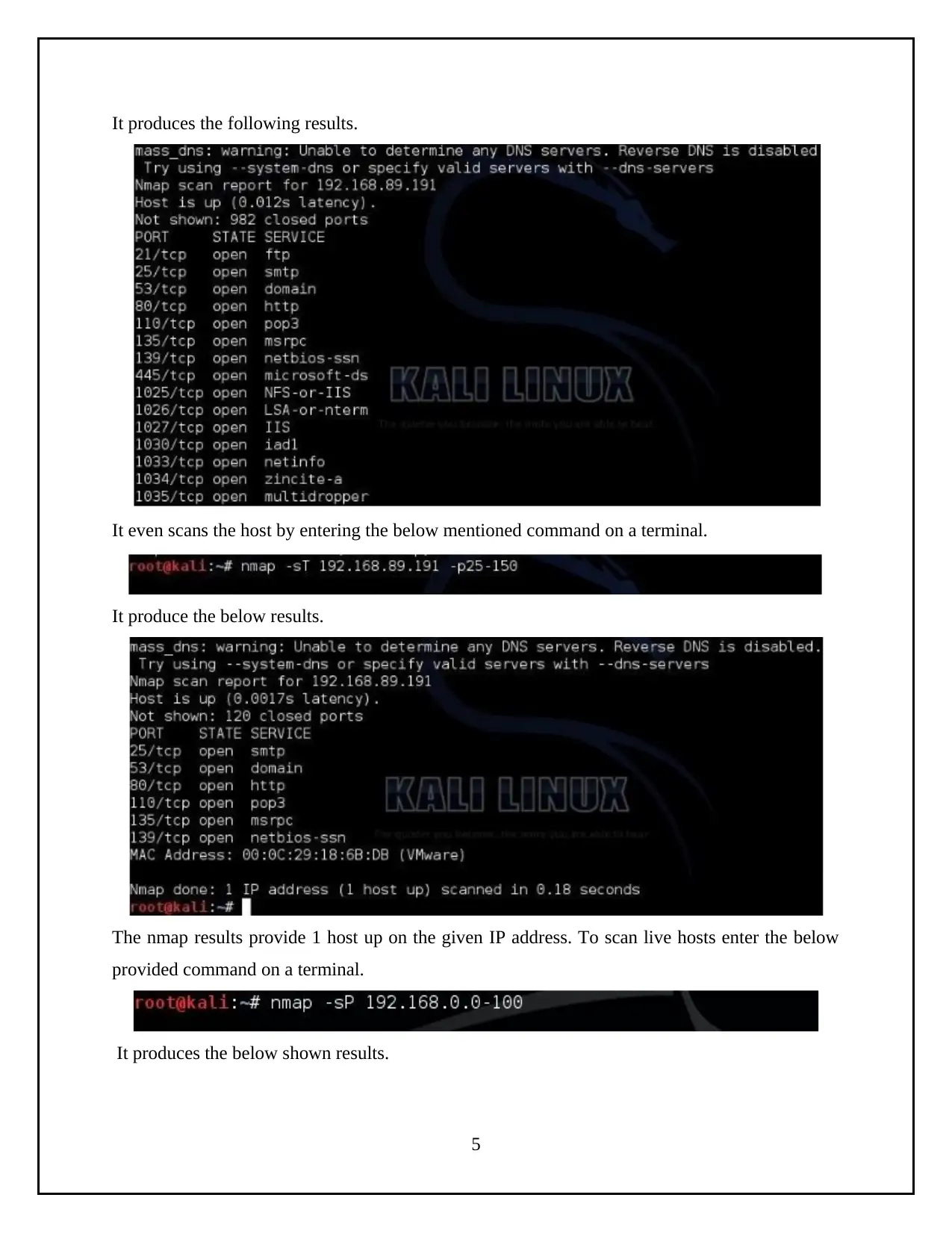
It produces the following results.
It even scans the host by entering the below mentioned command on a terminal.
It produce the below results.
The nmap results provide 1 host up on the given IP address. To scan live hosts enter the below
provided command on a terminal.
It produces the below shown results.
5
It even scans the host by entering the below mentioned command on a terminal.
It produce the below results.
The nmap results provide 1 host up on the given IP address. To scan live hosts enter the below
provided command on a terminal.
It produces the below shown results.
5
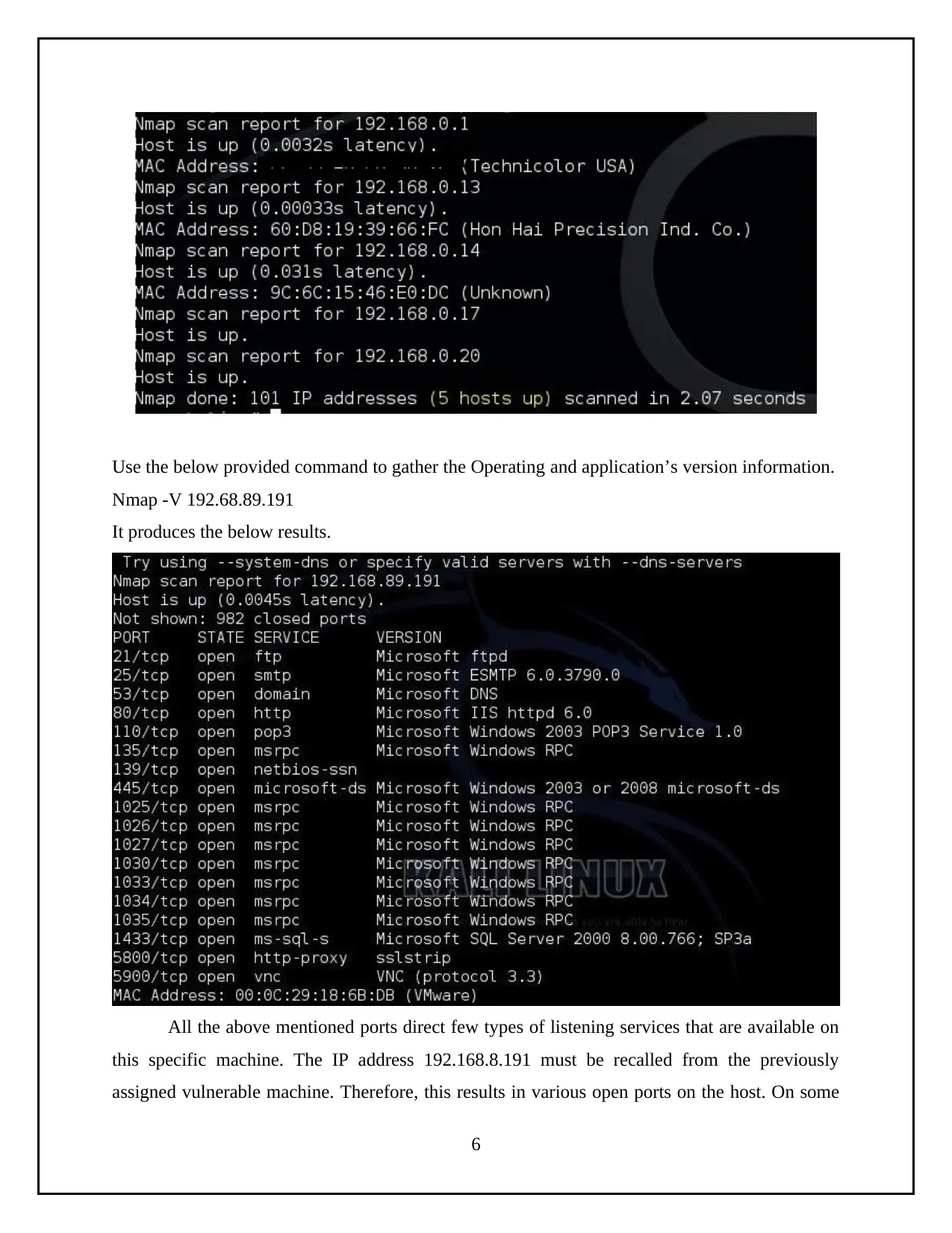
Use the below provided command to gather the Operating and application’s version information.
Nmap -V 192.68.89.191
It produces the below results.
All the above mentioned ports direct few types of listening services that are available on
this specific machine. The IP address 192.168.8.191 must be recalled from the previously
assigned vulnerable machine. Therefore, this results in various open ports on the host. On some
6
Nmap -V 192.68.89.191
It produces the below results.
All the above mentioned ports direct few types of listening services that are available on
this specific machine. The IP address 192.168.8.191 must be recalled from the previously
assigned vulnerable machine. Therefore, this results in various open ports on the host. On some
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

machines, these many open ports is not normal. Thus, it is essential to perform machine
investigation. The admin can easily track a physical machine on a network, where the machine
can be seen locally, however it is not fun, particularly when the Nmap could do it instantly.
2.4 Risk Mitigation Plan
Mitigate the risks by using foot printing and finger printing methods. The finger printing
is a process of determining the operating system on a device whereas, the foot prints is a
combination of passive and active reconnaissance technique, which is posed for establishing the
strategy of attack. And, when the user finishes foot printing, a user can draw out a network map
that contains the following:
Operating systems
IP address
Host Name
Listening Port Numbers
Host name
This method is to determine the vulnerabilities in the windows operating system and
applications. It is a generic firewall attack, and it is not necessarily intrusive to an organization
network. It can lead to create unsafe consequence. Therefore, organizations make an effort to
mitigate the risks associated with the reconnaissance attacks. So, the firewalls of the
organizational network must be set to ground the routers and firewalls that block or ping by
using the following command.
It produces the below mentioned results.
7
investigation. The admin can easily track a physical machine on a network, where the machine
can be seen locally, however it is not fun, particularly when the Nmap could do it instantly.
2.4 Risk Mitigation Plan
Mitigate the risks by using foot printing and finger printing methods. The finger printing
is a process of determining the operating system on a device whereas, the foot prints is a
combination of passive and active reconnaissance technique, which is posed for establishing the
strategy of attack. And, when the user finishes foot printing, a user can draw out a network map
that contains the following:
Operating systems
IP address
Host Name
Listening Port Numbers
Host name
This method is to determine the vulnerabilities in the windows operating system and
applications. It is a generic firewall attack, and it is not necessarily intrusive to an organization
network. It can lead to create unsafe consequence. Therefore, organizations make an effort to
mitigate the risks associated with the reconnaissance attacks. So, the firewalls of the
organizational network must be set to ground the routers and firewalls that block or ping by
using the following command.
It produces the below mentioned results.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
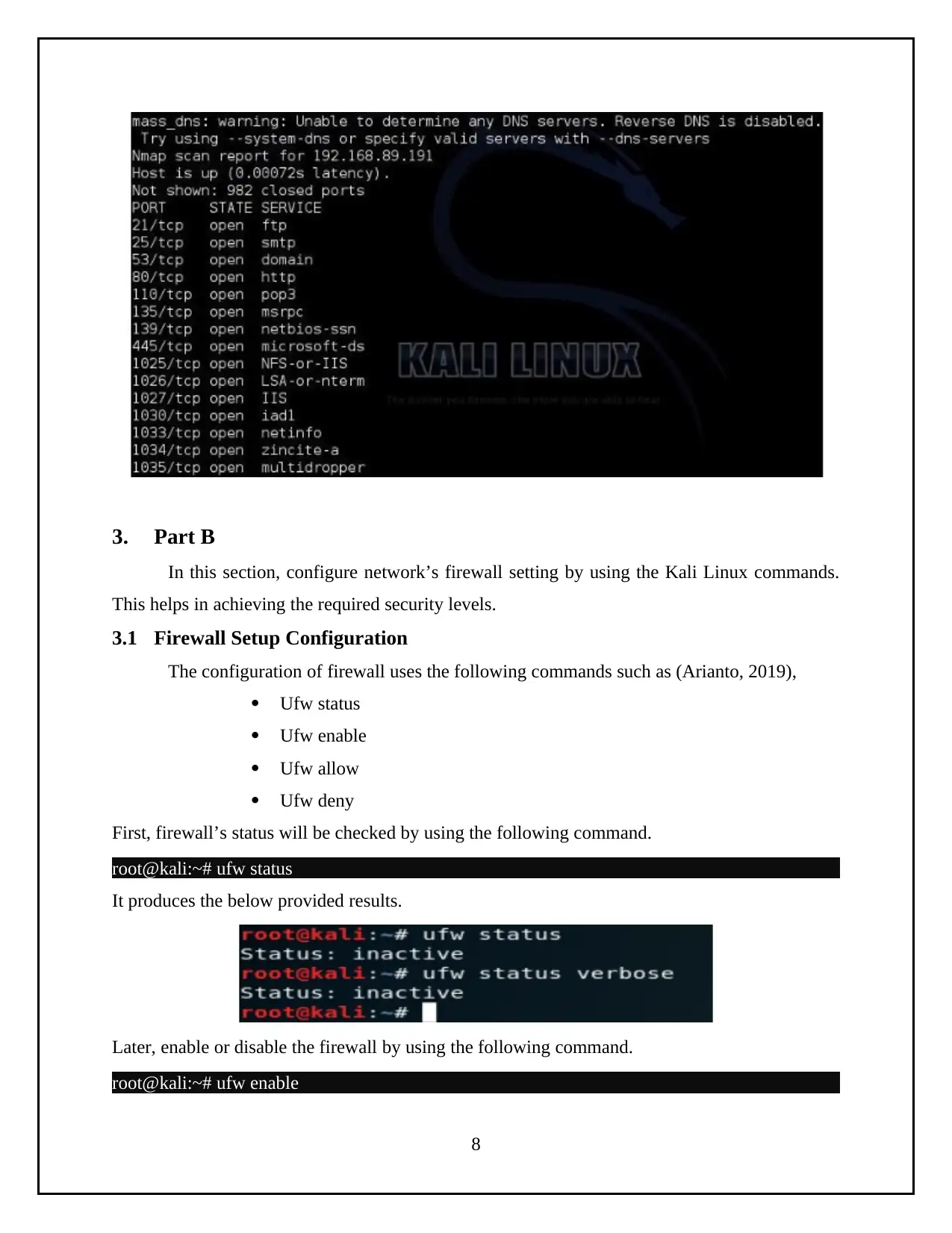
3. Part B
In this section, configure network’s firewall setting by using the Kali Linux commands.
This helps in achieving the required security levels.
3.1 Firewall Setup Configuration
The configuration of firewall uses the following commands such as (Arianto, 2019),
Ufw status
Ufw enable
Ufw allow
Ufw deny
First, firewall’s status will be checked by using the following command.
root@kali:~# ufw status
It produces the below provided results.
Later, enable or disable the firewall by using the following command.
root@kali:~# ufw enable
8
In this section, configure network’s firewall setting by using the Kali Linux commands.
This helps in achieving the required security levels.
3.1 Firewall Setup Configuration
The configuration of firewall uses the following commands such as (Arianto, 2019),
Ufw status
Ufw enable
Ufw allow
Ufw deny
First, firewall’s status will be checked by using the following command.
root@kali:~# ufw status
It produces the below provided results.
Later, enable or disable the firewall by using the following command.
root@kali:~# ufw enable
8
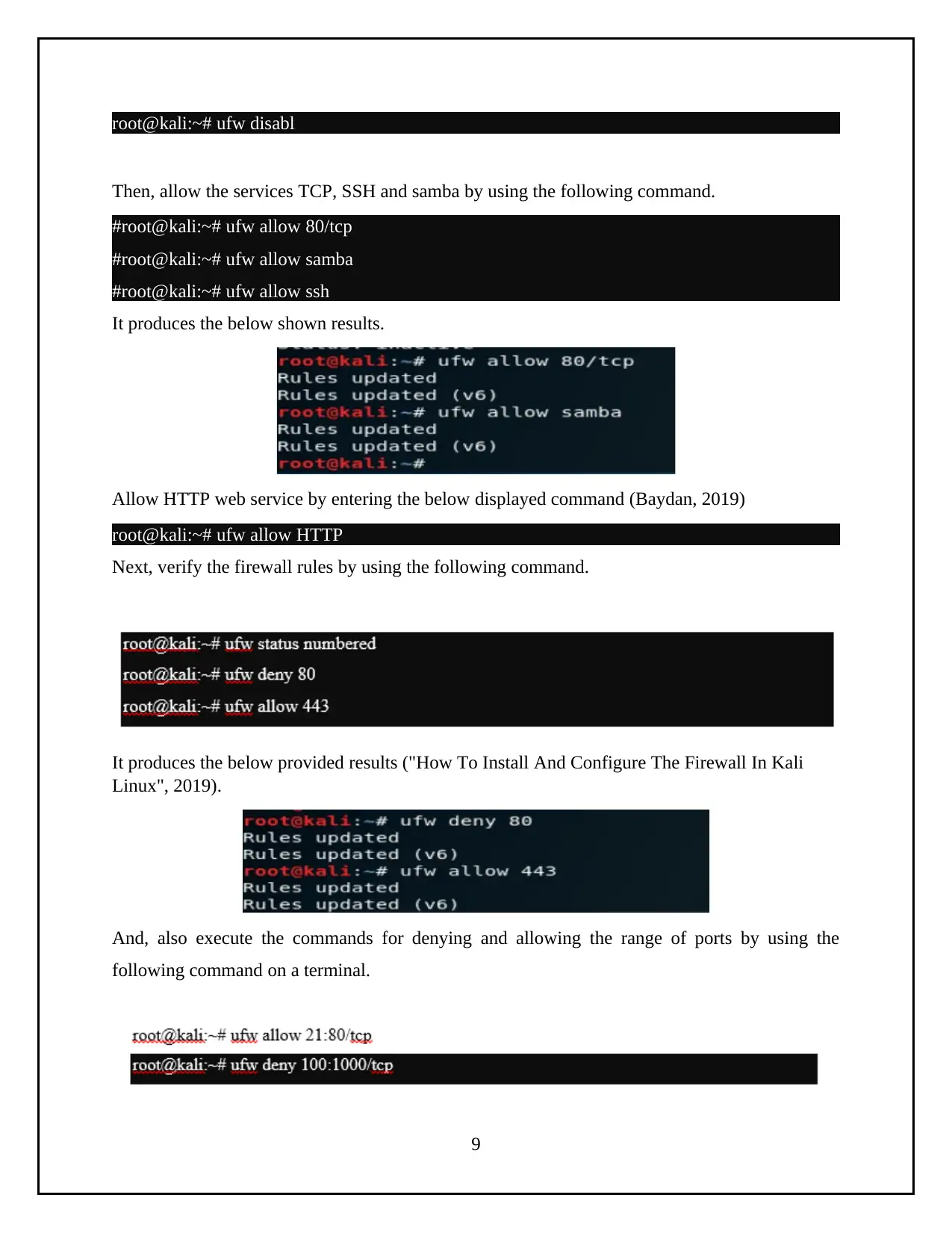
root@kali:~# ufw disabl
Then, allow the services TCP, SSH and samba by using the following command.
#root@kali:~# ufw allow 80/tcp
#root@kali:~# ufw allow samba
#root@kali:~# ufw allow ssh
It produces the below shown results.
Allow HTTP web service by entering the below displayed command (Baydan, 2019)
root@kali:~# ufw allow HTTP
Next, verify the firewall rules by using the following command.
It produces the below provided results ("How To Install And Configure The Firewall In Kali
Linux", 2019).
And, also execute the commands for denying and allowing the range of ports by using the
following command on a terminal.
9
Then, allow the services TCP, SSH and samba by using the following command.
#root@kali:~# ufw allow 80/tcp
#root@kali:~# ufw allow samba
#root@kali:~# ufw allow ssh
It produces the below shown results.
Allow HTTP web service by entering the below displayed command (Baydan, 2019)
root@kali:~# ufw allow HTTP
Next, verify the firewall rules by using the following command.
It produces the below provided results ("How To Install And Configure The Firewall In Kali
Linux", 2019).
And, also execute the commands for denying and allowing the range of ports by using the
following command on a terminal.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




