CMSC 426 - IT Security: Next Generation Firewalls and BIBA Model
VerifiedAdded on 2023/04/21
|9
|1504
|68
Homework Assignment
AI Summary
This assignment provides an overview of next-generation firewalls (NGFWs), contrasting them with traditional firewalls and listing five NGFW products. It also delves into the BIBA integrity model and its differences from the Bell-LaPadula model, illustrating a four-level security clearance model. Furthermore, the assignment includes a security analyst section that presents a data flow diagram for a data science company, identifies threats using the STRIDE model, rates these threats, and proposes mitigation strategies. Desklib offers a platform to explore similar assignments and resources for students.

Running head: IT SECURITY
IT Security
Name of the Student
Name of the University
Author Note:
IT Security
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2IT SECURITY
Table of Contents
1 Next Generation Firewall.................................................................................................3
3. Five “Next Generation Firewall” products......................................................................5
4 How is BIBA different form Bell-LaPadula.....................................................................5
5 Level security clearance model........................................................................................6
6 Security analyst section....................................................................................................7
7 Reference..........................................................................................................................9
Table of Contents
1 Next Generation Firewall.................................................................................................3
3. Five “Next Generation Firewall” products......................................................................5
4 How is BIBA different form Bell-LaPadula.....................................................................5
5 Level security clearance model........................................................................................6
6 Security analyst section....................................................................................................7
7 Reference..........................................................................................................................9

3IT SECURITY
1 Next Generation Firewall
The foremost determination of the paper is to focus on the third generation of the
firewall technology which is commonly termed as the next generation firewall. The
intrusion detection capability of the next generation firewall is much more than the
traditional firewall systems. The bandwidth management are one in a better way with the
help of the next generation firewall 1. The other essential activities of the next generation
firewall are the management of the packet payloads of the network. The networking
traffic can be filtered in a more effective way with the help of the networking activities.
The inspecting capability of the next generation firewall is more advanced and
reliable than the first generation and the second generation of the firewalls. The encrypted
applications of the computers systems can be secured in a better way with the help of the
next generation firewalls. The website-based malware attacks and the advanced phishing
mail attacks can be restricted to a significant with the help of the next generation
firewalls. The packet filtering capabilities of the next generations firewalls are also much
better than the firewalls of the previous two generations of the firewall2. The attacks on
the application layer can be also saved with the help of this edition of the firewall at the
same time it can be said that the threats and the weakness of the earlier editions are
1 Arunkumar, Saritha, et al. "Next generation firewalls for dynamic coalitions." 2017 IEEE SmartWorld,
Ubiquitous Intelligence & Computing, Advanced & Trusted Computed, Scalable Computing &
Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation
(SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI). IEEE, 2017.
2 Brown, S., S. Carlin, and I. Torres-Negron. "Next-Generation Defensive Cyber Operations (DCO)
Platform." Journal of Information Warfare 16.2 (2017): 43-55.
1 Next Generation Firewall
The foremost determination of the paper is to focus on the third generation of the
firewall technology which is commonly termed as the next generation firewall. The
intrusion detection capability of the next generation firewall is much more than the
traditional firewall systems. The bandwidth management are one in a better way with the
help of the next generation firewall 1. The other essential activities of the next generation
firewall are the management of the packet payloads of the network. The networking
traffic can be filtered in a more effective way with the help of the networking activities.
The inspecting capability of the next generation firewall is more advanced and
reliable than the first generation and the second generation of the firewalls. The encrypted
applications of the computers systems can be secured in a better way with the help of the
next generation firewalls. The website-based malware attacks and the advanced phishing
mail attacks can be restricted to a significant with the help of the next generation
firewalls. The packet filtering capabilities of the next generations firewalls are also much
better than the firewalls of the previous two generations of the firewall2. The attacks on
the application layer can be also saved with the help of this edition of the firewall at the
same time it can be said that the threats and the weakness of the earlier editions are
1 Arunkumar, Saritha, et al. "Next generation firewalls for dynamic coalitions." 2017 IEEE SmartWorld,
Ubiquitous Intelligence & Computing, Advanced & Trusted Computed, Scalable Computing &
Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation
(SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI). IEEE, 2017.
2 Brown, S., S. Carlin, and I. Torres-Negron. "Next-Generation Defensive Cyber Operations (DCO)
Platform." Journal of Information Warfare 16.2 (2017): 43-55.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4IT SECURITY
completely removed in this edition of the firewall. The weaknesses of the network are
also categorically removed with the help of the next generation firewalls. The
complications of the HTTP protocol are also saved with the help of the next generation
firewalls3. Identity based security approach are developed with the help of this next
generation firewall. The use of the applications and the websites in a server securely can
be done with the help of the next generation firewalls.
CISCO next generation firewall is an example of the next generation firewalls
which are very much useful to prevent the security breaches and the maintain safety in
the network of the organization. The business issues of the earlier versions of the
firewalls such as their privacy issue can be managed with the help of the next generation
firewalls. The mapping of the IP addresses is done in a better way with the help of this
firewall. The United Threat Management can be done in a better way with the help of the
next generation firewall.
2 Difference from traditional firewall
The next generation firewall is much more reliable as compared with the
traditional firewall. The packet filtering based on the websites and the applications of the
next generation of the next generation firewalls are much better than the traditional
firewalls. Non-disruptiveness is the other difference between the traditional firewalls and
the next generation firewalls along with that the scanning techniques of both the two
3 Fana, Cunqun, et al. "Research on firewall in software defined network." Advances in Computer, Signals
and Systems (2018).
completely removed in this edition of the firewall. The weaknesses of the network are
also categorically removed with the help of the next generation firewalls. The
complications of the HTTP protocol are also saved with the help of the next generation
firewalls3. Identity based security approach are developed with the help of this next
generation firewall. The use of the applications and the websites in a server securely can
be done with the help of the next generation firewalls.
CISCO next generation firewall is an example of the next generation firewalls
which are very much useful to prevent the security breaches and the maintain safety in
the network of the organization. The business issues of the earlier versions of the
firewalls such as their privacy issue can be managed with the help of the next generation
firewalls. The mapping of the IP addresses is done in a better way with the help of this
firewall. The United Threat Management can be done in a better way with the help of the
next generation firewall.
2 Difference from traditional firewall
The next generation firewall is much more reliable as compared with the
traditional firewall. The packet filtering based on the websites and the applications of the
next generation of the next generation firewalls are much better than the traditional
firewalls. Non-disruptiveness is the other difference between the traditional firewalls and
the next generation firewalls along with that the scanning techniques of both the two
3 Fana, Cunqun, et al. "Research on firewall in software defined network." Advances in Computer, Signals
and Systems (2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5IT SECURITY
categories of firewalls are different from each other. The next generation firewalls have
full stack visibility and the traditional firewalls have limited visibility. The future security
threat can be managed with the capabilities of the next generation firewalls unlike the
traditional firewalls.
3. Five “Next Generation Firewall” products
The five next generation firewall products are as followings:
Big IP advanced Firewall Manager.
Palo-Alto next generation firewalls.
FortiGate next generation firewalls.
CISCO firewall.
Sophos XG firewall
4 How is BIBA different form Bell-LaPadula
The difference between BIBA model and the Bell-LaPadula is the formal state
transition system whereas the Bell-LaPadula is the used for the management of the access
control4. The multi-level security polices maintained in the high security zones such as
uses the Bell-LaPadula model as the objects5.
4 Roslan, Saida Nafisah, Isredza Rahmi A. Hamid, and Palaniappan Shamala. "E-Store Management Using
Bell-LaPadula Access Control Security Model." JOIV: International Journal on Informatics Visualization
2.3-2 (2018).
5 Salman, Ola, et al. "Multi-level security for the 5G/IoT ubiquitous network." Fog and Mobile Edge
Computing (FMEC), 2017 Second International Conference on. IEEE, 2017.
categories of firewalls are different from each other. The next generation firewalls have
full stack visibility and the traditional firewalls have limited visibility. The future security
threat can be managed with the capabilities of the next generation firewalls unlike the
traditional firewalls.
3. Five “Next Generation Firewall” products
The five next generation firewall products are as followings:
Big IP advanced Firewall Manager.
Palo-Alto next generation firewalls.
FortiGate next generation firewalls.
CISCO firewall.
Sophos XG firewall
4 How is BIBA different form Bell-LaPadula
The difference between BIBA model and the Bell-LaPadula is the formal state
transition system whereas the Bell-LaPadula is the used for the management of the access
control4. The multi-level security polices maintained in the high security zones such as
uses the Bell-LaPadula model as the objects5.
4 Roslan, Saida Nafisah, Isredza Rahmi A. Hamid, and Palaniappan Shamala. "E-Store Management Using
Bell-LaPadula Access Control Security Model." JOIV: International Journal on Informatics Visualization
2.3-2 (2018).
5 Salman, Ola, et al. "Multi-level security for the 5G/IoT ubiquitous network." Fog and Mobile Edge
Computing (FMEC), 2017 Second International Conference on. IEEE, 2017.

6IT SECURITY
5 Level security clearance model
Let H be the human subject and the J be the object of an organization for the
following table.
Top Secret Only H can have the access.
Secret Both H and J can have the access.
Classified Both H and J have the access to this level
Unclassified Both H and J can have the access.
Table 1: 4 level security clearance model
(Source: Created by the author)
5 Level security clearance model
Let H be the human subject and the J be the object of an organization for the
following table.
Top Secret Only H can have the access.
Secret Both H and J can have the access.
Classified Both H and J have the access to this level
Unclassified Both H and J can have the access.
Table 1: 4 level security clearance model
(Source: Created by the author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
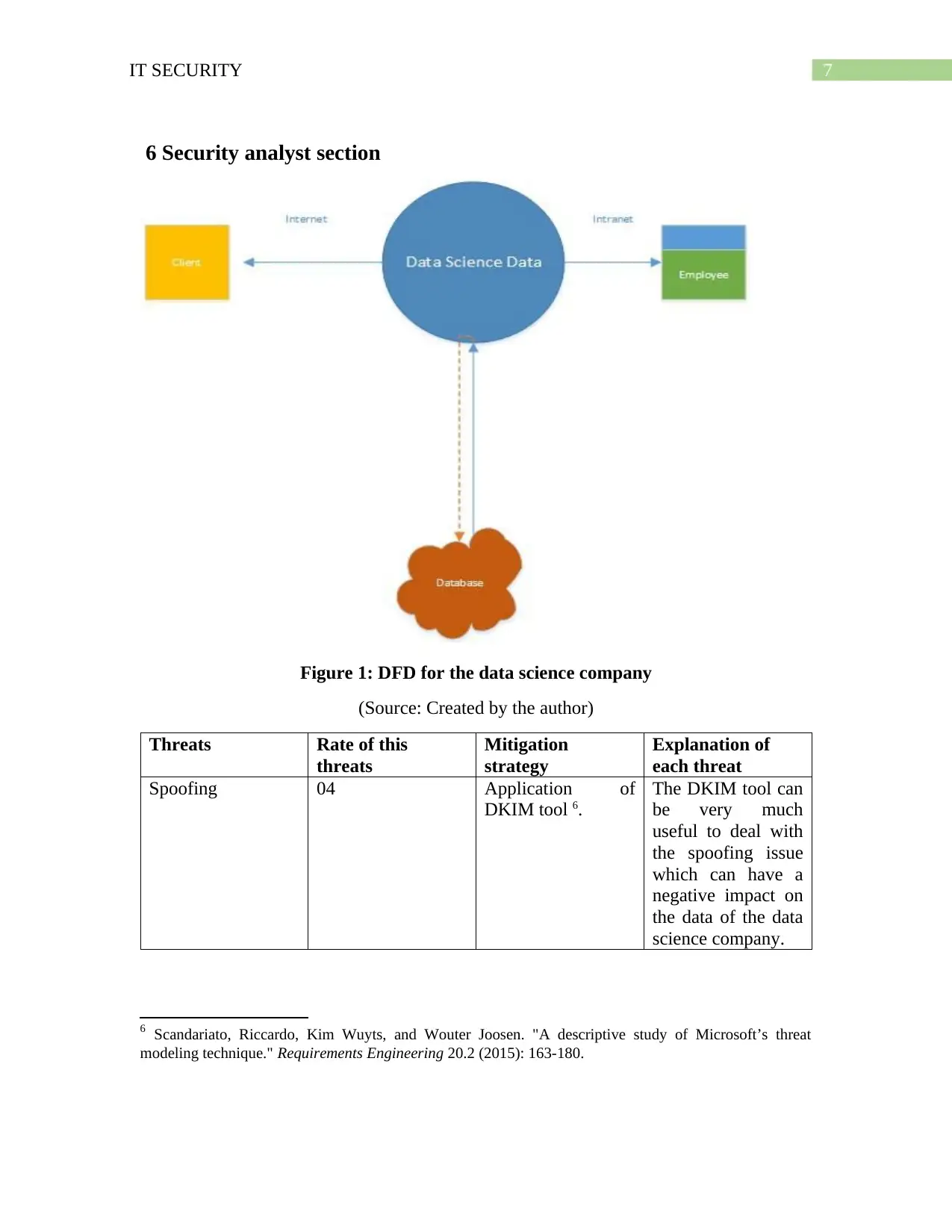
7IT SECURITY
6 Security analyst section
Figure 1: DFD for the data science company
(Source: Created by the author)
Threats Rate of this
threats
Mitigation
strategy
Explanation of
each threat
Spoofing 04 Application of
DKIM tool 6.
The DKIM tool can
be very much
useful to deal with
the spoofing issue
which can have a
negative impact on
the data of the data
science company.
6 Scandariato, Riccardo, Kim Wuyts, and Wouter Joosen. "A descriptive study of Microsoft’s threat
modeling technique." Requirements Engineering 20.2 (2015): 163-180.
6 Security analyst section
Figure 1: DFD for the data science company
(Source: Created by the author)
Threats Rate of this
threats
Mitigation
strategy
Explanation of
each threat
Spoofing 04 Application of
DKIM tool 6.
The DKIM tool can
be very much
useful to deal with
the spoofing issue
which can have a
negative impact on
the data of the data
science company.
6 Scandariato, Riccardo, Kim Wuyts, and Wouter Joosen. "A descriptive study of Microsoft’s threat
modeling technique." Requirements Engineering 20.2 (2015): 163-180.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
8IT SECURITY
Tampering 05 Application of
Tamper resistance
and anti-tamper
software
The anti-tamper
software can help
this data science
organization to
protect the data.
Repudiation 01 Data insurance tool The insurance of
the data of the data
science
organization is
maintained with the
help of the data
insurance tool.
Information
disclosure
04 Data Encryption
technique
The protection of
the data is
maintained with the
help of the data
encryption
technique.
DoS 03 Application of
Arbour networks
and Black Lotus
software
The anti-virus
software programs
are very much
useful to deal with
the security issues
such as DoS.
Elevation of
Privilege
02 Data Monitoring Monitoring of the
data is very much
important for this
data science
organization as the
data are handled by
both clients and
employees.
Table 2: Identification of threats using STRIDE
(Source: Created by the author)
The rating is given out of 5 in terms of the impact of the risk in increasing order
for this data science organization.
Tampering 05 Application of
Tamper resistance
and anti-tamper
software
The anti-tamper
software can help
this data science
organization to
protect the data.
Repudiation 01 Data insurance tool The insurance of
the data of the data
science
organization is
maintained with the
help of the data
insurance tool.
Information
disclosure
04 Data Encryption
technique
The protection of
the data is
maintained with the
help of the data
encryption
technique.
DoS 03 Application of
Arbour networks
and Black Lotus
software
The anti-virus
software programs
are very much
useful to deal with
the security issues
such as DoS.
Elevation of
Privilege
02 Data Monitoring Monitoring of the
data is very much
important for this
data science
organization as the
data are handled by
both clients and
employees.
Table 2: Identification of threats using STRIDE
(Source: Created by the author)
The rating is given out of 5 in terms of the impact of the risk in increasing order
for this data science organization.

9IT SECURITY
7 Reference
Arunkumar, Saritha, et al. "Next generation firewalls for dynamic coalitions." 2017 IEEE
SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computed,
Scalable Computing & Communications, Cloud & Big Data Computing, Internet of
People and Smart City Innovation
(SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI). IEEE, 2017.
Brown, S., S. Carlin, and I. Torres-Negron. "Next-Generation Defensive Cyber
Operations (DCO) Platform." Journal of Information Warfare 16.2 (2017): 43-55.
Fana, Cunqun, et al. "Research on firewall in software defined network." Advances in
Computer, Signals and Systems (2018).
Roslan, Saida Nafisah, Isredza Rahmi A. Hamid, and Palaniappan Shamala. "E-Store
Management Using Bell-LaPadula Access Control Security Model." JOIV: International
Journal on Informatics Visualization 2.3-2 (2018).
Salman, Ola, et al. "Multi-level security for the 5G/IoT ubiquitous network." 2017
Second International Conference on Fog and Mobile Edge Computing (FMEC). IEEE,
2017.
Scandariato, Riccardo, Kim Wuyts, and Wouter Joosen. "A descriptive study of
Microsoft’s threat modeling technique." Requirements Engineering 20.2 (2015): 163-180.
7 Reference
Arunkumar, Saritha, et al. "Next generation firewalls for dynamic coalitions." 2017 IEEE
SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computed,
Scalable Computing & Communications, Cloud & Big Data Computing, Internet of
People and Smart City Innovation
(SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI). IEEE, 2017.
Brown, S., S. Carlin, and I. Torres-Negron. "Next-Generation Defensive Cyber
Operations (DCO) Platform." Journal of Information Warfare 16.2 (2017): 43-55.
Fana, Cunqun, et al. "Research on firewall in software defined network." Advances in
Computer, Signals and Systems (2018).
Roslan, Saida Nafisah, Isredza Rahmi A. Hamid, and Palaniappan Shamala. "E-Store
Management Using Bell-LaPadula Access Control Security Model." JOIV: International
Journal on Informatics Visualization 2.3-2 (2018).
Salman, Ola, et al. "Multi-level security for the 5G/IoT ubiquitous network." 2017
Second International Conference on Fog and Mobile Edge Computing (FMEC). IEEE,
2017.
Scandariato, Riccardo, Kim Wuyts, and Wouter Joosen. "A descriptive study of
Microsoft’s threat modeling technique." Requirements Engineering 20.2 (2015): 163-180.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





