FMEC Modeling and Security Issues: Comprehensive Analysis
VerifiedAdded on 2020/03/04
|10
|2775
|128
Report
AI Summary
This report provides a detailed analysis of Fog and Mobile Edge Computing (FMEC) modeling and security issues. It explores the challenges associated with FMEC, which has emerged to address performance issues in cloud computing. The report investigates various modeling issues, including configuration, connectivity, and integration challenges, as well as security concerns related to network infrastructure, service infrastructure, core infrastructure, virtualization, and user devices. Specific security threats such as Denial of Service (DoS) attacks, man-in-the-middle attacks, and rogue gateway attacks are discussed. The research methodology involves qualitative research, including literature reviews and data collection from research papers and online sources. The report concludes with a summary of findings and potential measures to enhance the security of FMEC services, emphasizing the importance of addressing both modeling and security aspects for the successful implementation of FMEC.

FMEC Modeling & Security Issues
8/16/2017
[Type the abstract of the document here. The abstract is typically a short summary of the contents of
the document. Type the abstract of the document here. The abstract is typically a short summary of
the contents of the document.]
8/16/2017
[Type the abstract of the document here. The abstract is typically a short summary of the contents of
the document. Type the abstract of the document here. The abstract is typically a short summary of
the contents of the document.]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

FMEC Modeling & Security Issues
Table of Contents
Introduction.................................................................................................................................................3
Materials and Methods................................................................................................................................3
FMEC Modeling Issues...............................................................................................................................4
FMEC Security Issues.................................................................................................................................5
Results.........................................................................................................................................................7
Timeline......................................................................................................................................................7
Conclusion...................................................................................................................................................8
References...................................................................................................................................................9
2
Table of Contents
Introduction.................................................................................................................................................3
Materials and Methods................................................................................................................................3
FMEC Modeling Issues...............................................................................................................................4
FMEC Security Issues.................................................................................................................................5
Results.........................................................................................................................................................7
Timeline......................................................................................................................................................7
Conclusion...................................................................................................................................................8
References...................................................................................................................................................9
2

FMEC Modeling & Security Issues
Introduction
Cloud computing has grown to become an integral part of the present day applications and
services that are carried out in the business environment and in association with the individual
users. With the increase in the use and expansion of cloud computing, there are a number of
performance issues that have begun to emerge such as inability to meet the requirements in case
of low latency and mobility support. In order to deal with such problems, a specialized discipline
termed as Fog and Mobile Edge Computing (FMEC) has been created.
There is a lot of research that is going around in the area of FMEC as it provides the ability to the
cloud users to have a close connect with the services. However, there are a number of modeling
and security concerns that have been observed in the FMEC services. It is necessary to have an
idea of these issues to make sure that the services that are provided to the users are safe and
secure. Analysis and research to understand these concerns is important as it would provide a
deeper knowledge on the associated FMEC issues to develop the measures necessary to control
them. Therefore, the research in this area holds a lot of significance [1].
The aim of the research is to list down the modeling and security issues in association with
FMEC by exploring a number of different areas and domains.
Materials and Methods
The research methodology that has been used in order to carry out the research on the topic as
FMEC modeling and security issues is the qualitative research.
The first step that is included in the research is the research preparation by listing down the
research questions that shall be answered in the process. There are cloud computing applications
that are being widely used all across the globe. FMEC services have the attributes that may offer
better quality services; however, these services are being hampered by the issues that are present
in it. It is, therefore, required to answer the questions that are present around several issues in
association with FMEC services.
Many researchers have covered the topics such as, FMEC services, modeling information,
security and privacy issues and numerous others [2]. A literature review of many of these
3
Introduction
Cloud computing has grown to become an integral part of the present day applications and
services that are carried out in the business environment and in association with the individual
users. With the increase in the use and expansion of cloud computing, there are a number of
performance issues that have begun to emerge such as inability to meet the requirements in case
of low latency and mobility support. In order to deal with such problems, a specialized discipline
termed as Fog and Mobile Edge Computing (FMEC) has been created.
There is a lot of research that is going around in the area of FMEC as it provides the ability to the
cloud users to have a close connect with the services. However, there are a number of modeling
and security concerns that have been observed in the FMEC services. It is necessary to have an
idea of these issues to make sure that the services that are provided to the users are safe and
secure. Analysis and research to understand these concerns is important as it would provide a
deeper knowledge on the associated FMEC issues to develop the measures necessary to control
them. Therefore, the research in this area holds a lot of significance [1].
The aim of the research is to list down the modeling and security issues in association with
FMEC by exploring a number of different areas and domains.
Materials and Methods
The research methodology that has been used in order to carry out the research on the topic as
FMEC modeling and security issues is the qualitative research.
The first step that is included in the research is the research preparation by listing down the
research questions that shall be answered in the process. There are cloud computing applications
that are being widely used all across the globe. FMEC services have the attributes that may offer
better quality services; however, these services are being hampered by the issues that are present
in it. It is, therefore, required to answer the questions that are present around several issues in
association with FMEC services.
Many researchers have covered the topics such as, FMEC services, modeling information,
security and privacy issues and numerous others [2]. A literature review of many of these
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
FMEC Modeling & Security Issues
research works is done as the second step in the research process. There are several research
methodologies that are present and it is necessary to come down to a methodology that is
applicable to the research topic. Qualitative method of research is selected as the methodology
because of the nature of the research required to be done. Action research, grounded theory and
phenomenology are the qualitative measures that are used in the research process. Data
collection, data sampling and analysis of the data are the measures that are used and applied in
the series of next steps.
There are research papers, online journals and articles that have been used to collect the data and
gather the necessary information.
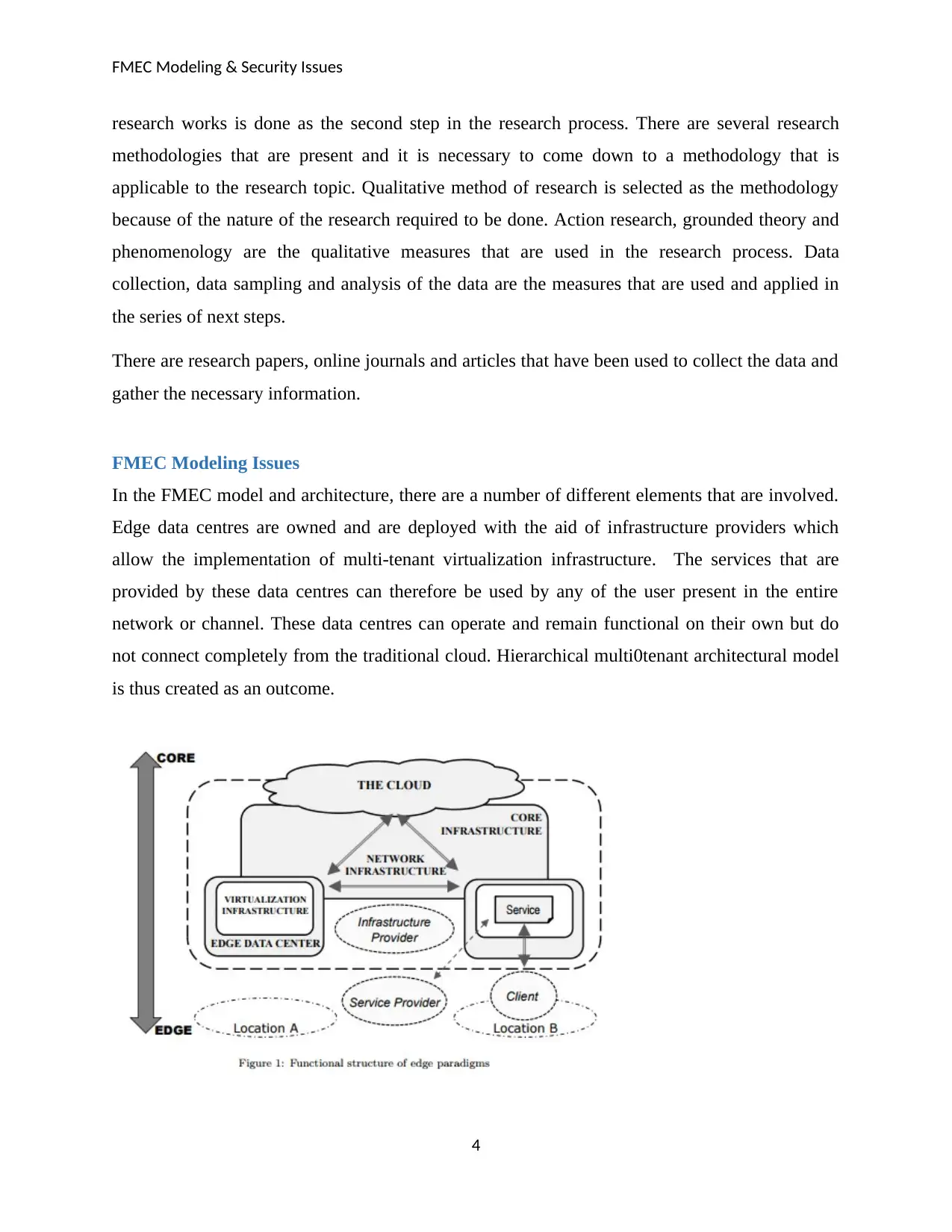
FMEC Modeling Issues
In the FMEC model and architecture, there are a number of different elements that are involved.
Edge data centres are owned and are deployed with the aid of infrastructure providers which
allow the implementation of multi-tenant virtualization infrastructure. The services that are
provided by these data centres can therefore be used by any of the user present in the entire
network or channel. These data centres can operate and remain functional on their own but do
not connect completely from the traditional cloud. Hierarchical multi0tenant architectural model
is thus created as an outcome.
4
research works is done as the second step in the research process. There are several research
methodologies that are present and it is necessary to come down to a methodology that is
applicable to the research topic. Qualitative method of research is selected as the methodology
because of the nature of the research required to be done. Action research, grounded theory and
phenomenology are the qualitative measures that are used in the research process. Data
collection, data sampling and analysis of the data are the measures that are used and applied in
the series of next steps.
There are research papers, online journals and articles that have been used to collect the data and
gather the necessary information.
FMEC Modeling Issues
In the FMEC model and architecture, there are a number of different elements that are involved.
Edge data centres are owned and are deployed with the aid of infrastructure providers which
allow the implementation of multi-tenant virtualization infrastructure. The services that are
provided by these data centres can therefore be used by any of the user present in the entire
network or channel. These data centres can operate and remain functional on their own but do
not connect completely from the traditional cloud. Hierarchical multi0tenant architectural model
is thus created as an outcome.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

FMEC Modeling & Security Issues
Due to the close association with the mobile platforms along with the presence of the traditional
cloud, there are a number of modeling issues that have been observed in association with the
FMEC services [3]. These issues are in the form of configuration, connectivity and integration. It
is because of the reason that the FMEC services are still in their initial expansion phase and are
not adapted by all. The path of transformation and up-gradation is still in progress that brings out
many modeling concerns.
There are heterogeneous hardware and components that are used in FMEC models that have a
great degree of mobility associated with them. The architecture of the FMEC services is de-
centralized and distributed in nature that welcomes many of the security concerns and design
issues as well [4].
FMEC Security Issues
Security is one of the most important and significant requirement that is present in the current
times. It is necessary for all of the services and solutions to ensure that the security is maintained
at every point of time.
In case of FMEC services, there are many of the security challenges and concerns that have been
observed that have the potential to cause damaging impacts on the users.
There are numerous security concerns on the basis of the network infrastructure involved with
the FMEC services. The primary network security issue that has been observed is in the form of
Denial of Service (DoS) attack. These attacks do not cause a complete breakdown of the FMEC
services as these services remain functional in autonomous or semi-autonomous manner.
However, they may cause a significant impact on the performance of the services which may
bring down the user experience and satisfaction level. There may be malicious entities that may
capture a certain part of the network through the methods such as eavesdropping [5]. These
attacks are termed as man in the middle attack and can be extremely damaging as these may
impact the elements that traverse through the targeted nodes. Another network based attack is the
rouge gateway attack in which the attackers launch their own gateway devices in the networking
channels. These attacks have the similar outcome as man in the middle attacks [6].
5
Due to the close association with the mobile platforms along with the presence of the traditional
cloud, there are a number of modeling issues that have been observed in association with the
FMEC services [3]. These issues are in the form of configuration, connectivity and integration. It
is because of the reason that the FMEC services are still in their initial expansion phase and are
not adapted by all. The path of transformation and up-gradation is still in progress that brings out
many modeling concerns.
There are heterogeneous hardware and components that are used in FMEC models that have a
great degree of mobility associated with them. The architecture of the FMEC services is de-
centralized and distributed in nature that welcomes many of the security concerns and design
issues as well [4].
FMEC Security Issues
Security is one of the most important and significant requirement that is present in the current
times. It is necessary for all of the services and solutions to ensure that the security is maintained
at every point of time.
In case of FMEC services, there are many of the security challenges and concerns that have been
observed that have the potential to cause damaging impacts on the users.
There are numerous security concerns on the basis of the network infrastructure involved with
the FMEC services. The primary network security issue that has been observed is in the form of
Denial of Service (DoS) attack. These attacks do not cause a complete breakdown of the FMEC
services as these services remain functional in autonomous or semi-autonomous manner.
However, they may cause a significant impact on the performance of the services which may
bring down the user experience and satisfaction level. There may be malicious entities that may
capture a certain part of the network through the methods such as eavesdropping [5]. These
attacks are termed as man in the middle attack and can be extremely damaging as these may
impact the elements that traverse through the targeted nodes. Another network based attack is the
rouge gateway attack in which the attackers launch their own gateway devices in the networking
channels. These attacks have the similar outcome as man in the middle attacks [6].
5

FMEC Modeling & Security Issues
There are many security issues that are associated with the edge data centres i.e. the service
infrastructure as well. Fog nodes or the devices owned by the users are some of the common
physical elements that the attackers may capture and cause damage to the same. The physical
damage that is caused to any of the elements of the FMEC services can bring down the
performance and functionality of the entire service. The information that passes through the fog
nodes is accessible to certain insider entities and may be accessed by the unauthorized entities by
breaching the security. In either of the cases, the security of the information that traverses
through the nodes is put at risk [7]. The configuration activities that are done in association with
the edge data centres are performed by the individuals that are not experts and may or may not
have received adequate training. As a result, the privileges that are considered to the users may
be implemented incorrectly providing an unauthorized user with additional set of privileges and
control on the services putting the overall security at stake. In the advanced form of security
issues associated with the edge data centres, there may be an event of rogue data centre that may
come up. In this case, the attackers may succeed in creating their own data centre infrastructure
leading to extremely adverse impacts on the security.
There are a number of core infrastructures that are associated with the FMEC services that have
their own set of security issues and concerns. The information flows from one layer to the other
and there may be leakage of information that may be present. Apart from the leakage of
information, the information may be manipulated by the malevolent entities which may lead to a
direct impact on the information security of the FMEC services [8].
Virtualization infrastructure related security concerns are also common in case of the FMEC
services. There may be malicious virtual machines that may be created by the attackers that may
result in the denial of service. These malicious machines may also misuse the resources present
in the entire flow leading to the negative impact on the entire infrastructure. A host system that is
associated with the adversary and is being controlled by the same can also cause many security
threats to the virtual machines that are associated with the host [9].
The loopholes in security present at the end of the user may also result in numerous security
issues and concerns such as loss of the user device leading to the security breaches or the
manipulation of the services due to the presence of security vulnerabilities [10].
6
There are many security issues that are associated with the edge data centres i.e. the service
infrastructure as well. Fog nodes or the devices owned by the users are some of the common
physical elements that the attackers may capture and cause damage to the same. The physical
damage that is caused to any of the elements of the FMEC services can bring down the
performance and functionality of the entire service. The information that passes through the fog
nodes is accessible to certain insider entities and may be accessed by the unauthorized entities by
breaching the security. In either of the cases, the security of the information that traverses
through the nodes is put at risk [7]. The configuration activities that are done in association with
the edge data centres are performed by the individuals that are not experts and may or may not
have received adequate training. As a result, the privileges that are considered to the users may
be implemented incorrectly providing an unauthorized user with additional set of privileges and
control on the services putting the overall security at stake. In the advanced form of security
issues associated with the edge data centres, there may be an event of rogue data centre that may
come up. In this case, the attackers may succeed in creating their own data centre infrastructure
leading to extremely adverse impacts on the security.
There are a number of core infrastructures that are associated with the FMEC services that have
their own set of security issues and concerns. The information flows from one layer to the other
and there may be leakage of information that may be present. Apart from the leakage of
information, the information may be manipulated by the malevolent entities which may lead to a
direct impact on the information security of the FMEC services [8].
Virtualization infrastructure related security concerns are also common in case of the FMEC
services. There may be malicious virtual machines that may be created by the attackers that may
result in the denial of service. These malicious machines may also misuse the resources present
in the entire flow leading to the negative impact on the entire infrastructure. A host system that is
associated with the adversary and is being controlled by the same can also cause many security
threats to the virtual machines that are associated with the host [9].
The loopholes in security present at the end of the user may also result in numerous security
issues and concerns such as loss of the user device leading to the security breaches or the
manipulation of the services due to the presence of security vulnerabilities [10].
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
FMEC Modeling & Security Issues
Results
There are a number of building blocks that lead to the formation of FMEC services. These
building blocks include peer-to-peer systems, wireless networks, distributed systems and many
others. It is required to ensure that the security mechanisms and protocols are installed and
maintained in each of these elements failing which there may be several security occurrences that
may be observed. It is not possible to ensure the security of the entire system only by ensuring
the security of a certain part.
Security issues in case of FMEC services can be clubbed in the categories as network
infrastructure, services infrastructure, core infrastructure, virtualization infrastructure and the
user devices. There are many security issues and concerns that are present in each of these
categories that shall be controlled, detected and prevented. In case of the modeling issues and
concerns, there are problems associated with the connectivity, interoperatibility and integration
that have been observed [11].
The security of the FMEC services can be enhanced by making use of the advanced security
protocols to control the attacks that are present in each of the threat categories.
The research work that is carried out on the topic as FMEC Modeling and Security Issues
resulted in the following set of outcomes:
A brief description of the FMEC services and a deep understanding on its functionalities
and requirements.
A detailed account of the modeling issues that are associated with the FMEC services
A detailed account of the security issues that are associated with the FMEC services
A brief account of the possible measures that may be taken.
Timeline
Week Task Covered in the Week
Week 1 Listing of the topics that may be selected as a
research topic and a brief analysis of each
Week 2 Selection of the research topic and justification
of the same
7
Results
There are a number of building blocks that lead to the formation of FMEC services. These
building blocks include peer-to-peer systems, wireless networks, distributed systems and many
others. It is required to ensure that the security mechanisms and protocols are installed and
maintained in each of these elements failing which there may be several security occurrences that
may be observed. It is not possible to ensure the security of the entire system only by ensuring
the security of a certain part.
Security issues in case of FMEC services can be clubbed in the categories as network
infrastructure, services infrastructure, core infrastructure, virtualization infrastructure and the
user devices. There are many security issues and concerns that are present in each of these
categories that shall be controlled, detected and prevented. In case of the modeling issues and
concerns, there are problems associated with the connectivity, interoperatibility and integration
that have been observed [11].
The security of the FMEC services can be enhanced by making use of the advanced security
protocols to control the attacks that are present in each of the threat categories.
The research work that is carried out on the topic as FMEC Modeling and Security Issues
resulted in the following set of outcomes:
A brief description of the FMEC services and a deep understanding on its functionalities
and requirements.
A detailed account of the modeling issues that are associated with the FMEC services
A detailed account of the security issues that are associated with the FMEC services
A brief account of the possible measures that may be taken.
Timeline
Week Task Covered in the Week
Week 1 Listing of the topics that may be selected as a
research topic and a brief analysis of each
Week 2 Selection of the research topic and justification
of the same
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
FMEC Modeling & Security Issues
Week 3 Analysis of the research work that has already
been done in association with the modeling and
security issues of FMEC
Week 4 Extraction of the relevant information from the
analysis of the research work done in the past
Week 5 Decision on the research methodology to be
used and its justification
Week 6 Data collection on the research topic
Week 7 Data sampling
Week 8 Analysis of the results that are obtained
Week 9 Listing of the outcomes from the research
Week 10 Presentation of the research work and the
results that are obtained
Conclusion
Cloud computing is one of the areas that has been widely researched and has seen a number of
developments and evolutions. Due to the presence of a huge traffic on the cloud, the performance
of certain application started fluctuating. Fog and Mobile Edge Computing (FMEC) is a
discipline that has been formed to overcome the issues that are related with the cloud services.
The FMEC services; however, have a few issues that shall be paid attention to. Some of the
major issues that are observed in the case of FMEC services are the modeling issues along with
the security concerns [12]. There are many problems in these two areas that have been reported
by the users and therefore, it is required to find a solution for the same. Security is one of the
areas that are witnessing some of the major changes and transformations with each passing day.
There are a number of security tools and protocols that are present that need to be enhanced in
order to be applied in association with the FMEC services. The research work done in the area
highlighted the issues to come up with the ideas and concepts that may be applied in order to
develop solutions for the problems.
8
Week 3 Analysis of the research work that has already
been done in association with the modeling and
security issues of FMEC
Week 4 Extraction of the relevant information from the
analysis of the research work done in the past
Week 5 Decision on the research methodology to be
used and its justification
Week 6 Data collection on the research topic
Week 7 Data sampling
Week 8 Analysis of the results that are obtained
Week 9 Listing of the outcomes from the research
Week 10 Presentation of the research work and the
results that are obtained
Conclusion
Cloud computing is one of the areas that has been widely researched and has seen a number of
developments and evolutions. Due to the presence of a huge traffic on the cloud, the performance
of certain application started fluctuating. Fog and Mobile Edge Computing (FMEC) is a
discipline that has been formed to overcome the issues that are related with the cloud services.
The FMEC services; however, have a few issues that shall be paid attention to. Some of the
major issues that are observed in the case of FMEC services are the modeling issues along with
the security concerns [12]. There are many problems in these two areas that have been reported
by the users and therefore, it is required to find a solution for the same. Security is one of the
areas that are witnessing some of the major changes and transformations with each passing day.
There are a number of security tools and protocols that are present that need to be enhanced in
order to be applied in association with the FMEC services. The research work done in the area
highlighted the issues to come up with the ideas and concepts that may be applied in order to
develop solutions for the problems.
8

FMEC Modeling & Security Issues
References
[1]R. Roman, "Mobile Edge Computing, Fog et al.: A Survey and Analysis of Security Threats
and Challenges", 2016. [Online]. Available:
https://www.nics.uma.es/pub/papers/RomanFog16.pdf. [Accessed: 16- Aug- 2017].
[2]V. Vassilakis, I. Chochliouros, A. Spiliopoulou, E. Sfakianakis, M. Belesioti, N.
Bompetsis, M. Wilson, C. Turyagyenda and A. Dardamanis, "Security Analysis of Mobile
Edge Computing in Virtualized Small Cell Networks", IFIP Advances in Information and
Communication Technology, pp. 653-665, 2016.
[3]K. Dolui, "Comparison of Edge Computing Implementations: Fog Computing, Cloudlet and
Mobile Edge Computing", 2017. [Online]. Available:
http://www.eurecom.fr/fr/publication/5193/download/comsys-publi-5193_1.pdf. [Accessed:
16- Aug- 2017].
[4]Y. Ai, "Edge cloud computing technologies for internet of things: A primer - ScienceDirect",
Sciencedirect.com, 2017. [Online]. Available:
http://www.sciencedirect.com/science/article/pii/S2352864817301335. [Accessed: 16-
Aug- 2017].
[5]I. Stojmenovic, S. Wen, X. Huang and H. Luan, "An overview of Fog computing and its
security issues", Concurrency and Computation: Practice and Experience, vol. 28, no. 10,
pp. 2991-3005, 2015.
[6]M. Shahid and M. Sharif, "Cloud Computing Security Models, Architectures, Issues and
Challenges: A Survey", The Smart Computing Review, pp. 602-616, 2015.
[7]M. Peng, S. Yan, K. Zhang and C. Wang, "Fog-computing-based radio access networks:
issues and challenges", IEEE Network, vol. 30, no. 4, pp. 46-53, 2016.
[8]A. Alrawais, A. Alhothaily, C. Hu and X. Cheng, "Fog Computing for the Internet of
Things: Security and Privacy Issues", IEEE Internet Computing, vol. 21, no. 2, pp. 34-42,
2017.
[9]A. Omotunde, F. Adekogbe, O. Ernest and P. Uchendu, "Cloud Computing: An Overview
9
References
[1]R. Roman, "Mobile Edge Computing, Fog et al.: A Survey and Analysis of Security Threats
and Challenges", 2016. [Online]. Available:
https://www.nics.uma.es/pub/papers/RomanFog16.pdf. [Accessed: 16- Aug- 2017].
[2]V. Vassilakis, I. Chochliouros, A. Spiliopoulou, E. Sfakianakis, M. Belesioti, N.
Bompetsis, M. Wilson, C. Turyagyenda and A. Dardamanis, "Security Analysis of Mobile
Edge Computing in Virtualized Small Cell Networks", IFIP Advances in Information and
Communication Technology, pp. 653-665, 2016.
[3]K. Dolui, "Comparison of Edge Computing Implementations: Fog Computing, Cloudlet and
Mobile Edge Computing", 2017. [Online]. Available:
http://www.eurecom.fr/fr/publication/5193/download/comsys-publi-5193_1.pdf. [Accessed:
16- Aug- 2017].
[4]Y. Ai, "Edge cloud computing technologies for internet of things: A primer - ScienceDirect",
Sciencedirect.com, 2017. [Online]. Available:
http://www.sciencedirect.com/science/article/pii/S2352864817301335. [Accessed: 16-
Aug- 2017].
[5]I. Stojmenovic, S. Wen, X. Huang and H. Luan, "An overview of Fog computing and its
security issues", Concurrency and Computation: Practice and Experience, vol. 28, no. 10,
pp. 2991-3005, 2015.
[6]M. Shahid and M. Sharif, "Cloud Computing Security Models, Architectures, Issues and
Challenges: A Survey", The Smart Computing Review, pp. 602-616, 2015.
[7]M. Peng, S. Yan, K. Zhang and C. Wang, "Fog-computing-based radio access networks:
issues and challenges", IEEE Network, vol. 30, no. 4, pp. 46-53, 2016.
[8]A. Alrawais, A. Alhothaily, C. Hu and X. Cheng, "Fog Computing for the Internet of
Things: Security and Privacy Issues", IEEE Internet Computing, vol. 21, no. 2, pp. 34-42,
2017.
[9]A. Omotunde, F. Adekogbe, O. Ernest and P. Uchendu, "Cloud Computing: An Overview
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

FMEC Modeling & Security Issues
of Data Security Issues", Communications on Applied Electronics, vol. 5, no. 9, pp. 14-19,
2016.
[10]S. Khan, S. Parkinson and Y. Qin, "Fog computing security: a review of current
applications and security solutions", Journal of Cloud Computing, vol. 6, no. 1, 2017.
[11]A. Almadhor, "A Fog Computing based Smart Grid Cloud Data Security", International
Journal of Applied Information Systems, vol. 10, no. 6, pp. 1-6, 2016.
[12]R. Sharma, and R. Trivedi, "Literature review: Cloud Computing –Security Issues,
Solution and Technologies", International Journal of Engineering Research, vol. 3, no. 4,
pp. 221-225, 2014.
10
of Data Security Issues", Communications on Applied Electronics, vol. 5, no. 9, pp. 14-19,
2016.
[10]S. Khan, S. Parkinson and Y. Qin, "Fog computing security: a review of current
applications and security solutions", Journal of Cloud Computing, vol. 6, no. 1, 2017.
[11]A. Almadhor, "A Fog Computing based Smart Grid Cloud Data Security", International
Journal of Applied Information Systems, vol. 10, no. 6, pp. 1-6, 2016.
[12]R. Sharma, and R. Trivedi, "Literature review: Cloud Computing –Security Issues,
Solution and Technologies", International Journal of Engineering Research, vol. 3, no. 4,
pp. 221-225, 2014.
10
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





