COIT20265 - Comprehensive Project Plan for FNU Network Redesign
VerifiedAdded on 2024/05/21
|11
|3048
|378
Project
AI Summary
This project plan outlines the redesign of First National University's (FNU) network, addressing connectivity, security, and scalability requirements across its 16 campuses and online programs. The plan details objectives such as connecting all campuses, supporting BYOD/WAH, implementing LAN/WAN technologies, ensuring network security, and facilitating external partnerships. Key constraints include renovating the IP scheme, meeting MTTR/MTBF standards, supporting over 64,000 users, ensuring 99.9% availability, increasing bandwidth, and maintaining network security policies. The statement of work is divided into four parts: FNU Network Security Plan, FNU Network Redesign, FNU Security Technology Implementation, and Proof of Documentation and Implementation, utilizing tools like Cisco Packet Tracer and Kali Linux for design and testing. A RACI matrix defines roles and responsibilities, and a Gantt chart provides a 12-week timeline for project completion. The plan also identifies potential risks and mitigation strategies to ensure successful project delivery. Desklib provides access to similar project plans and solved assignments for students.

Project Plan - COIT20265
1
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Project Plan................................................................................................................................3
Objectives...................................................................................................................................3
Constraints..................................................................................................................................3
Statement of Work.....................................................................................................................5
RACI Matrix..............................................................................................................................7
GANTT Chart............................................................................................................................9
Project Risks and Mitigation Plan............................................................................................10
2
Project Plan................................................................................................................................3
Objectives...................................................................................................................................3
Constraints..................................................................................................................................3
Statement of Work.....................................................................................................................5
RACI Matrix..............................................................................................................................7
GANTT Chart............................................................................................................................9
Project Risks and Mitigation Plan............................................................................................10
2

Project Plan
The aim of the project is to create a new network design on the basis of existing design of
First National University. There are different types of departments in the in the university and
all these departments are going to be connected according to the network requirement
commented by FNU’s management department. The university in total consists of 16
campuses which are as follows: a main campus, 5 regional and 10 metropolitan campuses
which deal with 45,000 campus students. Online and distance program are also conducted by
the university and 15,000 students gets education through this medium. The university also
includes various other facility departments like IT facility. The university has made a
proposal for a robust and strong network design and all the future demands must be fulfilled
by the network design.
Objectives
The objective of the proposed network design are as follows:
- All the university’s campuses that are main campus, metropolitan and regional campuses
must be connected in a great connectivity and should provide a network to its staff and
students.
- Bring your own device (BYOD) and Work at home (WAT) should be applied in the
network for staff and students.
- The network should successfully implement LAN and WAN technology.
- The network constructed must be secured well to keep away the intruders from attacking.
- University have several external partners like research centres, hospitals, technology
partners etc., they all must be able to interact with the network.
- The FNU University have various facility departments in different buildings, they all
must be able to provide facilities to the network.
- The network to be constructed must be robust in design which can meet all the
requirements.
Constraints
The FNU network design have number of constraints in it. Earlier design was lacking many
of the approaches and technologies which are now proposed by the university management
department. So there is a hard need for identification of constraints in the existing network
3
The aim of the project is to create a new network design on the basis of existing design of
First National University. There are different types of departments in the in the university and
all these departments are going to be connected according to the network requirement
commented by FNU’s management department. The university in total consists of 16
campuses which are as follows: a main campus, 5 regional and 10 metropolitan campuses
which deal with 45,000 campus students. Online and distance program are also conducted by
the university and 15,000 students gets education through this medium. The university also
includes various other facility departments like IT facility. The university has made a
proposal for a robust and strong network design and all the future demands must be fulfilled
by the network design.
Objectives
The objective of the proposed network design are as follows:
- All the university’s campuses that are main campus, metropolitan and regional campuses
must be connected in a great connectivity and should provide a network to its staff and
students.
- Bring your own device (BYOD) and Work at home (WAT) should be applied in the
network for staff and students.
- The network should successfully implement LAN and WAN technology.
- The network constructed must be secured well to keep away the intruders from attacking.
- University have several external partners like research centres, hospitals, technology
partners etc., they all must be able to interact with the network.
- The FNU University have various facility departments in different buildings, they all
must be able to provide facilities to the network.
- The network to be constructed must be robust in design which can meet all the
requirements.
Constraints
The FNU network design have number of constraints in it. Earlier design was lacking many
of the approaches and technologies which are now proposed by the university management
department. So there is a hard need for identification of constraints in the existing network
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

and the new requirements made by the FNU management. The below are some of the key
constraints of the network:
- To renovate the existing network IP scheme.
- The Mean time to repair (MTTR) should be maximum of 90 minutes and Mean time
between failures (MTBF) must be 6000 hours for the network as proposed by the
university.
- More than 64,000 users should be able to connect to the network.
- The availability of the network must always be 99.9% time.
- To speed up the usage of application over the network the bandwidth must be increased.
- Flexibility must be there on the network so that future demands are fulfilled.
- Suitability of the Network Security Policies (NSP) is a must so that network is highly
secured.
- Cost of the project must be met accordingly.
- Scheduled design implementation must be done for the achievement of the goal in
meantime.
- Awareness of the new Network policies
4
constraints of the network:
- To renovate the existing network IP scheme.
- The Mean time to repair (MTTR) should be maximum of 90 minutes and Mean time
between failures (MTBF) must be 6000 hours for the network as proposed by the
university.
- More than 64,000 users should be able to connect to the network.
- The availability of the network must always be 99.9% time.
- To speed up the usage of application over the network the bandwidth must be increased.
- Flexibility must be there on the network so that future demands are fulfilled.
- Suitability of the Network Security Policies (NSP) is a must so that network is highly
secured.
- Cost of the project must be met accordingly.
- Scheduled design implementation must be done for the achievement of the goal in
meantime.
- Awareness of the new Network policies
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Statement of Work
The network project consists of different stages and parts. Below are the phases of the
statement of work:
Part – 1
FNU Network Security Plan
New requirements demanded by the management of FNU needs to be fulfilled by the
overhauled network design. New security policies must be applied to secure the network of
FNU. The following are the issues that have to be resolved in the current network structure of
FNU:
- The network must be so strong and robust that intruders cannot attack the network.
- The operation work must be provided by the backup facility in an unconditional situation.
- There are different kinds of security policies that have to be implemented over the
network like – ACL policies, Email policies, Vulnerability policies, Physical security
policies, encryption policies.
Part – 2
FNU Network Redesign
The network redesign of FNUs existing network includes several components. There is a
requirement of security, scalability and availability of the network through the time in the
network design. Below are some of the changes that are needed for the redesign of the
network:
- The network must be so redesigned that all the users and devices included in the design
must be connected and should be communicable.
- Security policies must be applied to defend the network from attackers and intruders.
- Network in FNU should include Wireless Hotspot for wireless connectivity.
- Successful implementation of LAN and WAN of FNU will provide better connectivity.
- Proxy servers, DMZ (Demilitarized Zones), ACL like security technologies can be
applied to the network.
Part – 3
5
The network project consists of different stages and parts. Below are the phases of the
statement of work:
Part – 1
FNU Network Security Plan
New requirements demanded by the management of FNU needs to be fulfilled by the
overhauled network design. New security policies must be applied to secure the network of
FNU. The following are the issues that have to be resolved in the current network structure of
FNU:
- The network must be so strong and robust that intruders cannot attack the network.
- The operation work must be provided by the backup facility in an unconditional situation.
- There are different kinds of security policies that have to be implemented over the
network like – ACL policies, Email policies, Vulnerability policies, Physical security
policies, encryption policies.
Part – 2
FNU Network Redesign
The network redesign of FNUs existing network includes several components. There is a
requirement of security, scalability and availability of the network through the time in the
network design. Below are some of the changes that are needed for the redesign of the
network:
- The network must be so redesigned that all the users and devices included in the design
must be connected and should be communicable.
- Security policies must be applied to defend the network from attackers and intruders.
- Network in FNU should include Wireless Hotspot for wireless connectivity.
- Successful implementation of LAN and WAN of FNU will provide better connectivity.
- Proxy servers, DMZ (Demilitarized Zones), ACL like security technologies can be
applied to the network.
Part – 3
5

FNU Security Technology Implementation
The security of the FNU network is the key task and it is the most important need of the
network. FNU network must be so strong and robust that it can handle the attacks and cannot
be penetrated. The solution for such a great secured network is to implement latest security
features and policies to ensure the security of the network. These network security practices
will keep away the intruders and will prevent the network from cyber attacks.to provide best
security prevention from the outside network following can be the solution for security:
- Firewalls
- Software security technologies
- Intrusion Detection System
- Demilitarised Zones
- Availability of security
- Intrusion Prevention Systems
Part – 4
Proof of documentation and implementation for FNU
The documentation of the project is according to the case study of First National University.
The documentation includes all the features and requirements of FNU and the needs to be
fulfilled. The project network design is constructed on Cisco Packet Tracer. Cisco packet
tracer is a great implementation tool for network design and their visualisation. The network
design testing is done on Kali Linux which is a Linux Operating System for networking.
The documentation of the project will include all the network design related technologies
implemented and it’s testing.
6
The security of the FNU network is the key task and it is the most important need of the
network. FNU network must be so strong and robust that it can handle the attacks and cannot
be penetrated. The solution for such a great secured network is to implement latest security
features and policies to ensure the security of the network. These network security practices
will keep away the intruders and will prevent the network from cyber attacks.to provide best
security prevention from the outside network following can be the solution for security:
- Firewalls
- Software security technologies
- Intrusion Detection System
- Demilitarised Zones
- Availability of security
- Intrusion Prevention Systems
Part – 4
Proof of documentation and implementation for FNU
The documentation of the project is according to the case study of First National University.
The documentation includes all the features and requirements of FNU and the needs to be
fulfilled. The project network design is constructed on Cisco Packet Tracer. Cisco packet
tracer is a great implementation tool for network design and their visualisation. The network
design testing is done on Kali Linux which is a Linux Operating System for networking.
The documentation of the project will include all the network design related technologies
implemented and it’s testing.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
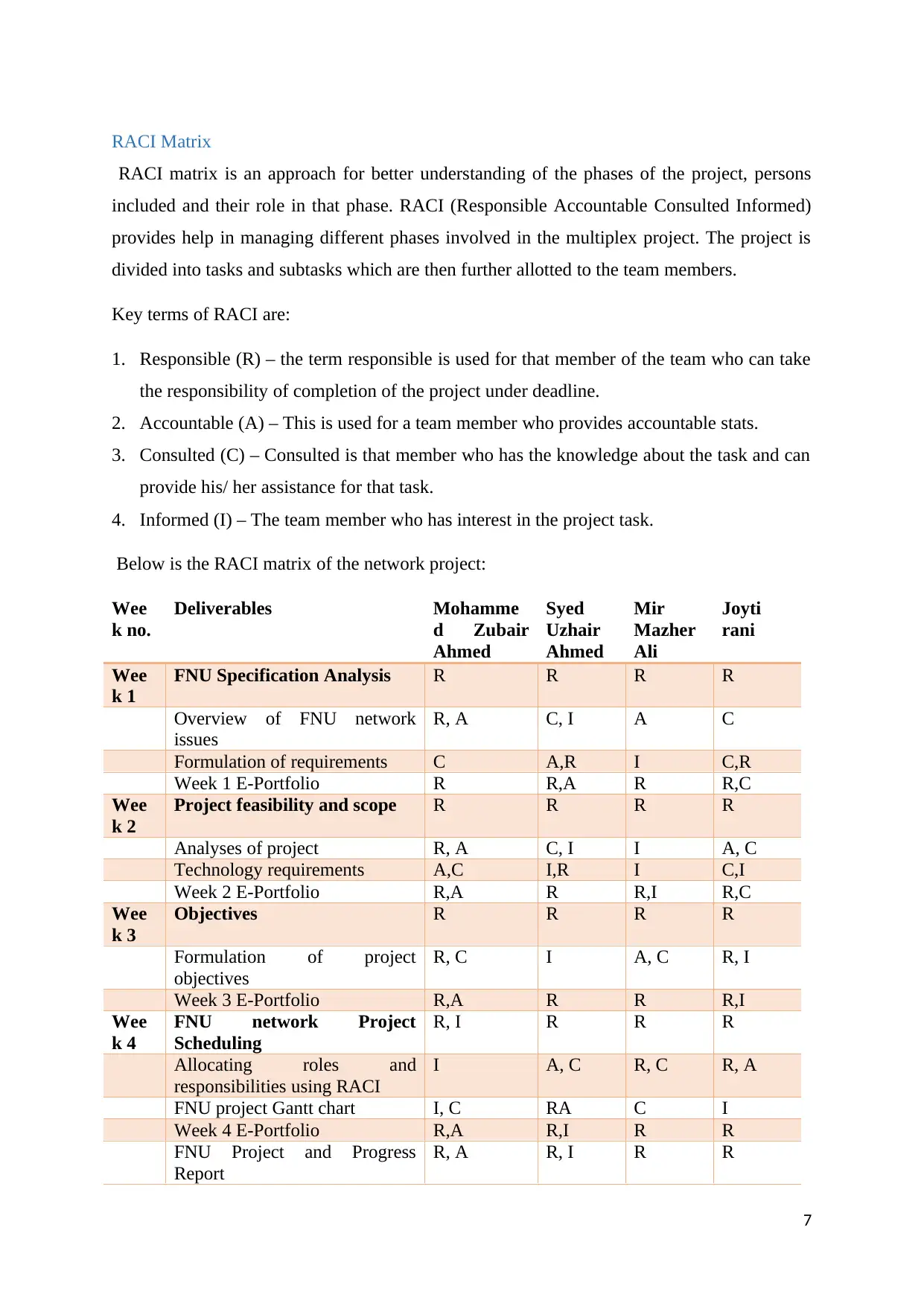
RACI Matrix
RACI matrix is an approach for better understanding of the phases of the project, persons
included and their role in that phase. RACI (Responsible Accountable Consulted Informed)
provides help in managing different phases involved in the multiplex project. The project is
divided into tasks and subtasks which are then further allotted to the team members.
Key terms of RACI are:
1. Responsible (R) – the term responsible is used for that member of the team who can take
the responsibility of completion of the project under deadline.
2. Accountable (A) – This is used for a team member who provides accountable stats.
3. Consulted (C) – Consulted is that member who has the knowledge about the task and can
provide his/ her assistance for that task.
4. Informed (I) – The team member who has interest in the project task.
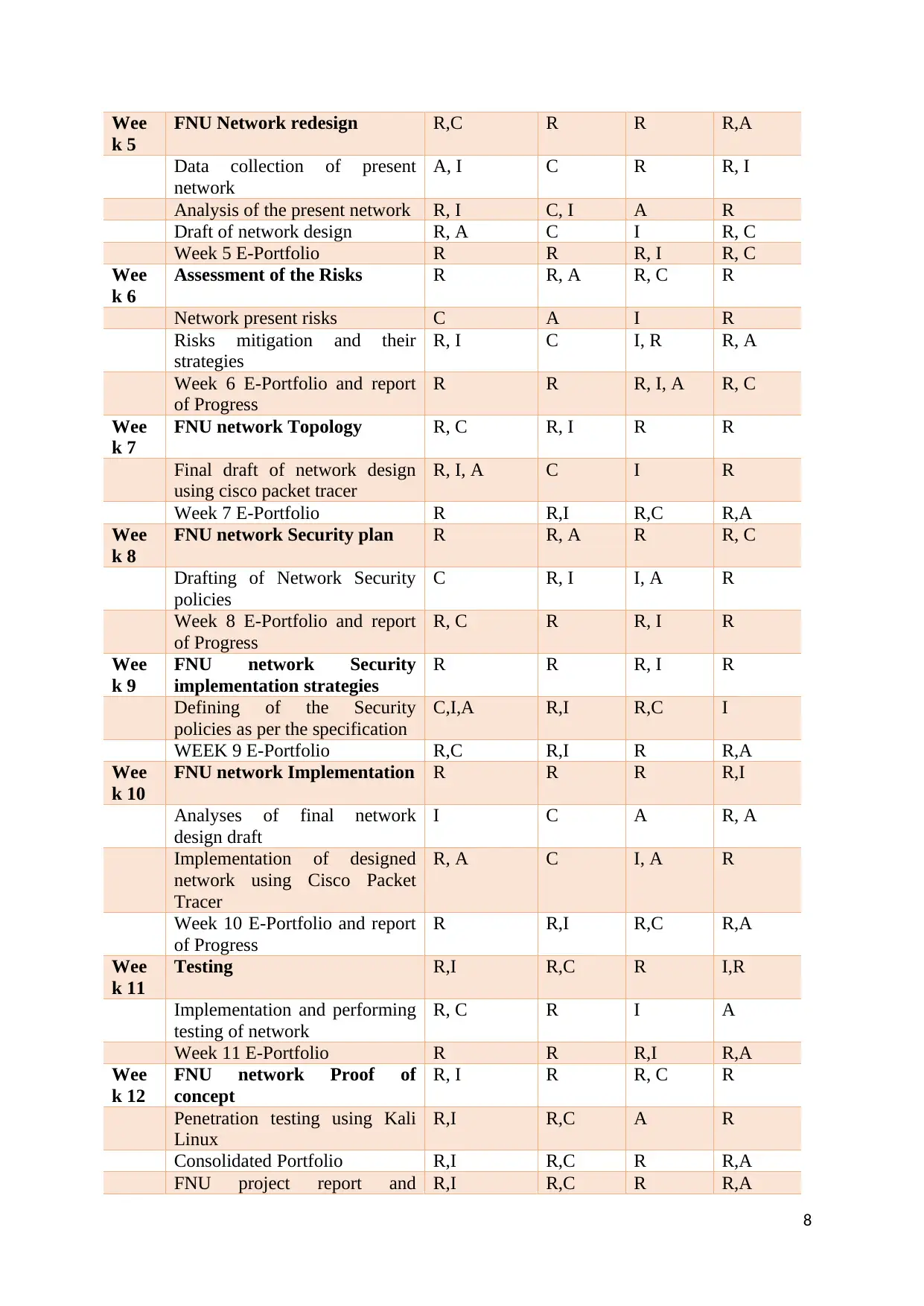
Below is the RACI matrix of the network project:
Wee
k no.
Deliverables Mohamme
d Zubair
Ahmed
Syed
Uzhair
Ahmed
Mir
Mazher
Ali
Joyti
rani
Wee
k 1
FNU Specification Analysis R R R R
Overview of FNU network
issues
R, A C, I A C
Formulation of requirements C A,R I C,R
Week 1 E-Portfolio R R,A R R,C
Wee
k 2
Project feasibility and scope R R R R
Analyses of project R, A C, I I A, C
Technology requirements A,C I,R I C,I
Week 2 E-Portfolio R,A R R,I R,C
Wee
k 3
Objectives R R R R
Formulation of project
objectives
R, C I A, C R, I
Week 3 E-Portfolio R,A R R R,I
Wee
k 4
FNU network Project
Scheduling
R, I R R R
Allocating roles and
responsibilities using RACI
I A, C R, C R, A
FNU project Gantt chart I, C RA C I
Week 4 E-Portfolio R,A R,I R R
FNU Project and Progress
Report
R, A R, I R R
7
RACI matrix is an approach for better understanding of the phases of the project, persons
included and their role in that phase. RACI (Responsible Accountable Consulted Informed)
provides help in managing different phases involved in the multiplex project. The project is
divided into tasks and subtasks which are then further allotted to the team members.
Key terms of RACI are:
1. Responsible (R) – the term responsible is used for that member of the team who can take
the responsibility of completion of the project under deadline.
2. Accountable (A) – This is used for a team member who provides accountable stats.
3. Consulted (C) – Consulted is that member who has the knowledge about the task and can
provide his/ her assistance for that task.
4. Informed (I) – The team member who has interest in the project task.
Below is the RACI matrix of the network project:
Wee
k no.
Deliverables Mohamme
d Zubair
Ahmed
Syed
Uzhair
Ahmed
Mir
Mazher
Ali
Joyti
rani
Wee
k 1
FNU Specification Analysis R R R R
Overview of FNU network
issues
R, A C, I A C
Formulation of requirements C A,R I C,R
Week 1 E-Portfolio R R,A R R,C
Wee
k 2
Project feasibility and scope R R R R
Analyses of project R, A C, I I A, C
Technology requirements A,C I,R I C,I
Week 2 E-Portfolio R,A R R,I R,C
Wee
k 3
Objectives R R R R
Formulation of project
objectives
R, C I A, C R, I
Week 3 E-Portfolio R,A R R R,I
Wee
k 4
FNU network Project
Scheduling
R, I R R R
Allocating roles and
responsibilities using RACI
I A, C R, C R, A
FNU project Gantt chart I, C RA C I
Week 4 E-Portfolio R,A R,I R R
FNU Project and Progress
Report
R, A R, I R R
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Wee
k 5
FNU Network redesign R,C R R R,A
Data collection of present
network
A, I C R R, I
Analysis of the present network R, I C, I A R
Draft of network design R, A C I R, C
Week 5 E-Portfolio R R R, I R, C
Wee
k 6
Assessment of the Risks R R, A R, C R
Network present risks C A I R
Risks mitigation and their
strategies
R, I C I, R R, A
Week 6 E-Portfolio and report
of Progress
R R R, I, A R, C
Wee
k 7
FNU network Topology R, C R, I R R
Final draft of network design
using cisco packet tracer
R, I, A C I R
Week 7 E-Portfolio R R,I R,C R,A
Wee
k 8
FNU network Security plan R R, A R R, C
Drafting of Network Security
policies
C R, I I, A R
Week 8 E-Portfolio and report
of Progress
R, C R R, I R
Wee
k 9
FNU network Security
implementation strategies
R R R, I R
Defining of the Security
policies as per the specification
C,I,A R,I R,C I
WEEK 9 E-Portfolio R,C R,I R R,A
Wee
k 10
FNU network Implementation R R R R,I
Analyses of final network
design draft
I C A R, A
Implementation of designed
network using Cisco Packet
Tracer
R, A C I, A R
Week 10 E-Portfolio and report
of Progress
R R,I R,C R,A
Wee
k 11
Testing R,I R,C R I,R
Implementation and performing
testing of network
R, C R I A
Week 11 E-Portfolio R R R,I R,A
Wee
k 12
FNU network Proof of
concept
R, I R R, C R
Penetration testing using Kali
Linux
R,I R,C A R
Consolidated Portfolio R,I R,C R R,A
FNU project report and R,I R,C R R,A
8
k 5
FNU Network redesign R,C R R R,A
Data collection of present
network
A, I C R R, I
Analysis of the present network R, I C, I A R
Draft of network design R, A C I R, C
Week 5 E-Portfolio R R R, I R, C
Wee
k 6
Assessment of the Risks R R, A R, C R
Network present risks C A I R
Risks mitigation and their
strategies
R, I C I, R R, A
Week 6 E-Portfolio and report
of Progress
R R R, I, A R, C
Wee
k 7
FNU network Topology R, C R, I R R
Final draft of network design
using cisco packet tracer
R, I, A C I R
Week 7 E-Portfolio R R,I R,C R,A
Wee
k 8
FNU network Security plan R R, A R R, C
Drafting of Network Security
policies
C R, I I, A R
Week 8 E-Portfolio and report
of Progress
R, C R R, I R
Wee
k 9
FNU network Security
implementation strategies
R R R, I R
Defining of the Security
policies as per the specification
C,I,A R,I R,C I
WEEK 9 E-Portfolio R,C R,I R R,A
Wee
k 10
FNU network Implementation R R R R,I
Analyses of final network
design draft
I C A R, A
Implementation of designed
network using Cisco Packet
Tracer
R, A C I, A R
Week 10 E-Portfolio and report
of Progress
R R,I R,C R,A
Wee
k 11
Testing R,I R,C R I,R
Implementation and performing
testing of network
R, C R I A
Week 11 E-Portfolio R R R,I R,A
Wee
k 12
FNU network Proof of
concept
R, I R R, C R
Penetration testing using Kali
Linux
R,I R,C A R
Consolidated Portfolio R,I R,C R R,A
FNU project report and R,I R,C R R,A
8
presentation
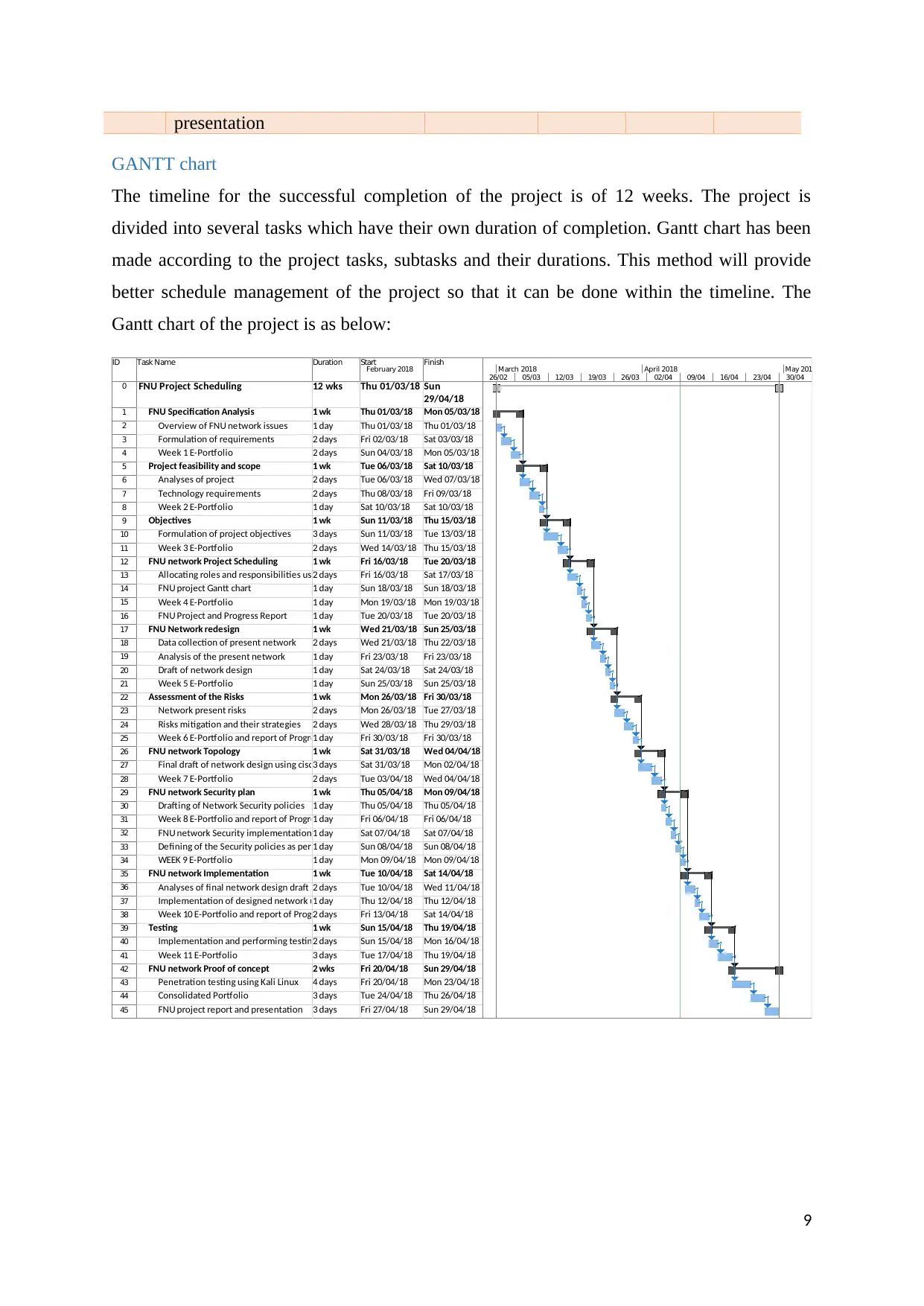
GANTT chart
The timeline for the successful completion of the project is of 12 weeks. The project is
divided into several tasks which have their own duration of completion. Gantt chart has been
made according to the project tasks, subtasks and their durations. This method will provide
better schedule management of the project so that it can be done within the timeline. The
Gantt chart of the project is as below:
ID Task Name Duration Start Finish
0 FNU Project Scheduling 12 wks Thu 01/03/18 Sun
29/04/18
1 FNU Specification Analysis 1 wk Thu 01/03/18 Mon 05/03/18
2 Overview of FNU network issues 1 day Thu 01/03/18 Thu 01/03/18
3 Formulation of requirements 2 days Fri 02/03/18 Sat 03/03/18
4 Week 1 E-Portfolio 2 days Sun 04/03/18 Mon 05/03/18
5 Project feasibility and scope 1 wk Tue 06/03/18 Sat 10/03/18
6 Analyses of project 2 days Tue 06/03/18 Wed 07/03/18
7 Technology requirements 2 days Thu 08/03/18 Fri 09/03/18
8 Week 2 E-Portfolio 1 day Sat 10/03/18 Sat 10/03/18
9 Objectives 1 wk Sun 11/03/18 Thu 15/03/18
10 Formulation of project objectives 3 days Sun 11/03/18 Tue 13/03/18
11 Week 3 E-Portfolio 2 days Wed 14/03/18 Thu 15/03/18
12 FNU network Project Scheduling 1 wk Fri 16/03/18 Tue 20/03/18
13 Allocating roles and responsibilities using RACI2 days Fri 16/03/18 Sat 17/03/18
14 FNU project Gantt chart 1 day Sun 18/03/18 Sun 18/03/18
15 Week 4 E-Portfolio 1 day Mon 19/03/18 Mon 19/03/18
16 FNU Project and Progress Report 1 day Tue 20/03/18 Tue 20/03/18
17 FNU Network redesign 1 wk Wed 21/03/18 Sun 25/03/18
18 Data collection of present network 2 days Wed 21/03/18 Thu 22/03/18
19 Analysis of the present network 1 day Fri 23/03/18 Fri 23/03/18
20 Draft of network design 1 day Sat 24/03/18 Sat 24/03/18
21 Week 5 E-Portfolio 1 day Sun 25/03/18 Sun 25/03/18
22 Assessment of the Risks 1 wk Mon 26/03/18 Fri 30/03/18
23 Network present risks 2 days Mon 26/03/18 Tue 27/03/18
24 Risks mitigation and their strategies 2 days Wed 28/03/18 Thu 29/03/18
25 Week 6 E-Portfolio and report of Progress1 day Fri 30/03/18 Fri 30/03/18
26 FNU network Topology 1 wk Sat 31/03/18 Wed 04/04/18
27 Final draft of network design using cisco packet tracer3 days Sat 31/03/18 Mon 02/04/18
28 Week 7 E-Portfolio 2 days Tue 03/04/18 Wed 04/04/18
29 FNU network Security plan 1 wk Thu 05/04/18 Mon 09/04/18
30 Drafting of Network Security policies 1 day Thu 05/04/18 Thu 05/04/18
31 Week 8 E-Portfolio and report of Progress1 day Fri 06/04/18 Fri 06/04/18
32 FNU network Security implementation strategies1 day Sat 07/04/18 Sat 07/04/18
33 Defining of the Security policies as per the specification1 day Sun 08/04/18 Sun 08/04/18
34 WEEK 9 E-Portfolio 1 day Mon 09/04/18 Mon 09/04/18
35 FNU network Implementation 1 wk Tue 10/04/18 Sat 14/04/18
36 Analyses of final network design draft 2 days Tue 10/04/18 Wed 11/04/18
37 Implementation of designed network using Cisco Packet tracer1 day Thu 12/04/18 Thu 12/04/18
38 Week 10 E-Portfolio and report of Progress2 days Fri 13/04/18 Sat 14/04/18
39 Testing 1 wk Sun 15/04/18 Thu 19/04/18
40 Implementation and performing testing of network2 days Sun 15/04/18 Mon 16/04/18
41 Week 11 E-Portfolio 3 days Tue 17/04/18 Thu 19/04/18
42 FNU network Proof of concept 2 wks Fri 20/04/18 Sun 29/04/18
43 Penetration testing using Kali Linux 4 days Fri 20/04/18 Mon 23/04/18
44 Consolidated Portfolio 3 days Tue 24/04/18 Thu 26/04/18
45 FNU project report and presentation 3 days Fri 27/04/18 Sun 29/04/18
26/02 05/03 12/03 19/03 26/03 02/04 09/04 16/04 23/04 30/04 07/05
February 2018 March 2018 April 2018 May 2018
9
GANTT chart
The timeline for the successful completion of the project is of 12 weeks. The project is
divided into several tasks which have their own duration of completion. Gantt chart has been
made according to the project tasks, subtasks and their durations. This method will provide
better schedule management of the project so that it can be done within the timeline. The
Gantt chart of the project is as below:
ID Task Name Duration Start Finish
0 FNU Project Scheduling 12 wks Thu 01/03/18 Sun
29/04/18
1 FNU Specification Analysis 1 wk Thu 01/03/18 Mon 05/03/18
2 Overview of FNU network issues 1 day Thu 01/03/18 Thu 01/03/18
3 Formulation of requirements 2 days Fri 02/03/18 Sat 03/03/18
4 Week 1 E-Portfolio 2 days Sun 04/03/18 Mon 05/03/18
5 Project feasibility and scope 1 wk Tue 06/03/18 Sat 10/03/18
6 Analyses of project 2 days Tue 06/03/18 Wed 07/03/18
7 Technology requirements 2 days Thu 08/03/18 Fri 09/03/18
8 Week 2 E-Portfolio 1 day Sat 10/03/18 Sat 10/03/18
9 Objectives 1 wk Sun 11/03/18 Thu 15/03/18
10 Formulation of project objectives 3 days Sun 11/03/18 Tue 13/03/18
11 Week 3 E-Portfolio 2 days Wed 14/03/18 Thu 15/03/18
12 FNU network Project Scheduling 1 wk Fri 16/03/18 Tue 20/03/18
13 Allocating roles and responsibilities using RACI2 days Fri 16/03/18 Sat 17/03/18
14 FNU project Gantt chart 1 day Sun 18/03/18 Sun 18/03/18
15 Week 4 E-Portfolio 1 day Mon 19/03/18 Mon 19/03/18
16 FNU Project and Progress Report 1 day Tue 20/03/18 Tue 20/03/18
17 FNU Network redesign 1 wk Wed 21/03/18 Sun 25/03/18
18 Data collection of present network 2 days Wed 21/03/18 Thu 22/03/18
19 Analysis of the present network 1 day Fri 23/03/18 Fri 23/03/18
20 Draft of network design 1 day Sat 24/03/18 Sat 24/03/18
21 Week 5 E-Portfolio 1 day Sun 25/03/18 Sun 25/03/18
22 Assessment of the Risks 1 wk Mon 26/03/18 Fri 30/03/18
23 Network present risks 2 days Mon 26/03/18 Tue 27/03/18
24 Risks mitigation and their strategies 2 days Wed 28/03/18 Thu 29/03/18
25 Week 6 E-Portfolio and report of Progress1 day Fri 30/03/18 Fri 30/03/18
26 FNU network Topology 1 wk Sat 31/03/18 Wed 04/04/18
27 Final draft of network design using cisco packet tracer3 days Sat 31/03/18 Mon 02/04/18
28 Week 7 E-Portfolio 2 days Tue 03/04/18 Wed 04/04/18
29 FNU network Security plan 1 wk Thu 05/04/18 Mon 09/04/18
30 Drafting of Network Security policies 1 day Thu 05/04/18 Thu 05/04/18
31 Week 8 E-Portfolio and report of Progress1 day Fri 06/04/18 Fri 06/04/18
32 FNU network Security implementation strategies1 day Sat 07/04/18 Sat 07/04/18
33 Defining of the Security policies as per the specification1 day Sun 08/04/18 Sun 08/04/18
34 WEEK 9 E-Portfolio 1 day Mon 09/04/18 Mon 09/04/18
35 FNU network Implementation 1 wk Tue 10/04/18 Sat 14/04/18
36 Analyses of final network design draft 2 days Tue 10/04/18 Wed 11/04/18
37 Implementation of designed network using Cisco Packet tracer1 day Thu 12/04/18 Thu 12/04/18
38 Week 10 E-Portfolio and report of Progress2 days Fri 13/04/18 Sat 14/04/18
39 Testing 1 wk Sun 15/04/18 Thu 19/04/18
40 Implementation and performing testing of network2 days Sun 15/04/18 Mon 16/04/18
41 Week 11 E-Portfolio 3 days Tue 17/04/18 Thu 19/04/18
42 FNU network Proof of concept 2 wks Fri 20/04/18 Sun 29/04/18
43 Penetration testing using Kali Linux 4 days Fri 20/04/18 Mon 23/04/18
44 Consolidated Portfolio 3 days Tue 24/04/18 Thu 26/04/18
45 FNU project report and presentation 3 days Fri 27/04/18 Sun 29/04/18
26/02 05/03 12/03 19/03 26/03 02/04 09/04 16/04 23/04 30/04 07/05
February 2018 March 2018 April 2018 May 2018
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Project Risks and Mitigation Plan
The following are the Risk and Mitigation plan for the project –
Scheduling of the Project
The project schedule is a very important part of the project. The project must be finished in
the deadline time provided by the FNU university else there can issues in the communication
of students and staff through the network and they have to suffer from the unavailability of
the new network. So a better scheduling method can lead the project to finish in the allotted
timeline.
Team Communication/ Collaboration
The group project always includes a team which works collaboratively to accomplish the
tasks involved in the project. There should always be a medium of communication between
the team members of the group. For this they can use several applications like Facebook,
Skype, office 365 etc. The team members should work in a team and must always share ideas
and should collaborate their working.
Team Roles/ Responsibilities
A team can only achieve its goals if and only if the team members completes the tasks of the
project. For this, each team member should be allotted their respected roles in the task
involved. Responsibilities are assigned so that the work between the team members gets
divided and working efficiency can be improved. For this RACI matrix can be a great
management tool for assigning roles and responsibilities.
FNU network devices
The network device configuration of FNU is a vast configuration topic. The network
designed consists of various network devices like switches, routers, topologies, modem,
wireless hotspots etc. each has their own configuration according to the network requirement
demanded by the FNU management. Restoration to factory settings can be implemented for
mitigating risk.
10
The following are the Risk and Mitigation plan for the project –
Scheduling of the Project
The project schedule is a very important part of the project. The project must be finished in
the deadline time provided by the FNU university else there can issues in the communication
of students and staff through the network and they have to suffer from the unavailability of
the new network. So a better scheduling method can lead the project to finish in the allotted
timeline.
Team Communication/ Collaboration
The group project always includes a team which works collaboratively to accomplish the
tasks involved in the project. There should always be a medium of communication between
the team members of the group. For this they can use several applications like Facebook,
Skype, office 365 etc. The team members should work in a team and must always share ideas
and should collaborate their working.
Team Roles/ Responsibilities
A team can only achieve its goals if and only if the team members completes the tasks of the
project. For this, each team member should be allotted their respected roles in the task
involved. Responsibilities are assigned so that the work between the team members gets
divided and working efficiency can be improved. For this RACI matrix can be a great
management tool for assigning roles and responsibilities.
FNU network devices
The network device configuration of FNU is a vast configuration topic. The network
designed consists of various network devices like switches, routers, topologies, modem,
wireless hotspots etc. each has their own configuration according to the network requirement
demanded by the FNU management. Restoration to factory settings can be implemented for
mitigating risk.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Technical Risks
The virtual designing and implementation of the network design of FNU is done using cisco
packet tracer. The team must have a great knowledge in operating the software for better
designing and testing of the network design. The risk can be mitigated by having a training
session for team members.
Project Implementation
All the network components must be successfully communicating with each other. Every
functional facility like operation building, backup facility etc. should provide their
functionality to the network.
Backup facility
A large amount of data storage is required for the FNU data. If there is an unconditional
situation of the operation building in which it cannot provide functionality to the network,
then a data backup and recovery facility can be a great idea for implementation. Mitigation of
the risk can be the option of proposing cloud storage.
Security Risks
FNU network should be able to prevent cyber-attacks from the intruders. For this various
security, technologies can be implemented like encryption techniques, ACL (Access Control
List), DMZs, Firewalls, Intrusion Prevention System and Intrusion Detection System.
Security Testing
The network designed and implemented must follow the security policies by applying
security technologies to prevent the network from outside attacks. But for the proper working
of the security implemented several measures can be taken like penetration testing via
backtrack method for testing the security level of the network.
11
The virtual designing and implementation of the network design of FNU is done using cisco
packet tracer. The team must have a great knowledge in operating the software for better
designing and testing of the network design. The risk can be mitigated by having a training
session for team members.
Project Implementation
All the network components must be successfully communicating with each other. Every
functional facility like operation building, backup facility etc. should provide their
functionality to the network.
Backup facility
A large amount of data storage is required for the FNU data. If there is an unconditional
situation of the operation building in which it cannot provide functionality to the network,
then a data backup and recovery facility can be a great idea for implementation. Mitigation of
the risk can be the option of proposing cloud storage.
Security Risks
FNU network should be able to prevent cyber-attacks from the intruders. For this various
security, technologies can be implemented like encryption techniques, ACL (Access Control
List), DMZs, Firewalls, Intrusion Prevention System and Intrusion Detection System.
Security Testing
The network designed and implemented must follow the security policies by applying
security technologies to prevent the network from outside attacks. But for the proper working
of the security implemented several measures can be taken like penetration testing via
backtrack method for testing the security level of the network.
11
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





